
ESET MAIL SECURITY
Copyright ©2020 ESET, spol. s r.o.
ESET Mail Security i s ontwi kke l d door ESET, spol. s r.o.
Ga voor meer informatie naar www.eset.com.
Alle rechten voorbehouden. Niets uit deze documentatie mag worden verveelvoudigd,
worden opgeslagen in een systeem voor het ophalen van gegevens of worden
overgedragen, in enige vorm of op enige wijze, hetzij elektronisch, mechanisch, door
fotokopie, opname, scan of enige andere manier, zonder schriftelijke toestemming
van de auteur.
ESET, spol. s r.o. behoudt zich het recht voor de beschreven toepassingssoftware
zonder voorafgaande kennisgeving te wijzigen.
Klantenservice: www.eset.com/support
REV. 17-4-2020

Inhoud
.......................................................6Voorwoord1.
.......................................................8Overzicht2.
....................................................................................................8Belangrijke functies2.1
....................................................................................................10Nieuwe functies2.2
....................................................................................................11E-mailflow2.3
....................................................................................................11
ESET Mail Security-functies en Exchange
Server-rollen
2.4
....................................................................................................13Exchange Server-rollen2.5
....................................................................................................13POP3-connector en antispam2.6
....................................................................................................14Beveiligingsmodules2.7
....................................................................................................15Meervoudige beveiliging2.8
..............................................................................15Beveiliging van postvakda taba se
2.8.1
..............................................................................16Beveiliging van e-mailtransport
2.8.2
..............................................................................17On-demand data basescan van postvak
2.8.3
..............................................................................19Sca n van Office 365-postvak
2.8.4
.......................................................20Voorbereiden op installatie3.
....................................................................................................21Systeemvereisten3.1
....................................................................................................22
Installatiestappen voor ESET Mail
Security
3.2
..............................................................................27Een bestaande insta llatie wijzigen
3.2.1
....................................................................................................28
Stille installatie/installatie zonder
toezicht
3.3
..............................................................................29Installatie vanaf opdrachtregel
3.3.1
....................................................................................................33Productactivering3.4
..............................................................................34ESET Busines s Account
3.4.1
..............................................................................34Activering voltooid
3.4.2
..............................................................................34Activering mis lukt
3.4.3
..............................................................................34Licentie
3.4.4
....................................................................................................35
Upgrade uitvoeren naar een nieuwere
versie
3.5
..............................................................................36
Upgrade uitvoeren via ESET Security Management
Center
3.5.1
..............................................................................38Upgrade uitvoeren via ESET-cluster
3.5.2
....................................................................................................41Installatie in een clusteromgeving3.6
....................................................................................................41Terminalserver3.7
....................................................................................................42Multiserver-/DAG-omgeving3.8
.......................................................43Aan de slag4.
....................................................................................................43Taken na afloop van de installatie4.1
....................................................................................................44
Beheerd via ESET Security Management
Center
4.2
....................................................................................................45Controle4.3
..............................................................................46Status
4.3.1
..............................................................................48Windows-update bes chikba ar
4.3.2
.......................................................49Als u ESET Mail Security5.
....................................................................................................49Scannen5.1
..............................................................................52Sca nvenster en scanlogboek
5.1.1
....................................................................................................54Logbestanden5.2
..............................................................................58Logbestanden filteren
5.2.1
....................................................................................................59Bijwerken5.3
....................................................................................................61Quarantaine voor e-mail5.4
....................................................................................................64Instellen5.5
..............................................................................65Server
5.5.1
..............................................................................65Computer
5.5.2
..............................................................................66Netwerk
5.5.3
..................................................................................66De wizard Probleemoplos sing - Netwerk
5.5.3.1
..............................................................................66Web en e-mail
5.5.4
..............................................................................67Hulpmiddelen - Regis tratie in diagnoselogboek
5.5.5
..............................................................................68Instellingen importeren en exporteren
5.5.6
....................................................................................................69Hulpmiddelen5.6
..............................................................................70Actieve processen
5.6.1
..............................................................................71Activiteit bekijken
5.6.2
..............................................................................73Beveiligingsstatistieken
5.6.3
..............................................................................74Cluster
5.6.4
..................................................................................76Clusterwizard - Knooppunten selecteren
5.6.4.1
..................................................................................77Clusterwizard - Clusterinstellingen
5.6.4.2
..................................................................................78Clusterwizard - Clusterinstallatie-ins tellingen
5.6.4.3
..................................................................................78Clusterwizard - Knooppuntcontrole
5.6.4.4
..................................................................................81Clusterwizard - Knooppunten installeren
5.6.4.5
..............................................................................83ESET-shell
5.6.5
..................................................................................85Syntaxis
5.6.5.1
..................................................................................90Opdrachten
5.6.5.2
..................................................................................92Batchbestanden/scripts
5.6.5.3
..............................................................................93ESET Dynamic Threat Defense
5.6.6
..............................................................................95ESET SysIns pector
5.6.7
..............................................................................95ESET SysRescue Live
5.6.8
..............................................................................96Planner
5.6.9
..................................................................................97Pla nner - Taak toevoegen
5.6.9.1
........................................................................99Taaktype
5.6.9.1.1
........................................................................100Taaktijden
5.6.9.1.2
........................................................................100Bij gebeurtenis
5.6.9.1.3
........................................................................100Toepa ssing uitvoeren
5.6.9.1.4
........................................................................101Overgesla gen ta ak
5.6.9.1.5
........................................................................101Overzicht van geplande taak
5.6.9.1.6
..............................................................................101Voorbeelden voor analyse verzenden
5.6.10
..................................................................................102Verda cht bes tand
5.6.10.1
..................................................................................102Verda chte site
5.6.10.2
..................................................................................102Vals pos itief bestand
5.6.10.3
..................................................................................103Vals pos itieve site
5.6.10.4
..................................................................................103Overige
5.6.10.5
..............................................................................104Quarantaine
5.6.11
.......................................................106Instellingen voor serverbeveiliging6.
....................................................................................................107Agentprioriteit instellen6.1
....................................................................................................107Antivirus en antispyware6.2
....................................................................................................110Antispambeveiliging6.3
..............................................................................111Filteren en verificatie
6.3.1
..............................................................................114Antispa m gea vanceerde instellingen
6.3.2
..............................................................................117Instellingen voor grijze lijs t
6.3.3

..............................................................................118SPF en DKIM
6.3.4
..............................................................................120Backscatterbeveiliging
6.3.5
....................................................................................................121Antiphishing-beveiliging6.4
....................................................................................................122Regels6.5
..............................................................................125Regelvoorwaarde
6.5.1
..............................................................................129Regelactie
6.5.2
..............................................................................131Regelvoorbeelden
6.5.3
....................................................................................................133Beveiliging van e-mailtransport6.6
..............................................................................136Gea vanceerde instellingen voor berichtentransport
6.6.1
....................................................................................................137Beveiliging van postvakdatabase6.7
..............................................................................138Achtergrondscan
6.7.1
....................................................................................................139On-demand databasescan van postvak6.8
..............................................................................141Da taba ses can van postvak
6.8.1
..............................................................................143Scan van Office 365-pos tvak
6.8.2
..............................................................................144Extra postvakitems
6.8.3
..............................................................................144Proxyserver
6.8.4
..............................................................................145Details van data basescanaccount
6.8.5
....................................................................................................146Typen Quarantaine voor e-mail6.9
..............................................................................147Loka le quarantaine
6.9.1
..................................................................................148Bestandopslag
6.9.1.1
..................................................................................148Webinterface
6.9.1.2
........................................................................154
E-mailquaranta inerapporten verzenden - geplande
taak
6.9.1.2.1
........................................................................155De gebruikerswebinterface voor e-mailquara nta ine
6.9.1.2.2
..............................................................................157Quarantainepos tvak en MS Exchange-quara nta ine
6.9.2
..................................................................................158Instellingen voor quarantainebeheer
6.9.2.1
..................................................................................158Proxyserver
6.9.2.2
..............................................................................159Accountdetails van quara nta inebeheer
6.9.3
....................................................................................................159Antivirustest6.10
....................................................................................................159Antispamtest6.11
....................................................................................................160Antiphishingtest6.12
.......................................................161Algemene instellingen7.
....................................................................................................161Computer7.1
..............................................................................162Uitzonderingen voor processen
7.1.1
..............................................................................164Uitsluitingen
7.1.2
..................................................................................164Uitsluiting toevoegen of bewerken
7.1.2.1
..............................................................................166Automa tische uitsluitingen
7.1.3
..............................................................................167Gedeelde lokale ca che
7.1.4
..............................................................................167Er is een infiltratie gedetecteerd
7.1.5
..............................................................................168Rea l-timebeveiliging va n bestandssysteem
7.1.6
..................................................................................169ThreatSense-parameters
7.1.6.1
........................................................................173Aanvullende ThreatSense-parameters
7.1.6.1.1
........................................................................173
Bestands extensies die moeten worden uitgesloten
van scans
7.1.6.1.2
..............................................................................174Op de cloud gebaseerde beveiliging
7.1.7
..................................................................................176Uitsluitingsfilter
7.1.7.1
..............................................................................177Malwarescans
7.1.8
..................................................................................178Profielbeheer
7.1.8.1
..................................................................................178Profieldoelen
7.1.8.2
..................................................................................180Scandoelen
7.1.8.3
..................................................................................182Sca n bij inactieve status
7.1.8.4
..................................................................................182Opstartscan
7.1.8.5
........................................................................182Automa tische bestandscontrole bij opsta rten
7.1.8.5.1
..................................................................................183Verwis selba re media
7.1.8.6
..................................................................................183Documentbescherming
7.1.8.7
..............................................................................184Hyper-V-scan
7.1.9
..............................................................................185HIPS
7.1.10
..................................................................................188HIPS-regelinstellingen
7.1.10.1
..................................................................................190Geava nceerde HIPS-instellingen
7.1.10.2
....................................................................................................191Updateconfiguratie7.2
..............................................................................194Ongeda an maken van updates
7.2.1
..............................................................................194Geplande taak - Bijwerken
7.2.2
..............................................................................195Updatemirror
7.2.3
....................................................................................................197Netwerkbeveiliging7.3
..............................................................................198IDS-uitzonderingen
7.3.1
..............................................................................199Zwarte lijst met tijdelijk geblokkeerde IP-adressen
7.3.2
....................................................................................................199Web en e-mail7.4
..............................................................................200Protocolfiltering
7.4.1
..................................................................................200Web- en e-mailclients
7.4.1.1
..............................................................................201SSL/TLS
7.4.2
..................................................................................202Lijst met bekende certificaten
7.4.2.1
..................................................................................202Gecodeerde SSL-communica tie
7.4.2.2
..............................................................................203Beveiliging van e-mailclient
7.4.3
..................................................................................204E-mailprotocollen
7.4.3.1
..................................................................................205Waarschuwingen en meldingen
7.4.3.2
..................................................................................205MS Outlook-werkba lk
7.4.3.3
..................................................................................206Outlook Express- en Windows Mail-werkbalk
7.4.3.4
..................................................................................206Bevestigingsvenster
7.4.3.5
..................................................................................206Berichten opnieuw scannen
7.4.3.6
..............................................................................206Beveiliging van webtoegang
7.4.4
..................................................................................207URL-adresbeheer
7.4.4.1
........................................................................208Nieuwe lijst maken
7.4.4.1.1
..............................................................................210Antiphishing-webbeveiliging
7.4.5
....................................................................................................211Apparaatbeheer7.5
..............................................................................211Apparaatregels
7.5.1
..............................................................................213Apparaatgroepen
7.5.2
....................................................................................................214Configuratie van Hulpmiddelen7.6
..............................................................................214Tijdvakken
7.6.1
..............................................................................215Microsoft Windows® Bijwerken
7.6.2
..............................................................................215ESET CMD
7.6.3
..............................................................................217ESET RMM
7.6.4
..............................................................................217WMI-provider
7.6.5
..................................................................................218Opgegeven gegevens
7.6.5.1
..................................................................................224Toegang tot opgegeven gegevens
7.6.5.2
..............................................................................225ERA/ESMC-scandoelen
7.6.6
..............................................................................225Negeermodus
7.6.7
..............................................................................229Logbestanden
7.6.8
..................................................................................232Sysloggebeurtenis sen koppelen
7.6.8.1
..............................................................................234Proxyserver
7.6.9
..............................................................................235Melding
7.6.10
..................................................................................235Toepassingsmeldingen
7.6.10.1
..................................................................................235Bureaubladmeldingen
7.6.10.2

Inhoud
..................................................................................236E-mailmeldingen
7.6.10.3
..................................................................................237Aanpassing
7.6.10.4
..............................................................................237Presentatiemodus
7.6.11
..............................................................................238Diagnostiek
7.6.12
..............................................................................239Cluster
7.6.13
....................................................................................................240Gebruikers7.7
..............................................................................241Wa ars chuwingen en berichtvensters
7.7.1
..............................................................................242Toegangsinstellingen
7.7.2
..............................................................................242ESET-shell
7.7.3
..............................................................................243GUI uitscha kelen op termina lserver
7.7.4
..............................................................................243Uitgeschakelde berichten en statussen
7.7.5
..................................................................................244Instellingen voor toepassingssta tus sen
7.7.5.1
..............................................................................245Systeemvakpictogram
7.7.6
....................................................................................................246Standaardinstellingen herstellen7.8
....................................................................................................246Help en ondersteuning7.9
..............................................................................247Ondersteuningsa anvraa g verzenden
7.9.1
..............................................................................248Info over ESET Mail Security
7.9.2
....................................................................................................248Woordenlijst7.10

6
1. Voorwoord
Deze gids is bedoeld om u te helpen zo optimaal mogelijk gebruik te maken van ESET Mail Security. Als u meer wilt
weten over een bepaald venster in het programma, drukt u op F1 op uw toetsenbord als het desbetreffende
venster is geopend. De Help-pagina voor het venster dat u op dat moment bekijkt, wordt weergegeven.
Voor consistentie en om verwarring te voorkomen, is het gebruik van terminologie in deze handleiding gebaseerd
op de namen van de ESET Mail Security-parameters. Ook is gebruikgemaakt van een uniforme reeks symbolen om
onderwerpen mee aan te duiden die met name interessant of belangrijk zijn.
OPMERKING
Een opmerking is alleen een korte observatie. Hoewel u opmerkingen kunt overslaan, kunnen opmerkingen
waardevolle informatie bevatten, zoals bepaalde functies of een koppeling naar een verwant onderwerp.
BELANGRIJK
Hiervoor is uw aandacht vereist. Het wordt niet aangeraden deze berichten over te slaan. Belangrijke
opmerkingen bevatten significante, maar niet kritische informatie.
WAARSCHUWING
Cruciale informatie die u volle aandacht behoeven. Waarschuwingen zijn bedoeld om te voorkomen dat u
fouten maakt met potentieel schadelijke gevolgen. Lees de tekst die in waarschuwingen staat aandachtig door
en zorg dat u die begrijpt, aangezien erin wordt verwezen naar uiterst gevoelige systeeminstellingen of iets
risicovols.
VOORBEELD
Dit is een use case of praktisch voorbeeld dat u zal helpen te begrijpen hoe een bepaalde functie kan worden
gebruikt.
Als u het volgende element rechtsboven op een Help-pagina ziet, wijst dat op een navigatiemogelijkheid in de
vensters van een grafische gebruikersinterface (GUI) van ESET Mail Security. Volg deze aanwijzingen om naar het
venster te gaan dat op de desbetreffende Help-pagina wordt beschreven.
ESET Mail Security Openen
Klik op Instellingen > Server > OneDrive-scan installeren > Registreren
Opmaakconventies:
Conventie
Betekenis
Vette tekst
Kopteksten van secties, namen van functies of gebruikersinterface-items, zoals knoppen.
Cursieve tekst
Tijdelijke plaatsaanduidingen voor informatie die u opgeeft. Een voorbeeld: bestandsnaam of pad
betekent dat u het daadwerkelijke pad of een naam van een bestand opgeeft.
Courier New
Codevoorbeelden of opdrachten.

7
Conventie
Betekenis
Hyperlink
Geeft snel toegang tot onderwerpen waarnaar wordt verwezen of tot externe weblocaties.
Hyperlinks zijn blauw gemarkeerd en kunnen onderstreept zijn.
%ProgramFiles
%
De Windows-systeemmap waarin geïnstalleerde programma's van Windows worden opgeslagen.
De online-Help-pagina's van ESET Mail Security zijn onderverdeeld in diverse hoofdstukken en onderdelen. U vindt
relevante informatie door te bladeren in de Inhoud van de Help-pagina's. Of u kunt met trefwoorden door de Index
bladeren of naar tekst zoeken met de functie Zoeken.

8
2. Overzicht
ESET Mail Security 7 voor Microsoft Exchange Server is een geïntegreerde oplossing die e-mailservers en de
postvakken van gebruikers beveiligt tegen diverse vormen van schadelijke inhoud, waaronder e-mailbijlagen die
zijn geïnfecteerd met wormen of Trojaanse paarden, documenten met schadelijke scripts, phishing en spam. ESET
Mail Security biedt vier typen beveiliging: Antivirus, anti-spam, anti-phishing en regels. ESET Mail Security filtert
kwaadaardige inhoud in postvakdatabases en in de laag Beveiliging van e-mailtransport voordat deze inhoud in het
postvak van de ontvanger terechtkomt.
ESET Mail Security ondersteunt Microsoft Exchange Server versie 2007 en hoger, alsmede Microsoft Exchange Server
in een clusteromgeving. Specifieke Exchange Server-rollen (postvak, hub, edge) worden ook ondersteund.
Hoewel Microsoft Exchange Server-beveiliging wordt geboden, biedt ESET Mail Security ook functionaliteit die zorgt
voor beveiliging van de server zelf (real-timebeveiliging van bestandssysteem, netwerkbeveiliging, beveiliging van
webtoegang en beveiliging van e-mailclient).
U kunt ESET Mail Security in grotere netwerken op afstand beheren met behulp van ESET Security Management
Center. U kunt ESET Mail Security ook met RMM-tools (Remote Monitoring and Management) van derden gebruiken.
2.1 Belangrijke functies
In de volgende tabel staat een lijst met functies die beschikbaar zijn in ESET Mail Security.
Echte 64-bits productkern
Hogere prestaties en betere stabiliteit voor de kernonderdelen van het product.
Anti-malware
Een bekroonde en innovatie bescherming tegen malware. Deze geavanceerde
technologie voorkomt aanvallen en elimineert allerlei soorten bedreigingen, zoals
virussen, ransomeware, rootkits, wormen en spyware met cloudgebaseerde scans
voor een nog betere detectiesnelheid. De systeembronnen worden slechts lichtelijk
belast, waardoor de prestaties hiervan niet in gevaar komen. De technologie maakt
gebruik van een gelaagd beveiligingsmodel. Elke laag, of elke fase, bevat een aantal
kerntechnologieën. In de fase Voor de uitvoering worden technologieën zoals UEFI-
scanner, netwerkaanvalbeveiliging, reputatie & cache, In-product Sandbox en DNA-
detecties ingezet. Tijdens de Uitvoering worden technologieën zoals Exploit blocker,
ransomwareschild, geavanceerde geheugenscanner en scriptscanner (AMSI) ingezet
en in de fase Na de uitvoering botnetbeveiliging, malwarebeveiligingssysteem via de
cloud en Sandboxing. De kerntechnologieën bevatten een rijke set functies en
bieden een ongeëvenaard niveau van bescherming.
Antispam
Antispam is een essentieel onderdeel van elke mailserver. ESET Mail Security
gebruikt de nieuwste antispam-engine die ongewenste e-mail en pogingen tot
phishing zeer efficiënt tegenhoudt. ESET Mail Security heeft opeenvolgende keren
de spamfiltertest van Virus Bulletin gewonnen. Virus Bulletin is een autoriteit op het
gebied van beveiligingstesten en heeft ons een aantal jaar op rij het certificaat
VBSpam+ toegekend. De antispam-engine filtert 99,99% van de ongewenste e-mail
met geen enkel onjuist resultaat, wat het tot een toonaangevende
spambeveiligingstechnologie maakt. ESET Mail Security antispambeveiliging bestaat
uit verschillende technologieën (RBL en DNSBL, 'vingerafdrukken',
reputati econtrole , i nhoudsanalyse , regels, handmatige witte/zwarte lijsten,
backscatterbeveiliging en berichtvalidatie met SPF en DKIM) voor een optimaal
detectieniveau. ESET Mail Security Antispam is op de cloud gebaseerd en de meeste
cloud-databases bevinden zich in ESET-datacenters. Met antispamservices in de
cloud zijn snelle gegevensupdates mogelijk, waardoor sneller kan worden
gereageerd wanneer er zich nieuwe spam aandient.

9
Antiphishing-beveiliging
Een functie die voorkomt dat gebruikers toegang krijgen tot webpagina's waarvan
bekend is dat er phishing plaatsvindt. In e-mailberichten kunnen koppelingen zijn
opgenomen die naar phishingwebpagina's verwijzen en ESET Mail Security maakt
gebruik van een geavanceerde parser die de berichttekst en het onderwerp van
inkomende e-mailberichten doorzoekt om dergelijke koppelingen (URL's) te
identificeren. De koppelingen worden vergeleken met een phishingdatabase.
Regels
Met de regels kunnen beheerders ongewenste e-mails en bijlagen filteren op basis
van het bedrijfsbeleid. Bijlagen zoals uitvoerbare bestanden, multimediabestanden,
archieven die met een wachtwoord zijn beveiligd etc. Er kunnen verschillende acties
worden uitgevoerd met gefilterde e-mailberichten en de bijbehorende bijlagen.
Deze kunnen bijvoorbeeld in quarantaine worden geplaatst, verwijderd,
beantwoord met een melding of in het gebeurtenissenlogboek worden
geregistreerd.
Exporteren naar syslog-
server (Arcsight)
Hiermee kan de inhoud van het logbestand van de beveiliging van de e-mailserver in
CEF-indeling (Common Event Format) worden gedupliceerd naar de server met
systeemlogbestanden om te worden gebruikt met oplossingen voor
logbestandsbeheer, zoals Micro Focus ArcSight. Gebeurtenissen kunnen via
SmartConnector worden ingevoerd in ArcSight of naar bestanden worden
geëxporteerd. Zo worden beveiligingsgebeurtenissen gemakkelijk centraal bewaakt
en beheerd. U kunt met name profiteren van deze functie als u over een complexe
infrastructuur met een groot aantal Microsoft Exchange Servers met de ESET Mail
Security-oplossing beschikt.
Scan van Office 365-postvak
Voor bedrijven die in een hybride Exchange-omgeving werken, bestaat nu de
mogelijkheid om postvakken in de cloud te scannen.
ESET Dynamic Threat
Defense (EDTD)
Op de cloud gebaseerde ESET-service. Wanneer ESET Mail Security een e-mailbericht
als verdacht aanmerkt, wordt het tijdelijk in de ESET Dynamic Threat Defense-
quarantine geplaatst. Een verdacht e-mailbericht wordt automatsch naar de ESET
Dynamic Threat Defense-server verzonden voor analyse door geavanceerde
malwaredetectie-engines. ESET Mail Security ontvangt vervolgens het resultaat van
de analyse. De verwerking van het verdachte bestand hangt af van het resultaat.
Quarantainebeheer voor e-
mail met webinterface
Een beheerder kan objecten in de quarantaine inspecteren en besluiten deze te
verwijderen of vrij te geven. Deze functie biedt een gebruiksvriendelijk
hulpprogramma voor beheer.
Met de quarantainewebinterface kan de inhoud op afstand worden beheerd. Het is
mogelijk om de beheerder te kiezen en/of om toegangsmachtigingen in te stellen.
Bovendien kunnen gebruikers hun eigen ongewenste e-mail inzien en beheren als
ze zijn aangemeld op de quarantainewebinterface voor e-mail, waar ze uitsluitend
toegang hebben tot hun eigen berichten.
E-mailquarantainerapporten
Quarantainerapporten zijn e-mails die worden verzonden aan geselecteerde
gebruikers of beheerders om informatie te geven over alle e-mailberichten die in
quarantaine zijn geplaatst. Het stelt hen ook in staat om inhoud die in quarantaine is
geplaatst op afstand te beheren.
On-demand databasescan
van postvak
On-demand databasescan van postvak stelt beheerders in staat om geselecteerde
postvakken handmatig te scannen of om de scan buiten kantooruren te plannen. De
databasescanner voor postvakken gebruikt de API EWS (Exchange Web Services) om
verbinding te maken met de Microsoft Exchange Server via HTTP/HTTPS. De scanner

10
gebruikt ook parallele uitvoering tijden het scanproces om de prestaties te
verbeteren.
ESET-cluster
Met ESET Cluster kunnen meerdere servers vanaf één locatie worden beheerd. Net
als bij ESET File Security voor Microsoft Windows Server maakt het toevoegen van
serverknooppunten aan een cluster het beheer gemakkelijker, omdat er één
configuratie naar alle knooppunten van een cluster kan worden verspreid. ESET
Cluster kan ook worden gebruikt om greylisting databases te synchroniseren en om
inhoud van de lokale e-mailquarantaine te synchroniseren.
Uitzonderingen voor
processen
Hiermee kunt u specifieke processen uitsluiten van scannen door anti-malware bij
procestoegang. Scannen op anti-malware bij procestoegang kan conflicten
opleveren in bepaalde situaties, bijvoorbeeld tijdens een back-upproces of tijdens
livemigraties van virtuele machines. Deze procesuitsluitingen helpen het risico van
potentiële conflicten te minimaliseren en verbeteren de prestaties van uitgesloten
toepassingen, wat een positief effect heeft op de algehele prestatie en stabiliteit
van het besturingssysteem. Uitsluiting van een proces/toepassing betekent
uitsluiting van diens uitvoerbare bestand (.exe).
eShell (ESET Shell)
eShell 2.0 is nu beschikbaar in ESET Mail Security. eShell is een
opdrachtregelinterface die geavanceerde gebruikers en beheerders de mogelijkheid
geeft om ESET-serverproducten met uitvoerige opties te beheren.
ESET Security Management
Center
Betere integratie met ESET Security Management Center, waaronder de
mogelijkheid om verschillende taken in te plannen. Zie de online-Help van ESET
Security Management Center voor meer informatie.
Op onderdelen gebaseerde
installatie
De installatie kan dusdanig worden aangepast dat het alleen bepaalde onderdelen
van het product bevat.
2.2 Nieuwe functies
Nieuwe functies en verbeteringen in ESET Mail Security, vergeleken met de vorige generatie (versie 6.x):
· Echte 64-bits productkern
· Scan van Office 365-postvak
· Antiphishing-beveiliging voor e-mail
· Backscatterbeveiliging
· Uitgebreide regels (nieuwe voorwaarden en acties toegevoegd, bijvoorbeeld een voorwaarde voor de
hoofdtekst van een bericht)
· Verbeterde quarantaineplaatsing voor e-mailbijlagen
· E-mailquarantainerapport voor de beheerder
· Synchronisatie van lokale mail in quarantaine via ESET Cluster
· Logboek SMTP-beveiliging
· ESET Dynamic Threat Defense
· Onde rsteuni ng voor ESET Enterprise Inspector
· ESET RMM
· Exporteren naar syslog-server (Arcsight)

11
2.3 E-mailflow
In het volgende diagram ziet u de e-mailflow binnen Microsoft Exchange Server en ESET Mail Security. Zie de Help-
pagina's van EDTD voor meer informatie over het gebruik van ESET Dynamic Threat Defense (EDTD) met ESET Mail
Security.
2.4 ESET Mail Security-functies en Exchange Server-rollen
De volgende tabel ziet u welke functies en rollen beschikbaar zijn voor elke ondersteunde versie van Microsoft
Exchange Server. De ESET Mail Security-installatiewizard controleert uw omgeving tijdens de installatie en na de
installatie geeft ESET Mail Security de functies en rollen weer op basis van de gedetecteerde versie van uw
Exchange Server.
Exchange Server-versie en serverrol
Antispam
beveiligin
g
Antiphishi
ng-
beveiliging
Regels
Beveiliging
van e-
mailtransport
On-demand
databasescan
van postvak
Beveiliging
van
postvakdata
base
Microsoft Exchange Server 2007
(meerdere rollen)
Microsoft Exchange Server 2007
(Edge)

12
Exchange Server-versie en serverrol
Antispam
beveiligin
g
Antiphishi
ng-
beveiliging
Regels
Beveiliging
van e-
mailtransport
On-demand
databasescan
van postvak
Beveiliging
van
postvakdata
base
Microsoft Exchange Server 2007
(Hub)
Microsoft Exchange Server 2007
(Mailbox)
Microsoft Exchange Server 2010
(meerdere rollen)
Microsoft Exchange Server 2010
(Edge)
Microsoft Exchange Server 2010
(Hub)
Microsoft Exchange Server 2010
(Mailbox)
Microsoft Exchange Server 2013
(meerdere rollen)
Microsoft Exchange Server 2013
(Edge)
Microsoft Exchange Server 2013
(Mailbox)
Microsoft Exchange Server 2016
(Edge)
Microsoft Exchange Server 2016
(Mailbox)
Microsoft Exchange Server 2019
(Edge)
Microsoft Exchange Server 2019
(Mailbox)
Windows Small Business Server 2008
SP2
Windows Small Business Server 2011

13
2.5 Exchange Server-rollen
De edge- en de hubrol
Bij zowel edgetransportservers als hubtransportservers zijn antispamfuncties standaard uitgeschakeld. Dit is de
gewenste configuratie in een Exchange-organisatie met een edgetransportserver. Wij raden aan dat u op de
edgetransportserver met ESET Mail Security antispam zodanig configureert dat berichten worden gefilterd alvorens
ze naar de Exchange-organisatie worden gerouteerd.
De edgefunctie is de voorkeurslocatie om op spam te scannen omdat ESET Mail Security hierdoor spam al vroeg in
het proces kan afwijzen voordat er onnodige inspanningen van de netwerklagen worden gevraagd. Met een
dergelijke configuratie worden binnenkomende berichten gefilterd door ESET Mail Security op de
edgetransportserver. Ze worden dus veilig naar de hubtransportserver verplaatst zonder dat er verder gefilterd
hoeft te worden.
Als uw organisatie geen edgetransportserver gebruikt en alleen een hubtransportserver heeft, raden wij aan dat u
antispamfuncties op de hubtransportserver inschakelt die via SMTP binnenkomende berichten van internet
ontvangt.
OPMERKING
Vanwege de technische beperkingen van Microsoft Exchange 2013 en nieuwere versies, biedt ESET Mail
Security geen ondersteuning voor een Microsoft Exchange Server-implementatie met alleen de CAS-rol
(standalone Client Access Server).
2.6 POP3-connector en antispam
In versies van Microsoft Windows Small Business Server (SBS) is een eigen POP3-connector ingebouwd waarmee de
server e-mailberichten kan ophalen bij externe POP3-servers. De implementatie van deze eigen POP3-connector
van Microsoft verschilt per SBS-versie.
ESET Mail Security biedt ondersteuning voor de Microsoft SBS POP3-connector, mits deze juist wordt
geconfigureerd. Berichten die worden gedownload via de Microsoft POP3-connector, worden gescand op de
aanwezigheid van spam. Antispambeveiliging voor deze berichten is mogelijk omdat de POP3-connector e-
mailberichten van een POP3-account via SMTP doorstuurt naar Microsoft Exchange Server.
ESET Mail Security is op de volgende SBS-systemen getest met populaire e-mailservices zoals Gmail.com,
Outlook.com, Yahoo.com, Yandex.com en gmx.de:
· Microsoft Windows Small Business Server 2008 SP2
· Microsoft Windows Small Business Server 2011
BELANGRIJK
Als u gebruikmaakt van de ingebouwde Microsoft SBS POP3-connector en alle e-mailberichten laat scannen op
spam, druk dan op F5 om naar Geavanceerde instellingen te gaan, navigeer naar Server > Beveiliging van e-
mailtransport > Geavanceerde instellingen en kies bij de instelling Ook berichten scannen die worden
ontvangen van geverifieerde of interne verbindingen de opti e Antivirus-, Antiphishing- en
Antispambeveiliging in de vervolgkeuzelijst. Zo zorgt u voor antispambeveiliging voor e-mail die bij POP3-
account(s) wordt opgehaald.
U kunt ook een POP3-connector van een derde gebruiken, zoals P3SS (in plaats van de ingebouwde Microsoft SBS
POP3-connector).

14
2.7 Beveiligingsmodules
De kernfunctionaliteit van ESET Mail Security omvat de volgende beveiligingsmodules:
Antivirus
Antivirusbeveiliging is een van de basisfuncties van ESET Mail Security. Antivirusbeveiliging biedt bescherming
tegen kwaadwillende systeemaanvallen door middel van controle over bestanden, e-mail en
internetcommunicatie. Als een bedreiging met schadelijke code wordt gedetecteerd, kan de antivirusmodule deze
onschadelijk maken door de code te blokkeren en deze vervolgens op te schonen, te verwijderen of in Quarantaine
te plaatsen.
Antispam
Antispambeveiliging bestaat uit verschillende technologieën (RBL, DNSBL, 'vingerafdrukken', reputatiecontrole,
inhoudsanalyse, regels, handmatige witte/zwarte lijsten, enzovoort) om e-mailbedreigingen maximaal te kunnen
detecteren.
ESET Mail Security Antispam is op de cloud gebaseerd en de meeste cloud-databases bevinden zich in ESET-
datacenters. Met antispamservices in de cloud zijn snelle gegevensupdates mogelijk, waardoor sneller kan worden
gereageerd wanneer er zich nieuwe spam aandient. Ook kunnen hierdoor onjuiste of valse gegevens worden
verwijderd van de zwarte lijsten van ESET. Communicatie met antispamservices in de cloud vindt indien mogelijk
plaats via een eigen protocol op poort 53535. Als het niet mogelijk is om via het eigen protocol van ESET te
communiceren, worden in plaats daarvan DNS -services gebruikt (poort 53). Het gebruik van DNS is echter minder
effectief, want hierbij moeten meerdere aanvragen worden verzonden tijdens het spamclassificatieproces voor
één e-mailbericht.
OPMERKING
Wij raden aan dat u TCP/UDP-poort 53535 opent voor de IP-adressen die staan vermeld in dit artikel in de
kennisbank . Deze poort wordt door ESET Mail Security gebruikt voor het verzenden van aanvragen.
Gewoonlijk worden tijdens het spamclassificatieproces geen e-mailberichten of onderdelen daarvan verzonden.
Maar als ESET LiveGrid® is ingeschakeld en u hebt expliciet toegestaan dat er voorbeelden worden ingediend ter
analyse, worden alleen berichten die zijn aangemerkt als spam (of zeer waarschijnlijk spam) mogelijk verzonden
ten behoeve van een grondige analyse en verbetering van de cloud-database.
Zi e ons KB-artikel voor nadere inlichtingen als u gevallen van valspositieve of -negatieve spamclassificatie wilt
melden.
Voorts kan ESET Mail Security ook de Greylisting-methode gebruiken (standaard uitgeschakeld) om spam te filteren.
Anti-Phishing
ESET Mail Security biedt antiphishingbeveiliging, waarmee wordt voorkomen dat gebruikers toegang hebben tot
webpagina's waarvan bekend is dat er phishing plaatsvindt. In het geval van e-mailberichten waarin koppelingen
naar phishingwebpagina's zijn opgenomen, maakt ESET Mail Security gebruik van een geavanceerde parser die het
tekstgedeelte van het bericht en het onderwerp van inkomende e-mailberichten doorzoekt om dergelijke
koppelingen (URL's) te identificeren. De koppelingen worden vergeleken met een phishingdatabase en regels met
voorwaarden Tekstgedeelte van bericht worden geëvalueerd.
Regels

15
De beschikbaarheid van regels voor Beveiliging van postvakdatabase, On-demand databasescan van postvak en
Beveiliging van e-mailtransport op uw systeem, hangt af van de versie van Microsoft Exchange Server die op de
server met ESET Mail Security is geïnstalleerd.
Met regels kunt u handmatig voorwaarden voor e-mailfiltering en te nemen acties bij gefilterde e-mails definiëren.
Er zijn verschillende sets met voorwaarden en acties. U kunt individuele regels maken die ook gecombineerd
kunnen worden. Als er in één regel meerdere voorwaarden worden gebruikt, worden de voorwaarden gekoppeld
met de logische operator AND. Zodoende wordt de regel alleen uitgevoerd als aan alle voorwaarden wordt voldaan.
Als er meerdere regels worden gemaakt, wordt de logische operator OR toegepast. Dit betekent dat de eerste regel
waarvan aan de voorwaarden wordt voldaan wordt uitgevoerd.
In de scanvolgorde is greylisting de eerste techniek die wordt gebruikt (indien ingeschakeld). Daarop volgende
procedures voeren altijd de volgende technieken uit: beveiliging op basis van door de gebruiker gedefinieerde
regels, gevolgd door een antivirusscan en ten slotte een antispamscan.
2.8 Meervoudige beveiliging
ESET Mail Security biedt complexe beveiliging op verschillende niveaus:
· Beveiliging van postvakdatabase
· Beveiliging van e-mailtransport
· On-demand databasescan van postvak
· Scan van Office 365-postvak
OPMERKING
Voor een compleet overzicht ziet u de matrix van ESET Mail Security-functies en Microsoft Exchange Server-
versies en de bijbehorende rollen.
2.8.1 Beveiliging van postvakdatabase
Het scannen van postvakken wordt geactiveerd en beheerd door de Microsoft Exchange Server. E-mails in de
opslagdatabase van Microsoft Exchange Server worden voortdurend gescand. Afhankelijk van de versie van
Microsoft Exchange Server, de VSAPI-interfaceversie en de door de gebruiker gedefinieerde instellingen, kan het
scannen worden geactiveerd in elk van de volgende situaties:
· Wanneer de gebruiker zijn e-mail opent, bijvoorbeeld in een e-mailclient (e-mail wordt altijd gescand met de
nieuwste detectie-engine).
· Op de achtergrond wanneer het gebruik van de Microsoft Exchange Server laag is.
· Proactief (op basis van het eigen algoritme van de Microsoft Exchange Server).
OPMERKING
Beveiliging van postvakdatabase is niet beschikbaar voor Microsoft Exchange Server 2013, 2016 en 2019.
Beveiliging van postvakdatabase is beschikbaar voor de volgende systemen:
Exchange Server-versie en serverrol
Antispamb
eveiliging
Antiphishing
-beveiliging
Regels
Beveiliging
van e-
mailtranspo
rt
On-demand
databasesca
n van
postvak
Beveiliging
van
postvakdata
base
Microsoft Exchange Server 2007
(Mailbox)

16
Exchange Server-versie en serverrol
Antispamb
eveiliging
Antiphishing
-beveiliging
Regels
Beveiliging
van e-
mailtranspo
rt
On-demand
databasesca
n van
postvak
Beveiliging
van
postvakdata
base
Microsoft Exchange Server 2007
(meerdere rollen)
Microsoft Exchange Server 2010
(Mailbox)
Microsoft Exchange Server 2010
(meerdere rollen)
Windows Small Business Server 2008
SP2
Windows Small Business Server 2011
Dit scantype kan worden uitgevoerd op een enkele serverinstallatie met meerdere Exchange Server-functies op
een computer (zolang deze de functie Postvakserver of Back-endserver heeft).
2.8.2 Beveiliging van e-mailtransport
SMTP-filtering op serverniveau wordt beveiligd met een speciale invoegtoepassing. In Microsoft Exchange Server
2007 en 2010 wordt de plug-in als een transportagent geregistreerd op de edge- of hubrol van de Microsoft
Exchange Server.
SMTP-filtering op serverniveau door een transportagent biedt beveiliging in de vorm van antivirus, antispam en
door de gebruiker gedefinieerde regels. In tegenstelling tot VSAPI-filtering wordt SMTP-filtering op serverniveau
uitgevoerd voordat de gescande e-mail arriveert in het postvak van Microsoft Exchange Server.
Voorheen bekend als berichtfiltering op het niveau van de SMTP-server. Deze beveiliging wordt geleverd door de
transportagent en is alleen beschikbaar voor Microsoft Exchange Server 2007 of nieuwer die de functie
Edgetransportserver of Hubtransportserver uitvoert. Dit scantype kan worden uitgevoerd op een enkele
serverinstallatie met meerdere Exchange Server-functies op een computer (zolang deze een van de genoemde
functies heeft).
Beveiliging van e-mailtransport is beschikbaar voor de volgende systemen:
Exchange Server-versie en
serverrol
Antispamb
eveiliging
Antiphishin
g-
beveiliging
Regels
Beveiliging
van e-
mailtranspor
t
On-demand
databasescan
van postvak
Beveiliging
van
postvakdata
base
Microsoft Exchange Server 2007
(Hub)
Microsoft Exchange Server 2007
(Edge)
Microsoft Exchange Server 2010
(meerdere rollen)

17
Exchange Server-versie en
serverrol
Antispamb
eveiliging
Antiphishin
g-
beveiliging
Regels
Beveiliging
van e-
mailtranspor
t
On-demand
databasescan
van postvak
Beveiliging
van
postvakdata
base
Microsoft Exchange Server 2013
(meerdere rollen)
Microsoft Exchange Server 2013
(Edge)
Microsoft Exchange Server 2013
(Mailbox)
Microsoft Exchange Server 2016
(Edge)
Microsoft Exchange Server 2016
(Mailbox)
Microsoft Exchange Server 2019
(Edge)
Microsoft Exchange Server 2019
(Mailbox)
Windows Small Business Server
2008 SP2
Windows Small Business Server
2011
2.8.3 On-demand databasescan van postvak
Hiermee kunt u een databasescan van een Exchange-postvak uitvoeren of plannen. Deze functie is alleen
beschikbaar voor Microsoft Exchange Server 2007 of nieuwer waarop de functiePostvakserver of Hubtransport wordt
uitgevoerd. Dit is ook van toepassing op een enkele serverinstallatie met meerdere Exchange Server-functies op
een computer (zolang deze een van de genoemde functies heeft).
On-demand databasescans van postvakken zijn beschikbaar voor de volgende systemen:
Exchange Server-versie en
serverrol
Antispamb
eveiliging
Antiphishing
-beveiliging
Regels
Beveiliging
van e-
mailtranspo
rt
On-demand
databasescan
van postvak
Beveiliging
van
postvakdataba
se
Microsoft Exchange Server 2007
(meerdere rollen)
Microsoft Exchange Server 2007
(Hub)
Microsoft Exchange Server 2007
(Mailbox)

18
Exchange Server-versie en
serverrol
Antispamb
eveiliging
Antiphishing
-beveiliging
Regels
Beveiliging
van e-
mailtranspo
rt
On-demand
databasescan
van postvak
Beveiliging
van
postvakdataba
se
Microsoft Exchange Server 2010
(meerdere rollen)
Microsoft Exchange Server 2010
(Hub)
Microsoft Exchange Server 2010
(Mailbox)
Microsoft Exchange Server 2013
(meerdere rollen)
Microsoft Exchange Server 2013
(Mailbox)
Microsoft Exchange Server 2016
(Mailbox)
Microsoft Exchange Server 2019
(Mailbox)
Windows Small Business Server
2008 SP2
Windows Small Business Server
2011

19
2.8.4 Scan van Office 365-postvak
ESET Mail Security biedt scanfunctionaliteit voor hybride Office 365-omgevingen. Deze functionaliteit is alleen
beschikbaar en zichtbaar in ESET Mail Security als u een hybride Exchange-omgeving hebt (lokaal en in de cloud).
Beide routeringsscenario's worden ondersteund, via Exchange Online of via de lokale organisatie. Zie
Transportroutering in hybride Exchange-implementaties voor meer informatie.
U kunt externe Office 365-postvakken en openbare mappen op dezelfde manier scannen als u bij een traditionele
On-demand databasescan van postvak zou doen.
Het uitvoeren van een volledige databasescan in grote omgevingen kan tot een ongewenste systeembelasting
leiden. Vermijd dit probleem door een scan uit te voeren op specifieke databases of postvakken. Gebruik het
tijdfilter boven in het venster om de invloed op het system verder te minimaliseren. Een voorbeeld: in plaats van
Alle berichten scannen kunt u Berichten scannen die in de afgelopen week zijn gewijzigd.
Wij raden u aan uw Office 365-account te configureren. Druk op de toets F5 en navigeer naar Server > On-demand
databasescan van postvak. Zie ook Details van databaseaccountscan.
Raadpleeg Logbestanden > Databasescan van postvak om de activiteit van de Office 365-postvakscan te zien.

20
3. Voorbereiden op installatie
Er zijn enkele stappen die wij u aanraden uit te voeren bij het voorbereiden van de installatie van het product:
· Downl oad he t .msi- install ati epakke t op de website van ESET nadat u ESET Mail Security hebt gekocht.
· Zorg dat de server waarop u ESET Mail Security wilt installeren, voldoet aan de systeemvereisten.
· Meld u met een beheerdersaccount aan bij de server.
OPMERKING
Let op: u moet het installatieprogramma uitvoeren met gebruik van het ingebouwde beheerdersaccount of
een domeinbeheerdersaccount (als het lokale beheerdersaccount is uitgeschakeld). Een andere gebruiker,
ook al is deze lid van de groep Beheerders, heeft niet voldoende toegangsrechten. Daarom moet u het
ingebouwde beheerdersaccount gebruiken, want u kunt de installatie niet met succes volbrengen onder een
ander gebruikersaccount dan dat van de lokale beheerder of de domeinbeheerder.
· Als u een upgrade van een bestaande installatie van ESET Mail Security wilt uitvoeren, raden wij aan met de
functie Instellingen exporteren een back-up van de huidige configuratie te maken.
· Verwijder alle antivirussoftware van uw systeem, indien van toepassing. Wij raden aan hiervoor ESET AV
Remover te gebruiken. Zie dit KB-artikel voor een lijst met antivirussoftware van derden die met ESET AV
Remover kan worden verwijderd.
· Als u installeert ESET Mail Security op Windows Server 2016 adviseert Microsoft om de functies van
Windows Defender te verwijderen en uw inschrijving bij Windows Defender ATP te beëindigen, om
problemen te voorkomen die worden veroorzaakt als er meerdere antivirusproducten op een machine zijn
geïnstalleerd.
· Voor een compleet overzicht ziet u de matrix van ESET Mail Security-functies en Microsoft Exchange Server-
versies en de bijbehorende rollen.
· U kunt het aantal postvakken controleren door het hulpprogramma Aantal postvakken uit te voeren. Zie ons
kennisbankartikel voor meer informatie. Nadat ESET Mail Security is geïnstalleerd, wordt het huidige aantal
postvakken weergegeven onderaan in het venster Controle.
U kunt het installatieprogramma van ESET Mail Security in twee installatiemodi uitvoeren:
· Grafische gebruikersinterface (GUI)
Dit is het aanbevolen installatietype in de vorm van een installatiewizard.
· Stille installatie/installatie zonder toezicht
Afgezien van de installatiewizard kunt u ESET Mail Security ook stil via de opdrachtregel installeren.
BELANGRIJK
Wij adviseren ten sterkste om ESET Mail Security te installeren op een zojuist geïnstalleerd en geconfigureerd
besturingssysteem, voor zover dat mogelijk is. Als u het product toch op een bestaand systeem moet
installeren, adviseren wij u de vorige versie van ESET Mail Security te verwijderen, de server opnieuw op te
starten en daarna de nieuwe ESET Mail Security te installeren.
· Upgrade uitvoeren naar een nieuwere versie
Als u een oudere versie van ESET Mail Security gebruikt, kunt u een geschikte upgrademethode kiezen.

21
Nadat u ESET Mail Security hebt geïnstalleerd of een upgrade hebt uitgevoerd, zijn dit de vervolgactiviteiten:
· Productactivering
De beschikbaarheid van de activeringsmethoden in het activeringsvenster kan per land verschillen en is
afhankelijk van de distributiemethode.
· Taken na afloop van de installatie
Zie de lijst met aanbevolen taken die u kunt uitvoeren na een geslaagde installatie van ESET Mail Security.
· Serverbeveiliging configureren
U kunt ESET Mail Security fijnregelen door geavanceerde instellingen van elke functie te wijzigen, zodat deze
beter aansluiten op uw behoeften.
3.1 Systeemvereisten
Ondersteunde besturingssystemen:
· Microsoft Windows Server 2019 (Server Core- en desktopervaring)
· Microsoft Windows Server 2016
· Microsoft Windows Server 2012 R2
· Microsoft Windows Server 2012
· Microsoft Windows Server 2008 R2 SP1
· Microsoft Windows Server 2008 SP2 (x64)
· Microsoft Windows Small Business Server 2011 (x64)
· Microsoft Windows Small Business Server 2008 SP2 (x64)
Ondersteunde versies van Microsoft Exchange Server:
· Microsoft Exchange Server 2019 CU1, CU2, CU3, CU4, CU5
· Microsoft Exchange Server 2016 CU1, CU2, CU3, CU4, CU5, CU6, CU7, CU8, CU9, CU10, CU11, CU12, CU13, CU14,
CU15, CU16
· Microsoft Exchange Server 2013 CU2, CU3, CU5, CU6, CU7, CU8, CU9, CU10, CU11, CU12, CU13, CU14, CU15, CU16,
CU17, CU18, CU19, CU20, CU21, CU22, CU23
· Microsoft Exchange Server 2010 SP1, SP2, SP3, UR27
· Microsoft Exchange Server 2007 SP1, SP2, SP3
OPMERKING
SP1, ook bekend als CU4, op Microsoft Exchange Server 2013 wordt niet ondersteund door ESET Mail Security.
Minimale hardwarevereisten:
Onderdeel
Vereiste
Processor
Intel of AMD single-core x86 of x64
Geheugen
256 MB aan vrij geheugen
Vaste schijf
700 MB aan vasteschijfruimte
Schermresolutie
800x600 pixels of hoger
ESET Mail Security heeft dezelfde aanbevolen hardwarevereisten als die van toepassing zijn op Microsoft Exchange
Server. Zie de volgende technische artikelen van Microsoft voor meer informatie:
Microsoft Exchange Server 2007

22
Microsoft Exchange Server 2010
Microsoft Exchange Server 2013
Microsoft Exchange Server 2016
OPMERKING
Wij adviseren u dringend het nieuwste servicepack voor uw Microsoft Server-besturingssysteem en
servertoepassing te installeren voordat u het ESET-beveiligingsproduct installeert. Ook raden wij u aan de
nieuwste Windows-updates en -hotfixes te installeren wanneer die beschikbaar zijn.
3.2 Installatiestappen voor ESET Mail Security
Dit is de standaard GUI-installatiewizard. Dubbelklik op het .msi-pakket en volg de stappen om ESET Mail Security te
installeren:
1. Kl ik op Volgende om door te gaan of klik op Annuleren als u de installatie wilt afsluiten.
2. De installatiewizard wordt uitgevoerd in de taal die staat aangegeven in de instelling Thuislocatie van een
Regio > Locatie van uw besturingssysteem (of de instelling Huidige locatie van ee n Regio en taal > Locatie in
oudere systemen). Gebruik het vervolgkeuzemenu om de Producttaal te selecteren waarin ESET Mail
Security wordt geïnstalleerd. De geselecteerde taal voor ESET Mail Security staat los van de taal die u in de
installatiewizard ziet.
3. Kl ik op Volgende. De licentieovereenkomst voor eindgebruikers wordt weergegeven. Nadat u de
Licentieovereenkomst voor eindgebruikers en het Privacybeleid hebt gelezen en ermee akkoord bent
gegaan, klikt u op Volgende.

23
4. Kies een van de beschikbare installatietypen (beschikbaarheid is afhankelijk van uw besturingssysteem):
Volledig
Hiermee installeert u alle functies van ESET Mail Security. Dit wordt ook wel een volledige installatie genoemd.
Dit is het aanbevolen installatietype, beschikbaar voor Windows Server 2012, 2012 R2, 2016 en 2019.
OPMERKING
Al s u Lokale quarantaine wilt gebruiken voor e-mailberichten en niet wilt dat in quarantaine geplaatste
berichten bij u op station C: worden opgeslagen, wijzigt u het pad van Gegevensmap in een station en locatie
die u voorkeur hebben. Onthoud echter dat alle ESET Mail Security-gegevensbestanden op deze locatie
worden opgeslagen.

24
Typisch
Hiermee installeert u de aanbevolen functies van ESET Mail Security. Beschikbaar voor Windows Server 2008
SP2, 2008 R2 SP1, Windows Small Business Server 2008 SP2 en 2011.
OPMERKING
Op Windows Server 2008 SP2 en Windows Server 2008 R2 SP1 is de installatie van het onderdeel
Netwerkbeveiliging standaard uitgeschakeld (installatietype Standaard). Als u dit onderdeel wilt installeren,
kiest u het installatietype Aangepast.
Aangepast

25
Hierbij kunt u selecteren welke functies van ESET Mail Security op uw systeem worden geïnstalleerd. Er wordt
een lijst met productmodules en functies weergegeven voordat de installatie begint. Dit is nuttig als u ESET
Mail Security wilt aanpassen en alleen de onderdelen wilt installeren die u nodig hebt.
5. U wordt gevraagd de locatie te selecteren waar ESET Mail Security wordt geïnstalleerd. Standaard wordt het
programma geïnstalleerd in C:\Program Files\ESET\ESET Mail Security. Klik op Bladeren om deze locatie te
wijzigen (niet aanbevolen).

26
6. Kl ik op Installeren om te beginnen met de installatie. Wanneer de installatie voltooid is, wordt de grafische
gebruikersinterface van ESET opgestart en wordt het systeemvakpictogram weergegeven in het
systeemvak.

27
3.2.1 Een bestaande installatie wijzigen
U kunt onderdelen toevoegen aan en verwijderen uit uw installatie. Voer hiervoor het .msi-installatiepakket uit dat
u tijdens de eerste installatie hebt gebruikt of ga naar Programma's en onderdelen (toegankelijk vanuit het
Configuratiescherm), klik met de rechtermuisknop op ESET Mail Security en selecteer Wijzigen. Volg de
onderstaande stappen om onderdelen toe te voegen of verwijderen.
Er zijn 3 opties beschikbaar. U kunt geïnstalleerde onderdelen Wijzigen, uw installatie van ESET Mail Security
Herstellen of vol le dig Verwijderen.
Als u voor Wijzigen kiest, wordt er een lijst met beschikbare programmaonderdelen weergegeven. Kies de
onderdelen die u wilt toevoegen of verwijderen. U kunt meerdere onderdelen tegelijk toevoegen/verwijderen.
Klik op het onderdeel en selecteer een optie in het vervolgkeuzemenu:

28
Wanneer u een optie hebt geselecteerd, klikt u op Aanpassen om de wijzigingen door te voeren.
OPMERKING
u kunt geïnstalleerde onderdelen op elk moment aanpassen door het installatieprogramma uit te voeren. Voor
de meeste onderdelen is het niet nodig de server opnieuw op te starten om de wijziging door te voeren. De
grafische gebruikersinterface wordt opnieuw gestart en u ziet alleen de onderdelen die u hebt gekozen om te
installeren. Voor onderdelen waarvoor de server opnieuw moet worden opgestart, vraagt het Windows-
installatieprogramma u de server opnieuw op te starten. Wanneer de server weer online is, zijn de nieuwe
onderdelen beschikbaar.
3.3 Stille installatie/installatie zonder toezicht
Voer de volgende opdracht uit om de installatie stil (zonder gebruikersinterface) op de opdrachtregel uit te voeren:
msiexec /i <packagename> /qn /l*xv msi.log
OPMERKING
Op Windows Server 2008 SP2 en Windows Server 2008 R2 SP1 wordt de functie Netwerkbeveiliging niet
geïnstalleerd.
Als u wilt controleren of de installatie geslaagd is of als er problemen zijn met de installatie, kunt u met behulp van
Windows Gebeurtenislogboeken het logboek Toepassingen bekijken (zoek naar records uit de bron: MsiInstaller).
VOORBEELD
Volledige installatie op een 64-bits systeem:
msiexec /i emsx_nt64.msi /qn /l*xv msi.log ADDLOCAL=NetworkProtection,RealtimeProtection,^
DeviceControl,DocumentProtection,Cluster,GraphicUserInterface,SysInspector,SysRescue,Rmm,eula

29
Wanneer de installatie wordt afgerond, wordt de grafische gebruikersinterface van ESET gestart en wordt het
systeemvakpictogram weergegeven in het systeemvak.
VOORBEELD
Installatie van het product in de opgegeven taal (Duits):
msiexec /i emsx_nt64.msi /qn ADDLOCAL=NetworkProtection,RealtimeProtection,^
DeviceControl,DocumentProtection,Cluster,GraphicUserInterface,^
SysInspector,SysRescue,Rmm,eula PRODUCT_LANG=1031 PRODUCT_LANG_CODE=de-de
Zie Taalparameters in Installatie op opdrachtregel voor meer informatie en de lijst met taalcodes.
BELANGRIJK
Wanneer u waarden opgeeft voor de parameter REINSTALL, moet u de overige functies die niet worden
gebruikt vermelden als waarden voor de parameter ADDLOCAL of de parameter REMOVE. Om de installatie via de
opdrachtregel goed te laten verlopen is het nodig dat u alle functies vermeldt als waarden voor de parameter
REINSTALL, ADDLOCAL en de parameter REMOVE. Toevoegen of verwijderen is mogelijk niet succesvol als u de
parameter REINSTALL niet gebruikt.
Zie het gedeelte Installatie via de opdrachtregel voor de complete lijst met functies.
VOORBEELD
Volledig verwijderen (de-installatie) op een 64-bits systeem:
msiexec /x emsx_nt64.msi /qn /l*xv msi.log
OPMERKING
Na een succesvolle installatie wordt uw server automatisch opnieuw opgestart.
3.3.1 Installatie vanaf opdrachtregel
De volgende instellingen zijn alleen bestemd voor gebruik met het niveau gereduceerd, basis en geen van de
gebruikersinterface. Zie de documentatie v oor de msiexec-versie gebruikt voor de juiste in-/uitschakelingen op
de opdrachtregel.
Ondersteunde parameters:
APPDIR=<pad>
· pad: geldig mappad
· Map voor toepassingsinstallatie
· Bijvoorbeeld: emsx_nt64.msi /qn APPDIR=C:\ESET\ ADDLOCAL=DocumentProtection
APPDATADIR=<pad>
· pad: geldig mappad
· Map voor installatie van toepassingsgegevens
MODULEDIR=<pad>
· pad - geldig mappad
· Map voor module-installatie
ADDLOCAL=<lijst>

30
· Installatie van onderdelen: lijst met niet-verplichte functies die lokaal worden geïnstalleerd.
· Gebruik met ESET .msi-pakketten: emsx_nt64.msi /qn ADDLOCAL=<list>
· Voor meer informatie over de eigenschap ADDLOCAL verwijzen wij u naar https://docs.microsoft.com/en-gb/
windows/desktop/Msi/addlocal
· De ADDLOCAL-lijst is een door komma's gescheiden lijst met alle functies die worden geïnstalleerd.
· Bij het selecteren van een functie die moet worden geïnstalleerd, moet het volledige pad (alle
bovenliggende functies) expliciet worden opgenomen in de lijst.
REMOVE=<list>
· Onderdeelinstallatie: bovenliggende functie die u niet geïnstalleerd wilt hebben.
· Gebruik met ESET .msi-pakketten: emsx_nt64.msi /qn REMOVE=<list>
· Voor meer informatie over de eigenschap REMOVE verwijzen wij u naar https://docs.microsoft.com/en-gb/
windows/desktop/Msi/remove
· De l ij st REMOVE is een lijst met door komma's gescheiden waarden van bovenliggende functies die niet
worden geïnstalleerd (of die worden verwijderd in het geval van een bestaande installatie).
· Het is onvoldoende alleen de bovenliggende functie aan te geven. Het is niet nodig om elke onderliggende
functie expliciet in de lijst op te nemen.
ADDEXCLUDE=<list>
· De ADDEXCLUDE-lijst is een lijst met door komma's gescheiden waarden met alle functienamen die niet
worden geïnstalleerd.
· Wanneer een functie wordt geselecteerd die niet moet worden geïnstalleerd, moeten het gehele pad (d.w.z.
alle onderliggende functies ervan) en alle verwante, onzichtbare functies expliciet in de lijst worden
opgenomen.
· Bijvoorbeeld: emsx_nt64.msi /qn ADDEXCLUDE=<list>
OPMERKING
ADDEXCLUDE kan niet worden gebruikt in combinatie met ADDLOCAL.
Aanwezigheid van functies
· Verplicht: de functie wordt altijd geïnstalleerd.
· Optioneel : de selectie van de functie kan ongedaan worden gemaakt voor de installatie.
· Onzichtbaar: logische functie die verplicht is, omdat anders andere functies niet naar behoren werken.
Lijst met functies van ESET Mail Security:
BELANGRIJK
De namen van alle functies zijn hoofdlettergevoelig. RealtimeProtection bijvoorbeeld is niet hetzelfde als
REALTIMEPROTECTION.
Functienaam
Aanwezigheid van functies
SERVER
Verplicht
RealtimeProtection
Verplicht
MAILSERVER
Verplicht
WMIProvider
Verplicht
HIPS
Verplicht
Updater
Verplicht
eShell
Verplicht

31
Functienaam
Aanwezigheid van functies
UpdateMirror
Verplicht
DeviceControl
Optioneel
DocumentProtection
Optioneel
WebAndEmail
Optioneel
ProtocolFiltering
Onzichtbaar
NetworkProtection
Optioneel
IdsAndBotnetProtection
Optioneel
Rmm
Optioneel
WebAccessProtection
Optioneel
EmailClientProtection
Optioneel
MailPlugins
Onzichtbaar
Cluster
Optioneel
_Base
eula
ShellExt
Optioneel
_FeaturesCore
GraphicUserInterface
Optioneel
SysInspector
Optioneel
SysRescue
Optioneel
EnterpriseInspector
Optioneel
Als u een van de volgende functies wilt verwijderen, moet u de hele groep verwijderen door elke functie aan te
geven die tot de groep behoort: Anders wordt de functie niet verwijderd. Hier zijn twee groepen (elke regel
vertegenwoordigt een groep):
GraphicUserInterface,ShellExt
NetworkProtection,WebAccessProtection,IdsAndBotnetProtection,ProtocolFiltering,MailPlugins,EmailClientProtection
VOORBEELD
Sluit het gedeelte Netwerkbeveiliging uit (ook onderliggende functies) van installatie met de parameter
REMOVE en door alleen de bovenliggende functie op te geven:
msiexec /i emsx_nt64.msi /qn ADDLOCAL=ALL REMOVE=NetworkProtection
Of u kunt de parameter ADDEXCLUDE gebruiken, maar u moet dan ook alle onderliggende functies opgeven:
msiexec /i emsx_nt64.msi /qn ADDEXCLUDE=NetworkProtection,WebAccessProtection,IdsAndBotnetProtection,^
ProtocolFiltering,MailPlugins,EmailClientProtection
Als u wilt dat uw ESET Mail Security na installatie automatisch wordt geconfigureerd, kunt u
basisconfiguratieparameters opgeven in de installatieopdracht.

32
VOORBEELD
Installeer ESET Mail Security en schakel ESET LiveGrid® uit:
msiexec /i emsx_nt64.msi /qn /l*xv msi.log CFG_LIVEGRID_ENABLED=0
Lijst van alle configuratie-eigenschappen:
Schakelaar
Waarde
CFG_POTENTIALLYUNWANTED_ENABLED=1/0
0 - Uitgeschakeld, 1 - Ingeschakeld
CFG_LIVEGRID_ENABLED=1/0
0 - Uitgeschakeld, 1 - Ingeschakeld
FIRSTSCAN_ENABLE=1/0
0 - Uitschakelen, 1 - Inschakelen
CFG_PROXY_ENABLED=0/1
0 - Uitgeschakeld, 1 - Ingeschakeld
CFG_PROXY_ADDRESS=<ip>
IP-adres van proxy
CFG_PROXY_PORT=<port>
Poortnummer van proxy
CFG_PROXY_USERNAME=<user>
Gebruikersnaam voor verificatie
CFG_PROXY_PASSWORD=<pass>
Wachtwoord voor verificatie
Taalparameters: Producttaal (u moet beide parameters opgeven)
Schakelaar
Waarde
PRODUCT_LANG=
LCID-decimaal (landinstellingen-id), bijvoorbeeld 1033 voor English - United
States. Zie de lijst met taalcodes .
PRODUCT_LANG_CODE=
LCID-tekenreeks (naam van taalcultuur) in kleine letters, bijvoorbeeld en-us
voor English - United States. Zie de lijst met taalcodes .

33
3.4 Productactivering
Wanneer de installatie is voltooid, wordt u gevraagd uw product te activeren.
U kunt ESET Mail Security op een van de volgende manieren activeren:
Een gekochte licentiecode gebruiken
Een unieke tekenreeks in de indeling XXXX-XXXX-XXXX-XXXX-XXXX, die wordt gebruikt ter identificatie van de
licentiehouder en voor activering van de licentie.
ESET Business Account
Gebruik deze optie als u geregistreerd bent en uw eigen ESET Business Account (EBA) hebt, waarin uw ESET
Mail Security-licentie is geïmporteerd. U kunt de referenties van de Beveiligingsbeheerder opgeven die u in de
ESET License Administrator-portal gebruikt.
Offlinelicentiebestand
Een automatisch gegenereerd bestand dat wordt overgedragen naar het ESET-product om licentie-informatie te
verstrekken. Uw offlinelicentiebestand wordt gegeneerd bij de licentieportal en wordt gebruikt in omgevingen
waarin de toepassing geen verbinding met de licentieautoriteit kan maken.
Kl ik op Later activeren met ESET Security Management Center als uw computer lid is van een beheerd netwerk en
uw beheerder activering via ESET Security Management Center uitvoert. U kunt deze optie ook gebruiken als u deze
client op een later moment wilt activeren.
Selecteer Help en ondersteuning > Licentie beheren in het hoofdprogrammavenster om uw licentie-informatie op
elk moment te beheren. U ziet de 'publieke id licentie' waarmee uw product door ESET wordt geïdentificeerd en dat
voor licentie-identificatiedoeleinden wordt gebruikt. Uw gebruikersnaam waaronder uw computer is geregistreerd,
bevindt zich in het gedeelte Info. Dit kunt u weergeven door met de rechtermuisknop op het systeemvakpictogram
te klikken.

34
Nadat u ESET Mail Security hebt geactiveerd, wordt het hoofdvenster van het programma geopend en wordt de
huidige status weergegeven op de pagina Controle. Het kan zijn dat er in eerste instantie wat aandacht is vereist. U
wordt bijvoorbeeld gevraagd of u wilt deelnemen aan ESET LiveGrid®.
In het hoofdvenster van het programma worden ook meldingen over andere items weergegeven, zoals
systeemupdates (Windows Updates) of updates voor de detectie-engine. Wanneer alle items die aandacht vereisen
zijn opgelost, wordt de controlestatus groen en wordt de status U bent beveiligd weergegeven.
Als u uw exemplaar van ESET Mail Security rechtstreeks vanuit het programma wilt activeren, klikt u op het
systeemvakpictogram en selecteert u Product is niet geactiveerd in het menu. U kunt uw product ook vanuit het
hoofdmenu activeren onder Help en ondersteuning > Product activeren of de status Controle > Product is niet
geactiveerd.
OPMERKING
ESET Security Management Center kan clientcomputers stilzwijgend activeren met licenties die de beheerder
beschikbaar stelt.
3.4.1 ESET Business Account
Met een ESET Business Account kunt u meerdere licenties beheren. Klik op Account maken als u geen ESET Business
Account hebt. U wordt dan doorgestuurd naar de webportal ESET Business Account waar u zich kunt registreren.
OPMERKING
Zie de gebruikersgids ESET Business Account (EBA) voor meer informatie.
Kl ik op Ik ben mijn wachtwoord vergeten als u Beveiligingsbeheerder-referenties gebruikt en u uw wachtwoord
bent vergeten. U wordt doorgestuurd naar de portal ESET License Administrator. Voer uw e-mailadres in en klik op
Verzenden om te bevestigen. U ontvangt hierna een bericht met instructies voor het opnieuw instellen van uw
wachtwoord.
3.4.2 Activering voltooid
De activering is gelukt. ESET Mail Security is nu geactiveerd. Vanaf nu ontvangt ESET Mail Security regelmatig
updates om de nieuwste bedreigingen te identificeren en om uw computer beveiligd te houden. Klik op Gereed om
de productactivering te voltooien.
3.4.3 Activering mislukt
Activering van ESET Mail Security is mislukt. Zorg dat u de juiste Licentiecode hebt opgegeven of een Offlinelicentie
hebt toegevoegd. Als u een andere Offlinelicentie hebt, voer dit dan opnieuw in. Klik op Licentiecode opnieuw
controleren als u de opgegeven licentiecode wilt controleren of voer een andere licentie in.
3.4.4 Licentie
U wordt gevraagd een licentie te selecteren die bij uw account hoort en die moet worden gebruikt voor ESET Mail
Security. Klik op Doorgaan om met activering door te gaan.

