ESET Cyber Security for macOS Gebruikershandleiding
- Type
- Gebruikershandleiding

ESET, spol. s r.o.
ESET Cybe r Security is ontwikkel d door ESET, s pol . s r.o.
Ga voor meer i nforma tie na ar www.eset.com.
Alle rechten voorbehouden. Niets uit deze documenta tie ma g worden verveelvoudigd, opgeslagen in een
systeem voor het ophalen van gegevens of overgedra gen, in enige vorm of op enige wijze, hetzij elektronisch,
mecha nisch, door fotokopie, opna me, s can of enige a ndere manier, zonder schriftelijke toestemming van de
auteur.
ESET, spol. s r.o. behoudt zich het recht voor de bes chreven toepass ingssoftwa re zonder voorafga ande
kennisgeving te wijzigen.
Klantenservice: www.eset.com/support
REV. 13-10-2017

Inhoudsopgave
.......................................................5ESET Cyber Security1.
....................................................................................................5Wat is nieuw in versie 61.1
....................................................................................................5Systeemvereisten1.2
.......................................................6Installatie2.
....................................................................................................6Standaardinstallatie2.1
....................................................................................................7Aangepaste installatie2.2
.......................................................8Productactivering3.
.......................................................9Verwijderen4.
.......................................................10Basisoverzicht5.
....................................................................................................10Sneltoetsen5.1
....................................................................................................11Beveiligingsstatus controleren5.2
....................................................................................................11
Te volgen procedure als het programma
niet correct werkt
5.3
.......................................................12Computerbeveiliging6.
....................................................................................................12Antivirus- en antispywarebeveiliging6.1
..............................................................................12Algemeen
6.1.1
..................................................................................12Uitsluitingen
6.1.1.1
..............................................................................13Beveiliging bij het opstarten
6.1.2
..............................................................................13Real-timebeveiliging va n bes tandss ysteem
6.1.3
..................................................................................13Geavanceerde opties
6.1.3.1
..................................................................................13
Wanneer moet de configuratie voor
Real-timebeveiliging worden gewijzigd?
6.1.3.2
..................................................................................14Real-timebeveiliging controleren
6.1.3.3
..................................................................................14
Te volgen procedure als Real-timebeveiliging niet
werkt
6.1.3.4
..............................................................................14On-demand computersca n
6.1.4
..................................................................................15Type sca n
6.1.4.1
........................................................................15Smart scan
6.1.4.1.1
........................................................................15Aangepa ste scan
6.1.4.1.2
..................................................................................15Scandoelen
6.1.4.2
..................................................................................16Scanprofielen
6.1.4.3
..............................................................................16Pa rameters voor ThreatSense-engine ins tellen
6.1.5
..................................................................................17Objecten
6.1.5.1
..................................................................................17Opties
6.1.5.2
..................................................................................17Opschonen
6.1.5.3
..................................................................................18Uitsluitingen
6.1.5.4
..................................................................................18Limiet
6.1.5.5
..................................................................................18Overige
6.1.5.6
..............................................................................18Er is een infiltratie gedetecteerd
6.1.6
....................................................................................................19
Scannen en blokkeren van
verwisselbare media
6.2
.......................................................20Antiphishing7.
.......................................................21Web- en e-mailbeveiliging8.
....................................................................................................21Webbeveiliging8.1
..............................................................................21Poorten
8.1.1
..............................................................................21URL-lijsten
8.1.2
....................................................................................................21E-mailbeveiliging8.2
..............................................................................22POP3-protocolcontrole
8.2.1
..............................................................................22IMAP-protocolcontrole
8.2.2
.......................................................23Bijwerken9.
....................................................................................................23Instellingen voor bijwerken9.1
..............................................................................23Geava nceerde opties
9.1.1
....................................................................................................23Updatetaken maken9.2
....................................................................................................24
ESET Cyber Security bijwerken naar een
nieuwe versie
9.3
....................................................................................................24Systeemupdates9.4
.......................................................25Hulpmiddelen10.
....................................................................................................25Logbestanden10.1
..............................................................................25Logbestanden onderhouden
10.1.1
..............................................................................26Logbestanden filteren
10.1.2
....................................................................................................26Planner10.2
..............................................................................27Nieuwe taken maken
10.2.1
..............................................................................27Door gebruiker gedefinieerde ta ken ma ken
10.2.2
....................................................................................................28Quarantaine10.3
..............................................................................28Bestanden in quara nta ine plaatsen
10.3.1
..............................................................................28Hers tellen va nuit quara nta ine
10.3.2
..............................................................................28Bestand verzenden vanuit qua rantaine
10.3.3
....................................................................................................28Actieve processen10.4
....................................................................................................29Live Grid10.5
..............................................................................29Live Grid installeren
10.5.1
.......................................................30Gebruikersinterface11.
....................................................................................................30Waarschuwingen en meldingen11.1
..............................................................................30Waarschuwingen weergeven
11.1.1
..............................................................................30Beveiligingsstatussen
11.1.2
....................................................................................................31Machtigingen11.2
....................................................................................................31Contextmenu11.3
.......................................................32Overige12.
....................................................................................................32Instellingen importeren en exporteren12.1
....................................................................................................32Proxyserver instellen12.2
.......................................................33Woordenlijst13.
....................................................................................................33Typen infiltraties13.1
..............................................................................33Virussen
13.1.1
..............................................................................33Wormen
13.1.2
..............................................................................33Trojaanse paarden
13.1.3
..............................................................................34Rootkits
13.1.4
..............................................................................34Adware
13.1.5
..............................................................................34Spyware
13.1.6
..............................................................................34Potentieel onveilige toepassingen
13.1.7
..............................................................................35Potentieel ongewenste toepassingen
13.1.8
....................................................................................................35Typen externe aanvallen13.2
..............................................................................35DoS-aanvallen
13.2.1

..............................................................................35DNS Poisoning
13.2.2
..............................................................................35Port scanning
13.2.3
..............................................................................35TCP-desynchronisatie
13.2.4
..............................................................................36SMB Relay
13.2.5
..............................................................................36ICMP-aanvallen
13.2.6
....................................................................................................36E-mail13.3
..............................................................................36Advertenties
13.3.1
..............................................................................37Nepmeldingen
13.3.2
..............................................................................37Phishing
13.3.3
..............................................................................37Oplichterijspam herkennen
13.3.4

5
1. ESET Cyber Security
ESET Cyber Security vertegenwoordigt een nieuwe benadering van echt geїntegreerde computerbeveiliging. De meest recente versie
van de ThreatSense®-scanengine houdt uw computer met snelheid en precisie veilig. Het resultaat is een intelligent systeem dat
continu alert is en uw computer verdedigt tegen aanvallen en schadelijke software.
ESET Cyber Security is een complete beveiligingsoplossing die voortkomt uit onze jarenlange inspanningen om een maximale
beveiliging te combineren met een minimale systeembelasting. De geavanceerde technologieën, gebaseerd op kunstmatige
intelligentie, kunnen proactief infiltraties door virussen, wormen, trojaanse paarden, spyware, adware, rootkits en andere
aanvallen vanaf internet tegen ESET Cyber Security voorkomen, zonder dat de prestaties van uw systeem daardoor achteruitgaan.
1.1 Wat is nieuw in versie 6
Met ESET Cyber Security versie 6 worden de volgende updates en verbeteringen geïntroduceerd:
· Anti-Phishing: verhindert dat nepsites zich als betrouwbare websites vermommen en uw persoonlijke informatie proberen te
stelen.
· Systeemupdates: ESET Cyber Security versie 6 biedt diverse oplossingen en verbeteringen, waaronder meldingen over
besturingss ysteemupdates . Zie de sectie Systeemupdates voor meer informatie.
· Beveiligingsstatussen: verbergt meldingen van het scherm Beveiligingsstatus (bijvoorbeeld Beveiliging van e-mail uitgeschakeld of
Computer moet opnieuw worden opgestart)
· Te scannen media: bepaalde mediatypen kunnen worden uitgesloten van de real-timescanner (lokale stations, verwisselbare
media, netwerkmedia)
1.2 Systeemvereisten
Voor optimale prestaties van ESET Cyber Security moet uw systeem voldoen aan de volgende minimale hardware- en
softwarevereisten:
Systeemvereisten
Processorarchitectuur
Intel 32-bits, 64-bits
Besturingssysteem
macOS 10.6 of later
Geheugen
300 MB
Vrije schijfruimte
200 MB
24

6
2. Installatie
Sluit alle programma's op de computer voordat u het installatieproces start. ESET Cyber Security bevat onderdelen die tot
conflicten kunnen leiden met andere antivirusprogramma's die op de computer zijn geïnstalleerd. ESET raadt u aan dergelijke
antivirusprogramma's te verwijderen om potentiële problemen te voorkomen.
Ga op een van de volgende manieren te werk om de installatiewizard te starten:
· Als u het programma installeert vanaf de installatie-cd/dvd, plaatst u deze in de computer, opent u deze vanaf het bureaublad of
het Finder-venster en dubbelklikt u op het pictogram Installeren.
· Als u installeert met een bestand dat u hebt gedownload van de ESET-website, opent u het bestand en dubbelklikt u op het
pictogram Installeren
De installatiewizard begeleidt u tijdens de installatie. Tijdens de eerste fase van de installatie zoekt het installatieprogramma
automatisch online naar de meest recente productversie. Als er een nieuwere versie wordt gevonden, hebt u de mogelijkheid de
nieuwste versie te downloaden alvorens het installatieproces voor te zetten.
Nadat u akkoord bent gegaan met de eindgebruikersovereenkomst wordt u gevraagd een van de volgende installatiemodi te
selecteren:
· Standaardinstallatie
· Aangepaste installatie
2.1 Standaardinstallatie
De standaard installatiemodus omvat de configuratieopties die geschikt zijn voor de meeste gebruikers. Deze instellingen bieden
maximale veiligheid in combinatie met uitstekende systeemprestaties. De standaardinstallatie is de standaardoptie en wordt
aanbevolen als u geen speciale vereisten hebt voor bepaalde instellingen.
ESET Live Grid
Het Live Grid vroegtijdig waarschuwingssysteem helpt waarborgen dat ESET onmiddellijk en continu wordt geïnformeerd over
nieuwe infiltraties teneinde klanten snel bescherming te kunnen bieden. Het systeem maakt het mogelijk nieuwe bedreigingen in te
zenden naar het bedreigingslaboratorium van ESET, waar deze worden geanalyseerd en verwerkt. ESET Live Grid inschakelen
(aanbevolen) is standaard geselecteerd. Klik op Instellen om gedetailleerde instellingen voor het verzenden van verdachte
bestanden te wijzigen. Zie Live Grid voor meer informatie.
Potentieel ongewenste toepassingen
De laatste stap in het installatieproces is het configureren van detectie van Mogelijk ongewenste toepassingen. Dergelijke
programma's zijn niet per se schadelijk, maar kunnen het gedrag van het besturingssysteem vaak negatief beïnvloeden. Deze
toepassingen worden vaak meegeleverd met andere programma's en vallen nauwelijks op tijdens de installatie. Hoewel bij deze
toepassingen gewoonlijk een melding wordt weergegeven tijdens de installatie, kunnen ze eenvoudig zonder uw toestemming
worden geïnstalleerd.
Na installatie van ESET Cyber Security moet u de computer scannen op schadelijke code. Klik in het hoofdvenster van het
pr ogra mma op Computerscan en kl ik vervolgens op Smart scan. Raadpleeg het gedeelte Computerscan op aanvraag voor meer
informatie over on-demand computerscans.
6
7
29
14

7
2.2 Aangepaste installatie
De aangepaste installatiemodus is bedoeld voor ervaren gebruikers die geavanceerde instellingen willen wijzigen tijdens de
installatie.
Proxyserver
Als u een proxyserver gebruikt, kunt u de parameters daarvan opgeven door de optie Ik gebruik een proxyserver te selecteren. Geef
in het volgende venster het IP-adres of de URL van uw proxyserver op in het veld Adres. Geef in het veld Poort de poort op waarop
de proxyserver verbindingen accepteert (standaard is dit 3128). Als de proxyserver verificatie vereist, moet u een geldige
gebruikersnaam en een geldig wachtwoord invoeren om toegang te krijgen tot de proxyserver. Als u geen proxyserver gebruikt,
s el ecteert u Ik gebruik geen proxyserver. Als u niet zeker weet of u een proxyserver gebruikt, kunt u uw huidige systeeminstellingen
gebrui ken door Systeeminstellingen gebruiken (aanbevolen) te selecteren.
Machtigingen
In de volgende stap kunt u gemachtigde gebruikers of groepen definiëren die de programmaconfiguratie kunnen bewerken.
Selecteer de gebruikers in de lijst aan de linkerkant en klik op Toevoegen om hen toe te voegen aan de lijst Gemachtigde
gebruikers. Als u alle systeemgebruikers wilt weergeven, selecteert u Alle gebruikers weergeven. Als u de lijst Gemachtigde
gebruikers leeg laat, worden alle gebruikers beschouwd als gemachtigd.
ESET Live Grid
Het Live Grid vroegtijdig waarschuwingssysteem helpt waarborgen dat ESET onmiddellijk en continu wordt geïnformeerd over
nieuwe infiltraties teneinde klanten snel bescherming te kunnen bieden. Het systeem maakt het mogelijk nieuwe bedreigingen in te
zenden naar het bedreigingslaboratorium van ESET, waar deze worden geanalyseerd en verwerkt. ESET Live Grid inschakelen
(aanbevolen) is standaard geselecteerd. Klik op Instellen... om gedetailleerde instellingen voor het verzenden van verdachte
bestanden te wijzigen. Zie Live Grid voor meer informatie.
Potentieel ongewenste toepassingen
De laatste stap in het installatieproces is het configureren van detectie van Mogelijk ongewenste toepassingen. Dergelijke
programma's zijn niet per se schadelijk, maar kunnen het gedrag van het besturingssysteem vaak negatief beïnvloeden. Deze
toepassingen worden vaak meegeleverd met andere programma's en vallen nauwelijks op tijdens de installatie. Hoewel bij deze
toepassingen gewoonlijk een melding wordt weergegeven tijdens de installatie, kunnen ze eenvoudig zonder uw toestemming
worden geïnstalleerd.
Na installatie van ESET Cyber Security moet u de computer scannen op schadelijke code. Klik in het hoofdvenster van het
pr ogra mma op Computerscan en kl ik vervolgens op Smart scan. Raadpleeg het gedeelte Computerscan op aanvraag voor meer
informatie over on-demand computerscans.
29
14

8
3. Productactivering
Na installatie wordt automatisch het venster Productactivering weergegeven. U kunt het dialoogvenster Productactivering op elk
moment oproepen door op het ESET Cyber Security-pictogram te klikken op de macOS-menubalk (boven aan het scherm) en
vervolgens op Productactivering... te klikken.
· Licentiecode: een unieke tekenreeks in de notatie XXXX-XXXX-XXXX-XXXX-XXXX of XXXX-XXXXXXXX die wordt gebruikt om de
licentie-eigenaar te identificeren en de licentie te activeren. Als u een versie in de detailhandel hebt aangeschaft, activeert u uw
product met een Licentiecode. Deze bevindt zich doorgaans binnen in of op de achterkant van de productverpakking.
· Gebruikersnaam en wachtwoord: als u een gebruikersnaam en wachtwoord hebt en niet weet hoe u ESET Cyber Security activeert,
kl ik dan op Ik heb een gebruikersnaam en wachtwoord. Wat kan ik doen?. U wordt dan doorverwezen naar my.eset.com, waar u
uw referenties kunt omzetten in een Licentiecode.
· Gratis bètatest: selecteer deze optie als u ESET Cyber Security wilt evalueren voordat u tot aanschaf overgaat. Vul uw e-
mailadres in om ESET Cyber Security voor een beperkte tijd te activeren. Uw testlicentie wordt per e-mail naar u verzonden.
Proeflicenties kunnen slechts eenmaal per klant worden geactiveerd.
· Licentie kopen: als u geen licentie hebt en er een wilt kopen, klikt u op Licentie kopen. U wordt dan doorgestuurd naar de website
va n de ESET-distributeur in uw regio.
· Later activeren: klik op deze optie als u op dit moment niet wilt activeren.

