ESET Smart Security Premium Gebruikershandleiding
- Type
- Gebruikershandleiding

Copyright ©2018 door ESET, spol. s r. o.
ESET Smart Security Premium is ontwikkeld door ESET, spol. s r. o.
Ga voor meer informatie naar www.eset.com.
Alle rechten voorbehouden. Niets uit deze documentatie mag worden verveelvoudigd,
worden opgeslagen in een systeem voor het ophalen van gegevens of worden overgedragen,
in enige vorm of op enige wijze, hetzij elektronisch, mechanisch, door fotokopie, opname,
scan of enige andere manier, zonder schriftelijke toestemming van de auteur.
ESET, spol. s r. o. behoudt zich het recht voor de beschreven toepassingssoftware zonder
voorafgaande kennisgeving te wijzigen.
Wereldwi jde kla ntonde rs teuning: www.eset.com/support
REV. 19-9-2018

Inhoud
.......................................................6ESET Smart Security Premium1.
....................................................................................................7Wat is er nieuw in deze versie1.1
....................................................................................................8Welk product heb ik?1.2
....................................................................................................9Systeemvereisten1.3
....................................................................................................9Preventie1.4
.......................................................11Installatie2.
....................................................................................................11Live-installatieprogramma2.1
....................................................................................................12Offline installatie2.2
..............................................................................13Een licentiecode invoeren
2.2.1
..............................................................................14Licentiebeheer gebruiken
2.2.2
..............................................................................14Geavanceerde instellingen
2.2.3
....................................................................................................14Algemene installatieproblemen2.3
....................................................................................................15Productactivering2.4
....................................................................................................16Licentiecode invoeren2.5
....................................................................................................16Upgraden naar een nieuwere versie2.6
....................................................................................................17Eerste scan na installatie2.7
.......................................................18Handleiding voor beginners3.
....................................................................................................18Het hoofdprogrammavenster3.1
....................................................................................................21Updates3.2
....................................................................................................22Instellingen voor vertrouwde zones3.3
....................................................................................................23Antidiefstal3.4
....................................................................................................24Hulpmiddelen voor Ouderlijk toezicht3.5
.......................................................25Werken met ESET Smart Security Premium4.
....................................................................................................27Computerbeveiliging4.1
..............................................................................28Detectie-engine
4.1.1
..................................................................................29Real-timebeveiliging van bestandssysteem
4.1.1.1
........................................................................30Aanvullende ThreatSense-parameters
4.1.1.1.1
........................................................................31Opschoonniveaus
4.1.1.1.2
........................................................................31
Wanneer moet de configuratie voor
real-timebeveiliging worden gewijzigd?
4.1.1.1.3
........................................................................31Real-timebeveiliging controleren
4.1.1.1.4
........................................................................32
Te volgen procedure als real-timebeveiliging niet
werkt
4.1.1.1.5
..................................................................................32Computerscan
4.1.1.2
........................................................................33Aangepaste scan starten
4.1.1.2.1
........................................................................35Scanvoortgang
4.1.1.2.2
........................................................................36Scanprofielen
4.1.1.2.3
........................................................................36Logbestand computerscan
4.1.1.2.4
..................................................................................36Scannen bij inactieve status
4.1.1.3
..................................................................................37Opstartscan
4.1.1.4
........................................................................37Automatische bestandscontrole bij opstarten
4.1.1.4.1
..................................................................................37Uitsluitingen
4.1.1.5
..................................................................................39ThreatSense-parameters
4.1.1.6
........................................................................43Opschonen
4.1.1.6.1
........................................................................44
Bestandsextensies die moeten worden uitgesloten
van scans
4.1.1.6.2
..................................................................................44Er is een infiltratie gedetecteerd
4.1.1.7
..................................................................................46Documentsbescherming
4.1.1.8
..............................................................................46Verwisselbare media
4.1.2
..............................................................................47Apparaatbeheer
4.1.3
..................................................................................48Regeleditor voor apparaatbeheer
4.1.3.1
..................................................................................49Regels voor apparaatbeheer toevoegen
4.1.3.2
..................................................................................50Editor beveiligingsregels webcam
4.1.3.3
..............................................................................51HIPS (Host-based Intrusion Prevention System)
4.1.4
..................................................................................53Geavanceerde instellingen
4.1.4.1
..................................................................................54Interactief venster van HIPS
4.1.4.2
..................................................................................55Potentieel ransomware-gedrag gedetecteerd
4.1.4.3
..............................................................................55Gamer-modus
4.1.5
....................................................................................................56Internet-beveiliging4.2
..............................................................................57Beveiliging van webtoegang
4.2.1
..................................................................................58Basis
4.2.1.1
..................................................................................58Webprotocollen
4.2.1.2
..................................................................................58URL-adresbeheer
4.2.1.3
..............................................................................59Beveiliging van e-mailclient
4.2.2
..................................................................................59E-mailclients
4.2.2.1
..................................................................................60E-mailprotocollen
4.2.2.2
..................................................................................61Waarschuwingen en meldingen
4.2.2.3
..................................................................................62Integratie met e-mailclients
4.2.2.4
........................................................................62Beveiliging van e-mailclient configureren
4.2.2.4.1
..................................................................................62POP3-, POP3S-filter
4.2.2.5
..................................................................................63Antispambeveiliging
4.2.2.6
..............................................................................65Protocolfiltering
4.2.3
..................................................................................65Web- en e-mailclients
4.2.3.1
..................................................................................66Uitgesloten toepassingen
4.2.3.2
..................................................................................67Uitgesloten IP-adressen
4.2.3.3
........................................................................67IPv4-adres toevoegen
4.2.3.3.1
........................................................................67IPv6-adres toevoegen
4.2.3.3.2
..................................................................................68SSL/TLS
4.2.3.4
........................................................................69Certificaten
4.2.3.4.1
........................................................................69Versleuteld netwerkverkeer
4.2.3.4.1.1
........................................................................69Lijst met bekende certificaten
4.2.3.4.2
........................................................................70Lijst met door SSL/TLS gefilterde toepassingen
4.2.3.4.3
..............................................................................70Antiphishing-beveiliging
4.2.4
....................................................................................................72Netwerkbeveiliging4.3
..............................................................................73Firewall
4.3.1
..................................................................................75Leermodusinstellingen
4.3.1.1
..................................................................................76Netwerkaanvalbeveiliging
4.3.1.2
..............................................................................76Firewallprofielen
4.3.2
..................................................................................76Profielen die zijn toegewezen aan netwerkadapters
4.3.2.1
..............................................................................77Regels configureren en gebruiken
4.3.3
..................................................................................78Firewallregels
4.3.3.1
..................................................................................79Werken met regels
4.3.3.2
..............................................................................80Zones configureren
4.3.4
..............................................................................80Bekende netwerken
4.3.5
..................................................................................81Editor voor bekende netwerken
4.3.5.1
..................................................................................84Netwerkverificatie - Serverconfiguratie
4.3.5.2
..............................................................................84Logboekregistratie
4.3.6
..............................................................................84Verbinding tot stand brengen - detectie
4.3.7
..............................................................................85Problemen oplossen met ESET Persoonlijke firewall
4.3.8
..................................................................................85Wizard Probleemoplossing
4.3.8.1

..................................................................................85
Regels of uitzonderingen registreren en maken van
logbestand
4.3.8.2
........................................................................86Regel maken van logbestand
4.3.8.2.1
..................................................................................86
Uitzonderingen maken van meldingen van
Persoonlijke firewall
4.3.8.3
..................................................................................86Geavanceerde PCAP-logboekregistratie
4.3.8.4
..................................................................................87Problemen oplossen met protocolfiltering
4.3.8.5
....................................................................................................88Beveiligingshulpprogramma's4.4
..............................................................................88Ouderlijk toezicht
4.4.1
..................................................................................90Categorieën
4.4.1.1
..................................................................................91Website-uitzonderingen
4.4.1.2
....................................................................................................92Het programma bijwerken4.5
..............................................................................95Update-instellingen
4.5.1
..................................................................................97Instellingen voor geavanceerde update
4.5.1.1
........................................................................97Updatemodus
4.5.1.1.1
........................................................................97Verbindingsopties
4.5.1.1.2
..............................................................................98Ongedaan maken van update
4.5.2
..............................................................................99Updatetaken maken
4.5.3
....................................................................................................100Hulpmiddelen4.6
..............................................................................101Password Manager
4.6.1
..................................................................................102Password Manager inschakelen
4.6.1.1
..................................................................................102Password Manager ontgrendelen
4.6.1.2
..................................................................................103Password Manager uitschakelen
4.6.1.3
..................................................................................103Ondersteunde browsers
4.6.1.4
..............................................................................103Identiteiten
4.6.2
..............................................................................104App-accounts
4.6.3
..............................................................................104Webaccounts
4.6.4
..............................................................................105Menu
4.6.5
..................................................................................105Instellingen
4.6.5.1
..................................................................................106Hulpmiddelen
4.6.5.2
..............................................................................107Mijn account
4.6.6
..................................................................................107Hoofdwachtwoord
4.6.6.1
..................................................................................107Synchronisatie
4.6.6.2
..............................................................................107Inleiding in Secure Data
4.6.7
..................................................................................107Installatie
4.6.7.1
..................................................................................108Aan de slag
4.6.7.2
........................................................................109Versleuteld virtueel station
4.6.7.2.1
........................................................................111Versleuteld verwisselbaar station
4.6.7.2.2
..............................................................................112Connected Home Monitor
4.6.8
..................................................................................113Netwerkapparaat
4.6.8.1
..............................................................................113Webcam-beveiliging
4.6.9
..............................................................................114Hulpmiddelen in ESET Smart Security Premium
4.6.10
..................................................................................115Logbestanden
4.6.10.1
........................................................................117Logbestanden
4.6.10.1.1
..................................................................................118Actieve processen
4.6.10.2
..................................................................................119Beveiligingsrapport
4.6.10.3
..................................................................................120Activiteit bekijken
4.6.10.4
..................................................................................121Netwerkverbindingen
4.6.10.5
..................................................................................122ESET SysInspector
4.6.10.6
..................................................................................123Planner
4.6.10.7
..................................................................................125Systeemopruiming
4.6.10.8
..................................................................................125ESET SysRescue
4.6.10.9
..................................................................................125Op de cloud gebaseerde beveiliging
4.6.10.10
........................................................................127Verdachte bestanden
4.6.10.10.1
..................................................................................127Quarantaine
4.6.10.11
..................................................................................128Proxyserver
4.6.10.12
..................................................................................129E-mailmeldingen
4.6.10.13
........................................................................131Berichtindeling
4.6.10.13.1
..................................................................................131Voorbeeld voor analyse selecteren
4.6.10.14
..................................................................................132Microsoft Windows®-update
4.6.10.15
..................................................................................132ESET CMD
4.6.10.16
....................................................................................................134Gebruikersinterface4.7
..............................................................................134Elementen van gebruikersinterface
4.7.1
..............................................................................136Waarschuwingen en meldingen
4.7.2
..................................................................................137Geavanceerde instellingen
4.7.2.1
..............................................................................138Toegangsinstellingen
4.7.3
..............................................................................139Programmamenu
4.7.4
.......................................................141Geavanceerde gebruiker5.
....................................................................................................141Profielen5.1
....................................................................................................141Sneltoetsen5.2
....................................................................................................142Diagnostiek5.3
....................................................................................................143Instellingen importeren en exporteren5.4
....................................................................................................143ESET SysInspector5.5
..............................................................................143ESET SysInspector
5.5.1
..................................................................................144ESET SysInspector starten
5.5.1.1
..............................................................................144Gebruikersinterface en gebruik van de toepassing
5.5.2
..................................................................................144Besturingselementen in programma
5.5.2.1
..................................................................................146Navigeren in ESET SysInspector
5.5.2.2
........................................................................148Sneltoetsen
5.5.2.2.1
..................................................................................149Vergelijken
5.5.2.3
..............................................................................150Opdrachtregelparameters
5.5.3
..............................................................................151Servicescript
5.5.4
..................................................................................151Servicescript genereren
5.5.4.1
..................................................................................151Structuur van het servicescript
5.5.4.2
..................................................................................154Servicescripts uitvoeren
5.5.4.3
..............................................................................155Veelgestelde vragen
5.5.5
....................................................................................................157Opdrachtregel5.6
.......................................................159Woordenlijst6.
....................................................................................................159Typen infiltraties6.1
..............................................................................159Virussen
6.1.1
..............................................................................159Wormen
6.1.2
..............................................................................160Trojaanse paarden
6.1.3
..............................................................................160Rootkits
6.1.4
..............................................................................160Adware
6.1.5
..............................................................................161Spyware
6.1.6
..............................................................................161Compressiesoftware
6.1.7
..............................................................................161Potentieel onveilige toepassingen
6.1.8
..............................................................................162Potentieel ongewenste toepassingen
6.1.9
..............................................................................164Botnet
6.1.10
....................................................................................................165Typen externe aanvallen6.2
..............................................................................165DoS-aanvallen
6.2.1

Inhoud
..............................................................................165DNS Poisoning
6.2.2
..............................................................................165Wormaanvallen
6.2.3
..............................................................................165Port Scanning
6.2.4
..............................................................................166TCP-desynchronisatie
6.2.5
..............................................................................166SMB Relay
6.2.6
..............................................................................166ICMP-aanvallen
6.2.7
....................................................................................................167ESET Technology6.3
..............................................................................167Exploit Blocker
6.3.1
..............................................................................167Geavanceerde geheugenscanner
6.3.2
..............................................................................167Netwerkaanvalbeveiliging
6.3.3
..............................................................................167ESET LiveGrid®
6.3.4
..............................................................................168Botnet-beveiliging
6.3.5
..............................................................................168Java Exploit Blocker
6.3.6
..............................................................................168Beveiliging van bankieren en betalingen
6.3.7
..............................................................................169Beveiliging tegen aanvallen met scripts
6.3.8
..............................................................................170Ransomwareschild
6.3.9
..............................................................................170UEFI-scanner
6.3.10
....................................................................................................170E-mail6.4
..............................................................................171Advertenties
6.4.1
..............................................................................171Nepmeldingen
6.4.2
..............................................................................171Phishing
6.4.3
..............................................................................172Spam herkennen
6.4.4
..................................................................................172Regels
6.4.4.1
..................................................................................172Witte lijst
6.4.4.2
..................................................................................173Zwarte lijst
6.4.4.3
..................................................................................173Uitzonderingenlijst
6.4.4.4
..................................................................................173Controle vanaf de server
6.4.4.5
.......................................................174Veelgestelde vragen7.
....................................................................................................174ESET Smart Security Premium bijwerken7.1
....................................................................................................174Een virus van de pc verwijderen7.2
....................................................................................................175
Communicatie toestaan voor een
bepaalde toepassing
7.3
....................................................................................................175
Ouderlijk toezicht inschakelen voor een
account
7.4
....................................................................................................176Een nieuwe taak maken in Planner7.5
....................................................................................................177
Een wekelijkse computerscantaak
plannen
7.6
....................................................................................................177
Geavanceerde instellingen
ontgrendelen
7.7

6
1. ESET Smart Security Premium
ESET Smart Security Premium vertegenwoordigt een nieuwe benadering van werkelijk geïntegreerde
computerbeveiliging. De recentste versie van de ESET LiveGrid®-scanengine, gecombineerd met de op maat
gemaakte module Firewall en Antispam, maakt gebruik van snelheid en precisie om uw computer te beveiligen. Het
resultaat is een intelligent systeem dat permanent alert is op aanvallen en schadelijke software die uw computer
mogelijk in gevaar brengen.
ESET Smart Security Premium is een complete beveiligingsoplossing, die maximale beveiliging combineert met een
minimale systeembelasting. Onze geavanceerde technologieën maken gebruik van kunstmatige intelligentie om
infiltratie door virussen, spyware, Trojaanse paarden, wormen, adware, rootkits en andere bedreigingen te
voorkomen, zonder dat de systeemprestaties worden gehinderd of uw computer wordt verstoord.
Functies en voordelen
Opnieuw vormgegeven
gebruikersinterface
De gebruikersinterface in deze versie is aanzienlijk gewijzigd en
vereenvoudigd op basis van de testresultaten betreffende de
bruikbaarheid. Alle GUI-aanduidingen en meldingen zijn gecontroleerd
en de interface biedt nu ondersteuning voor talen die van rechts naar
links worden gelezen zoals Hebreeuws en Arabisch. Online Help is nu
geï ntegreerd in ESET Smart Security Premium en omvat een bijgewerkte
inhoud met dynamische ondersteuning.
Antivirus en antispyware
Detecteert proactief bekende en onbekende virussen, wormen,
Trojaanse paarden en rootkits, en schoont deze op. Geavanceerde
heuristiek markeert zelfs niet eerder gedetecteerde malware, en
beschermt u zo tegen onbekende bedreigingen en neutraliseert deze
voordat ze schade kunnen veroorzaken. Beveiliging van webtoegang en
Antiphishing controleren de communicatie tussen webbrowsers en
externe servers (inclusief SSL). Beveiliging van e-mailclient biedt beheer
van e-mailcommunicatie die wordt ontvangen via POP3(S)- en IMAP(S)-
protocollen.
Regelmatige updates
Door regelmatig updates uit te voeren voor de detectie-engine
(voorheen 'database met viruskenmerken' genoemd) en
programmamodules bij te werken, bent u verzekerd van het maximale
beveiligingsniveau van de computer.
ESET LiveGrid®
(Reputatie via cloud)
U kunt de reputatie van actieve processen en bestanden rechtstreeks in
ESET Smart Security Premium bekijken.
Apparaatbeheer
Scant automatisch alle USB-flashstations, geheugenkaarten en cd's/dvd's.
Blokkeert verwisselbare media op basis van mediatype, fabrikant, grootte
en andere kenmerken.
HIPS-functie
U kunt het gedrag van het systeem gedetailleerd aanpassen: u kunt regels
voor het systeemregister, actieve processen en programma's opgeven, en
uw beveiligingspostuur verfijnen.
Gamer-modus
Stelt alle pop-upvensters, updates of andere systeem-intensieve
activiteiten uit om systeembronnen te besparen voor gaming en andere
activiteiten in volledige schermweergave.
Functies in ESET Smart Security Premium
Beveiliging van bankieren en
betalingen
Beveiliging van bankieren en betalingen biedt een veilige browser die wordt
gebruikt voor internetbankieren of online betaalgateways om te garanderen
dat alle online transacties plaatsvinden in een vertrouwde en veilige
omgeving.