35
3.5 Upgrade uitvoeren naar een nieuwere versie
Er worden nieuwe versies van ESET Mail Security uitgebracht om verbeteringen door te voeren of problemen op te
lossen die niet kunnen worden opgelost met automatische updates van programmamodules.
Upgrademethoden:
· Installatie ongedaan maken / Installeren - Verwijder de oude versie voordat u de nieuwe versie installeert.
Download de nieuwste versie van ESET Mail Security. Exporteer instellingen vanuit uw bestaande ESET Mail
Security als u de configuratie wilt behouden. Verwijder ESET Mail Security en start de server opnieuw op.
Voe r e en schone installatie uit met het installatieprogramma dat u hebt gedownload. Importeer instellingen
om uw configuratie te laden. Wij raden deze procedure aan als u één server hebt waarop ESET Mail Security
wordt uitgevoerd.
· In-place - Een upgrademethode waarbij u de bestaande versie niet verwijdert, maar de nieuwe ESET Mail
Security over de bestaande versie heen installeert.
BELANGRIJK
Het is belangrijk dat u geen Windows-updates in de planning hebt op uw server en ook geen herstart in de
planning hebt vanwege Windows-updates of om andere redenen. Als u een upgrade probeert uit te voeren
met Windows-updates of een herstart in de planning, wordt de bestaande versie van ESET Mail Security
mogelijk niet correct verwijderd. Er treden ook problemen op als u besluit de oude versie van ESET Mail
Security naderhand handmatig te verwijderen.
OPMERKING
De server moet opnieuw worden opgestart tijdens het uitvoeren van de upgrade van ESET Mail Security.
· Extern: voor gebruik in grote netwerkomgevingen die worden beheerd door ESET Security Management
Center. Dit is in de basis een schone upgrademethode, maar dan uitgevoerd op afstand. Deze methode is
handig als u meerdere servers hebt waarop ESET Mail Security wordt uitgevoerd.
· ESET-clusterwizard: kan ook worden gebruikt als upgrademethode. Wij raden deze methode aan bij twee of
meer servers met ESET Mail Security. Dit is in de basis een in-place-upgrade, maar dan uitgevoerd via ESET-
cluster. Verder kunt u ESET-cluster blijven gebruiken en gebruikmaken van de functies ervan nadat de
upgrade eenmaal is voltooid.
BELANGRIJK
Bij upgrades van versie 4.x worden bepaalde instellingen niet bewaard. Regels kunnen bijvoorbeeld niet
worden gemigreerd. Dit komt doordat wijzigingen in de regelfunctie die in latere productversies zijn
geïntroduceerd. Het is raadzaam uw regelinstellingen te noteren voordat u een upgrade van versie 4.x
uitvoert. U kunt regels instellen nadat de upgrade is voltooid. De nieuwe regels geven u meer flexibiliteit en
nog meer mogelijkheden in vergelijking met de regels in de vorige versie van ESET Mail Security.
Hieronder vindt u de instellingen uit eerdere versies van ESET Mail Security die behouden blijven:
· Algemene configuratie van ESET Mail Security.
Instellingen van Antispambeveiliging:
· Alle instellingen die gelijk zijn aan die in eerdere versies. Alle nieuwe instellingen gebruiken
standaardwaarden.
· Vermeldingen op een witte en zwarte lijst.

36
OPMERKING
Wanneer u een upgrade van ESET Mail Security hebt uitgevoerd, raden we aan dat u alle instellingen
controleert om er zeker van te zijn dat deze correct en volgens uw behoeften zijn geconfigureerd.
3.5.1 Upgrade uitvoeren via ESET Security Management Center
Met ESET Security Management Center kunt u op meerdere servers waarop een oudere versie van ESET Mail
Security wordt uitgevoerd een upgrade uitvoeren. Deze methode heeft het voordeel dat op grote aantallen servers
tegelijk een upgrade kan worden uitgevoerd, en tegelijk wordt gegarandeerd dat elke ESET Mail Security hetzelfde
wordt geconfigureerd (indien dit gewenst is).
De procedure bestaat uit de volgende fasen:
· U kunt handmatig een Upgrade uitvoeren van de eerste server door de nieuwste versie van ESET Mail Security
over uw bestaande versie heen te installeren om de gehele configuratie, waaronder regels, diverse witte en
zwarte lijsten, enz., te behouden. Deze fase wordt lokaal uitgevoerd op de server waarop ESET Mail Security
wordt uitgevoerd.
· Configuratie aanvragen van de nieuwe, geüpgradede ESET Mail Security naar versie 7.x en Converteren naar
beleid in ESET Security Management Center. Het beleid wordt later toegepast op alle servers waarop een
upgrade is uitgevoerd. Deze fase wordt extern uitgevoerd met ESMC, evenals de volgende fasen.
· Voer de taak Software verwijderen uit op alle servers waarop de oude versie van ESET Mail Security wordt
uitgevoerd.
· Voer de software-installatie uit op alle servers waarop u de nieuwste versie van ESET Mail Security wilt
uitvoeren.
· Wijs configuratiebeleid toe aan alle servers waarop de nieuwste versie van ESET Mail Security wordt
uitgevoerd.
De procedure stap voor stap:
1. Meld u aan bij een van de servers waarop ESET Mail Security wordt uitgevoerd en voer hierop een upgrade
uit door de nieuwste versie te downloaden en over uw bestaande installatie heen te installeren. Volg de
stappen voor een normale installatie. De oorspronkelijke configuratie van uw oude ESET Mail Security blijft
in zijn geheel behouden tijdens de installatie.
2. Open de webconsole ESET Security Management Center Web Console, selecteer een clientcomputer in de
groep Statisch of Dynamisch en klik op Details weergeven.

37
3. Navigeer naar het tabblad Configuratie en klik op de knop Configuratie aanvragen om de gehele
configuratie van beheerde producten te verzamelen. Het duurt even voordat de configuratie is verzameld.
Wanneer de nieuwste configuratie in de lijst wordt weergegeven, klikt u op Beveiligingsproduct en kiest u
Configuratie openen.

38
4. Maak een configuratiebeleid door te klikken op de knop Converteren naar beleid. Geef de Naam voor een
nieuw beleid op en klik op Voltooien.
5. Ga naar Clienttaken en kies de taak Software verwijderen . Wij raden aan dat u bij het maken van de
verwijdertaak aangeeft dat u de server na het verwijderen opnieuw wilt opstarten door het selectievakje
Automatisch opnieuw opstarten indien nodig in te schakelen. Nadat de taak is gemaakt, voegt u alle
gewenste doelcomputers toe waarop u software wilt verwijderen.
6. Zorg dat ESET Mail Security van alle doelen wordt verwijderd.
7. Maak de taak Software installeren om de nieuwste versie van ESET Mail Security op alle gewenste doelen
te installeren.
8. Wijs configuratiebeleid toe aan alle servers waarop de nieuwste versie van ESET Mail Security wordt
uitgevoerd, idealiter aan een groep.
3.5.2 Upgrade uitvoeren via ESET-cluster
Door e en ESET-cluster te maken kunt u op meerdere servers met een oudere versie van ESET Mail Security een
upgrade uitvoeren. Wij raden aan dat u de ESET-clustermethode gebruikt als u twee of meer servers met ESET Mail
Security in uw omgeving hebt. Een ander voordeel van deze upgrademethode is dat u het ESET-cluster kunt blijven
gebruiken om de ESET Mail Security-configuratie gesynchroniseerd te houden met alle lidknooppunten.
Volg de onderstaande stappen om met deze methode een upgrade uit te voeren:
1. Meld u aan bij een van de servers waarop ESET Mail Security wordt uitgevoerd en voer hierop een upgrade
uit door de nieuwste versie te downloaden en over uw bestaande installatie heen te installeren. Volg de
stappen voor een normale installatie. De oorspronkelijke configuratie van uw oude ESET Mail Security blijft
in zijn geheel behouden tijdens de installatie.
2. Voe r de ESET-clusterwizard uit en voeg clusterknooppunten toe (servers met ESET Mail Security waarop u
een upgrade wilt uitvoeren). Indien nodig kunt u andere servers toevoegen waarop ESET Mail Security nog

39
niet wordt uitgevoerd (hierop wordt een installatie uitgevoerd). Wij raden aan dat u de
standaardinstellingen behoudt wanneer u uw Clusternaam en installatietype opgeeft (zorg ervoor dat
Licentie naar knooppunten pushen zonder geactiveerd product is geselecteerd).
3. Controleer het scherm Logbestand van knooppuntcontrole. Hierin staan servers met een oudere versie en
dat het product opnieuw wordt geïnstalleerd. ESET Mail Security wordt ook geïnstalleerd op alle
toegevoegde servers waarop dit nog niet is geïnstalleerd.

40
4. He t scherm Knooppuntinstallatie en clusteractivering geeft de voortgang van de installatie weer. Wanneer
de installatie is voltooid, lijkt het resultaat in grote lijnen hierop:
Als uw netwerk of DNS niet correct is geconfigureerd, ontvangt u mogelijk het foutbericht Kan activeringstoken niet
bij de server ophalen. Probeer de ESET-clusterwizard nog een keer uit te voeren. Het cluster wordt hierbij
vernietigd en er wordt een nieuw cluster gemaakt (zonder het product opnieuw te installeren) en activering zou
deze keer wel succesvol moeten worden voltooid. Als het probleem blijft bestaan, controleer dan uw netwerk- en
DNS-instellingen.

41
3.6 Installatie in een clusteromgeving
U kunt in ESET Mail Security een clusteromgeving implementeren (bijvoorbeeld in een failovercluster). Wij raden
aan dat u ESET Mail Security in een actief knooppunt installeert en de installatie vervolgens met de functie ESET
Cluster van ESET Mail Security distribueert op een of meer passieve knooppunten. Afgezien van de installatie
fungeert ESET Cluster als replicatie van de ESET Mail Security-configuratie en zorgt voor consistentie tussen
clusterknooppunten, wat nodig is voor de juiste werking.
3.7 Terminalserver
Als u ESET Mail Security installeert op een Windows Server die als een terminalserver fungeert, wilt u de grafische
gebruikersinterface van ESET Mail Security mogelijk uitschakelen om te voorkomen dat die steeds wordt gestart
wanneer er zich een gebruiker aanmeldt. Zie GUI uitschakelen op terminalserver voor specifieke stappen om de
grafische gebruikersinterface uit te schakelen.

42
3.8 Multiserver-/DAG-omgeving
ESET Mail Security ondersteunt omgevingen met meerdere servers. Als uw infrastructuur uit meerdere servers
bestaat, bijvoorbeeld Database Availability Group (DAG), kunt u ESET Mail Security op elke Exchange Server met de
rol van postvak installeren.
De gemakkelijkste manier is om ESET Mail Security te installeren op alle servers die ESET Cluster gebruiken. Ook
raden we aan om Gebruik ESET Cluster om alle in quarantaine geplaatste berichten op één knooppunt te plaatsen in
te schakelen in de instellingen voor E-mailquarantaine. Schake l Synchroniseer greylisting-databases voor ESET-
clusters in als u van plan bent gebruik te maken van Greylisting.

43
4. Aan de slag
Met de informatie in het volgende deel kunt u snel aan de slag met ESET Mail Security.
Taken na afloop van de installatie
Bedoeld om u te helpen met de eerste configuratie.
Controle
Geeft u direct een overzicht van de huidige status van ESET Mail Security. U ziet in één oogopslag of er
problemen zijn die uw aandacht nodig hebben.
Beheerd via ESET Security Management Center
Met ESET Security Management Center kunt u ESET Mail Security op afstand beheren.
4.1 Taken na afloop van de installatie
Hieronder staan aanbevolen taken voor de eerste configuratie van uw ESET Mail Security.
Onderwerp
Beschrijving
Productactivering
Zorg dat uw ESET Mail Security is geactiveerd. U kunt activering op verschillende
manieren uitvoeren.
Bijwerken
Nadat het product is geactiveerd, wordt automatisch een module-update
uitgevoerd. Controleer de updatestatus om te zien of het bijwerken is gelukt.
Quarantainebeheer voor e-mail
Maak kennis met Quarantainebeheer voor e-mail. Deze functie is toegankelijk
in de grafische gebruikersinterface van het programma. Met deze functie kunt u
in quarantaine geplaatste berichten beheren, zoals spam, geïnfecteerde
bijlagen met malware, phishingberichten en berichten die door regels zijn
uitgefilterd. U kunt de details van elk bericht bekijken en actie ondernemen
(vrijgeven of verwijderen).
De webinterface Quarantaine
voor e-mail
De webinterface Quarantaine voor e-mail is een alternatief voor
Quarantainebeheer voor e-mail, waarmee u in quarantaine geplaatste items op
afstand kunt beheren. Verder kunt u met de webinterface Quarantaine voor e-
mail gebruikers (ontvangers van e-mail) toestaan hun eigen in quarantaine
geplaatste berichten te beheren. Gebruikers kunnen rapporten over nieuwe in
quarantaine geplaatste e-mails ontvangen. De rapporten worden per e-mail
verzonden. Wij raden u aan de rapporten te configureren.
E-mailquarantainerapporten
Maak een geplande taak om e-mailquarantainerapporten naar uzelf te
verzenden en naar geselecteerde gebruikers om ze in staat te stellen bepaalde
typen vals-positieve berichten vrij te geven (laten bezorgen) en hun in
quarantaine geplaatste inhoud te beheren via de webinterface Quarantaine
voor e-mail (onlineviewer). Gebruikers hebben toegang tot de webinterface
door op een koppeling te klikken die in de e-mailquarantainerapporten staat en
door zich aan te melden met hun domeinreferenties.
Antispam - Filteren en verificatie
Antispam is geavanceerde, op de cloud gebaseerde functionaliteit die
verhindert dat uw gebruikers (ontvangers van e-mail) spam ontvangen. Wij
raden u aan gebruik te maken van filters en verificatie en uw lokale IP-adressen
toe te voegen aan de lijst met te negeren IP-adressen. IP-adressen binnen uw
netwerkinfrastructuur worden vervolgens tijdens classificatie genegeerd. U
kunt de rest van de lijsten met goedgekeurde, geblokkeerde en genegeerde IP-

44
Onderwerp
Beschrijving
adressen configureren en beheren om filteren en verificatie aan te passen. Ook
kunt u Greylisting inschakelen als u besluit deze functie te gebruiken.
Regels
Een krachtige functie waarmee u e-mailberichten kunt filteren op basis van
gedefinieerde voorwaarden en acties. Gebruik vooraf gedefinieerde regels (pas
deze indien nodig aan) of maak nieuwe, aangepaste regels die aansluiten op uw
behoeften. Regels kunnen worden geconfigureerd voor elke beveiligingslaag
(Beveiliging van e-mailtransport, Beveiliging van postvakdatabase of On-
demand databasescan van postvak).
Antivirustest
Verifieer of Antivirusbeveiliging goed werkt.
Antispamtest
Verifieer of Antispambeveiliging goed werkt.
Antiphishingtest
Verifieer of Antiphishing goed werkt.
4.2 Beheerd via ESET Security Management Center
ESET Security Management Center (ESMC) is een toepassing waarmee u vanuit één centrale locatie ESET-producten
in een netwerkomgeving kunt plannen. Met het ESET Security Management Center-taakbeheersysteem kunt u ESET-
beveiligingsoplossingen installeren op externe computers en snel reageren op nieuwe problemen en
bedreigingen. ESET Security Management Center zelf biedt geen beveiliging tegen schadelijke code. Dit product is
afhankelijk van de aanwezigheid van ESET-beveiligingsoplossingen op elke client. ESET-beveiligingsoplossingen
ondersteunen netwerken met meerdere platformtypen. Uw netwerk kan bestaan uit een combinatie van Microsoft-
, Linux-, Mac OS- en mobiele besturingssystemen.
Zie Online-Help van ESET Security Management Center voor meer informatie.

45
4.3 Controle
Aan de beveiligingsstatus die wordt weergegeven in het gedeelte Controle kunt u zien wat het huidige
beveiligingsniveau van uw computer is. Er wordt een statusoverzicht over de werking van ESET Mail Security
weergegeven in het hoofdvenster.
De status U bent beveiligd geeft aan dat maximale beveiliging is gegarandeerd.
Het rode pictogram geeft ernstige problemen aan. Uw computer is zeer waarschijnlijk niet maximaal beveiligd.
Voor een lijst met mogelijke beveiligingsstatussen, verwijzen wij u naar het gedeelte Status.
Het oranje pictogram geeft aan dat uw ESET-product aandacht vereist voor een niet-kritisch probleem.
Modules die goed werken, krijgen een groen vinkje. Modules die niet volledig functioneel zijn, krijgen een rood
uitroepteken of een oranje waarschuwingspictogram. Aanvullende informatie over de module wordt weergegeven
in het bovenste deel van het venster. Tevens ziet u hier mogelijke oplossingen voor het probleem met de module.
U kunt de status van een individuele module wijzigen door op Instellingen in het hoofdmenu te klikken en
vervolgens op de gewenste module te klikken.
De controlepagina bevat ook informatie over uw systeem, waaronder het volgende:
· Productversie: versienummer van ESET Mail Security.
· Servernaam: hostnaam of FQDN van de computer.
· Systeem: details over het besturingssysteem.
· Computer: details over de hardware.
· Server uptime: geeft aan hoelang het systeem in bedrijf is. Dit is in principe het tegenovergestelde van
downtime.

46
Aantal postvakken
ESET Mail Security detecteert het aantal postvakken en geeft het gedetecteerde aantal weer:
· Domein: het aantal van alle postvakken in een bepaald domein waartoe de Exchange Server behoort.
· Lokaal: geeft het aantal postvakken aan (indien aanwezig) voor Exchange Server waarop ESET Mail Security is
geïnstalleerd.
Als u het probleem niet kunt verhelpen met de voorgestelde oplossingen, klikt u op Help en ondersteuning om
toegang te krijgen tot de Help-bestanden of de ESET-kennisbank te doorzoeken. Als u hulp nodig hebt, kunt u Een
supportaanvraag verzenden . ESET Technische ondersteuning reageert snel op uw vragen en helpt bij het vinden
van een oplossing.
4.3.1 Status
Er wordt een statusoverzicht van ESET Mail Security weergegeven in het hoofdvenster, met uitvoerige informatie
over uw systeem. Wanneer alles normaal en zonder problemen werkt, is de beveiligingsstatus groen . De
beveiligingsstatus kan onder bepaalde omstandigheden echter veranderen. De beveiligingsstatus wordt oranje
of rood, en er wordt een waarschuwingsbericht weergegeven als een van de volgende situaties zich voordoet:
Waarschuwingsbericht
Details van waarschuwingsbericht
Antivirusbeveiliging van e-
mailserver uitgeschakeld
Kl ik op Antivirusbeveiliging inschakelen op het tabblad Controle of schakel
Antivirus- en antispywarebeveiligingopnieuw in, in het deelvenster
Instellingen van het hoofdprogrammavenster.
E-mailserverintegratie
uitgeschakeld
E-mailserverintegratie is door de gebruiker uitgeschakeld. Klik op Integratie-
instelling bewerken om Beveiliging van e-mailverkeer in te schakelen
Antispam-engine heeft een
beperkte verbinding met de cloud
Dit duidt op verbindingsproblemen. Zorg dat relevante poorten zijn
ingeschakeld.
Detectie van een potentieel
ongewenste toepassing is niet
geconfigureerd
Een potentieel ongewenste toepassing is een programma waarin zich adware
bevindt, dat werkbalken installeert of andere onduidelijke bedoelingen
heeft. Er kunnen zich situaties voordoen waarin de gebruiker van mening is
dat de voordelen van een potentieel ongewenste toepassing opwegen tegen
de risico's ervan.
Product niet geactiveerd of Licentie
verlopen
Dit wordt aangegeven met een rood beveiligingsstatuspictogram. Er kunnen
geen updates meer worden uitgevoerd nadat de licentie is verlopen. Volg de
instructies in het waarschuwingsvenster om uw licentie te vernieuwen.
ESET LiveGrid® is uitgeschakeld
Dit probleem wordt aangegeven wanneer ESET LiveGrid® wordt uitgeschakeld
in Geavanceerde instellingen.
Real-timebeveiliging van
bestandssysteem is tijdelijk
uitgeschakeld
Kl ik op Real-timebeveiliging inschakelen op het tabblad Controle of schakel
Real-timebeveiliging van bestandssysteem opnieuw in op het tabblad
Instellingen in het hoofdprogrammavenster.
Besturingssysteem is niet up-to-
date
In het venster Systeemupdates staat een lijst met beschikbare updates die
kunnen worden gedownload en geïnstalleerd.
De computer moet opnieuw
worden opgestart
Kl ik op Computer opnieuw opstarten als u uw systeem meteen opnieuw wilt
opstarten of klik op Negeren als u later opnieuw wilt opstarten.

47
Waarschuwingsbericht
Details van waarschuwingsbericht
Netwerkaanvalbeveiliging (IDS) is
tijdelijk uitgeschakeld
Kl ik op Netwerkaanvalbeveiliging (IDS) inschakelen om deze functie opnieuw
in te schakelen.
Botnet-beveiliging is tijdelijk
uitgeschakeld
Kl ik op Botnetbeveiliging inschakelen om deze functie opnieuw in te
schakelen.
Beveiliging van webtoegang is
tijdelijk uitgeschakeld
Kl ik op Beveiliging van webtoegang inschakelen op het tabblad Controle of
schakel Beveiliging van webtoegang opnieuw in het deelvenster Instellingen
van het hoofdprogrammavenster in.
Antiphishing-beveiliging is niet
functioneel
Deze functie werkt niet, omdat andere vereiste programmamodules niet
actief zijn.
Beleid negeren geactiveerd
De configuratie die door het beleid is ingesteld, wordt tijdelijk genegeerd.
Waarschijnlijk tot het probleem is opgelost. Als u ESET Mail Security beheert
met ESMC en er beleid aan hebt toegewezen, wordt de statuskoppeling
vergrendeld (grijs weergegeven), afhankelijk van welke functies deel
uitmaken van het beleid.
Als u het probleem niet kunt oplossen, zoek dan in de ESET-kennisbank . Als u hulp nodig hebt, kunt u Een
supportaanvraag verzenden . ESET Technische ondersteuning reageert snel op uw vragen en helpt bij het vinden
van een oplossing.

48
4.3.2 Windows-update beschikbaar
In het venster Systeemupdates staat een lijst met beschikbare updates die kunnen worden gedownload en
geïnstalleerd. Het prioriteitsniveau van de update wordt naast de naam van de update vermeld. Klik met de
rechtermuisknop op een rij met updates en klik op Meer informatie om een pop-upvenster met extra informatie
weer te geven.
Kl ik op Systeemupdate uitvoeren om het venster Windows Update te openen en door te gaan met
systeemupdates.

49
5. Als u ESET Mail Security
In dit gedeelte vindt u een uitvoerige beschrijving van de gebruikersinterface van het programma en wordt
uitgelegd hoe u ESET Mail Security gebruikt.
Met de gebruikersinterface kunt u snel naar veelgebruikte functies gaan:
· Controle
· Logbestanden
· Scannen
· Bijwerken
· E-mailquarantaine
· Instellen
· Hulpmiddelen
5.1 Scannen
De scanner op aanvraag is een belangrijk onderdeel van ESET Mail Security. Hiermee worden scans uitgevoerd op
bestanden en mappen op uw computer. Voor de beveiliging van uw netwerk is het van essentieel belang dat
computerscans niet alleen worden uitgevoerd als infecties worden vermoed, maar regelmatig als onderdeel van
routinematige beveiligingsmaatregelen. We raden u aan regelmatig (bijvoorbeeld eens per maand) een dieptescan
van uw systeem uit te voeren. Zo kunt u virussen detecteren die nog niet zijn gedetecteerd met Real-
timebeveiliging van bestandssysteem. Dit kan zich voordoen als er een bedreiging plaatsvindt wanneer Real-
timebeveiliging van het bestandssysteem is uitgeschakeld, de detectie-engine niet is bijgewerkt of als een bestand
niet werd gedetecteerd toen het voor het eerst op de schijf werd opgeslagen.
Selecteer beschikbare scans op aanvraag voor ESET Mail Security:
Databasescan van postvak
Hiermee kunt u Op aanvraag database scannen uitvoeren. U kunt kiezen uit het scannen van mappen van het
type Openbaar, E-mailservers en Postvakken. Ook kunt u Planner gebruiken om een SharePoint-databasescan
op een bepaalde tijd of bij een bepaalde gebeurtenis uit te voeren.
OPMERKING
Als u Microsoft Exchange Server 2007, 2010, 2013 of 2016 uitvoert, kunt u kiezen tussen Beveiliging van
postvakdatabase en Op aanvraag database scannen. Er kan slechts één beveiligingstype tegelijk actief zijn. Als
u besluit Op aanvraag database scannen te gebruiken, dient u integratie van Beveiliging van postvakdatabase
uit te schakelen in Geavanceerde instellingen onder Server. Anders is Op aanvraag database scannen niet
beschikbaar.
Scan van Office 365-postvak
Hiermee kunt u externe postvakken scannen in hybride Office 365-omgevingen. Werkt op dezelfde manier als
On-demand databasescan van postvak.
Opslagscan
Hiermee worden alle gedeelde mappen op de lokale server gescand. Als Opslagscan niet beschikbaar is, bevat
uw server geen gedeelde mappen.
Uw computer scannen
Hiermee kunt u snel een computerscan starten en geïnfecteerde bestanden opschonen zonder dat
gebruikersinterventie is vereist. Het voordeel van Uw computer scannen is dat het gebruiksvriendelijk is en er
geen gedetailleerde scanconfiguratie nodig is. Deze scan controleert alle bestanden op lokale stations en
schoont automatisch gedetecteerde infiltraties op of verwijdert deze. Het opschoonniveau wordt automatisch
ingesteld op de standaardwaarde. Zie Opschonen voor meer informatie over typen opschoonbewerkingen.

50
OPMERKING
Wij adviseren u minimaal eenmaal per maand een computerscan uit te voeren. Scannen kan worden
geconfigureerd als een geplande taak in Hulpmiddelen > Planner.
Aangepaste scan
Aangepaste scan is een optimale oplossing als u scanparameters wilt opgeven, zoals scandoelen en
scanmethoden. Het voordeel van Aangepaste scan is dat u de scanparameters in detail kunt configureren.
Configuraties kunnen worden opgeslagen in door de gebruiker gedefinieerde scanprofielen. Deze profielen
zijn met name handig als het scannen herhaaldelijk plaatsvindt met dezelfde parameters.
OPMERKING
Het uitvoeren van computerscans met Aangepaste scan wordt alleen aangeraden voor ervaren gebruikers die
eerder antivirusprogramma's hebben gebruikt.
Verwisselbare media scannen
Vergelijkbaar met Smart scan: hiermee kunt u snel een scan starten van verwisselbare media (zoals cd/dvd/
USB) die op de computer zijn aangesloten. Dit kan handig zijn wanneer u een USB-flashstation aansluit op een
computer en u de inhoud wilt scannen op malware en andere mogelijke bedreigingen. Dit type scan kan ook
worden gestart door op Aangepaste scan te kl i kke n, Verwisselbare media te selecteren in het
vervolgkeuzemenu Scandoelen e n op Scannen te klikken.
Hyper-V-scan
Deze optie is alleen zichtbaar in het menu als Hyper-V-beheer is geïnstalleerd op de server waarop ESET Mail
Security wordt uitgevoerd. Met Hyper-V-scan kunt u schijven van virtuele machines op Microsoft Hyper-V-
server scannen zonder dat er een Agent op de desbetreffende VM hoeft te zijn geïnstalleerd.
Vorige scan herhalen
Herhaalt uw laatste scanbewerking met precies dezelfde instellingen.
OPMERKING
De functie Vorige scan herhalen is niet beschikbaar als Op aanvraag database scannen aanwezig is.

51
U kunt opties gebruiken en meer informatie weergeven over de scanstatussen:
Bestanden
slepen en
neerzetten
U kunt bestanden ook slepen en neerzetten in het ESET Mail Security-scanvenster. Deze
bestanden worden direct op virussen gescand.
Negeren/Alles
negeren
Gegeven berichten negeren.
Scanstatussen
De status van de eerste scan weergeven. Deze scan is voltooid of is door de gebruiker
onderbroken.
Logbestand
weergeven
Meer gedetailleerde informatie weergeven.
Meer informatie
U kunt tijdens een scan details zien zoals de Gebruiker die de scan heeft uitgevoerd, het aantal
Gescande objecten e n de Duur van de scan. Als Op aanvraag database scannen wordt
uitgevoerd, wordt de gebruiker weergegeven die de scan heeft gestart, niet het feitelijke
Databasescanaccount dat wordt gebruikt om gedurende de scan verbinding met EWS (Exchange
Web Services) te maken.
Scanvenster
openen
In het venster met de scanvoortgang wordt de huidige status van de scan en informatie over het
aantal gevonden bestanden met schadelijke code weergegeven.

52
5.1.1 Scanvenster en scanlogboek
In het scanvenster worden momenteel gescande objecten weergegeven waaronder hun locatie, aantal gevonden
bedreigingen (indien van toepassing), aantal gescande objecten en scanduur. In het onderste gedeelte van het
venster staan een scanlog met het versienummer van de detectie-engine, datum en tijd wanneer de scan is gestart
en de doelselectie.
Nadat de scan is gestart, kunt u op Onderbreken klikken als u de scan tijdelijk wilt onderbreken. De optie Hervatten
is beschikbaar wanneer het scanproces is onderbroken.
Scanlogboek doorbladeren
Laat deze optie ingeschakeld om automatisch door oude logboeken te bladeren en actieve logboeken te
bekijken in het venster Logbestanden.
OPMERKING
het is normaal dat sommige bestanden, zoals bestanden met wachtwoordbeveiliging of bestanden die
exclusief door het systeem worden gebruikt (doorgaans pagefile.sys en bepaalde logbestanden), niet kunnen
worden gescand.
Nadat de scan is voltooid, ziet u het scanlogboek met alle relevante informatie met betrekking tot de
desbetreffende scan.

53
Klik op het schakelpictogram Filteren om het venster Logbestanden filteren te openen, waarin u filteren of
zoekcriteria kunt definiëren. Klik met de rechtermuisknop op een bepaalde logboekvermelding om het
contextmenu weer te geven:
Actie
Syntaxis
Sneltoets
Zie ook
Filteren op
dezelfde
records
Hiermee wordt Logbestanden filteren geactiveerd en worden er
alleen records weergegeven van hetzelfde type als het
geselecteerde type.
Ctrl+Shift+F
Filteren...
Nadat u op deze optie hebt geklikt, kunt u filtercriteria voor
specifieke logboekvermeldingen opgeven in het venster
Logbestanden filteren.
Logbestanden
filteren
Filter
inschakelen
Hiermee worden filterinstellingen geactiveerd. De eerste keer dat
u filteren activeert, moet u instellingen definiëren.
Filter
uitschakelen
Hiermee wordt filteren uitgeschakeld (zelfde als klikken op het
schakelpictogram onderaan).
Kopiëren
Hiermee wordt informatie van geselecteerde/gemarkeerde
record(s) naar het Klembord gekopieerd.
Ctrl+C
Alles
kopiëren
Hiermee kopieert u informatie vanuit alle records in het venster.

54
Actie
Syntaxis
Sneltoets
Zie ook
Exporteren...
Hiermee worden geselecteerde/gemarkeerde record(s) naar een
xml-bestand geëxporteerd.
Alles
exporteren...
Hiermee wordt alle informatie in het venster naar een xml-bestand
geëxporteerd.
5.2 Logbestanden
Logbestanden bevatten informatie over belangrijke programmagebeurtenissen die zich hebben voorgedaan en
bieden een overzicht van scanresultaten, gedetecteerde bedreigingen, enz. Logbestanden vormen een essentieel
hulpmiddel bij systeemanalyse, bedreigingsdetectie en probleemoplossing. Logboekregistratie wordt zonder
gebruikersinteractie op de achtergrond uitgevoerd. Informatie wordt vastgelegd op basis van de huidige
detailinstellingen voor logboekregistratie. Het is mogelijk tekstberichten en logbestanden rechtstreeks in de ESET
Mail Security-omgeving te bekijken of te exporteren en elders te bekijken.
Kies het gewenste type logbestand in het vervolgkeuzemenu. De volgende logboeken zijn beschikbaar:
Detecties
Het logbestand met bedreigingen bevat uitgebreide informatie over infiltraties die door ESET Mail Security-
modules zijn gedetecteerd. Hierbij gaat het om informatie zoals het tijdstip van detectie, de naam van de
bedreiging, de locatie, de actie die is uitgevoerd en de naam van de gebruiker die ten tijde van detectie was
aangemeld. Dubbelklik om de details van een logboekvermelding in een apart venster weer te geven.
Gebeurtenissen
Alle belangrijke acties die worden uitgevoerd door ESET Mail Security, worden opgenomen in de
gebeurtenislogboeken. Het gebeurtenislogboek bevat informatie over gebeurtenissen en fouten die in het
programma zijn opgetreden. Hiermee kunnen systeembeheerders en gebruikers problemen oplossen. Vaak
kunt u met de hier verschafte informatie problemen in het programma oplossen.
Computerscan
Alle scanresultaten worden in dit venster weergegeven. Elke regel correspondeert met één computercontrole.
Dubbelklik op een vermelding om de details van de desbetreffende scan weer te geven.
Geblokkeerde bestanden
Bevat records van bestanden die zijn geblokkeerd en niet toegankelijk waren. Het protocol geeft de reden aan
en de bronmodule die het bestand heeft geblokkeerd, evenals de toepassingen en gebruiker die het bestand
heeft uitgevoerd.
Bestanden verzonden
Bevat records van bestanden, op de cloud gebaseerde beveiliging, ESET Dynamic Threat Defense en ESET
LiveGrid®.
HIPS
Bevat records van specifieke regels die zijn gemarkeerd voor registratie. Het protocol geeft de toepassing weer
die de bewerking heeft aangeroepen, het resultaat (of de regel was toegestaan of verboden) en de gemaakte
regelnaam.
Netwerkbeveiliging
Bevat records van bestanden die zijn geblokkeerd door Botnetbeveiliging en IDS (Netwerkaanvalbeveiliging).
Gefilterde websites
Lijst met websites die zijn geblokkeerd door Beveiliging van webtoegang en Antiphishing-beveiliging voor e-
mail. In deze logboeken ziet u de tijd, URL, gebruiker en toepassing die een verbinding met deze website heeft
geopend.
Apparaatbeheer

55
Hier ziet u records van verwisselbare media of apparaten die op de computer zijn aangesloten. Alleen
apparaten met een regel voor Apparaatbeheer worden opgenomen in het logbestand. Als de regel niet
overeenkomst met een aangesloten apparaat, wordt er geen logvermelding voor dat aangesloten apparaat
gemaakt. Hier kunt u ook details bekijken als apparaattype, serienummer, leverancier en mediagrootte (indien
beschikbaar).
Beveiliging e-mailserver
Alle berichten die door ESET Mail Security als infiltratie of als spam zijn gedetecteerd, worden hier vastgelegd.
Deze logbestanden zijn van toepassing op de volgende beveiligingstypen: Antispam, Antiphishing, Regels en
Antivirus. Als u dubbelklikt op een item, wordt er een pop-upvenster geopend met aanvullende informatie
over het gedetecteerde e-mailbericht, zoals IP-adres, HELO-domein, Bericht-id en Scantype die de
beveiligingslaag aangeeft waarop het bericht is gedetecteerd. U ziet ook het scanresultaat zien van Antivirus,
Antiphishing en Antispam, en de reden waarom het bericht is gedetecteerd, en of er een regel is geactiveerd.
OPMERKING
Niet alle verwerkte berichten worden opgenomen in het logbestand Beveiliging van e-mailserver. Maar alle
berichten die feitelijk zijn gewijzigd (bijlage verwijderd, aangepaste tekenreeks toegevoegd aan de koptekst
van het bericht enz.), worden in het logboek genoteerd.
Databasescan van postvak
Bevat de versie van de detectie-engine, datum, gescande locatie, aantal gescande objecten, aantal gevonden
bedreigingen, aantal geactiveerde regels en tijdstip van voltooiing.
SMTP-beveiliging
Alle berichten die zijn geëvalueerd met de greylistingmethode. SPF en Backscatter worden hier ook
weergegeven. Elke record bevat het HELO-domein, IP-adres van afzender en ontvanger, de status van acties
(afgewezen, niet afgewezen (niet geverifieerd) en geverifieerde binnenkomende berichten). Er is een nieuwe
actie om subdomeinen toe te voegen aan de grijze lijst. Zie de onderstaande tabel.
Hyper-V-scan
Bevat een lijst met Hyper-V-scanresultaten. Dubbelklik op een vermelding om de details van de
desbetreffende scan weer te geven.

56
In het contextmenu (klik met de rechtermuisknop) kunt u een actie voor de geselecteerde logrecord kiezen:
Actie
Syntaxis
Sneltoets
Zie ook
Weergeven
Geeft uitvoerige informatie weer over het geselecteerde
logbestand in een nieuw venster (zelfde als dubbelklikken).
Filteren op
dezelfde records
Hiermee wordt Logbestanden filteren geactiveerd en worden
er alleen records weergegeven van hetzelfde type als het
geselecteerde type.
Ctrl+Shift+F
Filteren...
Nadat u op deze optie hebt geklikt, kunt u filtercriteria voor
specifieke logboekvermeldingen opgeven in het venster
Logbestanden filteren.
Logbestanden
filteren
Filter inschakelen
Hiermee worden filterinstellingen geactiveerd. De eerste keer
dat u filteren activeert, moet u instellingen definiëren.
Filter
uitschakelen
Hiermee wordt filteren uitgeschakeld (zelfde als klikken op
het schakelpictogram onderaan).
Kopiëren
Hiermee wordt informatie van geselecteerde/gemarkeerde
record(s) naar het Klembord gekopieerd.
Ctrl+C
Alles kopiëren
Hiermee kopieert u informatie vanuit alle records in het
venster.
Verwijderen
Hiermee worden geselecteerde/gemarkeerde record(s)
verwijderd. Voor deze actie zijn beheerdersrechten vereist.

57
Actie
Syntaxis
Sneltoets
Zie ook
Alles verwijderen
Hiermee verwijdert u alle records in het venster. Voor deze
actie zijn beheerdersrechten vereist.
Exporteren...
Hiermee worden geselecteerde/gemarkeerde record(s) naar
een xml-bestand geëxporteerd.
Alles
exporteren...
Hiermee wordt alle informatie in het venster naar een xml-
bestand geëxporteerd.
Zoeken...
Hiermee wordt het venster Zoeken in logbestand geopend en
kunt u zoekcriteria opgeven. U kunt de functie Zoeken
gebruiken om zelfs met ingeschakeld filteren een bepaald
record te vinden.
Ctrl+F
Zoeken in
logbestand
Vol gende zoe ken
Hiermee zoekt u naar de volgende treffer van uw eerder
gedefinieerde zoekcriteria.
F3
Vori ge zoe ken
Hiermee zoekt u naar de vorige treffer.
Shift+F3
IP-adres
toevoegen aan de
witte lijst die
grijze lijsten kan
maken
Voegt het IP-adres van de afzender toe aan de witte lijst met
IP-adressen. U kunt de witte lijst met IP-adressen vinden
onder het gedeelte Greylisting en SPF van Filteren en
verificatie. Dit geldt voor items die zijn gelogd door Greylisting
of SPF.
Domein
toevoegen aan
greylisting en
witte SPF-lijst
Voegt het domein van de afzender toe aan de witte lijst met
naar IP-adressen omgezette domeinen. Alleen het domein
wordt toegevoegd. Het subdomein wordt genegeerd. Als
bijvoorbeeld het adres van de afzender sub.domain.com is,
wordt al le e n domain.com toegevoegd aan de witte lijst. U vindt
de witte lijst met naar IP-adressen omgezette domeinen in
het gedeelte Greylisting en SPF van Filteren en verificatie. Dit
geldt voor items die zijn gelogd door Greylisting.
Subdomein
toevoegen aan
greylisting en
witte SPF-lijst
Voegt het subdomein van de afzender toe aan de witte lijst
met naar IP-adressen omgezette domeinen. Het gehele
domein wordt toegevoegd, waaronder het subdomein
(bijvoorbeeld sub.domain.com). Dit biedt meer flexibiliteit
voor filterdoeleinden, indien nodig. U vindt de witte lijst met
naar IP-adressen omgezette domeinen in het gedeelte
Greylisting en SPF van Filteren en verificatie. Dit geldt voor
items die zijn gelogd door Greylisting.

58
5.2.1 Logbestanden filteren
Met de logfilterfunctie vindt u de informatie die u zoekt, met name wanneer er veel records zijn. U kunt er
logboekrecords mee filteren, bijvoorbeeld als u op zoek bent naar een bepaald type gebeurtenis, een bepaalde
status of tijdsduur. U kunt logboekrecords filteren door bepaalde zoekopties op te geven. Alleen records die
relevant zijn (volgens de zoekopties), worden in het venster Logbestanden weergegeven.
Typ het trefwoord waarop u wilt zoeken in het veld Tekst zoeken. Gebruik het vervolgkeuzemenu Zoeken in
kolommen om uw zoekopdracht te verfijnen. Kies een of meer records in het vervolgkeuzemenu Recordlogtypen.
Def ini ee r de Tijdsduur waarbinnen u de resultaten weergegeven wilt hebben. U kunt ook verdere zoekopties
gebrui ke n, zoal s Alleen hele woorden of Hoofdlettergevoelig.
Tekst zoeken
Typ een tekenreeks (een woord of deel van een woord). Alleen records die deze tekenreeks bevatten, worden
weergegeven. Andere records worden overgeslagen.
Zoeken in kolommen
Selecteer welke kolommen worden meegenomen bij het zoeken. U kunt één of meer kolommen selecteren om
bij het zoeken te gebruiken.
Recordtypes
Kies één of meer logrecordtypen in het vervolgkeuzemenu:

59
· Diagnostisch: hiermee wordt informatie geregistreerd die nodig is om het programma en alle bovenstaande
archieven af te stemmen.
· Informatief: hiermee registreert u informatieve berichten, waaronder berichten over geslaagde updates, plus
alle bovenstaande records.
· Waarschuwingen: hiermee worden kritieke fouten en waarschuwingsberichten geregistreerd.
· Fouten: hiermee worden fouten als "Fout bij downloaden van bestand" en kritieke fouten geregistreerd.
· Kritiek: hiermee worden alleen kritieke fouten geregistreerd (zoals fouten bij het starten van
antivirusbeveiliging).
Tijdsduur
Definieer de tijdsduur waarbinnen u de resultaten weergegeven wilt hebben.
· Niet opgegeven (standaard): hiermee wordt niet gezocht binnen de tijdsduur omdat in het hele logbestand
wordt gezocht
· Afgelopen dag
· Afgelopen week
· Afgelopen maand
· Tijdsduur: u kunt de precieze tijdsduur opgeven (Van: en Tot:) om alleen de records binnen een bepaalde
tijdsduur te filteren.
Alleen hele woorden
Schakel dit selectievakje in als u op hele woorden wilt zoeken om nauwkeurigere resultaten te krijgen.
Hoofdlettergevoelig
Schakel deze optie in als het belangrijk voor u is om hoofdletters of kleine letters te gebruiken tijdens het
filteren. Nadat u uw filter/zoekopties hebt geconfigureerd, klikt u op OK om gefilterde logboekrecords weer te
geven of op Zoeken om te beginnen met zoeken. De logboekbestanden worden van boven naar beneden
doorzocht, te beginnen bij uw huidige positie (de record die is gemarkeerd). Het zoeken stopt zodra de eerste
overeenkomende record is gevonden. Druk op F3 om naar de volgende record te zoeken of klik met de
rechtermuisknop en selecteer Zoeken om uw zoekopties te verfijnen.
5.3 Bijwerken
In het gedeelte Bijwerken ziet u de huidige updatestatus van uw ESET Mail Security, waaronder de datum en tijd van
de vorige geslaagde update. ESET Mail Security regelmatig bijwerken is de beste methode om het maximale
beveiligingsniveau op uw server te handhaven. De module Bijwerken zorgt ervoor dat het programma op twee
manieren altijd up-to-date is; door de detectie-engine en systeemonderdelen bij te werken. Het bijwerken van de
detectie-engine en programma-onderdelen is een belangrijk onderdeel van het leveren van volledige bescherming
tegen schadelijke code.
OPMERKING
Als u nog geen Licentiecode hebt opgegeven, ontvangt u geen updates en wordt u gevraagd uw product te
activeren. Ga hiervoor naar Help en ondersteuning > Product activeren.

60
Huidige versie
De buildversie van ESET Mail Security.
Vorige geslaagde update
De datum van de laatste update. Dit moet een recente datum zijn. Een recente datum geeft namelijk aan dat de
module actueel is.
Laatst gecontroleerd op updates
De datum van de laatste poging om modules bij te werken.
Alle modules weergeven
De lijst met geïnstalleerde modules openen.
Controleren op updates
Het bijwerken van modules is een belangrijk onderdeel van het handhaven van complete beveiliging tegen
schadelijke code.
Updatefrequentie wijzigen
U kunt de tijden van de geplande taak Regelmatige automatisch updates bewerken.
Als u niet zo snel mogelijk op updates controleert, wordt een van de volgende berichten weergegeven:
Foutbericht
Beschrijvingen
Module-update is verouderd
Deze fout wordt weergegeven na verschillende mislukte pogingen om de module
bij te werken. Wij adviseren de standaardinstellingen te controleren. De meest
gangbare reden voor deze fout is onjuist ingevoerde verificatiegegevens of
onj uist ge confi gure erde verbindingsinstellingen.

61
Foutbericht
Beschrijvingen
Bijwerken van modules
mislukt. Product is niet
geactiveerd.
De licentiecode is onjuist opgegeven tijdens het opgeven van instellingen voor
updates. Wij adviseren de verificatiegegevens te controleren. In het venster
Ge avancee rde instel lingen (F5) vindt u aanvullende updateopties. Klik op Help en
ondersteuning > Licentie beheren in het hoofdmenu om een nieuwe licentiecode
op te geven.
Er is een fout opgetreden
tijdens het downloaden van
updatebestanden
Deze fout wordt mogelijk veroorzaakt door instellingen voor de
internetverbinding. Wij adviseren de internetverbinding te controleren door een
willekeurige website te openen in uw webbrowser. Als de website niet wordt
geopend, is er waarschijnlijk geen internetverbinding of zijn er
verbindingsproblemen met uw computer. Neem contact op met uw
internetprovider als u geen actieve internetverbinding hebt.
Modules bijwerken mislukt
Fout 0073
Kl ik op Bijwerken > Controleren op updates voor meer informatie over dit artikel
in de kennisbank .
OPMERKING
Proxyserveropties voor verschillende updateprofielen kunnen verschillen. Als dit het geval is, configureert u
de verschillende updateprofielen in Geavanceerde instellingen (F5) door te klikken op Bijwerken > Profiel.
5.4 Quarantaine voor e-mail
E-mailberichten en onderdelen ervan, zoals bijlagen, worden in Quarantaine voor e-mail geplaatst in plaats van in
de traditionele Quarantaine voor bestanden. Quarantaine voor e-mail is een gemakkelijke manier om spam,
geïnfecteerde bijlagen met malware of phishingberichten te beheren. Er zijn verschillende redenen waarom e-
mailberichten in Quarantaine voor e-mail worden geplaatst, afhankelijk van welke ESET Mail Security-
beveiligingsmodule het bericht verwerkt (Antivirus, Antispam of Regels).
Filteren op pictogrammen
U kunt pictogrammen gebruiken om berichten te filteren om bijlagen, e-mails, of e-mails met alleen bijlagen te
zien.
Tijdsduur
Selecteer de periode waarvoor u in quarantaine geplaatste e-mails wilt zien. Wanneer u Aangepast selecteert,
kunt u een periode opgeven (Datum vanaf en Datum tot).
Snelzoeken
Voer een tekenreeks in het tekstvak in om weergegeven e-mails te filteren (er wordt in alle kolommen
gezocht).
Reden
Gebruik de selectievakjes om verder op type te filteren (spam, malware, regel of phishing).
BELANGRIJK
Gegevens van Beheer van e-mailquarantaine worden niet automatisch bijgewerkt. We raden aan dat u
rege lmatig op Vernieuwen klikt om de meest actuele items in Quarantaine voor e-mail te zien.

62
Vrijgeven
Geeft e-mail vrij aan de oorspronkelijke ontvanger(s) met behulp van de map Replay en verwijdert de e-mail
uit quarantaine. Klik op Ja om de actie te bevestigen. Als het in quarantaine geplaatste item een bijlage is van
een openbare map die niet voor e-mail is bedoeld, is de knop Vrijgeven niet beschikbaar.
OPMERKING
Wanneer een e-mail uit quarantaine wordt vrijgegeven, negeert ESET Mail Security de MIME-koptekst To:,
omdat deze gemakkelijk kan worden vervalst. In plaats daarvan wordt de oorspronkelijke ontvangerinformatie
van de opdracht RCPT TO: gebruikt die tijdens de SMTP-verbinding is verkregen. Hierdoor wordt gegarandeerd
dat de juiste e-mailontvanger het bericht ontvangt dat uit quarantaine wordt vrijgegeven.
Verwijderen
Verwijdert een of meer items uit quarantaine. Klik op Ja om de actie te bevestigen. Items die worden
verwijderd via GUI, worden uit de quarantaineweergave verwijderd, maar blijven in de opslag bewaard. Ze
worden later automatisch verwijderd (standaard na 3 dagen).
Herstellen naar
Met deze optie kunt u een of meerdere bijlagen op een bepaalde plaats herstellen. Deze optie is alleen
beschikbaar voor bijlagen (de optie wordt grijs weergegeven voor berichten). Als u het gehele bericht wilt
verwerken, gebruik hiervoor dan de functie Vrijgeven.
Details van in Quarantaine geplaatste e-mail
Dubbelklik op het in quarantaine geplaatste bericht of klik op de rechtermuisknop en selecteer Details. Er
wordt een pop-upvenster geopend met details over het in quarantaine geplaatste e-mailbericht. In de RFC-
koptekst van de e-mail vindt u ook aanvullende informatie.
Details van in quarantaine geplaatste bijlage

63
Wanneer er wordt gedubbelklikt op een bijlage, is het dialoogvenster met details anders dan het
dialoogvenster met e-mailberichtdetails. RFC-kopteksten zijn niet beschikbaar. In plaats daarvan wordt er een
gebied met een bijlage-enveloptekst weergegeven. U kunt aangepaste tekst van de bijlage-envelop opgeven
wanneer u die uit de e-mailquarantaine vrijgeeft.
Acties zijn ook beschikbaar in het contextmenu. Klik indien gewenst op Vrijgeven, Verwijderen of Definitief
verwijderen om een actie uit te voeren op een in quarantaine geplaatst e-mailbericht. Klik op Ja om de actie te
bevestigen. Als u Definitief verwijderen kiest, wordt het bericht ook verwijderd uit het bestandssysteem. Dit in
tege nste ll ing tot Verwijderen waarbij het item uit de weergave Beheer van e-mailquarantaine wordt verwijderd.

64
5.5 Instellen
Het venster van het menu Instellingen bevat de volgende gedeelten:
· Server
· Computer
· Netwerk
· Web en e-mail
· Hulpmiddelen: registratie in diagnoselogboek
Als u tijdelijk afzonderlijke modules wilt uitschakelen, klikt u naast de desbetreffende module op de groene
schuifbalk . Het beveiligingsniveau van uw server kan hierdoor worden verlaagd.
Als u de beveiliging van een uitgeschakeld beveiligingsonderdeel weer wilt inschakelen, klikt u naast de
desbetreffende module op de rode schuifregelaar . Het onderdeel krijgt weer de ingeschakelde status.
Klik op het tandrad om toegang te krijgen tot uitvoerige instellingen voor een bepaald beveiligingsonderdeel.
Instellingen voor importeren/exporteren
Laad de instellingsparameters met behulp van een .xml-configuratiebestand of sla de huidige
instellingsparameters in een configuratiebestand op.
Geavanceerde instellingen
Configureer geavanceerde instellingen en opties op basis van uw behoeften. Druk op F5 om overal in het
programma het scherm Geavanceerde instellingen te openen.

65
5.5.1 Server
U ziet een lijst met onderdelen die u kunt in/uitschakelen met de schuifbalk . Klik op het tandwielpictogram
om instellingen voor een specifiek item te configureren.
Antivirusbeveiliging
Biedt bescherming tegen schadelijke systeemaanvallen door middel van controle van bestanden, e-mail en
internetcommunicatie.
Antispambeveiliging
Integreert verschillende technologieën (RBL, DNSBL, 'vingerafdrukken', reputatiecontrole, inhoudsanalyse,
regels, handmatige witte/zwarte lijsten, enzovoort) om e-mailbedreigingen maximaal te kunnen detecteren.
Antiphishing-beveiliging
Parseert de berichttekst van inkomende e-mails op phishingkoppelingen (URL's).
Automatische uitsluitingen
Identificeert essentiële servertoepassingen en bestanden van het besturingssysteem van de server en voegt
deze automatisch toe aan de lijst met uitsluitingen. Met deze functionaliteit wordt het risico van mogelijke
conflicten geminimaliseerd en worden de algehele serverprestaties bij het uitvoeren van antivirussoftware
verbeterd.
Cluster
ESET Cluster configureren en activeren.
5.5.2 Computer
ESET Mail Security heeft alle benodigde onderdelen om voor een betekenisvolle beveiliging van de server als
computer te zorgen. Met deze module kunt u de volgende onderdelen inschakelen/uitschakelen:
Real-timebeveiliging van bestandssysteem
Alle bestanden worden gescand op schadelijke code wanneer ze worden geopend, gemaakt of uitgevoerd op
uw computer. Voor Real-timebeveiliging van bestandssysteem is er ook de optie Configureren of
Uitzonderinge n bewerken , waarmee u het venster met instellingen voor uitsluitingen opent. In dit venster
kunt u bestanden en mappen uitsluiten van scannen.
Apparaatbeheer
Met deze module kunt u een apparaat scannen of blokkeren, uitgebreide filters/machtigingen aanpassen voor
een apparaat en bepalen hoe de gebruiker een apparaat opent en ermee werkt.
Host Intrusion Prevention System (HIPS)
Het systeem controleert gebeurtenissen binnen het besturingssysteem en reageert hierop overeenkomstig
een aangepaste set regels.
· Geavanceerde geheugenscanner
· Exploit blocker
· Ransomwareschild
Presentatiemodus
Dit is een functie voor gebruikers die niet willen dat het gebruik van hun software wordt onderbroken, die niet
willen dat er pop-upvensters worden weergegeven en die willen dat de belasting van de CPU minimaal is. U
ontvangt een waarschuwingsbericht (potentieel beveiligingsrisico) en het hoofdprogrammavenster wordt in
oranje weergegeven wanneer u de Presentatiemodus hebt ingeschakeld.
Antivirus- en antispywarebeveiliging tijdelijk uitschakelen
Elke keer wanneer u Antivirus- en antispywarebeveiliging tijdelijk uitschakelt, kunt u opgeven hoe lang u het
geselecteerde onderdeel wilt uitschakelen. Dit kan in het vervolgkeuzemenu. Klik vervolgens op Toepassen om

66
het beveiligingsonderdeel uit te schakelen. Klik op Antivirus- en antispywarebeveiliging inschakelen of gebruik
de schuifregelaar om de beveiliging weer in te schakelen.
5.5.3 Netwerk
Dit wordt bereikt door individuele netwerkverbindingen toe te staan of te weigeren op basis van uw filterregels.
Een persoonlijke firewall biedt beveiliging tegen aanvallen vanaf externe computers en blokkeert bepaalde
potentieel gevaarlijke services.
In de module Netwerk kunt u de volgende onderdelen inschakelen/uitschakelen:
Netwerkaanvalbeveiliging (IDS)
Analyseert de inhoud van netwerkverkeer en beveiligt en beschermt tegen netwerkaanvallen. Al het verkeer
dat als schadelijk wordt beoordeeld, wordt geblokkeerd.
Botnetbeveiliging
Detectie en blokkering van botnetcommunicatie. Identificeert snel en nauwkeurig malware in het systeem.
Zwarte lijst met tijdelijk geblokkeerde IP-adressen (geblokkeerde adressen)
Een lijst met IP-adressen weergeven die als aanvalsbronnen zijn gedetecteerd en die aan de zwarte lijst zijn
toegevoegd, zodat hiermee gedurende een bepaalde tijd geen verbindingen kunnen worden gemaakt
Wizard Probleemoplossing (onlangs geblokkeerde toepassingen of apparaten)
Hiermee kunt u verbindingsproblemen verhelpen die worden veroorzaakt door netwerkaanvalbeveiliging.
5.5.3.1 De wizard Probleemoplossing - Netwerk
De wizard Probleemoplossing controleert alle geblokkeerde verbindingen en begeleidt u bij het
probleemoplossingsproces om problemen met de beveiliging tegen netwerkaanvallen bij specifieke toepassingen
of apparaten op te lossen. Vervolgens stelt de wizard een nieuwe set regels voor die kunnen worden toegepast als
u die goedkeurt.
5.5.4 Web en e-mail
In Web en e-mail kunt u de volgende onderdelen inschakelen/uitschakelen:
Beveiliging van webtoegang
Indien ingeschakeld, wordt alle HTTP- of HTTPS-verkeer gescand op schadelijke software.
Beveiliging van e-mailclient
Controleert communicatie die wordt ontvangen via het POP3- en IMAP-protocol.
Antiphishing-beveiliging
Beschermt u tegen pogingen uw wachtwoorden, bankgegevens en andere gevoelige gegevens te achterhalen
door frauduleuze websites te laten lijken op legitieme websites.

67
5.5.5 Hulpmiddelen - Registratie in diagnoselogboek
Schakel Registratie in diagnoselogboek in wanneer u gedetailleerde informatie wilt hebben over het gedrag van
een bepaalde ESET Mail Security-functie, bijvoorbeeld bij het oplossen van problemen. Wanneer u op het
tandradpictogram klikt, kunt u configureren voor welke functies diagnostische gegevens moeten worden
verzameld.
Kies hoelang de functie ingeschakeld moet blijven (10 minuten, 30 minuten, 1 uur, 4 uur, 24 uur, tot de server de
volgende keer wordt opgestart of permanent). Nadat het diagnoselogboek is ingeschakeld, verzamelt ESET Mail
Security gedetailleerde loggegevens over de ingeschakelde functies.

68
5.5.6 Instellingen importeren en exporteren
De functie voor het importeren/exporteren van instellingen is nuttig als u een back-up wilt maken van de huidige
configuratie van uw ESET Mail Security. U kunt de importeerfunctie ook gebruiken om dezelfde instellingen te
distribueren naar of toe te passen op andere servers met ESET Mail Security. Instellingen worden geëxporteerd naar
een .xml-bestand.
OPMERKING
Er kan een fout optreden bij het exporteren van instellingen als u geen rechten hebt om het geëxporteerde
bestand naar de opgegeven map te schrijven.

69
5.6 Hulpmiddelen
De volgende functies zijn beschikbaar voor het beheren van ESET Mail Security:
· Actieve processen
· Activiteit bekijken
· Beveiligingsstatistieken
· Cluster
· ESET-shell
· ESET Dynamic Threat Defense
· ESET SysInspector
· ESET SysRescue Live
· Planner
· Bestand verzenden voor analyse
· Quarantaine

70
5.6.1 Actieve processen
Met Actieve processen worden de programma's en processen weergegeven die worden uitgevoerd op uw computer
en wordt ESET direct en continu op de hoogte gehouden van nieuwe infiltraties. ESET Mail Security biedt
gedetailleerde informatie over actieve processen om gebruikers te beschermen die over ESET LiveGrid®-
technologie beschikken.
OPMERKING
Bekende toepassingen die zijn gemarkeerd als Beste reputatie (groen) zijn schoon (witte lijst) en worden
uitgesloten van scannen, omdat zo de scansnelheid van on-demand computerscans en real-timebeveiliging
van het bestandssysteem op uw computer wordt verbeterd.
Reputatie
In de meeste gevallen bepaalt de technologie van ESET Mail Security en ESET LiveGrid® de
objectreputatie op basis van een reeks heuristische regels die de kenmerken onderzoeken van
elk object (bestanden, processen, registersleutels, enz.) en vervolgens hun potentieel voor
schadelijke activiteiten weegt. Op basis van deze heuristieken worden objecten een
reputatieniveau toegewezen, van 9 - beste reputatie (groen) tot 0 - slechtste reputatie (rood).
Proces
Imagenaam van het programma of proces dat momenteel op de computer wordt uitgevoerd. U
kunt ook Windows Taakbeheer gebruiken als u alle actieve processen op uw computer wilt zien. U
kunt Taakbeheer openen door met de rechtermuisknop op een leeg gebied op de taakbalk te
klikken of te drukken op Ctrl+Shift+Esc op uw toetsenbord.
PID
Dit is een id van processen die in Windows-besturingssystemen worden uitgevoerd.

71
Reputatie
In de meeste gevallen bepaalt de technologie van ESET Mail Security en ESET LiveGrid® de
objectreputatie op basis van een reeks heuristische regels die de kenmerken onderzoeken van
elk object (bestanden, processen, registersleutels, enz.) en vervolgens hun potentieel voor
schadelijke activiteiten weegt. Op basis van deze heuristieken worden objecten een
reputatieniveau toegewezen, van 9 - beste reputatie (groen) tot 0 - slechtste reputatie (rood).
Aantal
gebruikers
Het aantal gebruikers dat een bepaalde toepassing gebruikt. Deze informatie wordt verzameld
door de ESET LiveGrid®-technologie.
Tijdstip van
detectie
De periode sinds de toepassing door de ESET LiveGrid®-technologie is ontdekt.
Toepassingsnaa
m
Naam van een programma waartoe dit proces behoort.
OPMERKING
Wanneer een toepassing wordt aangeduid als Onbekend (oranje), hoeft dit niet per se schadelijke software te
zijn. Doorgaans gaat het om een nieuwere toepassing. Als u niet zeker weet of het bestand veilig is, gebruik
dan de functie Voorbeeld verzenden voor analyse om het bestand naar het viruslab van ESET te sturen. Als het
bestand een schadelijke toepassing blijkt te zijn, wordt de detectie ervan in een van de volgende updates voor
de detectie-engine opgenomen.
Details weergeven
De volgende informatie wordt onder in het venster weergegeven:
· Pad: de locatie van een toepassing op de computer.
· Grootte: bestandsgrootte in kB (kilobytes) of MB (megabytes).
· Beschrijving: bestandskenmerken op basis van de beschrijving van het besturingssysteem.
· Bedrijf: de naam van de leverancier of het toepassingsproces.
· Versie: informatie van de uitgever van de toepassing.
· Product: de toepassingsnaam en/of bedrijfsnaam.
· Gemaakt op: de datum en het tijdstip waarop een toepassing is gemaakt.
· Gewijzigd op: de datum en tijd waarop een toepassing de laatste keer is gewijzigd.
Toevoegen aan procesuitsluitingen
Klik met de rechtermuisknop op een proces in het venster Actieve processen om het proces uit te sluiten van
scannen. Het pad naar het proces wordt toegevoegd aan de lijst Uitzonderingen voor processen.
5.6.2 Activiteit bekijken
Als u activiteit in grafiekvorm wilt bekijken, selecteert u de volgende activiteit in het vervolgkeuzemenu:
Activiteit van bestandssysteem
Hoeveelheid gelezen of geschreven gegevens. De verticale as van de grafiek vertegenwoordigt gelezen
gegevens (blauw) en geschreven gegevens (groen).
Netwerkactiviteit
Hoeveelheid ontvangen of verzonden gegevens. De verticale as van de grafiek vertegenwoordigt ontvangen
gegevens (blauw) en verzonden gegevens (groen).
E-mailserveractiviteit
Hoeveelheid verwerkte gegevens door transportbeveiliging (blauw) en databasebeveiliging (groen).

72
Onder aan de grafiek staat een tijdlijn waarop in real-time de activiteiten in het bestandssysteem voor de
geselecteerde periode worden weergegeven. Gebruik het vervolgkeuzemenu Vernieuwingssnelheid als u de
frequentie van updates wilt wijzigen.
De volgende opties zijn beschikbaar:
1 seconde
De grafiek wordt elke seconde vernieuwd en de periode beslaat de laatste 10 minuten.
1 minuut (afgelopen
24 uur)
De grafiek wordt elke minuut vernieuwd en de periode beslaat de afgelopen 24 uur.
1 uur (afgelopen
maand)
De grafiek wordt elk uur vernieuwd en de periode beslaat de afgelopen maand.
1 uur (geselecteerde
maand)
De grafiek wordt elk uur vernieuwd en de tijdlijn beslaat de geselecteerde maand. Selecteer
een maand (en een jaar) in het vervolgkeuzemenu om activiteit te zien. Klik op Wijzigen.

73
5.6.3 Beveiligingsstatistieken
Als u statistische gegevens wilt bekijken met betrekking tot beveiligingsmodules van ESET Mail Security, selecteert
u de toepasselijke beveiligingsmodule in het vervolgkeuzemenu. De statistieken bestaan uit informatie zoals het
aantal gescande objecten, het aantal geïnfecteerde objecten, het aantal opgeschoonde objecten en het aantal
schone objecten. Zweef met de muis over een object naast de grafiek om alleen de gegevens voor dat specifieke
object in de grafiek weer te geven. Als u statistische informatie voor de huidige beveiligingsmodule wilt wissen,
klikt u op Opnieuw instellen. Klik op Alles opnieuw instellen om gegevens voor alle modules te wissen.
De volgende grafieken met statistieken zijn beschikbaar in ESET Mail Security:
Antivirus- en antispywarebeveiliging
Geeft het totale aantal geïnfecteerde en opgeschoonde objecten weer
Beveiliging van bestandssysteem
Geeft objecten weer die alleen zijn gelezen of geschreven in het bestandssysteem.
Hyper-V-beveiliging
Geeft het totale aantal geïnfecteerde, opgeschoonde en schone objecten weer (alleen op systemen met Hyper-
V).
Beveiliging van e-mailclient
Geeft objecten weer die alleen zijn verzonden of ontvangen door e-mailclients.
Webtoegang- en antiphishing-beveiliging
Geeft objecten weer die alleen zijn gedownload door webbrowsers.
Beveiliging e-mailserver

74
Geeft antivirus- en antispywarestatistieken van de e-mailserver weer.
Antispambeveiliging van mailserver
Geeft de geschiedenis van antispamstatistieken weer. Het aantal bij Niet gescand verwijst naar objecten die
zijn uitgesloten van de scan (op basis van regels, interne berichten, geverifieerde verbindingen, enz.).
Greylistingbeveiliging e-mailserver
Bevat antispamstatistieken die worden gegenereerd met de greylistingmethode.
Beveiligingsactiviteit voor e-mailtransport
Geeft objecten weer die door de e-mailserver zijn geverifieerd/geblokkeerd/verwijderd
Beveiligingsprestaties voor e-mailtransport
Geeft gegevens weer in B/s die zijn verwerkt door VSAPI/Transportagent
Beveiligingsactiviteit voor postvakdatabase
Geeft objecten weer die zijn verwerkt door VSAPI (aantal geverifieerde, in quarantaine geplaatste en
verwijderde objecten).
Beveiligingsprestaties voor postvakdatabase
Geeft gegevens weer die zijn verwerkt door VSAPI (aantal verschillende gemiddelden voor Vandaag, voor
Afgelopen 7 dagen en gemiddelden voor Sinds vorige keer opnieuw ingesteld).
5.6.4 Cluster
Het ESET-cluster is een P2P-communicatie-infrastructuur van de reeks ESET-producten voor Microsoft Windows
Server. Het gebruik van ESET Cluster is ideaal als u een Exchange-infrastructuur hebt met meerdere servers zoals
DAG.
Dankzij deze infrastructuur kunnen ESET-serverproducten communiceren met elkaar en gegevens uitwisselen, zoals
configuratiegegevens en meldingen, en kunnen ze ook Greylisting-databases synchroniseren en gegevens
synchroniseren die nodig zijn voor de juiste werking van een reeks productexemplaren. Een voorbeeld van een
dergelijke groep is een groep knooppunten in een Windows-failovercluster of een NLB-cluster (Network Load
Balancing) met geïnstalleerde ESET-producten waarbij dezelfde configuratie van het product in het gehele cluster
moet voorkomen. Met ESET-cluster is deze consistentie tussen exemplaren gegarandeerd.
OPMERKING
Instellingen van de gebruikersinterface worden niet gesynchroniseerd tussen ESET-clusterknooppunten.
De pagina met de status van het ESET-cluster is toegankelijk via het hoofdmenu. Ga naar Hulpmiddelen > Cluster.
Indien juist geconfigureerd, ziet de statuspagina er als volgt uit:

75
OPMERKING
Het maken van ESET-clusters tussen ESET Mail Security en ESET-bestandsbeveiliging voor Linux wordt niet
ondersteund.
Als u het ESET-cluster instelt, zijn er twee manieren waarop u knooppunten kunt toevoegen:
Automatisch detecteren
Als u een bestaand Windows-failovercluster/NLB-cluster hebt, voegt Automatisch detecteren automatisch zijn
lidknooppunten aan het ESET-cluster toe.
Bladeren
U kunt knooppunten handmatig toevoegen door de servernamen te typen (leden van dezelfde werkgroep of
leden van hetzelfde domein).
OPMERKING
Se rve rs hoe ve n geen lid te zijn van een Windows-failovercluster/NLB-cluster om de ESET-clusterfunctie te
kunnen gebruiken. Een Windows-failovercluster of NLB-cluster is niet vereist in uw omgeving om ESET-clusters
te kunnen gebruiken.
Nadat u knooppunten aan uw ESET-cluster hebt toegevoegd, is de volgende stap de installatie van ESET Mail
Security op elk knooppunt. Dit wordt automatisch gedaan tijdens het instellen van het ESET-cluster. Referenties die
nodig zijn voor externe installatie van ESET Mail Security op andere clusterknooppunten:
Domeinscenario
Referenties van de domeinbeheerder.
Werkgroepscenario

76
U moet ervoor zorgen dat alle knooppunten dezelfde lokale beheerdersaccountreferenties gebruiken
In een ESET-cluster kunt u ook een combinatie van knooppunten gebruiken die automatisch als leden van een
bestaand Windows-failovercluster/NLB-cluster worden toegevoegd en knooppunten die handmatig worden
toegevoegd (op voorwaarde dat deze zich in hetzelfde domein bevinden).
BELANGRIJK
Het is niet mogelijk domeinknooppunten te combineren met werkgroepknooppunten.
Een andere vereiste voor het gebruik van een ESET-cluster is dat Bestands- en printerdeling moet zijn ingeschakeld
in Windows Firewall voordat ESET Mail Security aan ESET-clusterknooppunten wordt doorgegeven.
U kunt op elk moment nieuwe knooppunten toevoegen aan een bestaand ESET-cluster door de Clusterwizard uit te
voeren.
Certificaten importeren
Certificaten worden gebruikt om sterke machine-naar-machineverificatie te leveren wanneer HTTPS wordt
gebruikt. Er geldt een onafhankelijke certificaathiërarchie voor elk ESET-cluster. De hiërarchie heeft één
basiscertificaat en een reeks knooppuntcertificaten die door het basiscertificaat zijn ondertekend. De
privésleutel van het basiscertificaat wordt vernietigd nadat alle knooppuntcertificaten zijn gemaakt. Wanneer u
een nieuw knooppunt aan het cluster toevoegt, wordt er een nieuwe certificaathiërarchie gemaakt. Navigeer
naar de map met de certificaten (die zijn gegenereerd tijdens het gebruik van de clusterwizard). Selecteer het
certificaatbestand en klik op Openen.
Cluster verwijderen
ESET-clusters kunnen worden ontmanteld. Elk knooppunt schrijft een record in zijn gebeurtenissenlogboek dat
het ESET-cluster is verwijderd. Daarna worden alle ESET-firewallregels verwijderd uit Windows Firewall.
Voormalige knooppunten krijgen dan weer hun vorige status en kunnen indien nodig opnieuw worden gebruikt
in een ander ESET-cluster.
5.6.4.1 Clusterwizard - Knooppunten selecteren
De eerste stap bij het instellen van een ESET-cluster is het toevoegen van knooppunten. U kunt de optie
Automatische detectie gebrui ken of Bladeren... om knooppunten toe te voegen. Of typ de servernaam in het
tekstvak en klik op Toevoegen.
Automatisch detecteren
Voegt automatisch knooppunten toe van een bestaand Windows-failovercluster/NLB-cluster (Network Load
Balancing). De server die u gebruikt om het ESET-cluster mee te maken, moet lid zijn van dit Windows-
failovercluster/NLB-cluster om de knooppunten automatisch te kunnen toevoegen. Op het NLB-cluster moet de
functie Bediening op afstand toestaan zijn ingeschakeld in de clustereigenschappen. Anders detecteert het
ESET-cluster de knooppunten niet correct. Zodra u de lijst met nieuw toegevoegde knooppunten hebt, kunt u
ongewenste knooppunten verwijderen.
Bladeren
Computers in een domein of werkgroep vinden en selecteren. Met deze methode kunt u handmatig
knooppunten toevoegen aan het ESET-cluster. Een andere manier om knooppunten toe te voegen, is door de
hostnaam van de server te typen die u wilt toevoegen en te klikken op Toevoegen.
Laden
Lijst met knooppunten uit een bestand importeren.

