ESET Endpoint Security for macOS Gebruikershandleiding
- Type
- Gebruikershandleiding

ESET, spol. s.r.o.
ESET Endpoint Security is ontwikkeld door ESET, s pol. s r.o.
Ga voor meer i nforma tie na ar www.eset.com.
Alle rechten voorbehouden. Niets uit deze documentatie mag worden verveelvoudigd, opgeslagen in een
systeem voor het opha len van gegevens of overgedragen, in enige vorm of op enige wijze, hetzij elektronisch,
mecha nisch, door fotokopie, opna me, s can of enige a ndere manier, zonder schriftelijke toestemming van de
auteur.
ESET, spol. s r.o. behoudt zich het recht voor de bes chreven toepass ingssoftwa re zonder voorafgaande
kennisgeving te wijzigen.
Klantenservice: www.eset.com/support
REV. 10/13/2017

Inhoudsopgave
.......................................................5ESET Endpoint Security1.
....................................................................................................5Wat is er nieuw in versie 61.1
....................................................................................................5Systeemvereisten1.2
.......................................................6
Gebruikers die verbinding maken via ESET
Remote Administrator
2.
....................................................................................................6ESET Remote Administrator Server2.1
....................................................................................................7Webconsole2.2
....................................................................................................8Proxy2.3
....................................................................................................8Agent2.4
....................................................................................................8RD-sensor2.5
.......................................................9Installatie3.
....................................................................................................9Standaardinstallatie3.1
....................................................................................................10Aangepaste installatie3.2
....................................................................................................11Installatie op afstand3.3
..............................................................................11Een pakket voor insta llatie op afstand maken
3.3.1
..............................................................................12Installatie op afstand op doelcomputers
3.3.2
..............................................................................12Verwijdering op afstand
3.3.3
..............................................................................12Upgrade op afstand
3.3.4
.......................................................13Productactivering4.
.......................................................15Verwijderen5.
.......................................................16Basisoverzicht6.
....................................................................................................16Sneltoetsen6.1
....................................................................................................17Werking van het systeem controleren6.2
....................................................................................................17
Te volgen procedure als het programma
niet correct werkt
6.3
.......................................................18Computerbeveiliging7.
....................................................................................................18Antivirus- en antispywarebeveiliging7.1
..............................................................................18Algemeen
7.1.1
..................................................................................18Uitsluitingen
7.1.1.1
..............................................................................19Beveiliging bij het opstarten
7.1.2
..............................................................................19Real-timebeveiliging va n bes tandss ysteem
7.1.3
..................................................................................19Geavanceerde opties
7.1.3.1
..................................................................................20
Wanneer moet de configuratie voor
real-timebeveiliging worden gewijzigd?
7.1.3.2
..................................................................................20Real-timebeveiliging controleren
7.1.3.3
..................................................................................20
Te volgen procedure als rea l-timebeveiliging niet
werkt
7.1.3.4
..............................................................................21On-demand computersca n
7.1.4
..................................................................................21Type sca n
7.1.4.1
........................................................................21Smart scan
7.1.4.1.1
........................................................................22Aangepa ste scan
7.1.4.1.2
..................................................................................22Scandoelen
7.1.4.2
..................................................................................22Scanprofielen
7.1.4.3
..............................................................................23Pa rameters voor ThreatSense-engine instellen
7.1.5
..................................................................................24Objecten
7.1.5.1
..................................................................................24Opties
7.1.5.2
..................................................................................24Opschonen
7.1.5.3
..................................................................................25Uitsluitingen
7.1.5.4
..................................................................................25Limiet
7.1.5.5
..................................................................................25Overige
7.1.5.6
..............................................................................26Er is een infiltratie gedetecteerd
7.1.6
....................................................................................................26Web- en e-mailbeveiliging7.2
..............................................................................27Beveiliging van webtoegang
7.2.1
..................................................................................27Poorten
7.2.1.1
..................................................................................27URL-lijsten
7.2.1.2
..............................................................................27E-mailbeveiliging
7.2.2
..................................................................................28POP3-protocolcontrole
7.2.2.1
..................................................................................28IMAP-protocolcontrole
7.2.2.2
....................................................................................................28Antiphishing7.3
.......................................................29Firewall8.
....................................................................................................29Filtermodi8.1
....................................................................................................30Firewallregels8.2
..............................................................................30Nieuwe regels maken
8.2.1
....................................................................................................30Firewallzones8.3
....................................................................................................31Firewallprofielen8.4
....................................................................................................31Firewalllogboeken8.5
.......................................................32Apparaatbeheer9.
....................................................................................................32Regeleditor9.1
.......................................................34Webbeheer10.
.......................................................35Hulpmiddelen11.
....................................................................................................35Logbestanden11.1
..............................................................................35Onderhoud va n logbes tanden
11.1.1
..............................................................................36Logbestanden filteren
11.1.2
....................................................................................................37Planner11.2
..............................................................................38Nieuwe taken maken
11.2.1
..............................................................................38Een door gebruiker gedefinieerde ta ak ma ken
11.2.2
....................................................................................................39Live Grid11.3
..............................................................................39Verdachte bestanden
11.3.1
....................................................................................................40Quarantaine11.4
..............................................................................40Bestanden in quara nta ine plaatsen
11.4.1
..............................................................................40Een in quara ntaine geplaats t bestand herstellen
11.4.2
..............................................................................41Een bestand verzenden vanuit quara nta ine
11.4.3
....................................................................................................41Machtigingen11.5
....................................................................................................41Presentatiemodus11.6
....................................................................................................42Actieve processen11.7
.......................................................43Gebruikersinterface12.
....................................................................................................43Waarschuwingen en meldingen12.1
..............................................................................43Waarschuwingen weergeven
12.1.1
..............................................................................44Beveiligingsstatussen
12.1.2
....................................................................................................44Contextmenu12.2

.......................................................45Bijwerken13.
....................................................................................................45Instellingen voor update13.1
..............................................................................46Geava nceerde opties
13.1.1
....................................................................................................47Updatetaken maken13.2
....................................................................................................47Upgraden naar een nieuwe build13.3
....................................................................................................47Systeemupdates13.4
.......................................................49Overige14.
....................................................................................................49Instellingen importeren en exporteren14.1
....................................................................................................49Proxyserver instellen14.2
....................................................................................................50Gedeelde lokale cache14.3

5
1. ESET Endpoint Security
ESET Endpoint Security 6 vertegenwoordigt een nieuwe benadering van werkelijk geïntegreerde
computerbeveiliging. De recentste versie van de ThreatSense®-scanengine, in combinatie met onze aangepaste
firewall, beveiligt uw computer snel en nauwkeurig. Het resultaat is een intelligent systeem dat permanent alert is
op aanvallen en schadelijke software die uw computer mogelijk bedreigen.
ESET Endpoint Security 6 is een complete beveiligingsoplossing die is ontwikkeld voor de lange termijn om een
maximale beveiliging en een minimale systeemvoetafdruk te realiseren. De geavanceerde technologieën,
gebaseerd op artificiële intelligentie, kunnen proactief infiltratie door virussen, spyware, trojaanse paarden,
wormen, adware, rootkits en andere aanvallen via internet elimineren, zonder dat de systeemprestaties worden
gehinderd of de werking van uw computer wordt verstoord.
Het product is primair ontwikkeld voor gebruik op werkstations in kleine ondernemingen. In combinatie met ESET
Remote Administrator 6 kunt u eenvoudig elk gewenst aantal clientwerkstations beheren, beleid en regels
toepassen, detectieresultaten bijhouden en extern aanpassingen uitvoeren vanaf elke computer in het netwerk.
1.1 Wat is er nieuw in versie 6
De grafische gebruikersinterface van ESET Endpoint Security is helemaal opnieuw ontworpen om beter inzicht te
geven en een intuïtievere gebruikerservaring te bieden. Enkele van de verbeteringen die zijn doorgevoerd in versie
6 zijn:
· Firewall: u kunt firewallregels nu rechtstreeks vanuit het logbestand of het IDS (Intrusion detection system)-
meldingsvenster maken en profielen toewijzen aan netwerkinterfaces.
· Filter voor webtoegang - blokkeert webpagina's die mogelijk ongepast of schadelijk materiaal bevatten
· Beveiliging van webtoegang - bewaakt communicatie tussen webbrowsers en externe servers
· E-mailbeveiliging: biedt controle van e-mailcommunicatie die wordt ontvangen via het POP3- en IMAP-protocol
· Antiphishing: biedt bescherming tegen pogingen om wachtwoorden en andere gevoelige informatie te stelen
doordat de toegang tot schadelijke websites die legitieme websites nabootsen wordt beperkt
· Apparaatbeheer: hiermee kunt u uitgebreide filters en/of machtigingen scannen, blokkeren en aanpassen, en
bepalen hoe een gebruiker externe apparaten benadert en ermee werkt. Deze functie is beschikbaar in
productversie 6.1 en later.
· Presentatiemodus: hiermee kunt u ESET Endpoint Security op de achtergrond uitvoeren en pop-upvensters en
geplande taken onderdrukken
· Gedeelde lokale cache: hiermee kunt u sneller scannen in gevirtualiseerde omgevingen
1.2 Systeemvereisten
Voor optimale prestaties van ESET Endpoint Security moet uw systeem voldoen aan de volgende hardware- en
softwarevereisten:
Systeemvereisten:
Processorarchitectuur
Intel 32-bits, 64-bits
Besturingssysteem
macOS 10.9 en later
Geheugen
300 MB
Vrije schijfruimte
200 MB

6
2. Gebruikers die verbinding maken via ESET Remote Administrator
ESET Remote Administrator (ERA) 6 is een toepassing waarmee u ESET-producten in een netwerkomgeving vanaf
één centrale locatie kunt beheren. Met het ESET Remote Administrator-taakbeheersysteem kunt u ESET-
beveiligingsoplossingen op externe computers installeren en snel reageren op nieuwe problemen en
bedreigingen. ESET Remote Administrator biedt zelf geen bescherming tegen schadelijke code, maar vertrouwt
hiervoor op de aanwezigheid van een ESET-beveiligingsoplossing op elke client.
ESET-beveiligingsoplossingen ondersteunen netwerken die uit meerdere platformtypen bestaan. Uw netwerk kan
bestaan uit een combinatie van Microsoft-, Linux- en macOS-besturingssystemen die op mobiele apparaten worden
uitgevoerd (mobiele telefoons en tablets).
In de onderstaande afbeelding staat een voorbeeldarchitectuur van een netwerk dat door ERA met ESET-
beveiligingsoplossingen wordt beschermd:
OPMERKING: Zi e de online documentatie van ESET Remote Administrator voor meer informatie.
2.1 ESET Remote Administrator Server
ESET Remote Administrator Server is een uitvoerend onderdeel van ESET Remote Administrator. Hiermee worden
alle gegevens verwerkt die worden ontvangen van clients die verbinding maken met de server (via de ERA-agent
). De ERA-agent maakt communicatie tussen de client en server mogelijk. Gegevens (clientlogbestanden,
configuratie, agentreplicatie, enz.,) worden opgeslagen in een database waartoe ERA toegang heeft voor
rapportagedoeleinden.
8

7
Om de gegevens op de juiste wijze te verwerken is voor de ERA-server een stabiele verbinding met een
databaseserver nodig. We raden aan dat u ERA-server en uw database op aparte servers installeert om de prestaties
te optimaliseren. De computer waarop ERA-server wordt geïnstalleerd moet zodanig worden geconfigureerd dat
alle agent-/proxy-/RD-sensorverbindingen worden geaccepteerd, die met certificaten worden geverifieerd. Als ERA
Server is geïnstalleerd, kunt u de ERA-webconsole openen waarmee u eindpunt-werkstations kunt beheren
waarop ESET-oplossingen zijn geïnstalleerd.
2.2 Webconsole
ERA-webconsole is een op het web gebaseerde gebruikersinterface die gegevens vertegenwoordigt van ERA-
server en hiermee kunt u ESET-beveiligingsoplossingen in uw netwerk beheren. U hebt via een browser toegang
tot de webconsole. De webconsole geeft een overzicht van de status van clients in uw netwerk en kan worden
gebruikt om ESET-oplossingen op afstand te implementeren op niet-beheerde computers. U kunt de webserver
toegankelijk te maken via internet zodat ESET Remote Administrator vanaf vrijwel elke locatie en elk apparaat kan
worden gebruikt.
Het dashboard van de webconsole:
He t hul pprogramma Snelzoeken bevindt zich boven in de webconsole. Selecteer in het vervolgkeuzemenu
Computernaam, IPv4-/IPv6-adres of Naam van bedreiging, typ uw zoektekst in het tekstveld en klik op het
vergrootglas of druk op Enter om te zoeken. U wordt doorgestuurd naar het gedeelte Groepen, waar uw
zoekresultaat wordt weergegeven.
7
6

8
2.3 Proxy
ERA-proxy is een ander onderdeel van ESET Remote Administrator en heeft twee hoofddoelen. In een middelgroot
of groot bedrijfsnetwerk met veel clients (bijvoorbeeld 10.000 clients of meer) kunt u ERA-proxy gebruiken om de
werkbelasting te verdelen over meerdere ERA-proxy's die de ERA-hoofdserver ondersteunen. Het andere
voordeel van de ERA-proxy is dat u deze kunt gebruiken wanneer u verbinding maakt met een externe vestiging
met een slechte verbinding. Dit betekent dat de ERA-agent op elke client geen verbinding maakt met de ERA-
hoofdserver, maar rechtstreeks via de ERA-proxy die zich in hetzelfde lokale netwerk bevindt als de externe
vestiging. Deze configuratie zorgt ervoor dat de verbinding met de vestiging beter beschikbaar is. De ERA-proxy
accepteert verbindingen van alle lokale ERA-agenten, verzamelt de gegevens ervan en uploadt die naar de ERA-
hoofdserver (of een andere ERA-proxy). Hierdoor biedt uw netwerk ruimte aan meer clients zonder dat dit nadelige
gevolgen heeft voor de prestaties van uw netwerk en query's die naar de database worden verzonden.
Afhankelijk van uw netwerkconfiguratie kan een ERA-proxy verbinding maken met een andere ERA-proxy en
vervolgens verbinding maken met de ERA-hoofdserver.
Voor een juiste werking van de ERA-proxy moet op de hostcomputer waarop u de ERA-proxy installeert een ESET-
agent zijn geïnstalleerd en deze moet zijn verbonden met het hoogste niveau (een ERA-server of hoogste ERA-
proxy, als die er is) van uw netwerk.
2.4 Agent
De ERA-agent is een essentieel onderdeel van ESET Remote Administrator. ESET-beveiligingsoplossingen op
clientcomputers (bijvoorbeeld ESET Endpoint Security) communiceren via de agent met de ERA-server. Deze
communicatie maakt het beheer vanaf één centrale locatie mogelijk van de ESET-beveiligingsoplossingen op alle
externe clients. De agent verzamelt informatie van de client en verzendt deze naar de server. Als de server een taak
naar een client verzendt, wordt de taak verzonden naar de agent die vervolgens met de client communiceert. Alle
netwerkcommunicatie vindt plaats tussen de agent en het hoogste niveau van het ERA-netwerk - server en proxy.
De ESET-agent gebruikt een van de volgende drie methoden om verbinding te maken met de server:
1. De agent van de client is rechtstreeks verbonden met de server.
2. De agent van de client is verbonden via een proxy, die is verbonden met de server.
3. De agent van de client is via meerdere proxy's verbonden met de server.
De ESET-agent communiceert met ESET-oplossingen die op een client zijn geïnstalleerd, verzamelt informatie van
programma's op die client en geeft configuratie-informatie die van de server wordt ontvangen door aan de client.
OPMERKING: De ESET-proxy heeft zijn eigen agent, die alle communicatietaken tussen clients, andere proxy's en de
server afhandelt.
2.5 RD-sensor
RD (Rogue Detection) Sensor is een onderdeel van ESET Remote Administrator waarmee naar computers in uw
netwerk wordt gezocht. Het is een gemakkelijke manier om nieuwe computers toe te voegen aan ESET Remote
Administrator zonder ze handmatig te hoeven zoeken en toevoegen. Elke computer die in uw netwerk wordt
gevonden, wordt weergegeven in de webconsole en toegevoegd aan de standaardgroep Alles. Van daaruit kunt u
verdere acties met afzonderlijke clientcomputers ondernemen.
RD-sensor is een passieve luisterfunctie die computers detecteert die zich in het netwerk bevinden en informatie
over deze computers doorgeeft aan de ERA-server. De ERA-server bepaalt of de pc's die in het netwerk zijn
gevonden, onbekende of reeds beheerde computers zijn.
6