7
Ondersteuning voor
netwerksignaturen
Netwerksignaturen maken snelle identificatie mogelijk en blokkeren
schadelijk verkeer van en naar gebruikersapparaten, zoals bots en exploit
packs. De voorziening is een verbetering van Botnet-beveiliging.
Intelligente firewall
Voorkomt dat onbevoegde gebruikers toegang krijgen tot uw computer
en misbruik maken van uw persoonlijke gegevens.
ESET Antispam
Spam vormt tot 80 procent van alle e-mailcommunicatie.
Antispambeveiliging dient als bescherming tegen dit probleem.
ESET Antidiefstal
ESET Antidiefstal breidt de beveiliging op gebruikersniveau uit in het geval
van een verloren of gestolen computer. Wanneer gebruikers ESET Smart
Security Premium en ESET Antidiefstal hebben geïnstalleerd, wordt hun
apparaat weergegeven in de webinterface. Via de webinterface kunnen
gebruikers hun ESET Antidiefstal-configuratie en antidiefstalvoorzieningen
op het apparaat beheren.
Ouderlijk toezicht
Beschermt uw gezin tegen mogelijk aanstootgevende webinhoud door
verschillende websitecategorieën te blokkeren.
Er moet een licentie zijn geactiveerd om functies van ESET Smart Security Premium te kunnen gebruiken. U wordt
aangeraden uw licentie te verlengen enkele weken voordat de licentie voor ESET Smart Security Premium verloopt.
1.1 Wat is er nieuw in deze versie
De nieuwe versie van ESET Smart Security Premium bevat de volgende verbeteringen:
Logboekregistratie met één klik: met slechts één klik kunt u geavanceerde logboekregistraties maken.
UEFI-scanner (Unified Extensible Firmware Interface): voegt een verhoogd malwarebeveiligingsniveau toe door
bedreigingen te detecteren en verwijderen die potentieel worden gestart voordat het besturingssysteem wordt
opgestart. Klik hier voor meer informatie.
Hoge prestaties en lage systeemimpact: deze versie is bedoeld voor het efficiënte gebruik van de
systeembronnen, waardoor u kunt profiteren van optimale prestaties van uw computer en tegelijk op de beste
manier beschermd bent tegen nieuwe soorten bedreigingen.
Nieuwe indeling van Geavanceerde instellingen: ESET LiveGrid®-instellingen zijn verplaatst naar het gedeelte
Detectie-engine, Geavanceerde logboekregistratie van Antispam is verplaatst naar het gedeelte Diagnostisch,
enz.
Verbeterde ondersteuning voor schermlezer: ESET Smart Security Premium ondersteunt de meeste populaire
schermlezers (JAWS, NVDA, Verteller).
Scan slepen en neerzetten: u kunt een bestand of map handmatig scannen door het bestand of de map naar de
gemarkeerde plek te verplaatsen.
ESET Smart Security Premium wordt nu met een minimum aantal modules geïnstalleerd, waardoor de installatie
lichter en sneller is. Nadat het product is geïnstalleerd en geactiveerd, worden de modules gedownload.
ESET Smart Security Premium brengt u op de hoogte wanneer u verbinding maakt met een onbeveiligd draadloos
netwerk of een netwerk met een zwakke beveiliging.
Lees voor meer informatie over de nieuwe functies van ESET Smart Security Premium het volgende artikel in de
ESET-kennisbank:
Wat is er nieuw in deze versie van ESET-consumentenproducten

8
1.2 Welk product heb ik?
ESET biedt meerdere beveiligingslagen aan met nieuwe producten gaande van een krachtige en snelwerkende
antivirusoplossinge tot een all-in-one beveiligingsoplossing met een minimale belasting voor het systeem:
ESET NOD32 Antivirus
ESET Internet Security
ESET Smart Security Premium
Om na te gaan welk product u hebt geïnstalleerd, opent u het hoofdprogrammavenster (zie kennisbankartikel). Hier
ziet u de naam van het product helemaal bovenaan in de titelbalk van het venster.
Onderstaande tabel toon u de beschikbare functies voor elk product.
ESET NOD32 Antivirus
ESET Internet Security
ESET Smart Security
Premium
Antivirus
Antispyware
Exploit Blocker
Beveiliging tegen aanvallen met
scripts
Antiphishing
Beveiliging van webtoegang
HIPS (met onder meer
Antiransomwarebescherming)
Antispam
Firewall
Connected Home Monitor
Webcam-beveiliging
Netwerkaanvalbeveiliging
Botnet-beveiliging
Beveiliging van bankieren en
betalingen
Ouderlijk toezicht
Antidiefstal
ESET Password Manager
ESET Secure Data
OPMERKING
Enkele van de hiervoor genoemde producten zijn mogelijk niet beschikbaar in uw taal/regio.

9
1.3 Systeemvereisten
Uw systeem dient te voldoen aan onderstaande hard- en softwarevereisten zodat ESET Smart Security Premium
optimaal kan presteren:
Ondersteunde processors
Intel® en AMD x86-x64
Ondersteunde besturingssystemen
Microsoft® Windows® 10
Microsoft® Windows® 8.1
Microsoft® Windows® 8
Microsoft® Windows® 7
Microsoft® Windows® Vista
Microsoft® Windows® Home Server 2011 64-bit
OPMERKING
ESET Antidiefstal ondersteunt geen Microsoft Windows Home Servers.
1.4 Preventie
Wanneer u uw computer gebruikt en met name wanneer u op internet surft, moet u er altijd rekening mee houden
dat geen enkel antivirussysteem u volledig kan beschermen tegen infiltraties en aanvallen. Voor maximale
beveiliging en optimaal gebruiksgemak is het van essentieel belang dat u uw antivirusoplossing op de juiste manier
gebruikt en dat u een aantal belangrijke regels in acht neemt:
Regelmatig bijwerken
Volgens de statistieken van ThreatSense worden dagelijks duizenden nieuwe, unieke bedreigingen gemaakt, met
als doel de bestaande beveiligingsmaatregelen te omzeilen en de makers van de bedreigingen voordeel te
bezorgen ten koste van andere gebruikers. De specialisten van het onderzoekslaboratorium van ESET zijn dagelijks
bezig met het analyseren van deze bedreigingen. Vervolgens worden updates beschikbaar gesteld aan onze
gebruikers om zo het beveiligingsniveau constant te verbeteren. Voor een maximale effectiviteit van deze updates
is het belangrijk dat updates op de juiste manier op uw systeem worden geconfigureerd. Zie het hoofdstuk
Instellingen voor update voor meer informatie over het configureren van updates.
Beveiligingspatches downloaden
De auteurs van schadelijke software richten hun pijlen vaak op verschillende systeembeveiligingsproblemen om de
schadelijke code zo effectief mogelijk te verspreiden. Daarom controleren softwarebedrijven hun toepassingen
nauwkeurig op beveiligingsproblemen en brengen ze regelmatig beveiligingsupdates uit om potentiële
bedreigingen te elimineren. Het is belangrijk dat u deze beveiligingsupdates downloadt zodra ze zijn uitgebracht.
Microsoft Windows en webbrowsers zoals Internet Explorer zijn twee voorbeelden van programma's waarvoor op
regelmatige basis beveiligingsupdates worden uitgebracht.
Back-ups maken van belangrijke gegevens
Auteurs van malware trekken zich meestal niets aan van de belangen van gebruikers. De activiteiten van schadelijke
programma's leiden dan ook vaak tot ernstige storingen in het besturingssysteem en het verlies van belangrijke
gegevens. Het is belangrijk dat u regelmatig back-ups van belangrijke en vertrouwelijke gegevens maakt op een
externe bron, zoals een dvd of een externe vaste schijf. Op deze manier kunt u uw gegevens gemakkelijker en
sneller herstellen in het geval van een systeemstoring.

10
De computer regelmatig scannen op virussen
Detectie van meer bekende en onbekende virussen, wormen, Trojaanse paarden en rootkits worden afgehandeld
door de module Real-timebeveiliging van bestandssysteem. Dit betekent dat elke keer dat u een bestand opent, dit
wordt gescand op schadelijke activiteiten. Het wordt echter aangeraden ten minste één keer per maand een
volledige computerscan uit te voeren, omdat het herkenningspatroon van malware varieert en de detectie-engine
elke dag wordt bijgewerkt.
De algemene beveiligingsregels in acht nemen
Dit is de belangrijkste en effectiefste regel van allemaal: wees altijd voorzichtig. Tegenwoordig worden veel
bedreigingen pas geactiveerd en verspreid als de gebruiker dit proces in gang zet. Als u voorzichtig bent met het
openen van nieuwe bestanden, hoeft u later geen bedreigingen te verwijderen en kunt u zichzelf veel tijd en
moeite besparen. Hier volgen enkele nuttige richtlijnen:
Bezoek geen verdachte websites met veel pop-upvensters en knipperende reclameboodschappen.
Wees voorzichtig met het installeren van freewareprogramma's, codecpakketten, enzovoort. Gebruik alleen
veilige programma's en bezoek alleen veilige websites.
Wees voorzichtig met het openen van e-mailbijlagen, met name bijlagen bij e-mailberichten die in grote
hoeveelheden worden verzonden en e-mailberichten van onbekende afzenders.
Gebruik geen beheerdersaccount wanneer u dagelijkse werkzaamheden op uw computer uitvoert.

11
2. Installatie
Er zijn verschillende methoden om ESET Smart Security Premium te installeren op uw computer.
Installatiemethoden kunnen variëren, afhankelijk van het land en de manier van distributie:
Live-installatieprogramma kan worden gedownload van de website van ESET. Het installatiepakket is
universeel voor alle talen (u kiest de gewenste taal). Het Live-installatieprogramma is zelf een klein bestand.
De overige bestanden die nodig zijn voor het installeren van ESET Smart Security Premium worden
automatisch gedownload.
Offline installatie: dit type installatie wordt gebruikt wanneer u installeert vanaf een product-cd/dvd. Hierbij
wordt een .exe-bestand gebruikt dat groter is dan het Live-installatieprogramma. Een internetverbinding of
aanvullende bestanden om de installatie te voltooien zijn niet nodig.
BELANGRIJK
Controleer of er geen andere antivirusprogramma's op uw computer zijn geïnstalleerd voordat u ESET Smart
Security Premium installeert. Indien twee of meer antivirusoplossingen op één computer zijn geïnstalleerd,
kunnen deze met elkaar conflicteren. Wij adviseren u alle eventuele andere antivirusprogramma's van uw
systeem te verwijderen. Bekijk het artikel in de ESET-kennisbank voor een lijst met hulpprogramma's voor de
verwijdering van veelgebruikte antivirussoftware (beschikbaar in het Engels en een aantal andere talen).
2.1 Live-installatieprogramma
Nadat u het installatiepakkket Live-installatieprogramma hebt gedownload, dubbelklikt u op het installatiebestand
en volgt u de stapsgewijze instructies in het venster van het installatieprogramma.
BELANGRIJK
voor dit type installatie moet u verbonden zijn met internet.
Selecteer de gewenste taal in het vervolgkeuzemenu en klik op Doorgaan. Even geduld terwijl de
installatiebestanden worden gedownload.
Nadat u de Licentieovereenkomst voor eindgebruikers hebt geaccepteerd, wordt u gevraagd om ESET LiveGrid® en
detectie van mogelijk ongewenste toepassingen te configureren. ESET LiveGrid® helpt waarborgen dat ESET direct
en continu wordt geïnformeerd over nieuwe bedreigingen, zodat wij onze klanten de beste beveiliging kunnen
bieden. Het systeem maakt verzending mogelijk van nieuwe bedreigingen naar het onderzoekslaboratorium van
ESET, waar deze worden geanalyseerd, verwerkt en toegevoegd aan de detectie-engine.

12
Standaard is ESET LiveGrid®-feedbacksysteem inschakelen (aanbevolen) geselecteerd, waarmee deze functie wordt
geactiveerd.
De volgende stap in het installatieproces is het configureren van detectie van mogelijk ongewenste toepassingen.
Mogelijk ongewenste toepassingen zijn niet per se schadelijk, maar kunnen het gedrag van het besturingssysteem
negatief beïnvloeden. Zie het hoofdstuk Potentieel ongewenste toepassingen voor meer informatie.
Klik op Installeren om het installatieproces te starten. Dit kan enige ogenblikken duren. Klik op Gereed om de
installatie van het product te voltooien en de activering ervan te starten.
OPMERKING
Nadat het product is geïnstalleerd en geactiveerd, worden de modules gedownload. Beveiliging wordt
geïnitialiseerd en bepaalde functies werken mogelijk pas nadat het downloaden is voltooid.
OPMERKING
Als u een licentie hebt waarmee u andere versies van een product kunt installeren, kunt u het product
selecteren volgens uw wensen. Voor meer informatie over functies in elk specifiek product klikt u hier.
2.2 Offline installatie
Nadat u het het offline installatie (.exe) hebt gestart, wordt u met de installatiewizard door de installatie geleid.
Selecteer de gewenste taal in het vervolgkeuzemenu en klik op Installeren.
Nadat u de Licentieovereenkomst voor eindgebruikers hebt geaccepteerd, wordt u gevraagd een licentiecode in te
voeren of Licentiebeheer te gebruiken.
Als u nog geen licentie hebt, selecteert u Gratis proefversie om het ESET-product gedurende een beperkte periode
te testen, of selecteert u Licentie kopen. U kunt ook de Activering overslaan en doorgaan met de installatie zonder
de activeren. Later wordt aan u een licentiecode gevraagd.

13
2.2.1 Een licentiecode invoeren
De Installatiewizard selecteert het te installeren product aan de hand van uw licentiecode en geeft de productnaam
weer tijdens het installeren. Klik op Ander product voor een lijst met producten die u met uw licentie kunt
activeren. Voor meer informatie over de functies in elk specifiek product klikt u hier.
Nadat u hebt geklikt op Doorgaan wordt u gevraagd om ESET LiveGrid® en detectie van mogelijk ongewenste
toepassingen te configureren. ESET LiveGrid® draagt ertoe bij dat ESET direct en continu wordt geïnformeerd over
nieuwe bedreigingen, zodat wij onze klanten de beste beveiliging kunnen bieden. Het systeem maakt verzending
mogelijk van nieuwe bedreigingen naar het onderzoekslaboratorium van ESET, waar deze worden geanalyseerd,
verwerkt en toegevoegd aan de detectie-engine. Mogelijk ongewenste toepassingen zijn niet per se schadelijk,
maar kunnen het gedrag van het besturingssysteem negatief beïnvloeden. Zie het hoofdstuk Potentieel
ongewenste toepassingen voor meer informatie.
Klik op Installeren om het installatieproces te starten. Dit kan enige ogenblikken duren. Klik op Gereed om de
installatie van het product te voltooien en de activering ervan te starten.
OPMERKING
Nadat het product is geïnstalleerd en geactiveerd, worden de modules gedownload. Beveiliging wordt
geïnitialiseerd en bepaalde functies werken mogelijk pas nadat het downloaden is voltooid.
OPMERKING
Als u een licentie hebt waarmee u verschillende producten kunt installeren, kunt u een product naar voorkeur
installeren. Voor meer informatie over de functies in elk specifiek product klikt u hier.
Volg de instructies in het gedeelte 'Live-installatieprogramma' voor meer instructies over installatiestappen, ESET
LiveGrid® en Detectie van potentieel ongewenste toepassingen.