77
Als u de lijst met clusterknooppunten wilt wijzigen, selecteert u het knooppunt dat u wilt verwijderen en klikt u op
Verwijderen of, als u de gehele lijst wilt leegmaken, klikt u op Alles verwijderen.
Als u al een bestaand ESET-cluster hebt, kunt u op elk gewenst moment nieuwe knooppunten hieraan toevoegen.
De stappen zijn hetzelfde als hierboven beschreven.
OPMERKING
Alle knooppunten die in de lijst blijven staan, moeten online en bereikbaar zijn. Localhost wordt standaard
toegevoegd aan de clusterknooppunten.
5.6.4.2 Clusterwizard - Clusterinstellingen
Definieer de clusternaam en specifieke netwerkgegevens (indien vereist).
Clusternaam
Typ een naam voor uw cluster en klik op Volgende.
Luisterpoort: (standaardpoort is 9777)
Als u poort 9777 al gebruikt in uw netwerkomgeving, geef dan een ander poortnummer op dat niet in gebruik is.
Poort in Windows Firewall openen
Indien geselecteerd, wordt er een regel in Windows Firewall gemaakt.

78
5.6.4.3 Clusterwizard - Clusterinstallatie-instellingen
Definieer een certificaatdistributiemodus en of u het product op andere knooppunten wilt installeren.
Certificaatdistributie
· Automatisch extern: certificaat wordt automatisch geïnstalleerd.
· Handmatig: klik op Genereren en selecteer de juiste map om de certificaten in op te slaan. Er wordt een
basiscertificaat gemaakt, evenals een certificaat voor elk knooppunt, waaronder een (lokale computer) vanaf
waar u het ESET-cluster instelt. Klik op Ja om het certificaat op de lokale computer te registreren.
Productinstallatie op andere knooppunten
· Automatisch extern: ESET Mail Securitywordt automatisch op elk knooppunt geïnstalleerd (mits het
besturingssysteem ervan dezelfde architectuur heeft).
· Handmatig: ESET Mail Security handmatig installeren (bijvoorbeeld als u een andere
besturingssysteemarchitectuur op bepaalde knooppunten hebt).
Licentie naar knooppunten pushen zonder geactiveerd product
ESET Security activeert automatisch ESET-oplossingen die zonder licenties op knooppunten zijn geïnstalleerd.
OPMERKING
Als u een ESET-cluster met verschillende besturingssysteemarchitecturen wilt maken (32-bits en 64-bits), moet
u ESET Mail Security handmatig installeren. Besturingssystemen die in gebruik zijn, worden tijdens de
volgende stappen gedetecteerd en u ziet deze informatie in het logboekvenster.
5.6.4.4 Clusterwizard - Knooppuntcontrole
Nadat u de installatiedetails hebt opgegeven, wordt er een knooppuntcontrole uitgevoerd. De volgende informatie
wordt weergegeven in het Logbestand van knooppuntcontrole:
· controle of alle bestaande knooppunten online zijn
· controle of nieuwe knooppunten toegankelijk zijn
· knooppunt is online
· administratieve share is toegankelijk
· uitvoeren op afstand is mogelijk
· juiste productversies (of geen product) zijn geïnstalleerd
· controle of de nieuwe certificaten aanwezig zijn

79
U ziet het rapport nadat de knooppuntcontrole is voltooid:

80

81
5.6.4.5 Clusterwizard - Knooppunten installeren
Wanneer u tijdens de initialisatie van het ESET-cluster een installatie op een externe computer uitvoert, wordt
geprobeerd het installatieprogramma in de map %ProgramData%\ESET\ESET Security\Installer te vinden. Als het
installatiepakket daar niet wordt gevonden, wordt u gevraagd het bestand van het installatieprogramma te zoeken.
OPMERKING
Als u een automatische externe installatie probeert uit te voeren voor een knooppunt met een andere
architectuur (32 bits versus 64 bits), wordt dit gedetecteerd en wordt u gevraagd een handmatige installatie uit
te voeren.

82
Nadat u het ESET-cluster juist hebt geconfigureerd, wordt dit op de pagina Instellingen > Server weergegeven als
ingeschakeld.
OPMERKING
Als er al een oudere versie van ESET Mail Security op sommige knooppunten is geïnstalleerd, wordt u op de
hoogte gesteld dat de nieuwste versie op deze computers is vereist. Als gevolg van het bijwerken van ESET
Mail Security wordt de computer mogelijk automatisch opnieuw opgestart.

83
Ook kunt u de huidige status controleren op de pagina Clusterstatus (Hulpmiddelen > Cluster).
5.6.5 ESET-shell
eShell (een afkorting van ESET Shell) is een opdrachtregelinterface voor ESET Mail Security. Het is een alternatief
voor de grafische gebruikersinterface (GUI). eShell bevat alle functies en opties die u normaal gesproken in de GUI
hebt. Met eShell kunt het volledige programma configureren en beheren zonder gebruik van de GUI.
Afgezien van alle functies die beschikbaar zijn in de GUI, biedt de shell ook de mogelijkheid tot automatisering door
scripts uit te voeren om te configureren, configuraties te wijzigen of om een actie uit te voeren. eShell kan ook
nuttig zijn voor degenen die een opdrachtregelinterface verkiezen boven de GUI.
OPMERKING
Voor volledige functionaliteit raden we aan dat u eShell opent met behulp van Als Administrator uitvoeren.
Hetzelfde geldt wanneer u één opdracht via de Windows-opdrachtprompt (cmd) uitvoert. Open de prompt
met behulp van Als Administrator uitvoeren. Als u de opdrachtprompt niet als beheerder uitvoert, kunt u geen
opdrachten uitvoeren omdat u onvoldoende machtigingen bezit.
eShell kan in twee modi worden uitgevoerd:
1. Interactieve modus: dit is nuttig wanneer u met eShell wilt werken (en niet slechts één opdracht wilt
uitvoeren), bijvoorbeeld voor het wijzigen van de configuratie of het bekijken van logboeken. U kunt de
interactieve modus gebruiken als u nog niet bekend bent met alle opdrachten. De interactieve modus maakt
het u gemakkelijk wanneer u door eShell navigeert. In deze modus worden tevens de beschikbare
opdrachten weergegeven die u kunt gebruiken binnen een bepaalde context.

84
2. Enkelvoudige opdrachten/Batchverwerking: u kunt deze modus gebruiken als u slechts één opdracht wilt
uitvoeren, zonder de interactieve modus van eShell te activeren. U kunt dat vanaf de Windows-
opdrachtprompt doen door eshell met de juiste parameters te typen.
VOORBEELD
eshell get status of eshell set antivirus status disabled
Als u bepaalde opdrachten (zoals het tweede voorbeeld hierboven) in batchmodus/scriptmodus wilt uitvoeren,
moet u eerst enkele instellingen configureren. Anders ziet u het bericht Toegang geweigerd. Dit is uit
veiligheidsoverwegingen.
OPMERKING
Wijzigingen in instellingen zijn nodig om het gebruik van eShell-opdrachten van een Windows-
opdrachtprompt mogelijk te maken. Klik hier voor meer informatie over het uitvoeren van batchbestanden.
Er zijn twee manieren om de interactieve modus in eShell te openen:
1. Vi a he t menu Start van Windows: Start > Alle programma's > ESET > ESET Mail Security > ESET-shell
2. Vanaf de Windows-opdrachtregels door eshell te typen en op de toets Enter te drukken
BELANGRIJK
Als u een 'eshell' is not recognized as an internal or external command-fout krijgt, wordt dit
veroorzaakt door nieuwe omgevingsvariabelen die niet door uw systeem worden geladen na de installatie van
ESET Mail Security. U kunt een nieuwe opdrachtprompt openen en eShell opnieuw starten. Als u ook dan een
fout krijgt of een kerninstallatie van ESET Mail Security hebt, start eShell dan met een absoluut pad,
bijvoorbeeld "%PROGRAMFILES%\ESET\ESET Mail Security\eShell.exe" (u moet "" gebruiken anders werkt de
opdracht niet).
Wanneer u eShell voor het eerst in de interactieve modus uitvoert, wordt er een scherm voor de eerste keer
uitvoeren (taakbegeleiding) weergegeven.
OPMERKING
Als u het scherm voor de eerste keer uitvoeren later wilt weergeven, voert u de opdracht guide in. Het scherm
toont u enkele basisvoorbeelden van hoe u eShell kunt gebruiken, met syntaxis, voorvoegsels,
opdrachtpaden, afgekorte vormen, aliassen, etc.
De volgende keer dat u eShell uitvoert, ziet u dit scherm:

85
OPMERKING
Opdrachten zijn niet hoofdlettergevoelig. U kunt hoofdletters of kleine letters gebruiken en de opdracht
wordt in beide gevallen uitgevoerd.
eShell aanpassen
U kunt eShell in de context van ui eshell aanpassen. U kunt aliassen, kleuren, taal, uitvoeringsbeleid voor scripts,
instellingen voor verborgen opdrachten en meer configureren.
5.6.5.1 Syntaxis
Syntaxis
Opdrachten moeten de juiste syntaxis hebben om te werken en kunnen bestaan uit een voorvoegsel, een context,
argumenten, opties, enzovoort. Dit is de algemene syntaxis die overal in eShell wordt gebruikt:
[<voorvoegsel>] [<opdrachtpad>] <opdracht> [<argumenten>]
Voorbeeld (zo wordt documentbeveiliging ingeschakeld):
SET ANTIVIRUS DOCUMENT STATUS ENABLED
SET : een voorvoegsel
ANTIVIRUS DOCUMENT: pad naar een afzonderlijke opdracht, een context waar deze opdracht thuishoort
STATUS: de opdracht zelf
ENABLED: een argument voor de opdracht
Al s u ? als argument bij een opdracht invoert, wordt de syntaxis voor die specifieke opdracht weergegeven.
STATUS ? bijvoorbeeld geeft de syntaxis weer voor de opdracht STATUS:
SYNTAXIS:
[get] | status
set status enabled | disabled
Het valt u misschien op dat [get] tussen rechte haken staat. Hiermee wordt aangegeven dat het voorvoegsel get de
standaardinstelling is voor de opdracht status. Dit betekent dat wanneer u status uitvoert zonder een voorvoegsel
op te geven, in feite het standaardvoorvoegsel wordt gebruikt (in dit geval get status). Als u opdrachten zonder

86
een voorvoegsel gebruikt, bespaart u tijd met typen. get is doorgaans het standaardvoorvoegsel voor opdrachten,
maar u moet zeker weten wat het standaardvoorvoegsel voor een specifieke opdracht is en dat dit het juiste
voorvoegsel is voor de opdracht die u wilt uitvoeren.
OPMERKING
Opdrachten zijn niet hoofdlettergevoelig: u kunt hoofdletters of kleine letters gebruiken en de opdracht
wordt in beide gevallen uitgevoerd.
Voorvoegsel / Bewerking
Een voorvoegsel is een bewerking. Het voorvoegsel GET geeft u informatie over hoe bepaalde functionaliteit van
ESET Mail Security is geconfigureerd en geeft een status weer (zo geeft GET ANTIVIRUS STATUS de huidige
beveiligingsstatus weer). Het voorvoegsel SET configureert functionaliteit of wijzigt de status ervan (SET ANTIVIRUS
STATUS ENABLED activeert de beveiliging).
Dit zijn de voorvoegsels die u in eShell kunt gebruiken. Een opdracht kan deze voorvoegsels wel of niet
ondersteunen:
GET
hiermee wordt de huidige instelling/status
geretourneerd
SET
hiermee wordt een waarde/status ingesteld
SELECT
selecteert een item
ADD
voegt een item toe
REMOVE
verwijdert een item
CLEAR
hiermee worden alle items/bestanden verwijderd
START
start een actie
STOP
stopt een actie
PAUSE
onderbreekt een actie
RESUME
hervat een actie
RESTORE
hiermee worden standaardinstellingen/objecten/
bestanden hersteld
SEND
verzendt een object/bestand
IMPORT
importeert uit een bestand
EXPORT
exporteert naar een bestand
OPMERKING
Voorvoe gsel s zoals GET en SET worden in veel opdrachten gebruikt, maar bepaalde opdrachten (zoals EXIT)
gebruiken geen voorvoegsel.
Opdrachtpad / Context

87
Opdrachten worden geplaatst in contexten die een structuur vormen. Het hoogste niveau van de structuur is de
root. Wanneer u eShell uitvoert, bevindt u zich op het rootniveau:
eShell>
U kunt hier een opdracht uitvoeren of een contextnaam invoeren om binnen de structuur naar die context te
navigeren. Als u bijvoorbeeld TOOLS-context invoert, wordt er een lijst weergegeven met alle opdrachten en
subcontexten die vandaaruit beschikbaar zijn.
Gele opdrachten kunt u uitvoeren en grijze opdrachten zijn subcontexten die u kunt openen. Een subcontext bevat
verdere opdrachten.
Als u wilt teruggaan naar een hoger niveau, gebruikt u .. (twee punten).
VOORBEELD
Stel u bent hier:
eShell antivirus startup>
typ .. om één niveau omhoog te gaan:
eShell antivirus>
Of, als u terug wilt naar de hoofdmap vanaf eShell antivirus startup> (dus twee niveaus lager dan de hoofdmap),
typt u .. .. (twee punten, spatie, twee punten). Zo gaat u twee niveaus omhoog, in dit geval naar het
hoofdmapniveau. Gebruik een backslash \ om rechtstreeks vanaf elk niveau terug te keren naar de hoofdmap,
ongeacht hoe diep in de contextstructuur u zich bevindt. Als u naar een bepaalde context in een hoger niveau wilt
gaan, hoeft u alleen maar het juiste aantal ..-opdrachten te gebruiken om naar het gewenste niveau te gaan,
waarbij u een spatie als scheidingsteken gebruikt. Als u bijvoorbeeld drie niveaus omhoog wilt gaan, gebruikt u
.. .. ..
Het pad is afhankelijk van de huidige context. Als de opdracht deel uitmaakt van de huidige context, voert u geen
pad in. Om bijvoorbeeld GET ANTIVIRUS STATUS uit te voeren, voert u in:
GET ANTIVIRUS STATUS: als u zich in de hoofdmapcontext bevindt (opdrachtregel bevat eShell>)
GET STATUS : als u zich in de ANTIVIRUS-context bevindt (opdrachtregel bevat eShell antivirus>)
.. GET STATUS : als u zich in de ANTIVIRUS-context bevindt (opdrachtregel bevat eShell antivirus startup>)

88
U kunt één enkele punt . (punt) gebruiken in plaats van twee .. omdat één punt een afkorting is van twee punten.
VOORBEELD
. GET STATUS : als u zich in de ANTIVIRUS-context bevindt (opdrachtregel bevat eShell antivirus startup>)
Argument
Een argument is een actie die voor een bepaalde opdracht wordt uitgevoerd. De opdracht CLEAN-LEVEL (dat zich
be vi ndt i n ANTIVIRUS REALTIME ENGINE) kan worden gebruikt met de volgende argumenten:
no: niet opschonen
normal: normaal opschonen
strict: strikt opschonen
Een ander voorbeeld bestaat uit de argumenten ENABLED en DISABLED, die worden gebruikt voor het in- of
uitschakelen van functies.
Verkorte vorm / verkorte opdrachten
Met eShell kunt u contexten, opdrachten en argumenten inkorten (mits het argument een schakeloptie of
alternatieve optie is). Het is niet mogelijk een voorvoegsel of argument te verkorten dat een concrete waarde is,
zoals een nummer, naam of pad. U kunt de cijfers 1 en 0 gebruiken in plaats van ingeschakelde en uitgeschakelde
argumenten.
VOORBEELD
set status enabled => set stat en 1
set status disabled => set stat 0
Voorbeelden van de korte indeling:
VOORBEELD
set status enabled => set stat en
add antivirus common scanner-excludes C:\path\file.ext => add ant com scann C:\path
\file.ext
Als twee opdrachten of contexten met dezelfde letters beginnen (bijvoorbeeld ABOUT en ANTIVIRUS, en u A invoert
als verkorte opdracht), kan eShell niet bepalen welke van deze twee opdrachten u wilt uitvoeren. Daarom wordt
een foutbericht weergegeven met een lijst opdrachten die beginnen met "A", waaruit u kunt kiezen:
eShell>a
De volgende opdracht is niet uniek: a
De volgende opdrachten zijn in deze context beschikbaar:
ABOUT - geeft gegevens over programma weer
ANTIVIRUS - Hiermee gaat u naar de context antivirus
Als u een of meer letters toevoegt (bijvoorbeeld AB in plaats van alleen A), voert eShell ABOUT uit omdat deze nu
uniek is.

89
OPMERKING
Wanneer u er zeker van wilt zijn dat een opdracht op de gewenste manier wordt uitgevoerd, raden wij aan
geen opdrachten, argumenten enzovoort in te korten en de volledige indeling te gebruiken. Op deze manier is
de uitvoering exact zoals u wilt en voorkomt u ongewenste fouten. Dit geldt in het bijzonder voor
batchbestanden/-scripts.
Automatisch aanvullen
Deze nieuwe functie is geïntroduceerd in eShell 2.0 en is zeer vergelijkbaar met automatisch aanvullen op de
Windows-opdrachtprompt. Terwijl Windows-opdrachtprompt bestandspaden aanvult, vult eShell ook namen van
opdrachten, contexten en bewerkingen aan. Het aanvullen van argumenten wordt niet ondersteund. Als u een
opdracht typt, hoeft u alleen maar op Tab te drukken om beschikbare variaties aan te vullen of er doorheen te
bladeren. Druk op Shift + Tab om achteruit te bladeren. Het combineren van afgekorte vormen en automatisch
aanvullen wordt niet ondersteund. Gebruik een van de twee. Als u bijvoorbeeld antivir real scan typt en op Tab
drukt, gebeurt er niets. Typ in plaats hiervan antivir en druk op Tab om antivirus te voltooien, typ vervolgens real
+ Tab en scan + Tab. U kunt dan voor alle beschikbare variaties bladeren: scan-create, scan-execute, scan-open, etc.
Aliassen
Een alias is een alternatieve naam die kan worden gebruikt voor het uitvoeren van een opdracht (mits aan de
opdracht een alias is toegekend). Er zijn een paar standaardaliassen:
(global) close: exit
(global) quit: exit
(global) bye: exit
warnlog : tools log events
virlog: tools log detections
antivirus on-demand log: tools log scans
"(global)" betekent dat de opdracht overal kan worden gebruikt, onafhankelijk van de huidige context. Aan één
opdracht kunnen meerdere aliassen zijn toegewezen. De opdracht EXIT heeft de aliassen CLOSE, QUIT en BYE.
Wanneer u eShell wilt afsluiten, kunt u de opdracht EXIT zelf gebruiken of een van de aliassen van deze opdracht.
De al ias VIRLOG is een alias voor de opdracht DETECTIONS, die zich bevindt in de TOOLS LOG-context. Op deze manier
is de opdracht detections beschikbaar vanuit de ROOT-context, waardoor deze toegankelijker is (u hoeft TOOLS niet in
te voeren en vervolgens naar de LOG-context te gaan maar kunt de opdracht rechtstreeks vanuit ROOT uitvoeren).
Met eShell kunt u uw eigen aliassen definiëren. De opdracht ALIAS vindt u in de UI ESHELL-context.
Instellingen met wachtwoord beveiligen
ESET Mail Security-instellingen kunnen met een wachtwoord worden beveiligd. U kunt een wachtwoord instellen
via de grafische gebruikersinterface of via eShell met set ui access lock-password. U moet dit wachtwoord voor
bepaalde opdrachten interactief opgeven (zoals opdrachten waarmee instellingen of gegevens worden gewijzigd).
Als u van plan bent gedurende een lange periode met eShell te werken en het wachtwoord niet steeds opnieuw
wilt invoeren, kunt u eShell het wachtwoord laten onthouden met de opdracht set password. Uw wachtwoord
wordt dan automatisch ingevuld voor elke uitgevoerde opdracht waarvoor een wachtwoord is vereist. Het
wachtwoord wordt onthouden tot u eShell afsluit. Dit betekent dat u set password opnieuw moet gebruiken
wanneer u een nieuwe sessie start en eShell uw wachtwoord wilt laten onthouden.
Gebruikershandleiding/Help
Als u de opdracht GUIDE of HELP uitvoert, wordt een scherm bij de eerste keer uitvoeren weergegeven waarin wordt
uitgelegd hoe u eShell gebruikt. Deze opdracht is beschikbaar vanuit de context (eShell>).
Opdrachtsgeschiedenis
eShell houdt een geschiedenis bij van eerder uitgevoerde opdrachten. Dit is alleen van toepassing op de huidige
interactieve eShell-sessie. Zodra u eShell afsluit, wordt de opdrachtgeschiedenis verwijderd. Gebruik de pijltoetsen
omhoog en omlaag op uw toetsenbord om door de geschiedenis te navigeren. Zodra u de gewenste opdracht hebt

90
gevonden, kunt u deze nogmaals uitvoeren of bewerken zonder dat u de gehele opdracht opnieuw hoeft in te
vullen.
CLS (Clear screen: scherm wissen)
De opdracht CLS kan worden gebruikt om het scherm te wissen. Dit werkt op dezelfde manier als bij de Windows-
opdrachtprompt of soortgelijke opdrachtregelinterfaces.
EXIT / CLOSE / QUIT / BYE
Om eShell te sluiten of verlaten, gebruikt u een van de volgende opdrachten (EXIT, CLOSE, QUIT of BYE).
5.6.5.2 Opdrachten
Dit gedeelte bevat enkele elementaire eShell-opdrachten met een beschrijving.
OPMERKING
Opdrachten zijn niet hoofdlettergevoelig. U kunt hoofdletters of kleine letters gebruiken. De opdracht wordt
in beide gevallen uitgevoerd.
Voorbeeldopdrachten (binnen de context ROOT):
ABOUT
Hiermee wordt informatie over het programma weergegeven. Het bevat gegevens zoals:
· Naam van het geïnstalleerde ESET-beveiligingsproduct en het versienummer.
· Details van besturingssyteem en basishardware.
· Gebruikersnaam (inclusief domein), volledige computernaam (FQDN, als uw server een lid in een domein is)
en seatnaam.
· Geïnstalleerde onderdelen van uw ESET-beveiligingsproduct, waaronder het versienummer van elk
onderdeel.
CONTEXTPAD:
root
PASSWORD
Normaal gesproken wordt u bij het uitvoeren van met wachtwoord beveiligde opdrachten om beveiligingsredenen
gevraagd om een wachtwoord in te voeren. Dit is van toepassing op opdrachten die bijvoorbeeld de
antivirusbeveiliging uitschakelen of die van invloed zijn op de configuratie van ESET Mail Security. Iedere keer dat u
een dergelijke opdracht uitvoert, wordt u gevraagd om een wachtwoord. Als u echter wilt voorkomen dat u het
wachtwoord iedere keer moet invoeren, kunt u dit wachtwoord definiëren. Dit wordt onthouden in eShell en
automatisch ingevoerd wanneer er een opdracht met wachtwoordbeveiliging wordt uitgevoerd.
OPMERKING
Uw wachtwoord werkt alleen voor de huidige interactieve sessie van eShell. Wanneer u eShell afsluit, wordt
dit gedefinieerde wachtwoord vergeten. Wanneer u eShell opnieuw start, moet het wachtwoord opnieuw
worden gedefinieerd.
Het gedefinieerde wachtwoord kan ook worden gebruikt wanneer u niet-ondertekende batchbestanden of scripts
uitvoert. Zorg ervoor dat Uitvoeringsbeleid voor ESET-shell is ingesteld op Volledige toegang wanneer u niet-
ondertekende batchbestanden uitvoert. Hier volgt een voorbeeld van een dergelijk batchbestand:
eshell set password plain <yourpassword> "&" set status disabled
Deze bovenstaande samengevoegde opdracht definieert het wachtwoord en schakelt de beveiliging uit.

91
BELANGRIJK
U kunt het beste waar mogelijk ondertekende batchbestanden gebruiken. Zo voorkomt u dat er wachtwoorden
in leesbare tekst in het batchbestand worden opgenomen (als u de bovenstaande methode gebruikt). Zie
Batchbestanden/scripts (gedeelte Ondertekende batchbestanden) voor meer informatie.
CONTEXTPAD:
root
SYNTAXIS:
[get] | restore password
set password [plain <password>]
BEWERKINGEN:
get: hiermee wordt het wachtwoord weergegeven
set: hiermee wordt het wachtwoord ingesteld of gewist
restore: hiermee wordt het wachtwoord gewist
ARGUMENTEN:
plain: schakeloptie om wachtwoord als parameter in te voeren
password: wachtwoord
VOORBEELDEN:
set password plain <uw_wachtwoord>: hiermee wordt een wachtwoord ingesteld dat wordt gebruikt voor
opdrachten met wachtwoordbeveiliging
restore password: hiermee wordt het wachtwoord gewist
VOORBEELDEN:
get password: gebruik deze opdracht om te zien of het wachtwoord is geconfigureerd of niet (hiermee worden
alleen sterretjes "*" weergegeven, niet het wachtwoord zelf). Wanneer er geen sterretjes worden
weergegeven, betekent dit dat er geen wachtwoord is ingesteld.
set password plain <uw_wachtwoord>: gebruik deze opdracht om een gedefinieerd wachtwoord in te stellen
restore password: met deze opdracht wordt het gedefinieerde wachtwoord gewist
STATUS
Hiermee wordt informatie weergegeven over de huidige beveiligingsstatus van ESET Mail Security (vergelijkbaar
met de GUI).
CONTEXTPAD:
root
SYNTAXIS:
[get] | restore status
set status disabled | enabled
BEWERKINGEN:

92
get: de status van antivirusbeveiliging weergeven
set: antivirusbeveiliging uitschakelen/inschakelen
restore: standaardinstellingen herstellen
ARGUMENTEN:
disabled: antivirusbeveiliging uitschakelen
enabled: antivirusbeveiliging inschakelen
VOORBEELDEN:
get status: de huidige beveiligingsstatus weergeven
set status disabled: beveiliging uitschakelen
restore status: de beveiliging herstellen naar de standaardinstelling (ingeschakeld)
VIRLOG
Dit is een alias van de opdracht DETECTIONS. Deze opdracht is nuttig wanneer u informatie wilt zien over
gedetecteerde infiltraties.
WARNLOG
Dit is een alias van de opdracht EVENTS. Deze opdracht is nuttig wanneer u informatie wilt zien over verschillende
gebeurtenissen.
5.6.5.3 Batchbestanden/scripts
U kunt eShell als een krachtig scripthulpmiddel voor automatisering gebruiken. Als u een batchbestand met eShell
wilt gebruiken, moet u er een maken en daarin eShell en een opdracht opnemen.
VOORBEELD
eshell get antivirus status
U kunt opdrachten ook in ketens uitvoeren. Dit is soms nodig als u een type van een bepaalde geplande taak wilt
opvragen. Voer in zo'n geval het volgende in:
eshell select scheduler task 4 "&" get scheduler action
De selectie van een item (taaknummer 4 in dit geval) is doorgaans alleen van toepassing op een momenteel actief
exemplaar van eShell. Als u deze twee opdrachten direct na elkaar zou uitvoeren, zou de tweede opdracht
mislukken met de fout "Geen taak geselecteerd of geselecteerde taak bestaat niet meer".
Uit veiligheidsoverwegingen is het uitvoeringsbeleid standaard ingesteld op Beperkte scriptmogelijkheden.
Hierdoor kunt u eShell als controlehulpmiddel gebruiken, maar het is niet mogelijk configuratiewijzigingen in ESET
Mail Security aan te brengen door een script uit te voeren. Als u een script probeert uit te voeren met opdrachten
die mogelijk gevolgen voor de beveiliging hebben, bijvoorbeeld doordat de beveiliging wordt uitgeschakeld, wordt
he t be richt Toegang geweigerd weergegeven. Wij raden aan dat u gebruikmaakt van ondertekende batchbestanden
om opdrachten uit te voeren die configuratiewijzigingen aanbrengen.
Als u de configuratie wilt wijzigen met één opdracht die handmatig op de Windows-opdrachtprompt is ingevoerd,
moet u eShell volledige toegang verlenen (niet aanbevolen). Om volledige toegang te geven, gebruikt u de
opdracht ui eshell shell-execution-policy in de interactieve modus van eShell zelf, of via de grafische
gebrui ke rsi nte rf ace i n Geavanceerde instellingen (F5)> Gebruikersinterface > ESET-shell.

93
Ondertekende batchbestanden
Met eShell kunt u gangbare batchbestanden (*.bat) met een handtekening beveiligen. Scripts worden ondertekend
met hetzelfde wachtwoord dat wordt gebruikt om instellingen te beveiligen. Om een script te ondertekenen moet
u e erst Instellingen beveiligen inschakelen. Dit kunt u doen via de gebruikersinterface, of vanuit eShell met de
opdracht set ui access lock-password. Wanneer het wachtwoord voor de beveiliging van instellingen is
ingesteld, kunt u batchbestanden gaan ondertekenen.
OPMERKING
Als u het wachtwoord voor de beveiliging van instellingen wijzigt, moet u alle scripts opnieuw ondertekenen,
anders mislukt het uitvoeren van de scripts nadat u het wachtwoord hebt gewijzigd. Het wachtwoord dat
wordt opgegeven wanneer het script wordt ondertekend, moet namelijk overeenkomen met het wachtwoord
voor de beveiliging van instellingen op het doelsysteem.
Als u een batchbestand wilt ondertekenen, voert u sign <script.bat> uit vanuit de hoofdcontext van eShell,
waarbij script.bat het pad is naar het script dat u wilt ondertekenen. Voer het wachtwoord in dat voor
ondertekening wordt gebruikt en bevestig het wachtwoord. Dit wachtwoord moet overeenkomen met het
wachtwoord voor de beveiliging van instellingen. De handtekening wordt in de vorm van een opmerking aan het
eind van het batchbestand geplaatst. Als het script al is ondertekend, wordt de handtekening vervangen door de
nieuwe handtekening.
OPMERKING
Als u een eerder ondertekend batchbestand aanpast, moet dit opnieuw worden ondertekend.
Gebruik de volgende opdracht om een ondertekend batchbestand vanaf de Windows-opdrachtprompt of als een
geplande taak uit te voeren:
eshell run <script.bat>
Hierbij is script.bat het pad naar het batchbestand.
VOORBEELD
eshell run d:\myeshellscript.bat
5.6.6 ESET Dynamic Threat Defense
ESET Dynamic Threat Defense (EDTD) biedt nog een beveiligingslaag doordat gebruik wordt gemaakt van
geavanceerde ESET-cloudtechnologie om nieuwe, nog nooit eerdere geziene bedreigingstypen te detecteren. Dit is
een betaalde service. Hoewel deze service lijkt op ESET LiveGrid®, biedt ESET Dynamic Threat Defense u het
voordeel dat u beveiligd bent tegen mogelijke consequenties die door nieuwe bedreigingen worden veroorzaakt.
Als ESET Dynamic Threat Defense verdachte code of gedag detecteert, verhindert EDTD verdere activiteit van de
bedreiging door deze tijdelijk in de quarantaine van ESET Dynamic Threat Defense te plaatsen. Een verdacht
voorbeeld (bestand of e-mailbericht) wordt automatisch verzonden naar de ESET-cloud, waar de ESET Dynamic
Threat Defense-server het voorbeeld analyseert met moderne malwaredetectie-engines. Terwijl het bestand of de
e-mail in de quarantaine van ESET Dynamic Threat Defense staat, wacht ESET Mail Security op de resultaten van de
ESET Dynamic Threat Defense-server. Nadat de analyse is voltooid, haalt ESET Mail Security een rapport op met een
samenvatting van het gedrag van het gedetecteerde voorbeeld. Als het voorbeeld onschadelijk is, wordt het uit de
quarantaine van ESET Dynamic Threat Defense gehaald, anders blijft het in quarantaine staan. Als het om een vals-
positief resultaat gaat en u zeker weet dat het bestand of de e-mail geen bedreiging vormt, kunt u die uit de
quarantaine van ESET Dynamic Threat Defense vrijgeven voordat ESET Mail Security de ESET Dynamic Threat
Defense-serverresultaten heeft ontvangen.

94
ESET Dynamic Threat Defense-resultaten voor voorbeelden worden doorgaans binnen enkele minuten geleverd
voor e-mailberichten. Het standaardinterval voor wachten is echter ingesteld op 5 minuten. In zeldzame gevallen
wanneer ESET Dynamic Threat Defense-resultaten niet binnen dat interval worden ontvangen, wordt het bericht
vrijgegeven. U kunt het interval wijzigen in een tijd die uw voorkeur heeft (ergens tussen 5 tot 60 minuten, in
stappen van 1 minuut).
De ESET Dynamic Threat Defense-functie is zichtbaar in ESET Mail Security, ongeacht de activeringsstatus ervan. Als
u geen licentie hebt, is ESET Dynamic Threat Defense inactief. De ESET Dynamic Threat Defense-licentie wordt
be hee rd door ESET Security Management Center en de activering zelf moet met beleidsregels worden uitgevoerd
vanuit ESET Security Management Center.
Nadat u ESET Dynamic Threat Defense hebt geactiveerd, wordt uw eigen ESET Dynamic Threat Defense-profiel
gemaakt op de ESET Dynamic Threat Defense-server. In dit profiel worden alle ESET Dynamic Threat Defense-
analyseresultaten van voorbeelden opgeslagen die door uw ESET Mail Security zijn verzonden.
U hebt het volgende nodig om de ESET Dynamic Threat Defense-functie te laten werken:
ESET Mail Security beheerd via ESET Security Management Center
ESET Mail Security geactiveerd met een ESET Dynamic Threat Defense-licentie
Schakel ESET Dynamic Threat Defense in uw ESET Mail Security in met ESET Security Management Center-beleid
Vervolgens kunt u ESET Dynamic Threat Defense volledig benutten, en handmatig een voorbeeld verzenden voor
ESET Dynamic Threat Defense-analyse .

95
5.6.7 ESET SysInspector
ESET SysInspector is een toepassing die uw computer grondig inspecteert, gedetailleerde informatie verzamelt
over systeemonderdelen zoals geïnstalleerde stuurprogramma's en toepassingen, netwerkverbindingen of
belangrijke registervermeldingen, en die het risico van ieder onderdeel beoordeelt. Deze gegevens kunnen u
helpen de oorzaak van afwijkend systeemgedrag vast te stellen. Problemen kunnen worden veroorzaakt door een
malware-infectie, maar ook door incompatibele software of hardware.
Kl ik op Maken en voer een korte Opmerking in die het logbestand beschrijft dat wordt gemaakt. Wacht tot het ESET
SysInspector-logbestand is gegenereerd (status wordt weergegeven als Gemaakt). Het maken van het logbestand
kan enige tijd duren afhankelijk van uw hardwareconfiguratie en systeemgegevens.
Het venster ESET SysInspector bevat de volgende informatie over gemaakte logbestanden:
· Tijd: de tijd waarop het logbestand is gemaakt.
· Opmerking: een korte opmerking.
· Gebruiker: de naam van de gebruiker die het logbestand heeft gemaakt.
· Status: de status van het gemaakte logbestand.
De volgende acties zijn beschikbaar:
· Weergeven: hiermee wordt het gemaakte logbestand geopend. U kunt ook met de rechtermuisknop klikken
op een logbestand en Weergeven in het contextmenu selecteren.
· Vergelijken: hiermee worden twee bestaande logbestanden vergeleken.
· Maken: hiermee wordt een nieuw logbestand gemaakt. Geef een beknopte opmerking op die het logbestand
beschrijft dat wordt gemaakt en klik op Maken. Wacht tot het ESET SysInspector-logbestand is gemaakt
(Status wordt weergegeven als Gemaakt).
· Verwijderen: hiermee worden de geselecteerde logbestanden uit de lijst verwijderd.
Als u met de rechtermuisknop op een of meer geselecteerde logbestanden klikt, zijn de volgende opties
beschikbaar in het contextmenu:
· Weergeven: hiermee wordt het geselecteerde logbestand geopend in ESET SysInspector (net zoals wanneer
u dubbelklikt op een logbestand).
· Vergelijken: hiermee worden twee bestaande logbestanden vergeleken.
· Maken: hiermee wordt een nieuw logbestand gemaakt. Geef een beknopte opmerking op die het logbestand
beschrijft dat wordt gemaakt en klik op Maken. Wacht tot het ESET SysInspector-logbestand is gemaakt
(Status wordt weergegeven als Gemaakt).
· Verwijderen: hiermee worden de geselecteerde logbestanden uit de lijst verwijderd.
· Alles verwijderen: hiermee kunt u alle logbestanden verwijderen.
· Exporteren: hiermee wordt het logbestand geëxporteerd als een .xml-bestand of een ingepakt .xml-bestand.
5.6.8 ESET SysRescue Live
ESET SysRescue Live is een gratis hulpprogramma waarmee u een opstartbare cd/dvd of USB-station voor
noodherstel kunt maken. U kunt een geïnfecteerde computer opstarten vanaf uw noodherstelmedium en
vervolgens op malware scannen en geïnfecteerde bestanden opschonen.
Het belangrijkste voordeel van ESET SysRescue Live is dat de ESET Security-oplossing onafhankelijk van het
besturingssysteem kan worden uitgevoerd, maar het programma toch rechtstreeks toegang heeft tot de schijf en
het bestandssysteem. Hierdoor is het mogelijk bedreigingen te verwijderen die anders niet kunnen worden
verwijderd (bijvoorbeeld omdat het besturingssysteem actief is).

96
5.6.9 Planner
Planner beheert en start geplande taken volgens gedefinieerde parameters. U kunt een lijst met alle geplande
taken in de vorm van een tabel bekijken waarin de parameters van de taken worden weergegeven, zoals taaktype
en naam, de starttijd en tijdstip van vorige keer uitgevoerd. U kunt ook nieuwe geplande taken maken door op Taak
toevoegen te klikken. U kunt de configuratie van een bestaande geplande taak bewerken door te klikken op de
knop Bewerken. Stel de lijst met geplande taken terug op de standaardinstellingen, klik op Standaard en vervolgens
op Ongedaan maken . Alle wijzigingen worden ongedaan gemaakt, gaan verloren en kunnen niet meer worden
hersteld.
Er is een reeks vooraf gedefinieerde standaardtaken:
· Logbestanden onderhouden
· Regelmatige automatische update (gebruik deze taak om de frequentie te wijzigen)
· Automatisch update uitvoeren na inbelverbinding
· Automatisch bijwerken na aanmelding van gebruiker
· Automatische bestandscontrole bij opstarten (na aanmelding van de gebruiker)
· Automatische bestandscontrole bij opstarten (na geslaagde update van module)
OPMERKING
Schakel de desbetreffende selectievakjes in om taken te activeren of deactiveren.
Als u de volgende acties wilt uitvoeren, moet u met de rechtermuisknop op een taak klikken:

97
Taakdetails
weergeven
Geeft gedetailleerde informatie weer over een geplande taak wanneer u dubbelklikt op of met
de rechtermuisknop klikt op de geplande taak.
Nu uitvoeren
Voert een in Planner geselecteerde taak direct uit.
Toevoegen...
Hiermee start u een wizard waarmee u een nieuwe taak in Planner maakt.
Bewerken...
Hiermee bewerkt u de configuratie van een bestaande, geplande taak (zowel een standaardtaak
als een door de gebruiker gedefinieerde taak).
Verwijderen
Hiermee verwijdert u een bestaande taak.
5.6.9.1 Planner - Taak toevoegen
Een nieuwe geplande taak maken:
1. Kl ik op Taak toevoegen.
2. Ge ef e en Taaknaam op en configureer uw aangepaste, geplande taak.
3. Taaktype: selecteer het toepasselijke Taaktype in het vervolgkeuzemenu.
OPMERKING
Als u een taak wilt deactiveren, klikt u op de schuifregelaar naast Ingeschakeld. Als u de taak later wilt
activeren, gebruikt u het selectievakje in de weergave Planner.
4. Taaktijden: selecteer een van de opties om te definiëren wanneer u wilt dat de taak wordt uitgevoerd.
Afhankelijk van uw keuze, wordt u gevraagd om een bepaalde tijd, dag, een bepaald interval of een bepaalde
gebeurtenis te kiezen.

98
5. Overgeslagen taak: als de taak niet op het vooraf ingestelde tijdstip kon worden verricht, kunt u opgeven
wanneer de taak alsnog moet worden uitgevoerd.
6. Toepassing uitvoeren: als de taak is gepland om een externe toepassing uit te voeren, kiest u een
uitvoerbaar bestand in de mappenstructuur.
7. Als u wijzigingen wilt aanbrengen, klikt u op Terug om terug te keren naar een eerdere stap om parameters
aan te passen.
8. Kl ik op Voltooien om de taak te maken of wijzigingen toe te passen.
De nieuwe geplande taak wordt weergegeven in de weergave Planner.

99
5.6.9.1.1 Taaktype
De configuratiewizard is voor elk Taaktype van een geplande taak anders. Geef een Taaknaam op en selecteer een
gewenst Taaktype in het vervolgkeuzemenu:
· Externe toepassing uitvoeren: hiermee kunt u de uitvoering van een externe toepassing plannen.
· Onderhoud van logbestanden: logbestanden bevatten ook restanten van verwijderde records. Met deze taak
worden records in logbestanden regelmatig geoptimaliseerd, zodat deze effectief werken.
· Opstartbestanden van systeem controleren: hiermee worden bestanden gecontroleerd die tijdens het
opstarten of aanmelden mogen worden uitgevoerd.
· Momentopname van computerstatus maken: hiermee maakt u met ESET SysInspector een momentopname
van de computer, waarbij gedetailleerde informatie over systeemonderdelen (zoals stuurprogramma's en
toepassingen) wordt verzameld en het risiconiveau van elk onderdeel wordt beoordeeld.
· Computerscan op aanvraag: hiermee wordt een scan uitgevoerd op bestanden en mappen op uw computer.
· Bijwerken: hiermee wordt een updatetaak gepland door de detectie-engine en de programmaonderdelen bij
te werken.
· Database scan van postvak: hiermee kunt u een databasescan plannen en kiezen welke items worden
gescand. Het gaat hierbij in wezen om het uitvoeren van de functie Op aanvraag database scannen.
OPMERKING
Al s u Beveiliging van postvakdatabase hebt ingeschakeld, kunt u deze taak wel inplannen, maar wordt het
foutbericht ' Beveiliging van postvakdatabase - Scan is onderbroken vanwege een fout' weergegeven in het
gedeelte Scan van het hoofdvenster. Om dit te voorkomen, moet u ervoor zorgen dat Beveiliging van
postvakdatabase is uitgeschakeld gedurende de periode dat Databasescan van postvak is gepland om te
worden uitgevoerd.
· E-mail quarantaine rapporten verzenden: hiermee plant u het per e-mail verzenden van e-
mailquarantainerapporten.
· E-mail quarantaine rapporten voor de Administrator verzenden: hiermee plant u het per e-mail verzenden
van e-mailquarantainerapporten.
· Achtergrondscan: hiermee geeft u Exchange Server de gelegenheid indien nodig een achtergrondscan van de
database uit te voeren.
· Hyper-V-scan: plant een scan van de virtuele schijven in Hyper-V.
· Office 365-scan: plant een scan voor hybride Office 365-omgevingen.
Als u de taak wilt deactiveren nadat die is gemaakt, klikt u op de schakelaar naast Ingeschakeld. U kunt de taak later
activeren met het selectievakje in de weergave Planner. K li k op Volgende om door te gaan naar de volgende stap.

100
5.6.9.1.2 Taaktijden
Selecteer een van de volgende tijdopties:
· Eenmaal: de taak wordt slechts eenmaal uitgevoerd, en wel op de opgegeven datum en tijd. Deze optie is
bedoeld als u de taak slechts eenmaal wilt uitvoeren, op het opgegeven moment. Geef de begin- en eindtijd
op bi j Taakuitvoering.
· Herhaaldelijk: de taak wordt uitgevoerd volgens het opgegeven tijdsinterval (in minuten). Geef in
Taakuitvoering de tijd op waarop de taak elke dag moet worden uitgevoerd.
· Dagelijks: de taak wordt elke dag op het opgegeven tijdstip uitgevoerd.
· Wekelijks: de taak wordt een of meerdere keren per week uitgevoerd, op de geselecteerde dag(en) en tijd.
Deze optie is bedoeld om de taak alleen herhaaldelijk uit te voeren op bepaalde dagen van de week, te
beginnen op de opgegeven dag en tijd. Geef de begintijd op bij Tijd van taakuitvoering. Selecteer de dag of
dagen van de week waarop de taak moet worden uitgevoerd.
· Bij gebeurtenis - De taak wordt uitgevoerd nadat een opgegeven gebeurtenis heeft plaatsgevonden.
Al s u Taak overslaan indien op batterijvoeding inschakelt, wordt een taak niet gestart als het systeem op
batterijvoeding werkt op het moment dat de taak moet worden gestart, bijvoorbeeld op computers die op een
noodstroomvoorziening (UPS) werken.
5.6.9.1.3 Bij gebeurtenis
Bij het plannen van een taak die door een gebeurtenis wordt geactiveerd, kunt u het minimuminterval voor het
herhalen van de taak opgeven.
De taak kan worden geactiveerd door de volgende gebeurtenissen:
· Telkens wanneer de computer wordt opgestart
· De eerste keer dat de computer elke dag wordt opgestart
· Inbelverbinding met internet/VPN
· Module bijgewerkt
· Product bijgewerkt
· Gebruikersaanmelding: de taak wordt geïmplementeerd wanneer de gebruiker zich bij het systeem
aanmeldt. Als u zich meerdere keren per dag bij de computer aanmeldt, kies dan 24 uur om de taak slechts
eenmaal per dag uit te voeren, namelijk wanneer u zich de eerste keer op een dag aanmeldt, en daarna de
volgende dag.
· Bedreigingsdetectie
5.6.9.1.4 Toepassing uitvoeren
Met deze taak kunt u de uitvoering van een externe toepassing plannen.
· Uitvoerbaar bestand: kies een uitvoerbaar bestand in de mapstructuur, klik op Bladeren (...) of voer het pad
handmatig in.
· Werkmap: definieer de werkmap van de externe toepassing. Alle tijdelijke bestanden van het geselecteerde
uitvoerbare bestand worden in deze map gemaakt.
· Parameters: opdrachtregelparameters voor de toepassing (optioneel).

101
5.6.9.1.5 Overgeslagen taak
Als de taak niet op het vooraf ingestelde tijdstip kon worden uitgevoerd, kunt u opgeven wanneer de taak moet
worden uitgevoerd:
· Op het volgende geplande tijdstip: de taak wordt op het opgegeven tijdstip uitgevoerd (bijvoorbeeld na 24
uur).
· Zo spoedig mogelijk: de taak wordt zo spoedig mogelijk uitgevoerd, wanneer de acties die verhinderen dat
de taak kan worden uitgevoerd niet meer geldig zijn.
· Meteen, als tijd sinds vorige keer uitvoeren groter is dan een opgegeven waarde - Tijd sinds vorige keer
uitvoeren (uren): nadat u deze optie hebt geselecteerd, wordt de taak steeds herhaald na de opgegeven
tijdsperiode (in uur).
5.6.9.1.6 Overzicht van geplande taak
In dit dialoogvenster staat uitvoerige informatie over een geplande taak wanneer u dubbelklikt op de taak in de
weergave Planner of met de rechtermuisknop klikt op de geplande taak en Taakdetails weergeven kiest.
5.6.10 Voorbeelden voor analyse verzenden
In het dialoogvenster voor verzending van voorbeelden kunt u een bestand of site naar ESET verzenden om te laten
analyseren. Als u een bestand op uw computer of een site op internet ontdekt dat verdacht gedrag vertoont, stuur
dit dan naar het viruslaboratorium van ESET om het te laten analyseren. Als het bestand een schadelijke toepassing
of website blijkt te zijn, wordt detectie ervan in een van de volgende updates opgenomen.
U kunt het bestand per e-mail verzenden. Comprimeer het bestand of de bestanden met een programma zoals
WinRAR of WinZip, beveilig het archief met het wachtwoord infected en stuur het naar samples@eset.com. Gebruik
een duidelijk onderwerp en geef zo veel mogelijk informatie over het bestand (bijvoorbeeld de website waar u het
bestand hebt gedownload).
Controleer voordat u een voorbeeld naar ESET stuurt of deze aan een of beide van de volgende criteria voldoet:
· het bestand of de website wordt helemaal niet gedetecteerd
· het bestand of de websiteis onterecht aangemerkt als bedreiging
Als aan minimaal één van de bovenstaande vereisten niet wordt voldaan, ontvangt u geen reactie tot er meer
informatie wordt verstrekt.
Selecteer in het vervolgkeuzemenu Reden voor verzending van bestand de beschrijving die het best bij uw bericht
past:
· Verdacht bestand
· Verdachte site (een website die is geïnfecteerd met malware)
· Fout-positief bestand (een bestand dat wordt gedetecteerd als infectie, maar dat niet is geïnfecteerd)
· Fout-positieve site
· Anders
Bestand/site
Het pad naar het bestand dat of de website die u van plan bent om te verzenden.
E-mail van contactpersoon
Dit e-mailadres van de contactpersoon wordt samen met de verdachte bestanden naar ESET verzonden en kan
worden gebruikt om contact met u op te nemen als meer informatie nodig is voor de analyse. Het invoeren van
een e-mailadres voor de contactpersoon is optioneel. Omdat onze servers dagelijks tienduizenden bestanden

102
ontvangen, is het onmogelijk om iedereen te beantwoorden. U zult dan ook geen antwoord van ESET
ontvangen, tenzij er meer informatie nodig is.
Anoniem verzenden
Gebruik het selectievakje naast Anoniem verzenden om een verdacht bestand of een verdachte website te
verzenden zonder uw e-mailadres op te geven.
5.6.10.1 Verdacht bestand
Waargenomen tekens en symptomen van malware-infectie
Voer een beschrijving in van het verdachte gedrag van het bestand dat u op uw computer hebt waargenomen.
Oorsprong van bestand (URL-adres of leverancier)
Voer de oorsprong (bron) in van het bestand en hoe u dit bestand hebt ontdekt.
Opmerkingen en aanvullende informatie
Hier kunt u aanvullende informatie of een beschrijving invoeren die van pas kan komen bij het
identificatieproces van het verdachte bestand.
OPMERKING
De eerste parameter, Waargenomen tekenen en symptomen van malware-infectie, is verplicht. Het
verstrekken van aanvullende informatie kan onze laboratoria echter aanzienlijk helpen bij het
identificatieproces voor voorbeelden.
5.6.10.2 Verdachte site
Selecteer een van de volgende opties in het vervolgkeuzemenu Wat is er mis met de site:
Geïnfecteerd
Een website waarop zich virussen of andere schadelijke software bevindt die op diverse manieren wordt
verspreid.
Phishing
Wordt vaak gebruikt om toegang te krijgen tot gevoelige gegevens zoals bankrekeningnummers, pincodes,
enzovoort. Zie de woordenlijst voor meer informatie over dit type aanval.
Oplichting
Een malafide of frauduleuze website.
Anderis
Gebruik deze optie als geen van de bovenstaande opties van toepassing zijn op de site die u verzendt.
Opmerkingen en aanvullende informatie
U kunt verdere informatie of een beschrijving invoeren die kan helpen bij de analyse van de verdachte website.
5.6.10.3 Vals positief bestand
Wij vragen u om bestanden te verzenden die als infectie worden gedetecteerd maar dit niet zijn, zodat wij onze
antivirus- en antispyware-engine kunnen verbeteren en anderen beter kunnen beschermen. Valse positieven (VP)
kunnen optreden wanneer een patroon van een bestand overeenkomt met een patroon in de detectie-engine.
OPMERKING
De eerste drie parameters zijn vereist voor het identificeren van legitieme toepassingen en om deze te
kunnen onderscheiden van schadelijke code. Het verstrekken van aanvullende informatie kan onze laboratoria
echter aanzienlijk helpen bij het identificatieproces en de verwerking van voorbeelden.
Naam en versie van toepassing

103
Programmatitel en versie (bijvoorbeeld nummer, alias of codenaam).
Oorsprong van bestand (URL-adres of leverancier)
Voer de oorsprong (bron) van het bestand in en een opmerking over hoe u dit bestand hebt ontdekt.
Doel van toepassing
De algemene beschrijving van de toepassing, het type toepassing (bijvoorbeeld, browser, mediaspeler, ...) en
de functionaliteit ervan.
Opmerkingen en aanvullende informatie
Hier kunt u aanvullende informatie of beschrijvingen invoeren die kunnen helpen bij de verwerking van het
verdachte bestand.
5.6.10.4 Vals positieve site
Wij vragen u sites te melden die worden gedetecteerd als geïnfecteerd, oplichting of phishing, maar dit niet zijn.
Vals-positieven (VP) kunnen optreden wanneer een patroon van een bestand overeenkomt met een patroon in de
detectie-engine. Meld een dergelijke website om onze antivirus- en antiphishing-engine te verbeteren en anderen
beter te beschermen.
Opmerkingen en aanvullende informatie
Hier kunt u aanvullende informatie of beschrijvingen invoeren die kunnen helpen bij de verwerking van het
verdachte bestand.
5.6.10.5 Overige
Gebruik dit formulier als het bestand niet kan worden gecategoriseerd als Verdacht bestand of Vals positief.
Reden voor verzending van bestand
Geef hier een gedetailleerde beschrijving op en de reden waarom u het bestand verzendt.

104
5.6.11 Quarantaine
De hoofdfunctie van de quarantaine is het veilig opslaan van geïnfecteerde bestanden. Bestanden moeten in
quarantaine worden geplaatst als ze niet kunnen worden opgeschoond, als het niet veilig of raadzaam is om ze te
verwijderen of als ze onterecht door ESET Mail Security zijn gedetecteerd. U kunt elk bestand in quarantaine
plaatsen. Dit is raadzaam als een bestand zich verdacht gedraagt, maar niet door de antivirusscanner wordt
gedetecteerd. In quarantaine geplaatste bestanden kunnen voor analyse naar het viruslaboratorium van ESET
worden verzonden.
Bestanden die zijn opgeslagen in de quarantainemap, kunnen worden bekeken in een tabel waarin de datum en het
tijdstip van de quarantaine, het pad naar de oorspronkelijke locatie van het geïnfecteerde bestand, de grootte van
het bestand in bytes, de reden (bijvoorbeeld object toegevoegd door gebruiker) en het aantal bedreigingen
(bijvoorbeeld of het een archief is dat meerdere infiltraties bevat) worden weergegeven.
Als er e-mailberichtobjecten in de bestandsquarantaine in quarantaine zijn geplaatst, wordt het pad naar het
postvak of de map/bestandsnaam weergegeven.
Bestanden in quarantaine plaatsen
ESET Mail Security plaatst verwijderde bestanden automatisch in quarantaine (als u deze optie niet hebt
uitgeschakeld in het waarschuwingsvenster). U kunt elk willekeurig verdacht bestand handmatig in quarantaine
plaatsen door te klikken op de knop Quarantaine. In quarantaine geplaatste bestanden worden van hun
oorspronkelijke locatie verwijderd. Ook kan het contextmenu hiervoor worden gebruikt. Klik met de
rechtermuisknop in het venster Quarantaine e n se le cte e r Quarantaine.
Herstellen vanuit quarantaine
Bestanden die in quarantaine zijn geplaatst, kunnen ook worden teruggezet op de oorspronkelijke locatie.
Gebruik hiervoor de functie Herstellen, die beschikbaar is in het contextmenu, door met de rechtermuisknop te
klikken op het gewenste bestand in het venster Quarantaine. Als een bestand is gemarkeerd als een potentieel
ongewenste toepassing , is de optie Herstellen en uitsluiten van scannen beschikbaar. Het contextmenu biedt

105
tevens de optie Herstellen naar..., waarmee u bestanden kunt terugzetten naar een andere locatie dan waar
deze zijn verwijderd.
OPMERKING
Als het programma per ongeluk een onschadelijk bestand in quarantaine heeft geplaatst, sluit het bestand dan
uit van scannen nadat u het hebt teruggezet en stuur het bestand naar de klantenservice van ESET.
Een bestand verzenden vanuit quarantaine
Als u een verdacht bestand in quarantaine hebt geplaatst dat niet is gedetecteerd door het programma, of als
een bestand ten onrechte als geïnfecteerd is beoordeeld (bijvoorbeeld door heuristische analyse van de code)
en vervolgens in quarantaine is geplaatst, stuur het bestand dan naar het viruslaboratorium van ESET. U kunt
een bestand vanuit quarantaine verzenden door met de rechtermuisknop erop te klikken en Opsturen voor
analyse te selecteren in het contextmenu.
Uit quarantaine verwijderen
Klik met de rechtermuisknop op een bepaald item en selecteer Uit quarantaine verwijderen of selecteer de
toepasselijke items en druk op Del op uw toetsenbord.

106
6. Instellingen voor serverbeveiliging
Dit is de belangrijkste integratieoptie. Gebruik de schuifregelaar om integratie van Beveiliging van postvakdatabase
of Beveiliging van e-mailtransport in uw Exchange Server in of uit te schakelen.
OPMERKING
Als u Microsoft Exchange Server 2007 of 2010 uitvoert, kunt u kiezen tussen Beveiliging van postvakdatabase en
On-demand databasescan van postvak. Er kan slechts één beveiligingstype tegelijk actief zijn. Als u besluit om
On-demand databasescan van postvak te gebruiken, moet u de integratie van Beveiliging van postvakdatabase
uitschakelen. Anders is On-demand databasescan van postvak niet beschikbaar.
U kunt ook de prioriteit van agenten wijzigen.
ESET Mail Security biedt met de volgende functies significante beveiliging voor uw Microsoft Exchange Server:
· Antivirus en antispyware
· Antispambeveiliging
· Antiphishing-beveiliging
· Regels
· Beveiliging van e-mailtransport (Exchange Server 2007, 2010, 2013, 2016, 2019)
· Beveiliging van postvakdatabase (Exchange Server 2007, 2010)
· On-demand databasescan van postvak (Exchange Server 2007, 2010, 2013, 2016, 2019)
· Quarantaine voor e-mail (instellingen voor type e-mailquarantaine)

107
6.1 Agentprioriteit instellen
Indien nodig kunt u de volgorde aangeven waarin agenten van ESET Mail Security actief worden nadat de Microsoft
Exchange Server is gestart. Een numerieke waarde definieert de prioriteit. Een lager getal staat voor een hogere
prioriteit. Dit is van toepassing op Microsoft Exchange Server 2007 en nieuwer.
Omhoog/Omlaag
Hiermee verhoogt of verlaagt u de prioriteit van een geselecteerde agent door deze omhoog te verplaatsen in
de lijst met agenten.
6.2 Antivirus en antispyware
In dit gedeelte kunt u opties van Antivirus en antispyware configureren voor uw e-mailserver.
BELANGRIJK
Beveiliging van e-mailtransport wordt geleverd door de transportagent en is alleen beschikbaar voor Microsoft
Exchange Server 2007 en later, maar uw Exchange Server moet de functie Edgetransportserver of
Hubtransportserver hebben. Dit is ook van toepassing op een enkele serverinstallatie met meerdere Exchange
Server-functies op een computer (zolang deze de functie Edgetransportserver of Hubtransportserver heeft).
Beveiliging van e-mailtransport
Al s u Antivirus- en antispywarebeveiliging inschakelen voor e-mailtransport uitschakelt, blijft de ESET Mail
Security-invoegtoepassing voor Exchange-server geladen in het proces van Microsoft Exchange Server. De
berichten worden doorlopen zonder ze te scannen op virussen in de transportlaag. Berichten worden nog
steeds gescand op virussen en spam in de databaselaag, en bestaande regels worden ook nog steeds toegepast.

108
Beveiliging van postvakdatabase

109
Al s u Antivirus- en antispywarebeveiliging inschakelen voor postvakdatabase uitschakelt, blijft de ESET Mail
Security-invoegtoepassing voor Exchange-server geladen in het proces van Microsoft Exchange Server. De
berichten worden doorlopen zonder ze te scannen op virussen in de databaselaag. Berichten worden nog
steeds gescand op virussen en spam in de transportlaag, en bestaande regels worden ook nog steeds toegepast.
On-demand databasescan van postvak
Is beschikbaar nadat u Beveiliging van postvakdatabase hebt uitgeschakeld op de server.
ThreatSense-parameters
U kunt scanparameters wijzigen voor Beveiliging van e-mailtransport, Beveiliging van postvakdatabase en On-
demand databasescan van postvak.

110
6.3 Antispambeveiliging
Antispambeveiliging voor uw e-mailserver is standaard ingeschakeld. Gebruik de schuifregelaar naast
Antispambeveiliging inschakelen om deze functie uit te schakelen.
OPMERKING
Het uitschakelen van Antispambeveiliging heeft geen gevolgen voor de beveiligingsstatus. Zelfs als Antispam
is uitgeschakeld, wordt de groene tekst U bent beveiligd weergegeven in het gedeelte Controle van de hoofd-
GUI. Het uitschakelen van Antispam wordt niet beschouwd als een verlaging van het beveiligingsniveau.
Witte lijsten van Exchange Server gebruiken om antispambeveiliging automatisch over te slaan
Hiermee laat u ESET Mail Security specifieke witte lijsten van Exchange gebruiken. Als deze functie is
ingeschakeld, wordt rekening gehouden met het volgende:
· Het IP-adres van de server staat op de lijst met toegestane IP-adressen van de Exchange Server
· De ontvanger van het bericht heeft de vlag voor het omzeilen van antispam ingesteld in zijn of haar postvak
· De ontvanger van het bericht heeft het adres van de afzender in zijn of haar lijst met veilige afzenders staan
(zorg dat u synchronisatie van de lijst met veilige afzenders in uw Exchange-serveromgeving hebt
geconfigureerd, inclusief aggregatie van veilige lijsten)
Als een van de bovenstaande condities van toepassing is op een inkomend bericht, wordt de antispamcontrole
omzeild voor dit bericht. Het bericht wordt niet op SPAM beoordeeld en wordt afgeleverd in het postvak van de
ontvanger.
Markering Antispam overslaan accepteren die is ingesteld op SMTP-sessie
Is nuttig als u geverifieerde SMTP-sessies hebt tussen Exchange-servers met de instelling voor het omzeilen
van antispam. Als u bijvoorbeeld een edgeserver en een hubserver hebt, is scannen van het verkeer tussen de

111
twee servers niet nodig. De optie Markering Antispam overslaan accepteren die is ingesteld op SMTP-sessie is
standaard ingeschakeld maar is alleen van toepassing als de vlag voor het omzeilen van antispam is
geconfigureerd voor de SMTP-sessie op de Exchange-server. Als u Markering Antispam overslaan accepteren
die is ingesteld op SMTP-sessie uitschakelt, scant ESET Mail Security de SMTP-sessie op spam, ongeacht de
instellingen voor het omzeilen van antispam op uw Exchange Server.
OPMERKING
De Antispam-database moet regelmatig worden bijgewerkt, zodat de antispammodule de best mogelijke
beveiliging kan bieden. Zorg dat ESET Mail Security toegang heeft tot de juiste IP-adressen op de nodige
poorten om periodieke updates van de Antispam-database toe te staan. Zie ons KB-artikel voor meer
informatie over welke IP's en poorten u moet inschakelen in uw firewall van derden.
Meer instellingen voor elke functie vindt u in hun eigen gedeelte:
· Filteren en verificatie
· Geavanceerde instellingen
· Instellingen voor grijze lijst
· SPF en DKIM
· Backscatterbeveiliging
6.3.1 Filteren en verificatie
U kunt de lijsten Goedgekeurd, Geblokkeerd en Genegeerd configureren door criteria op te geven, zoals IP-adres of
bereik, domeinnaam, enz. Klik op Bewerken voor de lijst die u wilt beheren als u criteria wilt toevoegen, aanpassen
of verwijderen.
OPMERKING
IP-adressen of domeinen die zijn opgenomen in de lijsten Genegeerd worden niet getoetst aan de hand van
RBL of DNSBL. Wel worden er andere antispambeveiligingstechnieken op toegepast.
Lijsten Genegeerd moeten alle IP-adressen/domeinnamen van de interne infrastructuur bevatten. U kunt ook
IP-adressen/domeinnamen van uw internetproviders of extern verzendende mailservers openemen die
momenteel op een van de zwarte lijsten van RBL of DNSBL staan (een Blackhole List van ESET of een Blackhole
List van een andere leverancier). Hierdoor kunt u e-mails ontvangen van bronnen die op de lijsten Genegeerd
staan, ook al staan deze op een zwarte lijst. Dergelijke inkomende e-mails worden ontvangen en de inhoud
daarvan wordt nader onderzocht met behulp van andere antispambeveiligingstechnieken.
Lijst met
goedgekeurde IP-
adressen
Plaatst e-mails die afkomstig zijn van opgegeven IP-adressen automatisch op de witte lijst.
Lijst met
geblokkeerde IP-
adressen
Blokkeert automatisch e-mails die afkomstig zijn van opgegeven IP-adressen.
Lijst met genegeerde
IP-adressen
Lijst met IP-adressen die tijdens classificatie worden genegeerd. Gebruik de schuifregelaar
Is onderdeel van interne infrastructuur als u de lokale IP-adressen van uw netwerk op de
witte lijst plaatst. Zie onderstaande voorbeeld.
Lijst met
geblokkeerde
domeinen in
berichttekst
Blokkeert e-mailberichten waarin de opgegeven domeinnaam in het tekstgedeelte van
berichten staat. Alleen domeinen met een echt TLD (top-level domain) worden
geaccepteerd.