9
3. Installatie
Er zijn twee manieren om het ESET Endpoint Security-installatieprogramma te starten:
· Als u het programma installeert vanaf de installatie-CD/DVD, plaatst u deze in het CD/DVD-ROM-station en
dubbelklikt u op het installatiepictogram ESET Endpoint Security om het installatieprogramma te starten.
· Als u een gedownload bestand gebruikt, dubbelklikt u op dit bestand om het installatieprogramma te starten.
De installatiewizard begeleidt u tijdens de installatie. Tijdens de eerste fase van de installatie zoekt het
installatieprogramma automatisch online naar de meest recente productversie. Als er een nieuwere versie wordt
gevonden, hebt u de mogelijkheid de nieuwste versie te downloaden alvorens het installatieproces voor te zetten.
Nadat u akkoord bent gegaan met de eindgebruikersovereenkomst, kunt u kiezen uit de volgende installatietypen:
· Standaardinstallatie
· Aangepaste installatie
· Installatie op afstand
3.1 Standaardinstallatie
Een standaardinstallatiemodus omvat de configuratie-opties die geschikt zijn voor de meeste gebruikers. Deze
instellingen bieden maximale veiligheid in combinatie met uitstekende systeemprestaties. De standaardinstallatie
is de standaardoptie en wordt aanbevolen als u geen speciale vereisten hebt voor bepaalde instellingen.
ESET Live Grid
Het ESET Live Grid vroegtijdig waarschuwingssysteem helpt waarborgen dat ESET onmiddellijk en continu wordt
geïnformeerd over nieuwe infiltraties teneinde klanten snel bescherming te kunnen bieden. Het systeem maakt
het mogelijk nieuwe bedreigingen in te zenden naar het bedreigingslaboratorium van ESET, waar deze worden
geanalyseerd en verwerkt. Klik op Instellen om gedetailleerde instellingen voor het verzenden van verdachte
bestanden te wijzigen. Zie Live Grid voor meer informatie.
9
10
11
39

10
Potentieel ongewenste toepassingen
De laatste stap in het installatieproces is het configureren van detectie van Mogelijk ongewenste toepassingen.
Dergelijke programma's zijn niet per se schadelijk, maar kunnen het gedrag van het besturingssysteem vaak
negatief beïnvloeden. Deze toepassingen worden vaak meegeleverd met andere programma's en vallen nauwelijks
op tijdens de installatie. Hoewel bij deze toepassingen gewoonlijk een melding wordt weergegeven tijdens de
installatie, kunnen ze eenvoudig zonder uw toestemming worden geïnstalleerd.
Na installatie van ESET Endpoint Security moet u de computer scannen op schadelijke code. Klik in het hoofdvenster
van het programma op Computerscan en klik vervolgens op Smart scan. Raadpleeg de sectie On-demand
computerscan voor meer informatie over on-demand computerscans.
3.2 Aangepaste installatie
De aangepaste installatiemodus is bedoeld voor ervaren gebruikers die geavanceerde instellingen willen wijzigen
tijdens de installatie.
Programmaonderdelen
Met ESET Endpoint Security kunt u het product installeren zonder enkele kerncomponenten (bijvoorbeeld web- en
e-mailbeveiliging). Schakel het selectievakje naast een productcomponent uit om deze buiten de installatie te
laten.
Proxyserver
Als u een proxyserver gebruikt, kunt u de parameters daarvan opgeven door de optie Ik gebruik een proxyserver te
selecteren. Geef in het volgende venster het IP-adres of de URL van uw proxyserver op in het veld Adres. Geef in
het veld Poort de poort op waarop de proxyserver verbindingen accepteert (standaard is dit (3128). Als de
proxyserver verificatie vereist, moet u een geldige gebruikersnaam en een geldig wachtwoord invoeren om
toegang te krijgen tot de proxyserver. Als u geen proxyserver gebruikt, selecteer dan Ik gebruik geen proxyserver.
Als u er niet zeker van bent of u een proxyserver gebruikt of niet, kunt u de huidige systeeminstellingen gebruiken
door Dezelfde instellingen als de systeeminstellingen gebruiken (aanbevolen) te selecteren.
Machtigingen
In de volgende stap kunt u gemachtigde gebruikers of groepen definiëren die de programmaconfiguratie kunnen
bewerken. Selecteer de gebruikers in de lijst aan de linkerkant en klik op Toevoegen om hen toe te voegen aan de
lijst Gemachtigde gebruikers. Als u alle systeemgebruikers wilt weergeven, selecteert u Alle gebruikers
weergeven. Als u de lijst Gemachtigde gebruikers leeg laat, worden alle gebruikers beschouwd als gemachtigd.
ESET Live Grid
Het ESET Live Grid vroegtijdig waarschuwingssysteem helpt waarborgen dat ESET onmiddellijk en continu wordt
geïnformeerd over nieuwe infiltraties teneinde klanten snel bescherming te kunnen bieden. Het systeem maakt
het mogelijk nieuwe bedreigingen in te zenden naar het bedreigingslaboratorium van ESET, waar deze worden
geanalyseerd en verwerkt. Klik op Instellen om gedetailleerde instellingen voor het verzenden van verdachte
bestanden te wijzigen. Zie Live Grid voor meer informatie.
Potentieel ongewenste toepassingen
De volgende stap in het installatieproces is het configureren van detectie van Mogelijk ongewenste toepassingen.
Dergelijke programma's zijn niet per se schadelijk, maar kunnen het gedrag van het besturingssysteem vaak
negatief beïnvloeden. Deze toepassingen worden vaak meegeleverd met andere programma's en vallen nauwelijks
op tijdens de installatie. Hoewel bij deze toepassingen gewoonlijk een melding wordt weergegeven tijdens de
installatie, kunnen ze eenvoudig zonder uw toestemming worden geïnstalleerd.
Firewall
Selecteer een filtermodus voor de firewall. Zie Filtermodi voor meer informatie.
Na installatie van ESET Endpoint Security moet u de computer scannen op schadelijke code. Klik in het hoofdvenster
van het programma op Computerscan en klik vervolgens op Smart scan. Zi e Computerscan op aanvraag voor meer
informatie over computerscans op aanvraag.
21
39
29
21

11
3.3 Installatie op afstand
Met installatie op afstand kunt u een installatiepakket maken dat met software voor extern bureaublad op
doelcomputers kan worden geïnstalleerd. Nadat de installatie is voltooid, kan ESET Endpoint Security extern
worden beheerd via ESET Remote Administrator.
Een installatie op afstand bestaat uit twee fasen:
1. Een pakket voor installatie op afstand maken met de ESET installer
2. Installatie op afstand met software voor extern bureaublad
Als u de nieuwste versie van ESET Remote Administrator 6 gebruikt, kunt u ook een externe installatie uitvoeren op
macOS-clientcomputers. Voor meer instructies, volgt u de stappen in dit artikel in de kennisbank. (Het artikel is
mogelijk niet beschikbaar in uw taal.)
3.3.1 Een pakket voor installatie op afstand maken
Programmaonderdelen
Met ESET Endpoint Security kunt u het product installeren zonder enkele kerncomponenten (bijvoorbeeld web- en
e-mailbeveiliging). Schakel het selectievakje naast een productcomponent uit om deze buiten de installatie te
laten.
Proxyserver
Als u een proxyserver gebruikt, kunt u de parameters daarvan opgeven door de optie Ik gebruik een proxyserver te
selecteren. Geef in het volgende venster het IP-adres of de URL van uw proxyserver op in het veld Adres. Geef in
het veld Poort de poort op waarop de proxyserver verbindingen accepteert (standaard is dit (3128). Als de
proxyserver verificatie vereist, moet u een geldige gebruikersnaam en een geldig wachtwoord invoeren om
toegang te krijgen tot de proxyserver. Als u geen proxyserver gebruikt, selecteer dan Ik gebruik geen proxyserver.
Als u er niet zeker van bent of u een proxyserver gebruikt of niet, kunt u de huidige systeeminstellingen gebruiken
door Dezelfde instellingen als de systeeminstellingen gebruiken (aanbevolen) te selecteren.
Machtigingen
In de volgende stap kunt u gemachtigde gebruikers of groepen definiëren die de programmaconfiguratie kunnen
bewerken. Selecteer de gebruikers in de lijst aan de linkerkant en klik op Toevoegen om hen toe te voegen aan de
lijst Gemachtigde gebruikers. Als u alle systeemgebruikers wilt weergeven, selecteert u Alle gebruikers
weergeven. Als u de lijst Gemachtigde gebruikers leeg laat, worden alle gebruikers beschouwd als gemachtigd.
ESET Live Grid
Het ESET Live Grid vroegtijdig waarschuwingssysteem helpt waarborgen dat ESET onmiddellijk en continu wordt
geïnformeerd over nieuwe infiltraties teneinde klanten snel bescherming te kunnen bieden. Het systeem maakt
het mogelijk nieuwe bedreigingen in te zenden naar het bedreigingslaboratorium van ESET, waar deze worden
geanalyseerd en verwerkt. Klik op Instellen om gedetailleerde instellingen voor het verzenden van verdachte
bestanden te wijzigen. Zie Live Grid voor meer informatie.
Potentieel ongewenste toepassingen
De volgende stap in het installatieproces is het configureren van detectie van Mogelijk ongewenste toepassingen.
Dergelijke programma's zijn niet per se schadelijk, maar kunnen het gedrag van het besturingssysteem vaak
negatief beïnvloeden. Deze toepassingen worden vaak meegeleverd met andere programma's en vallen nauwelijks
op tijdens de installatie. Hoewel bij deze toepassingen gewoonlijk een melding wordt weergegeven tijdens de
installatie, kunnen ze eenvoudig zonder uw toestemming worden geïnstalleerd.
Firewall
Selecteer een filtermodus voor de firewall. Zie Filtermodi voor meer informatie.
Bestanden voor installatie op afstand
In de laatste stap van de installatiewizard selecteert u een doelmap voor het installatiepakket
(esets_remote_Install.pkg), het shellscript voor installatie (esets_setup.sh) en het shellscript voor verwijdering
(esets_remote_UnInstall.sh).
11
12
39
29

12
3.3.2 Installatie op afstand op doelcomputers
ESET Endpoint Security kan worden geïnstalleerd op doelcomputers met Apple Remote Desktop of een ander
hulpmiddel dat de installatie van standaard macOS-pakketten (.pkg) ondersteunt door de bestanden te kopiëren en
shellscripts op doelcomputers uit te voeren.
ESET Endpoint Security installeren met Apple Remote Desktop:
1. Klik op het pictogram Kopiëren in Apple Remote Desktop.
2. Kl ik op +, navigeer naar de shellscript voor installatie (esets_setup.sh) en selecteer dit.
3. Selecteer /tmp in het vervolgkeuzemenu Place items in en klik op Copy.
4. Kl ik op Install om het pakket naar de doelcomputers te verzenden.
Voor gedetailleerde instructies over het beheer van clientcomputers met ESET Remote Administrator verwijzen wij
u naar de onlinedocumentatie voor ESET Remote Administrator.
3.3.3 Verwijdering op afstand
Ga als volgt te werk om ESET Endpoint Security te verwijderen van clientcomputers:
1. Met de opdracht Items kopiëren in Apple Remote Desktop zoekt u het shellscript voor verwijdering
(esets_remote_unInstall.sh - samen met het installatiepakket gemaakt) en kopieert u het shellscript naar de
map /tmp op de doelcomputers (bijvoorbeeld /tmp/esets_remote_uninstall.sh).
2. Selecteer Gebruiker onder Opdracht uitvoeren als en typ vervolgens root in het veld Gebruiker.
3. Kl ik op Verzenden. Nadat de verwijdering is voltooid, wordt een consolelogbestand weergegeven.
3.3.4 Upgrade op afstand
Gebruik de opdracht Install packages in Apple Remote Desktop om de nieuwste versie van ESET Endpoint Security te
installeren wanneer er een nieuwe versie beschikbaar wordt gesteld.

13
4. Productactivering
Nadat de installatie is voltooid, wordt u gevraagd uw product te activeren. Er zijn meerdere activeringsmethoden
die u kunt gebruiken. De beschikbaarheid van een bepaalde activeringsmethode kan per land verschillen en is
afhankelijk van de distributiemethode (cd/dvd, ESET-website, enzovoort).
Als u uw exemplaar van ESET Endpoint Security rechtstreeks vanuit het programma wilt activeren, klikt u op het
pictogram ESET Endpoint Security op de macOS-menubalk (boven aan het scherm) en klikt u op
Productactivering. U kunt uw product ook vanuit het hoofdmenu activeren onder Help > Licentie beheren of
Beveiligingsstatus > Productlicentie activeren.
U kunt ESET Endpoint Security op een van de volgende manieren activeren:
· Activeren met licentiecode: een unieke tekenreeks in de indeling XXXX-XXXX-XXXX-XXXX-XXXX, die wordt
gebruik ter identificatie van de licentiehouder en voor de activering van de licentie. U vindt uw licentiecode in
het e-mailbericht dat u na aankoop hebt ontvangen of op de licentiekaart in de doos.
· Beveiligingsbeheerder: een account dat met referenties (e-mailadres en wachtwoord) op de licentiebeheerportal
van ESET wordt gemaakt. Met deze methode kunt u meerdere licenties tegelijk vanaf één locatie beheren.
· Offlinelicentie: een automatisch gegenereerd bestand dat wordt overgedragen naar het ESET-product om
licentie-informatie te verstrekken. Uw offlinelicentiebestand wordt gegeneerd op de portal ESET License
Administrator en wordt gebruikt in omgevingen waarin de toepassing geen verbinding met de licentieautoriteit
kan maken.
U kunt deze client ook later activeren als uw computer lid is van een beheerd netwerk en uw beheerder van plan is
uw product met ESET Remote Administrator te activeren.
OPMERKING: ESET Remote Administrator kan clientcomputers stilzwijgend activeren met licenties die de beheer
beschikbaar stelt.

14
ESET Endpoint Security versie 6.3.85.0 (of later) biedt u de mogelijkheid het product via Terminal te activeren. Geef
hiervoor de volgende opdracht op:
sudo ./esets_daemon --wait-respond --activate key=XXXX-XXXX-XXXX-XXXX-XXXX
Vervang XXXX-XXXX-XXXX-XXXX-XXXX door een licentiecode die al is gebruikt om ESET Endpoint Security te activeren
of dat is geregistreerd in ESET License Administrator. De opdracht retourneert de status "OK", of een fout als de
activering mislukt.

15
5. Verwijderen
Er zijn meerdere manieren om het verwijderingsprogramma voor ESET Endpoint Security te starten:
· plaats de installatie-CD/DVD van ESET Endpoint Security in uw computer, open deze vanaf het bureaublad of het
venster Finder en dubbelklik op Verwijderen
· open het ESET Endpoint Security-installatiebestand (.dmg) en dubbelklik op Verwijderen
· start Finder, open de map Programma's op de vaste schijf, houd Ctrl ingedrukt en klik op het pictogram ESET
Endpoint Security en selecteer de optie Toon pakketinhoud. Open de map Contents > Helpers en dubbelklik op
he t pi ctogram Uninstaller.

16
6. Basisoverzicht
Het hoofdvenster van ESET Endpoint Security is onderverdeeld in twee hoofdgedeelten. In het hoofdvenster aan de
rechterkant wordt informatie weergegeven over de optie die is geselecteerd in het hoofdmenu aan de linkerkant.
De volgende secties zijn bereikbaar vanuit het hoofdmenu:
· Beveiligingsstatus: hier vindt u informatie over de beveiligingsstatus van uw computer, firewall, web- en e-
mailbeveiliging.
· Computerscan: in dit gedeelte kunt u de Computerscan op aanvraag configureren en starten.
· Bijwerken: hier wordt informatie weergegeven over updates van de modules.
· Instellingen: selecteer deze sectie om het beveiligingsniveau van uw computer aan te passen.
· Hulpmiddelen: hier hebt u toegang tot Logbestanden , Planner , Quarantaine , Actieve processen en
andere functies van het programma.
· Help: hier hebt u toegang tot Help-bestanden, de kennisbank op internet, het aanvraagformulier voor
ondersteuning en aanvullende informatie over het programma.
6.1 Sneltoetsen
U kunt de volgende sneltoetsen gebruiken wanneer u met ESET Endpoint Security werkt:
· cmd+,: hiermee geeft u ESET Endpoint Security-voorkeuren weer,
· cmd+O: hiermee wijzigt u het formaat van het hoofdvenster van de gebruikersinterface van ESET Endpoint
Security in het standaardformaat en verplaatst u dit naar het midden van het scherm,
· cmd+Q: hiermee verbergt u het hoofdvenster van de gebruikersinterface van ESET Endpoint Security. U opent dit
door te klikken op het ESET Endpoint Security-pictogram op de macOS-menubalk (boven in het scherm),
· cmd+W: hiermee sluit u het hoofdvenster van de gebruikersinterface van ESET Endpoint Security.
De volgende sneltoetsen werken alleen als de optie Standaardmenu gebruiken is ingeschakeld onder Instellingen >
Voorkeuren voor toepassing opgeven... > Interface:
· cmd+alt+L: hiermee opent u het gedeelte Logbestanden,
· cmd+alt+S: hiermee opent u het gedeelte Planner,
· cmd+alt+Q: hiermee opent u het gedeelte Quarantaine.
21
35 37 40 42

17
6.2 Werking van het systeem controleren
Kl ik op Beveiligingsstatus in het hoofdmenu om uw beveiligingsstatus weer te geven. Er wordt een statusoverzicht
over de werking van ESET Endpoint Security-modules weergegeven in het hoofdvenster.
6.3 Te volgen procedure als het programma niet correct werkt
Als een module correct werkt, wordt er een groen vinkje weergegeven. Als een module niet correct werkt, wordt er
een rood uitroepteken of een oranje meldingspictogram weergegeven. Er wordt aanvullende informatie over de
module en een voorgestelde oplossing voor het probleem weergegeven in het hoofdvenster van het programma. U
kunt de status van afzonderlijke modules wijzigen door op de blauwe koppeling onder elk waarschuwingsbericht te
klikken.
Als u een probleem niet kunt oplossen met de voorgestelde oplossingen, kunt u een oplossing zoeken in de ESET-
knowledgebase of contact opnemen met de klantenservice van ESET. De klantenservice zal uw vragen zo spoedig
mogelijk beantwoorden en helpen met het vinden van een oplossing voor problemen met ESET Endpoint Security.