9
4. Verwijderen
Als u ESET Cyber Security wilt verwijderen, kan dit op de volgende manieren:
· plaats de installatie-cd/dvd van ESET Cyber Security in de computer, open deze vanaf het bureaublad of het Finder-venster en
dubbel kl i k op Verwijderen;
· open het installatiebestand van ESET Cyber Security (.dmg) en dubbelkl ik op Verwijderen;
· start Finder, open de map Programma's op de vaste schijf, druk op CTRL en klik op het pictogram ESET Cyber Security , en
selecteer Toon pakketinhoud. Open de map Contents > Helpers en dubbel kli k op het pictogram Uninstaller.

10
5. Basisoverzicht
Het hoofdvenster van ESET Cyber Security is onderverdeeld in twee hoofdgedeelten. In het hoofdvenster aan de rechterkant wordt
informatie weergegeven over de optie die is geselecteerd in het hoofdmenu aan de linkerkant.
De volgende onderdelen zijn toegankelijk vanuit het hoofdmenu:
· Start: hier vindt u informatie over de beveiligingsstatus van uw computer, web- en e-mailbeveiliging.
· Computerscan: in dit gedeelte kunt u de Computerscan op aanvraag configureren en starten.
· Bijwerken: hier wordt informatie weergegeven over updates van de detectiemodules.
· Instellingen: selecteer deze sectie om het beveiligingsniveau van uw computer aan te passen.
· Hulpmiddelen: hier hebt u toegang tot Logbestanden , Planner , Quarantaine , Actieve processen en andere functies
van het programma.
· Help: hier hebt u toegang tot Help-bestanden, de kennisbank op internet, het aanvraagformulier voor ondersteuning en
aanvullende informatie over het programma.
5.1 Sneltoetsen
U kunt de volgende sneltoetsen gebruiken wanneer u met ESET Cyber Security werkt:
· cmd+,: hiermee geeft u ESET Cyber Security-voorkeuren weer,
· cmd+O: hiermee wijzigt u het formaat van het hoofdvenster van de gebruikersinterface van ESET Cyber Security in het
standaardformaat en verplaatst u dit naar het midden van het scherm,
· cmd+Q: hiermee verbergt u het hoofdvenster van de gebruikersinterface van ESET Cyber Security. U opent dit door te klikken op
het ESET Cyber Securi ty-pictogram op de macOS-menubalk (boven in het scherm),
· cmd+W: hiermee sluit u het hoofdvenster van de gebruikersinterface van ESET Cyber Security.
De volgende sneltoetsen werken alleen als de optie Standaardmenu gebruiken i s i nges chakel d onder Instellingen > Voorkeuren
voor toepassing opgeven... > Interface:
· cmd+alt+L: hiermee opent u het gedeelte Logbestanden,
· cmd+alt+S: hiermee opent u het gedeelte Planner,
· cmd+alt+Q: hiermee opent u het gedeelte Quarantaine.
14
25 26 28 28

11
5.2 Beveiligingsstatus controleren
Klik op Thuis in het hoofdmenu als u uw beveiligingsstatus wilt controleren. Er wordt een statusoverzicht over de werking van ESET
Cyber Security-modules weergegeven in het hoofdvenster.
5.3 Te volgen procedure als het programma niet correct werkt
Wanneer een module correct werkt, wordt er een groen pictogram weergegeven. Wanneer een module niet correct werkt, wordt er
een rood uitroepteken of een oranje meldingspictogram weergegeven. Er wordt aanvullende informatie over de module en een
voorgestelde oplossing voor het probleem weergegeven. U kunt de status van afzonderlijke modules wijzigen door op de blauwe
koppeling onder elk waarchuwingsbericht te klikken.
Als u een probleem niet kunt oplossen met de voorgestelde oplossingen, kunt u zoeken in de ESET-kennisbank zoeken naar een
opl ossing of contact opnemen met de klantenservice van ESET. De klantenservice zal uw vragen zo spoedig mogelijk beantwoorden
en eventuele problemen met ESET Cyber Security oplossen.

12
6. Computerbeveiliging
De computerconfiguratie i s te vinden in Instellingen > Computer. Hier wordt de status weergegeven van Real-timebeveiliging van
bestandssysteem en Blokkering van verwisselbare media. U kunt afzonderlijke modules uitschakelen door de knop van de
betreffende module om te schakelen naar UITGESCHAKELD. Het beveiligingsniveau van de computer kan hierdoor verslechteren.
Voor toegang tot gedetailleerde instellingen voor elke module klikt u op Instellingen....
6.1 Antivirus- en antispywarebeveiliging
Antivirusbeveiliging beschermt tegen schadelijke aanvallen op het systeem door mogelijk gevaarlijke bestanden te wijzigen. Als
een bedreiging via schadelijke code wordt gedetecteerd, kan de antivirusmodule deze onschadelijk maken door de code eerst te
blokkeren en deze vervolgens op te schonen, te verwijderen of in quarantaine te plaatsen.
6.1.1 Algemeen
In het gedeelte Algemeen (Instellingen > Voorkeuren voor toepassing opgeven... > Algemeen) kunt u detectie van de volgende
soorten toepassingen inschakelen:
· Potentieel ongewenste toepassingen - deze toepassingen zijn niet per se schadelijk, maar kunnen de prestaties van uw
computer beïnvloeden. Voor de installatie van dergelijke toepassingen moet doorgaans toestemming worden gegeven. Deze
toepassingen veranderen de manier waarop uw computer werkt (vergeleken met de manier waarop deze werkte voordat deze
toepassingen werden geïnstalleerd). De meest ingrijpende wijzigingen omvatten ongewenste pop-upvensters, activering en
uitvoering van verborgen processen, toegenomen gebruik van systeembronnen, wijzigingen in zoekresultaten en programma's
die communiceren met externe servers.
· Potentieel onveilige toepassingen - deze toepassingen verwijzen naar commerciële, legitieme software die kan worden misbruikt
door aanvallers, als deze wordt geïnstalleerd zonder toestemming van de gebruiker. Deze categorie omvat programma's zoals
hulpmiddelen voor externe toegang. Dat is de reden waarom deze optie standaard is uitgeschakeld.
· Verdachte toepassingen - deze toepassingen omvatten programma's die zijn gecomprimeerd met packers of protectors. Deze
soorten protectors worden vaak door malwareauteurs gebruikt om detectie te omzeilen. Een packer is een zelfuitpakkend
uitvoerbaar bestand waarin verschillende soorten malware in één pakket zijn verzameld. De meest gebruikte packers zijn UPX,
PE_Compact, PKLite en ASPack. Dezelfde malware kan anders worden gedetecteerd wanneer deze met een andere packer is
gecomprimeerd. Packers kunnen hun 'handtekeningen' in de loop van de tijd doen veranderen, waardoor het moeilijker is
malware te detecteren en te verwijderen.
Voor het ins tell en van Uitsluitingen van het bestandssysteem of internet en e-mail kli kt u op de knop Instellen....
6.1.1.1 Uitsluitingen
In het gedeelte Uitsluitingen kunt u bepaalde bestanden en mappen, toepassingen of IP/IPv6-adressen opgeven die u wilt uitsluiten
van het scannen.
Bestanden en mappen die worden vermeld op het tabblad Bestandssysteem worden van alle scanners uitgesloten: Opstarten, Real-
time en On-demand (Computerscan).
· Pad: het pad naar uitgesloten bestanden en mappen.
· Bedreiging: als er naast een uitgesloten bestand de naam van een bedreiging wordt weergegeven, betekent dit dat het bestand
alleen wordt uitgesloten voor de betreffende bedreiging, maar niet volledig. Als het bestand later wordt geïnfecteerd door andere
malware, wordt het bestand gedetecteerd door de antivirusmodule.
· : hiermee wordt een nieuwe uitsluiting gemaakt. Voer het pad in naar een object (u kunt ook de jokertekens * en ? gebruiken)
of selecteer de map of het bestand in de boomstructuur.
· : hiermee worden geselecteerde vermeldingen verwijderd
· Standaard: hiermee worden alle uitsluitingen geannuleerd
Op het tabbl ad Web en e-mail kunt u bepaal de Toepassingen of IP/IPv6-adressen uitsluiten van protocolscannen.
12

13
6.1.2 Beveiliging bij het opstarten
Met Opstartbestanden controleren worden bestanden automatisch gescand bij het opstarten van het systeem. Deze scan wordt
standaard regelmatig als een geplande taak uitgevoerd nadat de gebruiker zich heeft aangemeld of na een update van de
detectiemodules. Voor het wijzigen van de parameterinstellingen voor de ThreatSense-engine die van toepassing zijn op het
scannen bij het opstarten, klikt u op de knop Instellen. Meer informatie over het instellen van de ThreatSense-engine vindt u in deze
sectie .
6.1.3 Real-timebeveiliging van bestandssysteem
De real-timebeveiliging van het bestandssysteem controleert alle typen media en de scan wordt geactiveerd door verschillende
gebeurtenissen. Real-timebeveiliging van het bestandssysteem door ThreatSense-technologie (beschreven in Parameters voor
ThreatSense-engine instellen ) kan voor nieuw gemaakte bestanden anders zijn dan voor reeds bestaande bestanden. Nieuwe
bestanden kunnen nauwkeuriger worden beheerd.
Standaard worden alle bestanden gescand op het moment dat ze worden geopend, gemaakt of uitgevoerd. Wij adviseren u deze
standaardinstellingen te handhaven aangezien deze uw computer het hoogste niveau van Real-timebeveiliging bieden. Real-
timebeveiliging wordt gestart bij het opstarten van het systeem en scant ononderbroken. In speciale gevallen (zoals bij een conflict
met een andere real-timescanner) kan de real-timebeveiliging worden beëindigd door op de menubalk (boven aan het scherm) op
het pi ctogram ESET Cyber Securi ty te klikken (boven aan het scherm. Selecteer daarna Real-timebeveiliging van bestandssysteem
uitschakelen. U kunt de real-timebeveiliging van bestanden ook in het hoofdvenster van het programma uitschakelen (klik op
Instellen > Computer en zet Real-timebeveiliging van bestandsysteem op UITGESCHAKELD).
De volgende mediatypen kunnen worden uitgesloten bij de scanner voor Real-time:
· Lokale stations: systeemschijven
· Verwisselbare media: cd's/dvd's, USB-media, Bluetooth-apparaten, enz.
· Netwerkmedia: alle gekoppelde stations
Het wordt aangeraden de standaardinstellingen te gebruiken en scanuitsluitingen alleen in specifieke gevallen te wijzigen,
bijvoorbeeld wanneer het scannen van bepaalde media tot aanzienlijke vertragingen in de gegevensoverdracht leidt.
Als u geavanceerde instellingen voor Real-timebeveiliging van bestandssysteem wilt wijzigen, gaat u naar Instellingen >
Voorkeuren voor toepassing opgeven... (of druk op cmd+, > Real-timebeveiliging en kli k op Instellen... naast Geavanceerde opties
(bes chreven i n Geavanceerde scanopties ).
6.1.3.1 Geavanceerde opties
In dit venster kunt u definiëren welke objecttypen door de ThreatSense-engine worden gescand. Voor meer informatie over
Zelfuitpakkende archieven, Software voor runtime-compressie en Geavanceerde heuristiek, verwijzen wi j u naar Parameters voor
ThreatSense-engine instellen .
We raden niet aan wijzigingen aan te brengen in het gedeelte Standaardarchiefinstellingen, tenzij u een specifiek probleem wilt
oplossen, aangezien hogere nestingsniveaus voor archieven de systeemprestaties negatief kunnen beïnvloeden.
ThreatSense-parameters voor uitgevoerde bestanden: standaa rd wordt Geavanceerde heuristiek gebruikt wanneer bestanden
worden uitgevoerd. Wij raden ten zeerste aan Smart-optimalisatie en ESET Live Grid ingeschakeld te laten om negatieve gevolgen
voor de systeemprestaties te beperken.
Compatibiliteit van netwerkvolumes vergroten: met deze optie verbetert u de prestaties wanneer bestanden via het netwerk
worden geopend. Deze optie moet worden ingeschakeld als u met vertragingen te maken krijgt wanneer bestanden op
netwerkstations worden geopend. Deze functie maakt op macOS 10.10 en later gebruik van de systeembestandcoördinator. Niet
al le toepassi ngen ondersteunen de systeembestandcoördi nator. Microsoft Word 2011 bijvoorbeeld ondersteunt deze functie niet
en Word 2016 wel.
6.1.3.2 Wanneer moet de configuratie voor Real-timebeveiliging worden gewijzigd?
Real-timebeveiliging is het meest essentiële onderdeel om een systeem veilig te houden met ESET Cyber Security. Wees voorzichtig
bij het aanpassen van de parameters voor Real-timebeveiliging. Wij adviseren u deze parameters alleen te wijzigen in specifieke
situaties. Bijvoorbeeld een situatie waarin er een conflict is met een bepaalde toepassing.
Na installatie van ESET Cyber Security zijn alle instellingen geoptimaliseerd om gebruikers een zo hoog mogelijk niveau van
systeembeveiliging te bieden. U kunt de standaardinstellingen herstellen door te klikken op Standaard linksonder in het venster
Real-timebeveiliging (Instellingen > Voorkeuren voor toepassing opgeven... > Real-timebeveiliging).
16
16
13
17