112
Lijst met
goedgekeurde IP-
adressen
Plaatst e-mails die afkomstig zijn van opgegeven IP-adressen automatisch op de witte lijst.
Lijst met genegeerde
domeinen in
berichttekst
Opgegeven domeinen in het tekstgedeelte van berichten worden tijdens classificatie
genegeerd. Alleen domeinen met een echt TLD (top-level domain) worden geaccepteerd.
Lijst met
geblokkeerde IP-
adressen in
berichttekst
Blokkeert e-mailberichten met het opgegeven IP-adres in het tekstgedeelte van berichten.
Lijst met genegeerde
IP-adressen in
berichttekst
Opgegeven IP-adressen in het tekstgedeelte van berichten worden tijdens classificatie
genegeerd.
Lijst met
goedgekeurde
afzenders
Plaatst e-mails die afkomstig zijn van de opgegeven afzender op de witte lijst.
Lijst met
geblokkeerde
afzenders
Blokkeert e-mails die afkomstig zijn van de opgegeven afzender.
Lijst met
goedgekeurde
domeinen-naar-IP-
adressen
Plaatst e-mails op de witte lijst die afkomstig zijn van IP-adressen die zijn omgezet vanuit
opgegeven domeinen. SPF-records (Sender Policy Framework) worden herkend bij het
omzetten van IP-adressen.
Lijst met
geblokkeerde
domeinen-naar-IP-
adressen
Blokkeert e-mails die afkomstig zijn van IP-adressen die zijn omgezet vanuit opgegeven
domeinen. SPF-records worden herkend bij het omzetten van IP-adressen.
Lijst met genegeerde
domeinen-naar-IP-
adressen
Lijst met domeinen die worden omgezet in IP-adressen die op hun beurt tijdens classificatie
niet meer worden gecontroleerd. SPF-records worden herkend bij het omzetten van IP-
adressen.
Lijst met
geblokkeerde landen
Blokkeert e-mails uit opgegeven landen. De blokkering is gebaseerd op GeoIP. Als een
spambericht wordt verzonden door een mailserver waarvan het IP-adres is vermeld in de
geolocatiedatabase voor een land dat u hebt geselecteerd in de Geblokkeerde landen,
wordt het automatisch gemarkeerd als spam en wordt actie ondernomen op grond van de
instelling Actie bij spamberichten onder Beveiliging van e-mailtransport.
OPMERKING
In domeinlijsten worden alleen domeinen met een echt TLD (top-level domain) geaccepteerd, volgens de
officiële Hoofdzonedatabase van TLD's .
Als u meerdere vermeldingen tegelijk wilt invoeren, klikt u op Geef meerdere waarden op in het pop-upvenster
Toevoegen en kiest u welk scheidingsteken moet worden gebruikt. Dit kan Nieuwe regel, Komma of Puntkomma
zijn.

113
VOORBEELD
Doelstelling: De lokale IP-adressen van uw infrastructuur uitsluiten van antispambeveiliging door deze toe te
voegen aan de lijst met te negeren IP-adressen
Navi ge e r naar Geavanceerde instellingen (F5) > Server > Antispambeveiliging > Filteren en verificatie.
Kl ik op Bewerken naast Lijst met genegeerde IP-adressen.
Kl ik op Toevoegen en geef het IP-adresbereik op van uw netwerkinfrastructuur (opmaak van IP-adresbereik
1.1.1.1-1.1.1.255). U kunt meer bereiken (of afzonderlijke IP-adressen) blijven toevoegen aan de lijst, indien
nodig.
Gebruik de schuifregelaar Is onderdeel van interne infrastructuur.
Greylisting en SPF
Geef het domein op dat u op de witte lijst met IP-adressen wilt plaatsen of geef de witte lijst met IP-adressen op
om Greylisting en SPF automatisch te omzeilen. U kunt Logbestanden in he t SMTP-beveiligingslogbestand bekijken.
Als u deze opties wilt gebruiken, moet u Greylisting of SPF inschakelen, of allebei de opties. In het geval van SPF
moet u de instelling Automatisch berichten afwijzen als SPF-controle is mislukt en/of de instelling Greylisting
automatisch omzeilen als SPF-controle is geslaagd inschakelen.
Gebruik antispamlijsten om greylisting automatisch te omzeilen
Indien ingeschakeld, wordt de lijst met goedgekeurde en genegeerde IP-adressen gebruikt in combinatie met
witte lijsten met IP-adressen en domeinen om Greylisting en SPF automatisch te omzeilen.
Whitelist met IP-adressen
U kunt IP-adressen, IP-adressen met een masker en IP-bereik toevoegen. U kunt de lijst wijzigen door op
Toevoegen, Bewerken of Verwijderen te klikken. Of u kunt uw aangepaste lijst importeren vanuit een bestand
in plaats van elke vermelding handmatig toe te voegen. Klik hiertoe op Importeren en blader naar uw bestand
met daarin de vermeldingen die u aan de lijst wilt toevoegen. Als u uw bestaande lijst naar een bestand wilt
exporteren, gaat u op soortgelijke wijze te werk, maar selecteert u Exporteren in het contextmenu.
Whitelist met naar IP-adressen omgezette domeinen
Met deze optie kunt u domeinen opgeven (bijvoorbeeld domainname.local) . Ge bruik Toevoegen, Verwijderen
of Alles verwijderen om de lijst te beheren. Als u uw aangepaste lijst wilt importeren vanuit een bestand in
plaats van elke vermelding handmatig toe te voegen, klikt u op Importeren en bladert u naar uw bestand met
daarin de vermeldingen die u aan de lijst wilt toevoegen. Als u uw bestaande lijst naar een bestand wilt
exporteren, gaat u op soortgelijke wijze te werk, maar selecteert u Exporteren in het contextmenu.
OPMERKING
Greylisting en SPF worden beoordeeld door Beveiliging van e-mailtransport en hiermee kunt u witte lijsten
met IP-adressen en domeinen gebruiken alsmede een lijst met goedgekeurde of te negeren IP-adressen. Als u
echter gebruikmaakt van SPF-regels wordt met geen van deze witte lijsten rekening gehouden voor regels.

114
6.3.2 Antispam geavanceerde instellingen
Op basis van deze instellingen kunnen berichten volgens de vooraf bepaalde criteria door externe servers
(ge defi nie erd al s RBL - Realtime Blackhole List en DNSBL - DNS Blocklist) worden geverifieerd.
Maximum aantal geverifieerde adressen van Received:-kopteksten
U kunt het aantal IP-adressen beperken dat door Antispam wordt gecontroleerd. Het gaat hierbij om de IP-
adressen die in Received: from-kopteksten zijn geschreven. De standaardwaarde is 0, wat betekent dat er geen
maximum is.
Verifieer het adres van de afzender bij de zwarte lijst met eindgebruikers
E-mailberichten die niet vanaf e-mailservers (computers die niet als e-mailservers staan vermeld) worden
verzonden, worden geverifieerd om ervoor te zorgen dat de afzender niet op de zwarte lijst staat. Deze optie is
standaard ingeschakeld. U kunt deze optie uitschakelen als dat nodig is, maar berichten die niet vanaf e-
mailservers worden verzonden, worden niet gecontroleerd bij de zwarte lijst.
Extra RBL-servers
Dit is een lijst met RBL-servers (Realtime Blackhole List) waar query's naartoe worden verzonden wanneer
berichten worden geanalyseerd.
OPMERKING
Voer bij de toevoeging van bijkomende RBL-servers de domeinnaam van de server in (bijvoorbeeld
sbl.spamhaus.org). Deze werkt met alle retourcodes die door de server worden ondersteund.
In plaats hiervan kunt u ook een servernaam opgeven met een retourcode in de notatie server:reactie
(bijvoorbeeld zen.spamhaus.org:127.0.0.4). Bij gebruik van deze notatie raden we u aan om elke servernaam en
retourcode afzonderlijk toe te voegen zodat u een volledige lijst hebt. Klik op Geef meerdere waarden op in het
venster Toevoegen om alle servernamen en hun retourcodes op te geven. Vermeldingen moeten er als het
onderstaande voorbeeld uitzien. De hostnamen en retourcodes van uw RBL-servers kunnen er anders uitzien:

115
Uitvoeringslimiet voor RBL-aanvragen (in seconden)
Met deze optie kunt u een maximumtijd voor RBL-query's instellen. Er worden alleen RBL-antwoorden gebruikt
van RBL-servers die op tijd reageren. Als de waarde wordt ingesteld op '0' wordt er geen time-out
afgedwongen.
Maximaal aantal RBL-geverifieerde adressen
Met deze optie kunt u beperken hoeveel IP-adressen van RBL-servers query's ontvangen. Het totale aantal RBL-
query's is het aantal IP-adressen in de koptekst Ontvangen: (maximaal RBL maxcheck IP-adressen),
vermenigvuldigd met het aantal RBL-servers dat in de RBL-lijst is opgegeven. Als de waarde is ingesteld op '0',
wordt een onbeperkt aantal ontvangen kopteksten gecontroleerd. IP's op de lijst met genegeerde IP-adressen
tellen niet mee voor de limiet op het aantal RBL IP-adressen.
Extra DNSBL-servers
Dit is een lijst met DNSBL-servers (DNS Blocklist) waar query's naartoe worden verzonden met domeinen en IP-
adressen die uit het tekstgedeelte van het bericht zijn gehaald.
OPMERKING
Voer bij de toevoeging van bijkomende DNSBL-servers de domeinnaam van de server in (bijvoorbeeld
dbl.spamhaus.org). Deze werkt met alle retourcodes die door de server worden ondersteund.

116
Als alternatief kunt u een servernaam opgeven met een retourcode onder de vorm van server:reactie
(bijvoorbeeld zen.spamhaus.org:127.0.0.4). In dit geval raden we u aan om elke servernaam en retourcode
afzonderlijk toe te voegen, zodat u een volledige lijst hebt. Klik op Geef meerdere waarden op in het venster
Toevoegen om alle servernamen en hun retourcodes op te geven. Vermeldingen moeten er als het onderstaande
voorbeeld uitzien. De hostnamen en retourcodes van uw DNSBL-servers kunnen er anders uitzien:
Uitvoeringslimiet voor DNSBL-aanvragen (in seconden)
Hiermee kunt u een maximale time-out instellen voor de voltooiing van alle DNSBL-query's.
Maximaal aantal DNSBL-geverifieerde adressen
Met deze optie kunt u beperken hoeveel IP-adressen bij de DNSBL-server worden geverifieerd.
Maximaal aantal DNSBL-geverifieerde domeinen
Met deze optie kunt u beperken hoeveel domeinen bij de DNSBL-server worden geverifieerd.
Maximumgrootte voor scannen van berichten (kB)
Hiermee voorkomt u dat Antispam berichten scant die groter zijn dan de opgegeven waarde. Standaardwaarde
0 betekent het scannen van berichten zonder beperking van de berichtgrootte. Er is doorgaans geen reden om
een antispamscan te beperken, maar als u dat in bepaalde situaties wel wilt, kunt u de waarde wijzigen in de
vereiste grootte. Indien ingesteld, verwerkt de Antispam-engine berichten tot de opgegeven grootte en
worden grotere berichten genegeerd.
OPMERKING
De kleinst mogelijke limiet is 12 kB. Als u een waarde instelt van 1 tot 12, leest de Antispam-engine altijd
mi nimaal 12 kB.
Tijdelijk afwijzen van onbepaalde berichten inschakelen
Als de antispamengine niet kan bepalen of het bericht wel of geen SPAM is, wat inhoudt dat het bericht enkele
verdachte kenmerken van SPAM heeft maar onvoldoende om het bericht als SPAM te markeren (bijvoorbeeld
de eerste e-mail van een campagne of een e-mail afkomstig van een IP-bereik met gemengde beoordelingen),
kan ESET Mail Security met deze instelling (indien ingeschakeld) het bericht tijdelijk afwijzen, net als dat bij
Greylisting het geval is, en het bericht blijven afwijzen gedurende een bepaalde periode, tot:
· De periode is verstreken en het bericht wordt geaccepteerd bij de volgende poging tot bezorgen. Dit bericht
behoudt zijn oorspronkelijke classificatie (SPAM of HAM).
· de antispamcloud genoeg gegevens heeft verzameld om het bericht correct te classificeren voordat de
periode is verstreken.

117
Het afgewezen bericht wordt niet door ESET Mail Security vastgehouden omdat het bericht overeenkomstig de
SMTP RFC opnieuw door de mailserver van de afzender moet worden verzonden.
Inschakelen verzenden van tijdelijk afgewezen berichten ter analyse
De inhoud van het bericht wordt automatisch voor verdere analyse verzonden. Hierdoor wordt de
berichtenclassificatie van toekomstige e-mailberichten verbeterd.
BELANGRIJK
Het is mogelijk dat tijdelijk afgewezen berichten die voor analyse worden verzonden, in feite HAM zijn. In
zeldzame gevallen kunnen tijdelijk afgewezen berichten handmatig worden geanalyseerd. Schakel deze
functie alleen in als er geen risico bestaat op het lekken van potentieel gevoelige gegevens.
6.3.3 Instellingen voor grijze lijst
Met de functie Greylisting inschakelen wordt een functie ingeschakeld waarmee gebruikers tegen spam worden
beveiligd met de volgende techniek: De transportagent stuurt een SMTP-retourwaarde voor “tijdelijk weigeren” (de
standaardinstelling is 451/4.7.1) voor alle e-mails die worden ontvangen van een niet-herkende afzender. Een
legitieme server zal het bericht na enige tijd opnieuw proberen te verzenden. Spamservers zullen het bericht
meestal niet opnieuw proberen te verzenden, aangezien doorgaans duizenden e-mailadressen worden verwerkt en
er geen tijd wordt genomen om het bericht opnieuw te verzenden. Greylisting is een extra laag antispambeveiliging
en is niet van invloed op de spambeoordelingsmogelijkheden van de antispammodule.
Bij de beoordeling van de berichtbron wordt bij de Greylisting-methode rekening gehouden met Lijst met
goedgekeurde IP-adressen, Lijst met genegeerde IP-adressen, de lijst Veilige afzenders en Lijst met toegestane
adressen op de Exchange-server, en de AntispamBypass-instellingen voor het postvak van de ontvanger. E-mails
van deze lijsten met IP-adressen/afzenders of e-mails die worden bezorgd in een postvak waarvoor de optie
AntispamBypass is ingeschakeld, worden overgeslagen door de Greylisting-detectiemethode.
Alleen domeingedeelte van afzenderadres gebruiken
Negeert de naam in het e-mailadres van de afzender; er wordt alleen rekening gehouden met het domein.
Synchroniseer greylisting-databases voor ESET-clusters
Databasevermeldingen op de greylist worden in real time gedeeld tussen de servers in de ESET-cluster. Als een
van de servers een bericht ontvangt dat met greylisting is verwerkt, wordt deze informatie door ESET Mail
Security uitgezonden naar de rest van de knooppunten in de ESET-cluster.
Tijdslimiet voor afwijzen van initiële verbinding (min.)
Wanneer een bericht de eerste keer wordt bezorgd en tijdelijk wordt geweigerd, wordt met deze parameter de
tijdsperiode gedefinieerd waarin het bericht altijd wordt geweigerd (gemeten vanaf de eerste weigering).
Nadat de gedefinieerde tijdsperiode is verstreken, wordt het bericht gewoon ontvangen. De minimumwaarde
die kan worden ingevoerd is 1 minuut.
Vervaltijd voor niet-geverifieerde verbindingen (uren)
Met deze parameter wordt het minimale tijdsinterval gedefinieerd waarin de drie gegevens worden
opgeslagen. Een geldige server moet een gewenst bericht opnieuw verzenden voordat deze periode verloopt.
Deze waarde moet groter zijn dan de waarde van Tijdlimiet voor afwijzen van initiële verbinding.
Vervaltijd voor geverifieerde verbindingen (dagen)
Het minimale aantal dagen dat de drie gegevens worden opgeslagen. Gedurende deze tijd worden e-mails van
een bepaalde afzender zonder vertraging ontvangen. Deze waarde moet groter zijn dan de waarde van
Vervaltijd voor niet-geverifieerde verbindingen.
SMTP-reactie voor tijdelijk afgewezen verbindingen.

118
Ge ef e en Reactiecode, Statuscode en Reactiebericht op waarmee de tijdelijke SMTP-afwijzingsreactie wordt
gedefinieerd die naar de SMTP-server wordt verzonden als een bericht is afgewezen. Voorbeeld van een SMTP-
weigeringsreactiebericht:
Reactiecode
Statuscode
Reactiebericht
451
4.7.1
Probeer het later opnieuw
WAARSCHUWING
onjuiste syntaxis van de SMTP-antwoordcodes kan leiden tot de verkeerde werking van de Greylisting-
beveiliging. Dit kan als gevolg hebben dat spamberichten aan clients worden bezorgd of dat berichten
helemaal niet worden bezorgd.
OPMERKING
U kunt ook systeemvariabelen gebruiken bij het definiëren van de SMTP-weigeringsreactie.
Alle berichten die zijn beoordeeld met de Greylisting-methode, worden in het SMTP-beveiligingslogboek
geregistreerd.
6.3.4 SPF en DKIM
Sender Policy Framework (SPF) en DomainKeys Identified Mail (DKIM) worden als validatiemethoden gebruikt om
te controleren of een inkomend e-mailbericht dat aangeeft van een specifiek domein afkomstig te zijn door de
eigenaar van dat domein is geautoriseerd. Deze methode beschermt geadresseerden tegen de ontvangst van
vervalste e-mailberichten. ESET Mail Security maakt tevens gebruik van DMARC-beoordeling (Domain-based
Message Authentication, Reporting and Conformance; op domein gebaseerde verificatie, rapportage en
conformiteit van berichten) voor een verdere verbetering ten opzichte van SPF en DKIM.
SPF
Er wordt een controle uitgevoerd om na te gaan of een e-mail door een legitieme afzender is verzonden. Een DNS-
lookup voor SPF-records van het domein van de verzender wordt uitgevoerd om een lijst met IP-adressen te
verkrijgen. Als een van de IP-adressen van de SPF-records overkomt met het werkelijke IP-adres van de afzender, is
het resultaat van de SPF-controle Geslaagd. Als het werkelijke IP-adres van deze afzender niet overeenkomt, is het
resultaat Mislukt. Niet alle domeinen hebben echter SPF-records die in DNS zijn gespecificeerd. Als er geen SPF-
records in DNS aanwezig zijn, is het resultaat Niet beschikbaar. Er kan af en toe een time-out optreden voor de DNS-
aanvraag als gevolg waarvan het resultaat ook Niet beschikbaar is.
DKIM
Wordt door organisaties gebruikt om te voorkomen dat e-mailberichten worden vervalst door een digitale
handtekening conform de DKIM-standaard toe te voegen aan de kopteksten van uitgaande berichten. Hierbij wordt
een privédomeinsleutel gebruikt om de kopteksten van uw uitgaande e-mail te versleutelen en een openbare
versie van de sleutel toe te voegen aan de DNS-records van het domein. ESET Mail Security kan vervolgens de
openbare versie van de sleutel ophalen om de inkomende kopteksten te ontsleutelen en verifiëren of het bericht
werkelijk afkomstig is van uw domein en de kopteksten niet ondertussen zijn gewijzigd.
OPMERKING
Exchange Server 2010 en oudere versies zijn niet volledig compatibel met DKIM, omdat kopteksten die in
digitaal ondertekende inkomende berichten zijn gevoegd tijdens de DKIM-validatie worden aangepast.
DMARC

119
Bouwt voort op twee bestaande mechanismen, SPF en DKIM. U kunt de regels voor beveiliging van e-mailtransport
gebruiken ter evaluatie van het DMARC-resultaat en voor de actie DMARC-beleid toepassen.
DNS-servers automatisch detecteren
Gebruikt instellingen van uw netwerkadapter.
IP-adres van DNS-server
Als u specifieke DNS-servers voor SPF en DKIM wilt gebruiken, voer dan het IP-adres (in IPv4- of IPv6-indeling)
van de gewenste DNS-server in.
Time-out van DNS-query (seconden)
Geef de time-out voor de DNS-reactie op.
Automatisch berichten afwijzen als SPF-controle is mislukt
Als de SPF-controle onmiddellijk resulteert in Mislukt, kan een e-mailbericht worden afgewezen voordat het
wordt gedownload.
VOORBEELD
De SPF-controle wordt uitgevoerd op de SMTP-laag. Deze kan echter automatisch op de SMTP-laag dan wel
tijdens de beoordeling van regels worden afgewezen.
Het is niet mogelijk om afgewezen berichten te registreren in het Gebeurtenissenlogboek als u automatische
afwijzing op de SMTP-laag gebruikt. Dat is omdat logboekregistratie gebeurt door een regelactie, terwijl de
automatische afwijzing direct plaatsvindt op de SMTP-laag, dus vóór de regelbeoordeling. Omdat de berichten
worden afgewezen voordat de regels worden beoordeeld, is er geen informatie beschikbaar voor
logboekregistratie op het moment dat de regelbeoordeling plaatsvindt.

120
U kunt afgewezen berichten registreren, maar alleen als u de berichten afwijst door middel van een
regelactie. Als u berichten wilt afwijzen die de SPF-controle niet hebben doorstaan en deze afgewezen
berichten in een logbestand wilt registreren, schakelt u Automatisch berichten afwijzen indien SPF-controle
mislukt uit en maakt u de volgende regel voor Beveiliging van e-mailtransport:
Voorwaarde
Type: SPF-resultaat
Bewerking: is
Parameter: Mislukt
Acties
Type: Bericht afwijzen
Type:Registreren in gebeurtenissenlogboek
Gebruiken From: koptekst als MAIL FROM leeg is
De kopte kst MAIL FROM kan leeg zijn en kan ook eenvoudig worden vervalst. Als deze optie is geactiveerd en
MAIL FROM is leeg, wordt het bericht gedownload en wordt in plaats daarvan de koptekst From: gebruikt.
Greylisting automatisch omzeilen als SPF-controle is geslaagd
Er is geen reden om Greylisting te gebruiken voor een bericht als het resultaat van de SPF-controle Geslaagd
was.
SMTP-afwijzingsreactie
U kunt een Reactiecode, Statuscode en Reactiebericht opgeven waarmee de tijdelijke SMTP-afwijzingsreactie
wordt gedefinieerd die naar de SMTP-server wordt verzonden als een bericht is afgewezen. U kunt een
reactiebericht in de volgende indeling typen:
Reactiecode
Statuscode
Reactiebericht
550
5.7.1
SPF-controle mislukt
6.3.5 Backscatterbeveiliging
Spambackscatter zijn verkeerd omgeleide niet-bezorgberichten die door mailservers worden verzonden.
Backscatter is een ongewenst neveneffect van spam. Wanneer een spambericht wordt geweigerd door de e-
mailserver van de ontvanger, wordt er een NDR (Non-Delivery Report), ook wel een niet-bezorgbericht genoemd,
verzonden naar de zogenaamde afzender (een e-mailadres dat is vervalst en als afzender van het oorspronkelijke
spambericht fungeert), niet de werkelijke afzender van de spam. Een gebruiker, die eigenaar is van het e-
mailadres, ontvangt een NDR-bericht, hoewel de gebruiker helemaal niet betrokken was bij het oorspronkelijke
spambericht. Dit is het punt waarop Backscatterbeveiliging aan de slag gaat. U kunt voorkomen dat spam-NDR's
worden bezorgd bij het postvak van gebruikers in uw organisatie door ESET Mail Security Backscatterbeveiliging te
gebruiken.
Wanne er u NDR-controle inschakelt, moet u Handtekening-seed opgeven (een tekenreeks van minimaal 8 tekens,
vergelijkbaar met een wachtwoordzin). ESET Mail Security Backscatterbeveiliging schrijft X-Eset-NDR: <hash> in de
koptekst van elk uitgaand e-mailbericht. <hash> is een versleutelde handtekening met daarin ook de Handtekening-
seed die u hebt opgegeven.
Als een legitiem e-mailbericht niet kan worden bezorgd, ontvangt uw e-mailserver doorgaans een NDR, die wordt
gecontroleerd door ESET Mail Security, die op zoek gaat naar X-Eset-NDR: <hash> in de kopteksten. Als de X-Eset-
NDR: aanwezig is en de handtekening <hash> komt overeen, wordt de NDR bezorgd bij de afzender van het
legitieme e-mailbericht om aan te geven dat bezorging van het bericht is mislukt. Als de Eset-NDR: niet aanwezig is
of de handtekening <hash> onjuist is, is dat het bewijs dat het om spambackscatter gaat en wordt de NDR
geweigerd.
NDR-automatisch negeren indien niet geslaagd voor controle

121
Als de NDR-controle onmiddellijk resulteert in Mislukt, kan een e-mailbericht worden afgewezen voordat het
wordt gedownload.
U kunt de activiteit van Backscatterbeveiliging i n he t SMTP-beveiligingslogbestand bekijken.
6.4 Antiphishing-beveiliging
Phishing is een poging om gevoelige informatie te verkrijgen, zoals gebruikersnamen, wachtwoorden, gegevens
van uw bankrekening of creditcard, en pincodes via e-mail of webpagina's die als een betrouwbare entiteit zijn
vermomd. Deze activiteit vindt doorgaans met kwade bedoelingen plaats. Het gaat hierbij om een vorm van 'sociaal
engineering' (manipulatie van gebruikers met als doel het verkrijgen van vertrouwelijke informatie).
ESET Mail Security biedt antiphishingbeveiliging, waarmee wordt voorkomen dat gebruikers toegang hebben tot
webpagina's waarvan bekend is dat er phishing plaatsvindt. In het geval van e-mailberichten waarin koppelingen
naar phishingwebpagina's zijn opgenomen, maakt ESET Mail Security gebruik van een geavanceerde parser die het
tekstgedeelte van het bericht en het onderwerp van inkomende e-mailberichten doorzoekt om dergelijke
koppelingen (URL's) te identificeren. De koppelingen worden vergeleken met een phishingdatabase. Als het
resultaat van de beoordeling positief is, wordt de e-mail als phishingbericht beschouwd en gaat ESET Mail Security
ermee om zoals is gedefinieerd in de instelling van Uit te voeren actie bij phishingbericht voor elke beveiligingslaag
(Beveiliging van e-mailtransport, Beveiliging van postvakdatabase en On-demand databasescan van postvak). Ook
regelacties worden uitgevoerd.
Ondersteunde standaarden voor e-mailindeling:
· Platte tekst
· Alleen HTML
· MIME
· Meerdelige MIME (een e-mail met zowel HTML als platte tekst)
Ondersteunde HTML-vermeldingen :
In phishingberichten kunnen HTML-entiteiten zijn opgenomen om phishing onzichtbaar te maken voor de
antiphishing-engine. Antiphishing-beveiliging parseert ook symbolen van HTML-entiteiten en zet deze om, om
onzichtbaar gemaakte URL's te vinden en correct te beoordelen.
Eén teken kan in verschillende vormen tot uitdrukking komen. Een punt kan bijvoorbeeld in de volgende vormen
tot uitdrukking komen:
Hoe koppelingen doorgaans worden
weergegeven in het e-mailbericht
voor de gebruiker
Waarde
Onzichtbaar gemaakte koppelingen in het
tekstgedeelte van een bericht
Type
http://www.example-phishing-
domain.com/Fraud
.
http://www.example-phishing-domain.com/
Fraud
teken
http://www.example-phishing-
domain.com/Fraud
&perio
d;
http://www.example-phishing-
domain.com/Fraud
entiteit naam
http://www.example-phishing-
domain.com/Fraud
�
2E;
http://www.example-phishing-
domain.com/Fraud
entiteit
hexadecimaal getal
http://www.example-phishing-
domain.com/Fraud
.
http://www.example-phishing-
domain.com/Fraud
entiteit decimaal
getal
Controleer Logbestanden > Beveiliging van e-mailserver om de activiteit van Antiphishing-beveiliging te zien. In het
logboek vindt u informatie over e-mailberichten en de phishingkoppelingen die erin zijn gevonden.

122
Een phishingsite rapporteren
Als u op Rapport klikt, kunt u een phishingwebsite of anderszins verdachte website aan ESET melden om te
laten analyseren.
6.5 Regels
Hiermee kunt u handmatig voorwaarden voor e-mailfiltering en te nemen acties bij gefilterde e-mails definiëren.
Ook kunt u bepaalde voorwaarden en acties definiëren die verschillen van regels die specifiek gelden voor
Beveiliging van e-mailtransport, Beveiliging van postvakdatabase en On-demand databasescan van postvak. Dit
komt doordat elk van deze beveiligingstypen, met name Beveiliging van e-mailtransport, een andere benadering
hanteert voor de verwerking van berichten.
OPMERKING
De beschikbaarheid van regels voor Beveiliging van postvakdatabase, On-demand databasescan van postvak
en Beveiliging van e-mailtransport op uw systeem, hangt af van de versie van Microsoft Exchange Server die op
de server met ESET Mail Security is geïnstalleerd.
BELANGRIJK
Onjuist gedefinieerde regels voor On-demand databasescan van postvak kunnen onherstelbare schade aan
postvakdatabases veroorzaken. Zorg dat u altijd de meest recente back-up van uw postvakdatabases hebt
voordat u voor het eerst een on-demand databasescan van een postvak uitvoert met gebruik van regels. Ook
adviseren wij ten sterkste om na te gaan of de regels naar verwachting werken. Hiertoe definieert u regels met
alleen de actie Registreren in gebeurtenissenlogboek, want alle andere acties kunnen leiden tot wijzigingen in
uw postvakdatabases. Na deze controle kunt u destructieve regelacties zoals Bijlage verwijderen toevoegen.
Regels worden in drie niveaus opgedeeld en in deze volgorde beoordeeld:
· Filterregels (1): regel die wordt beoordeeld vóór een antispam-, antivirus- en antiphishingscan
· Regels voor de verwerking van bijlagen (2): regel die wordt beoordeeld tijdens de antivirusscan
· Regels voor de verwerking van resultaten (3): regel wordt beoordeeld na een antispam-, antivirus- en
antiphishingscan
Regels met hetzelfde niveau worden beoordeeld in dezelfde volgorde waarin ze in het venster Regels worden
weergegeven. U kunt alleen de regelvolgorde wijzigen voor regels van hetzelfde niveau. Als u meerdere
filterregels hebt, kunt u de volgorde wijzigen waarin deze worden toegepast. U kunt de volgorde ervan niet
wijzigen door regels voor Verwerking van bijlagen vóór Filterregels te plaatsen, omdat de knoppen Omhoog/
Omlaag niet beschikbaar zijn. Met andere woorden, het is niet mogelijk regels van verschillende niveaus te
combineren.
In de kolom Treffers wordt het aantal keer weergegeven dat de regel succesvol is toegepast. Als u een selectievakje
(links van elke regelnaam) uitschakelt, wordt de overeenkomstige regel gedeactiveerd tot u het selectievakje weer
inschakelt.

123
Kl ik op Opnieuw instellen om de teller voor de geselecteerde regel in (de kolom Treffers) opnieuw in te stellen.
Met Weergeven kunt u een configuratie bekijken die vanuit ESET Security Management Center-beleid is
toegewezen.
BELANGRIJK
Normaliter stop de beoordeling van regels voor regels met een lagere prioriteit als aan de voorwaarden van
een regel wordt voldaan. Indien nodig kunt u echter een speciale Regelactie gebruiken met de naam Andere
regels beoordelen om de beoordeling te laten doorgaan.
Regels worden toegepast op een bericht wanneer dit wordt verwerkt door Beveiliging van e-mailtransport,
Beveiliging van postvakdatabase of On-demand databasescan van postvak. Elke beveiligingslaag heeft een eigen
reeks regels.
Wanneer wordt voldaan aan de scanregelvoorwaarden van Beveiliging van postvakdatabase of On-demand
databasescan van postvak, kan de regeltelling worden verhoogd met 2 of meer. Dit komt doordat deze
beveiligingslagen toegang kijken naar de tekst en naar de bijlagen van een bericht, zodat regels op elk onderdeel
afzonderlijk worden toegepast. Regels voor beveiliging van de postvakdatabase worden ook toegepast tijdens
scannen op de achtergrond (bijvoorbeeld wanneer ESET Mail Security een postvakscan uitvoert na het downloaden
van een nieuwe database met viruskenmerken), waardoor de regelteller kan worden verhoogd (treffers).
Regelwizard
1. Kl ik op Toevoegen (in het midden) en het venster Regelvoorwaarde wordt weergegeven, waarin u
voorwaardetype, bewerking en waarde kunt opgeven. Definieer eerst een of meer voorwaarden, en daarna
de actie(s).
BELANGRIJK
U kunt meerdere voorwaarden definiëren. Als u dat doet, moet aan alle voorwaarden worden voldaan om de
regel toe te passen. Alle voorwaarden zijn met elkaar verbonden door de logische operator AND. Zelfs als aan
de meeste voorwaarden is voldaan en er slechts één voorwaarde is waaraan niet is voldaan, wordt het

124
resultaat van de beoordeling van de voorwaarden beschouwd als niet voldaan en wordt de actie die bij de
regel hoort niet uitgevoerd.
2. Kl ik op Toevoegen (onderaan) om een Regelactie toe te voegen.
OPMERKING
Het is mogelijk meerdere acties voor een regel toe te voegen.
3. Wanneer voorwaarden en acties zijn gedefinieerd, typt u een Naam voor de regel (iets waaraan u de regel
herkent). Deze naam wordt weergegeven in de Lijst met regels. Naam is een verplicht veld. Als het rood is
gemarkeerd, typ dan een regelnaam in het tekstvak en klik op knop OK om de regel te maken. De rode
markering verdwijnt niet ondanks dat u een regelnaam hebt ingevoerd. De rode markering verdwijnt alleen
nadat u op OK hebt geklikt.
4. Als u regels wilt voorbereiden maar deze later wilt gebruiken, kunt u op de schuifregelaar klikken naast
Actief om de regel te deactiveren. Om de regel te activeren, schakelt u het selectievakje in naast de regel
die u wilt activeren.
OPMERKING
als er een nieuwe regel wordt toegevoegd of een bestaande regel is gewijzigd, worden berichten automatisch
opnieuw gescand met de nieuwe/gewijzigde regels.
Zie Regelvoorbeelden om te zien hoe regels kunnen worden gebruikt.

125
6.5.1 Regelvoorwaarde
Met deze wizard kunt u voorwaarden voor een regel toevoegen. Selecteer het Type voorwaarde en een Bewerking
in de vervolgkeuzelijst. De lijst met bewerkingen verandert afhankelijk van het regeltype dat u hebt gekozen.
Selecteer vervolgens een Parameter. Parametervelden veranderen en zijn afhankelijk van regeltype en bewerking.
Een voorbeeld: kies Bestandsgrootte > is groter dan en geef onder Parameter de waarde 10 MB op. Met deze
instellingen wordt elk bestand dat groter is dan 10 MB verwerkt met de regelacties die u hebt opgegeven. Om deze
reden moet u de actie opgeven die wordt uitgevoerd wanneer een gegeven regel wordt geactiveerd als u dat niet
hebt gedaan toen u de parameters voor die regel instelde.
Als u uw aangepaste lijst wilt importeren vanuit een bestand in plaats van elke vermelding handmatig toe te
voegen, klikt u met de rechtermuisknop in het midden van het venster en selecteert u Importeren in het
contextmenu en bladert u naar uw bestand (.xml of .txt) met daarin de vermeldingen (van elkaar gescheiden door
een nieuwe regel) die u aan de lijst wilt toevoegen. Als u uw bestaande lijst naar een bestand wilt exporteren, gaat
u op soortgelijke wijze te werk, maar selecteert u Exporteren in het contextmenu.
Of ge ef Reguliere expressie op, se le cte er Bewerking: komt overeen met reguliere expressie of komt niet overeen
met reguliere expressie.
OPMERKING
ESET Mail Security gebruikt std::regex. Zi e Syntaxis ECMAScript voor de opbouw van reguliere expressies. De
syntaxis voor reguliere expressies is niet hoofdlettergevoelig.
BELANGRIJK
U kunt meerdere voorwaarden definiëren. Als u dat doet, moet aan alle voorwaarden worden voldaan om de
regel toe te passen. Alle voorwaarden zijn met elkaar verbonden door de logische operator AND. Zelfs als aan
de meeste voorwaarden is voldaan en er slechts één voorwaarde is waaraan niet is voldaan, wordt het
resultaat van de beoordeling van de voorwaarden beschouwd als niet voldaan en wordt de actie die bij de
regel hoort niet uitgevoerd.
De volgende voorwaardetypen zijn beschikbaar voor Beveiliging van het e-mailtransport, Beveiliging van de
postvakdatabase en On-demand databasescan van postvak (bepaalde opties worden mogelijk niet weergegeven,
afhankelijk van de eerder door u geselecteerde voorwaarden):
Naam van voorwaarde
Beveilig
ing van
e-
mailtran
sport
Beveilig
ing van
postvak
databas
e
On-
demand
database
scan van
postvak
Beschrijving
Onderwerp
Is van toepassing op berichten die een specifieke
tekenreeks (of een reguliere expressie) wel of niet in het
onderwerp bevatten.
Afzender
Is van toepassing op berichten die door een specifieke
afzender zijn verzonden.
SMTP-afzender
Het MAIL FROM-envelopkenmerk dat tijdens een SMTP-
verbinding wordt gebruikt. Wordt ook gebruikt voor SPF-
verificatie.
IP-adres van afzender
Is van toepassing op berichten die vanaf een specifiek IP-
adres zijn verzonden.

126
Naam van voorwaarde
Beveilig
ing van
e-
mailtran
sport
Beveilig
ing van
postvak
databas
e
On-
demand
database
scan van
postvak
Beschrijving
Domein van afzender
Is van toepassing op berichten van een afzender met een
specifiek domein in zijn e-mailadres.
SMTP-domein van
afzender
Is van toepassing op berichten van een afzender met een
specifiek domein in zijn e-mailadres.
Uit koptekst - adres
“Van:”-waarde in kopteksten van berichten. Dit is het adres
dat zichtbaar is voor de ontvanger, maar er worden geen
controles uitgevoerd om na te gaan of het verzendende
systeem geautoriseerd is om namens dat adres te
verzenden. Dit wordt vaak misbruikt om een andere
afzender in berichten te simuleren.
Uit koptekst -
weergavenaam
“Van:”-waarde in kopteksten van berichten. Dit is de
weergavenaam die zichtbaar is voor de ontvanger, maar er
worden geen controles uitgevoerd om na te gaan of het
verzendende systeem geautoriseerd is om namens dat
adres te verzenden. Dit wordt vaak misbruikt om een
andere afzender in berichten te simuleren.
Ontvanger
Is van toepassing op berichten die naar een specifieke
ontvanger zijn verzonden.
Organisatie-eenheden
van ontvanger
Is van toepassing op berichten die naar een geadresseerde
van een specifieke organisatie-eenheid zijn verzonden.
Resultaat van validatie
van ontvanger
Is van toepassing op berichten die zijn verzonden naar een
geadresseerde die in Active Directory is gevalideerd.
Bijlagenaam
Is van toepassing op berichten met bijlagen met een
specifieke naam.
Bijlagegrootte
Is van toepassing op berichten met een bijlage die niet aan
een specifieke grootte voldoet, binnen een specifiek
groottebereik valt, of een specifieke grootte overschrijdt.
Bijlagetype
Is van toepassing op berichten met een specifiek
bestandtype als bijlage. Bestandstypen worden
gecategoriseerd in groepen, zodat deze gemakkelijk
kunnen worden geselecteerd. U kunt meerdere
bestandstypen of hele categorieën selecteren.
Berichtgrootte
Is van toepassing op berichten met bijlagen die niet aan
een specifieke grootte voldoen, binnen een specifiek
groottebereik vallen of een specifieke grootte
overschrijden.
Postvak
Is van toepassing op berichten die zich in een specifiek
postvak bevinden.

127
Naam van voorwaarde
Beveilig
ing van
e-
mailtran
sport
Beveilig
ing van
postvak
databas
e
On-
demand
database
scan van
postvak
Beschrijving
Kopteksten van berichten
Is van toepassing op berichten met specifieke gegevens in
de koptekst van het bericht.
Tekstgedeelte van bericht
Het tekstgedeelte van het bericht wordt onderzocht op de
opgegeven frase. U kunt de functie Strip HTML-tags
gebruiken om HTML-tags, kenmerken en waarden te
verwijderen en alleen tekst te behouden. De hoofdtekst
wordt vervolgens doorzocht.
Intern bericht
Is van toepassing afhankelijk van het feit of een bericht
intern of niet intern is.
Uitgaand bericht
Is van toepassing op uitgaande berichten.
Ondertekend bericht
Is van toepassing op ondertekende berichten.
Versleuteld bericht
Is van toepassing op versleutelde berichten.
Resultaat van
antispamscan
Is van toepassing op berichten die zijn gemarkeerd of niet
zijn gemarkeerd als Geen spam of Spam (zie voorbeeld).
Resultaat van
antivirusscan
Is van toepassing op berichten die als schadelijk of
onschadelijk worden aangeduid.
Resultaat van
Antiphishingscan
Is van toepassing op berichten die als phishing zijn
beoordeeld.
Tijd van ontvangst
Is van toepassing op berichten die voor of na een
specifieke datum, of tijdens een specifiek datumbereik zijn
ontvangen.
Bevat met wachtwoord
beveiligd archief
Is van toepassing op berichten met archiefbestanden die
met een wachtwoord zijn beveiligd.
Bevat beschadigd archief
Is van toepassing op berichten met archiefbijlagen die zijn
beschadigd (en zeer waarschijnlijk niet kunnen worden
geopend).
Bijlage is een archief dat
met een wachtwoord is
beveiligd
Is van toepassing op bijlagen die met een wachtwoord zijn
beveiligd.
Bijlage is beschadigd
archief
Is van toepassing op bijlagen die zijn beschadigd (en zeer
waarschijnlijk niet kunnen worden geopend).
Mapnaam
Is van toepassing op berichten die zich in een specifieke
map bevinden. Als de map niet bestaat, wordt die
gemaakt. Dit is niet van toepassing op Openbare mappen.

128
Naam van voorwaarde
Beveilig
ing van
e-
mailtran
sport
Beveilig
ing van
postvak
databas
e
On-
demand
database
scan van
postvak
Beschrijving
DKIM resultaat
Is van toepassing op berichten die voor verificatie door
DKIM zijn geslaagd of niet zijn geslaagd, indien niet
beschikbaar.
SPF resultaat
Van toepassing op berichten waarvoor het SPF-
beoordelingsresultaat is:
Gelukt: het IP-adres is geautoriseerd om vanuit het
domein te verzenden (SPF me t kw al if icatie "+")
Mislukt: SPF-record bevat niet de verzendende server
of de kwalificatie ("-") voor het IP-adres (SPF)
Beperkte werking: het IP-adres kan wel of niet zijn
geautoriseerd om vanuit het domein te verzenden
(SPF me t kwal ifi catie "~")
Neutraal: betekent dat de domeineigenaar zoals
aangegeven in de SPF-record niet wil beweren dat het
IP-adres is geautoriseerd om vanuit het domein (SPF
me t kwali fi cati e "?") te verzenden
Niet beschikbaar: SPF-resultaat van None betekent dat
er geen records zijn gepubliceerd door het domein of
dat er geen controleerbaar afzenderdomein is dat kan
worden bepaald op grond van de gegeven identiteit
U kunt RFC 4408 lezen voor meer details over SPF.
Als u SPF-resultaten gebruikt, wordt geen rekening
gehouden met witte lijsten in Filteren en verificatie voor
regels.
DMARC resultaat
Is van toepassing op berichten die voor verificatie door
SPF, DKIM of beide zijn geslaagd of niet zijn geslaagd,
indien niet beschikbaar.
He ef t omge ke erde DNS-
record
Is van toepassing op berichten waarin het domein van de
afzender een omgekeerde DNS-record heeft.
NDR resultaat
Is van toepassing op berichten waarvoor verificatie door
NDR is mislukt.
Aan het voorwaardetype zijn de volgende bewerkingen gekoppeld:
· Tekenreeks: is, is niet, bevat, bevat niet, komt overeen met, komt niet overeen met, is in, is niet in, komt
overeen met reguliere expressie, komt niet overeen met reguliere expressie
· Getal: is kleiner dan, is groter dan, is tussen
· Tekst: bevat, bevat niet, komt overeen met, komt niet overeen met
· Datum-tijd: is kleiner dan, is groter dan, is tussen
· Opsomming: is, is niet, is in, is niet in
OPMERKING

129
Al s de Bijlagenaam of he t Bijlagetype Microsoft Office-bestand (2007+) is, wordt de bijlage door ESET Mail
Security behandeld als een archief. Dit houdt in dat de inhoud wordt geëxtraheerd en dat elk bestand in het
Off ice- bestandsarchi ef ( bijvoorbe el d .docx, .xlsx, .xltx, .pptx, .ppsx, .potx enz.) apart wordt gescand.
Al s u Antivirusbeveiliging uitschakelt in het menu Instellingen of Geavanceerde instellingen (F5) > Server >
Antivirus en antispyware voor de laag Beveiliging van e-mailtransport en Beveiliging van postvakdatabase, heeft dit
gevolgen voor deze regelvoorwaarden:
· Bijlagenaam
· Bijlagegrootte
· Bijlagetype
· Resultaat van antivirusscan
· Bijlage is met een wachtwoord beveiligd
· Bijlage is beschadigd archief
· Bevat beschadigd archief
· Bevat met wachtwoord beveiligd archief
6.5.2 Regelactie
U kunt acties toevoegen die worden uitgevoerd bij berichten en/of bijlagen die aan regelvoorwaarden voldoen.
OPMERKING
Het is mogelijk meerdere acties voor een regel toe te voegen.
De lijst met beschikbare acties voor Beveiliging van e-mailtransport, Beveiliging van postvakdatabase en On-
demand databasescan van postvak (bepaalde opties worden mogelijk niet weergegeven, afhankelijk van uw
geselecteerde voorwaarden):
Actienaam
Beveili
ging
van e-
mailtra
nsport
Beveiligi
ng van
postvak
databas
e
On-
demand
database
scan van
postvak
Beschrijving
Quarantainebericht
Het bericht wordt niet bezorgd bij de geadresseerde en wordt
naar de e-mailquarantaine verplaatst. Gebruikers die geen
Administrator zijn, kunnen met deze regel e-mails in
quarantaine vrijgeven (via de webinterface of vanuit
quarantainerapporten).
Bijlage in quarantaine
plaatsen
Plaatst de e-mailbijlage in de bestandsquarantaine. De e-mail
wordt bij de geadresseerde bezorgd met de bijlage afgekapt
tot een lengte van nul.
Bijlage verwijderen
Verwijdert een berichtbijlage. Het bericht wordt zonder bijlage
bij de ontvanger bezorgd.
Bericht afwijzen
Verwijdert een bericht. Voor inkomende e-mails die worden
ontvangen via SMTP, moet er een NDR (Non-Delivery Report)
worden gegenereerd door de verzendende server.
Bericht stil
verwijderen
Verwijdert een bericht zonder een NDR te genereren.

130
Actienaam
Beveili
ging
van e-
mailtra
nsport
Beveiligi
ng van
postvak
databas
e
On-
demand
database
scan van
postvak
Beschrijving
SCL-waarde instellen
Wijzigt of bepaalt een specifieke SCL-waarde.
Gebeurtenismelding
verzenden naar
beheerder
Verzendt gebeurtenismeldingen naar een ontvanger die is
opge gev en i n E-mailmeldingen. U moet de functie
Gebeurtenismelding via e-mail verzenden inschakelen. U kunt
dan de indeling van de gebeurtenismeldingen aanpassen
(gebruik de knopinfo voor suggesties) terwijl u de regel maakt.
U kunt ook het detailniveau voor gebeurtenismeldingen
selecteren. Dit hangt echter af van het minimale detailniveau
dat in het deel E-mailmeldingen is ingesteld.
Antispamscan
overslaan
Bericht wordt niet door de antispamengine gescand.
Antivirusscan
overslaan
Bericht wordt niet door de antivirusengine gescand.
Antiphishingscan
overslaan
Bericht wordt niet geparseerd door Antiphishing-beveiliging.
Andere regels
beoordelen
Maakt de beoordeling van andere regels mogelijk, waardoor de
gebruiker meerdere voorwaardenverzamelingen en uit te
voeren acties kan definiëren voor bepaalde voorwaarden.
Registreren in
gebeurtenissenlogbo
ek
Schrijft informatie over de toegepaste regel in het
programmalogboek en definieert de indeling van
gebeurtenismeldingen (gebruik de knopinfo voor suggesties).
Als u het actietype Logbestand voor gebeurtenissen voor
Beveiliging van postvakdatabase configureert met de
parameter %IPAddress%, is de kolom Gebeurtenis in
Logbestanden leeg voor deze specifieke gebeurtenis. Dit komt
doordat er geen IP-adres is op het niveau Beveiliging van
postvakdatabase. Bepaalde opties zijn niet op alle
beveiligingsniveaus beschikbaar:
%IPAddress%: wordt genegeerd door On-demand
databasescan van postvak en Beveiliging van
postvakdatabase
%Mailbox%: genegeerd door Beveiliging van e-
mailtransport
De volgende opties zijn alleen van toepassing op
Verwerkingsregels voor bijlagen:
%Attname% : genegeerd door Filterregels en
Verwerkingsregels voor resultaat
%Attsize% : genegeerd door Filterregels en
Verwerkingsregels voor resultaat
Koptekstveld
toevoegen
Voegt een aangepaste tekenreeks aan de koptekst van een
bericht toe.

131
Actienaam
Beveili
ging
van e-
mailtra
nsport
Beveiligi
ng van
postvak
databas
e
On-
demand
database
scan van
postvak
Beschrijving
Prefix voor
onderwerp
toevoegen
Voegt een voorvoegsel toe aan een onderwerp.
Bijlage vervangen
door actie-informatie
Vervangt de bijlage door een tekstbestand met uitvoerige
informatie over een actie die is ondernomen.
Koptekstvelden
verwijderen
Verwijdert velden uit koptekst volgens opgegeven parameters.
Bericht verwijderen
Verwijdert een geïnfecteerd bericht.
Bericht verplaatsen
naar map
Het bericht wordt verplaatst naar de specifieke map.
Bericht naar
Prullenbak
verplaatsen
Plaatst een e-mailbericht in de prullenbak van de e-mailclient.
DMARC-beleid
toepassen
Als aan een DMARC-resultaatvoorwaarde is voldaan, wordt het
e-mailbericht verwerkt volgens het beleid dat is opgegeven in
de DMARC DNS-record voor het domein van de afzender.
Al s u Antivirusbeveiliging uitschakelt in het menu Instellingen of Geavanceerde instellingen (F5) > Server >
Antivirus en antispyware voor Beveiliging van e-mailtransport, heeft dat gevolgen voor deze regelacties:
· Bijlage in quarantaine plaatsen
· Bijlage verwijderen
6.5.3 Regelvoorbeelden
Quarantaineberichten waarin zich malware bevindt of een bijlage die met een wachtwoord is beveiligd, is
versleuteld of is beschadigd
VOORBEELD
Doelstelling: Quarantaineberichten waarin zich malware bevindt of een bijlage die met een wachtwoord is
beveiligd, is versleuteld of is beschadigd
Maak de volgende regel voor Beveiliging van e-mailtransport:
Voorwaarde
Type: Resultaat van antivirusscan
Bewerking: is niet
Parameter: Schoon
Actie
Type: Quarantainebericht

132
Berichten die de SPF-controle niet hebben doorstaan overbrengen naar een map Ongewenste e-mail
VOORBEELD
Doelstelling: Berichten die de SPF-controle niet hebben doorstaan overbrengen naar een map Ongewenste e-
mail
Maak de volgende regel voor Beveiliging van e-mailtransport:
Voorwaarde
Type: SPF-resultaat
Bewerking: is
Parameter: Mislukt
Actie
Type: SCL-waarde instellen
Waarde: 5 (Stel de waarde in op grond van de parameter SCLJunkThreshold van de cmdlet Get-
OrganizationConfig van uw Exchange-server. Nadere inlichtingen vindt u in het artikel SCL-
drempelacties.)
Berichten van specifieke afzenders verwijderen
VOORBEELD
Doelstelling: Berichten van specifieke afzenders verwijderen
Maak de volgende regel voor Beveiliging van e-mailtransport:
Voorwaarde
Type: Afzender
Bewerking: is / is een van
Parameter: spammer1@domein.com, spammer2@domein.com
Actie
Type: Bericht stil verwijderen
Een vooraf gedefinieerde regel aanpassen
VOORBEELD
Doelstelling: Een vooraf gedefinieerde regel aanpassen
Details: Archiefbijlagen in berichten van gespecificeerde IP-adressen toelaten (bijvoorbeeld voor interne
systemen) terwijl de regel Verboden archiefbestandsbijlagen wordt gebruikt
Open de regelreeks Beveiliging van e-mailtransport, se le cte er Verboden archiefbestandsbijlagen en klik op
Bewerken.
Voorwaarde
Type: IP-adres van afzender
Bewerking: is niet / is niet een van
Parameter: 1.1.1.2, 1.1.1.50-1.1.1.99
Tekstgedeelte van bericht

133
VOORBEELD
Doelstelling: Quarantaineberichten waarin zich een bepaalde tekenreeks in het tekstgedeelte van het bericht
bevindt
Maak de volgende regel voor Beveiliging van e-mailtransport:
Voorwaarde
Type: Tekstgedeelte van bericht
Bewerking: bevat een van, klik op Toevoegen typ webadres van website of gedeeltelijk webadres
Actie
Type: Quarantainebericht
Berichten voor niet-bestaande ontvangers opslaan
VOORBEELD
Doelstelling: Berichten voor niet-bestaande ontvangers opslaan
Details: Als u wilt dat alle berichten naar niet-bestaande ontvangers in quarantaine worden geplaatst
(ongeacht of ze als Antivirusbeveiliging of Antispambeveiliging zijn gemarkeerd)
Voorwaarde
Type: Resultaat van validatie van ontvanger
Bewerking: is
Parameter: Bevat ongeldige ontvanger
Actie
Type: Quarantainebericht
6.6 Beveiliging van e-mailtransport
U kunt acties configureren voor gedetecteerde bedreigingen op de transportlaag voor elke ESET Mail Security-
module afzonderlijk (Antivirus, Antiphishing en Antispam).
Uit te voeren acties als opschonen niet mogelijk is:
· Geen actie: geïnfecteerde berichten behouden dat niet kunnen worden opgeschoond
· Bericht in quarantaine plaatsen: hiermee worden geïnfecteerde berichten in het quarantainepostvak
geplaatst
· Bericht afwijzen: hiermee wordt een geïnfecteerd bericht afgewezen.
· Bericht stil verwijderen: hiermee worden berichten verwijderd zonder dat er een NDR (Non-Delivery Report)
wordt verzonden
OPMERKING
Al s u Geen actie selecteert en tegelijkertijd Opschoonniveau i nste lt op Niet opschonen in ThreatSense-
parameters van Antivirus en antispyware, wordt de beveiligingsstatus gewijzigd in geel. Dit is omdat het een
beveiligingsrisico is en we afraden om deze combinatie te gebruiken. Wijzig een van beide instellingen om
een goed beveiligingsniveau te bereiken.

134
Uit te voeren actie bij phishingbericht:
· Geen actie: hiermee blijft het bericht behouden, zelfs als het als phishing is aangemerkt
· Bericht in quarantaine plaatsen: hiermee worden als phishing gemarkeerde berichten in het
quarantainepostvak geplaatst
· Bericht afwijzen: hiermee worden als phishing gemarkeerde berichten afgewezen
· Bericht stil verwijderen: hiermee worden berichten verwijderd zonder dat er een NDR (Non-Delivery Report)
wordt verzonden
Uit te voeren actie bij spamberichten:
· Geen actie: hiermee blijft het bericht behouden, zelfs als het als spam is aangemerkt
· Bericht in quarantaine plaatsen: hiermee worden als spam gemarkeerde berichten in het quarantainepostvak
geplaatst
· Bericht afwijzen: hiermee worden als spam gemarkeerde berichten afgewezen
· Bericht stil verwijderen: hiermee worden berichten verwijderd zonder dat er een NDR (Non-Delivery Report)
wordt verzonden
SMTP-afwijzingsreactie
U kunt een Reactiecode, Statuscode en Reactiebericht opgeven waarmee de tijdelijke SMTP-afwijzingsreactie wordt
gedefinieerd die naar de SMTP-server wordt verzonden als een bericht is afgewezen. U kunt een reactiebericht in
de volgende indeling typen:
Reactiecode
Statuscode
Reactiebericht
250
2.5.0
Aangevraagde mailactie OK, voltooid

135
Reactiecode
Statuscode
Reactiebericht
451
4.5.1
Aangevraagde actie afgebroken:lokale fout bij verwerking
550
5.5.0
Aangevraagde actie niet uitgevoerd:postvak niet beschikbaar
554
5.6.0
Ongeldige inhoud
OPMERKING
u kunt ook systeemvariabelen gebruiken bij het configureren van SMTP-weigeringsantwoorden.
Scanresultaten naar berichtkopteksten schrijven
Indien ingeschakeld, worden scanresultaten in berichtkopteksten geschreven. Deze berichtkopteksten
be ginne n met X_ESET, waardoor ze gemakkelijk zijn te herkennen (bijvoorbeeld X_EsetResult of
X_ESET_Antispam).
Melding toevoegen aan de berichttekst van gescande berichten heeft drie opties:
· Niet toevoegen aan berichten: er wordt geen informatie toegevoegd.
· Alleen toevoegen aan geïnfecteerde berichten : alleen van toepassing op geïnfecteerde berichten.
· Aan alle berichten toevoegen (niet van toepassing op interne berichten): alle berichten worden gemarkeerd.
Onderwerp aanpassen
Indien ingeschakeld, kunt u sjablonen wijzigen die zijn toegevoegd aan het onderwerp van geïnfecteerde
berichten, spam of phishingberichten.
Sjabloon toegevoegd aan het onderwerp van geïnfecteerde berichten
ESET Mail Security voegt een meldingstag toe aan het e-mailonderwerp met de waarde die is gedefinieerd in
he t te kstve l d Sjabloon toegevoegd aan het onderwerp van geïnfecteerde berichten (de vooraf gedefinieerde
standaardte kst i s [found threat %VIRUSNAME%]). Deze aanpassing kan worden gebruikt om het filteren van
geïnfecteerde berichten te automatiseren door e-mails met een specifiek onderwerp te filteren, bijvoorbeeld
met regels of anders aan de client-kant (indien ondersteund door de e-mailclient) om dergelijke e-
mailberichten in een afzonderlijke map te plaatsen.
Sjabloon toegevoegd aan het onderwerp van spamberichten
ESET Mail Security voegt een meldingstag toe aan het e-mailonderwerp met de waarde die is gedefinieerd in
he t te kstve l d Sjabloon toegevoegd aan het onderwerp van spamberichten (de vooraf gedefinieerde
standaardte kst i s [SPAM]). Deze aanpassing kan worden gebruikt om spamfiltering te automatiseren door e-
mails met een specifiek onderwerp te filteren, bijvoorbeeld met regels of anders aan de kant van een client
(indien ondersteund door de e-mailclient) om dergelijke e-mailberichten in een afzonderlijke map te plaatsen.
Sjabloon toegevoegd aan het onderwerp van de phishing-berichten
ESET Mail Security voegt een meldingstag toe aan het e-mailonderwerp met de waarde die is gedefinieerd in
he t te kstve l d Sjabloon toegevoegd aan het onderwerp van phishingberichten (de vooraf gedefinieerde
standaardte kst i s [PHISH]). Deze aanpassing kan worden gebruikt om spamfiltering te automatiseren door e-
mails met een specifiek onderwerp te filteren, bijvoorbeeld met regels of anders aan de kant van een client
(indien ondersteund door de e-mailclient) om dergelijke e-mailberichten in een afzonderlijke map te plaatsen.
OPMERKING
U kunt ook systeemvariabelen gebruiken wanneer u tekst bewerkt die aan het onderwerp wordt toegevoegd.

136
6.6.1 Geavanceerde instellingen voor berichtentransport
U kunt instellingen voor de beveiliging van e-mailtransport verder aanpassen.
Ook berichten scannen die worden ontvangen van geverifieerde of interne verbindingen
U kunt kiezen welk type scan moet worden uitgevoerd op berichten die worden ontvangen van geverifieerde
bronnen of lokale servers. Het scannen van dergelijke berichten wordt aanbevolen omdat dit de beveiliging
verhoogt, maar is noodzakelijk als u gebruikmaakt van de ingebouwde Microsoft SBS POP3-connector om e-
mailberichten op te halen bij externe POP3-servers of e-mailservices (bijvoorbeeld Gmail.com, Outlook.com,
Yahoo.com, gmx.dem enz.). Zie POP3-connector en antispam voor meer informatie. Kies het beveiligingsniveau
in het vervolgkeuzemenu. Wij raden aan Antivirusbeveiliging (standaardinstelling) te gebruiken, met name
voor interne verbindingen, omdat het onwaarschijnlijk is dat phishing of spamberichten via uw lokale servers
worden gedistribueerd. U kunt de beveiliging voor de Microsoft SBS POP3-connector echter verhogen door
Antivirus- en antiphishing-beveiliging of ze lfs Antivirus-, antiphishing- en antispambeveiliging te kiezen.
OPMERKING
Deze instelling schakelt Antispambeveiliging in/uit voor geverifieerde gebruikers en interne verbindingen. E-
mails van niet-geverifieerde verbindingen worden altijd gescand, ook als u Niet scannen selecteert.
OPMERKING
Interne berichten van Outlook in de organisatie worden verzonden in de TNEF-indeling (Transport Neutral
Encapsulation Format). TNEF wordt niet ondersteund door Antispam. Interne, als TNEF opgemaakte e-mails
worden daarom niet gescand op SPAM, ongeacht de instelling van Ook berichten scannen die worden
ontvangen van geverifieerde of interne verbindingen.
Bestaande SCL-koptekst verwijderen voor de scan
Deze optie is standaard ingeschakeld. U kunt deze optie uitschakelen als u de SCL-koptekst (Spam Confidence
Level) wilt behouden.

137
6.7 Beveiliging van postvakdatabase
Als Proactief scannen is ingeschakeld, worden nieuwe binnenkomende berichten gescand in dezelfde volgorde als
waarin ze worden ontvangen. Als deze optie is ingeschakeld en een gebruiker een bericht opent dat nog niet is
gescand, wordt het bericht gescand vóór andere berichten in de wachtrij.
Achtergrondscans
Hiermee worden alle berichten op de achtergrond gescand (scannen wordt uitgevoerd in de opslag van postvakken
en openbare mappen, bijvoorbeeld de Exchange-database). Microsoft Exchange Server bepaalt of een
achtergrondscan wordt uitgevoerd of niet. Dit gebeurt op basis van verschillende factoren, zoals de huidige
systeembelasting, het aantal actieve gebruikers, enz. Microsoft Exchange Server houdt een record bij met alle
gescande berichten en de gebruikte versie van de database met viruskenmerken. Als u een bericht opent dat nog
niet is gescand met de meest actuele versie van de database met viruskenmerken, stuurt Microsoft Exchange Server
het bericht naar ESET Mail Security en wordt het gescand voordat het in uw e-mailclient wordt geopend.
U kunt kiezen voor Alleen berichten met bijlage scannen en filteren op het tijdstip van ontvangst met de volgende
opti es voor Limiet voor scantijd:
· Alle berichten
· Berichten die afgelopen jaar zijn ontvangen
· Berichten die afgelopen 6 maanden zijn ontvangen
· Berichten die afgelopen 3 maanden zijn ontvangen
· Berichten die zijn ontvangen in de afgelopen maand
· Berichten die zijn ontvangen in de afgelopen week
Aangezien scannen op de achtergrond van invloed is op de systeembelasting (er wordt gescand na elke update van
de detectie-engine), wordt aanbevolen dat u scans zodanig plant dat deze buiten kantooruren worden uitgevoerd.
Gepland op de achtergrond scannen kan worden geconfigureerd via een speciale taak in de Taakplanner. Wanneer u
een achtergrondscantaak plant, kunt u de starttijd, het aantal herhalingen en andere beschikbare parameters

138
instellen in de Taakplanner. Nadat de taak is gepland, wordt deze weergegeven in de lijst met geplande taken en
kunt u de parameters ervan wijzigen, de taak verwijderen, of de taak tijdelijk deactiveren.
Aantal scanthreads
Aantal scanthreads kan een bereik hebben tussen 1 en 21. U kunt het aantal onafhankelijke scanthreads
instellen dat tegelijk wordt uitgevoerd. Meer threads op computers met meerdere processors kunnen de
snelheid van de scans verhogen. Voor de beste prestaties van het programma raden wij aan een gelijk aantal
ThreatSense-scanengines en scanthreads te gebruiken.
RTF-berichtteksten scannen
Met deze optie activeert u het scannen van RTF-berichtteksten. RTF-berichtteksten kunnen macrovirussen
bevatten.
OPMERKING
de hoofdtekst van e-mail met tekst zonder opmaak wordt niet gescand door VSAPI.
Uit te voeren acties als opschonen niet mogelijk is:
· Geen actie: geen wijzigingen in bericht van toepassing
· Inkorten tot lengte nul: bijlage wordt ingekort tot lengte nul
· Inhoud vervangen door actie-informatie: oorspronkelijke berichttekst wordt vervangen door actie-
informatie. Inhoud van bijlage wordt vervangen door actie-informatie.
· Bericht verwijderen: bericht wordt verwijderd
Uit te voeren actie bij phishingbericht:
· Geen actie: geen wijzigingen in bericht van toepassing
· Bericht verwijderen: bericht wordt verwijderd
OPMERKING
Openbare mappen worden op dezelfde manier behandeld als postvakken. Dit betekent dat ook openbare
mappen worden gescand.
6.7.1 Achtergrondscan
Dit taaktype maakt een databasescan via VSAPI op de achtergrond mogelijk. Uw Exchange Server kan indien nodig
een achtergrondscan uitvoeren. De scan wordt door Exchange Server zelf geactiveerd. Dit betekent dat de Exchange
Server bepaalt of de scan binnen de toegestane tijd wordt uitgevoerd.
We raden aan om deze taak buiten de piekuren uit te laten voeren wanneer uw Exchange Server niet druk bezet is,
bijvoorbeeld 's nachts. Dit is nodig omdat de achtergrondscan van de database een bepaalde belasting voor uw
systeem kan betekenen. Om prestatie- of beschikbaarheidsproblemen te vermijden mag het tijdskader ook niet
overlappen met back-ups die op uw Exchange Server worden uitgevoerd.
OPMERKING
Beveiliging voor postvakdatabase moet zijn ingeschakeld om de geplande taak te kunnen uitvoeren. Dit
beveiligingstype is alleen beschikbaar voor Microsoft Exchange Server 2010 en 2007 die werken als
postvakserver (Microsoft Exchange 2010 en 2007).
Time-out (uur)
Geef op hoeveel uur uw Exchange Server de achtergrondscan van de database mag uitvoeren, gerekend vanaf
de tijd dat deze geplande taak wordt uitgevoerd. Zodra deze de time-out bereikt, krijgt Exchange de opdracht
de achtergrondscan te stoppen.

139
6.8 On-demand databasescan van postvak
OPMERKING
Als u Microsoft Exchange Server 2007 of 2010 uitvoert, kunt u kiezen tussen Beveiliging van postvakdatabase en
On-demand databasescan van postvak. Er kan slechts één beveiligingstype tegelijk actief zijn. Als u besluit On-
demand databasescan van postvak te gebruiken, moet u de integratie van Beveiliging van postvakdatabase
uitschakelen in Geavanceerde instellingen (F5) onde r Server. Anders is On-demand databasescan van postvak
niet beschikbaar.
Hostadres
Naam of IP-adres van de server waarop EWS (Exchange Web Services) wordt uitgevoerd.
Gebruikersnaam
Geef de referenties van een gebruiker op die de juiste toegang tot EWS (Exchange Web Services) heeft.
Gebruikerswachtwoord
Kl ik op Instellen naast Gebruikerswachtwoord en typ het wachtwoord voor dit gebruikersaccount.
BELANGRIJK
Voor het scannen van openbare mappen moet het gebruikersaccount dat voor On-demand databasescan van
postvak wordt gebruikt een postvak hebben. Anders wordt Failed to load public folders weergegeven in het
Databasescanlogboek, samen met een specifieker bericht dat door Exchange wordt geretourneerd.
Toegangsmethode voor postvak
Hier kunt u de toegangsmethode die uw voorkeur heeft voor uw postvak selecteren:
· Imitatie
Instellen is het gemakkelijkst en gaat het snelst met de ApplicationImpersonation-rol, die aan het scanaccount
moet worden toegewezen.
ApplicationImpersonation-rol aan gebruiker toewijzen
Als deze optie grijs wordt weergegeven, moet u een Gebruikersnaam opgeven. Klik op Toewijzen om de
ApplicationImpersonation-rol automatisch aan de geselecteerde gebruiker toe te wijzen. Of wijs de
ApplicationImpersonation-rol handmatig toe aan een gebruikersaccount. Er wordt nieuw onbeperkt EWS-
beperkingsbeleid voor het gebruikersaccount gemaakt. Zie Details van databasescanaccount voor meer
informatie.
· Delegeren
Gebruik dit toegangstype als toegangsrechten voor afzonderlijke postvakken zijn vereist, maar u een hogere
snelheid wilt wanneer er grote hoeveelheden gegevens worden gescand.
Gedelegeerde toegang toewijzen aan gebruiker
Als deze optie grijs wordt weergegeven, moet u een Gebruikersnaam opgeven. Klik op Toewijzen om de
geselecteerde gebruiker automatisch volledige toegang te geven tot alle gebruikers en gedeelde postvakken.
Er wordt nieuw onbeperkt EWS-beperkingsbeleid voor het gebruikersaccount gemaakt. Zie Details van
databasescanaccount voor meer informatie.
SSL gebruiken
Moet zijn ingeschakeld als EWS (Exchange Web Services) is ingesteld op SSL vereisen in IIS. Als SSL is
ingeschakeld, moet het Exchange Server-certificaat worden geïmporteerd op het systeem met ESET Mail
Security (in het geval de Exchange Server-functies zich op verschillende servers bevinden). Instellingen voor
EWS vindt u in IIS in Sites/Standaardwebsite/EWS/SSL-instellingen.