14
2.2.2 Licentiebeheer gebruiken
Na het selecteren van Licentiebeheer gebruiken wordt u gevraagd om my.eset.com-referenties in een nieuw
venster. Voer uw my.eset.com-referenties in en klik op Aanmelden om een licentie te gebruiken in Licentiebeheer.
Kies een licentie om voor activering te gebruiken, klik op Doorgaan en uw ESET Smart Security Premium wordt
geactiveerd.
OPMERKING
Als u nog geen my.eset.com-account hebt, klikt u op de knop Account maken om u te registreren.
OPMERKING
Als u uw wachtwoord bent vergeten, klikt u op Ik ben mijn wachtwoord vergeten en voert u de stappen uit op de
webpagina waar u naartoe wordt geleid.
ESET Licentiebeheer helpt u al uw ESET-licenties te beheren. U kunt uw licentie eenvoudig verlengen, upgraden of
uitbreiden en de belangrijke licentiegegevens bekijken. Eerst voert u uw licentiecode in. Vervolgens ziet u het
product, gekoppeld apparaat, het aantal beschikbare seats en de vervaldatum. U kunt specifieke apparaten
deactiveren of een nieuwe naam geven. Wanneer u op Verlengen klikt, wordt u naar de onlinewinkel geleid waar u
de aankoop kunt bevestigen en de verlenging kunt kopen.
Als u uw licentie wilt upgraden (bijvoorbeeld van ESET NOD32 Antivirus naar ESET Smart Security Premium) of uw
ESET-beveiligingsproduct op een ander apparaat wilt installeren, wordt u naar een onlinewinkel geleid.
In ESET Licentiebeheer kunt u verschillende licenties toevoegen, producten downloaden naar uw apparaten.
2.2.3 Geavanceerde instellingen
Nadat u Installatiemap wijzigen hebt geselecteerd, wordt u gevraagd een locatie voor de installatie te selecteren.
Standaard wordt het programma in de volgende map geïnstalleerd:
C:\Program Files\ESET\ESET Smart Security Premium\
Klik op Bladeren om deze locatie te wijzigen (niet aanbevolen).
Volg de instructies in het gedeelte Live-installatieprogramma (zie 'Live-installatieprogramma') om de volgende
installatiestappen, ESET LiveGrid® en Detectie van mogelijk ongewenste toepassingen uit te voeren.
Klik op Doorgaan en vervolgens op Installeren om de installatie te voltooien.
2.3 Algemene installatieproblemen
Als zich problemen voordoen tijdens de installatie, raadpleegt u onze lijst met algemene installatieproblemen en
oplossingen om een oplossing voor uw probleem te vinden.

15
2.4 Productactivering
Nadat de installatie is voltooid, wordt u gevraagd uw product te activeren.
Er zijn verschillende methoden om uw product te activeren. De beschikbaarheid van de activeringsmethoden in het
activeringsvenster kan verschillen per land en is afhankelijk van de distributiemethode (cd/dvd, ESET-website,
enzovoort):
Als u het product hebt aangeschaft in de detailhandel, activeert u uw product met een Licentiecode. De
Licentiecode bevindt zich doorgaans binnen in of op de achterkant van de productverpakking. De Licentiecode
moet worden ingevoerd zoals deze is verstrekt voor een geslaagde activering. Licentiecode: een unieke
tekenreeks in de indeling XXXX-XXXX-XXXX-XXXX-XXXX of XXXX-XXXXXXXX, die wordt gebruikt ter identificatie
van de licentiehouder en voor activering van de licentie.
Nadat u Licentiebeheer gebruiken hebt geselecteerd, wordt u in een nieuw venster gevraagd naar uw
referenties voor my.eset.com.
Als u ESET Smart Security Premium wilt evalueren voordat u tot aanschaf overgaat, selecteert u Gratis
proefversie. Vul uw e-mailadres en land in om ESET Smart Security Premium voor een bepaalde tijd te
activeren. U ontvangt de proeflicentie in een e-mail. Licenties voor proefversies kunnen slechts eenmaal per
klant worden geactiveerd.
Als u geen licentie hebt en er een wilt kopen, klikt u op Licentie kopen. U wordt hierop doorgestuurd naar de
website van de ESET-distributeur in uw regio.

16
2.5 Licentiecode invoeren
Automatische updates zijn belangrijk voor uw beveiliging. ESET Smart Security Premium wordt alleen bijgewerkt
nadat u de software hebt geactiveerd met behulp van uw Licentiecode.
Als u na installatie uw Licentiecode niet hebt ingevuld, wordt het product niet geactiveerd. U kunt uw licentie
aanpassen in het startvenster van het programma. Om dit te doen, klikt u op Help en ondersteuning > Licentie
activeren en voert u de licentiegegevens in die u hebt ontvangen bij uw ESET-beveiligingsproduct in het venster
Productactivering.
Wanneer uw Licentiecode invoert, is het van belang om deze exact over te nemen:
Licentiecode: een unieke tekenreeks in de indeling XXXX-XXXX-XXXX-XXXX-XXXX, die wordt gebruikt ter
identificatie van de licentiehouder en de activering van de licentie.
We raden u aan om de Licentiecode vanwege de nauwkeurigheid te kopiëren en te plakken uit uw registratie-e-
mail.
2.6 Upgraden naar een nieuwere versie
Er worden nieuwere versies van ESET Smart Security Premium uitgebracht om verbeteringen door te voeren of
problemen op te lossen die niet kunnen worden opgelost met de automatische updates van programmamodules. U
kunt op verschillende manieren een upgrade naar een recentere versie uitvoeren:
1. Automatisch via een update van het programma.
Aangezien de upgrade van het programma verspreid wordt onder alle gebruikers en van invloed kunnen zijn op
bepaalde systeemconfiguraties, wordt deze uitgebracht na uitgebreide tests om een soepele upgrade te kunnen
garanderen op alle mogelijke systeemconfiguraties. Als u een upgrade naar een nieuwere versie onmiddellijk
wilt uitvoeren nadat deze is uitgebracht, gebruikt u een van de onderstaande methoden.
2. Handmatig in het hoofdvenster door te klikken op Controleren op updates in het gedeelte Update.
3. Handmatig door een recentere versie te downloaden en deze over de oude installatie te installeren.

17
2.7 Eerste scan na installatie
Na installatie van ESET Smart Security Premium wordt er na de eerste keer bijwerken automatisch een scan van de
computer uitgevoerd om te controleren op de aanwezigheid van schadelijke code.
U kunt een computerscan ook handmatig starten vanuit het hoofdprogrammavenster door te klikken op
Computerscan > Uw computer scannen. Zie de sectie Computerscan voor meer informatie over computerscans.

18
3. Handleiding voor beginners
Dit hoofdstuk biedt een eerste overzicht van ESET Smart Security Premium en de basisinstellingen van het
programma.
3.1 Het hoofdprogrammavenster
Het hoofdprogrammavenster van ESET Smart Security Premium is onderverdeeld in twee hoofdgedeelten. In het
hoofdprogrammavenster aan de rechterkant wordt informatie weergegeven over de optie die is geselecteerd in het
hoofdmenu aan de linkerkant.
Hieronder volgt een beschrijving van de opties binnen het hoofdmenu:
Start: hier vindt u informatie over de beveiligingsstatus van ESET Smart Security Premium.
Computerscan: een scan van uw computer configureren en starten of een aangepaste scan maken.
Bijwerken: hier wordt informatie weergegeven over updates van de detectie-engine.
Hulpmiddelen: biedt toegang tot logbestanden, beveiligingsstatistieken, weergave van activiteiten, actieve
processen, netwerkverbindingen, Planner, ESET SysInspector en ESET SysRescue.
Instellingen: selecteer deze optie om het beveiligingsniveau aan te passen voor Computer, Internet,
Netwerkbeveiliging en Beveiligingshulpprogramma's.
Help en ondersteuning: biedt toegang tot Help-bestanden, de ESET-kennisbank, de website van ESET en
koppelingen voor een ondersteuningsverzoek aan de klantenservice.
In het gedeelte Start vindt u belangrijke informatie over het huidige beveiligingsniveau van uw computer. In het
statusvenster worden vaak gebruikte functies van ESET Smart Security Premium weergegeven. Hier vindt u ook
informatie over de meest recente update en de vervaldatum van uw programma.

19
Het groene pictogram en de groene status Maximale beveiliging geven aan dat er sprake is van maximale
beveiliging.
Te volgen procedure als het programma niet correct werkt.
Als een actieve beveiligingsmodule niet correct werkt, is het pictogram voor de beveiligingsstatus groen. Een rood
uitroepteken of oranje waarschuwing geeft aan dat de maximale beveiliging niet wordt gewaarborgd. Aanvullende
informatie over de beveiligingsstatus van de modules en mogelijke oplossingen voor het herstellen van de
volledige beveiliging worden weergegeven onder Start. Als u de status van individuele modules wilt wijzigen, klik
dan op Instellingen en selecteer de gewenste module.
Het rode pictogram en de melding 'Maximale beveiliging is niet gewaarborgd' duiden op kritieke problemen.
Er kunnen verschillende redenen zijn waarom deze status wordt weergegeven. Enkele voorbeelden:
Product niet geactiveerd – U kunt ESET Smart Security Premium activeren vanuit Start door te klikken op
Product activeren of Nu kopen onder de Beveiligingsstatus.
Detectie engine is verouderd: deze fout wordt weergegeven na verschillende mislukte pogingen om de
database met viruskenmerken bij te werken. Wij adviseren u de standaardinstellingen te controleren. De
meest gangbare reden voor deze fout is onjuist ingevoerde verificatiegegevens of onjuist
geconfigureerde verbindingsinstellingen.
Antivirus- en antispywarebeveiliging uitgeschakeld – U kunt antivirus- en antispywarebeveiliging
opnieuw inschakelen door te klikken op Alle modules voor antivirus- en antispywarebeveiliging
inschakelen.
ESET firewall uitgeschakeld – Dit probleem wordt ook aangegeven met een beveiligingsmelding naast het
item Netwerk op uw bureaublad. U kunt de netwerkbeveiliging weer inschakelen door op Firewall
inschakelen te klikken.
Licentie verlopen – Dit wordt aangegeven door een rood pictogram van de beveiligingsstatus. Er kunnen
geen updates meer worden uitgevoerd zodra de licentie verloopt. Volg de instructies in het

20
waarschuwingsvenster om uw licentie te vernieuwen.
Het oranje pictogram duidt op beperkte beveiliging. Er kan bijvoorbeeld sprake zijn van een probleem met
het bijwerken van het programma of uw licentie vervalt binnenkort.
Er kunnen verschillende redenen zijn waarom deze status wordt weergegeven. Enkele voorbeelden:
Antidiefstal-optimalisatiewaarschuwing – Dit apparaat is niet geoptimaliseerd voor ESET Antidiefstal.
Mogelijk is geen Phantom-account op uw computer gemaakt. Dit is een beveiligingsvoorziening die
automatisch wordt geactiveerd, wanneer u een apparaat markeert als ontbrekend. U kunt een Phantom-
account maken via de functie Optimalisatie in de ESET Antidiefstal-webinterface.
Gamermodus actief – Het inschakelen van de Gamermodus vormt een potentieel beveiligingsrisico. Als u
deze voorziening uitschakelt, worden alle pop-upvensters uitgeschakeld en worden geplande taken
gestopt.
Uw licentie verloopt binnenkort – Dit wordt aangegeven met een uitroepteken in het pictogram voor de
beveiligingsstatus naast de systeemklok. Wanneer uw licentie is verlopen, kan het programma niet meer
worden bijgewerkt en wordt het pictogram van de beveiligingsstatus rood.
Als u het probleem niet kunt verhelpen met de voorgestelde oplossingen, klikt u op Help en ondersteuning om
toegang te krijgen tot de Help-bestanden of de ESET-kennisbank te doorzoeken. Mocht u nog hulp nodig hebben,
dient u dan een verzoek om ondersteuning in. De klantenservice van ESET zal uw vragen zo spoedig mogelijk
beantwoorden en helpen met het vinden van een oplossing.

21
3.2 Updates
Het uitvoeren van updates van de detectie-engine en programmaonderdelen vormt een belangrijk onderdeel van
de beveiliging van uw systeem tegen schadelijke code. Stel de configuratie en werking zorgvuldig in. Klik in het
hoofdmenu op Bijwerken en klik vervolgens op Controleren op updates om te controleren op updates van de
detectie-engine.
Als de licentiesleutel niet is ingevoerd tijdens de activering van ESET Smart Security Premium, moet u deze op dit
punt opgeven.

22
Het venster Geavanceerde instellingen (klik op Instellingen in het hoofdmenu en klik vervolgens op Geavanceerde
instellingen, of druk op F5 op het toetsenbord) bevat extra updateopties. Als u geavanceerde updateopties wilt
configureren, zoals de updatemodus, proxyservertoegang en LAN-verbindingen, klikt u op het desbetreffende
tabblad in het venster Bijwerken.
3.3 Instellingen voor vertrouwde zones
Het is noodzakelijk om Vertrouwde zones te configureren om uw computer in een netwerkomgeving te beveiligen.
U kunt andere gebruikers toegang tot uw computer verlenen door een Vertrouwde zone te configureren om delen
toe te staan. Klik op Instellingen > Netwerkbeveiliging > Verbonden netwerken en klik op de koppeling onder het
verbonden netwerk. Er wordt een venster met opties weergegeven waarin u de gewenste beveiligingsmodus van
uw computer in het netwerk kunt kiezen.
De detectie van de vertrouwde zone vindt plaats na installatie van ESET Smart Security Premium en telkens
wanneer uw computer verbinding met een nieuw netwerk maakt. Daarom is het in de meeste gevallen niet nodig
de Vertrouwde zones te definiëren. Standaard wordt u wanneer er een nieuwe zone is gedetecteerd door een
dialoogvenster gevraagd om het beveiligingsniveau voor die zone in te stellen.

23
WAARSCHUWING
Een onjuiste configuratie van Vertrouwde zones kan een beveiligingsrisico opleveren voor uw computer.
OPMERKING
Standaard wordt aan werkstations in een vertrouwde zone toegang verleend tot gedeelde bestanden en
printers, is inkomende RPC-communicatie ingeschakeld en is het gebruik van Extern bureaublad mogelijk.
Meer informatie over deze voorziening vindt u in het volgende artikel in de ESET-kennisbank:
Nieuwe netwerkverbinding gedetecteerd in ESET Smart Security
3.4 Antidiefstal
Als u uw computer wilt beschermen in het geval van verlies of diefstal, kiest u een van de volgende opties om uw
computer te registreren bij het ESET Antidiefstal-systeem.
1. Na een geslaagde activering klikt u op Antidiefstal inschakelen om ESET Antidiefstal-functies te activeren voor
de computer die u zojuist hebt geregistreerd.
2. Als u het bericht ESET Antidiefstal is beschikbaar ziet in het deelvenster Start van ESET Smart Security Premium,
kunt u deze functie voor uw computer activeren. Klik op ESET Antidiefstal inschakelen om uw computer te
registreren bij ESET Antidiefstal.
3. Klik in het hoofdvenster van het programma op Instellingen > Beveiligingshulpprogramma's. Klik op
naast ESET Antidiefstal en volg de instructies in het pop-upvenster.

24
OPMERKING
ESET Antidiefstal ondersteunt geen Microsoft Windows Home Servers.
Voor meer instructies met betrekking tot de computerkoppeling van ESET Antidiefstal verwijzen wij u naar Een
nieuw apparaat toevoegen.
3.5 Hulpmiddelen voor Ouderlijk toezicht
Als u Ouderlijk toezicht al hebt ingeschakeld in ESET Smart Security Premium, moet u Ouderlijk toezicht ook
configureren voor de gewenste gebruikersaccounts om het goed te laten werken.
Wanneer Ouderlijk toezicht actief is maar er geen gebruikersaccounts zijn geconfigureerd, wordt Ouderlijk toezicht
is niet ingesteld weergegeven in het deelvenster Start van het hoofdprogrammavenster. Klik op Nu regels instellen
en raadpleeg het hoofdstuk Ouderlijk toezicht voor instructies over het maken van specifieke beperkingen voor uw
kinderen om hen te beschermen tegen mogelijk schadelijk materiaal.