14
6.1.3.3 Real-timebeveiliging controleren
Downl oa d het eicar.com-testbestand en controleer of ESET Cyber Security dit als bedreiging detecteert zodat u zeker weet dat Real-
timebeveiliging werkt en virussen detecteert. Dit testbestand is een speciaal, onschadelijk bestand dat door alle virusprogramma's
kan worden gedetecteerd. Het bestand is gemaakt door EICAR (European Institute for Computer Antivirus Research) om de werking
van antivirusprogramma's te testen.
6.1.3.4 Te volgen procedure als Real-timebeveiliging niet werkt
In dit hoofdstuk worden probleemsituaties beschreven die zich kunnen voordoen bij het gebruik van Real-timebeveiliging, en
oplos s ingen hi ervoor .
Real-timebeveiliging is uitgeschakeld
Als Real-timebeveiliging per ongeluk is uitgeschakeld door de gebruiker, moet Real-timebeveiliging opnieuw worden geactiveerd. U
kunt Real-timebeveiliging opnieuw activeren door in het hoofdmenu te klikken op Instellingen > Computer en Real-timebeveiliging
van bestandssystemen op INGESCHAKELD te zetten. U kunt Real-timebeveiliging van bestandssysteem ook inschakelen in het
venster met voorkeuren voor de toepassing onder Real-timebeveiliging door Real-timebeveiliging van bestandssysteem inschakelen
te selecteren.
Real-time beveiliging voert geen detecties uit en schoont geen infiltraties op
Controleer of er geen andere antivirusprogramma's zijn geïnstalleerd op de computer. Als twee programma's voor real-
timebeveiliging tegelijk zijn geactiveerd, conflicteren deze mogelijk. Wij adviseren u alle eventuele andere antivirusprogramma's
van uw systeem te verwijderen.
Real-timebeveiliging wordt niet gestart
Als real-timebeveiliging niet wordt geactiveerd wanneer u het systeem opstart, zijn er mogelijk conflicten met andere programma's.
Als dat het geval is, neem dan contact op met ESET Klantenservice.
6.1.4 On-demand computerscan
Als u vermoedt dat de computer is geïnfecteerd (deze gedraagt zich abnormaal), voert u Smart scan uit om uw computer te
onderzoeken op infiltraties. Voor een optimale beveiliging is het van belang regelmatig een computerscan uit te voeren als
onderdeel van routinematige beveiligingsmaatregelen, niet alleen wanneer u vermoedt dat de computer is geïnfecteerd. Door
regelmatig te scannen kunnen infiltraties worden gedetecteerd die niet door de real-timescanner zijn gedetecteerd op het moment
van opslag op de schijf. Dit kan gebeuren als de real-timescanner was uitgeschakeld op het moment van infectie of de
detectiemodules verouderd waren.
Wij adviseren u minimaal eenmaal per maand een on-demand scan uit te voeren. Scannen kan als geplande taak worden
gec onfi gureer d i n Hulpmiddelen > Planner.

15
Wij adviseren u minimaal eenmaal per maand een on-demand scan uit te voeren. Scannen kan als geplande taak worden
gec onfi gureer d i n Hulpmiddelen > Planner.
Ook kunt u geselecteerde bestanden en mappen vanaf uw bureaublad of vanuit het venster Finder slepen en neerzetten in het
hoofdvenster van ESET Cyber Security, het dock-pictogram, het menubalkpictogram (boven aan het scherm) of het pictogram van
de toepassi ng (in de map /Applications).
6.1.4.1 Type scan
Er zijn twee typen on-demand computerscan beschikbaar. Gebruik een Smart scan om het systeem snel zonder verdere configuratie
van de scanparameters te scannen. Met een Aangepaste scan kunt u elk van de vooraf gedefinieerde scanprofielen selecteren en
speci fi eke s ca ndoelen opgeven.
6.1.4.1.1 Smart scan
Met Smart scan kunt u snel een computerscan starten en geïnfecteerde bestanden opschonen zonder dat er gebruikersinterventie is
vereist. Het belangrijkste voordeel is de eenvoudige werking zonder gedetailleerde scanconfiguratie. Smart scan controleert alle
bestanden in alle mappen en schoont automatisch gedetecteerde infiltraties op of verwijdert deze. Het opschoonniveau wordt
automatisch ingesteld op de standaardwaarde. Zie het gedeelte over Opschonen voor meer informatie over typen
opschoonbewerkingen.
6.1.4.1.2 Aangepaste scan
Aangepaste scan is een optimale oplossing als u scanparameters wilt opgeven, zoals scandoelen en scanmethoden. Het voordeel
van het uitvoeren van een aangepaste scan is de mogelijkheid om de parameters in detail te configureren. Verschillende
configuraties kunnen worden opgeslagen in door de gebruiker gedefinieerde scanprofielen. Deze profielen zijn met name handig
als het scannen herhaaldelijk met dezelfde parameters plaatsvindt.
Als u scandoelen wilt selecteren, selecteert u Computerscan > Aangepaste scan en selecteert u s peci fieke Scandoelen in de
boomstructuur. Een scandoel kan tevens nader worden gespecificeerd door het pad naar de map met het bestand of de bestanden
die u wilt opnemen in te voeren. Als u alleen het systeem wilt scannen zonder aanvullende opschoonacties, selecteert u Scannen
zonder opschonen. Bovendien kunt u een keuze maken uit drie opschoonniveaus door op Instellen... > Opschonen te klikken.
OPMERKING: het uitvoeren van computerscans met Aangepaste scan wordt aanbevolen voor ervaren gebruikers die eerder
antivirusprogramma's hebben gebruikt.
6.1.4.2 Scandoelen
In de boomstructuur met scandoelen kunt u bestanden en mappen selecteren de u op virussen wilt scannen. Mappen kunnen ook
worden geselecteerd aan de hand van de instellingen van een profiel.
Een scandoel kan nader worden gespecificeerd door het pad naar de map met het bestand of de bestanden die u wilt opnemen in
de scan in te voeren. Selecteer doelen in de boomstructuur met alle mappen die beschikbaar zijn op de computer door het
selectievakje bij de bijbehorende bestanden of mappen in te schakelen.
17

16
6.1.4.3 Scanprofielen
U kunt uw voorkeursinstellingen voor scannen opslaan voor toekomstige scans. Wij adviseren u voor elke regelmatig gebruikte
scan een ander profiel te maken (met verschillende scandoelen, scanmethoden en andere parameters).
Als u een nieuw profiel wilt maken, klik dan in het hoofdmenu op Instellingen > Voorkeuren voor toepassing opgeven... (of druk op
cmd+,) > Computerscan en kl ik op Bewerken... naast de lijst met huidige profielen.
Raa dpl eeg het gedeel te Parameters voor ThreatSense-engine instellen voor een beschrijving van elke parameter van de
scaninstellingen, zodat u een scanprofiel kunt maken dat aan uw behoeften voldoet.
Voorbeeld: Stel, u wilt een eigen scanprofiel maken en de Smart scan-configuratie is deels geschikt, maar u wilt geen programma's
voor runtime-compressie of potentieel onveilige toepassingen scannen en u wilt ook Volledig opschonen toepassen. Voer de
profi el naam in het venster Profielenlijst voor on-demand scanner i n, kl ik op de knop Toevoegen en bevestig uw keuze met OK. Pas
vervolgens de parameters aan uw vereisten aan door de ThreatSense-engine en Scandoelen in te stellen.
Als u het besturingssysteem wilt uitschakelen en de computer wilt afsluiten nadat de on-demand scan is voltooid, gebruikt u de
optie Computer afsluiten na scan.
6.1.5 Parameters voor ThreatSense-engine instellen
ThreatSense is een exclusieve technologie van ESET die bestaat uit een combinatie van complexe methoden voor de detectie van
dreigingen. Deze technologie is proactief. Dit betekent dat tevens beveiliging wordt geboden tijdens de eerste uren van de
verspreiding van een nieuwe bedreiging. Er wordt gebruik gemaakt van een combinatie van verschillende methoden (codeanalyse,
code-emulatie, generieke kenmerken enz.) die samenwerken om de systeembeveiliging aanzienlijk te verbeteren. De scanengine is
in staat verschillende gegevensstromen tegelijk te besturen voor een maximale efficiëntie en een zo hoog mogelijk
detecti eper centa ge. De ThreatSense-technologie zorgt tevens voor de verwijdering van rootkits.
Via de ins telli ngsopties voor de ThreatSense-technologie kunt u verschillende scanparameters opgeven:
· Bestandstypen en extensies die moeten worden gescand
· De combinatie van verschillende detectiemethoden
· Opschoonniveaus, enz.
U opent het instellingenvenster door te klikken op Instellen > Voorkeuren voor toepassing opgeven (of druk op cmd+,) en klik op de
knop ThreatSense-engine instellen i n de modul e Beveiliging bij het opstarten, Real-timebeveiliging en Computerscan, die allemaal
gebrui kma ken va n ThreatSense-technologie (zie hieronder). Verschillende beveiligingsscenario's vereisen mogelijk verschillende
configuraties. ThreatSense is individueel configureerbaar voor de volgende beveiligingsmodules:
· Beveiliging bij het opstarten: automatisch bestanden controleren bij het opstarten
· Real-timebeveiliging: Real-timebeveiliging van bestandssysteem
· Computerscan: on-demand computerscan.
· Beveiliging van webtoegang
· E-mailbeveiliging
16

17
De ThreatSense-parameters zijn speciaal geoptimaliseerd voor elke module en wijziging hiervan kan een aanzienlijke invloed
hebben op de werking van het systeem. Als bijvoorbeeld instellingen voor het altijd scannen van programma's voor runtime-
compressie worden gewijzigd of als geavanceerde heuristiek wordt ingeschakeld in de module Real-timebeveiliging van
bestandssysteem, zou dit kunnen resulteren in een vertraging van het systeem. Daarom adviseren wij de standaard ThreatSense-
parameters ongewijzigd te laten voor alle modules met uitzondering van Computerscan.
6.1.5.1 Objecten
In het gedeelte Objecten kunt u definiëren welke bestanden worden gescand op infiltraties.
· Symbolische koppelingen - (alleen computerscan) scant bestandstypen die een tekenreeks bevatten die door het
besturingssysteem wordt geïnterpreteerd en gevolgd als een pad naar een ander bestand of een andere map.
· E-mailbestanden - (niet beschikbaar in real-timebeveiliging) scant e-mailbestanden.
· Postvakken - (niet beschikbaar in real-timebeveiliging) scant postvakken van gebruikers in het systeem. Onjuist gebruik van deze
optie kan leiden tot een conflict met uw e-mailclient. Meer informatie over de voor- en nadelen van deze optie vindt u in dit
knowledgebase-artikel.
· Archieven - (niet beschikbaar in real-timebeveiliging) scant bestanden die zijn gecomprimeerd in archieven (RAR, ZIP, ARJ, TAR,
enz.).
· Zelfuitpakkende archieven - (niet beschikbaar in real-timebeveiliging) scant bestanden die deel uitmaken van zelfuitpakkende
archiefbestanden.
· Software voor runtime-compressie - programma's voor runtime-compressie decomprimeren in het geheugen (in tegenstelling tot
standaardarchieftypen). Als dit is geselecteerd, worden standaardprogramma's voor statische compressie (zoals UPX, yoda,
ASPack, FGS) ook gescand.
6.1.5.2 Opties
In het gedeelte Opties kunt u de methoden selecteren die moeten worden gebruikt tijdens het scannen van het systeem. De volgende
opties zijn beschikbaar:
· Heuristiek: heuristiek maakt gebruik van een algoritme dat de (schadelijke) activiteit van programma's analyseert. Het
voornaamste voordeel van heuristieke detectie is de mogelijkheid om nieuwe schadelijke software te detecteren die eerder nog
niet bestond.
· Geavanceerde heuristiek: geavanceerde heuristiek bestaat uit een uniek heuristisch algoritme dat door ESET is ontwikkeld en dat
is geoptimaliseerd voor het detecteren van computerwormen en trojaanse paarden. Dit algoritme is geschreven in
programmeertalen van hoog niveau. De geavanceerde heuristiek breidt de detectiemogelijkheden van het programma aanzienlijk
uit.
6.1.5.3 Opschonen
De instellingen voor opschonen bepalen op welke manier de scanner geïnfecteerde bestanden opschoont. Er zijn 3
opschoonniveaus:
· Niet opschonen - geïnfecteerde bestanden worden niet automatisch opgeschoond. Er wordt een waarschuwingsvenster
weergegeven en u kunt een actie kiezen.
· Standaard opschonen - hiermee wordt automatisch geprobeerd een geïnfecteerd bestand op te schonen of te verwijderen. Als het
niet mogelijk is de juiste actie automatisch te selecteren, wordt een selectie van vervolgacties aangeboden. De beschikbare
vervolgacties worden tevens weergegeven als een vooraf gedefinieerde actie niet kon worden voltooid.
· Volledig opschonen - alle geïnfecteerde bestanden (inclusief archieven) worden opgeschoond of verwijderd. De enige
uitzonderingen zijn systeembestanden. Als het niet mogelijk is een bestand op te schonen, ontvangt u een melding en wordt u
gevraagd het type actie te selecteren dat moet worden ondernomen.
Waarschuwing: in de modus Standaard opschonen worden hele archiefbestanden alleen verwijderd als alle bestanden in het
archief zijn geïnfecteerd. Als een archief zowel legitieme bestanden als geïnfecteerde bestanden bevat, wordt het archief niet
verwijderd. Als een geïnfecteerd archiefbestand wordt gedetecteerd in de modus Volledig opschonen, wordt het hele archief
verwijderd, zelfs als er schone bestanden aanwezig zijn.