140
OPMERKING
Schakel SSL gebruiken alleen uit als u EWS in IIS zodanig hebt geconfigureerd dat SSL vereisen niet is
ingeschakeld.
Servercertificaatfouten negeren
Als u een zelfondertekend certificaat gebruikt, kunt u servercertificaatfouten negeren.
Clientcertificaat
Moet alleen worden ingesteld als Exchange Web Services (EWS) een clientcertificaat vereist. Klik op Selecteren
om een certificaat te selecteren.
Uit te voeren actie als opschonen niet mogelijk is
Met dit actieveld kunt u geïnfecteerde inhoud blokkeren.
· Geen actie: geen actie ondernemen op de geïnfecteerde inhoud van het bericht.
· Bericht naar Prullenbak verplaatsen: wordt niet ondersteund voor items in openbare mappen. In plaats
hiervan wordt de actie Object verwijderen toegepast.
· Object verwijderen: geïnfecteerde inhoud van het bericht wordt verwijderd.
· Bericht verwijderen: het volledige bericht verwijderen, inclusief de geïnfecteerde inhoud.
· Object vervangen met actie-informatie: verwijdert een object en vermeldt dat het object is verwijderd.
Uit te voeren actie bij phishingbericht:
· Geen actie: hiermee blijft het bericht behouden, zelfs als het als phishing is aangemerkt.
· Bericht naar Prullenbak verplaatsen: wordt niet ondersteund voor items in openbare mappen. In plaats
hiervan wordt de actie Object verwijderen toegepast.
· Bericht verwijderen: het volledige bericht verwijderen, inclusief de geïnfecteerde inhoud.
Aantal scanthreads
U kunt opgeven hoeveel threads ESET Mail Security moet gebruiken bij het scannen van databases. Hoe hoger
het getal, hoe beter de prestaties. Dit heeft echter gevolgen voor hoeveel systeembronnen er worden
gebruikt. De standaardwaarde is ingesteld op 4 scanthreads.
OPMERKING
Als u On-demand databasescan van postvak zodanig configureert dat er te veel threads worden gebruikt,
wordt uw systeem mogelijk te zwaar belast, waardoor dit andere processen vertraagt of zelfs uw gehele
systeem vertraagt. Mogelijk ziet u een foutbericht met de melding "Te veel gelijktijdige verbindingen geopend".
Office 365-account
Alleen zichtbaar als u een hybride Office 365-omgeving hebt.
Gebruikersnaam
Geef de referenties van een gebruiker op die de juiste toegang tot EWS (Exchange Web Services) heeft.
Gebruikerswachtwoord
Kl ik op Instellen naast Gebruikerswachtwoord en typ het wachtwoord voor dit gebruikersaccount.
ApplicationImpersonation-rol aan gebruiker toewijzen
Als deze optie grijs wordt weergegeven, moet u een Gebruikersnaam opgeven. Klik op Toewijzen om de
ApplicationImpersonation-rol automatisch aan de geselecteerde gebruiker toe te wijzen. Of wijs de
ApplicationImpersonation-rol handmatig toe aan een gebruikersaccount. Er wordt nieuw onbeperkt EWS-
beperkingsbeleid voor het gebruikersaccount gemaakt. Zie Details van databasescanaccount voor meer
informatie.

141
6.8.1 Databasescan van postvak
Het uitvoeren van een volledige databasescan in grote omgevingen kan leiden tot een ongewenste
systeembelasting. Vermijd dit probleem door een scan uit te voeren op specifieke databases of postvakken. Beperk
de gevolgen voor het serversysteem verder door scandoelen te filteren met behulp van berichttijdstempels.
BELANGRIJK
Onj uist ge defi ni ee rde regels voor On-demand databasescan van postvak kunnen onomkeerbare wijzigingen
aanbrengen aan postvakdatabases. Zorg dat u altijd de meest recente back-up van uw postvakdatabases hebt
voordat u voor het eerst met gebruik van regels een on-demand databasescan van een postvak uitvoert. Ook
adviseren wij ten sterkste om na te gaan of de regels naar verwachting werken. Hiertoe definieert u regels met
alleen de actie Registreren in gebeurtenissenlogboek, want alle andere acties kunnen leiden tot wijzigingen in
uw postvakdatabases. Na deze controle kunt u destructieve regelacties zoals Bijlage verwijderen toevoegen.
De volgende itemtypen worden gescand in zowel Openbare mappen als in Postvakken van gebruikers:
· E-mail
· Post
· Agenda-items (vergaderingen/afspraken)
· Taken
· Contactpersonen
· Logboeken
Gebruik de vervolgkeuzelijst om op basis van de tijdstempel te kiezen welke berichten u wilt scannen.
Bijvoorbeeld Berichten scannen die in de afgelopen week zijn gewijzigd. U kunt zo nodig ook kiezen voor Alle
berichten scannen.
Schakel het selectievakje in of uit naast Alleen berichten met bijlagen scannen als u het scannen van berichtbijlagen
wilt in of uitschakelen. Klik op Bewerken om de openbare map te selecteren die wordt gescand.

142
Schakel de selectievakjes in naast de serverdatabases en postvakken die u wilt scannen. Met Filter kunt u snel
databases en postvakken vinden, met name als er zich een groot aantal postvakken in uw Exchange-infrastructure
bevindt.

143
Kl ik op Opslaan om uw scandoelen en -parameters in het profiel van Scannen op aanvraag op te slaan. Nu kunt u op
Scannen klikken. Als u niet eerder Details van databasescanaccount hebt opgegeven, wordt er een pop-upvenster
geopend waarin u om referenties wordt gevraagd. Anders wordt On-demand databasescan van postvak gestart.
OPMERKING
Als u Microsoft Exchange Server 2007 of 2010 uitvoert, kunt u kiezen tussen Beveiliging van postvakdatabase en
On-demand databasescan van postvak. Er kan slechts één beveiligingstype tegelijk actief zijn. Als u besluit On-
demand databasescan van postvak te gebruiken, moet u de integratie van Beveiliging van postvakdatabase
uitschakelen in Geavanceerde instellingen onder Server. Anders is On-demand databasescan van postvak niet
beschikbaar.
6.8.2 Scan van Office 365-postvak
ESET Mail Security biedt scanfunctionaliteit voor hybride Office 365-omgevingen. Deze functionaliteit is alleen
beschikbaar en zichtbaar in ESET Mail Security als u een hybride Exchange-omgeving hebt (lokaal en in de cloud).
Beide routeringsscenario's worden ondersteund, via Exchange Online of via de lokale organisatie. Zie
Transportroutering in hybride Exchange-implementaties voor meer informatie.
U kunt externe Office 365-postvakken en openbare mappen op dezelfde manier scannen als u bij een traditionele
On-demand databasescan van postvak zou doen.
Het uitvoeren van een volledige databasescan in grote omgevingen kan tot een ongewenste systeembelasting
leiden. Vermijd dit probleem door een scan uit te voeren op specifieke databases of postvakken. Gebruik het
tijdfilter boven in het venster om de invloed op het system verder te minimaliseren. Een voorbeeld: in plaats van
Alle berichten scannen kunt u Berichten scannen die in de afgelopen week zijn gewijzigd.
Wij raden u aan uw Office 365-account te configureren. Druk op de toets F5 en navigeer naar Server > On-demand
databasescan van postvak. Zie ook Details van databaseaccountscan.

144
Raadpleeg Logbestanden > Databasescan van postvak om de activiteit van de Office 365-postvakscan te zien.
6.8.3 Extra postvakitems
In de instellingen van On-demand databasescan van postvak kunt u het scannen van andere postvakitemtypen in-
en uitschakelen:
· Agenda scannen
· Taken scannen
· Contactpersonen scannen
· Logboek scannen
OPMERKING
Als u met prestatieproblemen te maken krijgt, kunt u het scannen van deze items uitschakelen. Het scannen
duurt langer wanneer deze items zijn ingeschakeld.
6.8.4 Proxyserver
Als u een proxyserver gebruikt tussen uw Exchange Server met CAS-functie en de Exchange Server waarop ESET Mail
Security wordt geïnstalleerd, dient u de parameters van uw proxyserver op te geven. Dit is nodig omdat ESET Mail
Security via HTTP/HTTPS verbinding maakt met de API van Exchange Web Services (EWS). Anders werken
Quarantainepostvak en MS Exchange-quarantaine niet.
Proxyserver
Hier voert u het IP-adres of de naam in van de proxyserver die u gebruikt.
Poort
Hier voert u het poortnummer van de proxyserver in.
Gebruikersnaam, Wachtwoord
Hier geeft u de referenties op als voor uw proxyserver verificatie is vereist.

145
6.8.5 Details van databasescanaccount
Dit dialoogvenster wordt weergegeven als u geen gebruikersnaam en wachtwoord hebt opgegeven voor
Databasescan. Geef in dit pop-upvenster de referenties van de gebruiker op die toegang heeft tot EWS (Exchange
Web Services) en klik op OK. Of ga naar Geavanceerde instellingen door op F5 te drukken en naar Server > On-
demand databasescan van postvak te navigeren. Typ uw Gebruikersnaam, klik op Instellen, typ een wachtwoord
voor dit gebruikersaccount en klik op OK.
Klik op het selectievakje naast Accountinformatie opslaan om accountinstellingen op te slaan. Anders wordt u
telkens gevraagd accountinformatie in te voeren wanneer u On-demand databasescan van postvak uitvoert.
Als een gebruikersaccount niet de juiste toegang tot Exchange Web Services (EWS) heeft, kunt u
"ApplicationImpersonation"-roltoewijzing maken inschakelen om deze rol aan het gebruikersaccount toe te wijzen.
Of u kunt de ApplicationImpersonation-rol handmatig toewijzen. Zie de opmerking hieronder voor de details.
BELANGRIJK
Aan het scanaccount moet de rol ApplicationImpersonation zijn toegewezen, zodat de scanengine postvakken
van gebruikers in Exchange-postvakdatabases kan scannen. Als u Exchange Server 2010 of nieuwer uitvoert,
wordt er een nieuw onbeperkt EWS-beperkingsbeleid voor het gebruikersaccount gemaakt. Zorg ervoor dat
het EWS-beperkingsbeleid wordt geconfigureerd voor het scanaccount om te veel verwerkingsaanvragen door
ESET Mail Security te vermijden, wat anders kan leiden tot een time-out van bepaalde aanvragen. Zie Beste
werkwijzen voor EWS en Clientbeperkingsbeleid begrijpen voor meer informatie over het
beperkingsbeleid. Zie ook Gebruikersbeperkingsinstellingen voor specifieke gebruikers wijzigen voor meer
informatie en voorbeelden.
Als u de ApplicationImpersonation-rol handmatig aan een gebruikersaccount wilt toewijzen en een nieuw EWS-
beperkingsbeleid voor dit account wilt maken, kunt u de volgende opdrachten gebruiken (vervang ESET-user door
een echte accountnaam in uw systeem. U kunt ook beperkingen instellen voor het EWS-beperkingsbeleid door
$null te vervangen door cijfers):
Exchange Server 2007
Get-ClientAccessServer | Add-AdPermission -User ESET-user -ExtendedRights ms-Exch-EPI-
Impersonation
Get-MailboxDatabase | Add-AdPermission -User ESET-user -ExtendedRights ms-Exch-EPI-May-
Impersonate
Exchange Server 2010
New-ManagementRoleAssignment -Name:ESET-ApplicationImpersonation -Role:ApplicationImpersonation -
User ESET-user

146
Exchange Server 2007
Get-ClientAccessServer | Add-AdPermission -User ESET-user -ExtendedRights ms-Exch-EPI-
Impersonation
Get-MailboxDatabase | Add-AdPermission -User ESET-user -ExtendedRights ms-Exch-EPI-May-
Impersonate
Het kan even duren tot dit is toegepast
New-ThrottlingPolicy -Name ESET-ThrottlingPolicy -EWSFindCountLimit $null -
EWSFastSearchTimeoutInSeconds $null -EWSMaxConcurrency $null -EWSPercentTimeInAD $null -
EWSPercentTimeInCAS $null -EWSPercentTimeInMailboxRPC $null
Set-ThrottlingPolicyAssociation -Identity user-ESET -ThrottlingPolicy ESET-ThrottlingPolicy
Exchange Server 2013, 2016 en 2019
New-ManagementRoleAssignment -Name:ESET-ApplicationImpersonation -Role:ApplicationImpersonation -
User ESET-user
Het kan even duren tot dit is toegepast
New-ThrottlingPolicy -Name ESET-ThrottlingPolicy -EWSMaxConcurrency Unlimited -EwsCutoffBalance
Unlimited -EwsMaxBurst Unlimited -EwsRechargeRate Unlimited
Set-ThrottlingPolicyAssociation -Identity ESET-user -ThrottlingPolicy ESET-ThrottlingPolicy
6.9 Typen Quarantaine voor e-mail
Beheer van e-mailquarantaine is beschikbaar voor alle drie de quarantainetypen:
· Lokale quarantaine
· Quarantainepostvak
· MS Exchange-quarantaine
U kunt de inhoud van Quarantaine voor e-mail zien in Beheer van e-mailquarantaine voor alle quarantainetypen. De
lokale quarantaine kunt u ook in de webinterface voor Quarantaine voor e-mail zien.
Berichten voor niet-bestaande ontvangers opslaan
Deze instelling is van toepassing op berichten die door de antivirusbeveiliging, de antispambeveiliging of op
grond van regels zijn gemarkeerd voor quarantaine. Indien ingeschakeld worden berichten die worden
verzonden naar ontvangers die niet in uw Active Directory bestaan, opgeslagen in de e-mailquarantaine.
Schakel deze functie uit als u dergelijk bericht niet in uw E-mailquarantaine wilt bewaren. Indien uitgeschakeld
worden berichten naar onbekende ontvangers verwijderd zonder dat dit wordt gemeld.
Zie voorbeelden: als u alle berichten naar niet-bestaande ontvangers in quarantaine wilt plaatsen.
Beoordeling van regels overslaan wanneer e-mails worden vrijgegeven
Als u een bericht wilt vrijgeven uit quarantaine, wordt dit bericht niet door de regels beoordeeld. Dit is om te
vermijden dat het bericht terug in quarantaine wordt geplaatst, en het vrijgegeven bericht naar de ontvanger
wordt gestuurd. Deze functie wordt pas gebruikt wanneer de beheerder het bericht vrijgeeft. Als u deze functie
uitschakelt of als er een bericht wordt vrijgegeven door een andere gebruiker dan de beheerder, wordt het
bericht door de regels beoordeeld.
OPMERKING
De twee bovenstaande instellingen zijn alleen beschikbaar voor Microsoft Exchange Server 2007 en nieuwer.
E-mailhandtekeningseed voor omgevingen met meerdere servers
Hiermee kunt u de beoordeling van regels overslaan wanneer e-mails in een omgeving met meerdere servers
worden vrijgegeven. Voer dezelfde seed-waarde in (een tekenreeks, vergelijkbaar met een wachtwoordzin) op
alle servers waartussen u vertrouwen wilt instellen.

147
Opmaak voor bijlage-envelop
Wanneer een e-mailbericht wordt vrijgegeven vanuit quarantaine, wordt het als bijlage aan een nieuw bericht
toegevoegd (bijlage-envelop), die vervolgens bij de ontvanger wordt bezorgd. De ontvanger ontvangt het
oorspronkelijke bericht dat als bijlage vanuit e-mailquarantaine wordt vrijgegeven. U kunt de vooraf
gedefinieerde indeling van de envelop gebruiken of deze met de beschikbare variabelen aanpassen aan uw
vereisten.
Gebruik ESET Cluster om alle in quarantaine geplaatste berichten op één knooppunt te plaatsen
Als u ESET Cluster gebruikt, komt deze optie beschikbaar. Wij raden aan deze functie te gebruiken, omdat u
hiermee de opslag voor lokale quarantainebestanden op één plaats kunt houden; het hoofdknooppunt.
Hoofdknooppunt
Kies een van de knooppunten als hoofdknooppunt voor de opslag van lokale quarantainebestanden. U beheert
uw mailquarantaine in het hoofdknooppunt (u kunt Quarantainebeheer voor e-mail vanuit de hoofdinterface of
de webinterface van Quarantaine voor e-mail gebruiken).
6.9.1 Lokale quarantaine
Lokale quarantaine gebruikt uw lokale bestandssysteem om in quarantaine geplaatste e-mails en een SQLite-
database als index op te slaan. In quarantaine opgeslagen e-mailbestanden en databasebestanden worden om
beveiligingsredenen versleuteld. Deze bestanden bevinden zich onder C:\ProgramData\ESET\ESET Mail Security
\MailQuarantine (op Windows Server 2008 SP2 en 2012).
OPMERKING
Als u in quarantaine geplaatste bestanden op een andere schijf dan het standaardstation C: wilt hebben,
wijzigt u de Gegevensmap ti jde ns de installatie van ESET Mail Security in het door u gewenste pad.
Kenmerken van Lokale quarantaine:
· Spam en in quarantaine geplaatste e-mailberichten worden in een lokaal bestandssysteem opgeslagen, niet
in een Exchange-postvakdatabase.
· Versleuteling en comprimering van lokaal opgeslagen in quarantaine geplaatste e-mailbestanden.
· De webinterface van e-mailquarantaine als alternatief voor Beheer van e-mailquarantaine.
· Quarantainerapporten kunnen met een geplande taak naar een opgegeven e-mailadres worden verzonden.
· In quarantaine geplaatste e-mailbestanden die worden verwijderd uit het quarantainevenster (standaard na
21 dagen), worden in een bestandssysteem opgeslagen (tot automatische verwijdering plaatsvindt na een
opgegeven aantal dagen).
· Automatische verwijdering van oude e-mailbestanden (standaard na 3 dagen). Zie Instellingen
bestandsopslag voor meer informatie.
· U kunt verwijderde, in quarantaine geplaatste e-mailbestanden herstellen met eShell (ervan uitgaande dat
deze nog niet uit het bestandssysteem zijn verwijderd).
· Inspecteer in quarantaine geplaatste e-mailberichten en bepaal welke u wilt verwijderen of vrijgeven. Als u
in lokale quarantaine geplaatste e-mailberichten wilt bekijken en beheren, kunt u dat doen met Beheer van
e-mailquarantaine in de primaire grafische gebruikersinterface of met de webinterface voor Quarantaine
voor e-mail.
OPMERKING
Het nadeel van het gebruik van lokale quarantaine is dat wanneer u ESET Mail Security op meerdere servers
met de rol Hubtransportserver uitvoert, u de lokale quarantaine op elke server afzonderlijk moet beheren.
Hoe meer e-mailservers u hebt, hoe meer quarantaines u moet beheren.

148
6.9.1.1 Bestandopslag
In dit gedeelte kunt u instellingen voor bestandsopslag wijzigen die door de lokale quarantaine wordt gebruikt.
In quarantaine geplaatste bestanden comprimeren
Gecomprimeerde, in quarantaine geplaatste bestanden nemen minder schijfruimte in, maar als u besluit
bestanden niet te comprimeren, gebruik dan de schuifregelaar om comprimeren uit te schakelen.
Oude bestanden wissen na (dagen)
Wanneer berichten het opgegeven aantal dagen bereiken, worden ze uit het quarantainevenster verwijderd.
Bestanden worden echter niet verwijderd van de schijf gedurende het aantal dagen dat is opgegeven in
Verwijderde bestanden wissen na (dagen). Aangezien bestanden niet uit het bestandssysteem worden
verwijderd, is het mogelijk dergelijke bestanden met eShell te herstellen.
Verwijderde bestanden wissen na (dagen)
Verwijdert bestanden van de schijf na het opgegeven aantal dagen. Nadat ze zijn verwijderd, is geen herstel
mogelijk (tenzij u een back-upoplossing voor het bestandssysteem hebt).
6.9.1.2 Webinterface
De webinterface voor e-mailquarantaine is een alternatief voor Beheer van e-mailquarantaine, maar die is alleen
be schi kbaar voor Lokale quarantaine.
OPMERKING
De webinterface voor Quarantaine voor e-mail is niet beschikbaar op een server met de rol
Edgetransportserver omdat de Active Directory niet toegankelijk is voor verificatie.
Met de webinterface voor Quarantaine voor e-mail kunt u de status van de e-mailquarantaine bekijken. Hiermee
kunt u ook in quarantaine geplaatste e-mailobjecten beheren. Deze webinterface is toegankelijk via koppelingen
van quarantainerapporten of rechtstreeks door een URL in uw webbrowser in te voeren. Om toegang te krijgen tot
de webinterface voor Quarantaine voor e-mail moet u zich verifiëren met uw domeinreferenties. Internet Explorer
verifieert domeingebruikers automatisch. Het webpaginacertificaat moet echter geldig zijn, Automatisch
aanmelden moet zijn ingeschakeld in Microsoft Internet Explorer en u moet de website E-mailquarantaine aan
Lokale intranetsites toevoegen.
Elke bestaande gebruiker in Active Directory heeft toegang tot de webinterface voor e-mailquarantaine, maar ziet
alleen de items in quarantaine die naar zijn e-mailadres zijn gestuurd (dit omvat ook de aliassen van de gebruiker).
De beheerder kan alle items in quarantaine voor alle geadresseerden zien.
BELANGRIJK
ESET Mail Security maakt geen gebruik van IIS om de webinterface voor e-mailquarantaine uit te voeren. In
plaats daarvan wordt de API voor de HTTP-server gebruikt, waarin SSL-ondersteuning is opgenomen zodat
gegevens via veilige HTTP-verbindingen kunnen worden uitgewisseld.
Web-URL
Dit is de URL waarop de webinterface van E-mailquarantaine beschikbaar is. Standaard is dit de FQDN van de server
met /quarantine (bijvoorbeeld mailserver.company.com/quarantine). U kunt uw eigen virtuele map opgeven in
plaats van de standaardmap /quarantine. U kunt de Web-URL op elk moment wijzigen door de waarde te
bewerken.
De waarde voor Web-URL moet zonder schema (HTTP, HTTPS) en zonder poortnummer worden opgegeven. Gebruik
alleen de vorm fqdn/virtualdirectory. Het is ook mogelijk jokertekens te gebruiken in plaats van de FQDN.
Wanneer u de Web-URL eenmaal hebt gewijzigd, is het niet meer mogelijk de standaardinstelling voor de web-URL
te herstellen door te klikken op het pictogram voor ongedaan maken Verwijder de vermelding en laat het

149
tekstvak leeg. Start de server opnieuw op. Wanneer ESET Mail Security wordt gestart en merkt dat de web-URL leeg
is, wordt dit veld automatisch ingevuld met de fqdn/quarantine-standaardwaarde.
OPMERKING
ESET Mail Security biedt ondersteuning voor web-URL's in vier verschillende vormen:
Sterk jokerteken (+/quarantine)
Expliciet (mydomain.com/quarantine)
IP-gebonden zwak jokerteken (192.168.0.0/quarantine)
Zwak jokerteken (*/quarantine)
Zie het gedeelte Host-Specifier Categories in het artikel UrlPrefix Strings voor meer informatie.
Web- en rapporttaal
Hiermee kunt u de taal van de quarantainewebinterface en quarantainerapporten instellen.
HTTPS-poort
Wordt gebruikt voor de webinterface. Het standaardpoortnummer is 443.
HTTP-poort
Wordt gebruikt voor het via e-mailrapporten vrijgeven van e-mails uit quarantaine.
BELANGRIJK
Als u geen SSL-certificaat hebt geïnstalleerd op IIS, configureer dan HTTPS-poortbinding. Als u het
poortnummer voor HTTPS of HTTP wijzigt, zorg er dan voor dat u de bijbehorende poortbinding in IIS
toevoegt.
Releaseacties registreren in gebeurtenissenlogboek
Bij het vrijgeven van items uit e-mailquarantaine wordt deze actie in Logbestanden geschreven.
Standaardbeheerders inschakelen
Standaard krijgen alle leden van de beheerdersgroep beheerderstoegang tot de webinterface voor e-
mailquarantaine. Beheerderstoegang heeft geen beperkingen en laat de beheerder alle items in quarantaine
voor alle geadresseerden zien. Als u deze optie uitschakelt, hebben alleen beheerdersaccounts toegang tot de
webinterface voor e-mailquarantaine.
Aanvullende toegangsrechten
Verleen gebruikers aanvullende toegang tot de webinterface voor e-mailquarantaine en kies het toegangstype.
Kl ik op Bewerken om het venster Aanvullende toegangsrechten te openen, klik op Toevoegen om toegang aan
een gebruiker te verlenen. Klik in het pop-upvenster Nieuw toegangsrecht op Selecteren en kies een gebruiker
in Active Directory (u kunt slechts één gebruiker kiezen) en selecteer Toegangstype in de vervolgkeuzelijst:
· Beheerder: de gebruiker heeft beheerderstoegang tot de webinterface voor e-mailquarantaine.
· Gedelegeerde toegang: gebruik dit toegangstype als u een gebruiker (gedelegeerde) de berichten in
quarantaine van een andere geadresseerde wilt laten zien en beheren. Geef het Adres van ontvanger op door
een e-mailadres voor een gebruiker te typen waarvoor de berichten die in quarantaine zijn geplaatst door de
gedelegeerde worden beheerd. Als een gebruiker aliassen in Active Directory heeft, kunt u desgewenst
aanvullende toegangsrechten aan elke alias toevoegen.

150
Een voorbeeld van gebruikers die aanvullende toegangsrechten voor de webinterface voor e-mailquarantaine
hebben gekregen:
Als u toegang wilt tot de webinterface van e-mailquarantaine, opent u uw webbrowser en gebruikt u de URL die
wordt weergegeven bij Geavanceerde instellingen (F5) > Server > E-mailquarantaine > Webinterface > Web-URL.

151
Vrijgeven
Geeft e-mail(s) vrij aan de oorspronkelijke ontvanger(s) met behulp van de map Replay en verwijdert de e-mail
uit quarantaine. Klik op Verzenden om de actie te bevestigen.
OPMERKING
Wanneer een e-mail uit quarantaine wordt vrijgegeven, negeert ESET Mail Security de MIME-koptekst To:
omdat deze gemakkelijk kan worden vervalst. In plaats daarvan wordt de oorspronkelijke ontvangerinformatie
van de opdracht RCPT TO: gebruikt die tijdens de SMTP-verbinding is verkregen. Hierdoor wordt gegarandeerd
dat de juiste e-mailontvanger het bericht ontvangt dat uit quarantaine wordt vrijgegeven.
Verwijderen
Verwijdert item uit quarantaine. Kl ik op Verzenden om de actie te bevestigen.
Wanneer u op Onderwerp klikt, wordt er een pop-upvenster geopend met details over de in quarantaine geplaatste
e-mail, zoals Type, Reden, Afzender, Datum, Bijlagen, enz.

152

153
Kl ik op Kopteksten weergeven om de koptekst van de in quarantaine geplaatste e-mail weer te geven.
Klik indien gewenst op Vrijgeven of Verwijderen om een actie op een in quarantaine geplaatst e-mailbericht uit te
voeren.
OPMERKING
U moet uw browservenster sluiten om u volledig af te melden bij de webinterface voor Quarantaine voor e-
mail. Klik anders op Naar quarantaineweergave gaan om terug te keren naar het vorige scherm.
BELANGRIJK

154
Als u problemen hebt om met uw browser toegang te krijgen tot de webinterface voor e-mailquarantaine of
de f out HTTP Error 403.4 - Forbidden of iets soortgelijks ziet, controleer dan welk Quarantainetype is
geselecteerd en zorg ervoor dat dit Lokale quarantaine is en dat W ebinterface inschakel en is ingeschakeld.
6.9.1.2.1 E-mailquarantainerapporten verzenden - geplande taak
E-mailquarantainerapporten zijn meldingen per e-mail die worden verzonden naar geselecteerde gebruikers en
beheerders om ze te informeren over hun e-mailberichten die door ESET Mail Security in quarantaine zijn geplaatst.
In de rapporten staan koppelingen waarmee u, evenals gebruikers die de E-mailquarantainerapporten ontvangen,
vals-positieve (FP) e-mailberichten rechtstreeks kunnen verwijderen of vrijgeven (laten bezorgen). Bezorging van
bepaalde berichten die zijn uitgefilterd door regels of in e-mailquarantaine zijn geplaatst door Antivirusbeveiliging,
is niet toegestaan voor reguliere gebruikers.
Met de taak E-mailquarantainerapporten verzenden/E-mailquarantainerapporten voor de Administrator verzenden
wordt er per e-mail een e-mailquarantainerapport volgens de opgegeven geplande taak verzonden. Dit is een
voorbeeld van een e-mailquarantainerapport:
In een e-mailquarantainerapport staat ook een koppeling naar de webinterface E-mailquarantaine voor gebruikers
(er wordt een onlineviewer geopend).

155
OPMERKING
De taak E-mailquarantainerapporten verzenden is alleen beschikbaar wanneer u lokale quarantaine gebruikt.
U kunt deze taak niet gebruiken met Quarantainepostvak of MS Exchange-quarantaine.
Adres van afzender
Geef een e-mailadres op dat als afzender van het e-mailquarantainerapport moet worden weergegeven.
Maximaal aantal records in rapport
U kunt het aantal vermeldingen in het rapport beperken. Het standaardaantal is ingesteld op 50.
Web-URL
Deze URL wordt opgenomen in het e-mailquarantainerapport, zodat de ontvanger alleen maar op de koppeling
hoeft te klikken om toegang tot de webinterface van Quarantaine voor e-mail te krijgen.
Ontvangers
Kies gebruikers die e-mailquarantainerapporten moeten ontvangen. Klik op Bewerken om de postvakken voor
specifieke ontvangers te selecteren.
OPMERKING
Het rapport E-mailquarantaine wordt alleen verzonden als er berichten in quarantaine zijn geplaatst. Als de
quarantaine leeg is, wordt het rapport niet verzonden.
VOORBEELD
Doelstelling: Maak een geplande taak als u zichzelf als Administrator regelmatig e-mailquarantainerapporten
wilt toesturen, of als u andere gebruikers op de hoogte wilt brengen van hun spamberichten die zich
momenteel in e-mailquarantaine bevinden.
Navi ge e r naar Hulpmiddelen > Planner > Taak toevoegen en open de wizard.
Voe r e en Taaknaam in.
Selecteer Taaktype in het vervolgkeuzemenu: E-mailquarantainerapporten verzenden (het rapport bevat
alleen de spamberichten van een bepaalde gebruiker) of E-mailquarantainerapporten voor de Administrator
verzenden (het rapport bevat alle berichten, de gehele quarantaine) en klik op Volgende.
Selecteer een van de opties om te definiëren wanneer u wilt dat de taak wordt uitgevoerd. Bijvoorbeeld
Wekelijks om 10.00.00 AM uur op Vrijdag.
Geef Adres van afzender op (administrator@mijdomein.com).
Kl ik op Bewerken om Ontvangers uit de lijst toe te voegen. Selecteer de postvakken van de gebruikers die e-
mailquarantainerapporten moeten ontvangen.
6.9.1.2.2 De gebruikerswebinterface voor e-mailquarantaine
U hebt toegang tot een webinterface gekregen waarin u in quarantaine geplaatste berichten kunt beheren, zoals
spam of phishing, en berichten die zijn uitgefilterd door regels die door de beheerder zijn ingesteld. Normaliter
kunt u alleen berichten zien die naar uw e-mailadres zijn verzonden en die in quarantaine zijn geplaatst. Als u
echter gedelegeerde bent van in quarantaine geplaatste berichten van anderen, ziet u ook berichten van die andere
gebruikers. U kunt berichten per ontvanger van elkaar onderscheiden. Gebruik de zoekfunctie om berichten op
ontvanger te filteren bijvoorbeeld.

156
U kunt een actie kiezen om op een of meerdere berichten uit te voeren, zoals vrijgeven, verwijderen of geen actie.
De beschikbaarheid van acties is afhankelijk van het toegangsniveau en regelinstellingen. Het kan bijvoorbeeld zo
zijn dat u bepaalde typen berichten niet mag vrijgeven of verwijderen.
Als aan u beheerderstoegang is toegewezen, ziet u alle in quarantaine geplaatste berichten voor alle gebruikers en
kunt u elke actie uitvoeren.
Uw quarantaineberichten beheren:
· Met de quarantainewebinterface voor e-mail kunt u alles bekijken wat in quarantaine is geplaatst. Als u als
gedelegeerde of zelfs als beheerder toegang hebt, ziet u ook andere quarantaineberichten.
· Linksonder in het venster kunt u het aantal vermeldingen per pagina wijzigen (paginagrootte).
· Als er te veel berichten zijn, gebruikt u de functie Zoeken op de bovenste balk om naar een bepaalde e-mail
te zoeken of de inhoud op Onderwerp, Afzender of Ontvanger te filteren (Ontvanger is alleen beschikbaar
voor gebruikers met gedelegeerde- of beheerderstoegang). En u kunt de selectievakjes gebruiken om alleen
berichten weer te geven van een bepaald type (spam, malware, regel, phishing).
· Als u een bericht wilt vrijgeven (laten bezorgen) dat in quarantaine is geplaatst als gevolg van een vals-
positieve selectie tijdens classificatie, kunt u de keuzerondjes rechts gebruiken en Vrijgeven selecteren.
Selecteer de actie Verwijderen om een bericht te verwijderen. U kunt meerdere berichten tegelijk
selecteren om een actie op uit te voeren. Klik op Verzenden nadat u uw selectie hebt gemaakt. Berichten die
zijn gemarkeerd om te worden vrijgegeven, worden vervolgens bezorgd in uw postvak, of het postvak van de
oorspronkelijke ontvanger, als u gedelegeerdetoegang hebt en berichten voor anderen vrijgeeft. Berichten
die zijn gemarkeerd om te worden verwijderd, worden definitief uit quarantaine verwijderd.
OPMERKING
Bei de acti es, Vrijgeven en Verwijderen, zijn onomkeerbaar nadat u op Verzenden hebt geklikt.

157
· De weergave wordt automatisch vernieuwd wanneer u klikt op Verzenden, maar u kunt de weergave ook
handmatig vernieuwen door de knop Vernieuwen in uw webbrowser te gebruiken of door op F5 op uw
toetsenbord te drukken.
OPMERKING
Alleen spam en phishingberichten kunnen worden vrijgegeven. Het is niet toegestaan berichten van het type
malware en regels vrij te geven. Als u een dergelijk type bericht wilt vrijgeven, vraag uw beheerder dan om
hulp.
· U hoeft in quarantaine geplaatste berichten niet regelmatig te verwijderen. Ze worden automatisch
verwijderd na een bepaalde periode die de beheerder heeft ingesteld.
OPMERKING
U moet het venster van uw webbrowser sluiten om u volledig af te melden bij de webinterface van E-
mailquarantaine. Klik anders op Naar quarantaineweergave gaan om terug te keren naar het vorige scherm.
6.9.2 Quarantainepostvak en MS Exchange-quarantaine
Als u besluit Lokale quarantaine niet te gebruiken, hebt u twee opties: Quarantainepostvak en MS Exchange-
quarantaine. Welke optie u ook kiest, u dient een toegewijde gebruiker met een postvak te maken (bijvoorbeeld
hoofdquarantaine@bedrijf.com) die vervolgens wordt gebruikt om in quarantaine geplaatste e-mailberichten in op
te slaan. Deze gebruiker en dit postvak worden ook door Beheer van e-mailquarantaine gebruikt om in quarantaine
geplaatste items weer te geven en beheren. U moet accountdetails van deze gebruiker opgeven in Instellingen voor
quarantainebeheer.
OPMERKING
Het voordeel van het gebruik van Quarantainepostvak/MS Exchange-quarantaine in plaats van Lokale
quarantaine is dat items in e-mailquarantaine vanaf één plaats worden beheerd, ongeacht het aantal servers
met de rol Hubtransportserver. In tegenstelling tot lokale quarantaine, worden e-mailberichten van
quarantainepostvak/MS Exchange-quarantaine, SPAM en in quarantaine geplaatste e-mailberichten
opgeslagen in database(s) van het Exchange-postvak. Iedereen met toegang tot het quarantainepostvak kan in
quarantaine geplaatste berichten beheren.
Bij zow el Quarantainepostvak als MS Exchange-quarantaine wordt gebruikgemaakt van een speciaal postvak als
onderliggend mechanisme om in quarantaine geplaatste berichten te beheren, maar zij werken iets verschillend
van elkaar in hoe e-mailberichten bij het postvak worden bezorgd. Quarantainepostvak en MS Exchange-
quarantaine:
Quarantainepostvak
ESET Mail Security maakt een afzonderlijke wrapper-e-mail met aanvullende informatie en de oorspronkelijke e-
mails worden als bijlage toegevoegd en bij het postvak bezorgd.
Geef het adres van de quarantaine voor berichten op (bijvoorbeeld main_quarantine@company.com).
BELANGRIJK
We raden niet aan dat u het beheerdergebruikersaccount als quarantainepostvak gebruikt.
MS Exchange-quarantaine
Exchange Server is verantwoordelijk voor de bezorging van e-mail bij het postvak zelf. Het postvak moet worden
ingesteld als quarantaine op organisatieniveau in Active Directory (door een PowerShell-opdracht die hieronder
staat vermeld).

158
OPMERKING
Standaard is interne quarantaine niet geactiveerd in Microsoft Exchange Server. Tenzij het geactiveerd is,
opent u de Exchange-beheershell en voert u de volgende opdracht in (vervang Name@domain.com door een
werkelijk adres van uw toegewijde postvak):
Set-ContentFilterConfig -QuarantineMailbox name@domain.com
ESET Mail Security gebruikt het Microsoft Exchange-quarantainesysteem (dit is van toepassing op Microsoft
Exchange Server 2007 en nieuwer). Hierbij wordt het interne mechanisme van Exchange gebruikt voor het opslaan
van mogelijk geïnfecteerde berichten en spam.
6.9.2.1 Instellingen voor quarantainebeheer
Hostadres
Wordt automatisch weergegeven als uw Exchange Server met de rol Client Access Server (CAS) lokaal aanwezig
is. Of als de CAS-rol niet op dezelfde server aanwezig is waarop ESET Mail Security is geïnstalleerd maar wel in
Active Directory (AD) aanwezig is, wordt het hostadres automatisch weergegeven. Wordt dat niet
weergegeven, dan kunt u de hostnaam handmatig opgeven. Automatisch verwijderen werkt niet bij de rol
Edgetransportserver. IP-adres wordt niet ondersteund. U moet de hostnaam van de CAS-server gebruiken.
Gebruikersnaam
Quarantainegebruikersaccount dat u speciaal hebt gemaakt om in quarantaine geplaatste berichten in op te
slaan (of een account dat via toegangsdelegatie toegang heeft tot dit postvak). Bij de functie
Edgetransportserver die geen deel uitmaakt van het domein, is het nodig het gehele e-mailadres te gebruiken
(bijvoorbeeld main_quarantine@company.com).
Wachtwoord
Typ het wachtwoord van uw quarantaineaccount.
SSL gebruiken
Moet zijn ingeschakeld als Exchange Web Services (EWS) is ingesteld op SSL vereisen in IIS. Als SSL is
ingeschakeld, moet het Exchange Server-certificaat worden geïmporteerd op het systeem met ESET Mail
Security (in het geval de Exchange Server-functies zich op verschillende servers bevinden). Instellingen voor de
EWS vindt u in IIS in Sites/Default web site/EWS/SSL Settings.
OPMERKING
Schakel SSL gebruiken alleen uit als in IIS is geconfigureerd dat Exchange Web Services (EWS) geen SSL vereist.
Servercertificaatfouten negeren
De volgende statussen worden genegeerd: self-signed, wrong name in certificate, wrong usage, expired.
6.9.2.2 Proxyserver
Als u een proxyserver gebruikt tussen uw Exchange Server met CAS-functie en de Exchange Server waarop ESET Mail
Security wordt geïnstalleerd, dient u de parameters van uw proxyserver op te geven. Dit is nodig omdat ESET Mail
Security via HTTP/HTTPS verbinding maakt met de API van Exchange Web Services (EWS). Anders werken
Quarantainepostvak en MS Exchange-quarantaine niet.
Proxyserver
Hier voert u het IP-adres of de naam in van de proxyserver die u gebruikt.
Poort
Hier voert u het poortnummer van de proxyserver in.
Gebruikersnaam, Wachtwoord
Hier geeft u de referenties op als voor uw proxyserver verificatie is vereist.

159
6.9.3 Accountdetails van quarantainebeheer
Dit dialoogvenster wordt weergegeven als u geen accountdetails hebt opgegeven (gebruikersnaam en wachtwoord)
voor uw quarantainebeheer. Geef de referenties voor een gebruiker op die toegang heeft tot Quarantainepostvak
en klik op OK. Of druk op F5 om naar Geavanceerde instellingen te gaan en navigeer naar Server > Quarantaine voor
e-mail > Instellingen voor quarantainebeheer. Typ de Gebruikersnaam e n he t Wachtwoord voor uw
quarantainepostvak.
Klik op het selectievakje naast Accountinformatie opslaan om accountinstellingen op te slaan voor toekomstig
gebruik in quarantainebeheer.
6.10 Antivirustest
Gebruik een testbestand van eicar.com als u wilt verifiëren of real-timebeveiliging werkt en virussen detecteert.
Dit testbestand is een onschadelijk bestand dat door alle antivirusprogramma's wordt gescand. Het bestand is
gemaakt door het bedrijf EICAR (European Institute for Computer Antivirus Research) om de functionaliteit van
antivirusprogramma's te testen. Het bestand is op http://2016.eicar.org/85-0-Download.html beschikbaar om te
downloaden.
6.11 Antispamtest
Met een speciale tekenreeks genaamd GTUBE (Generic Test for Unsolicited Bulk Email) die voor testdoeleinden
wordt gebruikt, kunt u verifiëren of de antispamfunctie van ESET Mail Security werkt en inkomende spamberichten
detecteert.
U test de antispamfunctionaliteit door een e-mail te verzenden met de volgende tekenreeks van 68 bytes in het
tekstgedeelte van het bericht:
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X
Gebruik de tekenreeks zoals die wordt weergegeven (één regel, zonder witruimte of regeleinden). U kunt een
geschi kt e -mail bericht downloaden in RFC-822-indeling.

160
6.12 Antiphishingtest
U test de functionaliteit van antiphishing door een e-mail te verzenden met de volgende koppeling (URL) in het
tekstgedeelte van het bericht of het onderwerp:
https://www.amtso.org/check-desktop-phishing-page/
Controleer Logbestanden > Beveiliging van e-mailserver om de activiteit van Antiphishing-beveiliging te zien. In het
logboek vindt u informatie over e-mailberichten en de phishingkoppelingen die erin zijn gevonden.

161
7. Algemene instellingen
U kunt algemene instellingen en opties overeenkomstig uw behoeften configureren. Het menu aan de linkerkant
bevat de volgende categorieën:
Computer
Detectie van potentieel ongewenste, onveilige, verdachte toepassingen en Anti-Stealth-beveiliging
inschakelen of uitschakelen. Geef uitsluitingen op van processen of bestanden en mappen. Configureer Real-
timebeveiliging van bestandssysteem, ThreatSense-parameters, op de cloud gebaseerde beveiliging (ESET
LiveGrid®), malwarescans (Computerscan op aanvraag en andere scanopties), Hyper-V-scan en HIPS.
Bijwerken
Configureer update-opties zoals profielen, de leeftijd van de detectie-engine, momentopnamen voor het
terugdraaien van modules, updatetype, aangepaste updateserver, verbindings-/proxyserver, updatemirror,
toegang tot updatebestanden, HTTP-server, gebruikersaccountdetails voor netwerkverbinding, enz.
Web en e-mail
Hiermee kunt u het volgende configureren: Protocolfiltering en uitsluitingen (Uitgesloten toepassingen en IP-
adressen), opties voor SSL/TLS-protocolfiltering, Beveiliging van e-mailclient (integratie, e-mailprotocollen,
waarschuwingen en meldingen), Beveiliging van webtoegang (HTTP/HTTPS-webprotocollen en URL-
adresbeheer) en Antiphishing-beveiliging voor e-mailclients.
Apparaatbeheer
Hiermee kunt u integratie inschakelen en regels en groepen voor Apparaatbeheer configureren.
Instellingen voor hulpmiddelen
Hiermee kunt u hulpmiddelen aanpassen, zoals ESET CMD, ESET RMM, WMI-provider, ESET Security
Management Center-scandoelen, meldingen van Windows Update, Logbestanden, Proxyserver, E-
mailmeldingen, Diagnostische gegevens, Cluster, enz.
Gebruikers
Hiermee kunt u het gedrag van de grafische gebruikersinterface van het programma, statussen, licentie-
informatie, waarschuwingen en meldingen, wachtwoordbeveiliging, eShell-uitvoeringsbeleid, enz.
configureren.
7.1 Computer
Antivirus- en antispywarebeveiliging biedt bescherming tegen schadelijke systeemaanvallen door bestanden, e-
mail en netwerkcommunicatie te scannen. Als er een bedreiging wordt gedetecteerd, kan de antivirusmodule deze
onschadelijk maken door de code eerst te blokkeren en deze vervolgens op te schonen, te verwijderen of in
quarantaine te plaatsen.
Scanneropties
Met Scanneropties voor alle beveiligingsmodules (bijvoorbeeld Real-timebeveiliging van bestandssysteem,
Beveiliging van webtoegang) kunt u detectie van de volgende items in- of uitschakelen:
Potentieel ongewenste toepassingen
Een potentieel ongewenste toepassing is software waarvan de bedoeling niet direct schadelijk is, maar
waarmee mogelijk wel ongewenste software wordt geïnstalleerd, het gedrag van een digitaal apparaat wordt
gewijzigd, activiteiten worden uitgevoerd die niet de goedkeuring van de gebruiker hebben of die de gebruiker
niet verwacht of die onduidelijke doelstellingen heeft.
Tot deze categorie behoren: software waarmee reclame wordt weergegeven, wrappers worden gedownload,
diverse browsertaakbalken worden gedownload, software met misleidend gedrag, bundelware, trackware, enz.
Zi e de woordenlijst voor meer informatie over deze typen toepassingen.
Potentieel onveilige toepassingen

162
Deze classificatie wordt gegeven aan legitieme commerciële software die voor schadelijke doeleinden kan
worden misbruikt. Een onveilige toepassing verwijst naar legitieme commerciële software die kan worden
misbruikt voor schadelijke doeleinden.
Deze categorie omvat: hulpprogramma's om software te kraken, licentiecodes te genereren, hacken, op afstand
toegang te krijgen of de controle over te nemen, toepassingen om wachtwoorden te kraken en keyloggers
(programma's die elke toetsenbordaanslag van een gebruiker vastleggen). Deze optie is standaard
uitgeschakeld.
Zi e de woordenlijst voor meer informatie over deze typen toepassingen.
Potentieel verdachte toepassingen
Dit is software die door een merkgebonden compressie- en/of versleutelingsmethode van een
inpakprogramma is gecomprimeerd. Inpakprogramma's worden vaak gebruikt om reverse engineering te
verhinderen of de inhoud van het uitvoerbare bestand te verbergen (bijvoorbeeld om de aanwezigheid van
malware te verbergen).
Deze categorie bestaat uit: alle onbekende toepassingen die zijn gecomprimeerd met een inpakprogramma,
dat vaak wordt gebruikt om malware te comprimeren.
Eerste scan inschakelen
Hiermee kunt u een volledige systeemscan uitvoeren na productinstallatie en updates om bestaande malware
te detecteren en toekomstige systeemscans te versnellen. Deze scan kan net als andere scans worden
onderbroken of geannuleerd vanuit het hoofdvenster van Scan.
Anti-Stealth-beveiliging
Is een geavanceerd systeem dat gevaarlijke programma's zoals rootkits detecteert, die zichzelf kunnen
verbergen voor het besturingssysteem. Dit betekent dat deze programma's niet met de gebruikelijke
testmethoden kunnen worden gedetecteerd.
Uitsluitingen
Hiermee kunt u bestanden en mappen opgeven die u wilt uitsluiten van scannen. Om te garanderen dat alle
objecten worden gescand op bedreigingen, is het raadzaam alleen uitzonderingen te maken wanneer dat
absoluut noodzakelijk is. Situaties waarin u een object mogelijk wilt uitsluiten, zijn bijvoorbeeld grote
databasevermeldingen die de computer zouden vertragen tijdens een scan, of software die conflicteert met de
scan.
AMSI
Laat Microsoft Antimalware Scan Interface (AMSI) PowerShell-scripts scannen die door Windows Script Host
worden uitgevoerd.
7.1.1 Uitzonderingen voor processen
Met de functie Processen uitsluiten kunt u toepassingsprocessen alleen uitsluiten van scannen door anti-malware
bij toegang. Vanwege de essentiële rol van toegewijde servers (toepassingsserver, opslagserver, enz.) zijn
regelmatige back-ups verplicht om een tijdig herstel te kunnen garanderen van een incident, van welke aard dan
ook. Om de snelheid van het maken van back-ups te verhogen, en procesintegriteit en servicebeschikbaarheid te
verbeteren, worden tijdens het maken van back-ups bepaalde technieken gebruikt waarvan bekend is dat deze
conflicteren met antimalwarebeveiliging op bestandsniveau. Soortgelijke problemen kunnen zich voordoen bij
pogingen live migraties uit te voeren van virtuele machines. De enige effectieve manier om beide situaties te
vermijden, is om antimalwaresoftware uit te schakelen. Door het desbetreffende proces uit te sluiten
(bijvoorbeeld die van de back-upoplossing), worden alle bestandsbewerkingen die met een dergelijk uitgesloten
proces in verband worden gebracht, genegeerd en als veilig beschouwd, waardoor verstoring van het back-upproces
wordt geminimaliseerd. Wij raden aan dat u voorzichtig bent met het maken van uitsluitingen. Een back-
upprogramma dat is uitgesloten kan toegang krijgen tot geïnfecteerde bestanden zonder dat er een waarschuwing
wordt geactiveerd. Daarom zijn uitvoerige machtigingen alleen toegestaan in de real-time beveiligingsmodule.
Met de functie Uitzonderingen voor processen kunt u het risico van potentiële conflicten minimaliseren en de
prestaties van uitgesloten toepassingen verbeteren, wat weer een positief effect heeft op de algehele prestaties
en stabiliteit van het besturingssysteem. De uitsluiting van een proces/toepassing is een uitsluiting van het
bijbehorende uitvoerbare bestand (.exe).

163
U kunt uitvoerbare bestanden toevoegen aan de lijst met uitgesloten processen via Geavanceerde instellingen (F5)
> Computer > Real-timebeveiliging van bestandssysteem > Uitzonderingen voor processen of door de lijst met
actieve processen in het hoofdmenu Hulpmiddelen > Actieve processen te gebruiken.
Deze functie is bedoeld om back-uphulpmiddelen uit te sluiten. Door het proces van een back-uphulpmiddel uit te
sluiten van scannen, wordt niet alleen systeemstabiliteit gegarandeerd, maar zijn er ook geen gevolgen voor de
prestaties van back-ups, omdat de back-up niet wordt vertraagd terwijl die wordt uitgevoerd.
VOORBEELD
Kl ik op Bewerken om het beheervenster Uitzonderingen voor processen te openen, waarin u uitsluitingen
kunt Toevoegen en kunt bladeren naar een uitvoerbaar bestand (bijvoorbeeld Backup-tool.exe), dat wordt
uitgesloten van scannen.
Zodra he t .exe-bestand is toegevoegd aan de uitsluitingen, wordt activiteit van dit proces niet meer
gecontroleerd door ESET Mail Security en worden er geen scans meer uitgevoerd op bestandsbewerkingen die
door dit proces worden uitgevoerd.
BELANGRIJK
Als u de browsefunctie niet gebruikt wanneer u een uitvoerbaar procesbestand selecteert, moet u handmatig
een volledig pad naar het uitvoerbare bestand opgeven. Anders werkt de uitsluiting niet juist en rapporteert
HIPS mogelijk fouten.
U kunt ook bestaande processen Bewerken of uit uitsluitingen Verwijderen.
OPMERKING
Beveiliging van webtoegang houdt bijvoorbeeld geen rekening met deze uitsluiting, dus als u het uitvoerbare
bestand van uw webbrowser uitsluit, worden gedownloade bestanden nog steeds gescand. Op deze manier
kan een infiltratie nog steeds worden gedetecteerd. Dit scenario is slechts een voorbeeld en we raden niet
aan uitsluitingen voor webbrowsers te maken.

164
7.1.2 Uitsluitingen
Met uitsluitingen kunt u bestanden en mappen opgeven die u wilt uitsluiten van scannen. Om te garanderen dat
alle objecten worden gescand op bedreigingen, is het raadzaam alleen uitzonderingen te maken wanneer dat
absoluut noodzakelijk is. Situaties waarin u een object mogelijk wilt uitsluiten zijn bijvoorbeeld grote
databasevermeldingen die de computer zouden vertragen tijdens een scan of software die conflicteert met de scan
(bijvoorbeeld back-upsoftware).
WAARSCHUWING
Niet te verwarren met Uitgesloten extensies.
Als u een object van scannen wilt uitsluiten, klik dan op Toevoegen en geef het pad naar een object op of selecteer
het in de boomstructuur. U kunt geselecteerde vermeldingen ook Bewerken en Verwijderen.
OPMERKING
Een bedreiging in een bestand wordt niet gedetecteerd door de module Real-timebeveiliging van
bestandssysteem of de module Computerscan als dat bestand voldoet aan de criteria voor uitsluiting van
scannen.
In het venster Uitsluitingen wordt het Pad naar de uitgesloten bestanden en mappen weergegeven.
Bedreiging
Als de naam van een bedreiging naast een uitgesloten bestand wordt weergegeven, betekent dit dat het
bestand alleen wordt uitgesloten voor die bedreiging. Als dat bestand later geïnfecteerd raakt met andere
malware, wordt het door de antivirusmodule gedetecteerd. Dit type uitsluiting kan alleen voor bepaalde typen
infiltraties worden gebruikt en dit kan worden gedefinieerd in het waarschuwingsvenster (klik op
Geavanceerde opties weergeven e n se le cte er Uitsluiten van detectie), of door Hulpmiddelen > Quarantaine te
selecteren, met de rechtermuisknop op het bestand in quarantaine te klikken en Herstellen en uitsluiten van
scannen te selecteren in het contextmenu.
7.1.2.1 Uitsluiting toevoegen of bewerken
In dit dialoogvenster kunt u uitsluitingen toevoegen en bewerken. Kies het Type uitsluiting in het
vervolgkeuzemenu:
Pad uitsluiten
Sluit een bepaald pad uit (bestand of map) voor deze computer. Gebruik geen jokertekens - sterretje (*) in het
midden van een pad. Zie het volgende kennisbankartikel voor meer informatie.
OPMERKING
Als u de inhoud van een map wilt uitsluiten, vergeet dan niet een sterretje toe te voegen (*) aan het einde van
het pad (C:\Tools\*). C:\Tools wordt niet uitgesloten, omdat vanuit het perspectief van de scanner Tools ook
een bestandsnaam kan zijn.
Bedreiging uitsluiten
Er moet een geldige ESET-detectienaam/bedreigingsnaam worden opgegeven. Er zijn geen beperkingen voor
het gebruik van jokertekens in het midden van een pad. Raadpleeg voor een geldige detectienaam:
Logbestanden > Detecties. Uitsluitingen voor echte infiltraties zijn uiterst gevaarlijk. Sluit alleen getroffen
bestanden/mappen uit door naar de locatie ervan te bladeren in het Padmasker. Uitsluitingen zijn alleen van
toe passing op Potentieel ongewenste toepassingen, Potentieel onveilige toepassingen en verdachte
toepassingen.
Hash uitsluiten

165
Een bestand wordt uitgesloten op basis van een bepaalde hash (SHA1), ongeacht bestandstype, locatie, naam of
de extensie van het bestand.
Als u een groep bestanden wilt opgeven, kunt u gebruikmaken van jokertekens. Met een vraagteken (?) wordt één
variabel teken aangegeven en met een sterretje (*) wordt een variabelentekenreeks van nul of meer tekens
aangegeven.
VOORBEELD
Als u alle bestanden in een map wilt uitsluiten, typt u het pad naar de map en gebruikt u het masker *.*
· Als u een heel station met alle bestanden en onderliggende mappen wilt uitsluiten, gebruikt u het
masker D:\*
· Als u alleen documentbestanden wilt uitsluiten, gebruikt u het masker *.doc
· Als de naam van een uitvoerbaar bestand een bepaald aantal tekens heeft (en het om verschillende
tekens gaat) en u alleen het eerste teken zeker weet (bijvoorbeeld “D”), gebruikt u de volgende
indeling:
D????.exe (vraagtekens staan voor de ontbrekende/onbekende tekens)
VOORBEELD
Paduitsluitingen met een sterretje:
C:\Tools\*: pad moet eindigen op een backslash (\) en sterretje (*) om aan te geven dat dit een map is en
de gehele mapinhoud (bestanden en submappen) worden uitgesloten
C:\Tools\*.*: hetzelfde gedrag als C:\Tools\*, wat betekent dat dit recursief werkt
C:\Tools\*.dat: sl uit dat-bestanden uit in de map Tools
C:\Tools\sg.dat: sluit dit specifieke bestand in dat pad uit
VOORBEELD
U kunt systeemvariabelen gebruiken zoals %PROGRAMFILES% om scanuitsluitingen te definiëren.
· Als u de map Program Files met deze systeemvariabele wilt uitsluiten, gebruikt u het pad %
PROGRAMFILES%\ (zorg ervoor dat u de backslash aan het einde van het pad gebruikt wanneer u mappen
uitsluit)
· Als u alle bestanden in een submap %PROGRAMFILES% wilt uitsluiten, gebruikt u het pad %
PROGRAMFILES%\Excluded_Directory\*.*
De volgende variabelen kunnen worden gebruikt in de paduitsluitingsindeling:
%ALLUSERSPROFILE%
%COMMONPROGRAMFILES%
%COMMONPROGRAMFILES(X86)%
%COMSPEC%
%PROGRAMFILES%
%PROGRAMFILES(X86)%
%SystemDrive%
%SystemRoot%
%WINDIR%
%PUBLIC%

166
Gebruikersspecifieke systeemvariabelen (zoals %TEMP% of %USERPROFILE%) of omgevingsvariabelen (zoals
%PATH%) worden niet ondersteund.
VOORBEELD
Als u een bedreiging wilt uitsluiten, voer dan een geldige bedreigingsnaam in de volgende indeling in:
@NAME=Win32/Adware.Optmedia
@NAME=Win32/TrojanDownloader.Delf.QQI
@NAME=Win32/Bagle.D
7.1.3 Automatische uitsluitingen
De ontwikkelaars van servertoepassingen en besturingssystemen raden aan bepaalde werkbestanden en -mappen
van de meeste van hun producten uit te sluiten van antivirusscans. Antivirusscans kunnen een negatieve invloed
hebben op de prestaties van een server, kunnen leiden tot conflicten en kunnen zelfs verhinderen dat bepaalde
toepassingen worden uitgevoerd op de server. Met uitsluitingen kan het risico van mogelijke conflicten worden
geminimaliseerd en kunnen de algehele prestaties van de server worden verbeterd bij het uitvoeren van
antivirussoftware. Zie de volledige lijst met bestanden die zijn uitgesloten van scannen voor ESET-
serverproducten.
ESET Mail Security identificeert essentiële servertoepassingen en bestanden van het besturingssysteem van de
server, en voegt deze automatisch toe aan de lijst met uitzonderingen. Onde r Automatische uitsluitingen om te
genereren vindt u een lijst met gedetecteerde servertoepassingen waarvoor uitsluitingen zijn gemaakt. Alle
automatische uitsluitingen zijn standaard ingeschakeld. U kunt elke servertoepassing inschakelen/uitschakelen
door op de schakelaar te klikken, met het volgende resultaat:
· Als uitsluiting van een toepassing/besturingssysteem ingeschakeld blijft, worden alle cruciale bestanden en
mappen ervan toegevoegd aan de lijst met bestanden die zijn uitgesloten van scannen (Geavanceerde
instellingen (F5) > Computer > Basis > Uitsluitingen > Bewerken). Elke keer dat de server opnieuw wordt
opgestart, voert het systeem een automatische controle van uitsluitingen uit en worden alle uitsluitingen
hersteld die mogelijk van de lijst zijn verwijderd. Dit is de aanbevolen instelling als u zeker wilt weten dat de
aanbevolen automatische uitsluitingen altijd worden toegepast.
· Als de gebruiker een uitsluiting van een toepassing/besturingssysteem uitschakelt, blijven de cruciale
bestanden en mappen ervan op de ijst met bestanden staan die zijn uitgesloten van scannen (Geavanceerde
instellingen (F5) > Computer Basis > Uitsluitingen > Bewerken). Ze worden echter niet automatisch
gecontroleerd en vernieuwd op de lijst met Uitsluitingen wanneer de server opnieuw wordt opgestart (zie
punt 1 hierboven). Deze instelling wordt aanbevolen voor geavanceerde gebruikers die enkele van de
standaarduitsluitingen willen verwijderen of wijzigen.
Als u de uitsluitingen van de lijst wilt verwijderen zonder de server opnieuw op te starten, moet u deze handmatig
uit de lijst verwijderen. Alle door de gebruiker gedefinieerde uitsluitingen die handmatig zijn opgegeven, blijven
ongewijzigd als gevolg van de hierboven beschreven instellingen.
De automatische uitsluitingen voor Exchange-servers zijn gebaseerd op de aanbevelingen van Microsoft. ESET Mail
Security past alleen 'Uitsluitingen van mappen' toe ('Uitsluitingen van processen' en 'Uitsluitingen van
bestandsnaamextensies' worden niet toegepast). Zie de volgende Microsoft Knowledge Base-artikelen voor meer
informatie:
· Aanbevelingen voor virusscans op Enterprise-computers waarop de huidige ondersteunde versies van
Windows worden uitgevoerd
· Aanbevelingen voor probleemoplossing bij een Exchange Server-computer waarop antivirussoftware is
geïnstalleerd
· Antivirusscannen op bestandsniveau bij Exchange 2007
· Antivirusscannen op bestandsniveau bij Exchange 2010

167
· Antivirussoftware in het besturingssysteem op Exchange-servers (Exchange 2013)
· Windows-antivirussoftware uitvoeren op Exchange 2016-servers
OPMERKING
Er zijn ook Exchange-databasebestanduitsluitingen voor actieve en passieve databases in DAG (Database
Availability Group) die worden gehost op een lokale server. De lijst met automatische uitsluitingen wordt elke
30 minuten bijgewerkt. Als er een nieuw Exchange-databasebestand wordt gemaakt, wordt die automatisch
uitgesloten ongeacht de status ervan, of deze nu actief of passief is.
7.1.4 Gedeelde lokale cache
De gedeelde, lokale ESET-cache verbetert de prestaties in gevirtualiseerde omgevingen doordat er een einde wordt
gemaakt aan dubbel scannen in het netwerk. Zo wordt elk bestand slechts eenmaal gescand en in de gedeelde
cache opgeslagen. Zet de schakelaar Cacheoptie aan om informatie over scans van bestanden en mappen in uw
netwerk op te slaan in de lokale cache. Als u een nieuwe scan uitvoert, zoekt ESET Mail Security naar gescande
bestanden in de cache. Als de bestanden overeenkomen, worden ze uitgesloten van scannen.
De instellingen van Cacheserver bestaan uit:
· Hostnaam: de naam of het IP-adres van de computer waarop zich de cache bevindt.
· Poort: het nummer van de poort die wordt gebruikt voor communicatie (zoals ingesteld in Gedeelde lokale
cache).
· Wachtwoord: geef het wachtwoord voor de gedeelde lokale cache op, indien dat is vereist.
7.1.5 Er is een infiltratie gedetecteerd
Infiltraties kunnen het systeem bereiken vanaf verschillende toegangspunten, zoals vanaf webpagina's, vanuit
gedeelde mappen, via e-mail of vanaf verwisselbare apparaten (USB, externe schijven, cd's, dvd's, diskettes, enz.).
Standaardgedrag
Als algemeen voorbeeld van de manier waarop infiltraties door ESET Mail Security worden behandeld, kunt u
infiltraties vaststellen met:
· Real-timebeveiliging van bestandssysteem
· Beveiliging van webtoegang
· Beveiliging van e-mailclient
· Computerscan op aanvraag
Voor elk van deze opties wordt het standaardopschoonniveau gebruikt en bij alle opties wordt gepoogd het
bestand op te schonen en in Quarantaine te plaatsen of de verbinding te verbreken. Er wordt een meldingsvenster
weergegeven in het systeemvak rechtsonder in het scherm. Zie Opschonen voor meer informatie over
opschoonniveaus en gedrag.
Opschonen en verwijderen
Als er geen vooraf gedefinieerde actie is die voor Real-timebeveiliging van bestandssysteem wordt uitgevoerd,
wordt u in een waarschuwingsvenster gevraagd een optie te selecteren. Gewoonlijk zijn de opties Opschonen,
Verwijderen en Geen actie beschikbaar. Het wordt afgeraden de optie Geen actie te selecteren, omdat in dat geval
de geïnfecteerde bestanden ongewijzigd blijven. De uitzondering hierop is wanneer u er zeker van bent dat het
bestand onschadelijk is en het per vergissing is gedetecteerd.
Pas opschonen toe als een bestand is aangevallen door een virus dat schadelijke code aan het bestand heeft
toegevoegd. Als dit het geval is, probeer dan het geïnfecteerde bestand op te schonen, zodat het voor het
opschonen in de oorspronkelijke staat kan worden hersteld. Als het bestand uitsluitend uit schadelijke code
bestaat, wordt het verwijderd.