25
4. Werken met ESET Smart Security Premium
Met ESET Smart Security Premium-instellingsopties kunt u de beveiligingsniveaus aanpassen voor uw computer en
netwerk.
Het menu Instellingen is onderverdeeld in de volgende secties:
Computerbeveiliging
Internet-beveiliging
Netwerkbeveiliging
Beveiligingshulpprogramma's
Klik op een onderdeel om geavanceerde instellingen van de bijbehorende beveiligingsmodule aan te passen.
In de instellingen voor Computerbeveiliging kunt u de volgende onderdelen in- of uitschakelen:
Real-timebeveiliging van bestandssysteem: alle bestanden worden gescand op schadelijke code wanneer
deze worden geopend, gemaakt of uitgevoerd op de computer.
HIPS: het HIPS-systeem controleert de gebeurtenissen binnen het besturingssysteem en reageert hierop
overeenkomstig een aangepaste set regels.
Gamer-modus: hiermee schakelt u de Gamer-modus in of uit. U ontvangt een waarschuwingbericht
(potentiële beveiligingsrisico) en het hoofdprogrammavenster wordt oranje weergegeven wanneer u de
gamer-modus hebt ingeschakeld.
Webcambeveiliging: controleert de processen en toepassingen die gebruikmaken van de de camera van de
computer. Voor meer informatie klikt u hier.

26
In de instellingen voor Computerbeveiliging kunt u de volgende onderdelen in- of uitschakelen:
Beveiliging van webtoegang: indien ingeschakeld, wordt alle verkeer via HTTP of HTTPS gescand op schadelijke
software.
Beveiliging van e-mailclient: controleert communicatie die wordt ontvangen via het POP3- en IMAP-protocol.
Antispambeveiliging: hiermee wordt ongevraagde e-mail (spam) gescand.
Antiphishing-beveiliging: filtert websites die worden verdacht van het distribueren van inhoud om gebruikers
te manipuleren voor het verkrijgen van vertrouwelijke gegevens.
In de sectie Netwerkbeveiliging kunt u Firewall, Netwerkaanvalbeveiliging (IDS) en Botnet-beveiliging in- en
uitschakelen.
Als u Beveiligingshulpprogramma's instelt, kunt u de volgende modules aanpassen:
Beveiliging van bankieren en betalingen
Ouderlijk toezicht
Antidiefstal
Wachtwoordmanager
Secure Data
Met Ouderlijk toezicht kunt u webpagina's blokkeren die mogelijk schadelijk materiaal bevatten. Daarnaast kunnen
ouders de toegang verbieden tot meer dan 40 vooraf gedefinieerde websitecategorieën en meer dan 140
subcategorieën.
Als u een uitgeschakeld beveiligingsonderdeel weer wilt inschakelen, klikt u op de schuifregelaar zodat
een groen vinkje verschijnt .
OPMERKING
Wanneer beveiliging met deze methode wordt uitgeschakeld, worden alle uitgeschakelde beveiligingsmodules
ingeschakeld nadat een computer opnieuw wordt opgestart.
Onder in het instellingenvenster bevinden zich aanvullende opties. Met de koppeling Geavanceeerde instellingen
kunt u meer gedetailleerde parameters voor elke module instellen. Gebruik Instellingen importeren/exporteren
als u instellingsparameters wilt laden met een .xml-configuratiebestand of als u uw huidige instellingsparameters
in een configuratiebestand wilt opslaan.

27
4.1 Computerbeveiliging
Klik op Computerbeveiliging in het venster Instellingen om een overzicht weer te geven van alle
beschermingsmodules. Als u afzonderlijke modules tijdelijk wilt uitschakelen, klikt u op . U moet zich wel
realiseren dat het beveiligingsniveau van uw computer hierdoor kan afnemen. Klik op naast een
beveiligingsmodule om geavanceerde instellingen voor die module te openen.
Klik op > Uitsluitingen bewerken naast Real-timebeveiliging van bestandssysteem om het venster met
instellingen voor Uitsluitingen te openen, waarin u bestanden en mappen kunt uitsluiten van scannen.
Antivirus- en antispywarebeveiliging tijdelijk uitschakelen: schakelt alle modules voor antivirus- en
antispywarebeveiliging uit. Wanneer u een beveiliging uitschakelt, wordt een venster geopend waarin u kunt
bepalen hoe lang de beveiliging wordt uitgeschakeld met het vervolgkeuzemenu Tijdsinterval. Klik op Toepassen
om te bevestigen.

28
4.1.1 Detectie-engine
Antivirusbeveiliging biedt bescherming tegen kwaadwillende systeemaanvallen door middel van controle over
bestanden, e-mail en internetcommunicatie. Als een bedreiging via schadelijke code wordt gedetecteerd, kan de
antivirusmodule deze onschadelijk maken door de code eerst te blokkeren en deze vervolgens op te schonen, te
verwijderen of in quarantaine te plaatsen.
Met Scanneropties voor alle beveiligingsmodules (bijvoorbeeld Real-timebeveiliging van bestandssysteem,
Beveiliging van webtoegang) kunt u detectie van de volgende items in- of uitschakelen:
Potentieel ongewenste toepassingen zijn niet per se schadelijk, maar kunnen de prestaties van uw computer
negatief beïnvloeden.
Zie de woordenlijst voor meer informatie over deze typen toepassingen.
Potentieel onveilige toepassingen verwijst naar legitieme commerciële software die kan worden misbruikt voor
schadelijke doeleinden. Enkele voorbeelden van potentieel onveilige toepassingen zijn hulpprogramma's voor
externe toegang, toepassingen voor het kraken van wachtwoorden en keyloggers (programma's die de
toetsaanslagen van een gebruiker registreren). Deze optie is standaard uitgeschakeld.
Zie de woordenlijst voor meer informatie over deze typen toepassingen.
Verdachte toepassingen omvat programma's die zijn gecomprimeerd met software voor compressie of
beveiligingen. Deze typen beveiligingsprogramma's worden vaak misbruikt door auteurs van malware om
detectie te omzeilen.
Anti-Stealth-technologie is een geavanceerd systeem dat gevaarlijke programma's zoals rootkits detecteert, die
zichzelf kunnen verbergen voor het besturingssysteem. Dit betekent dat deze programma's niet kunnen worden
gedetecteerd met de gebruikelijke testmethoden.
Met Uitsluitingen kunt u bestanden en mappen opgeven die u wilt uitsluiten van scannen. Om te garanderen dat
alle objecten worden gescand op bedreigingen, is het raadzaam alleen uitzonderingen te maken wanneer dat
absoluut noodzakelijk is. Situaties waarin u een object mogelijk wilt uitsluiten zijn bijvoorbeeld grote
databasevermeldingen die de computer zouden vertragen tijdens een scan of software die conflicteert met de scan.
Zie Uitsluitingen als u een object wilt uitsluiten van scannen.

29
Geavanceerd scannen via AMSI inschakelen: met het hulpprogramma Antimalware Scan Interface van Microsoft
kunnen applicatieontwikkelaars nieuwe verdedigingsmiddelen aanbieden tegen malware (alleen voor Windows
10).
4.1.1.1 Real-timebeveiliging van bestandssysteem
Real-timebeveiliging van bestandssysteem controleert alle gebeurtenissen met betrekking tot antivirusbeveiliging
in het systeem. Alle bestanden worden gescand op schadelijke code wanneer ze worden geopend, gemaakt of
uitgevoerd op de computer. Real-timebeveiliging van bestandssysteem wordt uitgevoerd bij het opstarten van het
systeem.
Real-timebeveiliging van het bestandssysteem wordt standaard gestart bij het opstarten van het systeem en scant
ononderbroken. In bijzondere gevallen (bijvoorbeeld als er een conflict is met een andere real-time scanner) kan
real-timebeveiliging worden uitgeschakeld door Real-timebeveiliging van bestandssysteem automatisch
inschakelen uit te schakelen in Geavanceerde instellingen onder Real-timebeveiliging van bestandssysteem >
Basis.
Te scannen media
Standaard worden alle mediatypen gescand op mogelijke bedreigingen:
Lokale stations: hiermee worden alle systeemschijven gecontroleerd.
Verwisselbare media: hiermee worden cd's/dvd's, USB-opslagapparaten, Bluetooth-apparaten, enz.
gecontroleerd.
Netwerkstations: hiermee worden alle toegewezen stations gescand.
Het wordt aangeraden de standaardinstellingen te gebruiken en deze alleen in specifieke gevallen te wijzigen,
bijvoorbeeld wanneer het scannen van bepaalde media tot aanzienlijke vertragingen in de gegevensoverdracht
leidt.

30
Scannen uitvoeren bij
Standaard worden alle bestanden gescand als ze worden geopend, gemaakt of uitgevoerd. U wordt aangeraden
deze standaardinstellingen te behouden omdat deze het hoogste niveau van real-timebeveiliging voor uw
computer bieden:
Openen van bestand: hiermee wordt het scannen bij het openen van bestanden in- of uitgeschakeld.
Maken van bestanden: hiermee wordt het scannen bij het maken van bestanden in- of uitgeschakeld.
Uitvoeren van bestand: hiermee wordt het scannen bij het uitvoeren van bestanden in- of uitgeschakeld.
Toegang tot verwisselbaar medium: hiermee worden scans in- of uitgeschakeld die worden geactiveerd door
de toegang tot bepaalde verwisselbare media met opslagruimte.
Real-timebeveiliging van het bestandssysteem controleert alle typen media en wordt geactiveerd door
verschillende systeemgebeurtenissen, zoals het openen van een bestand. Met de detectiemethoden van de
ThreatSense-technologie (zoals beschreven in het gedeelte Parameters ThreatSense-engine instellen), kan real-
timebeveiliging van het bestandssysteem worden geconfigureerd om nieuw gemaakte bestanden anders te
behandelen dan bestaande bestanden. U kunt Real-timebeveiliging van bestandssysteem bijvoorbeeld zodanig
configureren dat nieuw gemaakte bestanden uitvoeriger worden gecontroleerd.
Om te zorgen voor een minimale systeembelasting bij het gebruik van real-timebeveiliging, worden reeds
gescande bestanden niet opnieuw gescand (tenzij ze zijn gewijzigd). Bestanden worden onmiddellijk na elke
update voor de detectie-engine opnieuw gescand. Dit gedrag wordt bestuurd met Smart-optimalisatie. Als Smart-
optimalisatie wordt uitgeschakeld, worden alle bestanden elke keer gescand wanneer ze worden gebruikt. Als u
deze instelling wilt wijzigen, drukt u op F5 om Geavanceerde instellingen te openen en vouwt u Detectie-engine >
Real-timebeveiliging van bestandssysteem uit. Klik op ThreatSense-parameter > Overige en schakel Smart-
optimalisatie inschakelen in of uit.
4.1.1.1.1 Aanvullende ThreatSense-parameters
Aanvullende ThreatSense-parameters voor nieuwe en aangepaste bestanden
De waarschijnlijkheid van infectie van nieuwe en gewijzigde bestanden is in vergelijking hoger dan van bestaande
bestanden. Om deze reden worden deze bestanden gecontroleerd met aanvullende scanparameters. ESET Smart
Security Premium werkt met geavanceerde heuristiek die nieuwe bedreigingen kan detecteren voordat de update
van de detectie-engine is uitgebracht in combinatie met scanmethoden op basis van viruskenmerken. Naast nieuwe
bestanden worden Zelfuitpakkende archieven (.SFX) en programma's voor Runtime-compressie (intern
gecomprimeerde uitvoerbare bestanden) ook gescand. Archieven worden standaard tot maximaal tien
nestingsniveaus gescand. De grootte van de archieven wordt voorafgaand aan de scan niet gecontroleerd. Als u de
instellingen voor het scannen van archieven wilt wijzigen, schakelt u Standaardinstellingen voor archieven scannen
uit.
Aanvullende ThreatSense-parameters voor uitgevoerde bestanden
Geavanceerde heuristiek voor uitvoeren bestanden: standaard wordt geavanceerde heuristiek gebruikt wanneer
bestanden worden uitgevoerd. Indien ingeschakeld raden we ten zeerste aan Smart-optimalisatie en ESET LiveGrid®
ingeschakeld te laten om de invloed op systeemprestaties te minimaliseren.
Geavanceerde heuristiek voor uitvoeren bestanden van verwisselbare media: geavanceerde heuristiek emuleert
code in een virtuele omgeving en beoordeelt het gedrag alvorens de code vanaf verwisselbare media mag worden
uitgevoerd.

31
4.1.1.1.2 Opschoonniveaus
Real-timebeveiliging biedt drie opschoonniveaus (u vindt de instellingen voor opschoonniveaus door te klikken op
Parameters voor ThreatSense-engine instellen in het gedeelte Real-timebeveiliging van bestandssysteem en
vervolgens op Opschonen te klikken).
Niet opschonen: geïnfecteerde bestanden worden niet automatisch opgeschoond. Er wordt een
waarschuwingsvenster weergegeven en de gebruiker kan een actie kiezen. Dit niveau is bedoeld voor gevorderde
gebruikers die weten welke stappen genomen moeten worden in geval van een infiltratie.
Normaal opschonen: het programma probeert automatisch een geïnfecteerd bestand op te schonen of te
verwijderen op basis van een vooraf gedefinieerde actie (afhankelijk van het type infiltratie). Detectie en
verwijdering van een geïnfecteerd bestand worden aangegeven met een melding in de rechterbenedenhoek van
het scherm. Als de juiste actie niet automatisch kan worden geselecteerd, worden andere vervolgacties
aangeboden. Hetzelfde gebeurt als een vooraf gedefinieerde actie niet kan worden voltooid.
Volledig opschonen: alle geïnfecteerde bestanden (inclusief archieven) worden opgeschoond of verwijderd. Dit
geld niet voor systeembestanden. Als deze niet kunnen worden opgeschoond, wordt een waarschuwingsvenster
geopend waarin de gebruiker een actie kan selecteren.
WAARSCHUWING
Archieven met een of meer geïnfecteerde bestanden kunnen op twee manieren worden verwerkt. In de
standaardmodus (Normaal opschonen) worden archieven waarin alle bestanden zijn geïnfecteerd, in hun geheel
verwijderd. In de modus Volledig opschonen worden archieven met minstens één geïnfecteerd bestand
verwijderd, ongeacht de status van de overige bestanden in het archief.
4.1.1.1.3 Wanneer moet de configuratie voor real-timebeveiliging worden gewijzigd?
Real-timebeveiliging vormt het meest essentiële onderdeel van het onderhouden van een veilig systeem. Wees
altijd voorzichtig bij het wijzigen van de bijbehorende parameters. Wij adviseren u de parameters alleen te wijzigen
in specifieke situaties.
Na installatie van ESET Smart Security Premium zijn alle instellingen geoptimaliseerd om gebruikers een zo hoog
mogelijk niveau van systeembeveiliging te bieden. Als u wilt terugkeren naar de standaardinstellingen, klik dan op
naast elk tabblad in het venster (Geavanceerde instellingen > Detectie-engine > Real-timebeveiliging van
bestandssysteem).
4.1.1.1.4 Real-timebeveiliging controleren
U kunt controleren of real-timebeveiliging werkt en virussen detecteert door een testbestand van eicar.com te
gebruiken. Dit testbestand is een onschadelijk bestand dat door alle antivirusprogramma's kan worden
gedetecteerd. Het bestand is gemaakt door het bedrijf EICAR (European Institute for Computer Antivirus Research)
om de werking van antivirusprogramma's te testen. Het bestand kan worden gedownload op
http://www.eicar.org/download/eicar.com.
OPMERKING
Voordat u een real-time beveiligingscontrole kunt uitvoeren, moet u de firewall uitschakelen. Als de firewall is
ingeschakeld, wordt het bestand gedetecteerd en wordt voorkomen dat testbestanden worden gedownload.