18
6.1.5.4 Uitsluitingen
Een extensie maakt deel uit van een bestandsnaam en wordt afgebakend door een punt. De extensie definieert het type en de
inhoud van een bestand. In dit gedeelte van de instellingen voor ThreatSense-parameters kunt u de typen bestanden definiëren die
u wilt uitsluiten van scannen.
Standaard worden alle bestanden gescand, ongeacht hun extensie. Elke extensie kan worden toegevoegd aan de lijst met bestanden
die zijn uitgesloten van scannen. Met de knoppen en kunt u het scannen van specifieke extensies inschakelen of
verbieden.
Het uitsluiten van bestanden van scannen is soms nodig als het scannen van bepaalde bestandstypen een onjuiste werking
veroorzaakt van het programma. Het kan bijvoorbeeld raadzaam zijn om log-, cfg- en tmp-bestanden uit te sluiten. De juiste notatie
voor het i nvoeren van bestandextensies is:
log
cfg
tmp
6.1.5.5 Limiet
Gebruik het gedeelte Limiet om de maximale grootte op te geven van objecten die moeten worden gescand, evenals het maximale
niveau voor het scannen van geneste archieven:
· Maximumgrootte: de maximale grootte van objecten die moeten worden gescand. Wanneer de maximale grootte is gedefinieerd,
scant de antivirusmodule uitsluitend objecten die kleiner zijn dan de opgegeven grootte. De waarde mag alleen worden
gewijzigd door gevorderde gebruikers die een specifieke reden hebben om grotere objecten niet te scannen.
· Maximumscantijd: de maximale tijd voor het scannen van een object. Als hier een door de gebruiker gedefinieerde waarde is
ingevoerd, wordt het scannen van een object beëindigd wanneer die tijd is verstreken, ongeacht of de scan is voltooid.
· Maximumnestingsniveau: het maximum aantal niveaus waarop archieven moeten worden gescand. Het is in de meeste gevallen
niet nodig de standaardwaarde van 10 te wijzigen. Als het scannen voortijdig wordt afgebroken omdat archieven dieper dan 10
niveaus zijn genest, blijft het archief ongecontroleerd.
· Maximumbestandsgrootte: gebruik deze optie om de maximale bestandsgrootte op te geven voor bestanden in archieven (als
deze worden uitgepakt) die moeten worden gescand. Als het scannen van een archief vanwege deze limiet voortijdig wordt
afgebroken, blijft het archief ongecontroleerd.
6.1.5.6 Overige
Smart-optimalisatie inschakelen
Wanneer Smart-optimalisatie is ingeschakeld, worden de instellingen geoptimaliseerd om het meest efficiënte scanniveau te
garanderen, zonder dat dit ten koste gaat van de scansnelheid. De diverse beveiligingsmodules scannen op intelligente wijze,
waarbij gebruik wordt gemaakt van verschillende scanmethoden. De Smart-optimalisatie is niet strikt gedefinieerd in het product.
Het ontwikkelingsteam van ESET implementeert continu nieuwe wijzigingen, die vervolgens via de regelmatige updates worden
geïntegreerd in ESET Cyber Security. Als de Smart-optimalisatie is uitgeschakeld, worden alleen de door de gebruiker gedefinieerde
instellingen in de ThreatSense-technologie van de betreffende module toegepast bij het uitvoeren van een scan.
Alternatieve gegevensstromen scannen (alleen on-demand scanner)
Alternatieve gegevensstromen (resource/gegevensvorken) die worden gebruikt door het bestandssysteem zijn bestands- en
mapkoppelingen die onzichtbaar zijn voor normale scantechnieken. Veel infiltraties proberen detectie te vermijden door zichzelf te
vermommen als alternatieve gegevensstromen.
6.1.6 Er is een infiltratie gedetecteerd
Infiltraties kunnen het systeem via verschillende toegangspunten bereiken: webpagina's, gedeelde mappen, e-mail of
verwisselbare computermedia (USB, externe schijven, cd's, dvd's enz.).
Als de computer tekenen van infectie door malware vertoont, bijvoorbeeld als deze trager is, vaak vastloopt, enz., adviseren wij u
het volgende te doen:
1. Klik op Computerscan.
2. Klik op Smart scan (zi e het gedeelte Smart scan voor meer informatie).
3. Nadat de scan is voltooid, controleert u in het logbestand het aantal gescande, geïnfecteerde en opgeschoonde bestanden.
Als u alleen een bepaald gedeelte van uw schijf wilt scannen, klikt u op Aangepaste scan en selecteert u doelen die u wilt scannen
op virussen.
Als algemeen voorbeeld van hoe infiltraties worden afgehandeld door ESET Cyber Security, gaan we ervan uit dat een infiltratie is
gedetecteerd door de real-timebewaking van het bestandssysteem, welke gebruikmaakt van het standaardopschoonniveau. De
real-timebewaking probeert het bestand op te schonen of te verwijderen. Als er geen vooraf gedefinieerde actie beschikbaar is voor
de module voor real-timebeveiliging, wordt u via een waarschuwingsvenster gevraagd om een optie te selecteren. Gewoonlijk zijn
15

19
de opti es Opschonen, Verwijderen en Geen actie beschi kbaar. Het wordt niet aanbevolen Geen actie te selecteren, aangezien de
geïnfecteerde bestanden dan geïnfecteerd zouden blijven. Deze optie is bedoeld voor situaties waarin u zeker weet dat het bestand
onschadelijk is en per ongeluk is gedetecteerd.
Opschonen en verwijderen - pas opschonen toe als een bestand is aangevallen door een virus dat schadelijke code aan het
bestand heeft toegevoegd. Als dit het geval is, probeert u eerst het geïnfecteerde bestand op te schonen zodat het in de
oorspronkelijke staat kan worden hersteld. Als het bestand uitsluitend uit schadelijke code bestaat, wordt het verwijderd.
Bestanden in archieven verwijderen - in de modus Standaard opschonen wordt het volledige archief alleen verwijderd als dit
uitsluitend geïnfecteerde en geen schone bestanden bevat. Met andere woorden, archieven worden niet verwijderd als zij ook
onschadelijke, schone bestanden bevatten. Wees echter voorzichtig bij het gebruik van een scan in de modus Volledig opschonen:
met Volledig opschonen wordt het archief verwijderd als het minimaal één geïnfecteerd bestand bevat, ongeacht de status van
andere bestanden in het archief.
6.2 Scannen en blokkeren van verwisselbare media
ESET Cyber Security biedt een on-demand scan van geplaatste verwisselbare media-apparaten (cd, dvd, USB, iOS-apparaat enz.).
Verwisselbare media kunnen schadelijke code bevatten en uw computer in gevaar brengen. Als u verwisselbare media wilt
blokkeren, klikt u op de knop Mediablokkering instellen (zie de bovenstaande afbeelding) of Instellingen > Voorkeuren voor
toepassing opgeven... > Media in het hoofdvenster van het programma en selecteert u de optie Blokkering van verwijderbare media
inschakelen. Als u toegang tot bepaalde typen media wilt toestaan, heft u de selectie van de gewenste mediavolumes op.
OPMERKING: Als u toegang wilt geven tot een extern cd-romstation dat via een USB-kabel op uw computer is aangesloten, schakelt
u de opti e Cd-rom uit.

20
7. Antiphishing
De term phishing definieert een criminele activiteit waarbij gebruik wordt gemaakt van social engineering (het manipuleren van
gebruikers om vertrouwelijke informatie te verkrijgen). Phishing wordt vaak gebruikt om toegang te krijgen tot gevoelige gegevens
zoals bankrekeningnummers, creditcardnummers, pincodes of gebruikersnamen en wachtwoorden.
Wij raden u aan om Antiphishing ingeschakeld te laten (Instellingen > Voorkeuren voor toepassing opgeven... > Antiphishing-
beveiliging). Alle potentiële phishingaanvallen die afkomstig zijn van websites of domeinen die in de ESET-malwaredatabase zijn
opgenomen, worden geblokkeerd en er wordt een waarschuwing weergegeven die u op de hoogte stelt van de aanval.

21
8. Web- en e-mailbeveiliging
Klik op Instellingen > Web en e-mail om toegang te krijgen tot Web- en e-mailbeveiliging in het hoofdvenster. Van hieruit hebt u ook
toegang tot de gedetailleerde instellingen voor elke module door te klikken op Instellen....
· Beveiliging van webtoegang: bewaakt HTTP-communicatie tussen webbrowsers en externe servers.
· Beveiliging van e-mailclient - biedt controle van e-mailcommunicatie die wordt ontvangen via het POP3- en IMAP-protocol.
· Antiphishing-beveiliging - blokkeert potentiële phishingaanvallen van websites of domeinen die in de ESET-database met
malware staan.
8.1 Webbeveiliging
Beveiliging van webtoegang controleert communicatie tussen webbrowsers en externe servers op naleving van HTTP-regels
(Hypertext Transfer Protocol).
Webfiltering kan worden gerealiseerd door de poortnummers voor HTTP-communicatie en/of URL-adressen te definiëren.
8.1.1 Poorten
Op het tabbl ad Poorten kunt u de poortnummers definiëren die worden gebruikt voor HTTP-communicatie. Standaard zijn de
poortnummers 80, 8080 en 3128 vooraf gedefinieerd.
8.1.2 URL-lijsten
In het gedeelte URL-lijsten kunt u HTTP-adressen opgeven die u wilt blokkeren, toestaan of uitsluiten van controle. Websites in de
lijst met geblokkeerde adressen zijn niet toegankelijk. Websites in de lijst met uitgesloten adressen zijn toegankelijk zonder te
worden gescand op schadelijke code.
Als u alleen toegang wilt toestaan tot de URL-adressen die worden vermeld in de lijst Toegestane URL, selecteert u de optie Niet-
toegankelijke URL-adressen.
Als u een lijst wilt activeren, selecteert u Ingeschakeld naast de lijstnaam. Als u een melding wilt krijgen wanneer u een adres
invoert van de huidige lijst, selecteert u de optie Op de hoogte gesteld.
In alle lijsten kunnen de speciale tekens * (s ter retj e) en ? (vraagteken) worden gebruikt. Het sterretje vervangt een willekeurige
tekenreeks en het vraagteken een willekeurig teken. Wees voorzichtig met het opgeven van uitgesloten adressen. De lijst mag alleen
vertrouwde en veilige adressen bevatten. Evenzo is het noodzakelijk ervoor te zorgen dat de tekens * en ? op de juiste wijze worden
gebruikt in de li js t.
8.2 E-mailbeveiliging
E-mailbeveiliging biedt controle van e-mailcommunicatie die wordt ontvangen via het POP3- en IMAP-protocol. Bij het
onderzoeken van binnenkomende berichten maakt het programma gebruik van al de geavanceerde scanmethoden van de
ThreatSense-scanengine. Het scannen van de communicatie via het POP3- en IMAP-protocol gebeurt onafhankelijk van de
gebruikte e-mailclient.
ThreatSense-engine: Instellingen: via de geavanceerde instellingen van de virusscanner kunt u scandoelen, detectiemethoden enz.
confi gureren. Kl ik op Instellingen om het venster met gedetailleerde scaninstellingen weer te geven.
Bericht toevoegen aan e-mailvoetnoot: nadat een e-mail is gescand, kan een melding met de scanresultaten aan het bericht
worden toegevoegd. U kunt niet zonder meer op de berichten vertrouwen, aangezien ze kunnen worden weggelaten in
problematische HTML-berichten en door sommige virussen kunnen worden vervalst. De volgende opties zijn beschikbaar:
· Nooit: er worden geen tagberichten toegevoegd
· Alleen geïnfecteerde e-mail: alleen berichten met schadelijke code worden gemarkeerd als gecontroleerd
· Naar alle gescande e-mail: er worden meldingen toegevoegd aan alle gescande e-mail
Opmerking toevoegen aan het onderwerp van ontvangen en gelezen geïnfecteerde e-mail: schakel dit selectievakje in als u een
viruswaarschuwing aan het onderwerp van geïnfecteerde e-mail wilt toevoegen. Met deze functie kunt u eenvoudig filteren op
geїnfecteerde e-mail. Het schept ook meer vertrouwen bij de ontvanger, en als een infiltratie wordt gedetecteerd beschikt u hiermee
over waardevolle informatie over het risiconiveau van een bepaalde e-mail of afzender.
Sjabloon toegevoegd aan het onderwerp van geïnfecteerde e-mail: u kunt deze sjabloon bewerken als u de indeling van het
onderwerpvoorvoegsel van een geїnfecteerde e-mail wilt wijzigen.
21 21

22
In het onderste gedeelte van dit venster kunt u ook de controle van e-mailcommunicatie in/uitschakelen die wordt ontvangen via
het POP3- en IMAP-protocol. Zie de volgende onderwerpen voor meer informatie hierover:
· POP3-protocolcontrole
· IMAP-protocolcontrole
8.2.1 POP3-protocolcontrole
Het POP3-protocol is het meest gebruikte protocol voor het ontvangen van e-mailcommunicatie in een e-mailclienttoepassing. ESET
Cyber Security biedt beveiliging voor dit protocol, ongeacht welke e-mailclient wordt gebruikt.
De beveiligingsmodule die deze controle biedt wordt automatisch gestart wanneer het systeem wordt opgestart en is vervolgens
actief in het geheugen. Zorg ervoor dat de module is ingeschakeld anders werkt protocolfiltering niet goed; POP3-protocolcontrole
wordt automatisch uitgevoerd zonder dat u uw e-mailclient daarvoor opnieuw hoeft te configureren. Standaard wordt alle
communicatie via poort 110 gescand, maar u kunt indien nodig andere communicatiepoorten toevoegen. Poortnummers moeten
worden gescheiden door een komma.
Al s de opti e POP3-protocolcontrole inschakelen is geselecteerd, wordt alle POP3-verkeer gecontroleerd op schadelijke software.
8.2.2 IMAP-protocolcontrole
Het Internet Message Access Protocol (IMAP) is een ander e-mailprotocol voor het ophalen van e-mail. IMAP heeft bepaalde
voordelen boven POP3. Meerdere clients kunnen bijvoorbeeld gelijktijdig verbinding maken met hetzelfde postvak en de
statusinformatie van berichten bijhouden, zoals of een bericht al dat niet is gelezen, beantwoord of verwijderd. ESET Cyber Security
biedt beveiliging voor dit protocol, ongeacht welke e-mailclient u gebruikt.
De beveiligingsmodule die deze controle biedt wordt automatisch gestart wanneer het systeem wordt opgestart en is vervolgens
actief in het geheugen. Zorg ervoor dat IMAP-protocolcontrole is ingeschakeld anders werkt de module niet goed; IMAP-
protocolcontrole wordt automatisch uitgevoerd zonder dat u uw e-mailclient daarvoor opnieuw hoeft te configureren. Standaard
wordt alle communicatie via poort 143 gescand, maar u kunt indien nodig andere communicatiepoorten toevoegen. Poortnummers
moeten worden gescheiden door een komma.
Als IMAP-protocolcontrole inschakelen is geselecteerd, wordt al het verkeer via IMAP gecontroleerd op schadelijke software.
22
22