168
Als een geïnfecteerd bestand is 'vergrendeld' of wordt gebruikt door een systeemproces, wordt het doorgaans pas
verwijderd wanneer het is vrijgegeven (normaliter na een herstart van het systeem).
Meerdere bedreigingen
Als niet alle geïnfecteerde bestanden zijn opgeschoond tijdens een Computerscan (of als het Opschoonniveau is
i ngeste ld op Niet opschonen), wordt er een waarschuwingsvenster weergegeven waarin u de acties voor die
bestanden kunt kiezen. Selecteer voor elke individuele bedreiging in de lijst een actie of gebruik Selecteer actie
voor alle vermelde bedreigingen en kies één actie die voor alle bedreigingen in de lijst moet worden ondernomen,
en klik vervolgens op Voltooien.
Bestanden in archieven verwijderen
In de modus Standaard opschonen wordt het volledige archief alleen verwijderd als dit uitsluitend geïnfecteerde
bestanden en geen schone bestanden bevat. Met andere woorden, archieven worden niet verwijderd als deze ook
onschadelijke, schone bestanden bevatten. Wees voorzichtig bij het gebruik van een scan in de modus Volledig
opschonen. Hierbij wordt het archief namelijk verwijderd als het minimaal één geïnfecteerd bestand bevat,
ongeacht de status van de andere bestanden in het archief.
7.1.6 Real-timebeveiliging van bestandssysteem
Real-timebeveiliging van bestandssysteem beheert alle aan antivirus gerelateerde gebeurtenissen in het systeem.
Alle bestanden worden gescand op schadelijke code wanneer ze worden geopend, gemaakt of op uw computer
worden uitgevoerd. Real-timebeveiliging van het bestandssysteem wordt standaard gestart bij het opstarten van
het systeem en scant ononderbroken. In bijzondere gevallen (bijvoorbeeld als er een conflict is met een andere
real-time scanner) kan real-timebeveiliging worden uitgeschakeld door Real-timebeveiliging van bestandssysteem
automatisch starten uit te schakelen in Geavanceerde instellingen (F5) onde r Real-timebeveiliging van
bestandssysteem > Basis.
Te scannen media
Standaard worden alle mediatypen gescand op mogelijke bedreigingen:
· Lokale stations: hiermee worden alle systeemschijven gecontroleerd.
· Verwisselbare media: hiermee worden cd's/dvd's, USB-opslagapparaten, Bluetooth-apparaten, enz.
gecontroleerd.
· Netwerkstations: hiermee worden alle toegewezen stations gescand.
Het wordt aangeraden de standaardinstellingen te gebruiken en deze alleen in specifieke gevallen te wijzigen,
bijvoorbeeld wanneer het scannen van bepaalde media tot aanzienlijke vertragingen in de gegevensoverdracht
leidt.
Scannen uitvoeren bij
Standaard worden alle bestanden gescand als ze worden geopend, gemaakt of uitgevoerd. Het wordt aangeraden
deze standaardinstellingen te behouden, omdat deze het hoogste niveau van real-timebeveiliging voor uw
computer bieden:
· Geopende bestanden: scannen wanneer bestanden worden geopend/benaderd.
· Gemaakte bestanden: scannen wanneer bestanden worden gemaakt/gewijzigd.
· Uitgevoerde bestanden: scannen wanneer bestanden worden uitgevoerd.
· Toegang tot verwisselbare media: scannen bij toegang tot verwisselbare opslag.
Uitzonderingen voor processen
Hiermee kunt u specifieke processen uitsluiten. Bij processen van de back-upoplossing bijvoorbeeld worden
alle bestandsbewerkingen die worden toegeschreven aan een dergelijk uitgesloten proces, genegeerd en als
veilig beschouwd, waardoor verstoring van het back-upproces wordt geminimaliseerd.
ThreatSense-parameters

169
Real-timebeveiliging van bestandssysteem controleert alle typen media en wordt geactiveerd door
verschillende systeemgebeurtenissen, zoals het openen van een bestand. Real-timebeveiliging van
bestandssysteem kan worden geconfigureerd om nieuw gemaakte bestanden anders te behandelen dan
bestaande bestanden. U kunt Real-timebeveiliging van bestandssysteem bijvoorbeeld zodanig configureren dat
nieuw gemaakte bestanden uitvoeriger worden gecontroleerd.
Om te zorgen voor een minimale systeembelasting bij het gebruik van real-timebeveiliging, worden reeds
gescande bestanden niet opnieuw gescand (tenzij ze zijn gewijzigd). Bestanden worden onmiddellijk na elke
update voor de detectie-engine opnieuw gescand. Dit gedrag wordt beheerd met Smart-optimalisatie. Als
Smart-optimalisatie wordt uitgeschakeld, worden alle bestanden elke keer gescand wanneer ze worden
gebruikt. Als u deze instelling wilt wijzigen, drukt u op F5 om Geavanceerde instellingen te openen en vouwt u
Computer > Real-timebeveiliging van bestandssysteem uit. Klik op ThreatSense-parameters > Overige en
schakel Smart-optimalisatie inschakelen in of uit.
Aanvullende ThreatSense-parameters
U kunt uitvoerige opties van de Aanvullende ThreatSense-parameters voor nieuw gemaakte en gewijzigde
bestanden of Aanvullende ThreatSense-parameters voor uitgevoerde bestanden wijzigen.
7.1.6.1 ThreatSense-parameters
ThreatSense is technologie die bestaat uit talloze complexe methoden voor het detecteren van bedreigingen. Deze
technologie is proactief. Dit betekent dat ook beveiliging wordt geboden tijdens de vroege verspreiding van een
nieuwe bedreiging. Er wordt gebruikgemaakt van een combinatie van codeanalyse, code-emulatie, generieke
kenmerken en viruskenmerken, die samenwerken om de systeembeveiliging aanzienlijk te verbeteren. De
scanengine is in staat verschillende gegevensstromen tegelijk te controleren voor een maximale efficiëntie en een
zo hoog mogelijk detectiepercentage. De ThreatSense-technologie zorgt tevens voor de verwijdering van rootkits.
OPMERKING
zie Opstartscan voor meer informatie over automatische controle van opstartbestanden.
Via de instellingsopties van de ThreatSense-engine kunt u verschillende scanparameters opgeven:
· Bestandstypen en extensies die moeten worden gescand
· De combinatie van verschillende detectiemethoden
· Opschoonniveaus, enz.
Kl ik op Parameters voor ThreatSense-engine instellen in het venster Geavanceerde instellingen(F5) van elke
module die gebruikmaakt van de ThreatSense-technologie (zie hieronder). Verschillende beveiligingsscenario's
vereisen mogelijk verschillende configuraties. Daarom is ThreatSense afzonderlijk configureerbaar voor de
volgende beveiligingsmodules:
· Beveiliging van e-mailtransport
· Beveiliging van postvakdatabase op aanvraag
· Beveiliging van postvakdatabase
· Hyper-V-scan
· Real-timebeveiliging van bestandssysteem
· Malwarescans
· Scannen bij inactieve status
· Opstartscan
· Documentbescherming
· Beveiliging van e-mailclient
· Beveiliging van webtoegang
ThreatSense-parameters zijn in hoge mate geoptimaliseerd voor elke module. Als u de parameters wijzigt, kan dit
een aanzienlijke invloed hebben op de werking van het systeem. Als bijvoorbeeld parameters voor het altijd
scannen van software voor runtime-compressie worden gewijzigd of als geavanceerde heuristiek wordt

170
ingeschakeld in de module voor Real-timebeveiliging van bestandssysteem, zou dit kunnen resulteren in een
vertraging van het systeem (normaliter worden alleen nieuw gemaakte bestanden gescand via deze methoden).
Wij adviseren de ThreatSense-standaardparameters ongewijzigd te laten voor alle modules met uitzondering van
Computerscan.
Te scannen objecten
In dit gedeelte kunt u opgeven welke computeronderdelen moeten worden gescand op infiltraties.
Werkgeheugen
Hiermee wordt gescand op bedreigingen die zijn gericht op het werkgeheugen van het systeem.
Opstartsectoren/UEFI
Hiermee worden opstartsectoren gescand op de aanwezigheid van virussen in de Master Boot Record (MBR). In
het geval van een virtuele Hyper-V-machine wordt de Master Boot Record van de desbetreffende schijf alleen
in de modus Alleen-lezen gescand.
E-mailbestanden
Het programma ondersteunt de volgende extensies: DBX (Outlook Express) en EML.
Archieven
Het programma ondersteunt de volgende extensies: ARJ, BZ2, CAB, CHM, DBX, GZIP, ISO/BIN/NRG, LHA, MIME,
NSIS, RAR, SIS, TAR, TNEF, UUE, WISE, ZIP, ACE, enzovoort.
Zelfuitpakkende archieven
Zelfuitpakkende archieven (SFX) zijn archieven die kunnen worden uitgepakt zonder gespecialiseerde
programma's (archieven) te gebruiken.
Software voor runtime-compressie
Na uitvoering wordt software voor runtime-compressie (in tegenstelling tot standaardarchieftypen) in het
geheugen uitgepakt. Dankzij emulatie van de programmacode kan de scanner niet alleen
standaardprogramma's voor statische compressie (zoals UPX, yoda, ASPack en FSG), maar ook allerlei andere
compressieprogramma's herkennen.
OPMERKING
Voor de functie Beveiliging van postvakdatabase worden bijgevoegde e-mailbestanden (bijvoorbeeld .eml
files) gescand, ongeacht de instelling onder Te scannen objecten. De reden hiervoor is dat Exchange Server het
bijgevoegde .eml-bestand parseert voordat het door ESET Mail Security voor een scan wordt ingediend. De
VSAPI-plug-in krijgt uitgepakte bestanden vanuit de .eml-bijlage en ontvangt niet het oorspronkelijke .eml-
bestand.
Scanopties
Selecteer de methoden die moeten worden gebruikt wanneer het systeem op infiltraties wordt gescand. De
volgende opties zijn beschikbaar:
Heuristiek
Een heuristiek is een algoritme dat de (schadelijke) activiteit van programma's analyseert. Het voornaamste
voordeel van deze technologie is het vermogen om schadelijke software te identificeren die nog niet bestond
of niet bekend was in de vorige detectie-engine.
Geavanceerde heuristiek/DNA-kenmerken
De geavanceerde heuristiek bestaat uit een uniek heuristisch algoritme dat door ESET is ontwikkeld en dat is
geoptimaliseerd voor het detecteren van computerwormen en Trojaanse paarden. Dit algoritme is geschreven

171
in geavanceerde programmeertalen. Het gebruik van geavanceerde heuristiek vergroot de
bedreigingsdetectiemogelijkheden van ESET-producten aanzienlijk. Kenmerken (handtekeningen) kunnen
virussen op betrouwbare wijze detecteren en identificeren. Dankzij het automatische updatesysteem zijn
nieuwe kenmerken binnen enkele uren beschikbaar. Het nadeel van kenmerken is dat ze alleen bekende
virussen (of varianten van deze virussen) detecteren.
Opschonen
De opschooninstellingen bepalen het gedrag van de scanner tijdens het opschonen van geïnfecteerde bestanden. Er
zijn 3 opschoonniveaus:
Niet opschonen
Geïnfecteerde bestanden worden niet automatisch opgeschoond. Er wordt een waarschuwingsvenster
weergegeven en de gebruiker kan een actie kiezen. Dit niveau is bedoeld voor gevorderde gebruikers die
weten welke stappen moeten worden genomen als er sprake is van een infiltratie.
Normaal opschonen
Het programma probeert automatisch een geïnfecteerd bestand op te schonen of te verwijderen op basis van
een vooraf gedefinieerde actie (afhankelijk van het type infiltratie). Detectie en verwijdering van een
geïnfecteerd bestand worden aangegeven met een melding rechtsonder in het scherm. Als de juiste actie niet
automatisch kan worden geselecteerd, worden andere vervolgacties aangeboden. Hetzelfde gebeurt als een
vooraf gedefinieerde actie niet kan worden voltooid.
Volledig opschonen
Alle geïnfecteerde bestanden (inclusief archieven) worden opgeschoond of verwijderd. Dit geldt niet voor
systeembestanden. Als het niet mogelijk is een bestand op te schonen, wordt de gebruiker gevraagd welke
type actie moet worden ondernomen.
WAARSCHUWING
Archieven met een of meer geïnfecteerde bestanden kunnen op twee manieren worden verwerkt. In de
standaardmodus, Normaal opschonen, worden archieven waarin alle bestanden zijn geïnfecteerd in hun
geheel verwijderd. In de modus Volledig opschonen worden archieven met minstens één geïnfecteerd
bestand verwijderd, ongeacht de status van de overige bestanden in het archief.
BELANGRIJK
Als Hyper-V-host wordt uitgevoerd op Windows Server 2008 R2 SP1, wordt er geen ondersteuning geboden
voor Normaal opschonen en Volledig opschonen. Het scannen van VM-schijven vindt in de modus Alleen-
lezen plaats. Er wordt niet opgeschoond. Ongeacht het opschoningsniveau dat wordt geselecteerd, wordt de
scan altijd uitgevoerd in de modus Alleen-lezen.
Uitsluitingen
Een extensie is het deel van een bestandsnaam dat wordt afgebakend door een punt. De extensie definieert het
type en de inhoud van het bestand. In dit gedeelte van de instellingen voor ThreatSense-parameters kunt u de
typen bestanden definiëren die u wilt uitsluiten van scannen.
Anderis
Wanneer u de instellingen van de parameters voor de ThreatSense-engine configureert voor een computerscan op
aanvraag, zijn ook de volgende opties beschikbaar in het gedeelte Overige:
Alternatieve gegevensstromen (ADS) scannen

172
Alternatieve gegevensstromen (ADS) die worden gebruikt door het NTFS-bestandssysteem zijn bestands- en
mapkoppelingen die onzichtbaar zijn voor normale scantechnieken. Veel infiltraties proberen detectie te
vermijden door zichzelf te vermommen als alternatieve gegevensstromen.
Achtergrondscans uitvoeren met lage prioriteit
Elke scanprocedure neemt een bepaalde hoeveelheid systeembronnen in beslag. Als u werkt met programma's
die de systeembronnen zwaar belasten, kunt u achtergrondscans met een lage prioriteit inschakelen en zo
bronnen besparen ten gunste van uw toepassingen.
Alle objecten in logbestand registreren
Als deze optie is geselecteerd, worden in het logbestand alle gescande bestanden weergegeven, zelfs niet-
geïnfecteerde bestanden.
Smart-optimalisatie inschakelen
Wanneer Smart-optimalisatie is ingeschakeld, worden de optimale instellingen gebruikt om het efficiëntste
scanniveau te garanderen, terwijl ook de hoogste scansnelheden worden behaald. De diverse
beveiligingsmodules scannen op intelligente wijze, waarbij gebruik wordt gemaakt van verschillende
scanmethoden die op specifieke bestandstypen worden toegepast. Als Smart-optimalisatie is uitgeschakeld,
worden alleen de door de gebruiker gedefinieerde instellingen in de ThreatSense-kern van de desbetreffende
module toegepast bij het uitvoeren van een scan.
Tijdstempel laatste toegang bewaren
Selecteer deze optie om de oorspronkelijke toegangstijd van gescande bestanden te handhaven in plaats van
deze bij te werken (bijvoorbeeld voor gebruik met back-upsystemen).
Limiet
Gebruik het gedeelte Limiet om de maximale grootte op te geven van objecten die moeten worden gescand,
evenals het maximale niveau voor het scannen van geneste archieven:
Standaardinstellingen voor objecten
Inschakelen als u standaardinstellingen wilt gebruiken (geen limieten). ESET Mail Security negeert uw
aangepaste instellingen.
Maximale objectgrootte
De maximale grootte van objecten die moeten worden gescand. De antivirusmodule scant dan alleen objecten
die kleiner zijn dan de opgegeven grootte. Deze waarde mag alleen worden gewijzigd door gevorderde
gebruikers die een specifieke reden hebben om grotere objecten niet te scannen. Standaardwaarde:
onbeperkt.
Maximale scantijd voor object (sec.)
De maximale tijd voor het scannen van een object. Als hier een waarde is ingevoerd, wordt het scannen van
een object beëindigd wanneer die tijd is verstreken, ongeacht of de scan is voltooid. Standaardwaarde:
onbeperkt.
Instellingen voor archieven scannen
Schakel Standaardinstellingen voor archieven scannen uit als u archiefscaninstellingen wilt wijzigen.
Nestingsniveau voor archieven
Het maximum aantal niveaus waarop archieven moeten worden gescand. Standaardwaarde: 10. Voor objecten
die worden gedetecteerd door Beveiliging van postvaktransport is het feitelijke nestingsniveau +1, omdat de
archiefbijlage in een e-mail als het eerste niveau wordt beschouwd.
VOORBEELD

173
Als u bijvoorbeeld het nestingsniveau hebt ingesteld op 3, wordt een archiefbestand met nestingsniveau 3
feitelijk alleen gescand bij een transportlaag tot niveau 2. Als u wilt dat archieven door Beveiliging van
postvaktransport tot niveau 3 worden gescand, dient u de waarde voor Nestingsniveau voor archieven in te
stellen op 4.
Maximale grootte van bestand in archief
Met deze optie kunt u de maximale bestandsgrootte opgeven voor bestanden in archieven (wanneer deze
worden uitgepakt) die moeten worden gescand. Standaardwaarde: onbeperkt.
OPMERKING
We raden niet aan de standaardwaarden te wijzigen. In de meeste gevallen is het niet nodig de
standaardwaarden te wijzigen.
7.1.6.1.1 Aanvullende ThreatSense-parameters
Aanvullende ThreatSense-parameters voor nieuwe en aangepaste bestanden
De waarschijnlijkheid dat nieuwe en gewijzigde bestanden geïnfecteerd zijn, is verhoudingsgewijs hoger dan
bij bestaande bestanden. Om deze reden worden die bestanden met aanvullende scanparameters
gecontroleerd. Naast de gewone scanmethoden op basis van viruskenmerken wordt ook gebruikgemaakt van
geavanceerde heuristiek, waarmee nieuwe bedreigingen worden gedetecteerd voordat de module wordt
vrijgegeven. Naast nieuwe bestanden worden zelfuitpakkende bestanden (.SFX) en programma's voor runtime-
compressie (intern gecomprimeerde uitvoerbare bestanden) gescand. Archieven worden standaard tot
maximaal tien nestingsniveaus gescand. De grootte van de archieven wordt voorafgaand aan de scan niet
gecontroleerd. Als u de instellingen voor het scannen van archieven wilt wijzigen, schakelt u
Standaardinstellingen voor archieven scannen uit.
Aanvullende ThreatSense-parameters voor uitgevoerde bestanden
Standaard wordt Geavanceerde heuristiek gebruikt wanneer bestanden worden uitgevoerd. Indien
ingeschakeld, raden we ten zeerste aan Smart-optimalisatie en ESET LiveGrid® ingeschakeld te laten om de
invloed op de systeemprestaties te minimaliseren.
7.1.6.1.2 Bestandsextensies die moeten worden uitgesloten van scans
Een extensie is het onderdeel van een bestandsnaam na de punt. De extensie geeft het bestandstype aan.
Normaliter worden alle bestanden gescand. Als u echter bestanden met een bepaalde extensie wilt uitsluiten, kunt
u met de parameterinstellingen voor ThreatSense-bestanden op basis van hun extensie uitsluiten van scannen.
Uitsluiten kan nuttig zijn als het scannen van bepaalde bestandstypen verhindert dat een toepassing wordt
uitgevoerd.
VOORBEELD
Als u een nieuwe extensie aan de lijst wilt toevoegen, klikt u op Toevoegen. Typ de extensie in het tekstveld
(bijvoorbeeld tmp) en klik op OK. Wanneer u Geef meerdere waarden op selecteert, kunt u meerdere
bestandsextensies toevoegen, van elkaar gescheiden door regels, komma's of puntkomma's (kies
bijvoorbeeld Puntkomma als scheidingsteken in het vervolgkeuzemenu en typ edb;eml;tmp).
Het is mogelijk het speciale teken ? (vraagteken) te gebruiken. Het vraagteken vertegenwoordigt elk symbool
(bijvoorbeeld ?db).
OPMERKING

174
Als u voor alle bestanden in een Windows-besturingssysteem de extensie (bestandstype) wilt weergeven,
schakel t u Extensies voor bekende bestandstypen verbergen ui t onde r Configuratiescherm > Mapopties >
Weergave.
7.1.7 Op de cloud gebaseerde beveiliging
ESET LiveGrid® is een geavanceerd vroegtijdig waarschuwingssysteem dat bestaat uit diverse op de cloud
gebaseerde technologieën. Hiermee kunt u opkomende bedreigingen detecteren op basis van reputatie en worden
scanprestaties verbeterd aan de hand van witte lijsten. Nieuwe informatie over bedreigingen wordt in real-time
naar de cloud gestreamd, waardoor het ESET Malware Research Lab tijdig kan reageren en steeds consistente
beveiliging kan bieden. De gebruiker kan de reputatie van actieve processen en bestanden rechtstreeks bekijken in
de programma-interface of het contextmenu met extra informatie van ESET LiveGrid®.
Selecteer een van de volgende opties wanneer u ESET Mail Security selecteert:
· U kunt ervoor kiezen ESET LiveGrid® niet in te schakelen. De software blijft op dezelfde wijze functioneren,
maar in bepaalde gevallen reageert ESET Mail Security mogelijk trager op nieuwe bedreigingen dan een
update van de detectie-engine.
· U kunt ESET LiveGrid® zodanig configureren dat er anonieme informatie wordt verzonden over nieuwe
bedreigingen en de locatie waar de nieuwe bedreigingscode is gedetecteerd. Dit bestand kan voor
gedetailleerde analyse naar ESET worden verzonden. Na bestudering van deze bedreigingen kan ESET haar
voorzieningen voor bedreigingsdetectie vervolgens bijwerken.
ESET LiveGrid® verzamelt informatie over uw computer met betrekking tot nieuw gedetecteerde bedreigingen.
Deze informatie kan een voorbeeld of kopie bevatten van het bestand waarin de bedreiging voorkwam, het pad
naar dat bestand, de bestandsnaam, de datum en tijd, het proces waarbij de bedreiging plaatsvond op uw computer
en informatie over het besturingssysteem van uw computer.
Standaard wordt ESET Mail Security zodanig geconfigureerd dat verdachte bestanden voor analyse naar het
viruslaboratorium van ESET worden verzonden. Bestanden met bepaalde extensies zoals .doc of .xls worden altijd
uitgesloten. U kunt ook andere extensies toevoegen als er specifieke bestanden zijn die u of uw organisatie niet wil
verzenden.
ESET LiveGrid®-reputatiesysteem inschakelen (aanbevolen)
Het ESET LiveGrid®-reputatiesysteem verbetert de efficiëntie van de antimalwareoplossingen van ESET door
gescande bestanden te vergelijken met een database met items die op een witte of zwarte lijst in de cloud zijn
geplaatst.
ESET LiveGrid®-feedbacksysteem inschakelen
Gegevens worden voor verdere analyse naar het ESET-onderzoekslab verzonden.
Crashrapporten en diagnostische gegevens verzenden
Gegevens verzenden zoals crashrapporten en geheugendumps van modules.
Anonieme statistieken verzenden
Sta ESET toe anonieme informatie te verzamelen over nieuw ontdekte bedreigingen, zoals de
bedreigingsnaam, datum en tijd van detectie, detectiemethode en bijbehorende metagegevens, gescande
bestanden (hash, bestandsnaam, oorsprong van het bestand, telemetrie), geblokkeerde en verdachte URL's,
productversie en -configuratie, waaronder informatie over uw systeem.
E-mail van contactpersoon (optioneel)
Uw e-mailadres wordt samen met verdachte bestanden verzonden, en we kunnen per e-mail contact met u
opnemen als we meer informatie nodig hebben voor de analyse. U ontvangt geen reactie van ESET tenzij er
meer informatie nodig is.
Verzenden van voorbeelden

175
Geïnfecteerde voorbeelden automatisch verzenden
Hiermee worden alle geïnfecteerde voorbeelden ter analyse naar ESET verzonden om toekomstige detectie te
verbeteren.
· Alle geïnfecteerde voorbeelden
· Alle voorbeelden behalve documenten
· Niet indienen
Verdachte voorbeelden automatisch verzenden
Verdachte voorbeelden en/of voorbeelden die qua inhoud of gedrag gelijkenis tonen met bedreigingen, worden
voor analyse naar ESET verzonden.
· Uitvoerbare bestanden: inclusief uitvoerbare bestanden: .exe, .dll, .sys
· Archieven: inclusief bestanden van het type archief: .zip, .rar, .7z, .arch, .arj, .bzip2, .gzip, .ace, .arc, .cab
· Scripts: inclusief bestanden van het type script: .bat, .cmd, .hta, .js, .vbs, .js, .ps1
· Overige: inclusief bestanden van het type: .jar, .reg, .msi, .swf, .lnk
· Mogelijk ongewenste e-mails: verbetert algemene detectie van spam.
· Documenten: inclusief Microsoft Office-documenten en PDF's met actieve inhoud.
Uitsluitingen
Klik op de optie Bewerken naast Uitsluitingen in ESET LiveGrid® om te configureren hoe bedreigingen voor
analyse naar het viruslaboratorium van ESET worden verzonden.
Maximumgrootte van voorbeelden (MB)
Definieer de maximale grootte van voorbeelden die moeten worden gescand.

176
7.1.7.1 Uitsluitingsfilter
Met Uitsluitingsfilter kunt u bepaalde bestanden/mappen uitsluiten van verzending (het kan bijvoorbeeld nuttig
zijn om bestanden uit te sluiten die vertrouwelijke informatie bevatten, zoals documenten en spreadsheets). De
weergegeven bestanden worden nooit voor analyse naar het lab van ESET verzonden, zelfs niet als de bestanden
een verdachte code bevatten. Veelgebruikte bestandstypen (.doc enz.) zijn standaard uitgesloten. U kunt
bestandstypen toevoegen aan de lijst met uitgesloten bestanden als u dat wilt.
Als u ESET LiveGrid® eerder hebt gebruikt en hebt uitgeschakeld, kunnen er nog gegevenspakketten zijn die moeten
worden verzonden. Zelfs na deactivering worden dergelijke pakketten naar ESET verzonden. Nadat alle huidige
informatie is verzonden, worden er geen nieuwe pakketten meer gemaakt.
Als u een verdacht bestand ontdekt, kunt u dit voor analyse naar onze bedreigingslaboratoria verzenden. Als het
bestand een schadelijke toepassing is, wordt de detectie ervan toegevoegd aan de volgende update van de
detectiemodule.

177
7.1.8 Malwarescans
In dit gedeelte vindt u opties om scanparameters te selecteren.
OPMERKING
Deze scanprofielselector is van toepassing op Op aanvraag scannenen Hyper-V-scan.
Geselecteerd profiel
Een bepaalde set parameters die door Scanner op aanvraag wordt gebruikt. U kunt een van de vooraf
gedefinieerde scanprofielen gebruiken of een nieuw profiel maken. De scanprofielen gebruiken verschillende
ThreatSense-engineparameters.
Lijst met profielen
Kl ik op Bewerken om een nieuw profiel toe te voegen. Typ de naam voor het profiel en klik op Toevoegen. Het
nieuwe profiel wordt weergegeven in het vervolgkeuzemenu Geselecteerd profiel, waarin bestaande
scanprofielen staan.
Scandoelen
Als u een bepaald doel wilt scannen, klikt u op Bewerken en kiest u een optie in het vervolgkeuzemenu of
selecteert u specifieke doelen in de mappenstructuur.
ThreatSense-parameters
Scanparameters voor een computerscan op aanvraag wijzigen.
He t pop- upve nste r Hyper-V-scan:
De ve rvol gke uzel ijst Scandoelen voor Hyper-V bevat de volgende, vooraf gedefinieerde scandoelen:
Met profielinstellingen
Hiermee selecteert u doelen die in het geselecteerde scanprofiel zijn ingesteld.
Alle virtuele machines
Hiermee selecteert u alle virtuele machines.

178
Met profielinstellingen
Hiermee selecteert u doelen die in het geselecteerde scanprofiel zijn ingesteld.
Ingeschakelde virtuele machines
Hiermee selecteert u alle online-VM's.
Uitgeschakelde virtuele
machines
Hiermee selecteert u alle offline-VM's.
Geen selectie
Hiermee worden alle selecties gewist.
Kl ik op Scannen om de scan uit te voeren met de aangepaste parameters die u hebt ingesteld. Nadat alle scans zijn
voltooid, controleert u Logbestanden > Hyper-V-scan.
7.1.8.1 Profielbeheer
In het vervolgkeuzemenu Scanprofiel kunt u vooraf gedefinieerde scanprofielen selecteren.
· Smart scan
· Scan van contextmenu
· Dieptescan
· Mijn profiel (van toepassing op Hyper-V-scan, Updateprofielen)
Raadpleeg het gedeelte Parameters voor ThreatSense-engine instellen voor een beschrijving van elke parameter
van de scaninstellingen, zodat u een scanprofiel kunt maken dat aan uw behoeften voldoet.
Profielbeheer wordt gebruikt op drie plaatsen in ESET Mail Security.
Computerscan op aanvraag
U kunt uw voorkeursparameters voor scannen opslaan voor toekomstige scans. Wij adviseren voor elke
regelmatig gebruikte scan een ander profiel te maken (met verschillende scandoelen, scanmethoden en
andere parameters).
Bijwerken
Met de profieleditor kunnen gebruikers nieuwe updateprofielen maken. Er hoeven alleen aangepaste
updateprofielen te worden gemaakt als uw computer op meerdere manieren verbinding maakt met
updateservers.
Hyper-V-scan
Selecteer Bewerken naast Lijst met profielen om een nieuw profiel te maken. Het nieuwe profiel wordt
weergegeven in het vervolgkeuzemenu Geselecteerd profiel, waarin bestaande scanprofielen staan.
7.1.8.2 Profieldoelen
U kunt opgeven wat er wordt gescand op infiltraties. Kies objecten (geheugen, opstartsectoren en UEFI, stations,
bestanden en mappen of netwerk) in de boomstructuur met alle beschikbare doelen op uw systeem.
OPMERKING
Deze scanprofielselector is van toepassing op Op aanvraag scannenen Hyper-V-scan.
Klik op het tandradpictogram linksboven om toegang te krijgen tot de vervolgkeuzemenu's Scandoelen en
Scanprofiel.

179
In het vervolgkeuzemenu Scandoelen kunt u vooraf gedefinieerde scandoelen selecteren:
Met
profielinstelling
en
Hiermee selecteert u doelen die in het geselecteerde scanprofiel zijn ingesteld.
Verwisselbare
media
Hiermee selecteert u diskettes, USB-opslagapparaten en cd's/dvd's.
Lokale stations
Hiermee selecteert u alle harde schijven van het systeem.
Netwerkstations
Hiermee selecteert u alle toegewezen netwerkstations.
Gedeelde
mappen
Hiermee selecteert u alle mappen op de lokale server die zijn gedeeld.
Aangepaste
selectie
Hiermee worden alle selecties gewist. Nadat deze zijn gewist, kunt u een eigen selectie maken.
Als u snel naar een scandoel (bestand of map) wilt gaan om deze in een scan op te nemen, geeft u het pad
ernaartoe op in het tekstveld onder de boomstructuur. De invoer van het pad is hoofdlettergevoelig.
In het vervolgkeuzemenu Scanprofiel kunt u vooraf gedefinieerde scanprofielen selecteren:
· Smart scan
· Scan van contextmenu
· Dieptescan
Deze scanprofielen gebruiken andere ThreatSense-engineparameters.
Voortgang van scan weergeven

180
Als u alleen het systeem wilt scannen zonder aanvullende opschoonacties, selecteer dan Scannen zonder
opschonen. Het is handig om op deze manier een overzicht te krijgen en te zien of er geïnfecteerde items zijn
en u uitvoerige informatie wilt hebben over deze infecties, als daar sprake van is. U kunt een keuze maken uit
drie opschoonniveaus door te klikken op Instellingen > ThreatSense -parameters > Opschonen. Informatie over
scannen wordt opgeslagen in een scanlogboek.
Uitsluitingen negeren
Wanne er u Uitsluitingen negeren selecteert, kunt u een scan uitvoeren terwijl uitsluitingen worden genegeerd
die anders van toepassing zouden zijn.
7.1.8.3 Scandoelen
Als u alleen een bepaald doel wilt scannen, kunt u Aangepaste scan gebruiken en een optie selecteren in het
vervolgkeuzemenu Scandoelen of bepaalde doelen selecteren in de mappenstructuur (boomstructuur).
De selector voor scandoelprofielen is van toepassing op:
· Scan op aanvraag
· Hyper-V-scan
Als u snel naar een scandoel wilt navigeren of een nieuw doelbestand of een nieuwe doelmap wilt toevoegen, voer
dan het doel in het lege veld onder de mappenlijst in. Dit is alleen mogelijk als er geen doelen zijn geselecteerd in
de structuur en het menu Scandoelen is ingesteld op Geen selectie.
De ve rvol gke uzel ijst Scandoelen bevat de volgende, vooraf gedefinieerde scandoelen.
Met
profielinstelling
en
Hiermee selecteert u doelen die in het geselecteerde scanprofiel zijn ingesteld.
Verwisselbare
media
Hiermee selecteert u diskettes, USB-opslagapparaten en cd's/dvd's.

181
Met
profielinstelling
en
Hiermee selecteert u doelen die in het geselecteerde scanprofiel zijn ingesteld.
Lokale stations
Hiermee selecteert u alle harde schijven van het systeem.
Netwerkstations
Hiermee selecteert u alle toegewezen netwerkstations.
Gedeelde
mappen
Hiermee selecteert u alle mappen op de lokale server die zijn gedeeld.
Aangepaste
selectie
Hiermee worden alle selecties gewist. Nadat deze zijn gewist, kunt u een eigen selectie maken.
U kunt een profiel kiezen in het vervolgkeuzemenu Scanprofiel dat u kunt gebruiken om gekozen doelen te
scannen. Het standaardprofiel is Smart scan. Er zijn nog twee vooraf gedefinieerde scanprofielen, genaamd
Dieptescan en Scan van contextmenu. Deze scanprofielen gebruiken verschillende ThreatSense-engineparameters.
He t pop- upve nste r Aangepaste scan:
Voortgang van scan weergeven
Als u alleen het systeem wilt scannen zonder aanvullende opschoonacties, selecteer dan Scannen zonder
opschonen. Het is handig om op deze manier een overzicht te krijgen en te zien of er geïnfecteerde items zijn
en u uitvoerige informatie wilt hebben over deze infecties, als daar sprake van is. U kunt een keuze maken uit
drie opschoonniveaus door te klikken op Instellingen > ThreatSense -parameters > Opschonen. Informatie over
scannen wordt opgeslagen in een scanlogboek.
Uitsluitingen negeren
U kunt een scan uitvoeren en uitsluitingen negeren die anders van toepassing zouden zijn.
Scannen
Hiermee kunt u de scan uitvoeren met de parameters die u hebt ingesteld.

182
Scannen als beheerder
Hiermee kunt u de scan uitvoeren vanuit het Admin-account. Klik hierop als de huidige gebruiker niet de juiste
rechten heeft om toegang te krijgen tot de bestanden die moeten worden gescand. Deze knop is niet
beschikbaar als de huidige gebruiker geen UAC-bewerkingen kan aanroepen als Administrator.
7.1.8.4 Scan bij inactieve status
Als de computer inactief is, wordt er een stille computerscan uitgevoerd op alle lokale stations. Detectie van
inactieve status wordt uitgevoerd wanneer uw computer zich in een van de volgende statussen bevindt:
· Scherm of schermbeveiliging uitschakelen
· Computervergrendeling
· Afmelden van gebruiker
Uitvoeren, zelfs als de computer op batterijvoeding werkt
Standaard wordt Scannen bij inactieve status niet uitgevoerd als de computer (notebook) op batterijvoeding
werkt.
Logboekregistratie inschakelen
Als u de uitvoer van een computerscan wilt vastleggen in het gedeelte Logboekbestanden (klik in het
hoofdprogrammavenster op Logboekbestanden en selecteer Computerscan in het vervolgkeuzemenu).
ThreatSense-parameters
Scanparameters aanpassen van de scanner voor de inactieve status.
7.1.8.5 Opstartscan
De automatische bestandscontrole bij opstarten wordt standaard uitgevoerd als het systeem wordt gestart
(gebruikersaanmelding) en na een geslaagde module-updates. Deze scan wordt beheerd door de configuratie en
taken van Planner.
Opstartscanopties maken deel uit van de geplande taak Opstartbestanden van systeem controleren.
Als u de opstartscanopties wilt wijzigen, navigeert u naar Hulpmiddelen > Planner, selecteert u een van de taken
genaamd Automatische bestandscontrole bij opstarten (gebruikersaanmelding of module-update) en klikt u op
Bewerken. Klik door de wizard en in de laatste stap kunt u gedetailleerde opties van Automatische
bestandscontrole bij opstarten wijzigen.
7.1.8.5.1 Automatische bestandscontrole bij opstarten
Wanneer u een geplande taak maakt voor Opstartbestanden van systeem controleren, hebt u verschillende opties
voor het aanpassen van de volgende parameters:
Met het vervolgkeuzemenu Scandoel bepaalt u de scandiepte voor bestanden die worden uitgevoerd bij het
opstarten van het systeem. Bestanden worden ingedeeld in oplopende volgorde, op basis van de volgende criteria:
· Alle geregistreerde bestanden (het grootste aantal bestanden wordt gescand)
· Zelden gebruikte bestanden
· Algemeen gebruikte bestanden
· Frequent gebruikte bestanden
· Alleen de meest frequent gebruikte bestanden (het kleinste aantal bestanden wordt gescand)
Er zijn ook twee specifieke groepen voor Scandoel:
Bestanden die worden uitgevoerd vóór aanmelding van gebruiker

183
Bevat bestanden van locaties waar de gebruiker toegang toe heeft zonder te zijn aangemeld (inclusief bijna alle
opstartlocaties, zoals services, browserhelperobjecten, meldingen voor Winlogon, planningsgegevens van
Windows, bekende dll's).
Bestanden die worden uitgevoerd na aanmelden van gebruiker
Bevat bestanden van locaties waar de gebruiker alleen toegang toe heeft wanneer hij of zij is aangemeld
(inclusief bestanden die alleen worden uitgevoerd door een specifieke gebruiker, zoals bestanden in
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run).
De lijsten van bestanden die moeten worden gescand, staan voor elke genoemde groep vast.
Scanprioriteit
Het prioriteitsniveau dat wordt gebruikt om te bepalen wanneer een scan wordt gestart:
· Normaal: met een gemiddelde systeembelasting
· Lager: met een lage systeembelasting.
· Laagst: met een zo laag mogelijk systeembelasting.
· Indien inactief: de taak wordt alleen uitgevoerd wanneer het systeem inactief is.
7.1.8.6 Verwisselbare media
ESET Mail Security biedt automatisch scannen van verwisselbare media (cd/dvd/USB). Met deze module kunt u
geplaatste media scannen. Dit kan handig zijn als de Administrator van de computer wil voorkomen dat gebruikers
verwijderbare media met ongewenste inhoud op de computer gebruiken.
Uit te voeren actie na plaatsen van verwisselbare media
Selecteer welke actie moet worden uitgevoerd als er een verwisselbaar medium in de computer wordt
geplaatst (cd/dvd/USB).
· Niet scannen: er wordt geen actie uitgevoerd en het venster Nieuw apparaat gedetecteerd wordt gesloten.
· Automatisch apparaat scannen: hiermee wordt een computerscan op aanvraag uitgevoerd op het ingevoerde
verwisselbare media-apparaat.
· Scanopties weergeven: hiermee opent u het gedeelte met instellingen voor verwisselbare media.
Als er een verwisselbaar medium wordt geplaatst, wordt het volgende dialoogvenster weergegeven:
· Nu scannen: hiermee wordt een scan van het verwisselbare medium geactiveerd.
· Later scannen: het scannen van het verwisselbare medium wordt uitgesteld.
· Instellingen: hiermee wordt Geavanceerde instellingen geopend.
· Altijd de geselecteerde optie gebruiken: als deze optie wordt geselecteerd, wordt dezelfde actie uitgevoerd
als er de volgende keer een verwisselbaar medium wordt geplaatst.
Daarnaast biedt ESET Mail Security de functie Apparaatbeheer. Hiermee kunt u regels definiëren voor het gebruik
van externe apparaten op een bepaalde computer. Meer informatie over Apparaatbeheer vindt u in het gedeelte
Apparaatbeheer.
7.1.8.7 Documentbescherming
Deze bescherming houdt in dat documenten van Microsoft Office worden gescand voordat ze worden geopend,
evenals bestanden die automatisch worden gedownload door Internet Explorer, zoals Microsoft ActiveX-
elementen. Documentsbescherming biedt extra bescherming boven op Real-timebeveiliging van bestandssysteem
en kan worden uitgeschakeld voor betere prestaties op systemen die niet worden blootgesteld aan grote aantallen
Microsoft Office-documenten.
Integreren in systeem
Met deze optie verbetert u de beveiliging van Microsoft Office-documenten (niet vereist onder normale
omstandigheden).
ThreatSense-parameters

184
Parameters voor Documentsbescherming wijzigen.
OPMERKING
Deze functionaliteit wordt geactiveerd door toepassingen die gebruikmaken van Microsoft Antivirus API
(bijvoorbeeld Microsoft Office 2000 en hoger of Microsoft Internet Explorer 5.0 en hoger).
7.1.9 Hyper-V-scan
De huidige versie van Hyper-V-scan ondersteunt het scannen van online en offline virtuele systemen in Hyper-V.
Ondersteunde scantypen op het gehoste Windows Hyper-V-systeem en de status van het virtuele systeem staan
hieronder:
Virtuele
systemen met
Hyper-V-functie
Windows Server
2008 R2 SP1
Hyper-V
Windows Server
2012 Hyper-V
Windows Server
2012 R2 Hyper-V
Windows Server
2016 Hyper-V
Windows Server
2019 Hyper-V
online-VM
geen scans
alleen-lezen
alleen-lezen
alleen-lezen
alleen-lezen
offline-VM
alleen-lezen/
opschonen
alleen-lezen/
opschonen
alleen-lezen/
opschonen
alleen-lezen/
opschonen
alleen-lezen/
opschonen
Hardwarevereisten
De server mag geen prestatieproblemen hebben wanneer deze virtuele machines uitvoert. Voor scanactiviteiten
worden hoofdzakelijk bronnen van de CPU gebruikt. Als u online VM's wilt scannen, is er vrije schijfruimte nodig. De
schijfruimte moet minimaal het dubbele zijn van de ruimte die door controlepunten/momentopnamen en virtuele
schijven wordt gebruikt.
Specifieke beperkingen
· Scannen op RAID-opslag, spanned volumes en dynamische schijven wordt niet ondersteund vanwege de
aard van dynamische schijven. Daarom raden wij aan dynamische schijven in uw virtuele machines indien
mogelijk te vermijden.
· Scannen wordt altijd uitgevoerd op de huidige virtuele machine en is niet van invloed op controlepunten of
momentopnamen.
· Hyper-V die op een host in een cluster wordt uitgevoerd, wordt momenteel niet ondersteund door ESET Mail
Security.
· Virtuele machines op een Hyper-V-host die wordt uitgevoerd op Windows Server 2008 R2 SP1 kunnen alleen
in de modus Alleen-lezen worden gescand (Niet opschonen), ongeacht het opschoningsniveau dat is
gese le cte erd i n ThreatSense-parameters.
OPMERKING
Hoewel MBR's van virtuele schijven kunnen worden gescand met ESET Security, zijn alleen-lezen scans de
enige ondersteunde methode voor deze doelen. Deze instelling kan worden gewijzigd in Geavanceerde
instellingen (F5) > Computer > Hyper-V-scan > ThreatSense-parameters > Opstartsectoren.
De te scannen virtuele machine is offline - de status is Uit
ESET Mail Security gebruikt Hyper-V-beheer om virtuele schijven van virtuele machines te detecteren en er
verbinding mee te maken. Op deze manier heeft ESET Mail Security dezelfde toegang tot de inhoud van de virtuele
schijven als wanneer toegang wordt gezocht tot gegevens en bestanden op elk algemeen station.
De te scannen virtuele machine is online: de status is Actief, Onderbroken, Opgeslagen

185
ESET Mail Security gebruikt Hyper-V-beheer om virtuele schijven te detecteren. Een echte verbinding met deze
schijven is niet mogelijk. Daarom maakt ESET Mail Security een controlepunt/momentopname van de virtuele
machine en wordt vervolgens verbinding met het controlepunt of de momentopname gemaakt. Nadat de scan is
voltooid, wordt het controlepunt of de momentopname verwijderd. Dit betekent dat er een alleen-lezen scan kan
worden uitgevoerd omdat de scanactiviteit geen gevolgen heeft voor de actieve virtuele machine(s).
Laat ESET Mail Security in één minuut een momentopname of controlepunt maken tijdens het scannen. U dient hier
rekening mee te houden als u een Hyper-V-scan op een groot aantal virtuele machines uitvoert.
Naamgevingsconventie
De module van Hyper-V-scan gebruikt volgende naamgevingsconventie:
VirtualMachineName\DiskX\VolumeY
Waarbij X het aantal schijven en Y het aantal volumes is. Een voorbeeld:
Computer\Disk0\Volume1
Het nummerachtervoegsel wordt toegevoegd op basis van de volgorde van detectie en is gelijk aan de volgorde die
in Schijfbeheer van de virtuele machine wordt weergegeven. Deze naamgevingsconventie wordt gebruikt in de lijst
met te scannen doelen, op de voortgangsbalk en ook in de logbestanden.
Een scan uitvoeren
· Op aanvraag: klik op Hyper-V-scan om een lijst met virtuele machines en volumes weer te geven die kunnen
worden gescand. Selecteer de virtuele machine(s), schijf/schijven of volume(s) die u wilt scannen en klik op
Scannen.
· Een geplande taak maken.
· Via ESET Security Management Center als clienttaak met de naam Serverscan .
· Hyper-V-scan kan worden beheerd en gestart via eShell.
Het is mogelijk meerdere Hyper-V-scans tegelijk uit te voeren. U krijgt een mededeling met een koppeling naar
logbestanden wanneer een scan is voltooid.
Mogelijke problemen
· Wanneer de scan wordt uitgevoerd op een online virtuele machine, moet er een controlepunt/
momentopname worden gemaakt van de desbetreffende virtuele machine en tijdens het maken van een
controlepunt/momentopname zijn bepaalde algemene acties van de virtuele machine mogelijk beperkt of
uitgeschakeld.
· Als een offline virtuele machine wordt gescand, kan deze niet worden ingeschakeld tot de scan is voltooid.
· In Hyper-V-beheer kunt u twee verschillende virtuele machines dezelfde naam geven, maar dit veroorzaakt
een probleem als u bij het bekijken van de scanlogbestanden onderscheid wilt maken tussen de machines.
7.1.10 HIPS
Host-based Intrusion Prevention System (HIPS) beschermt uw systeem tegen malware of andere ongewenste
activiteiten die als enig doel hebben de beveiliging van uw computer te omzeilen. HIPS koppelt geavanceerde
gedragsanalyse aan de detectiemogelijkheden van het netwerkfilter om actieve processen, bestanden en
registersleutels te controleren. HIPS werkt afzonderlijk van Real-timebeveiliging van bestandssysteem en is geen
firewall. Hiermee worden alleen processen gecontroleerd die in het besturingssysteem worden uitgevoerd.
WAARSCHUWING
Wijzigingen in de HIPS-instellingen mogen alleen worden aangebracht door ervaren gebruikers. Onjuiste
configuratie van HIPS-instellingen kan leiden tot systeeminstabiliteit.

186
Zelfverdediging activeren
ESET Mail Security is voorzien van geïntegreerde zelfverdedigingstechnologie, waarmee wordt verhinderd dat
schadelijke software uw antivirus- en antispywarebeveiliging beschadigt of uitschakelt, zodat uw systeem
gegarandeerd altijd beveiligd is. Wijzigingen aan de instellingen van HIPS inschakelen en Zelfverdediging
activeren worden pas doorgevoerd als het Windows-besturingssysteem opnieuw wordt gestart. Als het gehele
HIPS-systeem wordt uitgeschakeld, moet een computer ook opnieuw worden opgestart.
Beveiligingsservice inschakelen
Microsoft heeft in Windows Server 2012 R2 het concept van beveiligde services geïntroduceerd. Hiermee wordt
voorkomen dat een service bij een malwareaanval wordt uitgevoerd. De kernel van ESET Mail Security wordt
standaard als beveiligde service uitgevoerd. Deze functie is beschikbaar in Microsoft Windows Server 2012 R2
en latere serverbesturingssystemen.
Geavanceerde geheugenscanner inschakelen
Werkt in combinatie met Exploit blocker voor een betere bescherming tegen malware die is ontworpen om
detectie te omzeilen door middel van verhulling of codering. Geavanceerde geheugenscanner is standaard
ingeschakeld. Raadpleeg de woordenlijst voor meer informatie over dit type beveiliging.
Exploit Blocker inschakelen
Is ontworpen om de beveiliging te versterken van vaak bedreigde toepassingen, zoals webbrowsers, PDF-
lezers, e-mailclients en MS Office-onderdelen. Exploit blocker is standaard ingeschakeld. Raadpleeg de
woordenlijst voor meer informatie over dit type beveiliging.
Ransomwareschild inschakelen
Schakel HIPS en ESET Live Grid in als u deze functionaliteit wilt gebruiken. Meer informatie over ransomware
vindt u in de woordenlijst .
Filtermodus
U kunt een van de volgende filteringmodi kiezen:
· Automatische modus: bewerkingen worden ingeschakeld, met uitzondering van vooraf gedefinieerde regels
die uw systeem beveiligen. Alles is toegestaan behalve acties die door een regel worden geweigerd.
· Smart-modus: de gebruiker ontvangt alleen een melding over uiterst verdachte gebeurtenissen.
· Interactieve modus: de gebruiker wordt gevraagd bewerkingen te bevestigen. Toegang toestaan/weigeren,
Regel maken en Tijdelijk onthouden deze actie.
· Op beleid gebaseerde modus: bewerkingen worden geblokkeerd. Accepteert alleen door gebruikers/vooraf
gedefinieerde regels.
· Leermodus: bewerkingen worden ingeschakeld en er wordt na elke bewerking een regel gemaakt. Regels die
in deze modus zijn gemaakt, kunnen worden bekeken in de Regeleditor, maar hun prioriteit is lager dan de
prioriteit van de regels die handmatig zijn gemaakt of regels die zijn gemaakt in de automatische modus. Als
u Leermodus selecteert in het vervolgkeuzemenu van de HIPS-filtermodus, wordt de instelling Leermodus
eindigt om beschikbaar gemaakt. Selecteer hoe lang u de leermodus actief wilt hebben. De maximumduur is
14 dagen. Wanneer de opgegeven duur is verstreken, wordt u gevraagd de regels te bewerken die door HIPS
zijn gemaakt terwijl deze zich in de leermodus bevond. Ook kunt u een andere filtermodus kiezen, of de
beslissing uitstellen en doorgaan met de leermodus.
Regels
Regels bepalen welke toepassingen toegang tot welke bestanden, onderdelen van het register of andere
toepassingen krijgen. Het HIPS-systeem controleert gebeurtenissen in het besturingssysteem en reageert
dienovereenkomstig op basis van regels die zijn te vergelijken met regels die door de persoonlijke firewall
worden gebruikt. Klik op Bewerken om het venster HIPS-regelbeheer te openen. Als de standaardactie voor
een regel is ingesteld op Vragen, wordt er een dialoogvenster weergegeven elke keer wanneer de regel wordt
geactiveerd. U kunt kiezen uit Blokkeren en Toestaan. Als u in de opgegeven tijd geen actie kiest, wordt er een
nieuwe actie op basis van de regels geselecteerd.

187
In het dialoogvenster kunt u regels maken op basis van nieuwe door HIPS gedetecteerde acties en vervolgens de
voorwaarden definiëren waaronder die acties worden toegestaan of geblokkeerd. Klik op Details voor meer
informatie. Regels die op deze manier zijn gemaakt, zijn gelijkwaardig aan de regels die handmatig zijn gemaakt.
Hierdoor kan een regel die in een dialoogvenster is gemaakt, minder specifiek kan zijn dan de regel waardoor het
dialoogvenster is geactiveerd. Dit betekent dat wanneer een dergelijke regel is gemaakt, dezelfde bewerking
hetzelfde venster kan activeren.
Elke keer opnieuw vragen
Er wordt een dialoogvenster weergegeven elke keer wanneer de regel wordt geactiveerd. U kunt kiezen uit
Weigeren en Toestaan.
Onthouden tot toepassing wordt gesloten
Als u de actie Weigeren of Toestaan kiest, wordt er een tijdelijke HIPS-regel gemaakt tot de desbetreffende
toepassing wordt gesloten. Als u de filtermodus wijzigt, regels wijzigt, of de HIPS-module wordt bijgewerkt en
u het systeem opnieuw start, worden de tijdelijke regels ook verwijderd.
Regel maken en permanent onthouden
Maak een nieuwe HIPS-regel. U kunt deze regel later wijzigen in het gedeelte Beheer van HIPS-regels.

188
7.1.10.1 HIPS-regelinstellingen
In dit venster vindt u een overzicht van bestaande HIPS-regels.
Regel
Door de gebruiker gedefinieerde of automatisch gekozen regelnaam.
Ingeschakel
d
Schakel deze schakelaar uit als u de regel in de lijst wilt behouden maar deze niet wilt gebruiken.
Actie
De regel geeft een actie aan, namelijk Toestaan, Blokkeren of Vragen, die moet worden uitgevoerd
als aan de voorwaarden wordt voldaan.
Bronnen
De regel wordt alleen gebruikt als de gebeurtenis door een of meer toepassingen wordt/worden
geactiveerd.
Doelen
De regel wordt alleen gebruikt als de bewerking verband houdt met een bepaald bestand, een
bepaalde toepassing of een bepaalde registervermelding.
Ernst van
logboekregi
stratie
Als u deze optie activeert, wordt informatie over deze regel naar het HIPS-logboek geschreven.
Melden
Er wordt rechtsonder een klein pop-upvenster weergegeven als er een gebeurtenis wordt
geactiveerd.
Maak een nieuwe regel, klik op Toevoegen om een nieuwe HIPS-regel toe te voegen of op Bewerken om
geselecteerde vermeldingen te bewerken.
Regelnaam
Door de gebruiker gedefinieerde of automatisch gekozen regelnaam.
Actie
De regel geeft een actie aan, namelijk Toestaan, Blokkeren of Vragen, die moet worden uitgevoerd als aan de
voorwaarden wordt voldaan.
Bewerkingen die gevolgen hebben voor
U dient het type bewerking op te geven waarvoor de regel wordt toegepast. De regel wordt alleen voor dit type
bewerking en voor het geselecteerde doel gebruikt. De regel bestaat uit onderdelen die de voorwaarden
beschrijven die deze regel activeren.
Brontoepassingen
De regel wordt alleen gebruikt als de gebeurtenis door deze toepassing(en) wordt geactiveerd. Selecteer
Bepaalde toepassingen in het vervolgkeuzemenu en klik op Toevoegen om nieuwe bestanden of mappen toe
te voegen of selecteer Alle toepassingen in het vervolgkeuzemenu om alle toepassingen toe te voegen.
OPMERKING
Sommige bewerkingen van bepaalde regels die vooraf zijn gedefinieerd door HIPS kunnen niet worden
geblokkeerd en worden standaard toegestaan. Bovendien worden niet alle systeembewerkingen door HIPS
gecontroleerd. HIPS controleert bewerkingen die als onveilig worden beschouwd.
Beschrijving van belangrijke bewerkingen:
Bestandsbewerkingen:

189
Bestand
verwijderen
De toepassing vraagt om toestemming om het doelbestand te verwijderen.
Schrijven naar
bestand
De toepassing vraagt om toestemming om te schrijven in het doelbestand.
Rechtstreeks
toegang tot schijf
De toepassing probeert te lezen van of te schrijven naar de schijf op een manier die niet
standaard is en waarmee de gebruikelijke Windows-procedures worden omzeild. Dit kan
resulteren in bestanden die worden gewijzigd zonder toepassing van de overeenkomende
regels. Deze bewerking kan worden veroorzaakt door malware die detectie probeert te
omzeilen, back-upsoftware die een exacte kopie van een schijf probeert te maken of een
partitiebeheerprogramma dat schijfvolumes probeert te reorganiseren.
Algemene hook
installeren
Verwijst naar het aanroepen van de functie SetWindowsHookEx van de MSDN-bibliotheek.
Stuurprogramma
laden
Installatie en laden van stuurprogramma's in het systeem.
De regel wordt alleen gebruikt als de bewerking betrekking heeft op dit doel. Selecteer Bepaalde bestanden in het
vervolgkeuzemenu en klik op Toevoegen om nieuwe bestanden of mappen toe te voegen. U kunt ook Alle
bestanden in het vervolgkeuzemenu selecteren om alle toepassingen toe te voegen.
Toepassingsbewerkingen:
Een andere toepassing
debuggen
Hiermee kunt u een foutopsporingsprogramma aan het proces koppelen. Terwijl
fouten worden opgespoord in een toepassing, kunt u veel details van het gedrag
weergeven en wijzigen, en kunt u gegevens openen.
Gebeurtenissen van een
andere toepassing
onderscheppen
De brontoepassing probeert gebeurtenissen te detecteren die zijn gericht op een
bepaalde toepassing (bijvoorbeeld een keylogger die browsergebeurtenissen
probeert te detecteren).
Een andere toepassing
afsluiten/onderbreken
Stelt een proces uit of hervat of beëindigt een proces (deze optie is direct
toegankelijk vanuit de procesverkenner of het venster Processen).
Nieuwe toepassing starten
Starten van nieuwe toepassingen of processen.
Status van een andere
toe passing wi jzi gen
De brontoepassing probeert te schrijven naar het geheugen van de doeltoepassing
of probeert code namens de toepassing uit te voeren. Deze functie kan handig zijn
om een essentiële toepassing te beschermen door deze als doeltoepassing te
configureren in een regel waarmee het gebruik van deze bewerking wordt
geblokkeerd.
De regel wordt alleen gebruikt als de bewerking betrekking heeft op dit doel. Selecteer Bepaalde toepassingen in
het vervolgkeuzemenu en klik op Toevoegen om nieuwe bestanden of mappen toe te voegen. U kunt ook Alle
toepassingen in het vervolgkeuzemenu selecteren om alle toepassingen toe te voegen.
Registerbewerkingen:

190
Opstartinstelling
en wijzigen
Wijzigingen in instellingen die bepalen welke toepassingen worden uitgevoerd tijdens het
opstarten van Windows. Deze vindt u bijvoorbeeld door te zoeken naar de sleutel Run in het
Windows-register.
Uit register
verwijderen
Hiermee kunt u een registersleutel of de waarde ervan verwijderen.
Naam van
registersleutel
bewerken
Hiermee kunt u namen van registersleutels wijzigen
Register wijzigen
Nieuwe waarden van registersleutels maken, bestaande waarden wijzigen, gegevens
verplaatsen in de databasestructuur of gebruikers- of groepsrechten instellen voor
registersleutels.
De regel wordt alleen gebruikt als de bewerking betrekking heeft op dit doel. Selecteer Bepaalde vermeldingen uit
het vervolgkeuzemenu en klik op Toevoegen om nieuwe bestanden of mappen toe te voegen. U kunt ook Alle
vermeldingen in het vervolgkeuzemenu selecteren om alle toepassingen toe te voegen.
OPMERKING
U kunt met bepaalde beperkingen gebruikmaken van jokertekens wanneer u een doel invoert. In plaats van
een specifieke sleutel kan het symbool * (asterisk) worden gebruikt in registerpaden, bijvoorbeeld
HKEY_USERS\*\software can mean HKEY_USER\.default\software, maar niet HKEY_USERS\S-1-2-21-2928335913-
73762274-491795397-7895\.default\software. HKEY_LOCAL_MACHINE\system\ControlSet* is geen geldig
registersleutelpad. Een registersleutelpad dat \* bevat, definieert 'dit pad of elk ander pad op elk niveau na
dat symbool'. Dit is de enige manier waarop jokertekens voor bestandsdoelen worden gebruikt. Eerst wordt
het specifieke onderdeel van een pad geëvalueerd en vervolgens het pad na het jokerteken (*).
WAARSCHUWING
Mogelijk ontvangt u een melding als u een te algemene regel maakt.
7.1.10.2 Geavanceerde HIPS-instellingen
De volgende opties zijn handig voor het analyseren van de werking van een toepassing en om eventuele fouten op
te lossen:
Stuurprogramma's die altijd mogen worden geladen
Geselecteerde stuurprogramma's mogen altijd worden geladen, ongeacht de geconfigureerde filtermodus,
tenzij deze expliciet worden geblokkeerd door een gebruikersregel. De stuurprogramma's in deze lijst mogen
altijd worden geladen, ongeacht de HIPS-filtermodus, tenzij ze door een specifieke gebruikersregel worden
geblokkeerd. U kunt een nieuw stuurprogramma Toevoegen, Bewerken of Verwijderen uit de lijst.
OPMERKING
Kl ik op Opnieuw instellen als u stuurprogramma's wilt uitsluiten die u handmatig hebt toegevoegd. Dit kan
handig zijn als u diverse stuurprogramma's hebt toegevoegd en deze niet handmatig kunt verwijderen uit de
lijst.
Alle geblokkeerde bewerkingen in logboek opnemen
Alle geblokkeerde bewerkingen worden in het HIPS-logboek geschreven.
Melding weergeven bij wijzigingen in opstarttoepassingen

191
Geeft een melding weer op het bureaublad wanneer een toepassing wordt toegevoegd aan of verwijderd uit
de lijst met opstartbestanden.
7.2 Updateconfiguratie
In dit gedeelte wordt informatie gegeven over de bron van de update, zoals de updateservers die worden gebruikt
en verificatiegegevens voor deze servers.
OPMERKING
Het is belangrijk alle updateparameters correct in te vullen, zodat updates correct worden gedownload. Als u
een firewall gebruikt, dient u te controleren of uw ESET-programma met internet mag communiceren
(bijvoorbeeld HTTP-communicatie).
Basis
Selecteer standaardprofiel voor bijwerken
Kies een bestaand profiel of maak een nieuw profiel dat standaard moet worden toegepast voor updates.
Update-cache wissen
Als u problemen ondervindt met een update, klikt u op Wissen om de tijdelijke cache met updatebestanden
leeg te maken.
Maximumleeftijd voor detectie-engine automatisch instellen/Maximumleeftijd voor detectie-engine (dagen)
Hier kunt u het maximum aantal dagen instellen waarna de detectie-engine als verouderd wordt aangemerkt.
De standaardwaarde is 7.
Module terugdraaien
Als u vermoedt dat een nieuwe update van de detectie-engine en/of programmamodules instabiel of
beschadigd is, kunt u de vorige versie herstellen en alle updates voor een bepaalde periode uitschakelen. U
kunt ook eerder uitgeschakelde updates inschakelen als u ze voor onbepaalde tijd hebt uitgesteld. ESET Mail
Security maakt momentopnamen van de detectie-engine en programmamodules om deze met de functie
Terugdraaien te gebruiken. Laat Momentopnamen van updatebestanden maken ingeschakeld als u
momentopnamen van de detectie-engine wilt maken.
Aantal lokaal opgeslagen momentopnamen
Bepaalt het aantal eerdere momentopnamen van de module dat wordt opgeslagen.
Profielen
Als u een aangepast updateprofiel wilt maken, selecteert u Bewerken naast Lijst met profielen, geeft u uw eigen
Profielnaam op en klikt u op Toevoegen. Selecteer het te bewerken profiel en pas de parameters voor de typen
module-updates aan of maak een Mirror voor updates.
Updates
Selecteer het te gebruiken updatetype in het vervolgkeuzemenu:
· Reguliere update: standaard is Updatetype ingesteld op Reguliere update om ervoor te zorgen dat
updatebestanden automatisch worden gedownload bij de ESET-server met het minste netwerkverkeer.
· Bèta-update: dit zijn updates die intern grondig zijn getest en naar verwachting binnenkort voor iedereen
beschikbaar zijn. U kunt profijt hebben van bèta-updates, omdat u dan toegang hebt tot de recentste
detectiemethoden en oplossingen. Het is echter mogelijk dat bèta-updates nog niet altijd stabiel genoeg zijn.

192
Gebruik ze daarom NIET op productieservers en werkstations die een maximale beschikbaarheid en stabiliteit
moeten bieden.
· Uitgestelde update: hiermee worden alleen updates uitgevoerd vanaf speciale updateservers die nieuwe
versies van virusdatabases bieden met een vertraging van minstens X uur (d.w.z. databases zijn getest in een
echte omgeving en worden daarom als stabiel beschouwd).
Vragen alvorens update te downloaden
Wanneer er een nieuwe update beschikbaar is, wordt u gevraagd of u deze wilt downloaden.
Vragen of een updatebestand groter is dan (kB)
Als het updatebestand groter is dan de waarde die is opgegeven in het veld, wordt er een melding
weergegeven.
Melding over succesvolle update uitschakelen
Schakelt de systeemvakmelding uit rechtsonder in het scherm. Het is handig deze optie in te schakelen als u
een toepassing in de modus Volledig scherm uitvoert. In de Presentatiemodus zijn alle meldingen
uitgeschakeld.
Module-updates
Module-updates zijn standaard ingesteld op Automatisch kiezen. De updateserver is de locatie waar updates
worden opgeslagen. Als u een ESET-server gebruikt, raden we aan de standaardoptie geselecteerd te laten.
Bij gebruik van een lokale HTTP-server (ofwel de mirrorserver) moet de updateserver als volgt worden ingesteld:
http://computernaam_of_IP_adres:2221
Bij gebruik van een lokale HTTP-server met SSL moet de updateserver als volgt worden ingesteld:
https://computernaam_of_IP_adres:2221
Bij gebruik van een lokale gedeelde map moet de updateserver als volgt worden ingesteld:
\\computernaam_of_het_IP-adres_ervan\gedeelde_map
Vaker updates voor detectiekenmerken inschakelen
Detectie-engine wordt bijgewerkt in kortere intervallen. Als u deze optie uitschakelt, kan het
detectiepercentage afnemen.
Module-updates van verwisselbaar medium toestaan
Hiermee kunt u de software bijwerken vanaf een verwisselbaar medium als zich daarop een exacte kopie
be vi ndt. Al s Automatisch is geselecteerd, wordt het bijwerken op de achtergrond uitgevoerd. Selecteer Altijd
vragen als u updatedialoogvensters weergegeven wilt hebben.
Bijwerken van programmaonderdelen
Gebruik het vervolgkeuzemenu Updatemodus om te kiezen hoe ESET Mail Security-onderdeelupdates worden
toegepast wanneer er een nieuwe update beschikbaar is. Onderdeelupdates passen doorgaans bestaande
functies aan, maar kunnen ook nieuwe functies toevoegen. Afhankelijk van de gekozen updatemodus, kan de
onderdeelupdate automatisch worden uitgevoerd zonder interventie of bevestiging. Of u kunt ervoor kiezen
om een melding te ontvangen voordat de updates worden geïnstalleerd. Mogelijk moet de server opnieuw
worden opgestart na de onderdeelupdate. De volgende updatemodi zijn beschikbaar:
· Vragen alvorens bij te werken: u wordt gevraagd productupdates te bevestigen of te weigeren. Dit is de
standaardoptie. Mogelijk moet de server opnieuw worden opgestart na de onderdeelupdate.
· Automatisch bijwerken: onderdeelupdates worden automatisch gedownload en geïnstalleerd. Wij raden
deze optie niet aan, omdat ESET Mail Security uw server opnieuw opstart na de onderdeelupdate.