32
4.1.1.1.5 Te volgen procedure als real-timebeveiliging niet werkt
In dit hoofdstuk beschrijven wij problemen die zich kunnen voordoen bij het gebruik van real-timebeveiliging, en
oplossingen hiervoor.
Real-timebeveiliging is uitgeschakeld
Als real-timebeveiliging per ongeluk is uitgeschakeld door de gebruiker, moet deze opnieuw worden geactiveerd. U
kunt real-timebeveiliging opnieuw activeren door in het hoofdprogrammavenster naar Instellingen te gaan en te
klikken op Computerbeveiliging > Real-timebeveiliging van bestandssysteem.
Als real-timebeveiliging niet wordt gestart bij het opstarten van het systeem, komt dat waarschijnlijk doordat Real-
timebeveiliging van bestandssysteem inschakelen is uitgeschakeld. Als u deze optie wilt inschakelen, gaat u naar
Geavanceerde instellingen (F5) en klikt u op Detectie-engine > Real-timebeveiliging van bestandssysteem.
Als real-timebeveiliging geen detecties uitvoert en geen infiltraties opschoont
Controleer of er geen andere antivirusprogramma's zijn geïnstalleerd op de computer. Als er twee
antivirusprogramma's tegelijk zijn geïnstalleerd, conflicteren ze mogelijk met elkaar. U wordt aangeraden alle
andere antivirusprogramma's van uw systeem te verwijderen voordat u ESET installeert.
Real-timebeveiliging wordt niet gestart
Als real-timebeveiliging niet wordt gestart bij het opstarten van het systeem (en Real-timebeveiliging van
bestandssysteem inschakelen is ingeschakeld), komt dit waarschijnlijk door een conflict met andere programma's.
Neem voor hulp bij het oplossen van dit probleem contact op met de klantenservice van ESET.
4.1.1.2 Computerscan
De scanner op aanvraag is een belangrijk onderdeel van uw antivirusoplossing. Hiermee worden scans uitgevoerd
op bestanden en mappen op uw computer. Vanuit beveiligingsoogpunt is het van essentieel belang dat
computerscans niet alleen worden uitgevoerd als infecties worden vermoed, maar regelmatig als onderdeel van
routinematige beveiligingsmaatregelen. We raden u aan regelmatig dieptescans op uw systeem uit te voeren om
virussen te detecteren die niet worden gedetecteerd door Real-timebeveiliging van bestandssysteem wanneer
deze naar de schijf worden geschreven. Dit kan gebeuren als Real-timebeveiliging van bestandssysteem een keer
tijdelijk uitgeschakeld is geweest, als de detectie-engine niet meer actueel is of als een bestand niet als virus werd
gedetecteerd toen het op schijf werd opgeslagen.
Er zijn twee soorten Computerscan beschikbaar. Met Uw computer scannen maakt u snel een scan van het systeem
zonder dat u scanparameters hoeft op te geven. Met Aangepaste scan kunt u vooraf gedefinieerde scanprofielen
selecteren die speciaal zijn gericht op specifieke locaties en kunt u ook specifieke scandoelen.
Uw computer scannen
Met Uw computer scannen kunt u snel een computerscan starten en geïnfecteerde bestanden opschonen zonder
dat gebruikersinterventie is vereist. Het voordeel van Uw computer scannen is dat het gebruiksvriendelijk is en er
geen gedetailleerde scanconfiguratie nodig is. Deze scan controleert alle bestanden op lokale stations en schoont
automatisch gedetecteerde infiltraties op of verwijdert deze. Het opschoonniveau wordt automatisch ingesteld op
de standaardwaarde. Zie Opschonen voor meer informatie over typen opschoonbewerkingen.
U kunt ook de functie Scan slepen en neerzetten gebruiken om een bestand of map handmatig te scannen. U kikt op
het bestand of de map en verplaatst de muisaanwijzer naar het gemarkeerde gebied terwijl u de muisknop
ingedrukt houdt en vervolgens loslaat. Daarna wordt de toepassing naar de voorgrond verplaatst.
De volgende scanopties zijn beschikbaar onder Geavanceerde scans:

33
Aangepaste scan
Met Aangepaste scan kunt u scanparameters opgeven, zoals scandoelen en scanmethoden. Het voordeel van
Aangepaste scan is de mogelijkheid om de parameters in detail te configureren. Configuraties kunnen worden
opgeslagen in door de gebruiker gedefinieerde scanprofielen. Deze profielen zijn met name handig als het scannen
herhaaldelijk plaatsvindt met dezelfde parameters.
Verwisselbare media scannen
Vergelijkbaar met Uw computer scannen: snel een scan starten van verwisselbare media (zoals cd/dvd/USB) die op
dat moment op de computer zijn aangesloten. Dit kan handig zijn wanneer u een USB-flashstation aansluit op een
computer en u de inhoud wilt scannen op malware en andere mogelijke bedreigingen.
Dit type scan kan ook worden gestart door op Aangepaste scan te klikken, Verwisselbare media te selecteren in het
vervolgkeuzemenu Scandoelen en op Scannen te klikken.
Laatste scan herhalen
Hiermee kunt u snel de eerder uitgevoerde scan starten met dezelfde instellingen als waarmee deze is uitgevoerd.
Zie Scanvoortgang voor meer informatie over het scanproces.
OPMERKING
Wij adviseren u minimaal eenmaal per maand een computerscan uit te voeren. Scannen kan worden
geconfigureerd als een geplande taak in Hulpmiddelen > Meer hulpmiddelen > Planner. Een wekelijkse
computerscantaak plannen
4.1.1.2.1 Aangepaste scan starten
U kunt de Aangepaste scan gebruiken om specifieke delen van een schijf te scannen en niet de volledige schijf.
Hiervoor klikt u op Geavanceerde scans > Aangepaste scan en selecteert u een optie in de vervolgkeuzelijst
Scandoelen of selecteert u specifieke doelen in de boomstructuur.
De vervolgkeuzelij st Scandoelen bevat de volgende, vooraf gedefinieerde scandoelen.
Naar profielinstellingen: hiermee selecteert u doelen die in het geselecteerde scanprofiel zijn ingesteld.
Verwisselbare media: hiermee selecteert u diskettes, USB-opslagapparaten en cd's/dvd's.
Lokale stations: hiermee worden alle harde schijven van het systeem geselecteerd.
Netwerkstations: hiermee worden alle toegewezen netwerkstations geselecteerd.
Geen selectie: hiermee worden alle selecties geannuleerd.
Als u snel naar een scandoel wilt navigeren of een doelmap of bestand(en) wilt toevoegen, voert u de doelmap in
het lege veld onder de mappenlijst in. Dit is alleen mogelijk als er geen doelen zijn geselecteerd in de structuur en
het menu Scandoelen is ingesteld op Geen selectie.

34
U kunt de opschoningsparameters voor de scan configureren onder Geavanceerde instellingen > Detectie-engine >
Computerscan op vraag > ThreatSense-parameters > Opschoning. Om een scan uit te voeren zonder
opschoningsactie, selecteert u Scannen zonder opschonen. De scanhistoriek wordt bewaard in het scanlogboek.
Als Uitsluitingen negeren is ingeschakeld, worden de bestanden met extensies die eerder waren uitgesloten van
de scan, zonder uitzondering gescand.
U kunt een profiel kiezen in het vervolgkeuzemenu Scanprofiel dat u kunt gebruiken wanneer u bepaalde doelen
scant. Het standaardprofiel is Smart scan. Er zijn twee vooraf gedefinieerde scanprofielen, genaamd Dieptescan en
Scan van contextmenu. Deze scanprofielen gebruiken andere ThreatSense-parameters. De beschikbare opties
worden beschreven in Geavanceerde instellingen > Detectie-engine > Malwarescans > On-demand scan >
ThreatSense-parameters.
Klik op Scannen om de scan uit te voeren met de aangepaste parameters die u hebt ingesteld.
Met Scannen als Beheerder kunt u de scan uitvoeren vanuit het beheerdersaccount. Gebruik dit als de huidige
gebruiker niet de juiste rechten heeft om toegang te krijgen tot de bestanden die u wenst te scannen. Deze knop is
niet beschikbaar als de huidige gebruiker geen UAC-bewerkingen kan aanroepen als beheerder.
OPMERKING
U kunt de leogbestanden computerscan bekijken na elke scan door op Logbestanden weergeven te klikken.

35
4.1.1.2.2 Scanvoortgang
In het venster met de scanvoortgang wordt de huidige status van de scan en informatie over het aantal gevonden
bestanden met schadelijke code weergegeven.
OPMERKING
het is normaal dat sommige bestanden, zoals bestanden met wachtwoordbeveiliging of bestanden die exclusief
door het systeem worden gebruikt (doorgaans pagefile.sys en bepaalde logboekbestanden), niet kunnen
worden gescand. Meer informatie vindt u in ons kennisbankartikel.
Scanvoortgang: op de voortgangsbalk ziet u de status van reeds gescande objecten vergeleken met het
percentage nog te scannen objecten. De voortgang van de scan is afgeleid van het totale aantal objecten waarop
de scan wordt uitgevoerd.
Doel: de naam van het object dat wordt gescand en de locatie van het object.
Bedreigingen gevonden: hier wordt het totaalaantal gescande bestanden, gevonden bedreigingen en
opgeschoonde bedreigingen tijdens een scan weergegeven.
Tijdelijk uitschakelen: hiermee wordt een scan onderbroken.
Hervatten: deze optie is zichtbaar wanneer de scan is onderbroken. Klik op Hervatten om met het scannen door
te gaan.
Stoppen: hiermee wordt de scan beëindigd.
Scanlogboek doorbladeren: indien ingeschakeld schuift het scanlogboek automatisch omlaag wanneer nieuwe
invoer wordt toegevoegd, zodat de recentste vermeldingen zichtbaar zijn.
OPMERKING
Klik op het vergrootglas of de pijl om details weer te geven over de scan die op dat moment wordt uitgevoerd. U
kunt nog een parallelle scan uitvoeren door op Uw computer scannen of Aangepaste scan te klikken.
Actie na scannen: hiermee kunt u de computer gepland afsluiten of opnieuw opstarten nadat een scan is voltooid.
Wanneer de scan is voltooid, wordt een dialoogvenster ter bevestiging geopend waarna u 60 seconden de tijd hebt
voordat er actie wordt ondernomen.

36
4.1.1.2.3 Scanprofielen
U kunt uw voorkeursparameters voor scannen opslaan voor toekomstige scans. Wij adviseren u voor elke regelmatig
gebruikte scan een ander profiel te maken (met verschillende scandoelen, scanmethoden en andere parameters).
Als u een nieuw profiel wilt maken, opent u het venster Geavanceerde instellingen (F5) en klikt u op Detectie-
engine > Malwarescans > Op aanvraag scannen > Lijst met profielen. Het venster Profielbeheer bevat de
vervolgkeuzelijst Geselecteerd profiel met bestaande scanprofielen en de optie om een nieuw profiel te maken.
Raadpleeg het gedeelte Parameters voor ThreatSense-engine instellen voor een beschrijving van elke parameter
van de scaninstellingen, zodat u een scanprofiel kunt maken dat aan uw behoeften voldoet.
OPMERKING
Stel: u wilt een eigen scanprofiel maken en de configuratie voor Uw computer scannen is deels geschikt, maar u
wilt geen scanprogramma's voor runtime-compressie of potentieel onveilige toepassingen scannen en u wilt ook
Volledig opschonen toepassen. Geef de naam van uw nieuwe profiel op in het venster Profielbeheer en klik op
Toevoegen. Selecteer uw nieuwe profiel in het vervolgkeuzemenu Geselecteerd profiel en pas de resterende
parameters aan om aan uw vereisten te voldoen, en klik op OK om uw nieuwe profiel op te slaan.
4.1.1.2.4 Logbestand computerscan
Het logbestand computerscan geeft u algemene informatie over de scan. Het gaat hierbij om:
Tijdstip van voltooiing
Totale scantijd
Aantal gevonden bedreigingen
Aantal gescande objecten
Gescande schijven, mappen en bestanden
Datum en tijdstip van de scan
Versie van detectie-engine
4.1.1.3 Scannen bij inactieve status
Scannen bij inactieve status inschakelen: hiermee wordt een volledige computerscan uitgevoerd wanneer uw
computer niet in gebruik is.
Standaard wordt Scannen bij inactieve status niet uitgevoerd als de computer (notebook) op de accu werkt. U kunt
deze instelling ongedaan maken via de functie Ook uitvoeren wanneer de computers op batterij werkt.
Zet Logboekregistratie inschakelen aan als u de uitvoer van een computerscan wilt vastleggen in het gedeelte
Logboekbestanden (klik in het hoofdprogrammavenster op Hulpmiddelen > Meer hulpmiddelen > Logbestanden en
selecteer vervolgens Computerscan in het vervolgkeuzemenu Logbestand).
Detectie van inactieve status wordt uitgevoerd als uw computer de volgende status heeft:
Scherm of schermbeveiliging uitgeschakeld
Computervergrendeling
Afmelding van gebruiker
Klik op ThreatSense-parameters om scanparameters aan te passen (bijvoorbeeld detectiemethoden) voor Scannen
bij inactieve status.

37
4.1.1.4 Opstartscan
De automatische bestandscontrole bij opstarten wordt standaard uitgevoerd als het systeem wordt opgestart en bij
updates van de detectie-engine. Deze scan is afhankelijk van de configuratie en taken van de Planner.
De optie voor het scannen bij het opstarten maakt deel uit van een geplande taak van Controle opstartbestanden
van systeem. Als u de instellingen wilt aanpassen, gaat u naar Hulpmiddelen > Meer hulpmiddelen > Planner, klikt u
op Automatische bestandscontrole bij opstarten en vervolgens op Bewerken. Bij de laatste stap wordt het venster
Automatische bestandscontrole bij opstarten weergegeven (zie volgende hoofdstuk voor meer informatie).
Zie Nieuwe taken maken voor gedetailleerde instructies voor het maken en beheren van een geplande taak.
4.1.1.4.1 Automatische bestandscontrole bij opstarten
Wanneer u een geplande taak Controle opstartbestanden van systeem maakt, hebt u verschillende opties voor het
aanpassen van de volgende parameters:
In het vervolgkeuzemenu Algemeen gebruikte bestanden staat de scandiepte aangegeven voor bestanden die
tijdens het opstarten van het systeem worden uitgevoerd. Dit is gebaseerd op een geavanceerd geheim algortime.
Bestanden worden ingedeeld in aflopende volgorde, op basis van de volgende criteria:
Alle geregistreerde bestanden (het grootste aantal bestanden wordt gescand)
Zelden gebruikte bestanden
Algemeen gebruikte bestanden
Frequent gebruikte bestanden
Alleen de meest frequent gebruikte bestanden (het kleinste aantal bestanden wordt gescand)
Er zijn ook twee specifieke groepen in opgenomen:
Bestanden die worden uitgevoerd vóór aanmelden van gebruiker: bevat bestanden van locaties waar de
gebruiker toegang toe heeft zonder te zijn aangemeld (inclusief bijna alle opstartlocaties, zoals services,
browserhelperobjecten, Winlogon-meldingen, planningsgegevens van Windows, bekende dll's).
Bestanden uitgevoerd na aanmelding gebruiker: bevat bestanden van locaties waar de gebruiker alleen toegang
toe heeft wanneer hij of zij is aangemeld (inclusief bestanden die alleen worden uitgevoerd door een
specifieke gebruiker, zoals bestanden in
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run).
De lijsten van bestanden die moeten worden gescand, staan vast voor elke voorgenoemde groep.
Scanprioriteit: het prioriteitsniveau dat wordt gebruikt om te bepalen wanneer een scan wordt gestart:
Indien inactief: de taak wordt alleen uitgevoerd wanneer het systeem inactief is.
Laagst: met een zo laag mogelijk systeembelasting.
Lager: met een lage systeembelasting.
Normaal: met een gemiddelde systeembelasting.
4.1.1.5 Uitsluitingen
Met uitsluitingen kunt u bestanden en mappen opgeven die u wilt uitsluiten van scannen. Om te garanderen dat
alle objecten worden gescand op bedreigingen, is het raadzaam alleen uitzonderingen te maken wanneer dat
absoluut noodzakelijk is. Er zijn echter situaties waarbij u een object mogelijk moet uitsluiten, bijvoorbeeld grote
databasevermeldingen die de computer zouden vertragen tijdens een scan of software die conflicteert met de scan.
Een object uitsluiten van scannen:
1. Klik op Toevoegen,
2. Typ het pad naar een object of selecteer het in de onderstaande structuur.
Als u een groep bestanden wilt opgeven, kunt u gebruikmaken van jokertekens. Met een vraagteken (?) wordt één
variabel teken aangegeven en met een sterretje (*) wordt een variabelentekenreeks van nul of meer tekens
aangegeven.