18
7. Computerbeveiliging
De computerconfiguratie is te vinden onder Instellingen > Computer. Hier wordt de status van Real-timebeveiliging
van bestandssysteem weergegeven. U kunt afzonderlijke modules uitschakelen door de betreffende module om te
schakelen naar UITGESCHAKELD. U moet zich wel realiseren dat het beveiligingsniveau van uw computer hierdoor
kan afnemen. Om toegang te krijgen tot gedetailleerde instellingen voor een module, klikt u op Instellingen.
7.1 Antivirus- en antispywarebeveiliging
Antivirusbeveiliging beschermt tegen schadelijke aanvallen op het systeem door mogelijk gevaarlijke bestanden te
wijzigen. Als een bedreiging via schadelijke code wordt gedetecteerd, kan de antivirusmodule deze onschadelijk
maken door de code eerst te blokkeren en deze vervolgens op te schonen, te verwijderen of in quarantaine te
plaatsen.
7.1.1 Algemeen
In het gedeelte Algemeen (Instellingen > Voorkeuren voor toepassing opgeven... > Algemeen) kunt u detectie van
de volgende soorten toepassingen inschakelen:
· Potentieel ongewenste toepassingen - deze toepassingen zijn niet niet per se schadelijk maar kunnen de
prestaties van uw computer aantasten. Voor de installatie van dergelijke toepassingen moet doorgaans expliciet
toestemming worden gegeven. Deze toepassingen veranderen de manier waarop uw computer werkt. De meest
ingrijpende wijzigingen omvatten ongewenste pop-upvensters, activering en uitvoering van verborgen
processen, toegenomen gebruik van systeembronnen, wijzigingen in zoekresultaten en programma's die
communiceren met externe servers.
· Potentieel onveilige toepassingen - deze toepassingen verwijzen naar commerciële, legitieme software die kan
worden misbruikt door aanvallers, als deze wordt geïnstalleerd zonder toestemming van de gebruiker. Deze
categorie omvat programma's zoals hulpmiddelen voor externe toegang. Dat is de reden waarom deze optie
standaard is uitgeschakeld.
· Verdachte toepassingen - deze toepassingen omvatten programma's die zijn gecomprimeerd met packers of
protectors. Deze soorten protectors worden vaak door malwareauteurs gebruikt om detectie te omzeilen. Een
packer is een zelfuitpakkend, uitvoerbaar bestand waarin verschillende soorten malware in één pakket zijn
verzameld. De meest gebruikte packers zijn UPX, PE_Compact, PKLite en ASPack. Dezelfde malware kan anders
worden gedetecteerd wanneer deze met een andere packer is gecomprimeerd. Packers kunnen hun
'handtekeningen' in de loop van de tijd doen veranderen, waardoor het moeilijker is malware te detecteren en te
verwijderen.
Voor het instellen van Uitsluitingen van het bestandssysteem of internet en e-mail klikt u op Instellen.
7.1.1.1 Uitsluitingen
In de sectie Uitsluitingen kunt u bepaalde bestanden en mappen, toepassingen of IP/IPv6-adressen opgeven die u
wilt uitsluiten van het scannen.
Bestanden en mappen die worden vermeld op het tabblad Bestandssysteem worden uitgesloten van alle scanners:
Opstarten, Real-time en On-demand (Computerscan).
· Pad: het pad naar uitgesloten bestanden en mappen.
· Bedreiging: als er naast een uitgesloten bestand de naam van een bedreiging wordt weergegeven, betekent dit
dat het bestand alleen wordt uitgesloten voor de betreffende bedreiging, maar niet volledig. Als het bestand
later wordt geïnfecteerd door andere malware, wordt het bestand gedetecteerd door de antivirusmodule.
· : hiermee wordt een nieuwe uitsluiting gemaakt. Voer het pad in naar een object (u kunt ook de jokertekens *
en ? gebruiken) of selecteer de map of het bestand in de boomstructuur.
· - hiermee worden geselecteerde vermeldingen verwijderd
· Standaard: hiermee worden alle uitsluitingen geannuleerd
Op het tabblad Web en e-mail kunt u bepaalde Toepassingen of IP/IPv6-adressen uitsluiten van protocolscannen.
18

19
7.1.2 Beveiliging bij het opstarten
Met Opstartbestanden controleren worden bestanden automatisch gescand bij het opstarten van het systeem. Deze
scan wordt standaard regelmatig als een geplande taak uitgevoerd nadat de gebruiker zich heeft aangemeld of na
een update van de modules. Voor het wijzigen van de parameterinstellingen voor de ThreatSense-engine die van
toepassing zijn op het scannen bij het opstarten, klikt u op Instellingen. Meer informatie over het instellen van de
ThreatSense-engine vindt u in dit gedeelte .
7.1.3 Real-timebeveiliging van bestandssysteem
De real-timebeveiliging van het bestandssysteem controleert alle typen media en activeert de scan op basis van
diverse gebeurtenissen. Real-timebeveiliging van het bestandssysteem door ThreatSense-technologie (beschreven
in Parameters voor ThreatSense-engine instellen ) kan voor nieuw gemaakte bestanden anders zijn dan voor
reeds bestaande bestanden. Nieuwe bestanden kunnen nauwkeuriger worden beheerd.
Standaard worden alle bestanden gescand op het moment dat ze worden geopend, gemaakt of uitgevoerd. U wordt
aangeraden deze standaardinstellingen te behouden, omdat deze het hoogste niveau van real-timebeveiliging voor
uw computer bieden. Real-timebeveiliging wordt gestart bij het opstarten van het systeem en scant
ononderbroken. In speciale gevallen (zoals bij een conflict met een andere real-timescanner) kan de real-
timebeveiliging worden beëindigd door op de menubalk (boven aan het scherm) op het pictogram ESET Endpoint
Security te klikken (boven aan het scherm. Selecteer daarna Real-timebeveiliging van bestandssysteem
uitschakelen. U kunt de real-timebeveiliging van bestanden ook in het hoofdvenster van het programma
uitschakelen (klik op Instellen > Computer en zet Real-timebeveiliging van bestandsysteem op UITGESCHAKELD).
De volgende mediatypen kunnen worden uitgesloten bij de scanner voor Real-time:
· Lokale stations: systeemschijven
· Verwisselbare media: cd's/dvd's, USB-media, Bluetooth-apparaten, enz.
· Netwerkmedia: alle gekoppelde stations
Het wordt aangeraden de standaardinstellingen te gebruiken en scanuitsluitingen alleen in specifieke gevallen te
wijzigen, bijvoorbeeld wanneer het scannen van bepaalde media tot aanzienlijke vertragingen in de
gegevensoverdracht leidt.
Als u geavanceerde instellingen voor Real-timebeveiliging van bestandssysteem wilt wijzigen, gaat u naar
Instellingen > Voorkeuren voor toepassing opgeven... (of druk op cmd+, > Real-timebeveiliging en klik op
Instellen... naast Geavanceerde opties (be schre ven i n Geavanceerde scanopties ).
7.1.3.1 Geavanceerde opties
In dit venster kunt u definiëren welke objecttypen door de ThreatSense-engine worden gescand. Voor meer
i nformatie over Zelfuitpakkende archieven, Software voor runtime-compressie en Geavanceerde heuristiek,
verwijzen wij u naar Parameters voor ThreatSense-engine instellen .
We raden niet aan wijzigingen aan te brengen in het gedeelte Standaardarchiefinstellingen, tenzij u een specifiek
probleem wilt oplossen, aangezien hogere nestingsniveaus voor archieven de systeemprestaties negatief kunnen
beïnvloeden.
ThreatSense-parameters voor uitgevoerde bestanden: standaard wordt Geavanceerde heuristiek gebruikt wanneer
bestanden worden uitgevoerd. Wij raden ten zeerste aan Smart-optimalisatie en ESET Live Grid ingeschakeld te
laten om negatieve gevolgen voor de systeemprestaties te beperken.
Compatibiliteit van netwerkvolumes verhogen: met deze optie worden de prestaties verbeterd wanneer
bestanden via het netwerk worden geopend. Deze optie moet worden ingeschakeld als u met vertragingen te
maken krijgt wanneer bestanden op netwerkstations worden geopend. Deze functie maakt op OS X 10.10 en later
gebruik van de systeembestandcoördinator. Niet alle toepassingen ondersteunen de systeembestandcoördinator.
Microsoft Word 2011 bijvoorbeeld ondersteunt deze functie niet en Word 2016 wel.
23
23
19
24

20
7.1.3.2 Wanneer moet de configuratie voor real-timebeveiliging worden gewijzigd?
Real-timebeveiliging vormt het meest essentiële onderdeel van het onderhouden van een veilig systeem. Wees
voorzichtig bij het aanpassen van de parameters voor real-timebeveiliging. Wij adviseren u deze parameters alleen
te wijzigen in specifieke situaties. Als er bijvoorbeeld een conflict is met een bepaalde toepassing of real-
timescanner van een ander antivirusprogramma.
Na installatie van ESET Endpoint Security zijn alle instellingen geoptimaliseerd om gebruikers een zo hoog mogelijk
niveau van systeembeveiliging te bieden. U kunt de standaardinstellingen herstellen door op de knop Standaard in
de linkerbenedenhoek van het venster Real-timebeveiliging (Instellingen > Voorkeuren voor toepassing opgeven...
> Real-timebeveiliging).
7.1.3.3 Real-timebeveiliging controleren
Om te controleren of Real-timebeveiliging actief is en virussen detecteert, kunt u het testbestand eicar.com
gebruiken. Dit testbestand is een speciaal, onschadelijk bestand dat door alle virusprogramma's kan worden
gedetecteerd. Het bestand is gemaakt door EICAR (European Institute for Computer Antivirus Research) om de
werking van antivirusprogramma's te testen.
U kunt de status van de Real-timebeveiliging controleren zonder ESET Remote Administrator te gebruiken. Maak
hiervoor op afstand verbinding met de clientcomputer met gebruik van Terminal en geef de volgende opdracht:
/Applications/.esets/Contents/MacOS/esets_daemon --status
De status van de Real-timescanner wordt weergegeven als RTPStatus=Enabled of RTPStatus=Disabled.
De uitvoer van de Terminal bevat onder andere de volgende statussen:
· de versie van de ESET Endpoint Security die is geïnstalleerd op de clientcomputer
· datum en versie van de detectie-engine
· pad naar de updateserver
OPMERKING: gebruik van het Terminal-hulpprogramma wordt alleen aanbevolen voor geavanceerde gebruikers.
7.1.3.4 Te volgen procedure als real-timebeveiliging niet werkt
In dit hoofdstuk worden probleemsituaties beschreven die zich kunnen voordoen bij het gebruik van real-time
beveiliging, en oplossingen hiervoor.
Real-timebeveiliging is uitgeschakeld
Als real-timebeveiliging per ongeluk is uitgeschakeld door de gebruiker, moet deze opnieuw worden geactiveerd. U
kunt real-timebeveiliging opnieuw activeren door in het hoofdmenu naar Instellingen > Computer te gaan en Real-
time beveiliging van het bestandssysteem over te schakelen naar INGESCHAKELD. U kunt de real-timebeveiliging
van het bestandssysteem ook inschakelen in het venster met voorkeuren voor de toepassing onder Real-time
beveiliging door Real-timebeveiliging van bestandssysteem inschakelen te selecteren.
Real-time beveiliging voert geen detecties uit en schoont geen infiltraties op
Controleer of er geen andere antivirusprogramma's zijn geïnstalleerd op de computer. Als twee programma's voor
real-timebeveiliging tegelijk zijn geactiveerd, conflicteren deze mogelijk. Wij adviseren u alle eventuele andere
antivirusprogramma's van uw systeem te verwijderen.
Real-timebeveiliging wordt niet gestart
Als real-timebeveiliging niet wordt geactiveerd wanneer u het systeem opstart, zijn er mogelijk conflicten met
andere programma's. Als u op een probleem stuit, neemt u contact op met de klantenservice van ESET.

21
7.1.4 On-demand computerscan
Als u vermoedt dat de computer is geïnfecteerd (deze gedraagt zich abnormaal), voert u Smart scan uit om uw
computer te onderzoeken op infiltraties. Voor een optimale beveiliging is het van belang regelmatig een
computerscan uit te voeren als onderdeel van routinematige beveiligingsmaatregelen, en niet alleen wanneer u
vermoedt dat de computer is geïnfecteerd. Door regelmatig te scannen kunnen infiltraties worden gedetecteerd
die niet door de real-timescanner zijn gedetecteerd op het moment van opslag op de schijf. Dit kan gebeuren als de
real-timescanner was uitgeschakeld op het moment van infectie of als de modules verouderd waren.
Wij adviseren u minimaal eenmaal per maand een on-demand scan uit te voeren. Scannen kan worden
geconfigureerd als een geplande taak in Hulpmiddelen > Planner.
Ook kunt u geselecteerde bestanden en mappen vanaf uw bureaublad of vanuit het venster Finder slepen en
neerzetten in het hoofdvenster van ESET Endpoint Security, het dock-pictogram, het menubalkpictogram (boven
aan het scherm) of het pictogram van de toepassing (in de map /Applications).
7.1.4.1 Type scan
Er zijn twee typen on-demand computerscan beschikbaar. Gebruik een Smart scan om het systeem snel zonder
verdere configuratie van de scanparameters te scannen. Met een Aangepaste scan kunt u elk van de vooraf
gedefinieerde scanprofielen selecteren en specifieke scandoelen opgeven.
7.1.4.1.1 Smart scan
Met Smart scan kunt u snel een computerscan starten en geïnfecteerde bestanden opschonen zonder dat er
gebruikersinterventie is vereist. Het belangrijkste voordeel is de eenvoudige werking zonder gedetailleerde
scanconfiguratie. Smart scan controleert alle bestanden in alle mappen en schoont automatisch gedetecteerde
infiltraties op of verwijdert deze. Het opschoonniveau wordt automatisch ingesteld op de standaardwaarde. Zie
Opschonen voor meer informatie over typen opschoonbewerkingen.
24

22
7.1.4.1.2 Aangepaste scan
Met Aangepaste scan kunt u scanparameters opgeven, zoals scandoelen en scanmethoden. Het voordeel van het
uitvoeren van een aangepaste scan is de mogelijkheid om de scanparameters in detail te configureren.
Verschillende configuraties kunnen worden opgeslagen in door de gebruiker gedefinieerde scanprofielen. Deze
profielen zijn met name handig als het scannen herhaaldelijk plaatsvindt met dezelfde parameters.
Als u scandoelen wilt selecteren, selecteert u Computerscan > Aangepaste scan en selecteert u vervolgens
specifieke Scandoelen in de boomstructuur. Een scandoel kan tevens nader worden gespecificeerd door het pad
naar de map met het bestand of de bestanden die u wilt opnemen in te voeren. Als u alleen het systeem wilt
scannen zonder aanvullende opschoonacties, selecteer dan Scannen zonder opschonen. Bovendien kunt u een
keuze maken uit drie opschoonniveaus door op Instellen... > Opschonen te klikken.
OPMERKING: Het uitvoeren van computerscans met Aangepaste scan wordt alleen aanbevolen voor ervaren
gebruikers die eerder antivirusprogramma's hebben gebruikt.
7.1.4.2 Scandoelen
In de boomstructuur met scandoelen kunt u bestanden en mappen selecteren de u op virussen wilt scannen.
Mappen kunnen ook worden geselecteerd aan de hand van de instellingen van een profiel.
Een scandoel kan nader worden gespecificeerd door het pad naar de map met het bestand of de bestanden die u
wilt opnemen in de scan in te voeren. Selecteer doelen uit de boomstructuur met alle mappen die beschikbaar zijn
op de computer. Schakel het selectievakje in voor het betreffende bestand of de betreffende map.
7.1.4.3 Scanprofielen
U kunt uw voorkeursinstellingen voor scannen opslaan voor toekomstige scans. Wij adviseren u voor elke
regelmatig gebruikte scan een ander profiel te maken (met verschillende scandoelen, scanmethoden en andere
parameters).
Als u een nieuw profiel wilt maken, klik dan in het hoofdmenu op Instellingen > Voorkeuren voor toepassing
opgeven... (of druk op cmd+,) > Computerscan en klik op Bewerken naast de lijst met huidige profielen.
Raadpleeg het gedeelte Parameters voor ThreatSense-engine instellen voor een beschrijving van elke
parameter van de scaninstellingen, zodat u een scanprofiel kunt maken dat aan uw behoeften voldoet.
Voorbeeld: Stel, u wilt een eigen scanprofiel maken en de Smart scan-configuratie is deels geschikt, maar u wilt
geen programma's voor runtime-compressie of potentieel onveilige toepassingen scannen en u wilt ook Volledig
23