193
· Nooit bijwerken: er worden in het geheel geen onderdeelupdates uitgevoerd. Wij raden deze optie aan,
omdat u hiermee de onderdeelupdates handmatig kunt uitvoeren en uw server gedurende een periode van
gepland onderhoud opnieuw kunt opstarten.
BELANGRIJK
Met de modus Automatisch bijwerken wordt uw server automatisch opnieuw opgestart nadat de
onderdeelupdate is voltooid.
Verbindingsopties
Proxyserver
U krijgt als volgt toegang tot de proxyserverinstellingen voor een gegeven updateprofiel. Klik op Proxymodus
en selecteer een van de volgende drie opties:
· Geen proxyserver gebruiken: er wordt geen proxyserver gebruikt door ESET Mail Security tijdens het
uitvoeren van updates.
· Algemene instellingen voor proxyserver gebruiken: de proxyserverconfiguratie die is opgegeven in
Geavanceerde instellingen (F5)> Hulpmiddelen > Proxyserver wordt gebruikt.
· Verbinding maken via een proxyserver: gebruik deze optie in de volgende situaties:
Er moet een proxyserver worden gebruikt om ESET Mail Security bij te werken en deze verschilt van de proxyserver
die is opgegeven in de algemene instellingen (Hulpmiddelen > Proxyserver). Als dat het geval is, moeten de
instellingen hier worden opgegeven: proxyserveradres, communicatiepoort (standaard 3128), plus gebruikersnaam
en wachtwoord voor de proxyserver indien vereist.
De proxyserverinstellingen zijn niet algemeen ingesteld, maar ESET Mail Security maakt verbinding met een
proxyserver voor updates.
Uw computer maakt via een proxyserver verbinding met internet. De instellingen worden tijdens de installatie van
het programma overgenomen uit Internet Explorer, maar als deze vervolgens worden gewijzigd (bijvoorbeeld als u
verandert van internetprovider), moet u controleren of de HTTP-proxyinstellingen in dit venster correct zijn. Als dit
niet het geval is, kan het programma geen verbinding met de updateservers maken.
OPMERKING
Ve ri fi catie gege ve ns zoals Gebruikersnaam en Wachtwoord zijn bedoeld om toegang te krijgen tot de
proxyserver. Vul deze velden alleen in als een gebruikersnaam en wachtwoord vereist zijn. Deze velden zijn
niet bestemd voor uw gebruikersnaam/wachtwoord voor ESET Mail Security en moeten alleen worden
ingevuld als u weet dat u een wachtwoord nodig hebt om via een proxyserver verbinding te maken met
internet.
Gebruik een directe verbinding wanneer de proxy server niet beschikbaar is
Als een product is geconfigureerd om HTTP-proxy te gebruiken en de proxy is onbereikbaar, omzeilt het
product de proxy en wordt er rechtstreeks met ESET-servers gecommuniceerd.
Windows-shares
Bij het bijwerken vanaf een lokale server waarop Windows is geïnstalleerd, is standaard voor elke
netwerkverbinding verificatie vereist.
Verbinding maken met LAN als
Kies een van de volgende opties om uw account te configureren:

194
· Systeemaccount (standaard): gebruik het systeemaccount voor verificatie. Doorgaans vindt geen
verificatieproces plaats als er geen verificatiegegevens beschikbaar worden gesteld in het hoofdgedeelte van
de update-instellingen.
· Huidige gebruiker: selecteer deze optie om ervoor te zorgen dat het programma verificatie uitvoert via het
momenteel aangemelde gebruikersaccount. Het nadeel van deze oplossing is dat het programma geen
verbinding kan maken met de updateserver als er geen gebruiker is aangemeld.
· Opgegeven gebruiker: selecteer deze optie om een opgegeven gebruikersaccount voor verificatie te
gebruiken. Gebruik deze methode wanneer geen verbinding kan worden gemaakt via het
standaardsysteemaccount. Het opgegeven gebruikersaccount moet toegang hebben tot de map met
updatebestanden op de lokale server. Als de gebruiker geen toegang heeft, is het onmogelijk een verbinding
tot stand te brengen of updates te downloaden.
WAARSCHUWING
Als de optie Hui dige gebruiker of Opgegeven gebruiker is ingeschakeld, kan er een fout optreden bij het
wijzigen van de identiteit van het programma naar de gewenste gebruiker. We adviseren om de LAN-
verificatiegegevens op te nemen in het hoofdgedeelte van de update-instellingen. In dit gedeelte van de
update-instellingen moeten de verificatiegegevens als volgt worden ingevoerd: domain_name\user (als het
een werkgroep betreft, voert u workgroup_name\name in) en het wachtwoord. Bij het bijwerken vanaf de
HTTP-versie van de lokale server, is geen verificatie vereist.
Verbinding met server verbreken na bijwerken
Het verbreken van de verbinding forceren als de verbinding met de server zelfs na het downloaden van de
updates actief blijft.
Updatemirror
Configuratieopties voor de lokale mirrorserver bevinden zich in de structuur Geavanceerde instellingen (F5) op het
tabblad Bijwerken > Profielen > Mirror voor updates.
7.2.1 Ongedaan maken van updates
Als u klikt op Terugdraaien moet u een tijdsinterval selecteren in het vervolgkeuzemenu dat aangeeft hoe lang
updates van de detectie-engine en van programmamodules worden onderbroken.
Selecteer Tot ingetrokken om regelmatige updates voor onbepaalde tijd uit te stellen tot u de updatefunctie
handmatig herstelt. Aangezien dit een potentieel beveiligingsrisico met zich meebrengt, wordt afgeraden om deze
optie te selecteren.
De versie van de detectie-engine wordt teruggezet naar de oudste versie die beschikbaar is en wordt in het
bestandssysteem van de lokale computer bewaard als momentopname.
7.2.2 Geplande taak - Bijwerken
Als u het programma wilt bijwerken vanaf twee updateservers, moet u twee verschillende updateprofielen maken.
Als het downloaden van updatebestanden mislukt met de eerste server, schakelt het programma automatisch over
naar de alternatieve server. Dit is bijvoorbeeld handig voor gebruikers van een notebook, die normaal gesproken
updates uitvoeren vanaf een updateserver in het lokale netwerk, maar die ook vaak vanuit een ander netwerk
verbinding maken met internet. Dus als het eerste profiel niet werkt, wordt automatisch het tweede profiel
gebruikt om updatebestanden te downloaden bij de updateservers van ESET.
VOORBEELD

195
De onderstaande stappen begeleiden u bij de taak om een bestaande Regelmatige automatisch update te
bewerken.
1. Selecteer in het scherm Planner de taak Bijwerken met de naam Regelmatig automatisch bijwerken en klik
op Bewerken om de configuratiewizard te openen.
2. Stel de taak van de planner in op uitvoeren en selecteer een van de volgende tijdopties om op te geven
wanneer u een Geplande taak wilt uitvoeren.
3. Als u wilt voorkomen dat de taak wordt uitgevoerd wanneer het systeem op batterijvoeding werkt
(bijvoorbeeld een noodstroomvoorziening (UPS)), klik dan op de schakelaar naast Taak overslaan indien op
batterijvoeding.
4. Selecteer profiel bijwerken om het profiel bij te werken. Selecteer een actie die moet worden uitgevoerd
als de uitvoering van de geplande taak om welke reden dan ook mislukt.
5. Kl ik op Voltooien om de taak toe te passen.
7.2.3 Updatemirror
ESET Mail Security Openen
Druk op F5 > Bijwerken > Profielen > Mirror voor updates
Met ESET Mail Security kunt u kopieën maken van updatebestanden die kunnen worden gebruikt om andere
werkstations in het netwerk bij te werken. Het gebruik van een "mirror" - een kopie van de updatebestanden in de
LAN-omgeving - is handig omdat de updatebestanden dan niet herhaaldelijk door elk werkstation hoeven te
worden gedownload bij de updateserver van de leverancier. Updates worden gedownload naar de lokale
mirrorserver en vervolgens naar alle werkstations gedistribueerd, waardoor overbelasting van het netwerk wordt
voorkomen. Als clientwerkstations worden bijgewerkt op basis van een mirror, wordt de netwerkbelasting
gelijkmatig verdeeld en wordt bandbreedte voor uw internetverbinding bespaard.
Updatemirror
Mirror voor updates maken
Activeert opties voor mirrorconfiguraties.
Opslagmap
Kl ik op Wissen als u een gedefinieerde standaardmap wilt wijzigen om mirrorbestanden op te slaan C:
\ProgramData\ESET\ESET Security\mirror. Kl ik op Bewerken om naar een map op de lokale computer of een
gedeelde netwerkmap te bladeren. Als verificatie voor de opgegeven map is vereist, moeten
verificatiegegevens worden opgegeven in de velden Gebruikersnaam en Wachtwoord. Als de geselecteerde
doelmap zich bevindt op een netwerkschijf waarop het besturingssysteem Windows NT/2000/XP wordt
uitgevoerd, moeten aan de opgegeven gebruikersnaam en het opgegeven wachtwoord schrijfrechten voor de
geselecteerde map zijn toegewezen.
De gebruikersnaam en het wachtwoord moeten worden ingevoerd in de notatie Domain/User of Workgroup/
User. Geef ook de bijbehorende wachtwoorden op.
Bijwerken van programmaonderdelen
Bestanden
Bij het configureren van de mirror, kunt u de taalversies opgeven van de updates die u wilt downloaden. De
geselecteerde talen moeten worden ondersteund door de mirrorserver die door de gebruiker is
geconfigureerd.
Onderdelen automatisch bijwerken

196
Hiermee kunt u nieuwe functies en updates voor bestaande functies installeren. Een update kan automatisch
worden uitgevoerd zonder tussenkomst van de gebruiker, of u kunt ervoor kiezen een melding te ontvangen.
Nadat een update voor een product is geïnstalleerd, moet de computer mogelijk opnieuw worden opgestart.
Onderdelen nu bijwerken
Werkt uw programmaonderdelen bij naar de nieuwste versie.
HTTP-server
Serverpoort
De standaardpoort is ingesteld op 2221. Wijzig deze waarde als u een andere poort gebruikt.
Verificatie
Bepaalt de verificatiemethode die wordt gebruikt bij toegang tot updatebestanden. De volgende opties zijn
beschikbaar: Geen, Basis en NTLM.
· Selecteer Basis om base64-codering met standaardverificatie van gebruikersnaam en wachtwoord te
gebruiken.
· De opti e NTLM biedt codering via een veilige coderingsmethode. Voor verificatie wordt gebruikgemaakt van
de gebruiker die is gemaakt op het werkstation dat de updatebestanden deelt.
· De standaardinstelling is Geen, waarbij toegang tot de updatebestanden wordt geboden zonder dat
verificatie is vereist.
WAARSCHUWING
Als u toegang tot de updatebestanden wilt bieden via de HTTP-server, moet de mirrormap zich op dezelfde
computer bevinden als de instantie van ESET Mail Security die deze map maakt.
SSL voor HTTP-server
Voe g e en Ketenbestandcertificaat, toe (of genereer een certificaat dat zelf is ondertekend) als u de HTTP-
server wilt uitvoeren met ondersteuning voor HTTPS (SSL). De volgende certificaattypen zijn beschikbaar: PEM,
PFX en ASN. Voor extra beveiliging kunt u het HTTPS-protocol gebruiken om updatebestanden te downloaden.
Het is met dit protocol vrijwel onmogelijk om gegevensoverdracht en aanmeldingsgegevens te traceren.
De opti e Type privésleutel is standaard ingesteld op Geïntegreerd (en daarom is de optie Privésleutelbestand
standaard uitgeschakeld). Dit betekent dat de privésleutel onderdeel is van het geselecteerde
certificaatketenbestand.
Verbindingsopties
Windows-shares
Bij het bijwerken vanaf een lokale server waarop Windows is geïnstalleerd, is standaard voor elke
netwerkverbinding verificatie vereist.
Verbinding maken met LAN als
Kies een van de volgende opties om uw account te configureren:
· Systeemaccount (standaard): gebruik het systeemaccount voor verificatie. Doorgaans vindt geen
verificatieproces plaats als er geen verificatiegegevens beschikbaar worden gesteld in het hoofdgedeelte
voor update-instellingen.
· Huidige gebruiker: selecteer deze optie om ervoor te zorgen dat het programma verificatie uitvoert via het
momenteel aangemelde gebruikersaccount. Het nadeel van deze oplossing is dat het programma geen
verbinding kan maken met de updateserver als er geen gebruiker is aangemeld.
· Opgegeven gebruiker: selecteer deze optie om een opgegeven gebruikersaccount voor verificatie te
gebruiken. Gebruik deze methode wanneer geen verbinding kan worden gemaakt via het

197
standaardsysteemaccount. De opgegeven gebruikersaccount moet toegang hebben tot de map met
updatebestanden op de lokale server. Als de gebruiker geen toegang heeft, is het onmogelijk een verbinding
tot stand te brengen en updates te downloaden.
WAARSCHUWING
Als de optie Hui dige gebruiker of Opgegeven gebruiker is ingeschakeld, kan er een fout optreden bij het
wijzigen van de identiteit van het programma naar de gewenste gebruiker. We adviseren om de LAN-
verificatiegegevens op te nemen in het hoofdgedeelte van de update-instellingen. In dit gedeelte van de
update-instellingen moeten de verificatiegegevens als volgt worden ingevoerd: domain_name\user (als het
een werkgroep betreft, voert u workgroup_name\name in) en het wachtwoord. Bij het bijwerken vanaf de
HTTP-versie van de lokale server, is geen verificatie vereist.
Verbinding met server verbreken na bijwerken
Het verbreken van de verbinding forceren als de verbinding met de server zelfs na het downloaden van de
updates actief blijft.
7.3 Netwerkbeveiliging
OPMERKING
Op Windows Server 2008 SP2, Windows Server 2008 R2 SP1, Small Business Server 2008 SP2 en Small Business
Server 2011 is de installatie van het onderdeel Netwerkbeveiliging standaard uitgeschakeld. Als u deze functie
wilt installeren, kiest u het installatietype Aangepast. Als ESET Mail Security al bij u is geïnstalleerd, kunt u het
installatieprogramma nog een keer uitvoeren om uw bestaande installatie te wijzigen en het onderdeel
Netwerkbeveiliging toe te voegen.
Netwerkaanvalbeveiliging (IDS) inschakelen
Hier kunt u de toegang configureren tot bepaalde services die op uw computer worden uitgevoerd vanuit de
Vertrouwde zone, en kunt u detectie inschakelen/uitschakelen van diverse typen aanvallen en exploits die uw
computer mogelijk schade toebrengen.
Botnetbeveiliging inschakelen
Detecteert en blokkeert communicatie met schadelijke opdrachten en controleservers op basis van typische
patronen die erop wijzen dat een computer is geïnfecteerd en dat er een bot is die probeert te communiceren.
IDS-uitzonderingen
U kunt uitzonderingen op Intrusion Detection System (IDS) als netwerkbeveiligingsregels beschouwen. Klik op
Bewerken om IDS-uitzonderingen te definiëren.
Inbreukdetectie:
Protocol SMB: detecteert en blokkeert diverse beveiligingsproblemen met het SMB-protocol
Protocol RPC: detecteert en blokkeert diverse CVE's in het RPC-systeem die zijn ontwikkeld voor de Distributed
Computing Environment (DCE).
Protocol RDP: detecteert en blokkeert diverse CVE's in het RDP-protocol (zie hierboven).
Onveilig adres blokkeren na detectie van aanval: IP-adressen die zijn gedetecteerd als aanvalsbron worden
toegevoegd aan de zwarte lijst om verbindingen gedurende een bepaalde periode te voorkomen.

198
Protocol SMB: detecteert en blokkeert diverse beveiligingsproblemen met het SMB-protocol
Melding weergeven na detectie van aanval: hiermee schakelt u de melding in het systeemvak rechts onder in het
scherm in.
Ook meldingen weergeven bij inkomende aanvallen tegen beveiligingslekken: hiermee wordt u gewaarschuwd als
er aanvallen tegen beveiligingslekken worden gedetecteerd of als een bedreiging een poging onderneemt het
systeem op deze manier binnen te komen.
Controle van pakket:
Inkomende verbinding naar admin-shares toestaan in het SMB-protocol: de admin-shares (beheershares) zijn de
standaardnetwerkshares van gedeelde hardeschijfpartities (C$, D$, ...) in het systeem, samen met de systeemmap
(ADMIN$). Als u de verbinding naar admin-shares uitschakelt, wordt het beveiligingsrisico mogelijk kleiner. De
Conficker-worm bijvoorbeeld voert woordenboekaanvallen uit om verbinding met admin-shares te maken.
Oude (niet-ondersteunde) SMB-dialecten weigeren: SMB-sessies weigeren waarbij een oud SMB-dialect wordt
gebruikt dat niet door IDS wordt ondersteund. Moderne Windows-besturingssystemen bieden ondersteuning voor
oude SMB-dialecten vanwege achterwaartse compatibiliteit met oudere besturingssystemen zoals Windows 95. De
aanvaller kan zo een oud dialect in een SMB-sessie gebruiken om inspectie van het verkeer te omzeilen. Weiger
oude SMB-dialecten (of gebruik SMB-communicatie in zijn algemeen) als uw computer geen bestanden hoeft te
delen met computers waarop een oudere versie van Windows is geïnstalleerd.
SMB-beveiliging zonder beveiligingsextensies weigeren: er kan uitgebreide beveiliging tijdens de onderhandeling
over de SMB-sessie worden gebruikt om een veiliger verificatiemechanisme te kunnen bieden dan verificatie via
LAN Manager Challenge/Response (LM). Het LM-schema wordt over het algemeen als te zwak beoordeeld en is
ongeschikt om te gebruiken.
Communicatie met de Security Account Manager-service toestaan: zi e [MS-SAMR] voor meer informatie over
deze service.
Communicatie met de Local Security Authority-service toestaan: zi e [MS-LSAD] en [MS-LSAT] voor meer
informatie over deze service.
Communicatie met de Remote Registry-service toestaan: zi e [MS-RRP] voor meer informatie over deze service.
Communicatie met de Services Control Manager-service toestaan: zi e [MS-SCMR] voor meer informatie over
deze service.
Communicatie met de Server-service toestaan: zi e [MS-SRVS] voor meer informatie over deze service.
Communicatie met de andere services toestaan: overige MSRPC-services.
7.3.1 IDS-uitzonderingen
IDS-uitzonderingen (Intrusion Detection System) zijn in wezen netwerkbeveiligingsregels. De uitzonderingen
worden van boven naar beneden beoordeeld. Met de editor voor IDS-uitzonderingen kunt u het netwerkgedrag
wijzigen. De eerste overeenkomende uitzondering wordt toegepast. Dit gebeurt voor elk actietype afzonderlijk
(Blokkeren, Melden, In logboek registreren). Met Boven/Omhoog/Onder/Omlaag kunt u het prioriteitniveau van de
uitzonderingen wijzigen. Als u een nieuwe IDS-uitzondering wilt maken, klikt u op Toevoegen. Klik op Bewerken
om een bestaande IDS-uitzondering te wijzigen of op Verwijderen om deze te verwijderen.

199
Kies het type Waarschuwing in de vervolgkeuzelijstlist. Geef de Bedreigingsnaam op en de Richting. Blader naar
een Toepassing waarvoor u de uitzondering wilt maken. Geef een lijst met IP-adressen op (IPv4 of IPv6) of
subnetten. Gebruik voor meerdere vermeldingen een komma als scheidingsteken.
Configureer Actie voor IDS-uitzonderingen door een van de opties in de vervolgkeuzelijst te selecteren (Standaard,
Ja, Nee). Doe dit voor elk actietype (Blokkeren, Melden, In logbestand registreren).
VOORBEELD
Als u wilt dat er een melding wordt weergegeven in het geval van een waarschuwing over een IDS-
uitzondering, en ook het tijdstip van de gebeurtenis vastgelegd wilt hebben, laat het actietype Blokkeren dan
op Standaard staan en kies voor de andere twee actietypen (Melden en In logbestand registreren) de optie Ja
in het vervolgkeuzemenu.
7.3.2 Zwarte lijst met tijdelijk geblokkeerde IP-adressen
Een lijst met IP-adressen weergeven die als aanvalsbronnen zijn gedetecteerd en die aan de zwarte lijst zijn
toegevoegd, zodat hiermee gedurende een bepaalde tijd geen verbindingen kunnen worden gemaakt. Geeft IP-
adressen weer die zijn vergrendeld.
Reden van blokkeren
Geeft het type aanval aan dat afkomstig is van het adres en dat is voorkomen (bijvoorbeeld een TCP Port
Scanning-aanval).
Time-out
Geeft de datum en tijd aan waarop het adres in de zwarte lijst komt te vervallen.
Verwijderen/Alles verwijderen
Hiermee wordt het geselecteerde IP-adres verwijderd uit de tijdelijke zwarte lijst voordat de time-out wordt
bereikt of worden alle adressen direct uit de zwarte lijst verwijderd.
Uitzondering toevoegen
Voegt een firewalluitzondering toe aan IDS-filtering voor het geselecteerde IP-adres.
7.4 Web en e-mail
U kunt Protocolfiltering, Beveiliging van e-mailclient, Beveiliging van webtoegang en Antiphishing configureren om
uw server tijdens internetcommunicatie te beveiligen.
Beveiliging van e-mailclient
Regelt alle e-mailcommunicatie, beschermt tegen schadelijke code en geeft u de keuze welke actie moet
worden ondernomen wanneer er een infectie wordt gedetecteerd.
Beveiliging van webtoegang
Controleert de communicatie tussen webbrowsers en externe servers, waarbij de regels voor HTTP en HTTPS
worden gehanteerd. Met deze functie kunt u ook bepaalde URL-adressen blokkeren, toestaan of uitsluiten.
Protocolfiltering
Biedt geavanceerde beveiliging voor toepassingsprotocollen en wordt geleverd door de scanengine van
ThreatSense. Deze controle werkt automatisch, ongeacht of er een webbrowser of e-mailclient wordt gebruikt.
De controle werkt ook voor versleutelde (SSL/TLS) communicatie.
Antiphishing-beveiliging
Biedt u de mogelijkheid webpagina's te blokkeren waarvan bekend is dat deze voor phishingdoeleinden
worden gebruikt.

200
7.4.1 Protocolfiltering
Antivirusbeveiliging voor toepassingsprotocollen wordt geleverd door de ThreatSense-scanengine, die meerdere
geavanceerde technieken integreert voor het scannen op malware. Protocolfiltering werkt automatisch, ongeacht
de gebruikte internetbrowser of e-mailclient. Als protocolfiltering is ingeschakeld, controleert ESET Mail Security
communicatie waarbij gebruik wordt gemaakt van het SSL/TLS-protocol. Ga naar Web en e-mail > SSL/TLS.
Inhoudsfilter van toepassingsprotocol inschakelen
Als u protocolfiltering uitschakelt, is het raadzaam om te weten dat veel ESET Mail Security-onderdelen
(Beveiliging van webtoegang, Beveiliging van e-mailprotocollen en Antiphishing-beveiliging) ervan afhankelijk
zijn en niet alle functies ervan beschikbaar zijn.
Uitgesloten toepassingen
Om de communicatie van bepaalde toepassingen met toegang tot het netwerk uit te sluiten van
inhoudsfiltering, selecteert u deze in de lijst. De HTTP-/POP3-communicatie van de geselecteerde
toepassingen wordt niet op bedreigingen gecontroleerd. Hiermee kunt u specifieke toepassingen uitsluiten
van protocolfiltering. Klik op Bewerken en Toevoegen om een uitvoerbaar bestand te selecteren in de lijst.
BELANGRIJK
Het wordt aangeraden deze optie alleen te gebruiken voor toepassingen die niet correct werken wanneer de
communicatie ervan wordt gecontroleerd.
Uitgesloten IP-adressen
Hiermee kunt u specifieke externe adressen uitsluiten van protocolfiltering. IP-adressen in deze lijst worden
uitgesloten van filteren op protocolinhoud. HTTP-/POP3-/IMAP-communicatie van/naar de geselecteerde
adressen wordt niet op bedreigingen gecontroleerd.
BELANGRIJK
Wij raden aan dat u deze optie alleen gebruikt voor adressen die bekend staan als betrouwbaar.
Kl ik op Bewerken en Toevoegen om IP-adressen, een adresbereik of subnet op te geven waarop de uitsluiting moet
worden toegepast. Als u Geef meerdere waarden op selecteert, kunt u meerdere IP-adressen opgeven, van elkaar
gescheiden door nieuwe regels, komma's of puntkomma's. Als meervoudige selectie is ingeschakeld, worden
adressen in de lijst met uitgesloten IP-adressen weergegeven.
OPMERKING
Uitsluitingen zijn handig als protocolfiltering compatibiliteitsproblemen veroorzaakt.
7.4.1.1 Web- en e-mailclients
Met het oog op de enorme hoeveelheid schadelijke code die op internet circuleert, is veilig surfen een uiterst
belangrijk aspect van computerbeveiliging. Als gevolg van frauduleuze koppelingen en beveiligingsproblemen in
webbrowsers kan schadelijke code ongemerkt het systeem binnendringen. Daarom staat beveiliging van
webbrowsers in ESET Mail Security centraal. Elke toepassing die toegang tot het netwerk krijgt, kan als
internetbrowser worden gemarkeerd. Toepassingen die al protocollen voor communicatie of een toepassing van
geselecteerde paden gebruiken, kunnen worden toegevoegd aan de lijst met web- en e-mailclients.
OPMERKING
Vanaf Windows Vista Service Pack 1 en Windows Server 2008 SP2 wordt de nieuwe architectuur WFP (Windows
Filtering Platform) gebruikt om de netwerkcommunicatie te controleren. Aangezien WFP speciale
controletechnieken gebruikt, is het gedeelte Web- en e-mailclients niet beschikbaar.

201
7.4.2 SSL/TLS
ESET Mail Security kan op bedreigingen controleren in communicatie die gebruikmaakt van het Secure Sockets Layer
(SSL)/Transport Layer Security-protocol (TLS).
U kunt verscheidene scanmodi gebruiken om communicatie die is beveiligd met SSL te controleren met vertrouwde
certificaten, onbekende certificaten of certificaten die zijn uitgesloten van controle van communicatie die is
beveiligd met SSL.
SSL/TLS-protocolfiltering inschakelen
Als protocolfiltering is uitgeschakeld, scant het programma geen communicatie die via SSL/TLS plaatsvindt. De
Secure Sockets Layer (SSL)/Transport Layer Security (TLS)-protocolfilteringmodus is beschikbaar bij de volgende
opties:
· Automatische modus: selecteer deze optie om alle met SSL/TLS beveiligde communicatie te scannen,
behalve communicatie die wordt beveiligd door certificaten die van scannen zijn uitgesloten. Als nieuwe
communicatie een onbekend, ondertekend certificaat gebruikt, wordt u hierover niet gewaarschuwd en
wordt de communicatie automatisch gefilterd. Als u toegang krijgt tot een server met een niet-vertrouwd
certificaat dat als vertrouwd is gemarkeerd (het staat op de lijst met vertrouwde certificaten), wordt
communicatie met de server toegestaan en de inhoud van het communicatiekanaal wordt gefilterd.
· Interactieve modus: als u een nieuwe door SSL/TLS beveiligde site opgeeft (met een onbekend certificaat),
wordt er een actieselectievenster weergegeven. In deze modus kunt een lijst maken met SSL/TLS-certificaten
die van scannen worden uitgesloten.
· Beleidsmodus: alle SSL/TLS-verbindingen worden gefilterd, behalve geconfigureerde uitsluitingen.
Lijst met door SSL/TLS gefilterde toepassing
Voeg een gefilterde toepassing toe en stel een van de scanacties in. De lijst met door SSL/TLS gefilterde
toepassingen kan worden gebruikt om het gedrag van ESET Mail Security aan te passen voor bepaalde
toepassingen, en om gekozen acties te onthouden als Interactieve modus is geselecteerd in de Modus voor
SSL/TLS-protocolfiltering.
Lijst met bekende certificaten
Hiermee kunt u het gedrag van ESET Mail Security wijzigen voor bepaalde SSL-certificaten. De lijst kan worden
weergegeven en beheerd door te klikken op Bewerken naast Lijst met bekende certificaten.
Communicatie met vertrouwde domeinen uitsluiten
Als u communicatie met uitgebreide validatiecertificaten wilt uitsluiten van protocolcontrole
(internetbankieren).
Gecodeerde communicatie met het verouderde protocol SSL v2 blokkeren
Communicatie met deze oude versie van het SSL-protocol wordt automatisch geblokkeerd.
Basiscertificaat
Om er zeker van te zijn dat SSL/TLS-communicatie goed werkt in uw browsers/e-mailclients, is het noodzakelijk
dat u het basiscertificaat voor ESET toevoegt aan de lijst met bekende basiscertificaten (uitgevers). Het
toevoegen van het basiscertificaat aan bekende browsers moet zijn ingeschakeld. Selecteer deze optie om het
basiscertificaat van ESET automatisch toe te voegen aan bekende browsers (bijvoorbeeld Opera en Firefox). Het
certificaat wordt automatisch toegevoegd aan browsers die gebruikmaken van het archief met
systeemcertificaten (bijvoorbeeld in Internet Explorer).
Als u het certificaat wilt toepassen op niet-ondersteunde browsers, klikt u op Certificaat weergeven > Details >
Kopiëren naar bestand... en importeert u het certificaat handmatig in de browser.
Certificaatgeldigheid
Als het certificaat niet kan worden gecontroleerd met het TRCA-certificaatarchief

202
In bepaalde gevallen kan het certificaat niet worden gecontroleerd met het TRCA-certificaatarchief (Trusted
Root Certification Authorities). Dit betekent dat het certificaat door iemand is ondertekend (bijvoorbeeld de
Administrator van een webserver of een klein bedrijf). Een dergelijk certificaat als vertrouwd beschouwen, is
niet altijd een risico. De meeste grote bedrijven (zoals banken) gebruiken een door de TRCA ondertekend
ce rti fi caat. Al s Vragen naar geldigheid van certificaat (standaardinstelling) is ingeschakeld, wordt de gebruiker
gevraagd een actie te selecteren wanneer versleutelde communicatie tot stand wordt gebracht. U kunt
Communicatie blokkeren die gebruikmaakt van het certificaat selecteren om versleutelde verbindingen naar
sites met niet-geverifieerde certificaten altijd te verbreken.
Als het certificaat ongeldig of beschadigd is
Dit betekent dat het certificaat is verlopen of op een onjuiste manier is ondertekend. In dat geval raden we aan
dat u Communicatie blokkeren die gebruikmaakt van het certificaat ingeschakeld laat.
7.4.2.1 Lijst met bekende certificaten
Als u het gedrag van ESET Mail Security wilt aanpassen voor bepaalde Secure Sockets Layer (SSL)/Transport Layer
Security (TLS)-certificaten en gekozen acties wilt laten onthouden als Interactieve modus wordt geselecteerd in de
SSL/TLS-protocolfilteringmodus. U kunt het geselecteerde certificaat configureren of een certificaat Toevoegen
vanuit een URL of bestand. Zodra u in het venster Certificaat toevoegen bent, klikt u op URL of Bestand en geeft u de
URL van het certificaat op of bladert u naar een certificaatbestand. De volgende velden worden automatisch
ingevuld met gegevens van het certificaat:
· Certificaatnaam: de naam van het certificaat.
· Uitgever van certificaat: de naam van de maker van het certificaat.
· Certificaatonderwerp: in het onderwerpveld kunt u de entiteit zien die is gekoppeld aan de openbare code
die is opgeslagen in het veld voor het onderwerp van de openbare code.
Toegangsactie
· Automatisch: om vertrouwde certificaten toe te staan en naar niet-vertrouwde certificaten te vragen.
· Toestaan of blokkeren: om communicatie toe te staan/te blokkeren die wordt beveiligd door dit certificaat,
ongeacht de betrouwbaarheid ervan.
· Vragen: om een vraag te krijgen wanneer een bepaald certificaat wordt gedetecteerd.
Scanactie
· Automatisch: om in automatische modus te scannen en in interactieve modus te vragen.
· Scannen of negeren: om communicatie te scannen of negeren die wordt beveiligd met dit certificaat.
· Vragen: om een vraag te krijgen wanneer een bepaald certificaat wordt gedetecteerd.
7.4.2.2 Gecodeerde SSL-communicatie
Als uw systeem is geconfigureerd om het SSL-protocol te scannen, wordt er in twee situaties een dialoogvenster
weergegeven waarin u wordt gevraagd een actie te kiezen:
Ten eerste, als een website een niet-verifieerbaar of ongeldig certificaat gebruikt, en ESET Mail Security is
geconfigureerd om de gebruiker in dergelijke gevallen te vragen (standaard gebeurt dit wel bij niet-verifieerbare
certificaten maar niet bij ongeldige certificaten), wordt u in een dialoogvenster gevraagd of u de verbinding wilt
Toestaan of Blokkeren.
Ten tweede, als SSL-protocolfiltering is ingesteld op Interactieve modus wordt er een dialoogvenster weergegeven
voor elke website en wordt u gevraagd of u het verkeer wilt Scannen of Negeren. Bepaalde toepassingen
controleren of hun SSL-verkeer wordt aangepast of door anderen wordt geïnspecteerd. In dergelijke gevallen moet
ESET Mail Security dat verkeer Negeren om de toepassing te kunnen laten werken.

203
In beide gevallen kan de gebruiker kiezen om de geselecteerde actie te onthouden. Opgeslagen acties worden
bewaard in de lijst met bekende certificaten.
7.4.3 Beveiliging van e-mailclient
Door integratie van ESET Mail Security met e-mailclients neemt het actieve beveiligingsniveau tegen schadelijke
code in e-mailberichten toe. Als uw e-mailclient wordt ondersteund, kan integratie in ESET Mail Security worden
ingeschakeld. Als integratie wordt geactiveerd, wordt de ESET Mail Security-werkbalk rechtstreeks in de e-
mailclient opgenomen (de werkbalk wordt niet opgenomen in nieuwere versies van Windows Live Mail), waardoor
e-mailbeveiliging nog efficiënter is.
Integratie in e-mailclient
De e-mailclients die momenteel worden ondersteund zijn onder andere Microsoft Outlook, Outlook Express,
Windows Mail en Windows Live Mail. E-mailbeveiliging werkt als een plug-in voor deze programma's. Het
belangrijkste voordeel van de plug-in is dat deze onafhankelijk is van het gebruikte protocol. Wanneer de e-
mailclient een versleuteld bericht ontvangt, wordt dit ontsleuteld en naar de virusscanner verzonden. Zelfs als
integratie niet is ingeschakeld, wordt e-mailcommunicatie nog steeds beveiligd door de e-
mailclientbeveiligingsmodule (POP3, IMAP). Raadpleeg het volgende artikel in de kennisbank voor een
volledige lijst met ondersteunde e-mailclients en de bijbehorende versies.
Controle bij wijziging van inhoud van Postvak IN uitschakelen
Als het systeem trager wordt tijdens het werken met de e-mailclient (alleen MS Outlook). Dit kan bijvoorbeeld
gebeuren wanneer e-mail wordt opgehaald vanuit het archief van Kerio Outlook Connector.
E-mailbeveiliging met plug-ins van client inschakelen
Hiermee kunt u e-mailclientbeveiliging uitschakelen zonder integratie in uw e-mailclient te verwijderen. U
kunt alle plug-ins tegelijk uitschakelen of de volgende selectief uitschakelen:

204
· Ontvangen e-mail: hiermee wordt het controleren van ontvangen berichten in- of uitgeschakeld.
· Verzonden e-mail: hiermee wordt het controleren van verzonden berichten in- of uitgeschakeld.
· Gelezen e-mail: hiermee wordt het controleren van gelezen berichten in- of uitgeschakeld.
Uit te voeren actie op geïnfecteerde e-mail
· Geen actie: als u deze optie inschakelt, worden geïnfecteerde bijlagen gemeld, maar wordt niets gedaan met
e-mails.
· E-mail verwijderen: de gebruiker wordt geattendeerd op bedreigingen en het bericht wordt verwijderd.
· E-mail verplaatsen naar de map Verwijderde items: geïnfecteerde e-mails worden automatisch verplaatst
naar de map Verwijderde items.
· E-mail verplaatsen naar map: geïnfecteerde e-mails worden automatisch verplaatst naar de opgegeven map.
· Map: geef de aangepaste map op waar u geïnfecteerde e-mails naar toe wilt verplaatsen nadat deze zijn
gedetecteerd.
Scan herhalen na bijwerken
Hiermee wordt het opnieuw scannen na het bijwerken van de detectie engine in- of uitgeschakeld.
Scanresultaten van andere modules accepteren
Als dit is ingeschakeld, accepteert de module E-mailbeveiliging de scanresultaten van andere
beveiligingsmodules (scannen van POP3, IMAP-protocollen).
7.4.3.1 E-mailprotocollen
E-mailbeveiliging door protocolfiltering inschakelen
Het IMAP- en het POP3-protocol zijn de meest gebruikte protocollen voor het ontvangen van e-
mailcommunicatie in een e-mailclienttoepassing. ESET Mail Security biedt beveiliging voor deze protocollen,
ongeacht de e-mailclient die wordt gebruikt.
ESET Mail Security ondersteunt ook het scannen van IMAPS- en POP3S-protocollen, die gebruikmaken van een
versleuteld kanaal om gegevens uit te wisselen tussen server en client. ESET Mail Security controleert de
communicatie via SSL (Secure Socket Layer) en TLS (Transport Layer Security). Het programma scant alleen verkeer
op poorten die zijn gedefinieerd in poorten die worden gebruikt door het IMAPS/POP3S-protocol, ongeacht de
versie van het besturingssysteem.
Instellingen voor IMAPS/POP3S-scanner
Versleutelde communicatie wordt niet gescand als de standaardinstellingen in gebruik zijn. Navigeer naar SSL/
TLS-protocolcontrole als u scannen van versleutelde communicatie wilt inschakelen.
Het poortnummer identificeert welk type poort het is. Dit zijn de standaardpoorten voor e-mail voor:
Poortnaam
Poortnumm
ers
Beschrijving
POP3
110
Standaardpoort, POP3, niet-versleuteld.
IMAP
143
Standaardpoort, IMAP, niet-versleuteld.
Beveiligde IMAP
(IMAP4-SSL)
585
SSL/TLS-protocolfiltering inschakelen. Poortnummers moeten van elkaar
worden gescheiden door een komma.
IMAP4 via SSL
(IMAPS)
993
SSL/TLS-protocolfiltering inschakelen. Poortnummers moeten van elkaar
worden gescheiden door een komma.
Beveiligde POP3
(SSL-POP)
995
SSL/TLS-protocolfiltering inschakelen. Poortnummers moeten van elkaar
worden gescheiden door een komma.

205
7.4.3.2 Waarschuwingen en meldingen
E-mailbeveiliging biedt controle over e-mailcommunicatie die wordt ontvangen via de protocollen POP3 en IMAP.
Met behulp van de invoegtoepassing voor Microsoft Outlook en andere e-mailclients, biedt ESET Mail Security
controle over alle communicatie via de e-mailclient (POP3, MAPI, IMAP, HTTP). Bij het onderzoeken van
binnenkomende berichten maakt het programma gebruik van alle geavanceerde scanmethoden van de
ThreatSense-scanengine. Dit betekent dat detectie van schadelijke programma's plaatsvindt zelfs nog voordat deze
worden vergeleken met de virusdetectiedatabase. Het scannen van communicatie via het POP3- of IMAP-protocol
gebeurt onafhankelijk van de gebruikte e-mailclient.
Nadat een e-mail is gecontroleerd, kan een melding met het scanresultaat aan het bericht worden toegevoegd. U
kunt ook kiezen uit Tagmeldingen toevoegen aan ontvangen en gelezen e-mail, Opmerking toevoegen aan het
onderwerp van ontvangen en gelezen geïnfecteerde e-mail en Tagmeldingen toevoegen aan verzonden e-mail. In
zeldzame gevallen kunnen tagberichten in problematische HTML-berichten worden weggelaten. Dit kan ook
gebeuren als berichten worden vervalst door bepaalde malware. De meldingen kunnen aan ontvangen/gelezen e-
mailberichten en/of verzonden e-mailberichten worden toegevoegd. Beschikbare opties:
· Nooit: er worden geen meldingen toegevoegd.
· Alleen naar geïnfecteerde e-mail: alleen berichten met schadelijke software worden als gecontroleerd
gemarkeerd (standaardinstelling).
· Naar alle gescande e-mail: er worden meldingen toegevoegd aan alle gescande e-mail.
Opmerking toevoegen aan het onderwerp van verzonden geïnfecteerde e-mail
Schakel dit uit als u niet wilt dat er een viruswaarschuwing aan het onderwerp van een geïnfecteerde e-mail
wordt toegevoegd. Met deze functie kunt u geïnfecteerde e-mails eenvoudig filteren op basis van het
onderwerp (vooropgesteld dat uw e-mailprogramma hiervoor ondersteuning biedt). Door deze functie neemt
de geloofwaardigheid voor de geadresseerde toe en bij detectie van een infiltratie biedt de functie
waardevolle informatie over het bedreigingsniveau van een bepaalde e-mail of afzender.
Sjabloon toegevoegd aan het onderwerp van geïnfecteerde e-mail
Bewerk deze sjabloon als u de voorvoegselindeling voor het onderwerp van een geïnfecteerde e-mail wilt
wijzigen. Deze functie vervangt het berichtonderwerp Hello door de voorvoegselwaarde [virus] in de
vol gende i nde li ng: [virus] Hello.
7.4.3.3 MS Outlook-werkbalk
Microsoft Outlook-beveiliging werkt als een invoegtoepassing. Nadat ESET Mail Security is geïnstalleerd, wordt deze
werkbalk met de opties van de antivirusbeveiliging toegevoegd aan Microsoft Outlook:
ESET Mail Security
Door op het pictogram te klikken wordt het hoofdprogrammavenster van ESET Mail Security geopend.
Berichten opnieuw scannen
Klik hierop om e-mail handmatig te controleren. U kunt aangeven welke berichten u wilt controleren en u kunt
ontvangen e-mail opnieuw scannen. Zie Beveiliging van e-mailclient voor meer informatie.
Scannerinstellingen
Geeft opties met instellingen voor Beveiliging van e-mailclient weer.

206
7.4.3.4 Outlook Express- en Windows Mail-werkbalk
Outlook Express en Windows Mail worden beveiligd met een invoegtoepassing. Nadat ESET Mail Security is
geïnstalleerd, wordt deze werkbalk met de opties van de antivirusbeveiliging toegevoegd aan Outlook Express of
Windows Mail:
ESET Mail Security
Door op het pictogram te klikken wordt het hoofdprogrammavenster van ESET Mail Security geopend.
Berichten opnieuw scannen
Klik hierop om e-mail handmatig te controleren. U kunt aangeven welke berichten u wilt controleren en u kunt
ontvangen e-mail opnieuw scannen. Zie Beveiliging van e-mailclient voor meer informatie.
Scannerinstellingen
Geeft opties met instellingen voor Beveiliging van e-mailclient weer.
Uiterlijk aanpassen
U kunt de werkbalk voor uw e-mailclient op verschillende manieren aanpassen. Schakel deze optie uit om het
uiterlijk aan te passen, los van de parameters van het e-mailprogramma.
· Tekst weergeven: selecteer deze optie om omschrijvingen voor pictogrammen weer te geven.
· Tekst aan de rechterkant: omschrijvingen van opties worden niet onder, maar rechts van pictogrammen
weergegeven.
· Grote pictogrammen: er worden grote pictogrammen weergegeven voor menuopties.
7.4.3.5 Bevestigingsvenster
Er wordt een bevestigingsvenster weergegeven om de gebruiker te vragen de geselecteerde actie te bevestigen
voordat deze wordt uitgevoerd. Hierdoor kunnen fouten worden voorkomen. Het dialoogvenster biedt ook de optie
om bevestigingen uit te schakelen.
7.4.3.6 Berichten opnieuw scannen
Als de werkbalk van ESET Mail Security is geïntegreerd in e-mailclients, kan de gebruiker verschillende opties kiezen
om e-mail te controleren. De optie Berichten opnieuw scannen kan in twee modi worden uitgevoerd:
· Alle berichten in de huidige map : hiermee worden berichten in de op dat moment weergegeven map
gescand.
· Alleen geselecteerde berichten: hiermee worden alleen door de gebruiker geselecteerde berichten gescand.
· Reeds gescande berichten opnieuw scannen: hiermee kunnen gebruikers nog een scan uitvoeren op
berichten die eerder al zijn gescand.
7.4.4 Beveiliging van webtoegang
Beveiliging van webtoegang werkt door de communicatie tussen webbrowsers en externe servers te controleren
om u te beschermen tegen bedreigingen online. Hierbij worden de regels voor HTTP (Hypertext Transfer Protocol)
en HTTPS (HTTP met gecodeerde communicatie) nageleefd.
Toegang tot webpagina's waarvan bekend is dat deze schadelijke inhoud bevatten, wordt geblokkeerd voordat er
inhoud wordt gedownload. Alle overige webpagina's worden gescand door de ThreatSense-scanengine wanneer ze
worden geladen, en geblokkeerd als er schadelijke inhoud wordt ontdekt. Met Beveiliging van webtoegang wordt
er op twee niveaus beveiliging geboden; blokkeren op basis van zwarte lijsten en blokkeren op basis van inhoud.
Basis
Het wordt ten zeerste aangeraden de optie Beveiliging van webtoegang ingeschakeld te laten. Deze optie vindt u
ook in het hoofdprogrammavenster van ESET Mail Security door naar Instellingen > Web en e-mail > Beveiliging van
webtoegang te gaan.

207
Geavanceerd scannen van browserscripts inschakelen
Standaard worden alle JavaScript-programma's die door webbrowsers worden uitgevoerd door de detectie-
engine gecontroleerd.
Webprotocollen
Hiermee kunt u controle configureren voor deze standaardprotocollen, die door de meeste internetbrowsers
worden gebruikt. Standaard wordt ESET Mail Security geconfigureerd om het HTTP-protocol te controleren dat door
de meeste internetbrowsers wordt gebruikt.
ESET Mail Security ondersteunt ook HTTPS-protocolcontrole. HTTPS-communicatie maakt gebruikt van een
versleuteld kanaal om gegevens uit te wisselen tussen server en client. ESET Mail Security controleert de
communicatie via de protocollen SSL (Secure Socket Layer) en TLS (Transport Layer Security). Het programma scant
alleen verkeer op poorten die zijn gedefinieerd in Poorten die worden gebruikt door HTTPS-protocol, ongeacht de
versie van het besturingssysteem.
Versleutelde communicatie wordt niet gescand als de standaardinstellingen in gebruik zijn. Als u versleutelde
communicatie wilt scannen, gaat u naar Geavanceerde instellingen (F5) > Web en e-mail > SSL/TLS.
ThreatSense-parameters
Configureer instellingen zoals scantypen (e-mails, archieven, uitsluitingen, limieten, enz.) en
detectiemethoden voor Beveiliging van webtoegang.
7.4.4.1 URL-adresbeheer
Dankzij het URL-adresbeheer kunt u HTTP-adressen opgeven om deze te blokkeren, toe te staan of uit te sluiten van
controle. Websites op de lijst met geblokkeerde adressen zijn niet toegankelijk tenzij die ook zijn opgenomen in de
lijst met toegestane adressen. Websites op de lijst met adressen die zijn uitgesloten van controle, worden niet
gescand op schadelijke code wanneer die worden geopend. SSL/TLS-protocolfiltering moet worden ingeschakeld als
u naast HTTP-webpagina's ook HTTPS-adressen wilt filteren. Anders worden alleen de domeinen toegevoegd van
HTTPS-sites die u hebt bezocht, niet de volledige URL.
Een lijst met geblokkeerde adressen kan adressen bevatten van een externe openbare zwarte lijst, en een andere
lijst kan een eigen zwarte lijst zijn, waardoor het eenvoudiger is de externe lijst bij te werken en uw eigen lijst
ongewijzigd te laten.
Kl ik op Bewerken en Toevoegen om een nieuwe adreslijst te maken in aanvulling op de vooraf gedefinieerde
adreslijsten. Dit kan handig zijn als u verschillende adresgroepen logisch wilt splitsen. Standaard zijn de volgende
drie lijsten beschikbaar:
· Lijst met adressen die zijn uitgesloten van controle: adressen in deze lijst worden niet gecontroleerd op
schadelijke code.
· Lijst met toegestane adressen: als de optie Alleen toegang toestaan tot HTTP-adressen in de lijst met
toegestane adressen is ingeschakeld en de lijst met geblokkeerde adressen bevat * (overeenkomend met
alles), heeft de gebruiker alleen toegang tot adressen in deze lijst. De adressen in deze lijst worden
toegestaan, zelfs als ze in de lijst met geblokkeerde adressen staan.
· Lijst met geblokkeerde adressen: de gebruiker heeft geen toegang tot adressen in deze lijst, tenzij ze ook
staan in de lijst met toegestane adressen.

208
U kunt een nieuw URL-adres aan de lijst Toevoegen. Ook kunt u met een scheidingsteken meerdere waarden
opgeven. Klik op Bewerken om een bestaand adres in de lijst te wijzigen, of op Verwijderen om dit te verwijderen.
Verwijderen is alleen mogelijk voor adressen die zijn gemaakt met Toevoegen, niet met adressen die zijn
geïmporteerd.
In alle lijsten kunnen de speciale symbolen * (sterretje) en ? (vraagteken) worden gebruikt. Het sterretje
vertegenwoordigt elke willekeurige reeks cijfers of tekens, terwijl het vraagteken elk willekeurig teken
vertegenwoordigt. Wees met name voorzichtig bij het opgeven van uitgesloten adressen, omdat deze lijst alleen
vertrouwde en veilige adressen zou moeten bevatten. Ga tevens zorgvuldig om met de symbolen * en ? en zorg
ervoor dat deze correct worden gebruikt in deze lijst.
OPMERKING
Als u alle HTTP-adressen wilt blokkeren behalve adressen die in de actieve lijst met toegestane adressen
staan, voeg dan * toe aan de actieve lijst met geblokkeerde adressen
7.4.4.1.1 Nieuwe lijst maken
Deze lijst omvat de gewenste URL-adressen/domeinmaskers die worden geblokkeerd, toegestaan of uitgesloten
van controle. Geef het volgende op wanneer u een nieuwe lijst maakt:
· Adreslijsttype - kies het type (Uitgesloten van controle, Geblokkeerd of Toegestaan) uit de vervolgkeuzelijst.
· Lijstnaam: geef hier de naam van de lijst op. Dit veld wordt grijs weergegeven als een van de drie vooraf
gedefinieerde lijsten wordt bewerkt.
· Beschrijving van lijst: typ hier een korte beschrijving van de lijst (optioneel). Dit wordt grijs weergegeven als
een van de drie vooraf gedefinieerde lijsten wordt bewerkt.
· Lijst actief: gebruik de schakelaar om de lijst te deactiveren. U kunt de lijst later activeren wanneer dit nodig
is.

209
· Melden bij toepassen: als u een melding wilt ontvangen als een bepaalde lijst wordt gebruikt voor de
beoordeling van een HTTP/HTTPS-site die u hebt bezocht, selecteer dan Melden bij toepassen. Er wordt een
melding afgegeven als een website wordt geblokkeerd of toegestaan omdat deze zich op de lijst met
geblokkeerde of toegestane adressen bevindt. In de melding staat de naam van de lijst waar de
desbetreffende website op staat vermeld.
· Ernst van logboekregistratie: kies de ernst van de logboekregistratie (Geen, Diagnostisch, Informatie of
Waarschuwing) in de vervolgkeuzelijst. Records van het type Waarschuwing kunnen door ESET Security
Management Center worden verzameld.
Met ESET Mail Security kunt u de toegang tot bepaalde websites blokkeren en voorkomen dat de inhoud van deze
websites in de internetbrowser wordt weergegeven. Daarnaast kunt u de adressen opgeven van websites die niet
worden gecontroleerd. Als u niet weet wat de volledige naam van de externe server is of als u een groep externe
servers wilt opgeven, kunt u zogenaamde maskers gebruiken om de groep aan te geven.
De maskers hebben de symbolen ? en *:
· Met ?? kunt u een symbool vervangen
· gebruik * om een tekstreeks te vervangen
VOORBEELD
*.c?m is van toepassing op alle adressen waarin het laatste gedeelte begint met het gebruik van de letter c,
eindigt op de letter m en daartussen een onbekend symbool bevat (.com, .cam, etc.).
Een voorlope nde *.-reeks wordt speciaal behandeld als deze wordt gebruikt aan het begin van een domeinnaam.
Ten eerste kan het jokerteken * in dit geval geen slash ('/') vertegenwoordigen. Dit is bedoeld om te voorkomen dat
het masker wordt omzeild. Het masker *.domain.com komt bijvoorbeeld niet overeen met https://anydomain.com/
anypath#.domain.com (zo'n achtervoegsel kan worden toegevoegd aan elk webadres zonder dat dat gevolgen heeft
voor de download). Ten tweede komt het *. ook overeen met een lege tekenreeks in dit speciale geval. Dit is
bedoeld om overeenkomst met een geheel domein mogelijk te maken, waaronder alle eventuele subdomeinen
die één enkel masker gebruiken. Het masker *.domain.com komt bijvoorbeeld ook overeen met https://
domain.com. Het gebruik van *domain.com zou onjuist zijn, omdat dat ook overeenkomt met https://
anotherdomain.com.
Geef meerdere waarden op
Voeg meerdere URL-adressen toe, van elkaar gescheiden door nieuwe regels, komma's of puntkomma's. Als
meervoudige selectie is ingeschakeld, worden adressen in de lijst weergegeven.
Importeren
Tekstbestand met te importeren webadressen (scheid waarden van elkaar met een regeleinde, bijvoorbeeld
*.txt met codering UTF-8).

210
7.4.5 Antiphishing-webbeveiliging
De term 'phishing' verwijst naar een criminele activiteit die gebruikmaakt van 'social engineering'. Hierbij worden
gebruikers gemanipuleerd met als doel het verkrijgen van vertrouwelijke informatie. Met phishing wordt vaak
geprobeerd toegang te krijgen tot gevoelige gegevens, zoals bankrekeningnummers, pincodes en meer.
ESET Mail Security bevat Antiphishing-beveiliging, waarmee webpagina's worden geblokkeerd waarvan bekend is
dat deze dit type inhoud verspreiden. Wij raden ten zeerste aan om Antiphishing in te schakelen in ESET Mail
Security. Ga naar ons kennisbankartikel voor meer informatie over Antiphishing-beveiliging in ESET Mail Security.
Wanneer u een herkende phishingwebsite opent, wordt het volgende dialoogvenster weergegeven in uw
webbrowser. Als u de website weergegeven wilt hebben, klikt u op Bedreiging negeren (niet aanbevolen).
OPMERKING
Potentiële phishing-websites die op de witte lijst zijn geplaatst, verlopen standaard na enkele uren. Als u een
website definitief wilt toestaan, gebruik dan het hulpprogramma URL-adresbeheer.
Een phishingsite rapporteren

211
Als u een verdachte website ontdekt dat informatie lijkt te ontvreemden of anderszins schadelijk is, kunt u
deze voor analyse aan ESET rapporteren. Wanneer u een website naar ESET verzendt, moet deze aan de
volgende criteria voldoen:
· de website wordt helemaal niet gedetecteerd
· de website is onterecht aangemerkt als bedreiging. In dit geval kunt u een Vals positieve phishing-website
melden .
U kunt de website ook per e-mail versturen. Stuur uw e-mail naar samples@eset.com. Zorg ervoor dat u een
duidelijk onderwerp gebruikt en dat u zoveel mogelijk informatie over de website opgeeft (bijvoorbeeld via welke
website u naar deze site bent doorverwezen, hoe u van het bestaan van deze website weet, enz.).
7.5 Apparaatbeheer
ESET Mail Security beschikt over automatisch beheer van apparaten (cd/dvd/USB). Met deze module kunt u een
apparaat scannen, blokkeren of uitgebreide filters/machtigingen aanpassen voor een apparaat en bepalen hoe een
gebruiker toegang tot een apparaat krijgt en ermee werkt. Dit kan handig zijn als de Administrator van de computer
wil voorkomen dat er apparaten met ongewenste inhoud worden gebruikt.
OPMERKING
Wanneer u Apparaatbeheer inschakelt met de schakelaar Integreren in systeem, wordt de functie
Apparaatbeheer van ESET Mail Security geactiveerd. Uw systeem dient echter opnieuw te worden gestart om
deze wijziging van kracht te laten worden.
Apparaatbeheer wordt actief, waardoor u de instellingen ervan kunt bewerken. Als er een apparaat wordt
gedetecteerd dat door een bestaande regel wordt geblokkeerd, wordt er een meldingsvenster weergegeven en
wordt de toegang tot het apparaat geblokkeerd.
Regels
Met ee n regel voor apparaatbeheer wordt de actie gedefinieerd die wordt ondernomen als er een apparaat op
de computer wordt aangesloten dat aan de regelcriteria voldoet.
Groepen
Wanneer u op Bewerken klikt, kunt u Appraatgroepen beheren. Maak een nieuwe apparaatgroep of selecteer
een bestaande apparaatgroep om apparaten aan de lijst toe te voegen of eruit te verwijderen.
OPMERKING
U kunt apparaatbeheervermeldingen bekijken in Logbestanden.
7.5.1 Apparaatregels
Bepaalde apparaten kunnen worden toegestaan of geblokkeerd op gebruiker, gebruikersgroep of diverse
aanvullende apparaatparameters die in de regelconfiguratie worden gespecificeerd. De lijst met regels bevat
verschillende beschrijvingen van een regel, waaronder de naam, het type extern apparaat, de actie die moet
worden uitgevoerd wanneer er een apparaat wordt gedetecteerd, en de vastgelegde ernst.
U kunt een nieuwe regel Toevoegen of instellingen van een bestaande regel wijzigen. Geef een beschrijving van de
regel op in het veld Naam, zodat deze gemakkelijk te herkennen is. Klik op de schakelaar naast Regel ingeschakeld
om de regel in- of uit te schakelen. Dit kan handig zijn als u de regel niet definitief wilt verwijderen.
Toepassen tijdens
U kunt regels beperken met Tijdvakken. Maak eerst het tijdvak. Dit wordt vervolgens weergegeven in het
vervolgkeuzemenu.
Apparaattype

212
Kies het type extern apparaat in het vervolgkeuzemenu (schijfopslag/draagbaar apparaat/Bluetooth/FireWire/
...). De typen opslagapparaten worden overgenomen uit het besturingssysteem en kunnen worden
weergegeven in Apparaatbeheer in het systeem. Er moet dan wel een apparaat op de computer zijn
aangesloten. Opslagapparaten zijn onder andere externe schijven of gewone geheugenkaartlezers die zijn
aangesloten met USB of FireWire. Met smartcardlezers worden lezers bedoeld van smartcards met een
geïntegreerd circuit, zoals simkaarten of verificatiekaarten. Voorbeelden van scanapparaten zijn scanners en
camera's. Dergelijke apparaten geven geen informatie over gebruiker; alleen over hun acties. Dit houdt in dat
scanapparaten alleen algemeen kunnen worden geblokkeerd.
Actie
Toegang tot niet-opslagapparaten kan worden toegestaan of geblokkeerd. Met regels voor opslagapparaten
kunnen echter de volgende rechten worden geselecteerd:
· Lezen/schrijven: er is volledige toegang tot het apparaat mogelijk.
· Blokkeren: de toegang tot het apparaat wordt geblokkeerd.
· Alleen lezen: alleen leestoegang op het apparaat is toegestaan.
· Waarschuwen: elke keer dat een apparaat verbinding maakt, ontvangt de gebruiker een melding of het
apparaat werd toegestaan/geblokkeerd, en wordt er een vermelding in het logbestand opgenomen.
Apparaten worden niet onthouden, dus er wordt ook een melding weergegeven als hetzelfde apparaat later
opnieuw verbinding maakt.
OPMERKING
Houd er rekening mee dat niet alle rechten (acties) beschikbaar zijn voor alle apparaattypen. Als een apparaat
opslagruimte heeft, zijn alle vier de acties beschikbaar. Voor niet-opslagapparaten zijn slechts twee acties
beschikbaar (bijvoorbeeld de actie Alleen lezen is niet beschikbaar voor Bluetooth; dit houdt in dat Bluetooth-
apparaten alleen kunnen worden toegestaan of geblokkeerd).
Aanvullende parameters die hieronder worden weergegeven, kunnen worden gebruikt voor het verfijnen van
regels om ze nauwkeurig af te stemmen op apparaten. Alle parameters zijn hoofdlettergevoelig:
· Leverancier: u kunt filteren op leveranciersnaam of -id.
· Model: de naam van het apparaat.
· Serienummer: externe apparaten hebben doorgaans een eigen serienummer. Bij een cd of dvd is dit het
serienummer van het medium, niet dat van het station.
OPMERKING
Als deze drie descriptors leeg zijn, negeert de regel deze velden bij het zoeken naar overeenkomsten.
Filterparameters in alle tekstvelden zijn hoofdletterongevoelig en jokertekens (*, ?) worden niet
ondersteund.
Als de parameters van een apparaat wilt weten, maakt u een regel om dat apparaattype toe te staan, verbindt u het
apparaat met uw computer en bekijkt u de apparaatdetails in het logbestand van Apparaatbeheer.
Ki es de Ernst van logboekregistratie in de vervolgkeuzelijst:
· Altijd : alle gebeurtenissen worden vastgelegd.
· Diagnostisch: informatie die nodig is om het programma af te stemmen wordt vastgelegd.
· Informatief: informatieve berichten, waaronder berichten over geslaagde updates, plus alle bovenstaande
records worden geregistreerd.
· Waarschuwing: kritieke fouten en waarschuwingsberichten worden geregistreerd.
· Geen: er worden geen logbestanden geregistreerd.
Regels kunnen worden beperkt tot bepaalde gebruikers of gebruikersgroepen door ze toe te voegen aan de
Gebruikerslijst. Klik op Bewerken om de Gebruikerslijst te bewerken.

213
· Toevoegen: hiermee wordt het dialoogvenster Objecttypen: gebruikers of groepen weergegeven, waarin u
de gewenste gebruikers kunt selecteren.
· Verwijderen: hiermee verwijdert u de geselecteerde gebruiker uit het filter.
OPMERKING
Alle apparaten kunnen worden gefilterd met gebruikersregels (scanapparaten geven bijvoorbeeld geen
informatie over gebruikers, maar alleen over aangeroepen acties).
De volgende functies zijn beschikbaar:
Bewerken
Hiermee kunt u de naam van een geselecteerde regel of parameters voor de apparaten erin wijzigen
(leverancier, model, serienummer).
Kopiëren
Hiermee kunt u een nieuwe regel maken op basis van de parameters van de geselecteerde regel.
Verwijderen
Als u de geselecteerde regel wilt verwijderen. U kunt ook het selectievakje gebruiken naast een bepaalde regel
om deze uit te schakelen. Dit kan handig zijn als u een regel niet definitief wilt verwijderen, zodat u deze in de
toekomst opnieuw kunt gebruiken.
Invullen
Geeft met de volgende informatie een overzicht van alle huidige apparaten: apparaattype, apparaatleverancier,
model- en serienummer (indien beschikbaar). Wanneer u een apparaat selecteert (in de lijst met
gedetecteerde apparaten) en op OK klikt, wordt er een regeleditorvenster weergegeven met vooraf
gedefinieerde informatie (alle instellingen kunnen worden aangepast).
Regels worden in volgorde van prioriteit vermeld, waarbij regels met een hogere prioriteit boven in de lijst staan. U
kunt meerdere regels selecteren en acties toepassen, zoals deze verwijderen of omhoog of omlaag verplaatsen in
de lijst door te klikken op Boven/Omhoog/Omlaag/Beneden (pijltjestoetsen).
7.5.2 Apparaatgroepen
Het venster Apparaatgroepen bestaat uit twee delen. In het rechterdeel van het venster staat een lijst met
apparaten die tot de bijbehorende groep behoren en links in het venster staat een lijst met bestaande groepen.
Selecteer de groep met de apparaten die u wilt weergeven in het rechterdeelvenster.
U kunt verschillende groepen met apparaten maken waarop verschillende regels worden toegepast. U kunt ook één
groep met apparaten maken die zijn ingesteld op Lezen/Schrijven of Alleen-lezen. Hierdoor zorgt u ervoor dat niet-
herkende apparaten door Apparaatbeheer worden geblokkeerd als zij verbinding met uw computer proberen te
maken.
WAARSCHUWING
Een extern apparaat dat is verbonden met uw computer, kan een beveiligingsrisico vormen.
De volgende functies zijn beschikbaar:
Toevoegen
Voeg een nieuwe groep apparaten toe door de naam ervan op te geven of voeg een apparaat aan een
bestaande groep toe (en u kunt desgewenst details zoals fabrikantnaam, model en serienummer opgeven),
afhankelijk van in welk gedeelte van het venster u op de knop klikte.
Bewerken
Hiermee kunt u de naam van een geselecteerde groep of parameters voor de apparaten erin aanpassen
(fabrikant, model, serienummer).

214
Verwijderen
Hiermee verwijdert u de geselecteerde groep of het geselecteerde apparaat, afhankelijk van waar in het
venster u hebt geklikt. U kunt ook het selectievakje gebruiken naast een bepaalde regel om dit uit te schakelen.
Dit kan handig zijn als u een regel niet definitief wilt verwijderen, zodat u deze in de toekomst weer kunt
gebruiken.
Importeren
Hiermee importeert u een serienummerlijst met apparaten uit een bestand.
Invullen
Geeft met de volgende informatie een overzicht van alle huidige apparaten: apparaattype, apparaatleverancier,
model- en serienummer (indien beschikbaar). Wanneer u een apparaat selecteert (in de lijst met
gedetecteerde apparaten) en op OK klikt, wordt er een regeleditorvenster weergegeven met vooraf
gedefinieerde informatie (alle instellingen kunnen worden aangepast).
Kl ik op OK als u klaar bent met aanpassen. Klik op Annuleren om het venster Apparaatgroepen te verlaten zonder
uw wijzigingen op te slaan.
OPMERKING
Houd er rekening mee dat niet alle rechten (acties) beschikbaar zijn voor alle apparaattypen. Als een apparaat
opslagruimte heeft, zijn alle vier de acties beschikbaar. Voor niet-opslagapparaten zijn slechts twee acties
beschikbaar (bijvoorbeeld de actie Alleen lezen is niet beschikbaar voor Bluetooth; dit houdt in dat Bluetooth-
apparaten alleen kunnen worden toegestaan of geblokkeerd).
7.6 Configuratie van Hulpmiddelen
U kunt geavanceerde instellingen aanpassen voor het volgende:
· Tijdvakken
· ERA/ESMC-scandoelen
· Negeermodus
· ESET CMD
· ESET RMM
· WMI-provider
· Logbestanden
· Proxyserver
· E-mailmeldingen
· Presentatiemodus
· Diagnostiek
· Cluster
7.6.1 Tijdvakken
In Regels voor apparaatbeheer worden tijdvakken gebruikt, die beperken wanneer regels worden toegepast. Maak
een tijdvak en selecteer die wanneer u nieuwe regels toevoegt of bestaande regels wijzigt (de parameter
Toepassen tijdens). Hierdoor kunt u gangbare tijdvakken definiëren (werktijd, weekend, enz.) en deze gemakkelijk
hergebruiken zonder voor elke regel tijdvakken te hoeven definiëren. Een tijdvak moet toepasbaar zijn op elk
relevant type regel dat beheer op basis van tijd ondersteunt.