38
Voorbeelden
Als u alle bestanden in een map wilt uitsluiten, typt u het pad naar de map en gebruikt u het masker '*.*'.
Als u een heel station wilt uitsluiten, inclusief alle bestanden en submappen, gebruikt u het masker 'D:\*'.
Als u alleen doc-bestanden wilt uitsluiten, gebruikt u het masker '*.doc'.
Als de naam van een uitvoerbaar bestand een bepaald aantal (verschillende) tekens bevat en u alleen weet
dat het eerste teken een D is, gebruikt u de notatie: 'D????.exe'. De vraagtekens staan voor de ontbrekende
(onbekende) tekens.
OPMERKING
een bedreiging binnenin een bestand wordt niet gedetecteerd door de module Real-timebeveiliging van het
bestandssysteem of de module Computerscan als het bestand voldoet aan de criteria voor uitsluiting van
scannen.
Kolommen
Pad: het pad naar uitgesloten bestanden en mappen.
Bedreiging: als er naast een uitgesloten bestand de naam van een bedreiging wordt weergegeven, betekent dit
dat het bestand alleen wordt uitgesloten voor die bedreiging en dus niet volledig. Als dat bestand later
geïnfecteerd raakt met andere malware, wordt het door de antivirusmodule gedetecteerd. Dit type uitsluiting
kan alleen voor bepaalde typen infiltraties worden gebruikt en dit kan worden gedefinieerd in het
waarschuwingsvenster (klik op Geavanceerde opties weergeven en selecteer Uitsluiten van detectie), of door
op Hulpmiddelen > Meer hulpmiddelen > Quarantaine te klikken en vervolgens met de rechtermuisknop op het
bestand in quarantaine te klikken en Herstellen en uitsluiten van detectie te selecteren in het contextmenu.
Besturingselementen
Toevoegen: hiermee sluit u objecten uit van detectie.
Bewerken: hiermee kunt u geselecteerde vermeldingen bewerken.
Verwijderen: hiermee worden geselecteerde vermeldingen verwijderd.

39
4.1.1.6 ThreatSense-parameters
ThreatSense bestaat uit talloze complexe methoden voor het detecteren van bedreigingen. Deze technologie is
proactief. Dit betekent dat ook beveiliging wordt geboden tijdens de vroege verspreiding van een nieuwe
bedreiging. Er wordt gebruikgemaakt van een combinatie van codeanalyse, code-emulatie, generieke kenmerken,
viruskenmerken, die samenwerken om de systeembeveiliging aanzienlijk te verbeteren. De scanengine is in staat
verschillende gegevensstromen tegelijk te controleren voor maximale efficiëntie en een zo hoog mogelijk
detectiepercentage. De ThreatSense-technologie verhindert tevens de installatie van rootkits.
Via de instellingsopties van de ThreatSense-engine kunt u verschillende scanparameters opgeven:
Bestandstypen en extensies die moeten worden gescand
De combinatie van verschillende detectiemethoden
Opschoonniveaus, enz.
Klik op ThreatSense-parameters in het venster Geavanceerde instellingen van elke module die gebruikmaakt van
de ThreatSense-technologie (zie hieronder). Verschillende beveiligingsscenario's vereisen mogelijk verschillende
configuraties. Daarom is ThreatSense individueel configureerbaar voor de volgende beveiligingsmodules:
Real-timebeveiliging van bestandssysteem
Scannen bij inactieve status
Opstartscan
Documentsbescherming
Beveiliging van e-mailclient
Beveiliging van webtoegang
Computerscan
ThreatSense-parameters zijn in hoge mate geoptimaliseerd voor elke module. Als u de parameters wijzigt, kan dit
een aanzienlijke invloed hebben op de werking van het systeem. Als bijvoorbeeld parameters voor het altijd
scannen van software voor runtime-compressie worden gewijzigd of als geavanceerde heuristiek wordt
ingeschakeld in de module voor real-time beveiliging van het bestandssysteem, zou dit kunnen resulteren in een
vertraging van het systeem (normaliter worden alleen nieuw gemaakte bestanden gescand via deze methoden).
Wij adviseren de standaard ThreatSense-parameters ongewijzigd te laten voor alle modules met uitzondering van
Computerscan.
Te scannen objecten
In dit gedeelte kunt u opgeven welke computeronderdelen moeten worden gescand op infiltraties.
Werkgeheugen: hiermee wordt gescand op bedreigingen die gericht zijn op het werkgeheugen van het systeem.
Opstartsectoren: hiermee worden opstartsectoren gescand op de aanwezigheid van virussen in de Master Boot
Record.
E-mailbestanden: het programma ondersteunt de volgende extensies: DBX (Outlook Express) en EML.
Archieven: het programma ondersteunt de volgende extensies: ARJ, BZ2, CAB, CHM, DBX, GZIP, ISO/BIN/NRG,
LHA, MIME, NSIS, RAR, SIS, TAR, TNEF, UUE, WISE, ZIP, ACE, enzovoort.
Zelfuitpakkende archieven: zelfuitpakkende archieven zijn archieven die zichzelf kunnen uitpakken.
Software voor runtime-compressie: na uitvoering wordt software voor runtime-compressie (in tegenstelling tot
standaardarchieftypen) in het geheugen uitgepakt. Dankzij emulatie van de programmacode kan de scanner niet
alleen standaardprogramma's voor statische compressie (zoals UPX, yoda, ASPack en FSG), maar ook allerlei
andere compressiesoftware herkennen.
Scanopties
Selecteer de methoden die moeten worden gebruikt wanneer het systeem op infiltraties wordt gescand. De
volgende opties zijn beschikbaar:

40
Heuristiek: een heuristiek is een algoritme dat de (schadelijke) activiteit van programma's analyseert. Het
voornaamste voordeel van deze technologie is het vermogen om schadelijke software te identificeren die nog
niet bestond of niet werd behandeld in de vorige database met viruskenmerken. Aan de andere kant is er een
(uiterst kleine) kans op vals alarm.
Geavanceerde heuristiek/DNA/Smart-kenmerken: de geavanceerde heuristiek is een uniek heuristisch algoritme
dat door ESET is ontwikkeld en dat is geoptimaliseerd voor het detecteren van computerwormen en trojaanse
paarden. Dit algoritme is geschreven in geavanceerde programmeertalen. Het gebruik van geavanceerde
heuristiek vergroot bedreigingsdetectiemogelijkheden van ESET-producten aanzienlijk. Kenmerken
(handtekeningen) kunnen virussen op betrouwbare wijze detecteren en identificeren. Dankzij het automatische
updatesysteem zijn nieuwe kenmerken binnen enkele uren beschikbaar. Het nadeel van kenmerken is dat ze
alleen bekende virussen (of varianten van deze virussen) detecteren.
Grayware (of potentieel ongewenste toepassingen) is een brede categorie software die niet ondubbelzinnig
schadelijk is als andere typen malware, zoals virussen en Trojaanse paarden. Grayware kan echter aanvullende
ongewenste software installeren, het gedrag van het digitale apparaat wijzigen, of activiteiten uitvoeren die de
gebruiker niet heeft goedgekeurd of had verwacht.
Categorieën die tot grayware worden gerekend, zijn onder andere: software die advertenties weergeeft,
downloadpakketten, diverse taakbalken voor browsers, software met misleidend gedrag, bundleware, trackware of
andere twijfelachtige software, of software die gebruikmaakt van illegale of op zijn minst onethische zakelijke
praktijken (ondanks dat de software er legitiem uitziet) en door een eindgebruiker mogelijk als ongewenst wordt
beschouwd wanneer die weet wat de software kan doen als die zou worden geïnstalleerd.
Een potentieel onveilige toepassing is er een die op zich legitieme software is (mogelijk in de handel verkrijgbaar),
maar die door een aanvaller kan worden misbruikt. Detectie van deze typen applicaties kan worden ingeschakeld of
uitgeschakeld door gebruikers van ESET-software.
Er kunnen zich situaties voordoen waarin een gebruiker van mening is dat de voordelen van een potentieel
ongwenste toepassingen opwegen tegen de risico's ervan. ESET geeft om deze reden dergelijke toepassingen een
lagere risicocategorie in vergelijking tot andere typen schadelijke software, zoals Trojaanse paarden of wormen.
Waarschuwing - Potentiële bedreiging gevonden
Als er een potentieel ongewenste toepassing wordt gedetecteerd, kunt u beslissen welke actie moet worden
ondernomen:
1. Opschonen/Verbinding verbreken: met deze optie wordt de actie beëindigd en wordt voorkomen dat de
bedreiging uw systeem binnenkomt.
2. Negeren: Met deze optie kan een potentiële dreiging uw systeem binnendringen.
3. Als u wilt toestaan dat de toepassing in de toekomst zonder onderbreking op uw computer wordt uitgevoerd,
klikt u op Geavanceerde opties en schakelt u het selectievakje in naast Uitsluiten van detectie.

41
Wanneer een potentieel ongewenste applicatie wordt gedetecteerd die niet kan worden opgeschoond, verschijnt
het bericht Adres werd geblokkeerd. Voor meer informatie over deze gebeurtenis navigeert u naar Hulpmiddelen >
Logbestanden > Gefilterde websites in het hoofdmenu.
Potentieel ongewenste toepassingen - Instellingen
Tijdens de installatie van uw ESET-product kunt u kiezen of u detectie van potentieel ongewenste toepassingen wilt
inschakelen, zoals hieronder aangegeven:
WAARSCHUWING
Potentieel ongewenste toepassingen kunnen adware of werkbalken installeren, of andere ongewenste en
onveilige programmafuncties bevatten.
Deze instellingen kunnen op elk moment worden aangepast in uw programma-instellingen. Volg deze instructies
als u de detectie van potentieel ongewenste, onveilige of verdachte toepassingen wilt uitschakelen:
1. Open uw ESET-product. Mijn ESET-product openen
2. Druk op de toets F5 om Geavanceerde instellingen te openen.
3. Klik op Antivirus en schakel Detectie van potentieel ongewenste toepassingen inschakelen, Detectie van
potentieel onveilige toepassingen inschakelen en Detectie van verdachte toepassingen inschakelen in of uit
op basis van uw voorkeuren. Bevestig uw keuze door op OK te klikken.

42
Potentieel ongewenste toepassingen - Softwarewrappers
Een softwarewrapper is een speciaal soort aanpassing van een toepassing die door bepaalde websites wordt
gebruikt waarop bestanden als downloads worden aangeboden. Een hulpprogramma van derden installeert het
programma dat u wilt downloaden maar voegt er extra software aan toe, zoals werkbalken of adware. De extra
software kan ook de startpagina van uw webbrowser en zoekinstellingen wijzigen. Websites waarop dergelijke
bestanden worden gehost melden deze wijzigingen vaak niet aan de leverancier van de software en degenen die
de bestanden downloaden. Vaak wordt de optie om uit te schrijven ook verborgen. Om deze redenen classificeert
ESET softwarewrappers als een type potentieel ongewenste toepassing, zodat gebruikers kunnen kiezen of ze de
download accepteren of niet.
Raadpleeg dit artikel in de ESET-kennisbank voor een bijgewerkte versie van deze Help-pagina.
Potentieel onveilige toepassingen: Potentieel onveilige toepassingen is de aanduiding die wordt gebruikt voor
commerciële, legitieme programma's zoals hulpprogramma's voor externe toegang, toepassingen voor het kraken
van wachtwoorden en keyloggers (programma's die elke toetsaanslag van een gebruiker registreren). Deze optie
is standaard uitgeschakeld.
De opschooninstellingen bepalen het gedrag van de scanner tijdens het opschonen van geïnfecteerde bestanden.
Er zijn 3 opschoonniveaus.
Uitsluitingen
Een extensie is het deel van een bestandsnaam dat wordt afgebakend door een punt. De extensie definieert het
type en de inhoud van het bestand. In dit gedeelte van de instellingen van ThreatSense-parameters kunt u de
typen bestanden definiëren die u wilt scannen.
Overige
Wanneer u de instellingen van de parameters voor de ThreatSense-engine configureert voor een computerscan
op aanvraag, zijn ook de volgende opties beschikbaar in het gedeelte Overige:
Alternatieve gegevensstromen (ADS) scannen: alternatieve gegevensstromen (ADS) die worden gebruikt door het
NTFS-bestandssysteem zijn bestands- en mapkoppelingen die onzichtbaar zijn voor normale scantechnieken.
Veel infiltraties proberen detectie te vermijden door zichzelf te vermommen als alternatieve gegevensstromen.

43
Achtergrondscans uitvoeren met lage prioriteit: elke scanprocedure neemt een bepaalde hoeveelheid
systeembronnen in beslag. Als u werkt met programma's waarbij de systeembronnen zwaar worden belast, kunt u
achtergrondscans met een lage prioriteit inschakelen en zo bronnen besparen ten gunste van uw toepassingen.
Alle objecten in logbestand registreren: als deze optie wordt geselecteerd, worden alle gescande bestanden,
zelfs de niet-geïnfecteerde, in het logbestand vermeld. Als er in een archief bijvoorbeeld een infiltratie wordt
gevonden, bevat het logbestand ook schone bestanden in dat archief.
Smart-optimalisatie inschakelen: wanneer Smart-optimalisatie is ingeschakeld, worden de meest optimale
instellingen gebruikt om het meest efficiënte scanniveau te garanderen, terwijl ook de hoogste scansnelheden
worden behaald. De diverse beveiligingsmodules scannen op intelligente wijze, waarbij gebruik wordt gemaakt
van verschillende scanmethoden die op specifieke bestandstypen worden toegepast. Als de Smart-optimalisatie
is uitgeschakeld, worden alleen de door de gebruiker gedefinieerde instellingen in de ThreatSense-technologie
van de betreffende modules toegepast bij het uitvoeren van een scan.
Tijdstempel van laatste toegang bewaren: selecteer deze optie om de oorspronkelijke toegangstijd van gescande
bestanden te handhaven in plaats van deze bij te werken (bijvoorbeeld voor gebruik met back-upsystemen).
Limiet
Gebruik het gedeelte Limiet om de maximale grootte op te geven van objecten die moeten worden gescand,
evenals het maximale niveau voor het scannen van geneste archieven:
Objectinstellingen
Maximale objectgrootte: de maximale grootte van objecten die moeten worden gescand. De antivirusmodule
scant dan alleen objecten die kleiner zijn dan de opgegeven grootte. Deze waarde mag alleen worden
gewijzigd door gevorderde gebruikers die een specifieke reden hebben om grotere objecten niet te scannen.
Standaardwaarde: onbeperkt.
Maximale scantijd voor object (sec.): de maximale tijd voor het scannen van een object. Als hier een waarde
is ingevoerd, wordt het scannen van een object beëindigd wanneer die tijd is verstreken, ongeacht of de scan
is voltooid. Standaardwaarde: onbeperkt.
Instellingen voor archieven scannen
Nestingsniveau voor archieven: het maximum aantal niveaus waarop archieven moeten worden gescand.
Standaardwaarde: 10.
Maximale grootte van bestand in archief: gebruik deze optie om de maximale bestandsgrootte op te geven
voor bestanden in archieven (als deze worden uitgepakt) die moeten worden gescand. Standaardwaarde:
onbeperkt.
OPMERKING
Het is in de meeste gevallen niet nodig de standaardwaarden te wijzigen.
4.1.1.6.1 Opschonen
De opschooninstellingen bepalen het gedrag van de scanner tijdens het opschonen van geïnfecteerde bestanden. Er
zijn 3 opschoonniveaus.

44
4.1.1.6.2 Bestandsextensies die moeten worden uitgesloten van scans
Een extensie is het deel van een bestandsnaam dat wordt afgebakend door een punt. De extensie definieert het
type en de inhoud van het bestand. In dit gedeelte van de instellingen van ThreatSense-parameters kunt u de typen
bestanden definiëren die u wilt scannen.
Standaard worden alle bestanden gescand. Elke extensie kan worden toegevoegd aan de lijst met bestanden die
zijn uitgesloten van scannen.
Soms is het nodig bestanden uit te sluiten als door het scannen van bepaalde bestandstypen het programma dat
bepaalde extensies gebruikt niet goed wordt uitgevoerd. Het kan bijvoorbeeld raadzaam zijn de extensies
.edb, .eml en .tmp uit te sluiten als gebruik wordt gemaakt van Microsoft Exchange-servers.
Met de knoppen Toevoegen en Verwijderen kunt u het scannen van specifieke bestandsextensies inschakelen of
verbieden. Als u een nieuwe extensie aan de lijst wilt toevoegen, klikt u op Toevoegen, typt u de extensie in het
lege veld (bijvoorbeeld tmp) en klikt u op OK. Als u Geef meerdere waarden op selecteert, kunt u meerdere
bestandsextensies opgeven, van elkaar gescheiden door regels, komma's of puntkomma's. Als meervoudige
selectie is ingeschakeld, worden extensies in de lijst weergegeven. Selecteer een extensie in de lijst en klik op
Verwijderen om de extensie uit de lijst te verwijderen. Klik op Bewerken als u een geselecteerde extensie wilt
bewerken.
U kunt de speciale teken ? (vraagteken) gebruiken. Het vraagteken vertegenwoordigt elk willekeurig teken.
OPMERKING
Om de precieze extensie (indien aanwezig) van een bestand in een Windows-besturingssysteem te zien, dient u
de optie Extensies voor bekende bestandstypen verbergen uit te schakelen in Configuratiescherm > Mapopties >
tabblad Weergave en deze wijziging toe te passen.
4.1.1.7 Er is een infiltratie gedetecteerd
Infiltraties kunnen het systeem bereiken vanaf verschillende toegangspunten, zoals vanaf webpagina's, vanuit
gedeelde mappen, via e-mail of vanaf verwisselbare apparaten (USB, externe schijven, cd's, dvd's, diskettes, enz.).
Standaardgedrag
Als algemeen voorbeeld van de manier waarop infiltraties door ESET Smart Security Premium worden behandeld,
kunt u infiltraties vaststellen met:
Real-timebeveiliging van bestandssysteem
Beveiliging van webtoegang
Beveiliging van e-mailclient
Computerscan op aanvraag
Voor elk van deze opties wordt het standaardopschoonniveau gebruikt en bij alle opties wordt gepoogd het
bestand op te schonen en in Quarantaine te plaatsen of de verbinding te verbreken. Er wordt een meldingsvenster
weergegeven in het systeemvak in de rechterbenedenhoek van het scherm. Zie Opschonen voor meer informatie
over opschoonniveaus en gedrag.