23
opschonen toepassen. Typ de profielnaam in het venster Profielenlijst voor on-demand scanner, klik op Toevoegen
en bevestig vervolgens uw keuze met OK. Pas de parameters aan uw vereisten aan met de instellingen voor
ThreatSense-engine en Scandoelen.
Als u het besturingssysteem wilt uitschakelen en de computer wilt afsluiten na de on-demand scan, gebruikt u de
optie Computer uitschakelen na de scan.
7.1.5 Parameters voor ThreatSense-engine instellen
ThreatSense is een exclusieve technologie van ESET die bestaat uit een combinatie van complexe methoden voor
de detectie van dreigingen. Deze technologie is proactief. Dit betekent dat tevens beveiliging wordt geboden
tijdens de eerste uren van de verspreiding van een nieuwe bedreiging. Er wordt gebruik gemaakt van een
combinatie van verschillende methoden (codeanalyse, code-emulatie, generieke kenmerken enz.) die
samenwerken om de systeembeveiliging aanzienlijk te verbeteren. De scanengine is in staat verschillende
gegevensstromen tegelijk te controleren voor maximale efficiëntie en een zo hoog mogelijk detectiepercentage.
De ThreatSense-technologie voorkomt tevens de installatie van rootkits.
Via de instellingsopties voor ThreatSense-technologie kunt u verschillende scanparameters opgeven:
· Bestandstypen en extensies die moeten worden gescand
· De combinatie van verschillende detectiemethoden
· Opschoonniveaus, enz.
U kunt het instellingenvenster openen door te klikken op Instellingen > Voorkeuren voor toepassing opgeven... (of
druk op cmd+,) en klik vervolgens op de knop ThreatSense Engine instellen in de modules Systeembeveiliging,
Real-timebeveiliging en Computerscan, die allemaal gebruikmaken van de ThreatSense-technologie (zie
hieronder). Verschillende beveiligingsscenario's vereisen mogelijk verschillende configuraties. ThreatSense is
individueel configureerbaar voor de volgende beveiligingsmodules:
· Beveiliging bij het opstarten - Automatisch bestanden controleren bij het opstarten
· Real-timebeveiliging - Real-timebeveiliging van bestandssysteem
· Computerscan: on-demand computerscan
· Beveiliging van webtoegang
· E-mailbeveiliging
De ThreatSense-parameters zijn speciaal geoptimaliseerd voor elke module en wijziging hiervan kan een
aanzienlijke invloed hebben op de werking van het systeem. Als bijvoorbeeld instellingen voor het altijd scannen
van programma's voor runtime-compressie worden gewijzigd of als geavanceerde heuristiek wordt ingeschakeld in
de module voor real-timebeveiliging van het bestandssysteem, zou dit kunnen resulteren in een vertraging van het
systeem. Daarom adviseren wij de standaard ThreatSense-parameters ongewijzigd te laten voor alle modules met
uitzondering van Computerscan.

24
7.1.5.1 Objecten
In het gedeelte Objecten kunt u definiëren welke bestanden worden gescand op infiltraties.
· Symbolische koppelingen - (alleen computerscan) scant bestandstypen die een tekenreeks bevatten die wordt
geïnterpreteerd en gevolgd als een pad naar een ander bestand of een andere map.
· E-mailbestanden - (niet beschikbaar in real-timebeveiliging) scant e-mailbestanden.
· Postvakken - (niet beschikbaar in real-timebeveiliging) scant postvakken van gebruikers in het systeem. Onjuist
gebruik van deze optie kan leiden tot een conflict met uw e-mailclient. Meer informatie over de voor- en nadelen
van deze optie vindt u in dit knowledgebase-artikel.
· Archieven - (niet beschikbaar in real-timebeveiliging) scant bestanden die zijn gecomprimeerd in archieven (RAR,
ZIP, ARJ, TAR, enz.).
· Zelfuitpakkende archieven - (niet beschikbaar in real-timebeveiliging) scant bestanden die deel uitmaken van
zelfuitpakkende archiefbestanden.
· Software voor runtime-compressie - programma's voor runtime-compressie decomprimeren in het geheugen (in
tegenstelling tot standaardarchieftypen). Als dit is geselecteerd, worden standaardprogramma's voor statische
compressie (zoals UPX, yoda, ASPack, FGS) ook gescand.
7.1.5.2 Opties
In het gedeelte Opties kunt u de methoden selecteren die moeten worden gebruikt tijdens het scannen van het
systeem. De volgende opties zijn beschikbaar:
· Heuristiek: heuristiek maakt gebruik van een algoritme dat de (schadelijke) activiteit van programma's analyseert.
Het voornaamste voordeel van heuristieke detectie is de mogelijkheid om nieuwe schadelijke software te
detecteren die eerder nog niet bestond.
· Geavanceerde heuristiek: geavanceerde heuristiek bestaat uit een uniek heuristisch algoritme dat door ESET is
ontwikkeld en dat is geoptimaliseerd voor het detecteren van computerwormen en trojaanse paarden. Dit
algoritme is geschreven in programmeertalen van hoog niveau. De geavanceerde heuristiek breidt de
detectiemogelijkheden van het programma aanzienlijk uit.
7.1.5.3 Opschonen
De instellingen voor het opschonen bepalen op welke manier de scanner geïnfecteerde bestanden opschoont. Er
zijn 3 opschoonniveaus:
· Niet opschonen - geïnfecteerde bestanden worden niet automatisch opgeschoond. Er wordt een
waarschuwingsvenster weergegeven en u kunt een actie kiezen.
· Standaard opschonen - hiermee wordt automatisch geprobeerd een geïnfecteerd bestand op te schonen of te
verwijderen. Als het niet mogelijk is de juiste actie automatisch te selecteren, wordt een selectie van
vervolgacties aangeboden. De beschikbare vervolgacties worden tevens weergegeven als een vooraf
gedefinieerde actie niet kan worden voltooid.
· Volledig opschonen - alle geïnfecteerde bestanden (inclusief archieven) worden opgeschoond of verwijderd. De
enige uitzonderingen zijn systeembestanden. Als het niet mogelijk is een bestand op te schonen, ontvangt u een
melding en wordt u gevraagd een type actie te selecteren.
Waarschuwing: in de standaardmodus voor opschonen wordt het hele archiefbestand alleen verwijderd als alle
bestanden in het archief geïnfecteerd zijn. Als een archief legitieme bestanden bevat evenals geïnfecteerde
bestanden, wordt het niet verwijderd. Als een geïnfecteerd archiefbestand wordt gedetecteerd in de modus
Volledig opschonen, wordt het hele archief verwijderd, zelfs als er schone bestanden aanwezig zijn.

25
7.1.5.4 Uitsluitingen
Een extensie maakt deel uit van een bestandsnaam en wordt afgebakend door een punt. De extensie definieert het
type en de inhoud van een bestand. In dit gedeelte van Parameters voor ThreatSense-instellen kunt u de typen
bestanden definiëren die u van scannen wilt uitsluiten.
Standaard worden alle bestanden gescand, ongeacht hun extensie. Elke extensie kan worden toegevoegd aan de
lijst met bestanden die zijn uitgesloten van scannen. Met de knoppen en kunt u het scannen van specifieke
extensies inschakelen of verbieden.
Het uitsluiten van bestanden van het scannen is soms nodig als het scannen van bepaalde bestandstypen het
functioneren van het programma belemmert. Het kan bijvoorbeeld raadzaam zijn log-, cfg- e n tmp-bestanden uit te
sluiten. De juiste notatie voor het invoeren van bestandextensies is:
log
cfg
tmp
7.1.5.5 Limiet
Gebruik de sectie Limiet om de maximale grootte op te geven van objecten die moeten worden gescand, evenals
het maximale niveau voor het scannen van geneste archieven:
· Maximumgrootte:de maximale grootte van objecten die moeten worden gescand. De antivirusmodule scant
alleen objecten die kleiner zijn dan de opgegeven grootte. Het is in de meeste gevallen niet nodig de
standaardwaarde te wijzigen. De waarde mag alleen worden gewijzigd door gevorderde gebruikers die een
specifieke reden hebben om grotere objecten niet te scannen.
· Maximumscantijd:de maximale tijd voor het scannen van een object. Als hier een waarde is ingevoerd, wordt het
scannen van een object beëindigd wanneer die tijd is verstreken, ongeacht of de scan is voltooid.
· Maximumnestingsniveau:het maximum aantal niveaus waarop archieven moeten worden gescand. Het is in de
meeste gevallen niet nodig de standaardwaarde van 10 te wijzigen. Als het scannen voortijdig wordt afgebroken
omdat archieven dieper dan 10 niveaus zijn genest, worden archieven op lagere niveaus niet gecontroleerd.
· Maximumbestandsgrootte: Gebruik deze optie om de maximale bestandsgrootte op te geven voor bestanden in
archieven (als deze worden uitgepakt) die moeten worden gescand. Als het scannen van een archief vanwege
deze limiet voortijdig wordt afgebroken, blijft het archief ongecontroleerd.
7.1.5.6 Overige
Smart-optimalisatie inschakelen
Wanneer Smart-optimalisatie is ingeschakeld, worden de instellingen geoptimaliseerd om het meest efficiënte
scanniveau te garanderen, zonder dat dit ten koste gaat van de scansnelheid. De diverse beveiligingsmodules
scannen op intelligente wijze, waarbij gebruik wordt gemaakt van verschillende scanmethoden. De Smart-
optimalisatie is niet onveranderbaar vastgelegd in het product. Het ontwikkelingsteam van ESET implementeert
continu nieuwe wijzigingen, die vervolgens via de regelmatige updates worden geïntegreerd in ESET Endpoint
Security. Als de Smart-optimalisatie is uitgeschakeld, worden alleen de door de gebruiker gedefinieerde
instellingen in de ThreatSense-kern van de betreffende module toegepast bij het uitvoeren van een scan.
Alternatieve gegevensstromen scannen (alleen on-demand scanner)
Alternatieve gegevensstromen (resource/gegevensvorken) die worden gebruikt door het bestandssysteem zijn
bestands- en mapkoppelingen die onzichtbaar zijn voor normale scantechnieken. Veel infiltraties proberen
detectie te vermijden door zichzelf te vermommen als alternatieve gegevensstromen.

26
7.1.6 Er is een infiltratie gedetecteerd
Infiltraties kunnen het systeem via verschillende toegangspunten bereiken: webpagina's, gedeelde mappen, e-mail
of verwisselbare computermedia (USB, externe schijven, cd's, dvd's enz.).
Als de computer tekenen van infectie door malware vertoont, bijvoorbeeld als deze trager is, vaak vastloopt, enz.,
adviseren wij u het volgende te doen:
1. Kl ik op Computerscan.
2. Kl ik op Smart scan (zie de sectie Smart scan voor meer informatie).
3. Nadat de scan is voltooid, controleert u in het logbestand het aantal gescande, geïnfecteerde en opgeschoonde
bestanden.
Als u alleen een bepaald gedeelte van uw schijf wilt scannen, klik dan op Aangepaste scan en selecteer de doelen
die u wilt scannen op malware.
Als algemeen voorbeeld van hoe infiltraties worden afgehandeld door ESET Endpoint Security, gaan we ervan uit
dat een infiltratie is gedetecteerd door de real-timebewaking van het bestandssysteem, welke gebruikmaakt van
het standaardopschoonniveau. De real-timebewaking probeert het bestand op te schonen of te verwijderen. Als er
geen vooraf gedefinieerde actie beschikbaar is voor de module voor real-timebeveiliging, wordt u via een
waarschuwingsvenster gevraagd om een optie te selecteren. Gewoonlijk zijn de opties Opschonen, Verwijderen en
Geen actie beschikbaar. Het wordt niet aanbevolen Geen actie te selecteren, aangezien de geïnfecteerde
bestanden dan geïnfecteerd zouden blijven. Deze optie is bedoeld voor situaties waarin u zeker weet dat het
bestand onschadelijk is en per ongeluk is gedetecteerd.
Opschonen en verwijderen - pas opschonen toe als een bestand is aangevallen door een virus dat schadelijke code
aan het bestand heeft toegevoegd. Als dit het geval is, probeert u eerst het geïnfecteerde bestand op te schonen
zodat het in de oorspronkelijke staat kan worden hersteld. Als het bestand uitsluitend uit schadelijke code bestaat,
wordt het verwijderd.
Bestanden in archieven verwijderen - in de modus Standaard opschonen wordt het volledige archief alleen
verwijderd als dit uitsluitend geïnfecteerde en geen schone bestanden bevat. Met andere woorden, archieven
worden niet verwijderd als zij ook onschadelijke, schone bestanden bevatten. Wees voorzichtig bij het gebruik van
een scan in de modus Volledig opschonen: met Volledig opschonen wordt het archief verwijderd als het minimaal
één geïnfecteerd bestand bevat, ongeacht de status van andere bestanden in het archief.
7.2 Web- en e-mailbeveiliging
Kl ik op Instellingen > Web en e-mail om toegang te krijgen tot Web- en e-mailbeveiliging in het hoofdvenster. Van
hieruit hebt u ook toegang tot de gedetailleerde instellingen voor elke module door te klikken op Instellen.
· Beveiliging van webtoegang: bewaakt HTTP-communicatie tussen webbrowsers en externe servers.
· Beveiliging van e-mailclient: biedt controle van e-mailcommunicatie die wordt ontvangen via het POP3- en IMAP-
protocol.
· Antiphishing-beveiliging: blokkeert potentiële phishingaanvallen van websites of domeinen die in de ESET-
database met malware staan.
· Webbeheer: blokkeert webpagina's die mogelijk ongepast of schadelijk materiaal bevatten.
21

27
7.2.1 Beveiliging van webtoegang
Beveiliging van webtoegang controleert communicatie tussen webbrowsers en externe servers op naleving van
HTTP-regels (Hypertext Transfer Protocol).
Webfiltering kan worden gerealiseerd door de poortnummers voor HTTP-communicatie en/of URL-adressen
te definiëren.
7.2.1.1 Poorten
Op het tabblad Poorten kunt u de poortnummers definiëren die worden gebruikt voor HTTP-communicatie.
Standaard zijn de poortnummers 80, 8080 en 3128 vooraf gedefinieerd.
7.2.1.2 URL-lijsten
In het gedeelte URL-lijsten kunt u HTTP-adressen opgeven die u wilt blokkeren, toestaan of uitsluiten van controle.
Websites in de lijst met geblokkeerde adressen zijn niet toegankelijk. Websites in de lijst met uitgesloten adressen
zijn toegankelijk zonder te worden gescand op schadelijke code.
Als u alleen toegang wilt toestaan tot URL's in de lijst Toegestane URL, selecteert u Niet-toegankelijke URL-
adressen.
Als u een lijst wilt activeren, selecteert u Ingeschakeld naast de lijstnaam. Als u een melding wilt krijgen wanneer u
een adres invoert van de huidige lijst, selecteert u Op de hoogte gesteld.
U kunt de speciale tekens * ( sterretje ) e n ? (vraagteken) gebruiken als u URL-lijsten samenstelt. Het sterretje
vervangt een willekeurige tekenreeks en het vraagteken een willekeurig teken. Wees voorzichtig met het opgeven
van uitgesloten adressen. De lijst mag alleen vertrouwde en veilige adressen bevatten. Evenzo is het noodzakelijk
ervoor te zorgen dat de tekens * en ? op de juiste wijze worden gebruikt in de lijst.
7.2.2 E-mailbeveiliging
E-mailbeveiliging biedt controle van e-mailcommunicatie die wordt ontvangen via het POP3- en IMAP-protocol. Bij
het onderzoeken van binnenkomende berichten maakt het programma gebruik van alle geavanceerde
scanmethoden van de ThreatSense-scanengine. Het scannen van de communicatie via het POP3- en IMAP-protocol
gebeurt onafhankelijk van de gebruikte e-mailclient.
ThreatSense-engine: Instellingen: via de geavanceerde instellingen van de virusscanner kunt u scandoelen,
detectiemethoden enz. configureren. Klik op Instellingen om het venster met gedetailleerde scaninstellingen weer
te geven.
Bericht toevoegen aan e-mailvoetnoot: nadat een e-mail is gescand, kan een melding met de scanresultaten aan
het bericht worden toegevoegd. U kunt niet zonder meer op de berichten vertrouwen, aangezien ze kunnen
worden weggelaten in problematische HTML-berichten of door sommige virussen kunnen worden vervalst. De
volgende opties zijn beschikbaar:
· Nooit: er worden geen tagberichten toegevoegd
· Alleen geïnfecteerde e-mail: alleen berichten met schadelijke code worden gemarkeerd als gecontroleerd
· Naar alle gescande e-mail: er worden meldingen toegevoegd aan alle gescande e-mail
Opmerking toevoegen aan het onderwerp van ontvangen en gelezen geïnfecteerde e-mail: schakel dit
selectievakje in als u een viruswaarschuwing aan het onderwerp van geïnfecteerde e-mail wilt toevoegen. Met
deze functie kunt u eenvoudig filteren op geїnfecteerde e-mail. Het schept ook meer vertrouwen bij de ontvanger,
en als een infiltratie wordt gedetecteerd beschikt u hiermee over waardevolle informatie over het risiconiveau van
een bepaalde e-mail of afzender.
Sjabloon toegevoegd aan het onderwerp van geïnfecteerde e-mail: u kunt deze sjabloon bewerken als u de indeling
van het onderwerpvoorvoegsel van een geїnfecteerde e-mail wilt wijzigen.
27 27