215
7.6.2 Microsoft Windows® Bijwerken
Windows-updates leveren belangrijke oplossingen voor potentieel gevaarlijke beveiligingslekken en verbeteren
het algemene beveiligingsniveau van uw computer. Het is dan ook zeer belangrijk dat updates van Microsoft
Windows zo snel mogelijk worden geïnstalleerd. Afhankelijk van het waarschuwingsniveau dat u instelt, stuurt ESET
Mail Security u meldingen over ontbrekende updates. De volgende niveaus zijn beschikbaar:
· Geen updates: er worden geen systeemupdates aangeboden als download.
· Optionele updates: updates gemarkeerd als lage prioriteit en hoger worden aangeboden als download.
· Aanbevolen updates: updates gemarkeerd als normale prioriteit en hoger worden aangeboden als download.
· Belangrijke updates: updates gemarkeerd als belangrijke prioriteit en hoger worden aangeboden als
download.
· Essentiële updates: alleen essentiële updates worden aangeboden als download.
Kl ik op OK om de wijzigingen op te slaan. Het venster Systeemupdates wordt weergegeven nadat de status is
gecontroleerd op de updateserver. Informatie over systeemupdates is mogelijk niet direct beschikbaar na het
opslaan van wijzigingen.
7.6.3 ESET CMD
Dit is een functie die geavanceerde ecmd-opdrachten mogelijk maakt. Hiermee kunt u instellingen met behulp van
de opdrachtregel (ecmd.exe) exporteren en importeren. Tot nu toe was het alleen mogelijk om instellingen te
exporteren met de grafische gebruikersinterface. De ESET Mail Security-configuratie kan worden geëxporteerd naar
een .xml-bestand.
Wanneer u ESET CMD hebt ingeschakeld, zijn er twee autorisatiemethodes beschikbaar:
· Geen: geen autorisatie. Wij raden deze methode niet aan, omdat dit het importeren van niet-ondertekende
configuraties toestaat, wat een potentieel gevaar vormt.
· Wachtwoord voor geavanceerde instellingen: er is een wachtwoord vereist om een configuratie te
importeren uit een .xml-bestand. Dit bestand moet zijn ondertekend (zie 'Een .xml-configuratiebestand
ondertekenen' hieronder). Het wachtwoord dat is ingesteld in Toegangsinstellingen, moet worden
opgegeven voordat er een nieuwe configuratie kan worden geïmporteerd. Als u toegangsinstellingen niet
hebt ingeschakeld, komt uw wachtwoord niet overeen of is het .xml-configuratiebestand niet ondertekend
en wordt de configuratie niet geïmporteerd.
Nadat ESET CMD is ingeschakeld, kunt u de opdrachtregel gebruiken om ESET Mail Security-configuraties te
importeren of exporteren. U kunt dit handmatig doen of een script maken voor automatische doeleinden.
BELANGRIJK
Als u geavanceerde ecmd-opdrachten wilt gebruiken, moet u deze uitvoeren met beheerdersrechten of een
Windows-opdrachtprompt (cmd) openen met behulp van Als Administrator uitvoeren. Anders ziet u het
bericht Error executing command.. Ook wanneer u een configuratie exporteert, moet de doelmap bestaan. De
exportopdracht werkt ook als de ESET CMD-instelling is uitgeschakeld.
VOORBEELD
Opdracht instellingen exporteren:
ecmd /getcfg c:\config\settings.xml

216
Opdracht instellingen importeren:
ecmd /setcfg c:\config\settings.xml
OPMERKING
Geavanceerde ecmd-opdrachten kunnen alleen lokaal worden uitgevoerd. De clienttaak Opdracht uitvoeren
met ESET Security Management Center werkt niet.
Een .xml-configuratiebestand ondertekenen:
1. Uitvoerbaar XmlSignTool-bestand downloaden.
2. Open Windows Opdrachtprompt (cmd) met Als administrator uitvoeren.
3. Navigeer naar de locatie van xmlsigntool.exe
4. Voer een opdracht uit om het .xml-configuratiebestand te ondertekenen. Syntaxis: xmlsigntool /version
1|2 <xml_file_path>
BELANGRIJK
De waarde van de parameter /version hangt af van de versie van uw ESET Mail Security. Gebruik /version 2
voor ESET Mail Security 7 en nieuwer.
5. Voer het wachtwoord voor Geavanceerde instellingen in voer het daarna nog een keer in wanneer hier door
XmlSignTool naar wordt gevraagd. Uw .xml-configuratiebestand is nu ondertekend en kan worden gebruikt
om een ander exemplaar van ESET Mail Security te importeren met ESET CMD en de
wachtwoordautorisatiemethode.
VOORBEELD
De geëxporteerde configuratiebestandopdracht ondertekenen: xmlsigntool /version 2 c:\config
\settings.xml

217
OPMERKING
Als uw wachtwoord voor Toegangsinstellingen wordt gewijzigd en u een configuratie wilt importeren die
eerder met een oud wachtwoord is ondertekend, kunt u het .xml-configuratiebestand opnieuw ondertekenen
met uw huidige wachtwoord. Hierdoor kunt u een ouder configuratiebestand gebruiken zonder dat u dit
voorafgaand aan het importeren hoeft te exporteren naar een andere computer waarop ESET Mail Security
wordt uitgevoerd.
7.6.4 ESET RMM
Remote Monitoring and Management (RMM) is het proces van supervisie en beheer van softwaresystemen (zoals
op pc's, servers en mobiele apparaten) door middel van een lokaal geïnstalleerde agent die door een
managementserviceprovider kan worden benaderd.
RMM inschakelen
Hiermee wordt de opdracht Remote Monitoring and Management ingeschakeld. U moet beheerdersrechten
hebben om het RMM-hulpprogramma te gebruiken.
Werkmodus
Selecteer de werkmodus van RMM in het vervolgkeuzemenu:
· Alleen veilige bewerkingen
· Alle bewerkingen
Autorisatiemethode
Stel de RMM-autorisatiemethode in het vervolgkeuzemenu in:
· Geen: er wordt geen toepassingspadcontrole uitgevoerd. U kunt ermm.exe vanuit elke toepassing uitvoeren
· Toepassingspad: geef op welke toepassing door ermm.exe kan worden uitgevoerd
De standaardinstallatie van ESET Endpoint Security bevat het bestand ermm.exe, dat zich bevindt in ESET Mail
Security (standaardpad is c:\Program Files\ESET\ESET Mail Security). ermm.exe wisselt gegevens uit met RMM
Plugin, die met RMM Agent communiceert en met RMM Server is verbonden.
· ermm.exe: opdrachtregelhulpprogramma ontwikkeld door ESET waarmee Endpoint-producten en
communicatie met RMM Plugin kunnen worden beheerd.
· RMM Plugin: een toepassing van een derde die lokaal wordt uitgevoerd op het Endpoint Windows-systeem.
Plugin is ontworpen om met een specifieke RMM Agent (bijvoorbeeld alleen Kaseya) en met ermm.exe te
communiceren.
· RMM Agent: een toepassing van een derde (bijvoorbeeld van Kaseya) die lokaal wordt uitgevoerd op het
Endpoint Windows-systeem. Agent communiceert met RMM Plugin en met RMM Server.
· RMM Server: wordt als service uitgevoerd op een server van een derde. Ondersteunde RMM-systemen zijn
afkomstig van Kaseya, Labtech, Autotask, Max Focus en Solarwinds N-able.
7.6.5 WMI-provider
Windows Management Instrumentation (WMI) is de Microsoft-implementatie van Web-Based Enterprise
Management (WBEM). Dit is een initiatief van de industrie om een standaardtechnologie te ontwikkelen die in een
bedrijfsomgeving toegang geeft tot beheerinformatie.
Zie http://msdn.microsoft.com/en-us/library/windows/desktop/aa384642(v=vs.85).aspx voor meer informatie
over WMI
WMI-provider van ESET
Het doel van de WMI-provider van ESET is om ESET-producten op afstand in een bedrijfsomgeving te kunnen
bewaken zonder dat daarvoor specifieke software of hulpmiddelen van ESET nodig zijn. Door basisinformatie over
het product, de status en statistieken via WMI beschikbaar te stellen, beschikken Administrators over veel meer

218
mogelijkheden om ESET-producten te bewaken. Administrators kunnen de toegangsmethoden gebruiken die WMI
mogelijk maakt (opdrachtregel, scripts en controlehulpmiddelen van derden) om de status van hun ESET-producten
te bewaken.
De huidige implementatie biedt alleen-lezentoegang tot basisinformatie over producten, geïnstalleerde functies
en hun beveiligingsstatus, statistieken van afzonderlijke scanners, en productlogbestanden.
De WMI-provider maakt het gebruik mogelijk van de Windows WMI-standaardinfrastructuur en
standaardhulpmiddelen waarmee de status van producten en productlogboeken kan worden gelezen.
7.6.5.1 Opgegeven gegevens
Alle WMI-klassen met betrekking tot ESET-producten bevinden zich in de naamruimte 'hoofdmap\ESET'. De
volgende klassen, die hieronder uitvoeriger worden beschreven, zijn momenteel geïmplementeerd:
Algemeen
· ESET_Product
· ESET_Features
· ESET_Statistics
Logbestanden
· ESET_ThreatLog
· ESET_EventLog
· ESET_ODFileScanLogs
· ESET_ODFileScanLogRecords
· ESET_ODServerScanLogs
· ESET_ODServerScanLogRecords
· ESET_HIPSLog
· ESET_URLLog
· ESET_DevCtrlLog
· ESET_GreylistLog
· ESET_MailServeg
· ESET_HyperVScanLogs
· ESET_HyperVScanLogRecords
De klasse ESET_Product
Er kan slechts één exemplaar van de klasse ESET_Product zijn. Eigenschappen van deze klasse verwijzen naar de
basisinformatie over uw geïnstalleerde ESET-product:
· ID : producttype-id, bijvoorbeeld 'emsl'
· Name: naam van het product, bijvoorbeeld "ESET Mail Security"
· FullName: naam van het product, bijvoorbeeld "ESET Mail Security voor IBM Domino"
· Version: versie van het product, bijvoorbeeld '6.5.14003.0'
· VirusDBVersion: versie van de virusdatabase, bijvoorbeeld "14533 (20161201)"
· VirusDBLastUpdate: tijdstempel van de laatste update van de virusdatabase. De tekenreeks bevat het
tijdstempel in WMI-notatie voor datum en tijd, bijvoorbeeld '20161201095245.000000+060'
· LicenseExpiration: tijd waarop licentie verloopt. De tekenreeks bevat het tijdstempel in WMI-notatie voor
datum en tijd
· KernelRunning: booleaanse waarde die aangeeft of de ekrn-service op de computer wordt uitgevoerd,
bijvoorbeeld 'TRUE'
· StatusCode: getal dat de beveiligingsstatus van het product aangeeft: 0 - Groen (OK), 1 - Geel (waarschuwing),
2 - Rood (fout)
· StatusText: bericht dat de reden beschrijft waarom de statuscode niet nul is; indien nul, is er geen bericht.
De klasse ESET_Features

219
De klasse ESET_Features heeft meerdere exemplaren, afhankelijk van het aantal productfuncties. Elk exemplaar
bevat:
· Name: naam van de functie (lijst met namen vindt u hieronder)
· Status: status van de functie: 0 - inactief, 1 - uitgeschakeld, 2 - ingeschakeld
Een lijst met tekenreeksen die momenteel herkende productfuncties vertegenwoordigen:
· CLIENT_FILE_AV: real-time antivirusbeveiliging van bestandssysteem
· CLIENT_WEB_AV: antivirusbeveiliging voor client op het web
· CLIENT_DOC_AV: antivirusbeveiliging voor documenten op client
· CLIENT_NET_FW: persoonlijke firewall op client
· CLIENT_EMAIL_AV: antivirusbeveiliging voor e-mail op client
· CLIENT_EMAIL_AS: antispambeveiliging voor e-mail op client
· SERVER_FILE_AV: real-time antivirusbeveiliging voor bestanden op het beveiligde bestandsserverproduct,
bijvoorbeeld bestanden in de inhoudsdatabase van SharePoint in het geval van ESET Mail Security
· SERVER_EMAIL_AV: antivirusbeveiliging van e-mail van het beveiligde serverproduct, bijvoorbeeld e-mails in
MS Exchange of IBM Domino
· SERVER_EMAIL_AS: antispambeveiliging van e-mail van het beveiligde serverproduct, bijvoorbeeld e-mails in
MS Exchange of IBM Domino
· SERVER_GATEWAY_AV: antivirusbeveiliging voor beveiligde netwerkprotocollen op de gateway
· SERVER_GATEWAY_AS: antispambeveiliging voor beveiligde netwerkprotocollen op de gateway
De klasse ESET_Statistics
De klasse ESET_Statistics heeft meerdere exemplaren, afhankelijk van het aantal scanners in het product. Elk
exemplaar bevat:
· Scanner: tekenreekscode voor de specifieke scanner, bijvoorbeeld 'CLIENT_FILE'
· Total: totaal aantal gescande bestanden
· Infected: aantal geïnfecteerde bestanden dat is gevonden
· Cleaned: aantal opgeschoonde bestanden
· Timestamp: tijdstempel van de laatste wijziging van de statistieken. In WMI-notatie voor datum en tijd,
bijvoorbeeld '20130118115511.000000+060'
· ResetTime: tijdstempel van wanneer de statistiekenteller opnieuw is ingesteld. In WMI-notatie voor datum
en tijd, bijvoorbeeld '20130118115511.000000+060'
Lijst met tekenreeksen die momenteel herkende scanners vertegenwoordigen:
· CLIENT_FILE
· CLIENT_EMAIL
· CLIENT_WEB
· SERVER_FILE
· SERVER_EMAIL
· SERVER_WEB
De klasse ESET_ThreatLog
De klasse ESET_ThreatLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord van het
logbestand met gedetecteerde bedreigingen. Elk exemplaar bevat:
· ID: unieke id van deze scanlogrecord
· Timestamp: tijdstempel van wanneer het log is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Scanner: naam van de scanner die deze loggebeurtenis heeft gemaakt
· ObjectType: type object dat deze loggebeurtenis heeft geproduceerd

220
· ObjectName: naam van object dat deze loggebeurtenis heeft geproduceerd
· Threat: naam van de bedreiging die is gevonden in het object dat wordt beschreven door de eigenschappen
ObjectName en ObjectType
· Action: actie die is uitgevoerd nadat de bedreiging werd geïdentificeerd
· User: gebruikersaccount waarvoor deze loggebeurtenis is gegenereerd
· Information: aanvullende beschrijving van de gebeurtenis
· Hash: hash van het object dat deze loggebeurtenis heeft geproduceerd
ESET_EventLog
De klasse ESET_EventLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord van het
logbestand met gebeurtenissen. Elk exemplaar bevat:
· ID: unieke id van deze scanlogrecord
· Timestamp: tijdstempel van wanneer het log is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Module: naam van de module die deze loggebeurtenis heeft gemaakt
· Event: beschrijving van de gebeurtenis
· User: gebruikersaccount waarvoor deze loggebeurtenis is gegenereerd
ESET_ODFileScanLogs
De klasse ESET_ODFileScanLogs heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een record van een
bestandsscan op aanvraag. Dit komt overeen met de GUI-loglijst Computerscan op aanvraag. Elk exemplaar bevat:
· ID: unieke id van deze scanlogrecord
· Timestamp: tijdstempel van wanneer het log is gemaakt (in de WMI-notatie voor datum en tijd)
· Targets: de doelmappen/objecten van de scan
· TotalScanned: totaal aantal gescande objecten
· Infected: aantal geïnfecteerde objecten dat werd gevonden
· Cleaned: aantal opgeschoonde objecten
· Status: status van het scanproces
ESET_ODFileScanLogRecords
De klasse ESET_ODFileScanLogRecords heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord
in een van de scanlogs die worden vertegenwoordigd door exemplaren van de klasse ESET_ODFileScanLogs.
Exemplaren van deze klasse leveren logrecords van alle scans/logs op aanvraag. Wanneer slechts een exemplaar
van een bepaald scanlog is vereist, moeten deze worden gefilterd op de eigenschap LogID. Elk klasse-exemplaar
bevat:
· LogID: id van het scanlog waartoe deze record behoort (id van een van de exemplaren van de klasse
ESET_ODFileScanLogs)
· ID: unieke id van deze scanlogrecord
· Timestamp: tijdstempel van wanneer het log is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Log: het feitelijke logbericht
ESET_ODServerScanLogs
De klasse ESET_ODServerScanLogs heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt één keer
uitvoeren van de serverscan op aanvraag. Elk exemplaar bevat:
· ID: unieke id van deze scanlogrecord
· Timestamp: tijdstempel van wanneer het log is gemaakt (in de WMI-notatie voor datum en tijd)
· Targets: de doelmappen/objecten van de scan

221
· TotalScanned: totaal aantal gescande objecten
· Infected: aantal geïnfecteerde objecten dat werd gevonden
· Cleaned: aantal opgeschoonde objecten
· RuleHits: totaal aantal regelovereenkomsten
· Status: status van het scanproces
ESET_ODServerScanLogRecords
De klasse ESET_ODServerScanLogRecords heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een
logrecord in een van de scanlogs die worden vertegenwoordigd door exemplaren van de klasse
ESET_ODServerScanLogs. Exemplaren van deze klasse leveren logrecords van alle scans/logs op aanvraag. Wanneer
slechts een exemplaar van een bepaald scanlog is vereist, moeten deze worden gefilterd op de eigenschap LogID.
Elk klasse-exemplaar bevat:
· LogID: id van het scanlog waartoe deze record behoort (id van een van de exemplaren van de klasse ESET_
ODServerScanLogs)
· ID: unieke id van deze scanlogrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Log: het feitelijke logbericht
ESET_SmtpProtectionLog
De klasse ESET_SmtpProtectionLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord
van het 'Smtp protection'-logbestand. Elk exemplaar bevat:
· ID: unieke id van deze scanlogrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· HELODomain: naam van het HELO-domein
· IP: IP-adres van bron
· Sender: afzender van e-mail
· Recipient: ontvanger van e-mail
· Beveiligingstype: te gebruiken beveiligingstype
· Action: uitgevoerde actie
· Reden - Reden voor actie
· TimeToAccept: aantal minuten waarna de e-mail wordt geaccepteerd
ESET_HIPSLog
De klasse ESET_HIPSLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord van het HIPS-
logbestand. Elk exemplaar bevat:
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Application: brontoepassing
· Target: type bewerking
· Action: actie die is ondernomen door HIPS, bijvoorbeeld toestaan, weigeren, enz.
· Rule: naam van de regel die verantwoordelijk is voor de actie
· AdditionalInfo

222
ESET_URLLog
De klasse ESET_URLLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord van het log
met gefilterde websites. Elk exemplaar bevat:
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· URL: de URL
· Status: wat er met de URL is gebeurd, bijvoorbeeld 'Geblokkeerd door Webbeheer'
· Application: toepassing die de IRL heeft geprobeerd te openen
· User: gebruikersaccount waarmee de toepassing is uitgevoerd
ESET_DevCtrlLog
De klasse ESET_DevCtrlLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord van het log
van Apparaatbeheer. Elk exemplaar bevat:
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Device: apparaatnaam
· User: naam van gebruikersaccount
· UserSID: gebruikersaccount-SID
· Group: naam van gebruikersgroep
· GroupSID: Gebruikersgroep-SID
· Status: wat er met het apparaat is gebeurd, bijvoorbeeld 'Schrijven geblokkeerd'
· DeviceDetails: aanvullende info over het apparaat
· EventDetails: aanvullende info over de gebeurtenis
ESET_MailServerLog
De klasse ESET_MailServerLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord van het
log van E-mailserver. Elk exemplaar bevat:
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· IPAddr: IP-adres van bron
· HELODomain: naam van het HELO-domein
· Sender: afzender van e-mail
· Recipient: ontvanger van e-mail
· Subject: onderwerp van e-mail
· ProtectionType: beveiligingstype dat de actie heeft uitgevoerd die wordt beschreven in de huidige logrecord,
bijvoorbeeld antivirus, antispam of regels.
· Action: uitgevoerde actie
· Reason: de reden waarom de actie door het gegeven beveiligingstype is uitgevoerd op het object.
ESET_HyperVScanLogs
De klasse ESET_HyperVScanLogs heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een uitvoering van
de Hyper-V-bestandsscan. Dit komt overeen met de GUI-loglijst 'Hyper-V-scan'. Elk exemplaar bevat:

223
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· Targets: doelmachines/schijven/volumes van de scan
· TotalScanned: totaal aantal gescande objecten
· Infected: aantal geïnfecteerde objecten dat werd gevonden
· Cleaned: aantal opgeschoonde objecten
· Status: status van het scanproces
ESET_HyperVScanLogRecords
De klasse ESET_HyperVScanLogRecords heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een
logrecord in een van de scanlogs die worden vertegenwoordigd door exemplaren van de klasse
ESET_HyperVScanLogs. Exemplaren van deze klasse leveren logrecords van alle Hyper-V-scans/logs. Wanneer
slechts een exemplaar van een bepaald scanlog is vereist, moeten deze worden gefilterd op de eigenschap LogID.
Elk klasse-exemplaar bevat:
· LogID: id van het scanlog waartoe deze record behoort (id van een van de exemplaren van de klasse
ESET_HyperVScanLogs)
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Log: het feitelijke logbericht
ESET_NetworkProtectionLog
De klasse ESET_NetworkProtectionLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord
van het 'Netwerkbeveiligings'-logbestand. Elk exemplaar bevat:
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Gebeurtenis: gebeurtenis die netwerkbeveiligingsactie activeert
· Action: actie die wordt uitgevoerd door Netwerkbeveiliging
· Bron: bronadres van netwerkapparaat
· Doel: doeladres van netwerkapparaat
· Protocol: netwerkcommunicatieprotocol
· RuleOrWormName: regel- of wormnaam met betrekking tot de gebeurtenis
· Toepassing: de toepassing die de netwerkcommunicatie heeft gestart
· User: gebruikersaccount waarvoor deze loggebeurtenis is gegenereerd
ESET_SentFilesLog
De klasse ESET_SentFilesLog heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een logrecord van het
'Bestanden verzonden'-logbestand. Elk exemplaar bevat:
· ID: unieke id van deze logrecord
· Timestamp: tijdstempel van wanneer de logrecord is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Sha1: Sha-1-hash van verzonden bestand
· Bestand: verzonden bestand
· Grootte: grootte van verzonden bestand
· Categorie: categorie van verzonden bestand

224
· Reden: reden van het verzenden van het bestand
· Verzonden naar: ESET-afdeling waar het bestand naartoe is verzonden
· User: gebruikersaccount waarvoor deze loggebeurtenis is gegenereerd
ESET_OneDriveScanLogs
De klasse ESET_OneDriveScanLogs heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een uitvoering
van de OneDrive-scan. Dit komt overeen met de GUI-loglijst 'OneDrive-scan'. Elk exemplaar bevat:
· ID: unieke id van dit OneDrive-logbestand
· Timestamp: tijdstempel van wanneer het log is gemaakt (in de WMI-notatie voor datum en tijd)
· Targets: de doelmappen/objecten van de scan
· TotalScanned: totaal aantal gescande objecten
· Infected: aantal geïnfecteerde objecten dat werd gevonden
· Cleaned: aantal opgeschoonde objecten
· Status: status van het scanproces
ESET_OneDriveScanLogRecords
De klasse ESET_OneDriveScanLogRecords heeft meerdere exemplaren. Elk exemplaar vertegenwoordigt een
logrecord in een van de scanlogs die worden vertegenwoordigd door exemplaren van de klasse
ESET_OneDriveScanLogRecords. Exemplaren van deze klasse leveren logrecords van alle OneDrive-scans/logs.
Wanneer slechts een exemplaar van een bepaald scanlog is vereist, moeten deze worden gefilterd op de
eigenschap LogID. Elk exemplaar bevat:
· Log-id: id van het scanlog waartoe deze record behoort (id van een van de exemplaren van de klasse
ESET_OneDriveScanLogs)
· ID: unieke id van dit OneDrive-logbestand
· Timestamp: tijdstempel van wanneer het log is gemaakt (in de WMI-notatie voor datum en tijd)
· LogLevel: ernst van de logrecord uitgedrukt als getal in het interval [0-8]. Waarden komen overeen met de
volgende benoemde niveaus: Debug, Info-Voetnoot, Info, Info-Belangrijk, Waarschuwing, Fout,
Beveiligingswaarschuwing, Fout-Kritiek, Beveiligingswaarschuwing-Kritiek
· Log: het feitelijke logbericht
7.6.5.2 Toegang tot opgegeven gegevens
Hier volgen enkele voorbeelden van hoe u toegang kunt krijgen tot ESET WMI-gegevens vanaf de Windows-
opdrachtregel en PowerShell. Deze voorbeelden werken in principe voor alle momenteel gangbare Windows-
besturingssystemen. Er zijn echter veel andere manieren om toegang te krijgen tot gegevens met andere
scripttalen en hulpmiddelen.
Opdrachtregel zonder scripts
Kan worden gebruikt om toegang te krijgen tot diverse vooraf gedefinieerde of alle aangepaste WMI-klassen.
Volledige informatie weergeven over het product op de lokale computer:
wmic /namespace:\\root\ESET Path ESET_Product
Alleen productversienummer weergeven van het product op de lokale computer:
wmic /namespace:\\root\ESET Path ESET_Product Get Version
Volledige informatie weergeven over product op een externe computer met IP-adres 10.1.118.180:
wmic /namespace:\\root\ESET /node:10.1.118.180 /user:Administrator Path ESET_Product
PowerShell
Volledige informatie opvragen en weergeven over uw product op de lokale computer:
Get-WmiObject ESET_Product -namespace 'root\ESET'
Volledige informatie opvragen en weergeven over het product op een externe computer met IP-adres 10.1.118.180:
$cred = Get-Credential # vraagt de gebruiker naar referenties en slaat deze op in de variabele
Get-WmiObject ESET_Product -namespace 'root\ESET' -computername '10.1.118.180' -cred $cred

225
7.6.6 ERA/ESMC-scandoelen
Met deze functionaliteit kan ESET Security Management Center het scandoel (On-demand databasescan van postvak
en Hyper-V-scan) gebruiken wanneer de clienttaak Server scannen wordt uitgevoerd op een server met ESET Mail
Security. De instelling ERA/ESMC-scandoelen is alleen beschikbaar als u ESET Management Agent hebt
geïnstalleerd, anders is de optie grijs.
Wanne er u Doellijst genereren inschakelt, maakt ESET Mail Security een lijst met beschikbare scandoelen. Deze lijst
wordt periodiek gegenereerd, op basis van de door u opgegeven Updateperiode.
OPMERKING
Wanneer Doellijst genereren de eerste keer wordt ingeschakeld, kost het ESET Security Management Center
ongeveer de helft van de tijd die bij Updateperiode is opgegeven om de doellijst op te halen. Dus als
Updateperiode is ingesteld op 60 minuten, kost het ESMC ongeveer 30 minuten om de lijst met scandoelen te
ontvangen. Als u wilt dat ESET Security Management Center de lijst eerder verzamelt, stel de updateperiode
dan in op een kleinere waarde. U kunt dit later altijd verhogen.
Wanneer ESET Security Management Center een Serverscan-clienttaak uitvoert, wordt de lijst verzameld en wordt u
gevraagd de scandoelen voor Hyper-V-scan op die specifieke server te selecteren.
7.6.7 Negeermodus
Als u ESET Security Management Center-beleid hebt toegepast op ESET Mail Security, ziet u het pictogram van een
hangslot in plaats van de schakelaar Inschakelen/uitschakelen op de pagina Instellingen en het pictogram van
een hangslot naast de schakelaar in het venster Geavanceerde instellingen.

226
Doorgaans kunnen instellingen die zijn geconfigureerd in ESET Security Management Center-beleid niet worden
gewijzigd. Met de negeermodus kunt u deze instellingen tijdelijk ontgrendelen. U dient Negeermodus echter in te
schakelen in het ESET Security Management Center-beleid.
Meld u aan bij ESMC-webconsole , navigeer naar Beleid, selecteer en bewerk bestaand beleid dat is toegepast op
ESET Mail Security of maak nieuw beleid. Klik in Instellingen op Negeermodus, schakel deze in en configureer de
rest van de instellingen, waaronder Verificatietype (Active Directory-gebruiker of Wachtwoord).

227
Nadat het beleid is gewijzigd of nieuw beleid is toegepast op ESET Mail Security, wordt de knop Beleid negeren
weergegeven in het venster Geavanceerde instellingen.
Klik op de knop Negeren, stel de duur in en klik op Toepassen.

228
Al s u Wachtwoord als Verificatietype hebt geselecteerd, voert u het wachtwoord voor het te negeren beleid in.

229
Op het moment dat de negeermodus vervalt, keren alle configuratiewijzigingen die u hebt aangebracht terug naar
de oorspronkelijke ESET Security Management Center-beleidsinstellingen. U krijgt een melding te zien voordat het
negeren van het beleid komt te vervallen.
Met Negeren beëindigen kunt u het negeren van het beleid op elk moment beëindigen voordat het negeren komt
te vervallen. U kunt dit doen op de pagina Controle of in het venster Geavanceerde instellingen.
7.6.8 Logbestanden
In dit gedeelte kunt u de configuratie van ESET Mail Security-logboekregistratie wijzigen.
Logboekrecords
Records worden naar het logboek Gebeurtenissen (C:\ProgramData\ESET\ESET Security\Logs) geschreven en
kunnen worden bekeken in de viewer Logbestanden. Gebruik de schakelaars om een bepaalde functie in of uit te
schakelen:
Fouten met e-mailtransport in logboek registreren
Als deze optie is ingeschakeld en er problemen bij de e-mailtransportlaag optreden, worden er foutberichten
in het logboek Gebeurtenissen geschreven.
Uitzonderingen voor e-mailtransport in logboek registreren
Als er uitzonderingen bij de e-mailtransportlaag voorkomen, worden de details ervan in het logboek
Gebeurtenissen geschreven.
Logboekregistratiefilter
Produceert een aanzienlijke hoeveelheid gegevens omdat alle logopties standaard zijn ingeschakeld. Wij adviseren
een selectieve uitschakeling van de logboekregistratie van onderdelen die niet nuttig zijn of geen verband houden
met het probleem.
OPMERKING
Als u de logboekregistratie wilt starten, dient u de algemene registratie in Diagnostische logbestand op
productniveau in te schakelen in het hoofdmenu > Instellingen > Hulpmiddelen. Zodra de logboekregistratie
zelf is ingeschakeld, verzamelt ESET Mail Security uitvoerige loggegevens van in dit gedeelte ingeschakelde
functies.
Gebruik de schakelaars om een bepaalde functie in of uit te schakelen. Deze opties kunnen ook worden
gecombineerd, afhankelijk van de beschikbaarheid van individuele onderdelen in ESET Mail Security.
· Diagnostisch logbestand voor e-mailtransport
BELANGRIJK
Bij het oplossen van problemen met de databasescan die tijdens de normale werking wordt uitgevoerd,
adviseren wij om Diagnostisch logbestand voor e-mailtransport uit te schakelen. Anders kan het resulterende
logbestand vollopen en wordt analyse erg lastig.
· Registratie in diagnostisch logbestand voor Op aanvraag database scannen schrijft gedetailleerde informatie
in logbestanden, met name wanneer probleemoplossing noodzakelijk is.
· Registratie in diagnostisch clusterlogbestand: Registratie in diagnostisch clusterlogbestand maakt deel uit van
de algemene registratie in diagnostische logbestanden.

230
· Registratie in diagnostisch logbestand van antispam-engine: wanneer u problemen moet oplossen, ziet u
gedetailleerde antispam-engine-informatie in de logbestanden. Er wordt voor diagnostische doeleinden
gedetailleerde informatie over de antispam-engine in het logbestand geschreven. De antispam-engine
gebrui kt de Gebeurtenislogbestanden (he t be stand warnlog.dat) niet en dit bestand kan om die reden niet
worden weergegeven in de viewer voor logbestanden. Deze optie schrijft records rechtstreeks in een
speciaal tekstbestand (bijvoorbeeld C:\ProgramData\ESET\ESET Mail Security\Logs\antispam.0.log), zodat
alle diagnostische antispam-enginegegevens op één plaats worden bewaard. Op deze manier worden de
prestaties van ESET Mail Security niet negatief beïnvloed bij veel e-mailverkeer.
Logbestanden
Definieer hoe de logbestanden worden beheerd. Dit is met name belangrijk om te voorkomen dat de schijf
volloopt. Met standaardinstellingen kunt u oudere logbestanden verwijderen om schijfruimte te besparen.
Records automatisch verwijderen na (dagen)
Vermeldingen in logbestanden die ouder zijn dan het opgegeven aantal dagen, worden verwijderd.
Automatisch oude records verwijderen als grootte van logbestand wordt overschreden
Als het logbestand de waarde bij Max. logbestandgrootte [MB] overschrijdt, worden oude logrecords
ve rwi jde rd tot Verminderde logbestandgrootte [MB] is bereikt.
Back-up maken van automatisch verwijderde records
Van automatisch verwijderde logrecords en bestanden wordt een back-up gemaakt. Deze wordt in de
opgegeven map neergezet en eventueel als zip-bestand gecomprimeerd.
Back-up maken van diagnostische logbestanden
Er wordt een back-up gemaakt van automatisch verwijderde diagnostische logbestanden. Indien niet
ingeschakeld, wordt er geen back-up van diagnostische logbestanden gemaakt.
Back-upmap
Map waarin back-ups van logbestanden worden opgeslagen. U kunt back-ups van logbestanden als zip
comprimeren.
Logbestanden automatisch optimaliseren
Indien ingeschakeld, worden logbestanden automatisch gedefragmenteerd als het fragmentatiepercentage
hoger is dan de waarde die is opgegeven in het veld Als het aantal ongebruikte records groter is dan (%). Klik
op Optimaliseren om de defragmentatie van de logbestanden te starten. Alle lege logboekvermeldingen
worden verwijderd om de prestaties te verbeteren en de verwerking van logbestanden te versnellen. Deze
verbetering wordt vooral waargenomen als de logbestanden een groot aantal vermeldingen bevatten.
Tekstprotocol inschakelen
Opslag van logboeken inschakelen in een andere bestandsindeling dan voor Logbestanden:
· Doelmap: de map waarin logbestanden worden opgeslagen (alleen van toepassing op Tekst/CSV). Elk
logboekgedeelte heeft een eigen bestand met een vooraf gedefinieerde bestandsnaam (bijvoorbeeld
virlog.txt voor het gedeelte Gedetecteerde bedreigingen van logboekbestanden, als u platte tekst gebruikt
om logboeken op te slaan).
· Type: als u de bestandsindeling Tekst selecteert, worden logboeken opgeslagen in een tekstbestand;
gegevens worden door tabs gescheiden. Hetzelfde geldt voor de door komma's gescheiden CSV-
bestandsindeling. Als u Gebeurtenis kiest, worden logboeken opgeslagen in het Windows-
gebeurtenislogboek (kan worden bekeken via Logboeken in het Configuratiescherm) in plaats van in een
bestand.

231
· Alle logbestanden verwijderen: wist alle opgeslagen logboeken die zijn geselecteerd in het
vervolgkeuzemenu Type.
OPMERKING
Om problemen sneller te kunnen oplossen, kan het zijn dat u door ESET Technische ondersteuning wordt
gevraagd logboeken van uw computer op te sturen. Met ESET Log Collector kunt u gemakkelijk de benodigde
informatie verzamelen. Ga naar het artikel in onze kennisbank voor meer informatie over ESET Log Collector.
Logboek exporteren
Exporteren naar logbestanden voor Windows-toepassingen en -services
Hiermee kunt u records uit het beveiligingslogboek van de mailserver dupliceren naar het logboek voor
toepassingen en services. Als u het logboek voor mailserverbeveiliging wilt bekijken, opent u Windows
Gebeurtenislogboeken en navigeert u naar Logboeken Toepassingen en Services > ESET > Security >
ExchangeServer > MailProtection. ExchangeServer > MailProtection. De logboeken voor toepassingen en
services worden ondersteund op Microsoft Windows Server 2008 R2 SP1 en nieuwer.
Exporteren naar syslog-server
U kunt logboeken van Beveiliging van e-mailserver in CEF-indeling (Common Event Format) naar syslogserver
laten dupliceren. CEF is een gestandaardiseerde, uitbreidbare, tekstgebaseerde indeling, die kan worden
gebruikt om het verzamelen en aggregeren van gegevens voor latere analyse door een bedrijfsbeheersysteem
te vergemakkelijken. In dit geval kunt u de indeling gebruiken met SIEM- (Security Information and Event
Management) en logboekbeheeroplossingen zoals Micro Focus ArcSight. Zie Sysloggebeurtenissen koppelen
voor details van geëxporteerde gebeurtenisvelden en beschrijvingen.
Serveradres
Voer het IP-adres of de hostnaam van de server in. In het geval van ArcSight geeft u de server waarop
SmartConnector is geïnstalleerd op.
Protocol
Selecteer het protocol dat wordt gebruikt: TCP of UDP.
Poort
De standaardwaarde is 514 voor beide protocollen.
Exporteren naar bestand
Hiermee kunnen de logboeken lokaal in CEF-indeling naar een bestand worden geëxporteerd. De
opslagcapaciteit voor logboeken is beperkt. Daarom wordt logboekregistratie in lusvorm gebruikt. Records
worden achtereenvolgens in de bestanden geschreven (van mailserver.0.log tot mailserver.9.log). De
nieuwste records worden opgeslagen in mailserver.0.log. Zodra de maximale grootte is bereikt, wordt het
oudste be stand mailserver.9.log verwijderd en wordt de naam van de overige logboekbestanden
achtereenvolgens gewijzigd (de naam mailserver.0.log wordt gewijzigd in mailserver.1.log en zo verder).
Bestandspad
Standaardpad is C:\ProgramData\ESET\ESET Security\Logs. U kunt de locatie indien gewenst wijzigen.

232
7.6.8.1 Sysloggebeurtenissen koppelen
The following tables show ESET Mail Security event mapping to ArcSight data fields. You can use these tables as a
reference of what is being fed to ArcSight via SmartConnector.
Header
Device
Vendor
"ESET"
Device
Product
"EMSX"
"EMSX" or "ESET Mail Security for MS Exchange Server"
Device
Version
e.g. "7.1.10005.0"
Device Event
Class ID
e.g. "101"
Device Event Category unique identifier:
100-199 malware
200-299 phish
300-399 spam
400-499 policy
Event Name
e.g. "MailScanResult: malware"
A brief description of what happened in the event:
MailScanResult: malware
MailScanResult: phishing link
MailScanResult: spam
MailScanResult: policy
CEF Key Name
CEF Key Full Name
(Size)
Field Description
Detailed Field Description
rt
deviceReceiptTime
Time event was
generated
The time at which the event was generated, in
milliseconds since Jan 1st 1970
src
sourceAddress
Sender's IP
IP address of the sending mail server
shost
sourceHostName
(1023)
Sender's HELO domain
HELO domain of the sending mail server
flexString1
flexString1
Message-ID
Message-ID header from the email
dhost
destinationHostNa
me (1023)
Receiving server
Hostname of the machine that received the
communication
msg
message (1023)
Message subject
Subject of the message, from the RFC5233 header
"Subject:"
suser
sourceUserName
(1023)
SMTP sender
SMTP sender of the email (MAIL FROM)
duser
destinationUserNa
me (1023)
SMTP recipient(s)
SMTP recipient(s) of the email (RCPT TO)
act
deviceAction (63)
Action taken
Action taken (cleaned, quarantined, etc.)

233
CEF Key Name
CEF Key Full Name
(Size)
Field Description
Detailed Field Description
cat
deviceEventCatego
ry (1023)
Detection category
Most significant detection (malware >> phish >>
spam >> SPF/DKIM >> policy)
sourceServiceNa
me
sourceServiceNam
e
Type of protection
"SMTP Transport agent", "On-demand database
scan", etc.
deviceExternalId
deviceExternalId
Engine version
Anti-Malware engine version, antispam engine
version, e.g. "18620,7730"
cs1
deviceCustomStrin
g1
Anti-Malware result
Result of Anti-Malware scan, including threat
name
cs1Label
deviceCustomStrin
g1Label
"Anti-Malware result"
cs2
deviceCustomStrin
g2
Antispam result
Result of Antispam scan, including reason for
marking as spam
cs2Label
deviceCustomStrin
g2Label
"Antispam result"
cs3
deviceCustomStrin
g3
Anti-Phishing result
Result of Anti-Phishing scan, including detected
URL
cs3Label
deviceCustomStrin
g3Label
"Anti-Phishing result"
cs4
deviceCustomStrin
g4
SPF/DKIM/DMARC result
Result of SPF/DKIM/DMARC check, in RFC7601
format
cs4Label
deviceCustomStrin
g4Label
"SPF/DKIM/DMARC
result"
cs5
deviceCustomStrin
g5
"From:" sender
Sender address from RFC5322 header "From:"
cs5Label
deviceCustomStrin
g5Label
"From header"
cs6
deviceCustomStrin
g6
"To:" and "Cc:"
recipients
Recipients addresses from RFC5322 headers "To:"
and "Cc:"
cs6Label
deviceCustomStrin
g6Label
"To and Cc headers"
fname
filename (1023)
Attachment name
Name of the first detected attachment
fileHash
fileHash (255)
Attachment hash
Hash of the first detected attachment
fsize
fileSize
Attachment size
Size of the first detected attachment

234
CEF Key Name
CEF Key Full Name
(Size)
Field Description
Detailed Field Description
reason
reason (1023)
Rule/policy activated
Name of the policy triggered by the email or it's
content
ESETEMSXFileDet
ails
ESETEMSXFileDetai
ls
File details
Information about all detected attachments, their
names, hashes and sizes
Optional
CEF Key
Name
CEF Key Full Name
(Size)
Field Description
Detailed Field Description
end
endTime
Time event has
ended
The time at which the activity ended, in milliseconds since Jan
1st 1970. Useful only if sand boxing technology is used, i.e.
ESET Dynamic Threat Defense.
dtz
deviceTimeZone
(255)
Timezone of the
server
request
requestURL
Detected URL
Malign or blacklisted URL extracted from mail body or mail
headers.
Note: ESET Mail Security does not provide single URL in logs
due to the fact that multiple URL's can be detected in email
messages by various detection components.
7.6.9 Proxyserver
In grote LAN-netwerken kan de internetverbinding van uw computer via een proxyserver tot stand worden
gebracht. In dat geval moeten de volgende instellingen worden opgegeven. Als u de instellingen niet definieert,
kunnen er geen automatische updates voor het programma worden uitgevoerd. In ESET Mail Security zijn de
instellingen van de proxyserver beschikbaar in twee verschillende onderdelen binnen het venster Geavanceerde
instellingen (F5):
1. Geavanceerde instellingen (F5) > Bijwerken > Profielen > Updates > Verbindingsopties > HTTP-proxy
Deze instelling is van toepassing op het gegeven updateprofiel en wordt aanbevolen voor laptops die vaak
modules van verschillende locaties ontvangen.
2. Geavanceerde instellingen (F5) > Hulpmiddelen > Proxyserver
Als u de proxyserver op dit niveau opgeeft, definieert u algemene proxyserverinstellingen voor ESET Mail
Security als geheel. Deze parameters worden gebruikt door alle modules die verbinding met internet
maken.
U kunt instellingen voor de proxyserver op dit niveau opgeven door de schakelaar Proxyserver gebruiken in te
schakelen en vervolgens het adres van de proxyserver in te voeren in het veld Proxyserver, samen met het
poortnummer van de proxyserver.
Proxyserver vereist verificatie
Als voor netwerkcommunicatie via de proxyserver verificatie is vereist, schakel dan deze optie in en geef
Gebruikersnaam en Wachtwoord op.
Proxyserver detecteren
Kl ik op Detecteren om proxyserverinstellingen automatisch te detecteren en in te vullen. De in Internet
Explorer opgegeven parameters worden gekopieerd.

235
OPMERKING
Met deze functie worden geen verificatiegegevens opgehaald (gebruikersnaam en wachtwoord). Deze
moeten door u worden opgegeven.
Gebruik een directe verbinding wanneer de proxy server niet beschikbaar is
Als een product is geconfigureerd om HTTP-proxy te gebruiken en de proxy is onbereikbaar, omzeilt het
product de proxy en wordt direct met ESET-servers gecommuniceerd.
7.6.10 Melding
Meldingen op het bureaublad en ballontips zijn alleen informatief bedoeld en hiervoor is geen gebruikersinteractie
vereist. Ze worden weergegeven in het systeemvak rechtsonder op het scherm. Meer gedetailleerde opties, zoals
weergaveduur van meldingen en transparantie van het venster, kunnen hieronder worden aangepast. Zet de
schakelaar Geen meldingen weergeven wanneer toepassingen in de modus Volledig scherm worden uitgevoerd
aan om alle niet-interactieve meldingen te onderdrukken.
Melding over succesvolle update weergeven
Wanneer een update is toegepast, wordt er een pop-upmelding weergegeven.
Gebeurtenismeldingen via e-mail verzenden
Schakel dit in om e-mailmeldingen te activeren.
Toepassingsmeldingen
Kl ik op Bewerken om de beeldschermtoepassingsmeldingen in of uit te schakelen.
7.6.10.1 Toepassingsmeldingen
U kunt ESET Mail Security-meldingen configureren die worden weergegeven op het bureaublad en/of die per e-
mail worden verzonden.
OPMERKING
Zorg er bij e-mailmeldingen voor dat u Gebeurtenismeldingen via e-mail verzenden inschakelt in het
gedeelte Basis, ve rvol gens SMTP-server configureren inschakelt en indien nodig andere details inschakelt.
7.6.10.2 Bureaubladmeldingen
U kunt configureren hoe bedreigingswaarschuwingen en systeemmeldingen (zoals berichten over geslaagde
updates) worden afgehandeld door ESET Mail Security, bijvoorbeeld de Duur en Transparantie van de weergave van
meldingen in het systeemvak (dit is alleen van toepassing op systemen die ondersteuning bieden voor meldingen
in het systeemvak).
In het vervolgkeuzemenu Minimaal detailniveau voor weergegeven gebeurtenissen kunt u de ernst selecteren voor
waarschuwingen en meldingen. De volgende opties zijn beschikbaar:
· Diagnostisch: hiermee wordt informatie geregistreerd die nodig is om het programma en alle bovenstaande
archieven af te stemmen.
· Informatief: hiermee registreert u informatieve berichten, waaronder berichten over geslaagde updates, plus
alle bovenstaande records.
· Waarschuwingen: hiermee worden kritieke fouten en waarschuwingsberichten geregistreerd.
· Fouten: hiermee worden fouten als "Fout bij downloaden van bestand" en kritieke fouten geregistreerd.
· Kritiek: hiermee worden alleen kritieke fouten geregistreerd (zoals fouten bij het starten van
antivirusbeveiliging).

236
In het veld In systemen met meerdere gebruikers meldingen weergeven op het scherm van deze gebruiker kunt u
opgeven welke gebruiker in systemen met meerdere gebruikers meldingen van het systeem en andere meldingen
moet ontvangen. Gewoonlijk is dit een systeem- of netwerkbeheerder. Deze optie is met name handig voor
terminalservers, mits alle systeemmeldingen naar de Administrator worden verzonden.
7.6.10.3 E-mailmeldingen
ESET Mail Security kan automatisch meldingen per e-mail verzenden zodra een gebeurtenis met het geselecteerde
detailniveau plaatsvindt.
OPMERKING
SMTP-servers met TLS-codering worden ondersteund door ESET Mail Security.
SMTP-server
De naam van de SMTP-server die wordt gebruikt om waarschuwingen en meldingen te verzenden. Dit is doorgaans
de naam van uw Microsoft Exchange Server.
Gebruikersnaam en wachtwoord
Als voor de SMTP-server verificatie is vereist, moet u een geldige gebruikersnaam en een geldig wachtwoord in
deze velden invullen, zodat toegang tot de SMTP-server kan worden verkregen.
Adres van afzender
Voer het adres in van de afzender dat wordt weergegeven in de koptekst van e-mailmeldingen. Dit is wat de
ontvanger ziet in het veld Van.
Adres van ontvanger
Voer het e-mailadres in van de ontvanger (Aan) bij wie meldingen worden bezorgd.
TLS inschakelen
Hiermee kunt u waarschuwingen en meldingen inschakelen die door TLS-codering worden ondersteund.
E-mailinstellingen
Minimaal detailniveau voor meldingen
Geeft het minimale detailniveau aan van meldingen die worden verzonden.
Interval waarna nieuwe meldingen per e-mail worden verzonden (min)
Interval in minuten waarna nieuwe meldingen per e-mail worden verzonden. Stel deze waarde in op 0 als u wilt
dat deze meldingen direct worden verzonden.
Elke melding in een afzonderlijke e-mail verzenden
Indien ingeschakeld, ontvangt de ontvanger een nieuw e-mailbericht voor elke afzonderlijke melding. Dit kan
resulteren in veel e-mailberichten die in korte tijd worden ontvangen.
Berichtindeling
De communicatie tussen het programma en een externe gebruiker of systeembeheerder verloopt via e-mails of
LAN-berichten (door middel van de Windows-berichtenservice). De standaardindeling van de
waarschuwingsberichten en meldingen is geschikt voor de meeste situaties. Het kan echter gebeuren dat u de
berichtindeling van gebeurtenisberichten wilt wijzigen.
Indeling van gebeurtenisberichten
De indeling van gebeurtenisberichten die op externe computers worden weergegeven.
Indeling van waarschuwingsberichten bij bedreigingen

237
Waarschuwingen en meldingen over bedreigingen hebben een vooraf gedefinieerde standaardindeling. U kunt
deze indeling beter niet veranderen. In bepaalde omstandigheden (als u bijvoorbeeld over een
geautomatiseerd e-mailverwerkingssysteem beschikt) kan het zijn dat u de indeling van dergelijke berichten
wilt wijzigen.
Sleutelwoorden (tekenreeksen tussen procenttekens (%) worden in het bericht vervangen door de feitelijke
informatie voor de desbetreffende waarschuwing. De volgende sleutelwoorden zijn beschikbaar:
· %TimeStamp%: de datum en tijd van de gebeurtenis.
· %Scanner%: de desbetreffende module.
· %ComputerName%: de naam van de computer waarop de waarschuwing is gegenereerd.
· %ProgramName%: het programma dat de waarschuwing heeft gegenereerd.
· %InfectedObject%: de naam van het geïnfecteerde bestand, bericht, enzovoort.
· %VirusName%: de identificatie van de infectie.
· %ErrorDescription%: beschrijving van een niet-virusgebeurtenis.
De sl eute lw oorde n %InfectedObject% en %VirusName% worden alleen gebruikt in bedreigingswaarschuwingen,
en %ErrorDescription% wordt alleen gebruikt in gebeurtenisberichten.
Tekenset
U kunt coderen in het vervolgkeuzemenu kiezen. Het e-mailbericht wordt geconverteerd volgens de
geselecteerde tekencodering.
Geciteerd-afdrukbare codering gebruiken
De bron van het e-mailbericht wordt gecodeerd in Q.P. (Quoted-printable), een indeling waarbij ASCII-tekens
worden gebruikt en speciale taalgebonden tekens correct in 8-bits indeling (áéíóú) per e-mail kunnen worden
verzonden.
7.6.10.4 Aanpassing
Dit bericht wordt weergegeven in de voettekst van alle geselecteerde meldingen.
Standaardmeldingsbericht
Een standaardbericht dat wordt weergegeven in de voettekst van meldingen.
Bedreigingen
Meldingen over malware niet automatisch sluiten
Zorgt ervoor dat malwaremeldingen op het scherm blijven staan tot u deze handmatig sluit.
Standaardbericht gebruiken
U kunt standaardberichten uitschakelen en aangepaste Meldingen over bedreigingen opgeven die worden
weergegeven wanneer een bedreiging is geblokkeerd.
Meldingsbericht over bedreigingen
Geef een aangepast bericht op om weer te geven wanneer er een bedreiging wordt geblokkeerd.
7.6.11 Presentatiemodus
De Presentatiemodus is een functie voor gebruikers die niet willen dat het gebruik van hun software wordt
onderbroken, die niet willen dat er pop-upvensters verschijnen en die willen dat de belasting van de CPU minimaal
is. De Presentatiemodus kan ook worden gebruikt tijdens presentaties die niet mogen worden verstoord door
antivirusactiviteit. Indien ingeschakeld, worden alle pop-upvensters uitgeschakeld en worden alle geplande taken
niet uitgevoerd. Systeembeveiliging wordt nog steeds uitgevoerd op de achtergrond, maar er is geen interactie van
de gebruiker vereist.
Presentatiemodus automatisch inschakelen wanneer toepassingen in de modus Volledig scherm worden
uitgevoerd

238
Presentatiemodus wordt automatisch geactiveerd telkens wanneer u een toepassing in een volledig scherm
uitvoert. Wanneer Presentatiemodus is ingeschakeld, ziet u geen meldingen of een statuswijziging van uw ESET
Mail Security.
Presentatiemodus automatisch uitschakelen na
Ook kunt u de tijdsduur opgeven waarna de Presentatiemodus automatisch moet worden uitgeschakeld.
7.6.12 Diagnostiek
Diagnostiek zorgt voor crashdumps van ESET-toepassingsprocessen (bijvoorbeeld ekrn). Als een toepassing
vastloopt, wordt er een dump gegenereerd. Aan de hand hiervan kunnen ontwikkelaars diverse ESET Mail Security
problemen opsporen en verhelpen.
Klik op het vervolgkeuzemenu naast Dumptype en selecteer een van de drie beschikbare opties:
· Uitschakelen: om deze functie uit te schakelen.
· Mini (standaardinstelling): hiermee wordt de kleinst mogelijke hoeveelheid nuttige informatie vastgelegd
waarmee kan worden geïdentificeerd waarom de toepassing onverwachts vastliep. Dit type dumpbestand
kan handig zijn wanneer er beperkte ruimte beschikbaar is. Omdat er echter maar weinig informatie in is
opgenomen, worden fouten die niet rechtstreeks werden veroorzaakt door de thread die werd uitgevoerd op
het moment van het probleem, mogelijk niet ontdekt door een analyse van dit bestand.
· Volledig: Hiermee wordt de volledige inhoud van het systeemgeheugen vastgelegd wanneer een toepassing
onverwacht stopt. Een volledige geheugendump kan gegevens bevatten van processen die werden
uitgevoerd op het moment dat de geheugendump werd gemaakt.
Doelmap
Map waarin het dumpbestand bij het vastlopen wordt gegenereerd.
Diagnostiekmap openen
Kl ik op Openen om deze map in een nieuw Windows Verkenner-venster te openen.
Diagnostische dump maken
Kl ik op Maken om diagnostische dumpbestanden te maken in de doelmap.
Geavanceerde logging
Geavanceerd logbestand voor Apparaatbeheer inschakelen
Alle gebeurtenissen registreren die plaatsvinden in Apparaatbeheer om diagnose en oplossen van problemen
mogelijk te maken.
Geavanceerde logbestanden licensieverlening inschakelen
Alle productcommunicatie met licentieserver registreren.
Geavanceerde logbestanden voor netwerkbeveiliging inschakelen
Registreer alle netwerkgegevens die in PCAP-indeling door netwerkbeveiliging worden verwerkt, om de
ontwikkelaars te helpen problemen met netwerkbeveiliging te diagnosticeren en op te lossen.
Geavanceerd logbestand voor besturingssysteem inschakelen
Er wordt aanvullende informatie verzameld over het besturingssysteem, zoals over actieve processen, CPU-
activiteit en schijfbewerkingen.
Geavanceerde logboekregistratie inschakelen voor Protocolfiltering
Registreer alle gegevens die in PCAP-indeling door de engine van Protocolfiltering worden verwerkt, om
ontwikkelaars te helpen problemen met Protocolfiltering te diagnosticeren en op te lossen.
Geavanceerde logbestanden voor update-engine inschakelen

239
Registreer alle gebeurtenissen die tijdens het updateproces plaatsvinden. Hiermee kunnen ontwikkelaars
problemen diagnosticeren en oplossen die betrekking hebben op de update-engine.
Technische ondersteuning
Systeemconfiguratiegegevens verzenden
Selecteer Altijd verzenden als u niet wilt worden gevraagd voordat u uw ESET Mail Security-
configuratiegegevens naar de klantenservice verzendt, of gebruik Vragen alvorens te verzenden.
7.6.13 Cluster
De optie Cluster inschakelen wordt automatisch ingeschakeld als het ESET-cluster is geconfigureerd. U kunt dit
handmatig uitschakelen in het venster Geavanceerde instellingen (F5)door te klikken op het schakelpictogram
(bijvoorbeeld als u de configuratie wilt wijzigen zonder dat dit gevolgen heeft voor alle knooppunten in het ESET-
cluster). Deze schakelaar schakelt alleen de ESET-clusterfunctionaliteit in of uit. Als u het cluster wilt instellen of
verwijderen, gebruikt u de Clusterwizard of de optie Verwijderen, die u vindt in het gedeelte Hulpmiddelen >
Cluster van het hoofdvenster.
ESET-cluster niet geconfigureerd en uitgeschakeld:
ESET-cluster op de juiste wijze geconfigureerd met de details en opties ervan:

240
7.7 Gebruikers
Configureer het gedrag van de grafische gebruikersinterface (GUI) van ESET Mail Security. U kunt de vormgeving en
effecten van het programma aanpassen.
Elementen van gebruikersinterface
Gebruik het vervolgkeuzemenu GUI-startmodus om een keuze te maken uit de volgende startmodi voor de
grafische gebruikersinterface (GUI):
· Volledig: de volledige grafische gebruikersinterface wordt weergegeven.
· Terminal: er worden geen meldingen of waarschuwingen weergegeven. De grafische gebruikersinterface kan
alleen door de Administrator worden gestart. De gebruikersinterface moet worden ingesteld op Terminal als
grafische elementen de prestaties van uw computer vertragen of andere problemen veroorzaken. U kunt
eventueel ook de grafische gebruikersinterface op een terminalserver uitschakelen. Voor meer informatie
over ESET Mail Security geïnstalleerd op een terminalserver verwijzen we u naar het onderwerp GUI
uitschakelen op terminalserver.
Welkomstscherm weergeven bij opstarten
Schakel deze optie uit als u er de voorkeur aan geeft niet het welkomstscherm weer te geven wanneer de GUI
van uw ESET Mail Security wordt gestart, bijvoorbeeld tijdens het aanmelden bij het systeem.
Geluidssignaal gebruiken
ESET Mail Security speelt een geluid af als er zich een belangrijke gebeurtenis voordoet tijdens een scan,
bijvoorbeeld als er een bedreiging is ontdekt of als het scannen is voltooid.
Integreren in het contextmenu

241
Indien ingeschakeld, worden ESET Mail Security-bedieningselementen geïntegreerd in het contextmenu. Het
contextmenu wordt weergegeven wanneer u met de rechtermuisknop op een object (bestand) klikt. In het
menu staan alle acties die u kunt uitvoeren op een object.
Toepassingsstatussen
Kl ik op Bewerken om statussen te selecteren die worden weergegeven in het venster Controle. U kunt ook ESET
Security Management Center-beleid gebruiken om de statussen van uw toepassingen te configureren. Er
wordt ook een toepassingsstatus weergegeven als uw product niet is geactiveerd of als uw licentie is verlopen.
Licentie-informatie/Licentie-informatie tonen
Als deze functie is ingeschakeld, worden berichten en meldingen over uw licentie weergegeven.
Waarschuwingen en berichtvensters
Door Waarschuwingen en meldingen te configureren, kunt u het gedrag van gedetecteerde bedreigingen en
systeemmeldingen wijzigen. U kunt deze aan uw behoeften aanpassen. Als u ervoor kiest sommige meldingen
niet weer te geven, worden deze weergegeven in het gedeelte Uitgeschakelde berichten en statussen. Hier
kunt u de status ervan controleren, meer informatie weergeven of ze uit dit venster verwijderen.
Toegangsinstellingen
U kunt ongeoorloofde wijzigingen voorkomen door er met het hulpmiddel Toegangsinstellingen voor te zorgen
dat de beveiliging hoog blijft.
ESET-shell
U kunt toegangsrechten voor productinstellingen, functies en gegevens configureren via eShell door het
Uitvoeringsbeleid voor ESET-shell te wijzigen.
Systeemvakpictogram
Alle instellingen in dit gedeelte herstellen
7.7.1 Waarschuwingen en berichtvensters
U kunt configureren hoe bedreigingswaarschuwingen en systeemmeldingen (zoals berichten over geslaagde
updates) worden afgehandeld door ESET Mail Security, bijvoorbeeld de Duur en Transparantie van de weergave van
meldingen in het systeemvak (dit is alleen van toepassing op systemen die ondersteuning bieden voor meldingen
in het systeemvak).
Waarschuwingen weergeven
Als u deze functie uitschakelt, worden door ESET Mail Security geen waarschuwingen weergegeven in het
Windows-systeemvak.
Berichtvensters worden gebruikt voor het weergeven van korte tekstberichten of vragen.
Berichtvensters automatisch sluiten
U kunt pop-upvensters automatisch na een bepaalde tijd laten sluiten. Als de waarschuwingsvensters niet
handmatig worden gesloten, gebeurt dit automatisch nadat de opgegeven tijdsduur is verstreken.
Bevestigingsberichten
Als u op Bewerken klikt, wordt er een pop-upvenster geopend met een lijst met bevestigingsberichten die door
ESET Mail Security worden weergegeven voordat er een actie wordt uitgevoerd. Gebruik de selectievakjes om
uw voorkeuren voor bevestigingsberichten aan te passen.

242
7.7.2 Toegangsinstellingen
Voor maximale beveiliging van uw systeem, is het noodzakelijk dat ESET Mail Security juist is geconfigureerd. Elke
niet-gekwalificeerde aanpassing kan problemen opleveren of leiden tot verlies van belangrijke gegevens. U kunt
uw ESET Mail Security-configuratie met een wachtwoord beveiligen om niet-gekwalificeerde aanpassingen te
voorkomen.
BELANGRIJK
Als u ESET Mail Security verwijdert terwijl u gebruikmaakt van een wachtwoord om de toegang tot de
installatie te beveiligen, wordt u gevraagd het wachtwoord op te geven. Anders kunt u ESET Mail Security niet
verwijderen.
Instellingen met wachtwoord beveiligen
Vergrendelt/ontgrendelt de installatieparameters van het programma. Klik om het venster Wachtwoord
instellen te openen.
Wachtwoord instellen
Kl ik op Instellen om een wachtwoord in te stellen of wijzigen om de installatieparameters te beveiligen. Er
moet een nieuw wachtwoord worden ingesteld om de voor ESET Mail Security ingestelde parameters te
beveiligen en ongeoorloofde wijzigingen te voorkomen. Als u een bestaand wachtwoord wilt wijzigen, typt u
uw oude wachtwoord in het veld Oud wachtwoord, en uw nieuwe wachtwoord in het veld Nieuw wachtwoord
en het veld Wachtwoord bevestigen. Klik vervolgens op OK. Dit wachtwoord is nodig voor alle toekomstige
aanpassingen van ESET Mail Security.
Volledige beheerdersrechten vereist voor beperkte beheerdersaccounts
Selecteer deze optie om de huidige gebruiker (die geen beheerdersrechten heeft) te vragen om referenties
van een beheerdersaccount op te geven wanneer die bepaalde parameters wijzigt, zoals het uitschakelen van
beveiligingsmodules.
OPMERKING
Als het wachtwoord voor Toegangsinstellingen wordt gewijzigd en u wilt een bestaand .xml-
configuratiebestand importeren (dat voorafgaand aan de wijziging van het wachtwoord is ondertekend) met
de opdrachtrege l ESET CMD, zorgt u er dan voor dat u het bestand opnieuw ondertekent met uw huidige
wachtwoord. Hierdoor kunt u een ouder configuratiebestand gebruiken zonder dat u dit voorafgaand aan het
importeren hoeft te exporteren op de andere computer waarop ESET Mail Security wordt uitgevoerd.
7.7.3 ESET-shell
U kunt toegangsrechten voor productinstellingen, functies en gegevens configureren via eShell door
Uitvoeringsbeleid voor ESET-shell te wijzigen. De standaardinstelling is Beperkte scriptmogelijkheden, maar u kunt
dit indien nodig wijzigen in Uitgeschakeld, Alleen-lezen of Volledige toegang.
Uitgeschakeld
eShell kan helemaal niet worden gebruikt. Alleen de configuratie van eShell zelf is toegestaan, in de context
van ui eshell. U kunt de vormgeving van eShell wijzigen, maar hebt geen toegang tot productinstellingen of
gegevens.
Alleen-lezen
eShell kan als controlehulpmiddel worden gebruikt. U kunt alle instellingen weergeven in zowel Interactieve
modus als Batchmodus, maar u kunt geen instellingen, functies of enige gegevens wijzigen.
Beperkte scriptmogelijkheden
In de interactieve modus kunt u alle instellingen, functies en gegevens aanpassen. In de batchmodus werkt
eShell alsof u zich in de modus Alleen-lezen bevindt, maar als u ondertekende batchbestanden gebruikt, kunt u
instellingen bewerken en gegevens aanpassen.

243
Volledige toegang
Toegang tot alle instellingen is onbeperkt in zowel de Interactieve modus als de Batchmodus (wanneer
batchbestanden worden uitgevoerd). U kunt elke instelling bekijken en aanpassen. U moet een
beheerdersaccount gebruiken om eShell met volledige toegang uit te voeren. Als Gebruikersaccountbeheer is
ingeschakeld, is ook uitbreiding van bevoegdheden vereist.
7.7.4 GUI uitschakelen op terminalserver
In dit hoofdstuk wordt beschreven hoe u de GUI van ESET Mail Security kunt uitschakelen die wordt uitgevoerd op
Windows Terminal Server voor gebruikerssessies.
Normaal gesproken wordt de GUI van ESET Mail Security gestart wanneer een externe gebruiker zich aanmeldt bij
de server en een terminalsessie begint. Dit is meestal niet gewenst op terminalservers. Als u de grafische
gebruikersinterface wilt uitschakelen voor terminalsessies, kunt u dat doen via eShell door de opdracht set ui ui
gui-start-mode none uit te voeren. Hiermee wordt de grafische gebruikersinterface in de terminalmodus gezet. Dit
zijn de twee beschikbare modi om in de grafische gebruikersinterface op te starten:
set ui ui gui-start-mode full
set ui ui gui-start-mode none
Als u wilt weten welke modus momenteel wordt gebruikt, voert u de opdracht get ui ui gui-start-mode uit.
OPMERKING
Als u ESET Mail Security op een Citrix-server hebt geïnstalleerd, raden we aan dat u instellingen gebruikt die
zijn beschreven in ons kennisbankartikel .
7.7.5 Uitgeschakelde berichten en statussen
Bevestigingsberichten
Hiermee wordt een lijst met bevestigingsberichten weergegeven en kunt u selecteren of u deze wilt
weergeven of niet.
Instellingen voor toepassingsstatussen
Hiermee kunt u de weergavestatus in- of uitschakelen in het venster Controle van het hoofdvenster.

244
7.7.5.1 Instellingen voor toepassingsstatussen
In dit dialoogvenster kunt u selecteren welke toepassingsstatussen wel of niet worden weergegeven. Als u
bijvoorbeeld Antivirus- en antispywarebeveiliging tijdelijk onderbreekt, wordt de beveiligingsstatus gewijzigd en
dit wordt aangegeven op de pagina Controle. Er wordt ook een toepassingsstatus weergegeven als uw product niet
is geactiveerd of als uw licentie is verlopen.
Toepassingsstatussen kunnen worden beheerd via ESET Security Management Center-beleid . Categorieën en
statussen worden met twee opties in de lijst weergegeven: de status Weergeven en de status Verzenden. De
verzendkolom voor toepassingsstatussen is alleen zichtbaar in de configuratie van ESET Security Management
Center-beleid . ESET Mail Security geeft instellingen met het pictogram van een hangslot weer. Met Negeermodus
kunt u toepassingsstatussen tijdelijk wijzigen.

245
7.7.6 Systeemvakpictogram
Biedt snelle toegang tot vaak gebruikte items en functies van ESET Mail Security. Deze zijn beschikbaar door met de
rechtermuisknop te klikken op het pictogram in het systeemvak.
Meer informatie
Opent de pagina Controle om de huidige beveiligingsstatus en berichten aan u weer te geven.
Beveiliging tijdelijk uitschakelen
Geeft het bevestigingsdialoogvenster weer waarmee Antivirus- en antispywarebeveiliging wordt
uitgeschakeld, die bescherming biedt tegen aanvallen door bestands-, web- en e-mailcommunicatie te
beveiligen. Wanneer u Antivirus- en antispywarebeveiliging tijdelijk uitschakelt via het pictogram in het
systeemvak, wordt het dialoogvenster Beveiliging tijdelijk uitschakelen weergegeven. Hiermee wordt
beveiliging tegen malware gedurende de gekozen tijdsduur uitgeschakeld. Als u de beveiliging definitief wilt
uitschakelen, gaat u naar Geavanceerde instellingen. Wees voorzichtig met het uitschakelen van de beveiliging,
omdat uw systeem dan wordt blootgesteld aan bedreigingen.
Geavanceerde instellingen
Gebruik deze optie om naar Geavanceerde instellingen te gaan.
Logbestanden
De logbestanden bevatten informatie over alle belangrijke programmagebeurtenissen die zich hebben
voorgedaan en bieden een overzicht van gedetecteerde bedreigingen.
ESET Mail Security Verbergen
Hiermee verbergt u het ESET Mail Security-venster.
Vensterlay-out herstellen
Hiermee stelt u het venster van ESET Mail Security opnieuw in op de standaardgrootte en het venster wordt
hiermee opnieuw op de standaardpositie van het scherm geplaatst.
Controleren op updates
Hiermee worden de modules bijgewerkt om ervoor te zorgen dat u bent beschermd tegen schadelijke code.
Info

246
Biedt systeeminformatie, details over de geïnstalleerde versie van ESET Mail Security en de geïnstalleerde
programmamodules, en de vervaldatum van uw licentie. Informatie over uw besturingssysteem en
systeembronnen vindt u onderaan op de pagina.
7.8 Standaardinstellingen herstellen
U kunt instellingen terugzetten op de standaardwaarden in Geavanceerde instellingen. Er zijn twee opties. U kunt
alles terugzetten op de standaardinstellingen of alleen de instellingen van een bepaald gedeelte terugzetten (de
instellingen in de andere gedeelten blijven ongewijzigd).
Alle instellingen terugzetten
Alle instellingen in alle gedeelten van Geavanceerde instellingen worden teruggezet in de stand die ze hadden
nadat u ESET Mail Security installeerde. U kunt deze actie beschouwen als Fabrieksinstellingen herstellen.
OPMERKING
Nadat u op Standaard herstellen hebt geklikt, gaan alle wijzigingen verloren die zijn aangebracht. Deze actie
kan niet ongedaan worden gemaakt.
Alle instellingen in dit gedeelte herstellen
Hiermee zet u module-instellingen in het geselecteerde gedeelte terug op waarden. Alle wijzigingen die u
hebt aangebracht in dit gedeelte gaan verloren.
Inhoud van tabellen herstellen
Indien ingeschakeld, gaan de regels, raken en profielen verloren, die handmatig of automatisch zijn
toegevoegd.
7.9 Help en ondersteuning
ESET Mail Security bevat probleemoplossingsfuncties en ondersteuningsinformatie waarmee u eventuele
problemen kunt oplossen.
Help
Zoeken in ESET-kennisbank
In de ESET-kennisbank staan antwoorden op veelgestelde vragen en aanbevolen oplossingen voor
verschillende problemen. De kennisbank wordt regelmatig bijgewerkt door de technische specialisten van ESET
en vormt zo een krachtig hulpmiddel om een breed scala aan problemen op te lossen.
Help openen

247
Hiermee worden online-Help-pagina's gestart voor ESET Mail Security.
Snelle oplossing zoeken
Selecteer dit als u oplossingen voor de meest voorkomende problemen wilt weergeven. Wij adviseren dit
gedeelte door te lezen voordat u contact opneemt met Technische ondersteuning.
Technische ondersteuning
Ondersteuningsaanvraag verzenden
Als u geen oplossing voor uw probleem kunt vinden, kunt u ook dit formulier op de website van ESET gebruiken
om snel contact op te nemen met onze afdeling Technische ondersteuning.
Details voor technische ondersteuning
Geef gedetailleerde informatie weer (productnaam, productversie, enz.) voor Technische ondersteuning.
Ondersteuningshulpmiddelen
Bedreigingsencyclopedie
Biedt een koppeling naar de bedreigingsencyclopedie van ESET, waarin u informatie vindt over de gevaren en
symptomen van verschillende soorten infiltraties.
ESET-logbestandverzamelaar
Biedt een koppeling naar de downloadpagina van ESET Log Collector. Log Collector is een toepassing die
automatisch informatie verzamelt, zoals configuratie- en logbestanden van uw server, zodat problemen sneller
kunnen worden opgelost.
Geschiedenis van detectie-engine
Biedt een koppeling naar de ESET-virusradar, waarin zich informatie bevindt over versies van de ESET-
detectiemodules.
ESET Specialized Cleaner
ESET Gespecialiseerd opschoonprogramma is een hulpmiddel om gangbare infecties van malware te
verwijderen, zoals Conficker, Sirefef, Necurs, enz.
Product- en licentie-informatie
Product activeren / Licentie wijzigen
Klik om het productactiveringsvenster te openen. Selecteer een van de beschikbare methoden om ESET Mail
Security te activeren.
Info over ESET Mail Security
Hier wordt informatie weergegeven over uw exemplaar van ESET Mail Security.
7.9.1 Ondersteuningsaanvraag verzenden
Om zo snel en nauwkeurig mogelijk hulp te kunnen bieden, heeft ESET informatie nodig over uw configuratie van
ESET Mail Security, uitvoerige informatie over uw systeem, actieve processen (ESET SysInspector-logbestand) en
registergegevens. ESET gebruikt deze gegevens alleen om de klant technische hulp te kunnen bieden. Deze
instelling kan ook worden geconfigureerd vanuit Geavanceerde instellingen (F5) > Hulpmiddelen > Diagnostische
gegevens > Technische ondersteuning.
OPMERKING
Als u besluit om systeemgegevens te verzenden, moet u het webformulier invullen en verzenden. Anders
wordt er geen ticket voor u gemaakt en gaan uw systeemgegevens verloren.
Als u het webformulier verzendt, worden de gegevens van uw systeemconfiguratie naar ESET verzonden. Selecteer
Deze informatie altijd verzenden om deze actie voor dit proces te onthouden.
Geen gegevens verzenden

248
Gebruik deze optie als u geen gegevens wilt verzenden. U wordt dan doorgestuurd naar de webpagina ESET
Technische ondersteuning.
7.9.2 Info over ESET Mail Security
In dit venster ziet u informatie over de geïnstalleerde versie van ESET Mail Security. In het bovenste deel van het
venster staat informatie over uw besturingssysteem en systeembronnen, de huidige gebruiker en de volledige
computernaam.
Geïnstalleerde onderdelen
Bevat informatie over modules. U kunt een lijst met geïnstalleerde onderdelen en de details ervan weergeven.
Kl ik op Kopiëren om de lijst naar uw Klembord te kopiëren. Dit kan van pas komen tijdens het oplossen van
problemen of wanneer u contact opneemt met Technische ondersteuning.
7.10 Woordenlijst
Ga naar de pagina Woordenlijst voor meer informatie over technische termen, bedreigingen en
internetbeveiliging.
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
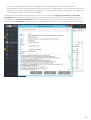 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
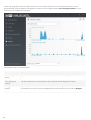 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
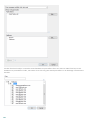 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
 162
162
-
 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
-
 179
179
-
 180
180
-
 181
181
-
 182
182
-
 183
183
-
 184
184
-
 185
185
-
 186
186
-
 187
187
-
 188
188
-
 189
189
-
 190
190
-
 191
191
-
 192
192
-
 193
193
-
 194
194
-
 195
195
-
 196
196
-
 197
197
-
 198
198
-
 199
199
-
 200
200
-
 201
201
-
 202
202
-
 203
203
-
 204
204
-
 205
205
-
 206
206
-
 207
207
-
 208
208
-
 209
209
-
 210
210
-
 211
211
-
 212
212
-
 213
213
-
 214
214
-
 215
215
-
 216
216
-
 217
217
-
 218
218
-
 219
219
-
 220
220
-
 221
221
-
 222
222
-
 223
223
-
 224
224
-
 225
225
-
 226
226
-
 227
227
-
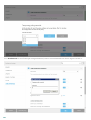 228
228
-
 229
229
-
 230
230
-
 231
231
-
 232
232
-
 233
233
-
 234
234
-
 235
235
-
 236
236
-
 237
237
-
 238
238
-
 239
239
-
 240
240
-
 241
241
-
 242
242
-
 243
243
-
 244
244
-
 245
245
-
 246
246
-
 247
247
-
 248
248
ESET Mail Security for Exchange Server 7.1 de handleiding
- Type
- de handleiding
- Deze handleiding is ook geschikt voor
Gerelateerde artikelen
-
ESET Mail Security for Exchange Server Gebruikershandleiding
-
ESET Mail Security for Exchange Server Gebruikershandleiding
-
ESET Mail Security for Exchange Server 10.0 de handleiding
-
ESET Server Security for Windows Server (File Security) 7.1 de handleiding
-
ESET Security for Microsoft SharePoint 7.0 de handleiding
-
ESET Endpoint Security 7 de handleiding
-
ESET ENDPOINT SECURITY 8 de handleiding
-
ESET Security for Microsoft SharePoint 7.2 de handleiding
-
ESET Security for Microsoft SharePoint 10.0 de handleiding
-
ESET SMART SECURITY Gebruikershandleiding
























































































































































































































