23
9. Bijwerken
ESET Cyber Security moet regelmatig worden bijgewerkt om het maximale beveiligingsniveau te kunnen blijven bieden. De
updatemodule waarborgt dat het programma altijd is bijgewerkt door steeds de meest recente detectiemodules te downloaden.
Kl ik in het hoofdmenu op Bijwerken voor het weergeven van de actuele updatestatus van ESET Cyber Security, inclusief de datum en
tijd van de laatste update en of er een update nodig is. U begint het updateproces handmatig door te klikken op Modules
bijwerken.
Onder normale omstandigheden, dus wanneer updates zonder problemen worden gedownload, wordt het bericht Bijwerken is niet
nodig. De geïnstalleerde modules zijn up-to-date in het venster Bijwerken weergegeven. Als de modules niet kunnen worden
bi jgewerkt, wordt aangeraden de update-instellingen te controleren. De meest voorkomende reden voor deze fout is onjuist
ingevoerde verificatiegegevens (gebruikersnaam en wachtwoord) of onjuist geconfigureerde verbindingsinstellingen .
Het updatevenster bevat ook het versienummer van de detectie-engine. Het versienummer is gekoppeld aan de webpagina van ESET
waar de updategegevens over de detectie-engine staan.
9.1 Instellingen voor bijwerken
Als u alle tijdelijk opgeslagen updategegevens wilt verwijderen, klikt u op Opschonen naast Updatecache wissen. Gebruik deze
optie als er problemen optreden tijdens de update.
9.1.1 Geavanceerde opties
Als u meldingen na elke geslaagde update wilt uitschakelen, selecteert u Geen meldingen over voltooide updates weergeven.
Schakel Bèta-updates in om ontwikkelmodules te downloaden die de testfase bijna hebben voltooid. In veel bèta-updates zijn
opl ossi ngen voor productproblemen opgenomen. Met Vertraagde updates downloadt u updates enkele uren nadat ze zijn
vrijgegeven. Zo zorgt u ervoor dat clients geen updates ontvangen tot is bevestigd dat deze vrij zijn van praktische problemen.
In ESET Cyber Security worden momentopnames van de detectie-engine en programmamodules vastgelegd voor gebruik met de
functie Ongedaan maken van updates. La a t Momentopnamen maken van updatebestanden ingeschakeld, zodat ESET Cyber
Security deze momentopnamen automatisch maakt. Als u vermoedt dat een nieuwe update van de detectiemodule en/of
programmamodule instabiel of beschadigd is, kunt u terugkeren naar de vorige versie en alle updates voor een bepaalde periode
uitschakelen. Of u kunt eerder uitgeschakelde updates inschakelen als u deze voor onbepaalde tijd hebt uitgesteld. Wanneer u de
functie Ongedaan maken van updates gebruikt om terug te keren naar een eerdere update, gebruikt u het vervolgkeuzemenu
Periode van opschorting instellen op om de tijdperiode op te geven gedurende welke u updates wilt opschorten. Als u tot
ingetrokken selecteert, worden normale updates pas weer hervat als u deze handmatig herstelt. Wees voorzichtig met het instellen
van de tijdperiode om updates op te schorten.
Maximumleeftijd voor database automatisch instellen: hier kunt u de maximale tijd (in dagen) instellen waarna de
detectiemodules als verouderd worden aangemerkt. De standaardwaarde is 7 dagen.
9.2 Updatetaken maken
Updates kunnen handmatig worden geactiveerd door in het hoofdmenu te klikken op Bijwerken en vervolgens te klikken op
Modules bijwerken.
Updates kunnen ook worden uitgevoerd als geplande taken. Als u een geplande taak wilt configureren, klikt u op Hulpmiddelen >
Planner. Standaard zijn in ESET Cyber Security de volgende taken geactiveerd:
· Regelmatig automatisch bijwerken
· Automatisch bijwerken na aanmelding van gebruiker
Elk van de updatetaken kan worden gewijzigd om te voldoen aan uw behoeften. Behalve de standaardupdatetaken kunt u ook
nieuwe updatetaken maken met een door de gebruiker gedefinieerde configuratie. Zie het gedeelte Planner voor meer informatie
over het maken en configureren van updatetaken.
23
32
26

24
9.3 ESET Cyber Security bijwerken naar een nieuwe versie
Voor maximale beveiliging is het belangrijk dat u de nieuwste build van ESET Cyber Security gebruikt. U controleert of er een
nieuwe versie beschikbaar is door in het hoofdmenu op Thuis te klikken. Als er een nieuwe build beschikbaar is, wordt een bericht
weergegeven. Kl ik op Meer informatie... om een nieuw venster te openen met het versienummer van de nieuwe build en het
wijzigingslogboek.
Klik op Ja om de nieuwste build te downloaden of klik op Niet nu om het venster te sluiten en de upgrade later te downloaden.
Al s u op Ja hebt geklikt, wordt het bestand gedownload naar uw downloadmap (of naar de standaardmap die door de browser is
ingesteld). Nadat het downloaden van het bestand is voltooid, kunt u het bestand starten en de installatie-instructies uitvoeren.
Uw gebruikersnaam en wachtwoord worden automatisch overgezet naar de nieuwe installatie. We raden aan dat u regelmatig
controleert of er upgrades beschikbaar zijn, vooral als u ESET Cyber Security via een cd/dvd installeert.
9.4 Systeemupdates
De macOS-systeemupdatefunctie is een belangrijk onderdeel dat is gemaakt om gebruikers te kunnen beschermen tegen
schadelijke software. Voor een maximale beveiliging raden wij aan om deze updates zo snel mogelijk te installeren nadat deze
beschikbaar zijn gekomen. ESET Cyber Security brengt u op de hoogte van eventueel ontbrekende updates volgens het niveau dat u
zelf opgeeft. U kunt de mate van updatemeldingen die u ontvangt aanpassen in Instellingen > Voorkeuren voor toepassing
opgeven... (of druk op cmd+,) > Waarschuwingen en meldingen > Instellen... en wijzig de opties van Weergavevoorwaarden naast
Updates van het besturingssysteem.
· Alle updates weergeven - er wordt een melding weergegeven als er een systeemupdate ontbreekt
· Alleen aanbevolen weergeven - u ontvangt alleen meldingen over aanbevolen updates
Als u geen meldingen over ontbrekende updates wilt ontvangen, schakel het selectievakje naast Updates van het
besturingssysteem dan uit.
Het meldingenvenster geeft een overzicht van de updates die beschikbaar zijn voor het macOS-besturingssysteem en de
toepassingen die met het hulpprogramma van macOS zelf (Software-updates) zijn en kunnen worden bijgewerkt. U kunt de update
rechtstreeks vanuit het meldingenvenster installeren of vanuit de sectie Thuis van ESET Cyber Security door te klikken op De
ontbrekende update installeren.
In het meldingenvenster staan de toepassingsnaam, versie, grootte, eigenschappen (vlaggen) en aanvullende informatie over
beschikbare updates. In de kolom Vlaggen staat de volgende informatie:
· [aanbevolen] - de fabrikant van het besturingssysteem raadt aan dat u deze update installeert om de beveiliging en stabiliteit
van het systeem te vergroten
· [opnieuw opstarten] - het opnieuw opstarten van de computer is vereist na de installatie
· [afsluiten] - de computer moet worden afgesloten en daarna opnieuw opgestart na de installatie
In het meldingsvenster staat welke updates door het opdrachtregelhulpprogramma genaamd 'softwareupdate' worden opgehaald.
Updates die door dit hulpprogramma worden opgehaald, kunnen anders zijn dan de updates die worden weergegeven door de
toepassing 'Software-updates'. Als u alle beschikbare updates wilt installeren die in het venster 'Ontbrekende systeemupdates'
worden weergegeven en ook de updates die niet door de toepassing 'Software-updates' worden weergegeven, moet u het
opdrachtregelhulpprogramma 'softwareupdate' gebruiken. Lees voor meer informatie over dit hulpprogramma de handleiding voor
s oftwa re-upda tes door man softwareupdate te typen in een Terminal-venster. Dit wordt alleen aangeraden voor ervaren
gebruikers.

25
10. Hulpmiddelen
Het menu Hulpmiddelen omvat modules die het programmabeheer helpen vereenvoudigen en aanvullende opties voor
geavanceerde gebruikers.
10.1 Logbestanden
De logbestanden bevatten informatie over belangrijke programmagebeurtenissen die zich hebben voorgedaan en bieden een
overzicht van gedetecteerde bedreigingen. Logboekregistratie vormt een essentieel hulpmiddel bij systeemanalyse,
bedreigingsdetectie en probleemoplossing. Logboekregistratie wordt zonder gebruikersinteractie op de achtergrond uitgevoerd.
Informatie wordt vastgelegd op basis van huidige detailinstellingen voor logboekregistratie. U kunt tekstberichten en logboeken
rechtstreeks vanuit de ESET Cyber Security-omgeving weergeven. U kunt de logboeken ook archiveren.
Logbestanden zijn toegankelijk vanuit het hoofdmenu van ESET Cyber Security door op Hulpmiddelen > Logboeken te klikken.
Selecteer het gewenste logboektype in de vervolgkeuzelijst Logboek boven in het venster. De volgende logboeken zijn beschikbaar:
1. Gedetecteerde bedreigingen - met deze optie geeft u alle informatie weer over gebeurtenissen die verband houden met de
detectie van infiltraties.
2. Gebeurtenissen - met deze optie kunnen systeembeheerders en gebruikers problemen oplossen. Alle belangrijke acties die
worden uitgevoerd door ESET Cyber Security, worden opgenomen in de gebeurtenislogboeken.
3. Computerscan - in dit logboek worden de resultaten van alle voltooide scans weergegeven. Dubbelklik op een vermelding om de
details voor de desbetreffende on-demand computerscan weer te geven.
4. Gefilterde websites: deze lijst is nuttig als u een lijst met websites wilt bekijken die door Beveiliging van webtoegang zijn
geblokkeerd. In deze logboeken ziet u de tijd, URL, status, het IP-adres, de gebruiker en toepassing die een verbinding met deze
website heeft geopend.
U kunt de informatie in elke sectie rechtstreeks naar het klembord kopiëren door de gewenste vermelding te selecteren en op de
knop Kopiëren te klikken.
10.1.1 Logbestanden onderhouden
De configuratie van logbestanden voor ESET Cyber Security is toegankelijk vanuit het hoofdvenster van het programma. Klik op
Instellen > Voorkeuren voor toepassing opgeven (of druk op cmd+,) > Logboekbestanden. U kunt de volgende opties opgeven voor
logbestanden:
· Oude logboekrecords automatisch verwijderen: logboekvermeldingen die ouder zijn dan het opgegeven aantal dagen, worden
automatisch verwijderd (standaard 90 dagen).
· Logbestanden automatisch optimaliseren: logbestanden worden automatisch gedefragmenteerd als het opgegeven percentage
ongebruikte records is overschreden (standaard 25%).
Alle relevante informatie die wordt weergegeven in de grafische gebruikersinterface en berichten over bedreigingen en
gebeurtenissen kunnen worden opgeslagen in een voor mensen leesbare tekstindeling, zoals tekst zonder opmaak of CSV-
bestanden (Comma-separated values). Als u deze bestanden beschikbaar wilt maken voor verwerking met programma's van
derden, schakelt u het sel ectievakje naast Registratie naar tekstbestanden inschakelen in.
Klik op Instellingen naast Geavanceerde opties om de doelmap te definiëren waarin de logbestanden moeten worden opgeslagen.
Afhankelijk van de opties die u hebt geselecteerd onder Tekstlogbestanden: Bewerken, kunt u logbestanden opslaan waarin de
volgende informatie wordt geschreven:
· Gebeurteni s s en zoa l s Gebruikersnaam en wachtwoord ongeldig, Modules kunnen niet worden bijgewerkt enz., worden naar het
bestand eventslog.txt geschreven.
· Bedreigingen die zijn gedetecteerd door de Opstartscanner, Real-timebeveiliging of Computerscan worden opgeslagen in het
bestand met de naam threatslog.txt.
· De resultaten van alle voltooide scans worden opgeslagen in de indeling scanlog.NUMMER.txt
Al s u filters wilt configureren voor Standaardlogboekrecords voor computerscans, klikt u op Bewerken en selecteert u de
benodigde typen logbestanden of heft u de selectie ervan op. Meer informatie over deze logtypen vindt u Logbestanden filteren .
26

26
10.1.2 Logbestanden filteren
In logbestanden (ook wel logboeken genoemd) wordt informatie over belangrijke systeemgebeurtenissen opgeslagen. U kunt
logbestanden filteren om alleen records voor een bepaald type gebeurtenis weer te geven.
Hieronder worden de meest gebruikte typen logbestanden beschreven:
· Kritieke waarschuwingen - kritieke systeemfouten (bijvoorbeeld het niet starten van de antivirusbeveiliging)
· Fouten - foutmeldingen zoals 'Fout bij downloaden van bestand' en kritieke fouten.
· Waarschuwingen - waarschuwingsberichten
· Informatieve records- informatieve berichten, met betrekking tot onder andere geslaagde updates, waarschuwingen enz.
· Diagnostische records - informatie die nodig is voor het instellen van het programma, plus alle hierboven beschreven records.
10.2 Planner
De Planner is te vinden in het hoofdmenu van ESET Cyber Security onder Hulpmiddelen. De Planner bevat een lijst met alle geplande
taken en hun configuratie-eigenschappen, zoals de vooraf gedefinieerde datum en tijd en het gebruikte scanprofiel.
De Planner beheert en start geplande taken met vooraf gedefinieerde configuraties en eigenschappen. De configuratie en
eigenschappen bevatten informatie zoals de datum en tijd alsmede opgegeven profielen die moeten worden gebruikt tijdens de
uitvoering van de taak.
Standaard worden de volgende geplande taken in de Planner weergegeven:
· Logbestanden onderhouden (nadat de opti e Systeemtaken weergeven is ingeschakeld in de instellingen voor de Planner)
· Opstartbestand controleren na aanmelding gebruiker
· pstartbestand controleren na succesvolle update van de detectiemodules
· Regelmatig automatisch bijwerken
· Automatisch bijwerken na aanmelding van gebruiker
U kunt de configuratie van een bestaande geplande taak (zowel standaard als door de gebruiker gedefinieerd) bewerken door Ctrl
ingedrukt te houden, op de taak te klikken die u wilt wijzigen en op Bewerken te klikken, of door de taak te selecteren en op Taak
bewerken te klikken.