28
In het onderste gedeelte van dit venster kunt u ook de controle van e-mailcommunicatie in/uitschakelen die wordt
ontvangen via het POP3- en IMAP-protocol. Zie de volgende onderwerpen voor meer informatie hierover:
· POP3-protocolcontrole
· IMAP-protocolcontrole
7.2.2.1 POP3-protocolcontrole
Het POP3-protocol is het meest gebruikte protocol voor het ontvangen van e-mailcommunicatie in een e-
mailclienttoepassing. ESET Endpoint Security biedt beveiliging voor dit protocol, ongeacht welke e-mailclient wordt
gebruikt.
De beveiligingsmodule die deze controle biedt wordt automatisch gestart wanneer het systeem wordt opgestart en
is vervolgens actief in het geheugen. Zorg ervoor dat de module is ingeschakeld voor protocolfiltering, anders werkt
de module niet correct. POP3-protocolcontrole wordt automatisch uitgevoerd. U hoeft uw e-mailclient niet te
configureren. Standaard wordt alle communicatie via poort 110 gescand, maar u kunt indien nodig andere
communicatiepoorten toevoegen. Poortnummers moeten worden gescheiden door een komma.
Als de optie POP3-protocolcontrole inschakelen is ingeschakeld, wordt al het POP3-verkeer gecontroleerd op
schadelijke software.
7.2.2.2 IMAP-protocolcontrole
Het Internet Message Access Protocol (IMAP) is een ander e-mailprotocol voor het ophalen van e-mail. IMAP heeft
enkele voordelen ten opzichte van POP3. Er kunnen bijvoorbeeld meerdere clients gelijktijdig verbinding maken
met hetzelfde postvak, waarbij de informatie over de berichtstatus (gelezen, beantwoord, verwijderd, enzovoort)
behouden blijft. ESET Endpoint Security biedt beveiliging voor dit protocol, ongeacht welke e-mailclient wordt
gebruikt.
De beveiligingsmodule die deze controle biedt wordt automatisch gestart wanneer het systeem wordt opgestart en
is vervolgens actief in het geheugen. Zorg ervoor dat IMAP-protocolcontrole is ingeschakeld, anders werkt de
module niet correct. IMAP-protocolcontrole wordt automatisch uitgevoerd. U hoeft uw e-mailclient niet te
configureren. Standaard wordt alle communicatie via poort 143 gescand, maar u kunt indien nodig andere
communicatiepoorten toevoegen. Poortnummers moeten worden gescheiden door een komma.
Als de optie IMAP-protocolcontrole inschakelen is ingeschakeld, wordt al het IMAP-verkeer gecontroleerd op
schadelijke software.
7.3 Antiphishing
De te rm phishing definieert een criminele activiteit waarbij gebruik wordt gemaakt van social engineering (het
manipuleren van gebruikers om vertrouwelijke informatie te verkrijgen). Phishing wordt vaak gebruikt om toegang
te krijgen tot gevoelige gegevens zoals bankrekeningnummers, creditcardnummers, pincodes of gebruikersnamen
en wachtwoorden.
Wij raden u aan om Antiphishing ingeschakeld te laten (Instellingen > Voorkeuren voor toepassing opgeven... >
Antiphishing-beveiliging). Alle potentiële phishingaanvallen die afkomstig zijn van websites of domeinen die in de
ESET-malwaredatabase zijn opgenomen, worden geblokkeerd en er wordt een waarschuwing weergegeven die u op
de hoogte stelt van de aanval.
28
28

29
8. Firewall
De firewall beheert alle netwerkwerkverkeer naar en van het systeem door afzonderlijke netwerkverbindingen toe
te staan of the weigeren op basis van opgegeven filterregels. De firewall biedt bescherming tegen aanvallen van
externe computers en maakt het blokkeren van bepaalde services mogelijk. Hij biedt ook antivirusbeveiliging voor
de protocollen HTTP, POP3 en IMAP.
De firewallconfiguratie is te vinden in Instellingen > Firewall. Hier kunt u de filtermodus, regels en gedetailleerde
instellingen aanpassen. Daarnaast kunt u van hieruit toegang krijgen tot meer gedetailleerde instellingen van het
programma.
Al s u Alle netwerkverkeer blokkeren: verbinding met netwerk verbreken inschakelt, worden alle inkomende en
uitgaande communicatie door de firewall geblokkeerd. Gebruik deze optie alleen als u denkt dat er kritieke
beveiligingsrisico's zijn waarvoor de verbinding van het systeem met het netwerk moet worden verbroken.
8.1 Filtermodi
Er zijn drie filtermodi beschikbaar voor de firewall van ESET Endpoint Security. Instellingen voor filtermodi zijn te
vinden onder Instellingen > Voorkeuren voor toepassing opgeven... > Firewall. Het gedrag van de firewall verandert
op basis van de geselecteerde modus. Filtermodi zijn ook van invloed op de benodigde mate van
gebruikersinteractie.
Alle verkeer geblokkeerd: alle binnenkomende en uitgaande verbindingen worden geblokkeerd.
Automatisch met uitzonderingen: de standaardmodus. Deze modus is geschikt voor gebruikers die de voorkeur
geven aan eenvoudig en handig gebruik van de firewall, zonder regels te hoeven definiëren. De automatische
modus staat al het standaard uitgaande verkeer voor het opgegeven systeem toe en blokkeert alle niet-geïnitieerde
verbindingen die van de netwerkkant tot stand worden gebracht. U kunt ook aangepaste, door de gebruiker
gedefinieerde regels toevoegen.
Interactief: hiermee kunt u een aangepaste configuratie instellen voor uw firewall. Wanneer er communicatie
wordt gedetecteerd waarop geen bestaande regels van toepassing zijn, wordt er een dialoogvenster weergegeven
waarin een onbekende verbinding wordt gemeld. Het dialoogvenster biedt de gebruiker de mogelijkheid
communicatie toe te staan of te weigeren, en de hierbij genomen beslissing kan als nieuwe regel voor de firewall
worden onthouden. Als u ervoor kiest een nieuwe regel te maken, worden alle toekomstige verbindingen van dit
type toegestaan of geblokkeerd op basis van de regel.
Als u gedetailleerde informatie over alle geblokkeerde verbindingen wilt vastleggen in een logbestand, selecteer
dan Alle geblokkeerde verbindingen vastleggen in logboek. Als u de logboeken van de firewall wilt controleren, klik
dan in het hoofdmenu op Hulpmiddelen > Logboeken e n selecteer Firewall in het vervolgkeuzemenu Logboek.

30
8.2 Firewallregels
Regels vertegenwoordigen een reeks condities die worden gebruikt om alle netwerkverbindingen te testen en alle
acties te bepalen die zijn toegewezen aan deze condities. Met de firewallregels kunt u definiëren welke actie moet
worden ondernomen als een door een regel gedefinieerde verbinding tot stand wordt gebracht.
Binnenkomende verbindingen zijn afkomstig van een externe computer die een verbinding tot stand probeert te
brengen met het lokale systeem. Uitgaande verbindingen werken andersom. Het lokale systeem maakt contact met
een externe computer.
Als er nieuwe, onbekende communicatie wordt gedetecteerd, moet u zorgvuldig overwegen of u deze toestaat of
weigert. Ongevraagde, niet beveiligde of onbekende verbindingen vormen een beveiligingsrisico voor het
systeem. Als een dergelijke verbinding tot stand wordt gebracht, raden we u aan speciale aandacht te besteden aan
de externe computer en de toepassing die probeert verbinding te maken met uw computer. Veel infiltraties
proberen persoonlijke gegevens te verkrijgen en verzenden, of downloaden andere schadelijke toepassingen naar
hostwerkstations. De firewall stelt u in staat dergelijke verbindingen te detecteren en te beëindigen.
Standaard kunnen toepassingen die zijn ondertekend door Apple automatisch toegang krijgen tot het netwerk. Als
u deze mogelijkheid wilt uitschakelen, deselecteer dan Software die is ondertekend door Apple automatisch
netwerktoegang geven.
8.2.1 Nieuwe regels maken
He t tabblad Regels bevat een lijst met alle regels die worden toegepast op het verkeer dat door afzonderlijke
toepassingen wordt gegenereerd. Regels worden automatisch toegevoegd aan de hand van reacties van de
gebruiker op nieuwe communicatie.
1. Om een nieuwe regel te maken, klikt u op Toevoegen , voert u een naam in voor de regel en sleept u het
pictogram van de toepassing naar het lege veld of klikt u op Bladeren om het programma te zoeken in de
map /Applications. Als u de regel wilt toepassen op alle toepassingen die op de computer zijn geїnstalleerd,
se lecte ert u Alle toepassingen.
2. In het volgende venster geeft u de Actie op (de communicatie tussen de geselecteerde toepassing en het
netwerk toestaan of weigeren ) en de Richting van de communicatie (binnenkomend, uitgaand of beide).
Selecteer Logboekregel om alle communicatie vast te leggen waarbij deze regel betrokken is. Als u de
firewalllogboeken wilt controleren, klikt u in het hoofdmenu van ESET Endpoint Security op Hulpmiddelen >
Logboeken en selecteert u Firewall in het vervolgkeuzemenu Logboek.
3. Stel in de sectie Protocol/poorten het protocol en de poort in waarvan de toepassing gebruikmaakt (indien TCP-
of UDP-protocol is geselecteerd) voor de communicatie. De transportprotocollaag zorgt voor veilige en efficiënte
gegevensoverdracht.
4. Geef tot slot de criteria voor het Doel op (IP-adres, bereik, subnet, ethernet of internet) voor de regel.
8.3 Firewallzones
Een zone is een verzameling netwerkadressen die één logische groep vormen. Aan elk adres in een bepaalde groep
worden vergelijkbare regels toegewezen, die centraal worden gedefinieerd voor de hele groep.
U kunt deze zones maken door op de knop Toevoegen te klikken. Gee f e en Naam e n e en Beschrijving (optioneel)
van de zone op, selecteer een profiel waartoe de zone behoort en voeg een IPv4-/IPv6-adres, adresbereik, subnet,
WiFi-netwerk of een interface toe.

31
8.4 Firewallprofielen
Met Profielen kunt u het gedrag van de firewall van ESET Endpoint Security bepalen. Wanneer u een regel voor de
firewall maakt of bewerkt, kunt u deze toewijzen aan een bepaald profiel. Wanneer u een profiel selecteert,
worden alleen de algemene regels (waarvoor geen profiel is opgegeven) en de regels die zijn toegewezen aan dat
profiel toegepast. U kunt het gedrag van de firewall eenvoudig wijzigen door meerdere profielen te maken waaraan
verschillende regels zijn toegewezen.
8.5 Firewalllogboeken
De firewall van ESET Endpoint Security slaat alle belangrijke gebeurtenissen op in een logbestand. Als u de
firewalllogboeken wilt openen vanuit het hoofdmenu, klikt u op Hulpmiddelen > Logboeken e n se lecte er Firewall
in het vervolgkeuzemenu Logboek.
Logbestanded zijn een waardevol hulpmiddel bij het detecteren van fouten en het aan het licht brengen van
inbreuken in het systeem. De logboeken van de ESET-firewall bevatten de volgende gegevens:
· Datum en tijd van de gebeurtenis
· Naam van de gebeurtenis
· Bron
· Doelnetwerkadres
· Netwerkcommunicatieprotocol
· Regel toegepast
· Betrokken toepassing
· Gebruiker
Een grondige analyse van deze gegevens kan helpen bij het detecteren van pogingen de systeembeveiliging in
gevaar te brengen. Er zijn veel andere factoren die kunnen wijzen op potentiële risico's en waartegen u zich kunt
beveiligen met de firewall, zoals: frequente verbindingen vanaf onbekende locaties, meerdere pogingen om
verbindingen tot stand te brengen, communicatie via onbekende toepassingen of gebruik van ongebruikelijke
poortnummers.

32
9. Apparaatbeheer
Met ESET Endpoint Security kunt u een apparaat scannen, blokkeren en uitgebreide filters en/of machtigingen
ervoor aanpassen en bepalen hoe de gebruiker een apparaat opent en ermee werkt. Dit is handig als de beheerder
van de computer wil voorkomen dat er apparaten met ongewenste inhoud worden gebruikt.
Ondersteunde externe apparaten:
· Schijfopslag (HDD, USB-flashstation)
· Cd/dvd
· USB-printer
· Scanapparaat
· Seriële poort
· Netwerk
· Draagbaar apparaat
Als er een apparaat wordt geplaatst dat door een bestaande regel wordt geblokkeerd, wordt er een
meldingsvenster weergegeven en wordt de toegang tot het apparaat geblokkeerd.
In het logbestand van Apparaatbeheer worden alle incidenten geregistreerd waardoor Apparaatbeheer is
geactiveerd. Logboekvermeldingen kunnen worden weergegeven in het hoofdprogrammavenster van ESET
Endpoint Security via Hulpmiddelen > Logbestanden .
9.1 Regeleditor
De opties voor de instellingen van Apparaatbeheer kunnen worden aangepast in Instellingen > Voorkeuren voor
toepassing opgeven... > Apparaatbeheer.
Als u op Apparaatbeheer inschakelen klikt, wordt de functie Apparaatbeheer ingeschakeld in ESET Endpoint
Security. Wanneer Apparaatbeheer is ingeschakeld, kunt u de functies voor Apparaatbeheer beheren en bewerken.
Schakel het selectievakje in naast een regelnaam om de desbetreffende regel in te schakelen.
Met de knoppen en kunt u regels toevoegen en verwijderen. Regels worden in volgorde van prioriteit
vermeld, waarbij regels met een hogere prioriteit hoger in de lijst staan. Als u de volgorde wilt wijzigen, verplaatst
u een regel met slepen-en-neerzetten naar een nieuwe positie of klikt u op en kiest u een van de opties.
ESET Endpoint Security detecteert automatisch alle op dat moment geplaatste apparaten en hun parameters
(Apparaattype, Leverancier, Model, Serienummer). Klik in plaats van handmatig regels te maken op de optie
Invullen, selecteer het apparaat en klik op Doorgaan om de regel te maken.
Bepaalde apparaten kunnen worden toegestaan of geblokkeerd op basis van gebruiker, gebruikersgroep of diverse
aanvullende apparaatparameters die in de regelconfiguratie worden opgegeven. De lijst met regels bevat
verschillende beschrijvingen van een regel, waaronder de naam, het apparaattype, de ernst van de
logboekregistratie en de actie die moet worden uitgevoerd nadat een apparaat verbinding met uw computer heeft
gemaakt.
Naam
Geef een beschrijving van de regel op in het veld Naam, zodat deze gemakkelijk is te herkennen. Met het
selectievakje Regel ingeschakeld kan deze regel worden in- of uitgeschakeld. Dit kan handig zijn als u de regel
niet definitief wilt verwijderen.
Apparaattype
Kies het type externe apparaat in het vervolgkeuzemenu. Informatie over het apparaattype wordt bij het
besturingssysteem verzameld. Opslagapparaten zijn onder andere externe schijven of gewone
geheugenkaartlezers die zijn aangesloten via USB of FireWire. Voorbeelden van scanapparaten zijn scanners of
camera's. Omdat deze apparaten alleen informatie over hun acties weergeven en geen informatie weergeven
over hun gebruikers, kunnen ze alleen in hun algemeenheid worden geblokkeerd.
35