45
Opschonen en verwijderen
Als er geen vooraf gedefinieerde actie is die voor Real-timebeveiliging van bestandssysteem wordt uitgevoerd,
wordt u in een waarschuwingsvenster gevraagd een optie te selecteren. Gewoonlijk zijn de opties Opschonen,
Verwijderen en Geen actie beschikbaar. U wordt afgeraden de optie Geen actie te selecteren, omdat in dat geval de
geïnfecteerde bestanden ongewijzigd blijven. De uitzondering hierop is wanneer u er zeker van bent dat het
bestand onschadelijk is en het per vergissing is gedetecteerd.
Pas opschonen toe als een bestand is aangevallen door een virus dat schadelijke code aan het bestand heeft
toegevoegd. Als dit het geval is, probeert u eerst het geïnfecteerde bestand op te schonen zodat het in de
oorspronkelijke staat kan worden hersteld. Als het bestand uitsluitend uit schadelijke code bestaat, wordt het
verwijderd.
Als een geïnfecteerd bestand is 'vergrendeld' of wordt gebruikt door een systeemproces, wordt het doorgaans pas
verwijderd wanneer het is vrijgegeven (normaliter na een herstart van het systeem).
Meerdere bedreigingen
Als niet alle geïnfecteerde bestanden zijn opgeschoond tijdens een Computerscan (of als het Opschoonniveau is
ingesteld op Niet opschonen), wordt een waarschuwingsvenster weergegeven waarin u de acties voor die
bestanden kunt kiezen. Selecteer de acties voor de bestanden (acties worden per bestand in de lijst ingesteld) en
klik op Voltooien.
Bestanden in archieven verwijderen
In de modus Standaard opschonen wordt het volledige archief alleen verwijderd als dit uitsluitend geïnfecteerde
bestanden en geen schone bestanden bevat. Met andere woorden, archieven worden niet verwijderd als deze ook
onschadelijke, schone bestanden bevatten. Wees voorzichtig bij het gebruik van een scan in de modus Volledig
opschonen. Hierbij wordt het archief namelijk verwijderd als het minimaal één geïnfecteerd bestand bevat,
ongeacht de status van de andere bestanden in het archief.

46
Als de computer tekenen van infectie door malware vertoont, bijvoorbeeld traag is, vaak vastloopt, enz., wordt u
aangeraden het volgende te doen:
Open ESET Smart Security Premium en klik op Computerscan
Klik op Uw computer scannen (zie voor meer informatie Computerscan).
Als de scan is voltooid, controleer dan in het logbestand het aantal gescande, geïnfecteerde en opgeschoonde
bestanden
Als u alleen een bepaald gedeelte van uw schijf wilt scannen, klik dan op Aangepaste scan en selecteer de doelen
die u wilt scannen op virussen.
4.1.1.8 Documentsbescherming
Deze bescherming houdt in dat documenten van Microsoft Office worden gescand voordat ze worden geopend,
evenals bestanden die automatisch worden gedownload door Internet Explorer, zoals Microsoft ActiveX-
elementen. Documentsbescherming biedt extra bescherming boven op Real-timebeveiliging van bestandssysteem
en kan worden uitgeschakeld voor betere prestaties op systemen die geen grote aantallen Microsoft Office-
documenten kunnen verwerken.
Om Documentsbescherming te activeren, opent u het venster Geavanceerde instellingen (druk op F5) > Detectie-
engine > Malwarescans > Documentsbescherming en klikt u op de schakelaar Integreren in systeem.
OPMERKING
Deze functionaliteit wordt geactiveerd door toepassingen die gebruikmaken van Microsoft Antivirus API
(bijvoorbeeld Microsoft Office 2000 en hoger of Microsoft Internet Explorer 5.0 en hoger).
4.1.2 Verwisselbare media
ESET Smart Security Premium biedt automatisch scannen van verwisselbare media (cd/dvd/USB/...). Met deze
module kunt u geplaatste media scannen. Dit kan handig zijn als de beheerder van de computer wil voorkomen dat
gebruikers verwisselbare media met ongewenste inhoud op de computer gebruiken.
Actie bij invoeren van verwisselbare media: selecteer de standaardactie die wordt uitgevoerd wanneer een
verwisselbaar media-apparaat in de computer wordt geplaatst (cd/dvd/USB). Als Scanopties weergeven wordt
geselecteerd, wordt er een melding weergegeven waarin u de gewenste actie kunt kiezen:
Niet scannen: er wordt geen actie uitgevoerd en het venster Nieuw apparaat gedetecteerd wordt gesloten.
Automatisch apparaat scannen: hiermee wordt een computerscan op aanvraag uitgevoerd op het ingevoerde
verwisselbare media-apparaat.
Scanopties weergeven: hiermee opent u het gedeelte met instellingen voor verwisselbare media.
Als er een verwisselbaar medium wordt geplaatst, wordt het volgende dialoogvenster weergegeven:
Nu scannen: hiermee wordt een scan van het verwisselbare medium geactiveerd.
Later scannen: het scannen van het verwisselbare medium wordt uitgesteld.
Instellingen: hiermee wordt Geavanceerde instellingen geopend.
Altijd de geselecteerde optie gebruiken: als deze optie wordt geselecteerd, wordt dezelfde actie uitgevoerd als er
de volgende keer een verwisselbaar medium wordt geplaatst.

47
Daarnaast biedt ESET Smart Security Premium de functie Apparaatbeheer. Hiermee kunt u regels definiëren voor
het gebruik van externe apparaten op een bepaalde computer. Meer informatie over apparaatbeheer vindt u in het
gedeelte Apparaatbeheer.
4.1.3 Apparaatbeheer
Apparaatbeheer
ESET Smart Security Premium biedt automatisch beheer van apparaten (cd/dvd/USB/...). Met deze module kunt u
een apparaat blokkeren of uitgebreide filters/machtigingen ervoor aanpassen en bepalen hoe de gebruiker een
apparaat opent en ermee werkt. Dit kan handig zijn als de beheerder van de computer wil voorkomen dat er
apparaten met ongewenste inhoud worden gebruikt.
Ondersteunde externe apparaten:
Schijfopslag (HDD, verwisselbare USB-schijf)
Cd/dvd
USB-printer
FireWire-opslag
Bluetooth-apparaat
Smartcardlezer
Scanapparaat
Modem
LPT/COM-poort
Draagbaar apparaat
Microfoon
Alle apparaattypen
De opties van Instellingen van apparaatbeheer kunnen worden aangepast via Geavanceerde instellingen (F5) >
Apparaatbeheer.
Als u de schakelaar naast Integreren in systeem inschakelt, wordt de functie Apparaatbeheer geactiveerd in ESET
Smart Security Premium; u dient de computer opnieuw op te starten om de wijzigingen te bekrachtigen. Als
Apparaatbeheer is ingeschakeld, wordt Regels actief, waardoor u het venster Regeleditor kunt openen.
OPMERKING
U kunt verschillende groepen met apparaten maken waarop verschillende regels worden toegepast. Ook kunt u
slechts een groep met apparaten maken waarop de regels met de actie Lezen/Schrijven of Alleen-lezen wordt
toegepast. Hierdoor zorgt u ervoor dat niet-herkende apparaten door Apparaatbeheer worden geblokkeerd als
zij verbinding met uw computer proberen te maken.
Als er een apparaat wordt geplaatst dat door een bestaande regel wordt geblokkeerd, wordt er een
meldingsvenster weergegeven en wordt de toegang tot het apparaat geblokkeerd.
Webcam-beveiliging
Door de schakelaar naast In systeem integreren om te zetten worden de functie Webcam-beveiliging geactiveerd in
ESET Smart Security Premium. Als Webcam-beveiliging is ingeschakeld, wordt Regels actief, waardoor u het venster
Regeleditor kunt openen.

48
4.1.3.1 Regeleditor voor apparaatbeheer
In het venster Regeleditor voor apparaatbeheer worden bestaande regels weergegeven. In dit venster kunnen
externe apparaten die gebruikers op de computer aansluiten, gedetailleerd worden beheerd.
Bepaalde apparaten kunnen per gebruiker of gebruikersgroep worden toegestaan of geblokkeerd. Dit wordt
gebaseerd op aanvullende apparaatparameters die in de regelconfiguratie worden gespecificeerd. De lijst met
regels bevat verschillende beschrijvingen van een regel, waaronder de naam, het type extern apparaat, de actie die
moet worden uitgevoerd na het aansluiten van een extern apparaat in uw computer en de vastgelegde ernst.
Klik op Toevoegen of Bewerken om een regel te beheren. Klik op Kopiëren om een nieuwe regel te maken aan de
hand van vooraf gedefinieerde opties die al voor een andere geselecteerde regel gelden. De XML-tekenreeks die
wordt weergegeven als u op een regel klikt, kan worden gekopieerd naar het klembord om systeembeheerders te
helpen bij het exporteren/importeren van deze gegevens, bijvoorbeeld om deze te gebruiken in ESET Remote
Administrator.
Door Ctrl ingedrukt te houden en te klikken, kunt u meerdere regels selecteren en meerdere acties toepassen op
de geselecteerde regels; u kunt deze bijvoorbeeld omhoog of omlaag verplaatsen in de lijst. Met het selectievakje
Ingeschakeld kan een regel worden in- of uitgeschakeld. Dit kan handig zijn als u de regel niet permanent wilt
verwijderen en later nog wilt gebruiken.
Het beheer wordt uitgevoerd met regels die gesorteerd zijn op prioriteit. De regels met hoge prioriteit staan
bovenaan.
Logboekvermeldingen kunnen worden weergegeven in het hoofdprogrammavenster van ESET Smart Security
Premium in Hulpmiddelen > Meer hulpmiddelen > Logbestanden.
In het Apparaatbeheerlogbestand worden alle gebeurtenissen vastgelegd waardoor Apparaatbeheer wordt
geactiveerd.

49
4.1.3.2 Regels voor apparaatbeheer toevoegen
Met een regel voor apparaatbeheer wordt de actie gedefinieerd die wordt genomen als er een apparaat op de
computer wordt aangesloten dat voldoet aan de regelcriteria.
Geef een beschrijving van de regel op in het veld Naam, zodat deze gemakkelijk te herkennen is. Klik op de
schakelaar naast Regel ingeschakeld om de regel in- of uit te schakelen. Dit kan handig zijn als u de regel niet
definitief wilt verwijderen.
Apparaattype
Kies het type extern apparaat in het vervolgkeuzemenu (schijfopslag/draagbaar apparaat/Bluetooth/FireWire/...).
Informatie over apparaattypen wordt verzameld bij het besturingssysteem en is zichtbaar in Apparaatbeheer van
het systeem als er een apparaat met de computer is verbonden. Opslagapparaten zijn onder andere externe
schijven of gewone geheugenkaartlezers die zijn aangesloten met USB of FireWire. Met smartcardlezers worden
lezers bedoeld van smartcards met een geïntegreerd circuit, zoals SIM-kaarten of verificatiekaarten. Voorbeelden
van scanapparaten zijn scanners of camera's. Omdat deze apparaten alleen informatie over hun acties weergeven
en geen informatie weergeven over hun gebruikers, kunnen ze alleen in hun algemeenheid worden geblokkeerd.
Actie
Toegang tot niet-opslagapparaten kan worden toegestaan of geblokkeerd. Met regels voor opslagapparaten kunnen
echter de volgende rechten worden geselecteerd:
Lezen/schrijven: er is volledige toegang tot het apparaat mogelijk.
Blokkeren: de toegang tot het apparaat wordt geblokkeerd.
Alleen-lezen: alleen leestoegang op het apparaat is toegestaan.
Waarschuwen: elke keer dat een apparaat verbinding maakt, ontvangt de gebruiker een melding of het
apparaat is toegestaan/geblokkeerd, en wordt er een vermelding in het logbestand opgenomen. Apparaten
worden niet onthouden, dus er wordt ook een melding weergegeven als hetzelfde apparaat later opnieuw
verbinding maakt.
Houd er rekening mee dat niet alle acties (machtigingen) beschikbaar zijn voor alle apparaattypen. Als het apparaat
een opslagapparaat is, zijn alle vier de acties beschikbaar. Voor apparaten die geen opslagapparaat zijn, zijn slechts
drie acties beschikbaar (een voorbeeld: de actie Alleen lezen is niet beschikbaar voor Bluetooth; dit houdt in dat

50
voor Bluetooth-apparaten alleen de volgende drie acties mogelijk zijn: toestaan, blokkeren en waarschuwen).
Criteriatype – Selecteer Apparaatgroep of Apparaat.
Aanvullende parameters die hieronder worden weergegeven, kunnen worden gebruikt voor het verfijnen van
regels om ze nauwkeurig af te stemmen op apparaten. Alle parameters zijn hoofdlettergevoelig:
Leverancier: u kunt filteren op leveranciersnaam of -id.
Model: de naam van het apparaat.
Serienummer: externe apparaten hebben doorgaans een eigen serienummer. Bij een cd of dvd is dit het
serienummer van het medium, niet dat van het station.
OPMERKING
Als deze parameters niet zijn opgegeven, zal de regel deze velden negeren. Filterparameters in alle tekstvelden
zijn ongevoelig voor hoofdletters en jokertekens (*, ?) worden niet ondersteund.
OPMERKING
Als u informatie over een apparaat wilt zien, maakt u een regel voor dat apparaattype, verbindt u het apparaat
met uw computer en controleert u de apparaatdetails in het logbestand van Apparaatbeheer.
Ernst van logboekregistratie
ESET Smart Security Premium slaat belangrijke gebeurtenissen op in een logbestand, dat rechtstreeks vanuit het
hoofdmenu kan worden bekeken. Klik op Hulpmiddelen > Logbestanden en selecteer vervolgens Apparaatbeheer
in het vervolgkeuzemenu Logbestand.
Altijd : alle gebeurtenissen worden vastgelegd.
Diagnostisch: informatie die nodig is om het programma af te stemmen wordt vastgelegd.
Informatie: informatieve berichten, waaronder berichten over geslaagde updates, plus alle bovenstaande
records worden geregistreerd.
Waarschuwing: kritieke fouten en waarschuwingsberichten worden geregistreerd.
Geen: er worden geen logbestanden geregistreerd
Regels kunnen worden beperkt tot bepaalde gebruikers. Hiervoor voegt u de regels toe aan de Lijst met gebruikers:
Toevoegen: hiermee wordt het dialoogvenster Objecttypen: gebruikers of groepen weergegeven, waarin u de
gewenste gebruikers kunt selecteren.
Verwijderen: hiermee verwijdert u de geselecteerde gebruiker uit het filter.
OPMERKING
Alle apparaten kunnen worden gefilterd met gebruikersregels (scanapparaten geven bijvoorbeeld geen
informatie over gebruikers, maar alleen over acties).
4.1.3.3 Editor beveiligingsregels webcam
Dit venster biedt een overzicht van de bestaande regels en laat de controle van de applicaties en processen toe die
toegang hebben tot uw webcam op basis van de actie die u hebt ondernomen.
De volgende acties zijn beschikbaar:
Toegang blokkeren
Vragen
Toegang toestaan