27
10.2.1 Nieuwe taken maken
U kunt een nieuwe taak maken in de Planner door op Taak toevoegen... te klikken of door op CTRL te drukken en te klikken in het
l ege veld en Toevoegen... te selecteren in het contextmenu. Er zijn vijf typen geplande taken beschikbaar:
· Toepassing uitvoeren
· Bijwerken
· Logbestanden onderhouden
· On-demand computerscan
· Systeemopstartbestand controleren
OPMERKING: Door Toepassing uitvoeren te selecteren, kunt u programma's uitvoeren als systeemgebruiker genaamd "nobody".
Machtigingen voor het uitvoeren van toepassingen via de Planner worden door macOS gedefinieerd.
In het onderstaande voorbeeld gebruiken we de Planner om een nieuwe updatetaak toe te voegen, aangezien bijwerken een van de
meest geplande taken is:
1. Ga naar de vervolgkeuzel ijs t Geplande taak en s el ecteer Bijwerken.
2. Voer de naam van de taak in het veld Taaknaam in.
3. Selecteer de frequentie van de taak in de vervolgkeuzelijst Taak uitvoeren. Op basis van de geselecteerde frequentie wordt u
gevraagd om waarden voor verschillende updateparameters in te voeren. Als u Door gebruiker gedefinieerd selecteert, wordt u
gevraagd een datum/tijd op te geven in cron-notatie (zie het gedeelte Door gebruiker gedefinieerde taak maken voor meer
details).
4. In de volgende stap definieert u welke actie moet worden ondernomen als de taak niet kan worden uitgevoerd of voltooid op
het geplande tijdstip.
5. In de laatste stap wordt een overzichtsvenster weergegeven met informatie over de huidige geplande taak. Klik op Voltooien. De
nieuwe geplande taak wordt toegevoegd aan de lijst met actuele geplande taken.
ESET Cyber Security bevat voorgedefinieerde geplande taken waarmee de juiste werking wordt gewaarborgd. Deze mogen niet
worden gewijzigd en zijn standaard verborgen. Als u deze taken zichtbaar wilt maken, klik dan in het hoofdmenu op Instellingen >
Voorkeuren voor toepassing opgeven... (of druk op cmd+,) > Planner en s el ecteer Systeemtaken weergeven.
10.2.2 Door gebruiker gedefinieerde taken maken
De datum en tijd van een door de gebruiker gedefinieerde taak moeten worden opgegeven in cron-notatie met jaaruitbreiding (een
tekenreeks bestaande uit zes velden, elk van elkaar gescheiden door een spatie):
minuut(0-59) uur(0-23) dag van maand(1-31) maand(1-12) jaar(1970-2099) dag van week(0-7)(zondag = 0 of
7)
Voorbeeld:
30 6 22 3 2012 4
Speciale tekens die worden ondersteund in cron-expressies:
· sterretje (*) - expressie geldt voor alle waarden van het veld. Een sterretje in het derde veld (dag van maand) betekent
bijvoorbeeld elke dag
· verbindingsstreepje-) - definieert bereiken, bijvoorbeel d 3-9
· komma (,) - scheidt items in een lijst, bijvoorbeeld 1,3,7,8
· schuine streep (/) - definieert verhogingen van bereiken, bijvoorbeeld 3-28/5 in het derde veld (dag van maand) betekent de
derde dag van elke maand en vervolgens elke vijf dagen.
Namen van dagen (Monday-Sunday) en namen van maanden (January-December) worden niet ondersteund.
OPMERKING: als u zowel de dag van de maand als de dag van de week definieert, wordt de opdracht alleen uitgevoerd als beide
velden overeenkomen.
27

28
10.3 Quarantaine
Het hoofddoel van quarantaine is het veilig opslaan van geïnfecteerde bestanden. Bestanden moeten in quarantaine worden
geplaatst als ze niet kunnen worden opgeschoond, als het niet veilig of raadzaam is om ze te verwijderen of als ze onterecht door
ESET Cyber Security zijn gedetecteerd.
U kunt elk bestand in quarantaine plaatsen. Dit is raadzaam als een bestand zich verdacht gedraagt maar niet wordt gedetecteerd
door de antivirusscanner. In quarantaine geplaatste bestanden kunnen voor analyse naar het bedreigingslaboratorium van ESET
worden verzonden.
Bestanden die zijn opgeslagen in de quarantainemap kunnen worden bekeken in een tabel waarin de datum en het tijdstip van de
quarantaine, het pad naar de oorspronkelijke locatie van het geïnfecteerde bestand, de grootte van het bestand in bytes, de reden
(bijvoorbeeld toegevoegd door gebruiker…) en het aantal bedreigingen (bijvoorbeeld of het een archief is dat meerdere infiltraties
bevat) worden weergegeven. De quarantainemap met de bestanden in quarantaine (/Library/Application
Support/Eset/cache/esets/quarantine) blijft aanwezig in het systeem, zelfs als u ESET Cyber Security verwijdert. Bestanden in
quarantaine worden veilig gecodeerd opgeslagen en kunnen weer worden teruggezet na installatie van ESET Cyber Security.
10.3.1 Bestanden in quarantaine plaatsen
ESET Cyber Security plaatst verwijderde bestanden automatisch in quarantaine (als u deze optie niet hebt gedeselecteerd in het
waarschuwingsvenster). U kunt elk verdacht bestand in quarantaine plaatsen door op Quarantaine... te klikken . Het contextmenu
kan eveneens worden gebruikt voor dit doel. Druk op Ctrl en klik in het lege veld, selecteer Quarantaine, selecteer het bestand dat u
in quarantaine wilt plaatsen en klik op Openen.
10.3.2 Herstellen vanuit quarantaine
In quarantaine geplaatste bestanden kunnen ook worden hersteld naar hun oorspronkelijke locatie. Dit doet u door een in
quarantaine geplaatst bestand te selecteren en op Herstellen te klikken. Herstellen is ook beschikbaar in het contextmenu. Klik met
CTRL ingedrukt op een bestand in het venster Quarantaine en klik vervolgens op Herstellen. Het contextmenu biedt tevens de optie
Herstellen naar..., waarmee u bestanden kunt herstellen naar een andere locatie dan waarvan ze zijn verwijderd.
10.3.3 Bestand verzenden vanuit quarantaine
Als u een verdacht bestand in quarantaine hebt geplaatst dat niet is gedetecteerd door het programma, of als een bestand ten
onrechte als geïnfecteerd is beoordeeld (bijvoorbeeld door heuristische analyse van de code) en vervolgens in quarantaine
geplaatst, stuurt u het bestand naar het bedreigingslaboratorium van ESET. U kunt een bestand vanuit quarantaine verzenden door
er met Ctrl ingedrukt op te klikken en Bestand verzenden voor analyse te selecteren in het contextmenu.
10.4 Actieve processen
In de l ij st Actieve processen worden de processen weergegeven die op uw computer worden uitgevoerd. ESET Cyber Security biedt
gedetailleerde informatie over actieve processen om gebruikers te beschermen met ESET Live Grid-technologie.
· Proces - de naam van het proces dat momenteel op uw computer wordt uitgevoerd. Als u alle actieve processen wilt zien, kunt u
ook Activity Monitor gebruiken (te vinden in /Programma's/Hulpprogramma's).
· Risiconiveau - in de meeste gevallen wijzen ESET Cyber Security en ESET Live Grid-technologie risiconiveaus toe aan objecten
(bestanden, processen enz.) met een reeks heuristische regels die de kenmerken van elk object onderzoeken en vervolgens
afwegen wat hun potentieel is voor schadelijke activiteiten. Op basis van deze heuristiek wordt aan objecten een risiconiveau
toegewezen. Bekende toepassingen die groen zijn gemarkeerd zijn zeker schoon (staan op de witte lijst) en worden uitgesloten
van scannen. Hierdoor wordt de snelheid van zowel de On-demand scan als de Real-time scan verhoogd. Als een toepassing is
gemarkeerd als onbekend (geel), hoeft deze geen schadelijke software te zijn. Gewoonlijk is het slechts een nieuwere toepassing.
Als u twijfelt hebt over een bestand, kunt u het bestand voor analyse naar het bedreigingslaboratorium van ESET te verzenden.
Als het bestand een schadelijke toepassing blijkt te zijn, worden de kenmerken ervan toegevoegd aan een van de volgende
updates.
· Aantal gebruikers - het aantal gebruikers dat een bepaalde toepassing gebruikt. Deze informatie wordt verzameld door de ESET
Live Grid-technologie.
· Tijdstip van detectie - de periode sinds de toepassing werd gedetecteerd door de ESET Live Grid-technologie.
· Toepassingsbundel-id - de naam van de leverancier of het toepassingsproces.
Als u op een bepaald proces klikt, wordt de volgende informatie onder in het venster weergegeven:
· Bestand: de locatie van een toepassing op de computer
· Bestandsgrootte: de fysieke grootte van het bestand op de schijf
· Beschrijving van bestand: bestandskenmerken gebaseerd op de beschrijving van het besturingssysteem
· Toepassingsbundel-id: de naam van de leverancier of het toepassingsproces
· Versie van bestand: informatie over de uitgever van het bestand
· Productnaam: de naam van de toepassing en/of de bedrijfsnaam

29
10.5 Live Grid
Het Live Grid vroegtijdige waarschuwingssysteem houdt ESET onmiddellijk en continu op de hoogte van nieuwe infiltraties. Het
bidirectionele Live Grid vroegtijdig waarschuwingssysteem heeft één enkel doel, namelijk de beveiliging verbeteren die wij u
kunnen bieden. Dit kunnen we het beste doen door ervoor te zorgen dat we nieuwe bedreigingen zo spoedig mogelijk in de gaten
krijgen door deze aan zoveel mogelijk van onze klanten te 'koppelen' en hen te gebruiken als onze bedreigingsscouts. Er zijn twee
opties:
1. U kunt ervoor kiezen om het Live Grid vroegtijdig waarschuwingssysteem niet in te schakelen. De software blijft op dezelfde
wijze functioneren en u ontvangt nog steeds de beste beveiliging beveiliging die wij u kunnen bieden.
2. U kunt het Live Grid vroegtijdig waarschuwingssysteem zodanig configureren dat anonieme informatie wordt verzonden over
nieuwe bedreigingen en waar de nieuwe bedreigingscode voorkomt. Deze informatie kan voor gedetailleerde analyse naar ESET
worden verzonden. Door deze bedreigingen te bestuderen kan ESET de database met bedreigingen bijwerken en de
detectiemogelijkheden van het programma verbeteren.
Het Live Grid vroegtijdig waarschuwingssysteem verzamelt informatie over uw computer met betrekking tot nieuw gedetecteerde
bedreigingen. Deze informatie kan een voorbeeld of kopie bevatten van het bestand waarin de bedreiging voorkwam, het pad naar
dat bestand, de bestandsnaam, de datum en tijd, het proces waarbij de bedreiging plaatsvond op uw computer en informatie over
het besturingssysteem van uw computer.
Hoewel de kans bestaat dat het bedreigingslaboratorium van ESET hiermee nu en dan informatie over u of uw computer in bezit
krijgt (gebruikersnamen in een directorypad enz.), wordt deze informatie niet gebruikt voor andere doelen dan ons te helpen
onmiddellijk te reageren op nieuwe bedreigingen.
Als u Live Grid in het hoofdvenster wilt instellen, klik dan op Instellingen > Voorkeuren voor toepassing opgeven... (of druk op
cmd+,) > Live Grid. Selecteer Vroegtijdig waarschuwingssysteem van Live Grid inschakelen om Live Grid te activeren en klik op
Instellen... naast Geavanceerde opties.
10.5.1 Live Grid installeren
ESET Cyber Security is standaard geconfigureerd om verdachte bestanden voor gedetailleerde analyse naar het
bedreigingslaboratorium van ESET te verzenden. Als u deze bestanden niet automatisch wilt laten verzenden, schakelt u Bestanden
indienen uit.
Als u een verdacht bestand aantreft, kunt u dit naar ons bedreigingslaboratorium versturen voor analyse. Klik hiervoor in het
hoofdvenster van het programma op Hulpmiddelen > Voorbeeld verzenden voor analyse. Als het een schadelijke toepassing is,
wordt de detectie ervan toegevoegd aan een komende update.
Anonieme statistieken verzenden: het vroegtijdig waarschuwingssysteem van ESET Live Grid verzamelt anonieme informatie over
uw computer met betrekking tot nieuw gedetecteerde bedreigingen. Deze informatie omvat de naam van de infiltratie, de datum en
het tijdstip waarop deze is gedetecteerd, de versie van het ESET-beveiligingsproduct, de versie van uw besturingssysteem en de
locatie-instelling. Deze statistische gegevens worden doorgaans een- of tweemaal per dag naar de servers van ESET verzonden.
Hieronder ziet u een voorbeeld van een verzonden statistisch pakket:
# utc_time=2005-04-14 07:21:28
# country=“Slovakia“
# language=“ENGLISH“
# osver=9.5.0
# engine=5417
# components=2.50.2
# moduleid=0x4e4f4d41
# filesize=28368
# filename=Users/UserOne/Documents/Incoming/rdgFR1463[1].zip
Uitsluitingsfilter: met het uitsluitingsfilter kunt u bepaalde bestandstypen uitsluiten van verzending. Het kan bijvoorbeeld handig
zijn bestanden uit te sluiten die mogelijk vertrouwelijke informatie bevatten, zoals documenten of spreadsheets. Veelgebruikte
bestandstypen (DOC, RTF enz.) worden standaard uitgesloten. U kunt bestandstypen toevoegen aan de lijst met uitgesloten
bestanden.
E-mailadres van contactpersoon (optioneel): uw e-mailadres kan worden gebruikt als meer informatie nodig is voor analyse. U zult
geen antwoord van ESET ontvangen, tenzij nadere informatie nodig is voor de analyse.

30
11. Gebruikersinterface
Via de configuratie-opties voor de gebruikersinterface kunt u de werkomgeving aan uw eigen behoeften aanpassen. Deze opties zijn
toegankelijk vanuit het hoofdmenu door te klikken op Instellingen > Voorkeuren voor toepassing opgeven... (of druk op cmd+,) >
Interface.
· Als u het welkomscherm van ESET Cyber Security wilt weergeven bij het opstarten van het systeem, selecteer dan Welkomscherm
weergeven bij opstarten.
· Met Toepassing in Dock weergeven kunt u het ESET Cyber Security-pictogram weergeven in het OS X Dock en heen en weer
schakelen tussen ESET Cyber Security en andere toepassingen die worden uitgevoerd door op cmd+tab te drukken. Wijzigingen
worden van kracht nadat u ESET Cyber Security opnieuw hebt gestart (doorgaans geactiveerd door het opnieuw opstarten van de
computer).
· Vi a de optie Standaardmenu gebruiken kunt u bepaal de snel toetsen gebruiken (zie Sneltoetsen ) en de standaardmenuopties
zien (Gebruikersinterface, Instellingen en Hulpmiddelen) op de menubalk van macOS (boven in het scherm).
· U kunt knopinfo inschakelen voor bepaalde opties van ESET Cyber Security door Knopinfo weergeven te selecteren.
· Met Verborgen bestanden weergeven kunt u verborgen bestanden weergeven en selecteren in de instellingen voor Scandoelen
va n een Computerscan.
· Standaard wordt het ESET Cyber Security-pictogram weergegeven op de menubalk Extra die rechts van de macOS-menubalk
(boven in het scherm) wordt weergegeven. Als u dit wilt uitschakelen, deselecteert u Pictogram weergeven in Extra op menubalk.
Deze wijziging wordt van kracht nadat u ESET Cyber Security opnieuw hebt gestart (doorgaans geactiveerd door het opnieuw
opstarten van de computer).
11.1 Waarschuwingen en meldingen
In het gedeelte Waarschuwingen en meldingen kunt u configureren hoe waarschuwingen en systeemmeldingen bij bedreigingen
worden verwerkt door ESET Cyber Security.
Wa nneer u Waarschuwingen weergeven uitschakelt, worden alle waarschuwingsvensters geannuleerd. Dit wordt alleen in
bepaalde situaties aangeraden. Voor de meeste gebruikers adviseren wij de standaardoptie (ingeschakeld) voor deze optie te laten
staan. Geavanceerde opties worden bes chreven in dit hoofdstuk .
Wa nneer u Meldingen weergeven op bureaublad selecteert, worden er waarschuwingsvensters op het bureaublad weergegeven
waarvoor geen gebruikersinteractie nodig is (standaard rechtsboven in het scherm). U kunt opgeven hoe lang een melding wordt
weergegeven door de waarde van Meldingen automatisch sluiten na X seconden te wijzigen (standaard 5 seconden).
Sinds ESET Cyber Security versie 6.2 kunt u ook verhinderen dat bepaalde Beveiligingsstatussen in het hoofdvenster van het
programma worden weergegeven (het venster Beveiligingsstatus). Zi e Beveiligingsstatussen voor meer informatie hierover.
11.1.1 Waarschuwingen weergeven
In ESET Cyber Security worden waarschuwingsdialoogvensters weergegeven om u te informeren over nieuwe programmaversies,
nieuwe updates voor het besturingssysteem, het uitschakelen van bepaalde programmaonderdelen, het verwijderen van logboeken
enz. U kunt elke melding afzonderlijk onderdrukken door Dit dialoogvenster niet meer weergeven te selecteren.
Via Lijst met dialoogvensters (Instellingen > Voorkeuren voor toepassing opgeven... > Waarschuwingen en meldingen > Instellen...)
kunt u de lijst weergeven met alle dialoogvensters die worden geactiveerd door ESET Cyber Security. Als u elke melding wilt
inschakelen of onderdrukken, schakelt u het selectievakje in links van de Naam van dialoogvenster. Daarnaast kunt u
Weergavevoorwaarden definiëren op basis waarvan meldingen over nieuwe programmaversies en updates van het
besturingssysteem worden weergegeven.
11.1.2 Beveiligingsstatussen
De huidige beveiligingsstatus van ESET Cyber Security kan worden gewijzigd door statussen te activeren of deactiveren in
Instellingen > Voorkeuren voor toepassing opgeven... > Waarschuwingen en meldingen > Weergeven in het scherm
Beveiligingsstatus: Instellingen. De status van verschillende programmafuncties worden weergegeven of verborgen in het
hoofdvenster van ESET Cyber Security (het venster Beveiligingsstatus).
U kunt de beveiligingsstatus van de volgende programmafuncties verbergen:
· Antiphishing
· Beveiliging van webtoegang
· Beveiliging van e-mailclient
· Updates voor besturingssysteem
· Licentie verloopt
· Computer moet opnieuw worden opgestart
10
30
30