33
Actie
Toegang tot niet-opslagapparaten kan worden toegestaan of geblokkeerd. Met regels voor opslagapparaten
kunnen echter de volgende rechten worden geselecteerd:
Lezen/schrijven: er is volledige toegang tot het apparaat mogelijk
Alleen lezen: alleen leestoegang op het apparaat is toegestaan
Blokkeren: de toegang tot het apparaat wordt geblokkeerd
Criteriatype
Selecteer Apparaatgroep of Apparaat. Aanvullende parameters die hieronder worden weergegeven, kunnen
worden gebruikt voor het verfijnen van regels om ze nauwkeurig af te stemmen op apparaten.
Leverancier: u kunt filteren op leveranciersnaam of -id
Model: de naam van het apparaat
Serienummer: externe apparaten hebben doorgaans een eigen serienummer. Bij een cd of dvd is dit het
serienummer van het medium, niet dat van het cd-/dvd-station.
OPMERKING: Als deze parameters niet zijn opgegeven, zal de regel deze velden negeren. Filterparameters in alle
tekstvelden zijn ongevoelig voor hoofdletters en jokertekens (*, ?) worden niet ondersteund.
TIP: Als u informatie over een apparaat wilt zien, maakt u een regel voor dat apparaattype en verbindt u het
apparaat met uw computer. Wanneer het apparaat is verbonden, worden de apparaatdetails in het logbestand van
Apparaatbeheer weergegeven.
Ernst van logboekregistratie
Altijd: alle gebeurtenissen worden vastgelegd
Diagnostisch: informatie die nodig is om het programma af te stemmen wordt vastgelegd
Informatie: informatieve berichten en alle bovenstaande meldingen worden vastgelegd
Waarschuwing: kritieke fouten en waarschuwingsberichten worden vastgelegd
Geen: er worden geen logbestanden vastgelegd
Gebruikerslijst
Regels kunnen worden beperkt tot bepaalde gebruikers door de regels toe te voegen aan de lijst met
gebruikers:
Bewerken...: hiermee opent u de Identiteitseditor, waarin u gebruikers of groepen kunt selecteren. Als u een
lijst met gebruikers wilt opgeven, selecteert u deze in de lijst Gebruikers aan de linkerkant en klikt u op
Toevoegen. Als u een gebruiker wilt verwijderen, selecteert u de desbetreffende naam in de lijst
Geselecteerde gebruikers en klikt u op Verwijderen. Als u alle systeemgebruikers wilt weergeven, selecteert u
Alle gebruikers weergeven. Als de lijst leeg is, zijn alle gebruikers toegestaan
OPMERKING: Niet alle apparaten kunnen worden gefilterd met gebruikersregels (scanapparaten geven
bijvoorbeeld geen informatie over gebruikers, maar alleen over acties).
35

34
10. Webbeheer
Met de functie Webbeheer kunt u instellingen configureren waarmee u uw bedrijf beschermt tegen het risico van
juridische aansprakelijkheid. Webbeheer kan de toegang beheren tot websites die intellectuele-eigendomsrechten
schenden. Het doel is te voorkomen dat werknemers pagina's met ongepaste of schadelijke inhoud openen, of
pagina's die mogelijk een negatieve invloed hebben op de productiviteit. Werknemers of systeembeheerders de
toegang verbieden tot meer dan 27 vooraf gedefinieerde websitecategorieën en meer dan 140 subcategorieën.
Standaard is Webbeheer uitgeschakeld. Als u deze functie wilt inschakelen, klikt u op Instellingen > Voorkeuren
voor toepassing opgeven > Webbeheer en schakelt u het selectievakje naast Webbeheer inschakelen in.
In het venster Regeleditor worden bestaande op URL gebaseerde of op categorieën gebaseerde regels
weergegeven. De lijst met regels bevat verschillende beschrijvingen van een regel, waaronder de naam, het
blokkeringstype, de actie die wordt uitgevoerd wanneer wordt voldaan aan een regel voor Webbeheer en de
vastgelegde ernst.
Klik op de knop als u een nieuwe regel wilt maken. Dubbelklik op het veld Naam en geef een beschrijving op
van de regel voor betere identificatie.
Met het selectievakje in het veld Ingeschakeld wordt deze regel in-/uitgeschakeld. Dit kan handig zijn als u de regel
later wilt gebruiken maar deze niet definitief wilt verwijderen.
Type
Op URL gebaseerde actie: toegang tot de desbetreffende website. Dubbelklik op het veld URL/categorie en
geef het juiste URL-adres op.
In de URL-adreslijst kunnen de speciale symbolen * (sterretje) en ? (vraagteken) niet worden gebruikt.
Adressen met meerdere TLD's (top-level domains) moeten worden ingevoerd bij de gemaakte groep
(voorbeeldpagina.com, voorbeeldpagina.sk, enzovoort). Als u een domein toevoegt aan de lijst, wordt alle
inhoud in dit domein en alle subdomeinen (bijvoorbeeld sub.voorbeeldpagina.com) geblokkeerd of
toegestaan, afhankelijk van uw op URL-gebaseerde actie.
Op categorie gebaseerde actie: dubbelklik op het veld URL/categorie en selecteer de categorieën.
Identiteit
hiermee kunt u gebruikers selecteren op wie de regel wordt toegepast.
Toegangsrechten
Toestaan: er wordt toegang tot het URL-adres/de categorie verleend
Blokkeren: blokkeert het URL-adres/de categorie
Ernst (om logbestanden te filteren )
Altijd: alle gebeurtenissen worden vastgelegd
Diagnostisch: informatie die nodig is om het programma af te stemmen wordt vastgelegd
Informatie: informatieve berichten en alle bovenstaande meldingen worden vastgelegd
Waarschuwing: kritieke fouten en waarschuwingsberichten worden vastgelegd
Geen: er worden geen logbestanden gemaakt
35
36

35
11. Hulpmiddelen
He t menu Hulpmiddelen omvat modules die het programmabeheer helpen vereenvoudigen en aanvullende opties
voor geavanceerde gebruikers.
11.1 Logbestanden
De logbestanden bevatten informatie over alle belangrijke programmagebeurtenissen die zich hebben voorgedaan
en bieden een overzicht van gedetecteerde bedreigingen. Registratie in logbestanden vormt een essentieel
hulpmiddel bij systeemanalyse, bedreigingsdetectie en probleemoplossing. Logboekregistratie wordt zonder
gebruikersinteractie op de achtergrond uitgevoerd. Informatie wordt vastgelegd op basis van de huidige
detailinstellingen voor logboekregistratie. U kunt tekstberichten en logboeken rechtstreeks vanuit de ESET
Endpoint Security-omgeving weergeven. U kunt de logboeken ook archiveren.
Logbestanden zijn toegankelijk vanuit het hoofdmenu van ESET Endpoint Security door op Hulpmiddelen >
Logbestanden te klikken. Selecteer het gewenste logboektype in de vervolgkeuzelijst Logboek boven in het
venster. De volgende logboeken zijn beschikbaar:
1. Gedetecteerde bedreigingen: informatie over gebeurtenissen met betrekking tot de detectie van infiltraties.
2. Gebeurtenissen: alle belangrijke acties die door ESET Endpoint Security worden uitgevoerd, worden in de
gebeurtenislogboeken geregistreerd.
3. Computerscan: in dit venster worden de resultaten van alle voltooide scans weergegeven. Dubbelklik op een
vermelding om de details van een specifieke computerscan weer te geven.
4. Apparaatbeheer: hierin staan records van verwijderbare media of apparaten die op de computer zijn
aangesloten. Alleen apparaten met een regel voor Apparaatbeheer worden opgenomen in het logbestand. Als
de regel niet overeenkomst met een aangesloten apparaat, wordt er geen logvermelding voor dat aangesloten
apparaat gemaakt. Hier kunt u ook details bekijken als het apparaattype, het serienummer, de leverancier en de
mediagrootte (indien beschikbaar).
5. Firewall: in het firewalllogbestand worden alle externe aanvallen weergegeven die door de firewall zijn
gedetecteerd. In firewalllogboeken staat informatie over gedetecteerde aanvallen op uw systeem. In de kolom
Gebeurtenis staan de gedetecteerde aanvallen, in de kolom Bron leest u meer over de aanvaller in in de kolom
Protocol vindt u het communicatieprotocol dat voor de aanval is gebruikt.
6. Webbeheer: hier worden geblokkeerde en toegestane URL-adressen weergegeven, en details over hoe ze zijn
gecategoriseerd.
7. Gefilterde websites: deze lijst is handig als u een lijst met websites wilt bekijken die door Beveiliging van
webtoegang zijn geblokkeerd. of Webbeheer . In deze logboeken ziet u de tijd, URL, status, het IP-adres,
de gebruiker en toepassing die een verbinding met deze website heeft geopend.
Klik met de rechtermuisknop op een logbestand en klik op Kopiëren om de inhoud van dat logbestand te kopiëren
naar het klembord.
11.1.1 Onderhoud van logbestanden
De configuratie van logbestanden voor ESET Endpoint Security is toegankelijk vanuit het hoofdvenster van het
programma. Klik op Instellingen > oorkeuren voor toepassing opgeven > Hulpmiddelen > Logboekbestanden. U kunt
de volgende opties opgeven voor logbestanden:
· Oude logboekrecords automatisch verwijderen: logboekvermeldingen die ouder zijn dan het opgegeven aantal
dagen, worden automatisch verwijderd.
· Logbestanden automatisch optimaliseren: logbestanden worden automatisch gedefragmenteerd als het
opgegeven percentage ongebruikte records wordt overschreden.
Alle relevante informatie die wordt weergegeven in de grafische gebruikersinterface en berichten over
bedreigingen en gebeurtenissen kunnen worden opgeslagen in leesbare tekst zoals tekstbestanden of CSV-
bestanden (Comma-separated values). Als u deze bestanden beschikbaar wilt maken voor verwerking met externe
programma's, selecteert u het selectievakje naast Loggen naar tekstbestanden inschakelen.
27 34

36
Kl ik op Instellen naast Geavanceerde instellingen om de map te specificeren waar de logbestanden moeten worden
opgeslagen.
Afhankelijk van de opties die u hebt geselecteerd onder Tekstlogbestanden: Bewerken, kunt u logbestanden
opslaan met de volgende geschreven informatie:
· Gebe urteni sse n zoal s Gebruikersnaam en wachtwoord ongeldig, Modules kunnen niet worden bijgewerkt enz.,
worden naar het bestand eventslog.txt geschreven.
· Bedreigingen gedetecteerd door de Opstartscanner, Real-timebeveiliging of Computerscan worden opgeslagen in
het bestand met de naam threatslog.txt.
· De resultaten van alle voltooide scans worden opgeslagen in de indeling scanlog.NUMMER.txt.
· Apparaten die worden geblokkeerd door Apparaatbeheer, worden vermeld in devctllog.txt
· Alle gebeurtenissen die gerelateerd zijn aan communicatie die door de firewall loopt, worden naar firewalllog.txt
geschreven,
· Webpagina's die worden geblokkeerd door Webbeheer, worden vermeld in webctllog.txt
Als u filters wilt configureren voor Standaardlogboekrecords voor computerscans, klikt u op Bewerken en selecteert
u de benodigde typen logbestanden of heft u de selectie ervan op. Meer informatie over deze logtypen vindt u
Logbestanden filteren .
11.1.2 Logbestanden filteren
In logbestanden (ook wel logboeken genoemd) wordt informatie over belangrijke systeemgebeurtenissen
opgeslagen. U kunt logbestanden filteren om alleen records voor specifieke gebeurtenissen weer te geven.
Hieronder worden de meest gebruikte typen logbestanden beschreven:
· Kritieke waarschuwingen - kritieke systeemfouten (bijvoorbeeld het niet starten van de antivirusbeveiliging)
· Fouten - foutmeldingen zoals 'Fout bij downloaden van bestand' en kritieke fouten.
· Waarschuwingen - waarschuwingsberichten
· Informatieve records- informatieve berichten, met betrekking tot onder andere geslaagde updates,
waarschuwingen, enzovoort.
· Diagnostische records - informatie die nodig is voor het instellen van het programma, plus alle hierboven
beschreven records.
36

37
11.2 Planner
De Planner is te vinden in het hoofdmenu van ESET Endpoint Security onder Hulpmiddelen. De Planner bevat een
lijst met alle geplande taken en hun configuratie-eigenschappen, zoals de vooraf gedefinieerde datum en tijd en
het gebruikte scanprofiel.
De Planner beheert en start geplande taken met vooraf gedefinieerde configuraties en eigenschappen. De
configuratie en eigenschappen bevatten informatie zoals de datum en tijd alsmede opgegeven profielen die
moeten worden gebruikt tijdens de uitvoering van de taak.
Standaard worden de volgende geplande taken in de Planner weergegeven:
· Logboekonderhoud (nadat Systeemtaken weergeven is ingeschakeld in de instellingen voor de Planner)
· Opstartbestand controleren na aanmelding gebruiker
· Opstartbestand controleren na succesvolle update van de detectiemodules
· Reguliere automatische update
· Automatisch bijwerken na aanmelding van gebruiker
U kunt de configuratie van een bestaande geplande taak (zowel standaard als door de gebruiker gedefinieerd)
bewerken door Ctrl ingedrukt te houden, op de taak te klikken die u wilt wijzigen en op Bewerken te klikken, of
door de taak te selecteren en op Taak bewerken... te klikken.

38
11.2.1 Nieuwe taken maken
U kunt een nieuwe taak maken in de Planner door op Taak toevoegen... te klikken of door op CTRL te drukken en te
klikken in het lege veld en Toevoegen te selecteren in het contextmenu. Er zijn vijf typen geplande taken
beschikbaar:
· Toepassing uitvoeren
· Bijwerken
· Onderhoud van logbestanden
· On-demand computerscan
· Controle van systeemopstartbestanden
OPMERKING: Door Toepassing uitvoeren te selecteren, kunt u programma's uitvoeren als systeemgebruiker
genaamd "nobody". Machtigingen voor het uitvoeren van toepassingen via de Planner worden door macOS
gedefinieerd.
In het onderstaande voorbeeld gebruiken we de Planner om een nieuwe updatetaak toe te voegen, aangezien
bijwerken een van de meest geplande taken is:
1. Selecteer Geplande taak in de vervolgkeuzelijst Bijwerken.
2. Typ een naam voor de taak in het veld Taaknaam.
3. Selecteer de frequentie van de taak in de vervolgkeuzelijst Taak uitvoeren. Op basis van de geselecteerde
frequentie wordt u gevraagd om waarden voor verschillende updateparameters in te voeren. Als u Door
gebruiker gedefinieerd selecteert, wordt u gevraagd een datum/tijd op te geven in de cron-notatie (zie het
gedeelte Door gebruiker gedefinieerde taak maken voor meer details).
4. In de volgende stap definieert u welke actie moet worden ondernomen als de taak niet kan worden uitgevoerd
of voltooid op het geplande tijdstip.
5. Kl ik op Voltooien. De nieuwe geplande taak wordt toegevoegd aan de lijst met actuele geplande taken.
ESET Endpoint Security bevat voorgedefinieerde geplande taken waarmee de juiste werking wordt gewaarborgd.
Deze mogen niet worden gewijzigd en zijn standaard verborgen. Als u deze taken zichtbaar wilt maken, klikt u in het
hoof dme nu op Instellingen > Voorkeuren voor toepassing opgeven > Planner en selecteert u Systeemtaken
weergeven.
11.2.2 Een door gebruiker gedefinieerde taak maken
Er zijn enkele speciale parameters die moeten worden opgegeven als u Door de gebruiker gedefinieerd als taaktype
in het vervolgkeuzemenu Uitvoeren.
De datum en tijd van een Door gebruiker gedefinieerde taak moeten worden opgegeven in cron-notatie met
jaaruitbreiding (een tekenreeks bestaande uit zes velden, gescheiden door een witruimte):
minuut(0-59) uur(0-23) dag van maand(1-31) maand(1-12) jaar(1970-2099) dag van week(0-7)(zondag = 0 of
7)
Bijvoorbeeld:
30 6 22 3 2012 4
De volgende speciale tekens worden ondersteund in CRON-expressies:
· sterretje (*) - expressie geldt voor alle waarden van het veld. Een sterretje in het derde veld (dag van maand)
betekent bijvoorbeeld elke dag
· verbindingsstreepje (-) - definieert bereiken, bijvoorbeeld 3-9
· komma (,) - scheidt items in een lijst, bijvoorbeeld 1,3,7,8
· schuine streep (/) - definieert verhogingen van bereiken, bijvoorbeeld 3-28/5 in het derde veld (dag van maand)
betekent de derde dag van elke maand en vervolgens elke vijf dagen.
38

39
Namen van dagen (Monday-Sunday) en namen van maanden (January-December) worden niet ondersteund.
OPMERKING: als u zowel de dag van de maand als de dag van de week definieert, wordt de opdracht alleen
uitgevoerd als beide velden overeenkomen.
11.3 Live Grid
Het Live Grid vroegtijdige waarschuwingssysteem houdt ESET onmiddellijk en continu op de hoogte van nieuwe
infiltraties. Het bidirectionele Live Grid vroegtijdig waarschuwingssysteem heeft één enkel doel, namelijk de
beveiliging verbeteren die wij u kunnen bieden. Dit kunnen we het beste doen door ervoor te zorgen dat we
nieuwe bedreigingen zo spoedig mogelijk in de gaten krijgen door deze aan zoveel mogelijk van onze klanten te
'koppelen' en de informatie te gebruiken die ze verzamelen om onze detectiemodules steeds up-to-date te
houden. Selecteer een van de twee opties voor Live Grid:
1. U kunt ervoor kiezen om het Live Grid vroegtijdig waarschuwingssysteem niet in te schakelen. De software blijft
op dezelfde wijze functioneren, maar in bepaalde gevallen reageert ESET Endpoint Security mogelijk sneller op
nieuwe bedreigingen dan een update van de detectiemodule.
2. U kunt het Live Grid vroegtijdig waarschuwingssysteem zodanig configureren dat anonieme informatie wordt
verzonden over nieuwe bedreigingen en waar de nieuwe bedreigingscode voorkomt. Deze informatie kan voor
gedetailleerde analyse naar ESET worden verzonden. Door deze bedreigingen te bestuderen kan ESET de
database met bedreigingen bijwerken en de detectiemogelijkheden verbeteren.
Het Live Grid vroegtijdig waarschuwingssysteem verzamelt informatie over uw computer met betrekking tot nieuw
gedetecteerde bedreigingen. Deze informatie kan een voorbeeld of kopie bevatten van het bestand waarin de
bedreiging voorkwam, het pad naar dat bestand, de bestandsnaam, de datum en tijd, het proces waarbij de
bedreiging plaatsvond op uw computer en informatie over het besturingssysteem van uw computer.
Hoewel de kans bestaat dat het bedreigingslaboratorium van ESET hiermee nu en dan informatie over u of uw
computer in bezit krijgt (gebruikersnamen in een directorypad enz.), wordt deze informatie niet gebruikt voor
andere doelen dan ons te helpen onmiddellijk te reageren op nieuwe bedreigingen.
Als u Live Grid in het hoofdvenster wilt instellen, klik dan op Instellingen > Voorkeuren voor toepassing opgeven >
Live Grid. Se lecte er ESET Live Grid™-reputatiesysteem inschakelen (aanbevolen) om Live Grid te activeren en klik
ve rvolgens op Instellingen naast Geavanceerde opties.
11.3.1 Verdachte bestanden
Standaard wordt ESET Endpoint Security zodanig geconfigureerd dat verdachte bestanden voor gedetailleerde
analyse naar het ESET-bedreigingslaboratorium worden verzonden. Als u deze bestanden niet automatisch wilt
versturen, schakelt u Verzenden van verdachte bestanden(Instellingen > Voorkeuren voor toepassing opgeven >
Live Grid > Instellingen) uit.
Als u een verdacht bestand aantreft, kunt u dit naar ons bedreigingslaboratorium versturen voor analyse. Klik
hiervoor in het hoofdvenster van het programma op Hulpmiddelen > Bestand verzenden voor analyse. Als het een
schadelijke toepassing is, wordt de detectie ervan toegevoegd aan een komende update.
Verzenden van anonieme statistische informatie: het ESET Live Grid vroegtijdig waarschuwingssysteem verzamelt
anonieme informatie over uw computer met betrekking tot nieuw gedetecteerde bedreigingen. Deze informatie
omvat de naam van de infiltratie, de datum en het tijdstip waarop deze is gedetecteerd, de versie van het ESET-
beveiligingsproduct, de versie van uw besturingssysteem en de locatie-instelling. Deze statistische gegevens
worden gewoonlijk een- of tweemaal per dag naar de servers van ESET verzonden.

40
Hieronder ziet u een voorbeeld van een verzonden statistisch pakket:
# utc_time=2005-04-14 07:21:28
# country=“Slovakia“
# language=“ENGLISH“
# osver=9.5.0
# engine=5417
# components=2.50.2
# moduleid=0x4e4f4d41
# filesize=28368
# filename=Users/UserOne/Documents/Incoming/rdgFR1463[1].zip
Uitsluitingsfilter: met het uitsluitingsfilter kunt u bepaalde bestandstypen uitsluiten van verzending. Het kan
bijvoorbeeld handig zijn bestanden uit te sluiten die mogelijk vertrouwelijke informatie bevatten, zoals
documenten of spreadsheets. Veelgebruikte bestandstypen worden standaard uitgesloten ((.doc, .rtf enz.). U kunt
bestandstypen toevoegen aan de lijst met uitgesloten bestanden.
E-mailadres van contactpersoon (optioneel): uw e-mailadres kan worden gebruikt als meer informatie nodig is voor
analyse. U zult geen antwoord van ESET ontvangen, tenzij nadere informatie nodig is voor de analyse.
11.4 Quarantaine
Het hoofddoel van de quarantaine is het veilig opslaan van geïnfecteerde bestanden. Bestanden moeten in
quarantaine worden geplaatst als ze niet kunnen worden opgeschoond, als het niet veilig of raadzaam is om ze te
verwijderen of als ze onterecht door ESET Endpoint Security zijn gedetecteerd.
U kunt elk bestand in quarantaine plaatsen. Dit is raadzaam als een bestand zich verdacht gedraagt maar niet wordt
gedetecteerd door de antivirusscanner. In quarantaine geplaatste bestanden kunnen voor analyse naar het ESET-
bedreigingslaboratorium worden verzonden.
Bestanden die zijn opgeslagen in de quarantainemap, kunnen worden bekeken in een tabel waarin de datum en het
tijdstip van de quarantaine, het pad naar de oorspronkelijke locatie van het geïnfecteerde bestand, de grootte van
het bestand in bytes, de reden van de quarantaine (bijvoorbeeld object toegevoegd door gebruiker) en het aantal
gedetecteerde bedreigingen worden weergegeven. De quarantainemap (/Library/Application
Support/Eset/esets/cache/quarantine) blijft zelfs na het verwijderen van ESET Endpoint Security op het systeem
staan. Bestanden in quarantaine worden veilig gecodeerd opgeslagen en kunnen weer worden teruggezet na
installatie van ESET Endpoint Security.
11.4.1 Bestanden in quarantaine plaatsen
ESET Endpoint Security plaatst verwijderde bestanden automatisch in quarantaine (als u deze optie niet hebt
uitgeschakeld in het waarschuwingsvenster). In het venster Quarantaine kunt u op Quarantaine klikken om
handmatig bestanden in quarantaine te plaatsen. U kunt ook op elk gewenst moment met Ctrl+klikken op een
bestand klikken en Services > ESET Endpoint Security - Bestanden aan quarantaine toevoegen selecteren in het
contextmenu om het bestand in quarantaine te plaatsen.
11.4.2 Een in quarantaine geplaatst bestand herstellen
In quarantaine geplaatste bestanden kunnen ook naar hun oorspronkelijke locatie worden hersteld. Hiervoor
selecteert u het in quarantaine geplaatste bestand en klikt u op Herstellen. Herstellen is ook beschikbaar in het
contextmenu. Houd Ctrl ingedrukt terwijl u op het gewenste bestand in het venster Quarantaine klikt en klik op
Herstellen. U kunt Herstellen naar gebruiken om een bestand naar een andere locatie te herstellen dan de locatie
waar het bestand oorspronkelijk vandaan kwam.

41
11.4.3 Een bestand verzenden vanuit quarantaine
Als u een verdacht bestand in quarantaine hebt geplaatst dat niet is gedetecteerd door het programma, of als een
bestand ten onrechte als geïnfecteerd is beoordeeld (bijvoorbeeld door heuristische analyse van de code) en
vervolgens in quarantaine geplaatst, stuurt u het bestand naar het ESET-bedreigingslaboratorium. U kunt een
bestand verzenden vanuit quarantaine door Ctrl ingedrukt te houden terwijl u op het bestand klikt en Bestand
verzenden voor analyse te selecteren in het contextmenu.
11.5 Machtigingen
De instellingen van ESET Endpoint Security kunnen van groot belang zijn voor het beveiligingsbeleid van uw
organisatie. Onbevoegde wijzigingen kunnen de stabiliteit en beveiliging van uw systeem in gevaar brengen.
Daarom kunt u kiezen welke gebruikers gemachtigd zijn om de configuratie van het programma te wijzigen.
U kunt gemachtigde gebruikers configureren onder Instellingen > Voorkeur voor toepassing opgeven > Gebruiker >
Machtigingen.
Om maximale beveiliging voor uw systeem te waarborgen is het van essentieel belang dat het programma correct
wordt geconfigureerd. Onbevoegde wijzigingen kunnen resulteren in het verlies van belangrijke gegevens. Als u
een lijst met gemachtigde gebruikers wilt instellen, selecteert u deze in de lijst Gebruikers aan de linkerkant en
klikt u op Toevoegen. Als u een gebruiker wilt verwijderen, selecteert u de desbetreffende naam in de lijst
Gemachtigde gebruikers aan de rechterkant en klikt u op Verwijderen. Als u alle systeemgebruikers wilt
weergeven, selecteert u Alle gebruikers weergeven.
OPMERKING: als de lijst met gemachtigde gebruikers leeg is, zijn alle gebruikers van het systeem gemachtigd de
programma-instellingen te bewerken.
11.6 Presentatiemodus
De Presentatiemodus is een functie voor gebruikers die niet willen dat het gebruik van hun software wordt
onderbroken, die niet willen dat er pop-upvensters verschijnen en die willen dat de belasting van de CPU minimaal
is. De Presentatiemodus kan ook worden gebruikt tijdens presentaties die niet mogen worden verstoord door
antivirusactiviteit. Indien ingeschakeld, worden alle pop-upvensters uitgeschakeld en worden alle geplande taken
niet uitgevoerd. Systeembeveiliging wordt nog steeds uitgevoerd op de achtergrond, maar er is geen interactie van
de gebruiker vereist.
Als u de presentatiemodus handmatig wilt inschakelen, klikt u op Instellingen > Voorkeuren voor toepassing
opgeven.. > Presentatiemodus > Presentatiemodus inschakelen.
Schakel het selectievakje naast Presentatiemodus automatisch in volledig scherm inschakelen in om de
Presentatiemodus automatisch in te schakelen als toepassingen worden uitgevoerd in de modus voor volledig
scherm. Als deze functie is ingeschakeld, wordt de Presentatiemodus gestart wanneer u een toepassing in volledig
scherm opent en wordt de modus automatisch beëindigd als u de toepassing sluit. Dit is met name handig voor het
starten van een presentatie.
Ook kunt u Presentatiemodus automatisch uitschakelen na selecteren om de tijdsduur op te geven waarna de
Presentatiemodus automatisch wordt uitgeschakeld.

42
Omdat het inschakelen van de Presentatiemodus een potentieel beveiligingsrisico is, wordt het pictogram met de
beveiligingsstatus van ESET Endpoint Security oranje en wordt er een waarschuwing weergegeven.
OPMERKING: Als de firewall zich in de Interactieve modus bevindt en de Presentatiemodus is ingeschakeld, kunt u
mogelijk moeilijk verbinding maken met internet. Dit kan een probleem zijn als u een toepassing start die
verbinding maakt met internet. Doorgaans zou u worden gevraagd een dergelijke actie te bevestigen (als er geen
communicatieregels of uitzonderingen zijn gedefinieerd), maar in de Presentatiemodus is interactie met de
gebruiker uitgeschakeld. De oplossing hiervoor is een communicatieregel te definiëren voor elke toepassing die
zou kunnen conflicteren met dit gedrag, of een andere filtermodus te gebruiken in de firewall. Houd er ook
rekening mee dat als de Presentatiemodus is ingeschakeld en u naar een webpagina of toepassing gaat die een
beveiligingsrisico met zich meebrengt, deze mogelijk wordt geblokkeerd maar er geen uitleg of waarschuwing
wordt weergegeven, omdat interactie met de gebruiker is uitgeschakeld.
11.7 Actieve processen
De l ijst Actieve processen geeft de processen weer die op uw computer worden uitgevoerd. ESET Endpoint Security
biedt gedetailleerde informatie over actieve processen om gebruikers te beschermen die ESET Live Grid-
technologie gebruiken.
· Proces - de naam van het proces dat momenteel op uw computer wordt uitgevoerd. U kunt ook Activity Monitor
gebruiken (te vinden in /Applications/Utilities) om alle processen weer te geven die op uw computer worden
uitgevoerd.
· Risiconiveau - in de meeste gevallen wijzen ESET Endpoint Security en ESET Live Grid-technologie risiconiveaus
toe aan objecten * bestanden, processen enz.) met een reeks heuristische regels die de kenmerken van elk
object onderzoeken en vervolgens afwegen wat hun potentieel is voor schadelijke activiteiten. Op basis van deze
heuristiek wordt aan objecten een risiconiveau toegewezen. Bekende toepassingen die groen zijn gemarkeerd
zijn zeker schoon (staan op de witte lijst) en worden uitgesloten van scannen. Hierdoor wordt de snelheid van
zowel On-demand scan als Real-time scan verhoogd. Als een toepassing is gemarkeerd als onbekend (geel), hoeft
deze geen schadelijke software te zijn. Gewoonlijk is het slechts een nieuwere toepassing. Als u niet zeker bent
van een bestand, kunt u het naar het ESET-bedreigingslaboratorium sturen ter analyse. Als het bestand een
schadelijke toepassing blijkt te zijn, wordt de detectie ervan in een van de volgende updates opgenomen.
· Aantal gebruikers - het aantal gebruikers dat een bepaalde toepassing gebruikt. Deze informatie wordt verzameld
door de ESET Live Grid-technologie.
· Tijdstip van detectie - de periode sinds de toepassing werd gedetecteerd door de ESET Live Grid-technologie.
· Toepassingsbundel-id - de naam van de leverancier of het toepassingsproces.
Als u op een bepaald proces klikt, wordt de volgende informatie onder in het venster weergegeven:
· Bestand - de locatie van een toepassing op de computer
· Bestandsgrootte - de fysieke grootte van het bestand op de schijf,
· Beschrijving van bestand - bestandskenmerken gebaseerd op de beschrijving van het besturingssysteem
· Toepassingsbundel-id - de naam van de leverancier of het toepassingsproces
· Versie van bestand - informatie over de uitgever van het bestand
· Productnaam - de naam van de toepassing en/of de bedrijfsnaam

43
12. Gebruikersinterface
Via de configuratie-opties voor de gebruikersinterface kunt u de werkomgeving aan uw eigen behoeften
aanpassen. Deze opties zijn toegankelijk vanuit het hoofdmenu door te klikken op Instellingen > Voorkeuren voor
toepassing opgeven... > Interface.
· Als u het welkomscherm van ESET Endpoint Security wilt weergeven bij het opstarten van het systeem, selecteer
dan Welkomscherm weergeven bij opstarten.
· Met Toepassing in Dock weergeven kunt u het ESET Endpoint Security-pictogram weergeve n i n macOS Dock, en
heen en weer schakelen tussen ESET Endpoint Security en andere geactiveerde toepassingen door op cmd+tab te
drukken. Wijzigingen worden van kracht nadat u ESET Endpoint Security opnieuw hebt gestart (doorgaans
geactiveerd door het opnieuw opstarten van de computer).
· Via Standaardmenu gebruiken kunt u bepaalde sneltoetsen gebruiken (zie Sneltoetsen ) en de
standaardmenu-opties zien (Gebruikersinterface, Instellingen en Hulpmiddelen) op de menubalk van macOS
(boven in het scherm).
· Schakel Knopinfo weergeven in om knopinfo weer te geven als de cursor op bepaalde opties in ESET Endpoint
Security wordt geplaatst.
· Met Verborgen bestanden weergeven kunt u verborgen bestanden weergeven en selecteren in de instellingen
voor Scandoelen v oor e en Computerscan.
· Standaard wordt het ESET Endpoint Security-pictogram weergegeven op de menubalk Extra die rechts van de
macOS-menubalk (boven in het scherm) wordt weergegeven. Als u dit wilt uitschakelen, deselecteert u
Pictogram weergeven in Extra op menubalk. Deze wijziging wordt van kracht nadat u ESET Endpoint Security
opnieuw hebt gestart (doorgaans geactiveerd door het opnieuw opstarten van de computer).
12.1 Waarschuwingen en meldingen
In het gedeelte Waarschuwingen en meldingen kunt u configureren hoe waarschuwingen voor bedreigingen,
meldingen over de beveiligingsstatus en systeemmeldingen door ESET Endpoint Security worden verwerkt.
Wanne er u Waarschuwingen weergeven uitschakelt, worden alle waarschuwingsvensters geannuleerd. Dit wordt
alleen aanbevolen in bepaalde situaties. Voor de meeste gebruikers adviseren wij de standaardoptie
(ingeschakeld) te gebruiken. Geavanceerde opties worden beschreven in dit hoofdstuk .
Wanne er u Meldingen weergeven op bureaublad selecteert, wordt het weergeven van waarschuwingsvensters op
het bureaublad waarvoor geen gebruikersinteractie nodig is ingeschakeld (standaard in de rechterbovenhoek van
het scherm). U kunt opgeven hoe lang een melding wordt weergegeven door de waarde van Meldingen
automatisch sluiten na X seconden te wijzigen (standaard 5 seconden).
Sinds ESET Endpoint Security versie 6.2 kunt u ook verhinderen dat bepaalde Beveiligingsstatussen in het
hoofdvenster van het programma worden weergegeven (het venster Beveiligingsstatus). Zie
Beveiligingsstatussen voor meer informatie hierover.
12.1.1 Waarschuwingen weergeven
In ESET Endpoint Security worden waarschuwingsdialoogvensters weergegeven om u te informeren over een
nieuwe programmaversie, updates voor het besturingssysteem, het uitschakelen van bepaalde
programmaonderdelen, het verwijderen van logboeken enz. U kunt elke melding afzonderlijk onderdrukken door in
elk dialoogvenster de optie Dit dialoogvenster niet meer weergeven te selecteren.
Via Lijst met dialoogvensters (te vinden onder Instellingen > Voorkeuren voor toepassing opgeven... >
Waarschuwingen en meldingen > Waarschuwingen weergeven: Instellingen...) wordt de lijst met alle
waarschuwingsdialoogvensters weergegeven die worden geactiveerd door ESET Endpoint Security. Als u een
melding wilt inschakelen of onderdrukken, schakelt u het selectievakje links naast Naam van dialoogvenster in.
Daarnaast kunt u Weergavevoorwaarden definiëren waaronder meldingen over nieuwe updates voor apparaten en
het besturingssysteem worden weergegeven.
16
43
44

44
12.1.2 Beveiligingsstatussen
De huidige beveiligingsstatus van ESET Endpoint Security kan worden gewijzigd door statussen te activeren of
de acti vere n i n Instellingen > Voorkeuren voor toepassing opgeven... > Waarschuwingen en meldingen >
Weergeven in het scherm Beveiligingsstatus: Instellingen. De status van verschillende programmafuncties worden
weergegeven of verborgen in het hoofdvenster van ESET Endpoint Security (het venster Beveiligingsstatus).
U kunt de beveiligingsstatus van de volgende programmafuncties verbergen:
· Firewall
· Antiphishing
· Beveiliging van webtoegang
· Beveiliging van e-mailclient
· Presentatiemodus
· Updates voor besturingssysteem
· Licentie verloopt
· Computer moet opnieuw worden opgestart
12.2 Contextmenu
Als u de functies van ESET Endpoint Security beschikbaar wilt maken in he contextmenu, klikt u op Instellingen >
Voorkeuren voor toepassing opgeven > Contextmenu en schakel het selectievakje naast Integreren in het
contextmenu in. Wijzigingen gaan in nadat u zich hebt afgemeld en uw computer opnieuw hebt opgestart. Opties
van het contextmenu zijn beschikbaar op het bureaublad en in het venster Finder als u CTRL+klikken op een bestand
of map uitvoert.