31
11.2 Machtigingen
De instellingen van ESET Cyber Security kunnen van groot belang zijn voor het beveiligingsbeleid van uw organisatie. Onbevoegde
wijzigingen kunnen de stabiliteit en beveiliging van uw systeem in gevaar brengen. Om deze reden kunt u bepalen welke gebruikers
de configuratie van het programma mogen wijzigen.
Als u gemachtigde gebruikers wilt opgeven, klikt u op Instellingen > Voorkeuren voor toepassing opgeven.. (of druk op cmd+,) >
Machtigingen. Selecteer de gebruikers of groepen in de lijst links en klik op Toevoegen. Als u alle
systeemgebruikers/systeemgroepen wi lt weergeven, selecteert u Alle gebruikers weergeven/Alle groepen weergeven. Als u een
gebruiker wilt verwijderen, selecteert u de naam van de gebruiker in de lijst Geselecteerde gebruikers aan de rechterkant en klikt u
op Verwijderen.
OPMERKING: Als u de lijst Geselecteerde gebruikers leeg laat, worden alle gebruikers beschouwd als gemachtigd.
11.3 Contextmenu
U kunt de integratie in het contextmenu inschakelen door te klikken op Instellingen > Voorkeuren voor toepassing opgeven... (of
dr uk op cmd+,) > Contextmenu door de optie Integreren in het contextmenu te selecteren. Meld u af of start de computer opnieuw
op om de wijzigingen door te voeren. Opties van het contextmenu zijn beschikbaar in het venster Finder als u CTRL+klikken op een
bestand uitvoert.

32
12. Overige
12.1 Instellingen importeren en exporteren
Als u een bestaande configuratie wilt importeren of uw ESET Cyber Security-configuratie wilt exporteren, klikt u op Instellingen >
Instellingen voor importeren of exporteren.
Importeren en exporteren is nuttig wanneer u een back-up wilt maken van uw huidige configuratie van ESET Cyber Security, zodat u
deze later kunt gebruiken. Instellingen exporteren is ook handig voor gebruikers die hun voorkeursconfiguratie van ESET Cyber
Security op meerdere systemen willen gebruiken. U kunt eenvoudig het configuratiebestand importeren om zo de gewenste
instellingen over te brengen.
Als u een configuratie wilt importeren, selecteert u Instellingen importeren en kl ikt u op Bladeren om naar het configuratiebestand
te navigeren dat u wilt importeren. Als u wilt exporteren, selecteert u Instellingen exporteren en gebruikt u de browser om een
locatie op uw computer te selecteren waar u het configuratiebestand opslaat.
12.2 Proxyserver instellen
Instellingen voor de proxyserver kunt u configureren in Instellingen > Voorkeuren voor toepassing opgeven... (of druk op cmd+,) >
Proxyserver. Als u de proxyserver op dit niveau opgeeft, worden algemene instellingen voor de proxyserver gedefinieerd voor alle
functies van ESET Cyber Security. De hier gedefinieerde parameters hier worden gebruikt door alle modules die verbinding met
internet vereisen. ESET Cyber Security ondersteunt de basistoegang en NTLM-verificatie (NT LAN Manager).
U kunt instellingen voor de proxyserver op dit niveau opgeven door het selectievakje Proxyserve r ge bruiken in te schakelen en het
IP-adres of de URL van de proxyserver in te voeren in het veld Proxyserver. Geef in het veld Poort de poort op waarop de
proxyserver verbindingen accepteert (standaard is dit 3128). U kunt ook op Detecteren klikken om het programma beide velden te
laten invullen.
Als voor communicatie met de proxyserver verificatie is vereist, geeft u een geldige Gebruikersnaam en Wachtwoord op in de
desbetreffende velden.

33
13. Woordenlijst
13.1 Typen infiltraties
Bij een infiltratie probeert schadelijke software de computer van een gebruiker binnen te dringen en/of te beschadigen.
13.1.1 Virussen
Een computervirus is een infiltratie die bestaande bestanden op uw computer beschadigt. De naam 'virussen' verwijst naar
biologische virussen, omdat ze vergelijkbare methoden gebruiken om zich van computer tot computer te verspreiden.
Computervirussen hebben het doorgaans voorzien op uitvoerbare bestanden, scripts en documenten. Een virus verspreidt zich
door zijn code aan het einde van een doelbestand vast te maken. Een computervirus werkt als volgt: nadat het geïnfecteerde
bestand is uitgevoerd, activeert het virus zichzelf (vóór de oorspronkelijke toepassing) en wordt de vooraf gedefinieerde taak van
het virus uitgevoerd. Pas dan kan de oorspronkelijke toepassing worden uitgevoerd. Een computer kan alleen met een virus worden
geïnfecteerd als een gebruiker het schadelijke programma per ongeluk of opzettelijk uitvoert of opent.
Het doel en het gevaar van computervirussen kan variëren. Sommige virussen zijn uiterst gevaarlijk omdat ze worden gebruikt om
opzettelijk bestanden van een vaste schijf te verwijderen. Andere virussen veroorzaken geen schade, maar zijn alleen ontwikkeld
om de gebruiker te irriteren en de technische vaardigheden van de ontwikkelaars tentoon te spreiden.
Een belangrijke ontwikkeling is dat virussen steeds minder vaak voorkomen (in vergelijking met trojaanse paarden of spyware)
omdat ze niet commercieel interessant zijn voor de makers van schadelijke software. De term 'virus' wordt bovendien vaak ten
onrechte gebruikt voor alle typen infiltraties. Hier komt echter langzaam verandering in doordat de nieuwe term
'malware' (malicious software = schadelijke software), die de lading beter dekt, in zwang is gekomen.
Als uw computer met een virus is geïnfecteerd, moet u de oorspronkelijke staat van de geïnfecteerde bestanden herstellen door ze
op te schonen met een antivirusprogramma.
13.1.2 Wormen
Een computerworm is een programma met schadelijke code dat hostcomputers aanvalt en zich verspreidt via een netwerk. Het
belangrijkste verschil tussen een virus en een worm is dat een worm in staat is zichzelf te verspreiden en te verplaatsen. Wormen
zijn niet afhankelijk van hostbestanden (of opstartsectoren). Wormen verspreiden zich via e-mailadressen in uw lijst met
contactpersonen of maken gebruik van beveiligingsproblemen in netwerktoepassingen.
Wormen zijn daarom veel hardnekkiger dan computervirussen. Door het massale gebruik van het internet kunnen wormen zich
enkele uren (soms zelfs enkele minuten) nadat ze in omloop zijn gebracht, over de hele wereld verspreiden. Doordat wormen zich
zelfstandig met grote snelheid kunnen verspreiden, zijn ze gevaarlijker dan andere typen malware, zoals virussen.
Als een worm in een systeem wordt geactiveerd, kan dat leiden tot verschillende problemen: de worm kan bestanden verwijderen,
de prestaties van het systeem verminderen of zelfs programma's deactiveren. Door zijn eigenschappen is de worm geschikt als
'transportmiddel' voor andere typen infiltraties.
Als uw computer is geïnfecteerd met een worm, adviseren wij u de geïnfecteerde bestanden te verwijderen omdat ze waarschijnlijk
schadelijke code bevatten.
13.1.3 Trojaanse paarden
Volgens de traditionele definitie zijn trojaanse paarden bedreigingen die zichzelf proberen voor te doen als nuttige programma's
en die vervolgens door nietsvermoedende gebruikers worden uitgevoerd. Tegenwoordig hoeven trojaanse paarden hun ware aard
niet meer te verbergen. Trojaanse paarden worden gebruikt om zo eenvoudig mogelijk te infiltreren, zodat ze hun schadelijke
praktijken kunnen uitvoeren. De term 'trojaans paard' heeft nu een algemene betekenis en wordt gebruikt voor infiltraties die niet
in een specifieke categorie infiltraties kunnen worden ingedeeld.
Omdat deze categorie erg breed is, worden trojaanse paarden vaak verdeeld in een aantal subcategorieën:
· Downloader - een schadelijk programma waarmee andere bedreigingen van het internet kunnen worden gedownload
· Dropper - een type trojaans paard waarmee andere typen malware kunnen worden geïnstalleerd op computers met
beveiligingsproblemen
· Backdoor - een toepassing die communiceert met externe aanvallers, waardoor zij toegang tot een systeem kunnen krijgen en het
systeem kunnen overnemen
· Keylogger - (keystroke logger) - een programma waarmee elke toetsaanslag van een gebruiker wordt geregistreerd, waarna de
gegevens naar externe aanvallers worden verzonden

34
· Dialer - dialers zijn programma's waarmee automatisch verbinding wordt gemaakt met nummers met hoge tarieven. Het is
vrijwel onmogelijk te merken dat er een nieuwe verbinding tot stand is gebracht. Dialers kunnen alleen schade veroorzaken voor
gebruikers met inbelmodems, die niet vaak meer worden gebruikt.
Trojaanse paarden zijn meestal uitvoerbare bestanden. Als er een trojaans paard op uw computer wordt gedetecteerd, adviseren
wij u het bestand te verwijderen omdat het waarschijnlijk schadelijke code bevat.
13.1.4 Rootkits
Rootkits zijn schadelijke programma's die aanvallers op internet onbeperkte toegang tot een systeem geven, waarbij hun
aanwezigheid wordt verborgen. Nadat ze toegang hebben verkregen tot het systeem (gewoonlijk door gebruik te maken van een
zwakke plek in het systeem) maken rootkits gebruik van functies van het systeem om detectie door antivirussoftware te voorkomen:
ze verbergen processen en bestanden. Daarom is het vrijwel onmogelijk ze te detecteren met normale testtechnieken.
13.1.5 Adware
Adware is een afkorting voor door advertenties ondersteunde software. Programma's waarin reclamemateriaal wordt weergegeven
vallen onder deze categorie. Adwareprogramma's openen vaak automatisch een nieuw pop-upvenster met reclame in een
internetbrowser of wijzigen de startpagina van de browser. Adware is vaak opgenomen in freewareprogramma's, waardoor de
makers van de freeware de ontwikkelkosten van hun (gewoonlijk nuttige) toepassingen kunnen terugverdienen.
Adware is op zichzelf niet gevaarlijk. Gebruikers worden gewoonlijk alleen lastiggevallen met advertenties. Het gevaar schuilt in
het feit dat adware ook traceringsfuncties kan uitvoeren (zoals spyware doet).
Als u besluit een freewareproduct te gebruiken, let dan speciaal op het installatieprogramma. Het installatieprogramma
waarschuwt u gewoonlijk bij de installatie van een extra adwareprogramma. Vaak kunt u deze annuleren en het programma
installeren zonder adware.
In sommige gevallen kunnen programma's niet worden geïnstalleerd zonder adware of wordt hun functionaliteit beperkt. Dit
betekent vaak dat adware mogelijk op 'legale' wijze toegang heeft tot het systeem, omdat gebruikers hiermee akkoord zijn gegaan.
In dat geval is het beter het zekere voor het onzekere te nemen. Als er op uw computer een bestand als adware wordt
geïdentificeerd, is het raadzaam dit te verwijderen aangezien de kans groot is dat dit schadelijke code bevat.
13.1.6 Spyware
Deze categorie omvat alle toepassingen waarmee persoonlijke gegevens worden verzonden zonder dat de gebruiker daar
toestemming voor heeft gegeven of zonder dat de gebruiker zich ervan bewust is. Spyware gebruikt traceerfuncties om
verschillende statistische gegevens te verzenden, zoals websites die de gebruiker heeft bezocht, e-mailadressen van de
contactpersonen van de gebruiker of toetsaanslagen van de gebruiker.
De makers van spyware beweren dat deze toepassingen zijn bedoeld om de wensen en interesses van de gebruiker te
inventariseren, zodat ze hun reclameboodschappen beter op de gebruiker kunnen afstemmen. Het probleem is echter dat er geen
duidelijk onderscheid tussen nuttige en schadelijke toepassingen kan worden gemaakt. Bovendien kan niemand garanderen dat er
geen misbruik van de gegevens wordt gemaakt. Voorbeelden van gegevens die kunnen worden verzameld met spywaretoepassingen
zijn beveiligingscodes, pincodes, bankrekeningnummers, enzovoort. Spyware wordt vaak bij gratis versies van een programma
gevoegd door de maker van het programma om inkomsten te genereren of om de gebruiker ertoe te bewegen de software aan te
schaffen. Vaak worden gebruikers tijdens de installatie van een programma geïnformeerd over de aanwezigheid van spyware om
hun ertoe te bewegen een betaalde versie zonder spyware aan te schaffen.
Voorbeelden van bekende freewareproducten waarbij spyware wordt meegeleverd, zijn clienttoepassingen van P2P-netwerken
(peer-to-peer). Spyfalcon of Spy Sheriff (en vele andere programma's) behoren tot een speciale subcategorie spywareprogramma's.
Deze programma's doen zich voor als antispywareprogramma's, maar zijn in feite zelf spywareprogramma's.
Als er op uw computer een bestand als spyware wordt geïdentificeerd, is het raadzaam dit te verwijderen, aangezien de kans groot
is dat dit schadelijke code bevat.
13.1.7 Potentieel onveilige toepassingen
Er zijn veel legitieme programma's die zijn bedoeld om het beheer van computers in een netwerk te vereenvoudigen. In de verkeerde
handen kunnen deze programma's echter worden gebruikt om schadelijke praktijken uit te oefenen. ESET Cyber Security biedt de
optie dergelijke bedreigingen te detecteren.
Potentieel onveilige toepassingen zijn doorgaans commerciële, legitieme software. Deze categorie omvat hulpprogramma's voor
externe toegang, toepassingen voor het kraken van wachtwoorden, keyloggers (programma's die elke toetsaanslag van een
gebruiker registreren), enzovoort.