45
13. Bijwerken
ESET Endpoint Security moet regelmatig worden bijgewerkt om het maximale beveiligingsniveau te kunnen blijven
bieden. De updatemodule \orgt ervoor dat het programma altijd is bijgewerkt door steeds de meest recente
detectiemodules te downloaden.
Klik in het hoofdmenu op Bijwerken voor het weergeven van de actuele updatestatus, inclusief de datum en tijd
van de laatste update en controleer of er een update nodig is. U begint het updateproces handmatig door te klikken
op Modules bijwerken.
Onder normale omstandigheden, dus wanneer updates zonder problemen worden gedownload, wordt het bericht
Bijwerken is niet nodig. De geïnstalleerde modules zijn up-to-date in het venster Bijwerken weergegeven als u over
de nieuwste modules beschikt. Als de modules niet kunnen worden bijgewerkt, wordt aangeraden dat u de update-
instellingen controleert. De meest voorkomende redenen voor deze fout zijn onjuist ingevoerde
licentiegegevens en onjuist geconfigureerde verbindingsinstellingen .
He t ve nste r Bijwerken bevat ook het versienummer van de detectie-engine. Deze numerieke indicator is gekoppeld
aan de ESET-website waar informatie over updates van de detectie-engine wordt weergegeven.
13.1 Instellingen voor update
In het gedeelte met instellingen voor update wordt informatie opgegeven over de bron van de update, zoals
updateservers en verificatiegegevens voor deze servers. Standaard is de vervolgkeuzelijst Updateserver ingesteld
op Automatisch kiezen om te waarborgen dat de updatebestanden automatisch worden gedownload van de ESET-
server met het minste netwerkverkeer.
45
13 49

46
De lijst met beschikbare updateservers is toegankelijk in de vervolgkeuzelijst Updateserver. Als u een nieuwe
updateserver wilt toevoegen, klikt u op Bewerken, voert u het adres van de nieuwe server in het invoervak
Updateserver in en klik op Toevoegen.
ESET Endpoint Security maakt het mogelijk een alternatieve of reserve-updateserver in te stellen. De Primair server
zou uw mirrorserver kunnen zijn, en de Secundair server de standaard ESET-updateserver. Uw secundaire server
moet een andere server zijn dan de primaire. Anders wordt deze niet gebruikt. Als u geen secundaire updateserver,
gebruikersnaam en wachtwoord opgeeft, werkt de reserve-updatefunctionaliteit niet. U kunt ook Automatisch
kiezen selecteren en uw gebruikersnaam en wachtwoord invoeren in de desbetreffende velden, zodat ESET
Endpoint Security automatisch de beste updateserver kiest.
Met Proxymodus kunt u detectiemodules met een proxyserver bijwerken (bijvoorbeeld een lokale HTTP-proxy). De
server kan de algemene proxyserver zijn die op alle programmafuncties van toepassing is die een verbinding
vereisen of de server kan een andere proxyserver zijn. Instellingen voor de algemene proxyserver zouden tijdens
de installatie of bij Proxyserver instellen al moeten zijn opgegeven.
Zo configureert u een client zodat deze alleen updates bij een proxyserver downloadt:
1. selecteer Verbinding maken via een proxyserver in het vervolgkeuzemenu.
2. kl ik op Detecteren om ESET Endpoint Security het IP-adres en het poortnummer te laten invullen (standaard
3128).
3. Geef een geldige Gebruikersnaam en een geldig Wachtwoord op in de desbetreffende velden als voor
communicatie met de proxyserver verificatie is vereist.
ESET Endpoint Security detecteert de proxyinstellingen in Systeemvoorkeuren van macOS. Deze kunnen in macOS
worden geconfigureerd onder > Systeemvoorkeuren > Netwerk > Geavanceerd > Proxy's.
Al s u Directe verbinding gebruiken als HTTP-proxy niet beschikbaar is inschakelt, probeert ESET Endpoint Security
automatisch zonder proxy verbinding met de updateservers te maken. Deze wordt aangeraden aan mobiele
gebruikers met een MacBook.
Als u problemen ondervindt bij het downloaden van updates voor de detectie-engine, klikt u op Updatecache
wissen om tijdelijke updatebestanden te verwijderen.
13.1.1 Geavanceerde opties
Als u meldingen na elke geslaagde update wilt uitschakelen, selecteert u Geen meldingen over geslaagde updates
weergeven.
Schakel Bèta-updates in als u ontwikkelmodules wilt downloaden die op dat moment voor het laatst worden getest.
In veel bèta-updates zijn oplossingen voor productproblemen opgenomen. Uitgestelde updates worden
gedownload enkele uren nadat deze zijn vrijgegeven om ervoor te zorgen dat uw clients geen updates ontvangen
tot is bevestigd dat de updates geen rare problemen veroorzaken bij gebruikers.
In ESET Endpoint Security worden momentopnames van de detectie-engine en programmamodules vastgelegd voor
gebruik met de functie Ongedaan maken van updates. Laat Momentopnamen van updatebestanden maken
ingeschakeld als u wilt dat ESET Endpoint Security deze momentopnamen automatisch registreert. Als u vermoedt
dat een nieuwe update van de detectiemodule en/of programmamodule instabiel of beschadigd is, kunt u met de
functie Updates terugdraaien terugkeren naar de vorige versie en alle updates voor een bepaalde periode
uitschakelen. U kunt ook eerder uitgeschakelde updates die u voor onbepaalde tijd had uitgesteld, opnieuw
inschakelen. Als u een eerdere update met de functie Updates terugdraaien ongedaan maakt, gebruikt u het
vervolgkeuzemenu Periode van opschorting instellen op om de periode in te stellen waarvoor u updates wilt
opschorten. Als u Tot ingetrokken selecteert, worden normale updates pas hervat nadat u deze handmatig hebt
hersteld. Wees voorzichtig met het instellen van de tijdperiode om updates op te schorten.
Maximumleeftijd voor database automatisch instellen: hier kunt u de maximale tijd (in dagen) instellen waarna de
detectiemodules als verouderd worden aangemerkt. De standaardwaarde is 7 dagen.
49

47
13.2 Updatetaken maken
Klik op Bijwerken > Modules bijwerken om het bijwerken van een update voor detectiemodules handmatig te
activeren.
Updates kunnen ook worden uitgevoerd als geplande taken. Als u een geplande taak wilt configureren, klikt u op
Hulpmiddelen > Planner. Standaard zijn in ESET Endpoint Security de volgende taken geactiveerd:
· Reguliere automatische update
· Automatisch bijwerken na aanmelding van gebruiker
Elk van de updatetaken kan worden gewijzigd om te voldoen aan uw behoeften. Behalve de standaardupdatetaken
kunt u ook nieuwe updatetaken maken met een door de gebruiker gedefinieerde configuratie. Zie Planner voor
meer informatie over het maken en configureren van updatetaken.
13.3 Upgraden naar een nieuwe build
Voor maximale beveiliging is het belangrijk dat u de nieuwste build van ESET Endpoint Security gebruikt. U
controleert of een nieuwe versie beschikbaar is door links in het hoofdmenu op Bijwerken te klikken. Als er een
nieuwe build beschikbaar is, wordt onder in het venster een melding weergegeven. Klik op Meer informatie om
een nieuw venster te openen met het versienummer van de nieuwe build en het wijzigingslogboek.
Als u op Downloaden hebt geklikt, wordt het bestand gedownload naar uw downloadmap (of naar de standaardmap
die door de browser is ingesteld). Nadat het downloaden van het bestand is voltooid, kunt u het bestand starten en
de installatie-instructies uitvoeren. Uw licentiegegevens worden automatisch overgezet naar de nieuwe installatie.
We raden aan dat u regelmatig controleert of er upgrades beschikbaar zijn, vooral als u ESET Endpoint Security vanaf
cd/dvd installeert.
13.4 Systeemupdates
De macOS-systeemupdatefunctie is een belangrijk onderdeel dat is ontworpen om gebruikers te beschermen tegen
schadelijke software. Voor een maximale beveiliging raden wij aan om deze updates zo snel mogelijk te installeren
nadat deze beschikbaar zijn gekomen. ESET Endpoint Security brengt u op de hoogte van eventueel ontbrekende
updates volgens het beveiligingsniveau. U kunt het niveau van updates aanpassen waarvoor meldingen worden
we erge geve n i n Instellingen > Voorkeuren voor toepassing > Waarschuwingen en meldingen > Instellen met het
vervolgkeuzemenu Weergavevoorwaarden naast Updates van het besturingssysteem.
· Alle updates weergeven - er wordt een melding weergegeven als er een systeemupdate ontbreekt
· Alleen aanbevolen weergeven - u ontvangt alleen meldingen over aanbevolen updates
Als u geen meldingen over ontbrekende updates wilt ontvangen, schakel het selectievakje naast Updates van het
besturingssysteem dan uit.
Het meldingenvenster geeft een overzicht van de updates die beschikbaar zijn voor het macOS-besturingssysteem
en de toepassingen die met het hulpprogramma van macOS zelf (Software-updates) zijn en kunnen worden
bijgewerkt. U kunt de update rechtstreeks vanuit het meldingenvenster installeren of vanuit de sectie Thuis van
ESET Endpoint Security door te klikken op De ontbrekende update installeren.
In het meldingenvenster staan de toepassingsnaam, versie, grootte, eigenschappen (vlaggen) en aanvullende
informatie over beschikbare updates. In de kolom Vlaggen staat de volgende informatie:
· [aanbevolen] - de fabrikant van het besturingssysteem raadt aan dat u deze update installeert om de beveiliging
en stabiliteit van het systeem te vergroten
· [opnieuw opstarten] - het opnieuw opstarten van de computer is vereist na de installatie
· [afsluiten] - de computer moet worden afgesloten en daarna opnieuw opgestart na de installatie
37

48
In het meldingsvenster staat welke updates door het opdrachtregelhulpprogramma genaamd 'softwareupdate'
worden opgehaald. Updates die door dit hulpprogramma worden opgehaald, kunnen anders zijn dan de updates die
worden weergegeven door de toepassing 'Software-updates'. Als u alle beschikbare updates wilt installeren die in
het venster 'Ontbrekende systeemupdates' worden weergegeven en ook de updates die niet door de toepassing
'Software-updates' worden weergegeven, moet u het opdrachtregelhulpprogramma 'softwareupdate' gebruiken.
Lees voor meer informatie over dit hulpprogramma de handleiding voor software-updates door man
softwareupdate te typen in een Terminal-venster. Dit wordt alleen aangeraden voor ervaren gebruikers.

49
14. Overige
14.1 Instellingen importeren en exporteren
Als u een bestaande configuratie wilt importeren of uw ESET Endpoint Security-configuratie wilt exporteren, klikt u
op Instellingen > Instellingen importeren en exporteren.
Importeren en exporteren is nuttig wanneer u een back-up wilt maken van uw huidige configuratie van ESET
Endpoint Security, zodat u deze later kunt gebruiken. Instellingen exporteren is ook handig voor gebruikers die hun
voorkeursconfiguratie van ESET Endpoint Security op meerdere systemen willen gebruiken. U kunt eenvoudig het
configuratiebestand importeren om zo de gewenste instellingen over te brengen.
Als u een configuratie wilt importeren, selecteert u Instellingen importeren en klikt u op Bladeren om naar het
configuratiebestand te navigeren dat u wilt importeren. Selecteer Instellingen exporteren als u wilt exporteren en
gebruik de browser om een locatie op uw computer te selecteren waar u het configuratiebestand wilt opslaan.
14.2 Proxyserver instellen
Instellingen voor de proxyserver kunnen worden geconfigureerd in Instellingen > Voorkeuren voor toepassing
opgeven > Proxyserver. Als u de proxyserver op dit niveau opgeeft, worden algemene instellingen voor de
proxyserver gedefinieerd voor alle functies van ESET Endpoint Security. Parameters die hier zijn geconfigureerd,
worden gebruikt door alle modules die verbinding met internet vereisen. ESET Endpoint Security ondersteunt Basic
Access- e n NTLM (NT LAN Manager)-verificatie.
U kunt instellingen voor de proxyserver op dit niveau opgeven door het selectievakje Proxyserver gebruiken in te
schakelen en het IP-adres of de URL van de proxyserver in te voeren in het veld Proxyserver. Geef in het veld Poort
de poort op waarop de proxyserver verbindingen accepteert (standaard is dit (3128). U kunt ook op Detecteren
klikken om het programma beide velden te laten invullen.
Als voor communicatie met de proxyserver verificatie is vereist, geeft u een geldige Gebruikersnaam en een geldig
Wachtwoord op in de betreffende velden.

50
14.3 Gedeelde lokale cache
Als u de gedeelde lokale cache wilt inschakelen, klikt u op Instellingen > Voorkeuren voor toepassing opgeven >
Gedeelde lokale cache en schakelt u het selectievakje naast Caching inschakelen met ESET Gedeelde, lokale cache
in. Het gebruik van deze functie verbetert de prestaties in gevirtualiseerde omgevingen doordat dubbel scannen in
het netwerk wordt voorkomen. Hierdoor wordt elk bestand slechts een keer gescand en in de gedeelde cache
opgeslagen. Als de functie is ingeschakeld, wordt informatie over scans van bestanden en mappen op uw netwerk
opgeslagen naar de lokale cache. Als u een nieuwe scan uitvoert, zoekt ESET Endpoint Security naar gescande
bestanden in de cache. Als de bestanden overeenkomen, worden ze uitgesloten van scannen.
Gedeelde lokale cache bevat de volgende instellingen:
· Serveradres: de naam of het IP-adres van de computer waarop zich de cache bevindt.
· Poort: het poortnummer dat wordt gebruikt voor communicatie (standaard (3537)
· Wachtwoord - het wachtwoord voor Gedeelde lokale cache (optioneel)
OPMERKING: Raadpleeg de gebruikershandleiding ESET Shared Local Cache voor uitvoerige instructies over hoe u
ESET Gedeelde lokale cache installeert en configureert. (Deze handleiding is alleen beschikbaar in het Engels.)
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
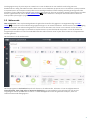 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
ESET Endpoint Security for macOS Gebruikershandleiding
- Type
- Gebruikershandleiding
Gerelateerde papieren
-
ESET Endpoint Antivirus for macOS Gebruikershandleiding
-
ESET Endpoint Security 7 de handleiding
-
ESET ENDPOINT SECURITY 8 de handleiding
-
ESET Cyber Security for macOS Gebruikershandleiding
-
ESET Cyber Security Pro for macOS Gebruikershandleiding
-
ESET Endpoint Antivirus Gebruikershandleiding
-
ESET Endpoint Security Gebruikershandleiding
-
ESET Endpoint Antivirus Gebruikershandleiding
-
ESET Endpoint Security Gebruikershandleiding
-
ESET Endpoint Antivirus 8 de handleiding


















