35
13.1.8 Potentieel ongewenste toepassingen
Potentieel ongewenste toepassingen zijn niet niet per se schadelijk, maar kunnen de prestaties van uw computer aantasten. Voor
de installatie van dergelijke toepassingen moet doorgaans toestemming worden gegeven. Deze toepassingen veranderen de manier
waarop uw computer werkt. De voornaamste wijzigingen zijn:
· Weergave van vensters die u niet eerder hebt gezien
· Activering en uitvoering van verborgen processen
· Verhoogd gebruik van systeembronnen
· Wijzigi ngen in zoekres ul ta ten
· Communicatie tussen toepassingen en externe servers
13.2 Typen externe aanvallen
Er zijn veel speciale technieken waarmee aanvallers externe systemen in gevaar kunnen brengen. Deze zijn verdeeld in
verschillende categorieën.
13.2.1 DoS-aanvallen
DoS, ofwel Denial of Service, is een poging ervoor te zorgen dat een computer of netwerk niet beschikbaar is voor de bedoelde
gebruikers. De communicatie tussen getroffen gebruikers wordt belemmerd en kan niet meer op een functionele manier doorgaan.
Computers die getroffen zijn door een DoS-aanval moeten gewoonlijk opnieuw worden opgestart om weer goed te werken.
In de meeste gevallen zijn de doelen webservers en is het de bedoeling ervoor te zorgen dat deze voor een bepaalde periode niet
beschikbaar zijn voor gebruikers.
13.2.2 DNS Poisoning
Met DNS Poisoning (Domain Name Server) kunnen hackers de DNS-server van een computer laten geloven dat de nepgegevens die ze
hebben opgegeven legitiem en authentiek zijn. De valse informatie wordt een bepaalde tijd lang opgeslagen in de cache, zodat
aanvallers DNS-antwoorden van IP-adressen kunnen herschrijven. Hierdoor kunnen gebruikers die proberen toegang te krijgen tot
websites op internet computervirussen of wormen downloaden in plaats van de oorspronkelijke inhoud.
13.2.3 Port scanning
Port scanning wordt gebruikt om te bepalen welke computerpoorten zijn geopend op een netwerkhost. Een poortscanner is
software die is ontworpen om dergelijke poorten te zoeken.
Een computerpoort is een virtueel punt dat binnenkomende en uitgaande gegevens verwerkt. Dit is cruciaal vanuit een
beveiligingsstandpunt. In een groot netwerk kan de informatie die door poortscanners wordt verzameld helpen bij het identificeren
van potentiële beveiligingsrisico's. Een dergelijk gebruik is legitiem.
Port scanning wordt echter ook vaak gebruikt door hackers die proberen de beveiliging te omzeilen. Hun eerste stap is het
verzenden van pakketten naar elke poort. Aan de hand van het type antwoord kan worden bepaald welke poorten in gebruik zijn.
Het scannen zelf veroorzaakt geen schade, maar deze activiteit kan potentiële beveiligingsrisico's aan het licht brengen en
aanvallers in staat stellen externe computers over te nemen.
Netwerkbeheerders wordt geadviseerd alle ongebruikte poorten te blokkeren en de poorten die in gebruik zijn te beveiligen tegen
onbevoegde toegang.
13.2.4 TCP-desynchronisatie
TCP-desynchronisatie is een techniek die wordt gebruikt bij TCP-kapingaanvallen. Het wordt geactiveerd door een proces waarbij
het volgnummer van binnenkomende pakketten afwijkt van het verwachte volgnummer. Pakketten met een onverwacht volgnummer
worden overgeslagen (of opgeslagen in de bufferopslag, als ze aanwezig zijn in het huidige communicatievenster).
Bij desynchronisatie slaan beide communicatie-endpoints ontvangen pakketten over, waarna externe aanvallers kunnen
infiltreren en pakketten kunnen aanleveren met een juist volgnummer. De aanvallers kunnen zelfs communicatie manipuleren of
wijzigen.
TCP-kaping is bedoeld om communicatie tussen server en client of peer-to-peer te onderbreken. Veel aanvallen kunnen worden
voorkomen door verificatie te gebruiken voor elk TCP-segment. Ook wordt geadviseerd de aanbevolen configuratie te gebruiken
voor uw netwerkapparaten.

36
13.2.5 SMB Relay
SMBRelay en SMBRelay2 zijn speciale programma's die aanvallen kunnen uitvoeren op externe computers. Deze programma's
maken gebruik van het Server Message Block-protocol voor het delen van bestanden, dat als laag op het NetBIOS is
geїmplementeerd. Een gebruiker die een map of directory deelt binnen een LAN gebruikt hoogstwaarschijnlijk dit protocol voor het
delen van bestanden.
Binnen de lokale netwerkcommunicatie worden wachtwoordhashes uitgewisseld.
SMBRelay krijgt een verbinding via UDP-poort 139 en 445, geeft de pakketten door die door de client en server worden uitgewisseld
en wijzigt deze. Nadat verbinding is gemaakt en geverifieerd, wordt de verbinding met de client verbroken. SMBRelay maakt een
nieuwe virtueel IP-adres. SMBRelay geeft SMB-protocolcommunicatie door, met uitzondering van onderhandeling en verificatie.
Externe aanvallers kunnen het IP-adres gebruiken zolang de clientcomputer is verbonden.
SMBRelay2 werkt volgens hetzelfde principe als SMBRelay, behalve dat het gebruik maakt van NetBIOS-namen in plaats van IP-
adressen. Beide kunnen 'man-in-het-midden'-aanvallen uitvoeren. Deze aanvallen stellen externe aanvallers in staat berichten die
worden uitgewisseld tussen twee communicatie-eindpunten te lezen, in te voegen en te wijzigen, zonder te worden opgemerkt.
Computers die zijn getroffen door dergelijke aanvallen reageren vaak niet meer of starten onverwachts opnieuw op.
Ter voorkoming van aanvallen raden we u aan verificatiewachtwoorden of -codes te gebruiken.
13.2.6 ICMP-aanvallen
Het ICMP (Internet Control Message Protocol) is een populair en veelgebruikt internetprotocol. Het wordt voornamelijk gebruikt
door netwerkcomputers voor het verzenden van diverse foutmeldingen.
Externe aanvallers proberen gebruik te maken van de zwakke plekken van het ICMP-protocol. Het ICMP-protocol is ontworpen voor
communicatie in één richting waarvoor geen verificatie vereist is. Hierdoor kunnen externe aanvallers DoS-aanvallen (Denial of
Service) uitvoeren, of aanvallen waarbij onbevoegde personen toegang krijgen tot binnenkomende en uitgaande pakketten.
Kenmerkende voorbeelden van een ICMP-aanval zijn ping floods, ICMP_ECHO-floods en smurfaanvallen. Computers die zijn
getroffen door een ICMP-aanval zijn aanzienlijk langzamer (dit geldt voor alle toepassingen die internet gebruiken) en hebben
problemen met verbinding maken met internet.
13.3 E-mail
E-mail, ofwel elektronische post, is een moderne vorm van communicatie met talloze voordelen. Het is flexibel, snel en direct en
heef een cruciale rol gespeeld bij de opkomst van internet begin jaren '90.
Helaas is er door het hoge niveau van anonimiteit in e-mail en op internet ruimte voor illegale activiteiten, zoals spammen. Spam
omvat ongevraagde advertenties, nepmeldingen en de verspreiding van schadelijke software - malware. Het ongemak en gevaar
voor u wordt verhoogd door het feit dat de kosten voor het verzenden van spam minimaal zijn en auteurs van spam beschikken
over allerlei hulpmiddelen om nieuwe e-mailadressen mee te verzamelen. Daarnaast maakt de hoeveelheid en verscheidenheid
van spam het uiterst moeilijk te reguleren. Hoe langer u een e-mailadres gebruikt, hoe groter de kans dat dit terechtkomt in de
database van een spam-engine. Enkele tips om dit te voorkomen:
· publiceer uw e-mailadres indien mogelijk niet op internet
· geef uw e-mailadres alleen aan personen die u vertrouwt
· gebruik indien mogelijk geen algemene aliassen. Bij complexere aliassen is het onwaarschijnlijker dat deze worden gevolgd
· beantwoord geen spam die al in uw Postvak IN is gearriveerd
· wees voorzichtig bij het invullen van formulieren op internet. Let vooral op opties zoals Ja, ik wil graag informatie ontvangen
· gebruik 'gespecialiseerde' e-mailadressen, bijvoorbeeld een voor zakelijk gebruik, een voor communicatie met vrienden enz.
· wijzig uw e-mailadres van tijd tot tijd
· gebruik een antispamoplossing
13.3.1 Advertenties
Adverteren op internet is een van de snelst groeiende vormen van adverteren. De belangrijkste marketingvoordelen zijn de
minimale kosten en hoge mate van directheid. Bovendien worden berichten vrijwel onmiddellijk afgeleverd. Veel bedrijven maken
gebruik van hulpmiddelen voor e-mailmarketing om doeltreffend te communiceren met hun huidige en potentiële klanten.
Dit type adverteren is legitiem, aangezien u mogelijk geїnteresseerd bent in het ontvangen van commerciele informatie over
bepaalde producten. Veel bedrijven verzenden echter ongevraagd grote hoeveelheden commerciële berichten. In dergelijke gevallen
wordt de grens overschreden en worden e-mailadvertenties spam.
De hoeveelheid ongevraagde e-mail is een probleem geworden en dit lijkt vooralsnog niet af te nemen. Auteurs van ongevraagde e-
mail proberen spam vaak te vermommen als legitieme berichten.

37
13.3.2 Nepmeldingen
Een nepmelding of hoax is onjuiste informatie die op internet wordt verspreid. Nepmeldingen worden gewoonlijk verstuurd via e-
mail of communicatiehulpmiddelen zoals ICQ en Skype. Het bericht zelf is vaak een grap of een 'broodje aap'-verhaal.
Nepmeldingen over computervirussen proberen angst, onzekerheid en twijfel op te roepen bij de ontvangers, door hen te laten
geloven dat er een 'niet detecteerbaar' virus bestanden wist en wachtwoorden steelt, of andere schadelijke activiteiten uitvoert op
hun systeem.
Sommige nepmeldingen werken door de ontvanger te vragen de berichten door te sturen naar hun contactpersonen, zodat de
nepmelding wordt voortgezet. Er zijn nepmeldingen voor mobiele telefoons, pleidooien om hulp, personen die aanbieden u geld te
sturen vanuit het buitenland enz. Vaak is het onmogelijk de bedoeling van de maker te achterhalen.
Als u een bericht ziet waarin u wordt gevraagd dit door te sturen naar iedereen die u kent, is de kans groot dat dit een nepmelding
is. Er zijn veel websites op internet waar u kunt controleren of een e-mail legitiem is. Zoek, voordat u het doorstuurt, eerst op
internet naar een bericht waarvan u vermoedt dat het een nepmelding is.
13.3.3 Phishing
De term phishing definieert een criminele activiteit waarbij gebruik wordt gemaakt van 'social engineering' (het manipuleren van
gebruikers om vertrouwelijke informatie te verkrijgen). Het doel ervan is toegang te verkrijgen tot gevoelige gegevens, zoals
bankrekeningnummers, pincodes enz.
Toegang wordt gewoonlijk verkregen door een e-mail te versturen die zich voordoet als zijnde afkomstig van een betrouwbaar
persoon of bedrijf (bijvoorbeeld een financiële instelling of een verzekeringsmaatschappij). De e-mail kan er heel echt uitzien en
bevat vaak afbeeldingen en inhoud die oorspronkelijk afkomstig zijn van de bron die wordt geїmiteerd. U wordt, onder diverse
valse voorwendselen (verificatie van gegevens, financiële activiteiten), gevraagd enkele van uw persoonlijke gegevens in te voeren
- bankrekeningnummers of gebruikersnamen en wachtwoorden. Al deze gegevens kunnen worden gestolen en misbruikt als u ze
invoert.
Banken, verzekeringsmaatschappijen en andere legitieme bedrijven zullen nooit vragen om gebruikersnamen en wachtwoorden in
een ongevraagde e-mail.
13.3.4 Oplichterijspam herkennen
Doorgaans zijn er een paar aanwijzingen die u kunnen helpen bij het herkennen van spam (ongevraagde e-mail) in uw Postvak IN.
Als een bericht aan ten minste enkele van de volgende criteria voldoet, is het waarschijnlijk een spambericht.
· Het adres van de afzender is niet van iemand in uw lijst met contactpersonen
· u wordt een groot geldbedrag aangeboden, maar u moet eerst een klein bedrag betalen
· u wordt, onder diverse valse voorwendselen (verificatie van gegevens, financiële activiteiten), gevraagd enkele van uw
persoonlijke gegevens in te voeren - bankrekeningnummers, gebruikersnamen en wachtwoorden enz.;
· het is geschreven in een vreemde taal
· u wordt gevraagd een product te kopen waarin u niet geïnteresseerd bent. Als u toch besluit het te kopen, controleer dan of de
afzender van het bericht een betrouwbare leverancier is (raadpleeg de fabrikant van het originele product)
· sommige woorden zijn onjuist gespeld als poging uw spamfilter te misleiden. Bijvoorbeeld vaigra i n pl aats va n viagra enz.
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
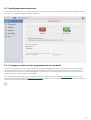 11
11
-
 12
12
-
 13
13
-
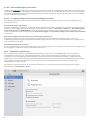 14
14
-
 15
15
-
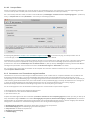 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
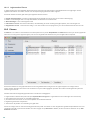 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
ESET Cyber Security for macOS Gebruikershandleiding
- Type
- Gebruikershandleiding
Gerelateerde papieren
-
ESET Endpoint Security for macOS Gebruikershandleiding
-
ESET Endpoint Antivirus for macOS Gebruikershandleiding
-
ESET Glossary de handleiding
-
ESET Endpoint Security for macOS 6.10 de handleiding
-
ESET Endpoint Antivirus for macOS 6.1X de handleiding
-
ESET Cyber Security Pro for macOS 6 de handleiding
-
ESET Endpoint Security for macOS 6.9 de handleiding
-
ESET Cyber Security for macOS 6 de handleiding
-
ESET NOD32 Antivirus Gebruikershandleiding
-
ESET Cyber Security for macOS Snelstartgids





