51
4.1.4 HIPS (Host-based Intrusion Prevention System)
WAARSCHUWING
Wijzigingen in de HIPS-instellingen mogen alleen worden aangebracht door ervaren gebruikers. Onjuiste
configuratie van HIPS-instellingen kunnen leiden tot systeeminstabiliteit.
Het Host-based Intrusion Prevention System (HIPS) beschermt uw systeem tegen malware of andere ongewenste
activiteiten die als enig doel hebben de beveiliging van uw computer te omzeilen. HIPS koppelt geavanceerde
gedragsanalyse aan de detectiemogelijkheden van het netwerkfilter om actieve processen, bestanden en
registersleutels te controleren. HIPS werkt afzonderlijk van Real-timebeveiliging van bestandssysteem en is geen
firewall. Hiermee worden alleen processen gecontroleerd die in het besturingssysteem worden uitgevoerd.
U vindt de HIPS-instellingen onder Geavanceerde instellingen (F5) > Detectie-engine > HIPS > Basis. De HIPS-status
(ingeschakeld/uitgeschakeld) wordt weergegeven in het ESET Smart Security Premium-hoofdprogrammavenster,
onder Instellingen > Computerbeveiliging.
ESET Smart Security Premium gebruikt de ingebouwde Zelfverdedigingstechnologie als onderdeel van HIPS om te
voorkomen dat schadelijke software uw antivirus- en antispywarebeveiliging beschadigt of uitschakelt.
Zelfverdediging beschermt cruciale systeemprocessen en processen van ESET, registersleutels en bestanden, zodat
deze niet worden gemanipuleerd.
Beveiligingsservice inschakelen: schakelt de kernelbeveiliging in (Windows 8.1, 10).
Geavanceerde geheugenscanner werkt in combinatie met Exploit blocker voor een betere bescherming tegen
malware die is ontworpen om detectie te omzeilen door middel van verhulling of codering. Geavanceerde
geheugenscanner is standaard ingeschakeld. Raadpleeg de woordenlijst voor meer informatie over dit type
beveiliging.
Exploit Blocker is ontworpen om de beveiliging te verstevigen van veelbedreigde toepassingen zoals webbrowsers,
PDF-readers, e-mailclients en MS Office-onderdelen. Exploit blocker is standaard ingeschakeld. Raadpleeg de
woordenlijst voor meer informatie over dit type beveiliging.
Ransomwareschild is een andere beschermlaag die werkt als onderdeel van de HIPS-functie. U moet het LiveGrid®-
reputatiesysteem inschakelen om ervoor te zorgen dat het Ransomwareschild werkt. Klik hier voor meer informatie

52
over dit type beveiliging.
Het filteren kan op vier manieren worden uitgevoerd:
Automatische modus: bewerkingen worden ingeschakeld, met uitzondering van vooraf gedefinieerde regels die uw
systeem beveiligen.
Smart-modus: de gebruiker ontvangt alleen een melding over uiterst verdachte gebeurtenissen.
Interactieve modus: gebruiker moet bewerkingen bevestigen.
Op beleid gebaseerde modus: bewerkingen worden geblokkeerd.
Leermodus: bewerkingen worden ingeschakeld en er wordt na elke bewerking een regel gemaakt. Regels die in
deze modus zijn gemaakt, kunnen worden bekeken in de Regeleditor, maar hun prioriteit is lager dan de prioriteit
van de regels die handmatig zijn gemaakt of regels die zijn gemaakt in de automatische modus. Als u Leermodus
selecteert in het vervolgkeuzemenu van de HIPS-filtermodus, wordt de instelling Leermodus eindigt om
beschikbaar gemaakt. Selecteer hoe lang u de leermodus actief wilt hebben. De maximumduur is 14 dagen.
Wanneer de opgegeven duur is verstreken, wordt u gevraagd de regels te bewerken die door HIPS zijn gemaakt
terwijl deze zich in de leermodus bevond. Ook kunt u een andere filtermodus kiezen, of de beslissing uitstellen en
doorgaan met de leermodus.
Modus ingesteld na vervallen van leermodus: selecteer de filtermodus om te gebruiken na het vervallen van de
leermodus.
Het HIPS-systeem controleert gebeurtenissen binnen het besturingssysteem en reageert dienovereenkomstig op
basis van de regels die vergelijkbaar zijn met die van de Firewall. Klik op Bewerken naast Regels om het venster
HIPS-regelbeheer te openen. In het venster HIPS-regels kunt u regels selecteren, toevoegen of verwijderen.
In het volgende voorbeeld laten we zien hoe u ongewenst gedrag van toepassingen kunt beperken:
1. Geef de regel een naam en selecteer Blokkeren in het vervolgkeuzemenu Actie.
2. Zet de schakelaar Gebruiker informeren aan om een melding weer te geven wanneer er een regel wordt
toegepast.
3. Selecteer minimaal één bewerking waarvoor de regel wordt toegepast. Selecteer in het venster
Brontoepassingen de optie Alle toepassingen in het vervolgkeuzemenu om uw nieuwe regel toe te passen
op alle toepassingen die een van de geselecteerde bewerkingen op alle opgegeven toepassingen proberen
uit te voeren.
4. Selecteer Status van een andere toepassing wijzigen. (alle bewerkingen worden beschreven in de Help-
pagina's van het product, die kunnen worden geopend door op F1 te drukken.).
5. Selecteer Bepaalde toepassingen in de vervolgkeuzelijst en Toevoegen om een of meerdere toepassingen
toe te voegen die u wilt beveiligen.
6. Klik op Voltooien om uw nieuwe regel op te slaan.

53
4.1.4.1 Geavanceerde instellingen
De volgende opties zijn handig voor het analyseren van de werking van een toepassing en om eventuele fouten op
te lossen:
Stuurprogramma's die altijd mogen worden geladen: geselecteerde stuurprogramma's mogen altijd worden
geladen ongeacht de geconfigureerde filtermodus, tenzij deze expliciet door een gebruikersregel worden
geblokkeerd.
Alle geblokkeerde bewerkingen in logboek opnemen: alle geblokkeerde bewerkingen worden geregistreerd in het
HIPS-logboek.
Melding weergeven bij wijzigingen in opstarttoepassingen: geeft een melding weer op het bureaublad wanneer
een toepassing wordt toegevoegd aan of verwijderd uit de lijst met opstartbestanden.
Raadpleeg het artikel in onze ESET-kennisbank voor een bijgewerkte versie van deze Help-pagina.

54
4.1.4.2 Interactief venster van HIPS
Als de standaardactie voor een regel is ingesteld op Vragen, wordt er een dialoogvenster weergegeven elke keer
wanneer de regel wordt geactiveerd. U kiezen uit Weigeren en Toestaan. Als u in de opgegeven tijd geen actie
kiest, wordt er een nieuwe actie op basis van de regels geselecteerd.
In het dialoogvenster kunt u regels maken op basis van nieuwe door HIPS gedetecteerde acties en vervolgens de
voorwaarden definiëren waaronder die acties worden toegestaan of geweigerd. Instellingen voor de exacte
parameters kunnen worden geopend door op Details te klikken. Regels die op deze manier zijn gemaakt, zijn
gelijkwaardig aan de regels die handmatig zijn gemaakt. Hierdoor kan een regel die in een dialoogvenster is
gemaakt, minder specifiek kan zijn dan de regel waardoor het dialoogvenster is geactiveerd. Dit betekent dat
wanneer een dergelijke regel is gemaakt, dezelfde bewerking hetzelfde venster kan activeren.
Met Onthouden tot toepassing wordt gesloten wordt de actie (Toestaan/Weigeren) gebruikt tot de regels of
filtermodus worden gewijzigd, de HIPS-module wordt bijgewerkt of het systeem opnieuw wordt gestart. Na een
van deze drie acties worden tijdelijke regels verwijderd.

55
4.1.4.3 Potentieel ransomware-gedrag gedetecteerd
Dit interactief venster verschijnt wanneer nieuw potentieel ransomwaregedrag werd gedetecteerd. U kiezen uit
Weigeren en Toestaan.
Het dialoogvenster laat toe om het bestand te laten analyseren of uit te sluiten van detectie. Klik op Details voor
extra detectieparameters.
BELANGRIJK
ESET Live Grid moet zijn ingeschakeld om Ransomware-beveiliging correct te laten werken.
4.1.5 Gamer-modus
De Gamer-modus is een functie voor gebruikers die niet willen dat het gebruik van hun software wordt
onderbroken, die niet willen dat er pop-upvensters verschijnen en die willen dat de belasting van de CPU minimaal
is. De Gamer-modus kan ook worden gebruikt tijdens presentaties die niet mogen worden gestoord door
antivirusactiviteit. Als u deze functie inschakelt, worden alle pop-upvensters uitgeschakeld en wordt de activiteit
van de planner volledig gestopt. Systeembeveiliging wordt nog steeds uitgevoerd op de achtergrond, maar er wordt
geen interactie van de gebruiker gevraagd.
U kunt de Gamer-modus in- of uitschakelen in het hoofdprogrammavenster onder Instellingen >
Computerbeveiliging door te klikken op of naast Gamer-modus. Omdat het inschakelen van de
Gamer-modus een potentieel beveiligingsrisico is, wordt het pictogram met de beveiligingsstatus op de taakbalk
oranje en wordt er een waarschuwing weergegeven. U ziet deze waarschuwing ook in het hoofdprogrammavenster,
waar Gamer-modus actief oranje wordt weergegeven.
Activeer Gamer-modus automatisch inschakelen wanneer toepassingen in de modus Volledig scherm worden
uitgevoerd onder Geavanceerde instellingen (F5) Hulpmiddelen > Gamer-modus om de Gamer-modus te starten
wanneer u een toepassing op het volledige scherm start en te stoppen nadat u de toepassing hebt afgesloten.
Activeer Gamer-modus automatisch uitschakelen na om de tijdsduur te bepalen waarna de Gamer-modus
automatisch wordt uitgeschakeld.
OPMERKING
Als de Firewall zich in de Interactieve modus bevindt en de Gamer-modus is ingeschakeld, kunt u mogelijk
moeilijk verbinding maken met internet. Dit kan een probleem zijn als u een game start die verbinding maakt
met internet. Gewoonlijk wordt u gevraagd een dergelijke actie te bevestigen (als er geen communicatieregels
of uitzonderingen zijn gedefinieerd), maar in de Gamer-modus is interactie met de gebruiker uitgeschakeld. Als

56
u communicatie toestaat, definieert u een communicatieregel voor toepassingen die dit probleem ondervinden
of gebruikt u een andere Filtermodus in de Firewall. Houd er rekening mee dat als de Gamer-modus is
ingeschakeld en u naar een webpagina of toepassing gaat die een beveiligingsrisico met zich meebrengt, deze
mogelijk wordt geblokkeerd zonder uitleg of waarschuwing omdat interactie met de gebruiker is uitgeschakeld.
4.2 Internet-beveiliging
De web- en e-mailconfiguratie is te vinden in het venster Instellingen door te klikken op Internet-beveiliging. Hier
kunt u meer geavanceerde instellingen van het programma weergeven.
Internettoegang is een standaardfunctie op personal computers. Helaas is internet het belangrijkste medium
geworden voor het verspreiden van schadelijke code. Daarom is het essentieel dat u de instellingen voor
Beveiliging van webtoegang zorgvuldig overweegt.
Klik op om beschermingsinstellingen voor web/e-mail/antiphishing/antispam te openen in Geavanceerde
instellingen.
Beveiliging van e-mailclient biedt beheer van e-mailcommunicatie die wordt ontvangen via het POP3- en IMAP-
protocol. Met behulp van de invoegtoepassing voor uw e-mailclient biedt ESET Smart Security Premium controle
over alle communicatie van en naar uw e-mailclient (POP3, MAPI, IMAP, HTTP).
Antispambeveiliging filtert ongevraagde e-mail.
Als u op het tandrad klikt naast Antispambeveiliging worden de volgende opties beschikbaar:
Configureren...: hiermee opent u geavanceerde instellingen voor antispambeveiliging van de e-mailclient.
Witte lijst/Zwarte lijst/Uitzonderingenlijst van gebruiker: hiermee opent u een dialoogvenster waarin u als
veilig of onveilig beschouwde e-mailadressen kunt toevoegen, bewerken of verwijderen. Volgens de hier
opgegeven regels, wordt e-mail afkomstig van deze adressen niet gescand en niet als spam beschouwd. Klik op

57
Uitzonderingenlijst van gebruiker om een dialoogvenster te openen waarin u e-mailadressen kunt toevoegen,
bewerken of verwijderen die mogelijk vervalst zijn (spoofing) en die worden gebruikt voor het verzenden van
spam. E-mailberichten afkomstig van adressen die in de uitzonderingenlijst staan worden altijd gescand op
spam.
Antiphishing-beveiliging biedt u de mogelijkheid webpagina's te blokkeren waarvan bekend is dat deze voor
phishingdoeleinden worden gebruikt. Wij adviseren u dringend alle opties van Antiphishing ingeschakeld te laten.
Het is mogelijk om de beschermingsmodule voor web/e-mail/antiphishing/antispam tijdelijk uit te schakelen door
te klikken op .
4.2.1 Beveiliging van webtoegang
Internettoegang is een standaardfunctie op een personal computer. Helaas is het ook het belangrijkste medium
geworden voor het overdragen van schadelijke code. Beveiliging van webtoegang wordt geregeld door de
communicatie tussen webbrowsers en externe servers te controleren. Hierbij worden de regels voor HTTP
(Hypertext Transfer Protocol) en HTTPS (HTTP met gecodeerde communicatie) gehanteerd.
Toegang tot webpagina's waarvan bekend is dat deze schadelijke inhoud bevatten, wordt geblokkeerd voordat er
inhoud wordt gedownload. Alle overige webpagina's worden gescand door de ThreatSense-scanengine wanneer ze
worden geladen, en geblokkeerd als er schadelijke inhoud wordt ontdekt. Met Beveiliging van webtoegang wordt
op twee niveaus beveiliging geboden; blokkeren op basis van zwarte lijsten en blokkeren op basis van inhoud.
U wordt dringend geadviseerd de optie Beveiliging van webtoegang in te schakelen. Deze optie vindt u in het
hoofdprogrammavenster van ESET Smart Security Premium door naar Instellingen > Internetbeveiliging >
Beveiliging van webtoegang te gaan.
De volgende opties zijn beschikbaar in Geavanceerde instellingen (F5) > Web en e-mail > Beveiliging van
webtoegang:
Webprotocollen: hiermee kunt u de controle configureren voor deze standaardprotocollen, die door de meeste
internetbrowsers worden gebruikt.
URL-adresbeheer: hier kunt u HTTP-adressen opgeven die u wilt blokkeren, toestaan of uitsluiten van controle.
ThreatSense-parameters: dit zijn geavanceerde instellingen voor de virusscanner. Hier kunt u instellingen
configureren zoals welke typen objecten u wilt scannen (e-mail, archieven, enz.), detectiemethoden voor
Beveiliging van webtoegang, enz.

58
4.2.1.1 Basis
Beveiliging van webtoegang inschakelen: als dit is ingeschakeld, worden Beveiliging webtoegang en Antiphishing-
beveiliging niet uitgevoerd.
Geavanceerd scannen van browserscripts inschakelen: als dit is ingeschakeld, worden JavaScript-programma's
uitgevoerd door internetbrowsers gecontroleerd door de antivirusscanner.
OPMERKING
Het wordt ten zeerste aangeraden de optie Beveiliging van webtoegang ingeschakeld te laten.
4.2.1.2 Webprotocollen
ESET Smart Security Premium is standaard geconfigureerd om het HTTP-protocol te controleren, dat door de meeste
webbrowsers wordt gebruikt.
Instellingen voor HTTP-scanner
In Windows Vista en later wordt HTTP-verkeer altijd gecontroleerd op alle poorten voor alle toepassingen. In
Windows XP kunt u Poorten die worden gebruikt door HTTP-protocol aanpassen in Geavanceerde instellingen
(F5) > Web en e-mail > Beveiliging van webtoegang > Webprotocollen. HTTP-verkeer wordt gecontroleerd op de
opgegeven poorten voor alle toepassingen, en op alle poorten voor toepassingen die zijn gemarkeerd als Web-
en e-mailclients.
Instellingen voor HTTPS-scanner
ESET Smart Security Premium ondersteunt ook HTTPS-protocolcontrole. HTTPS-communicatie maakt gebruikt
van een gecodeerd kanaal om gegevens uit te wisselen tussen server en client. ESET Smart Security Premium
controleert de communicatie via de protocollen SSL (Secure Socket Layer) en TLS (Transport Layer Security). Het
programma scant alleen verkeer op poorten die zijn gedefinieerd in Poorten die worden gebruikt door HTTP-
protocol, ongeacht de versie van het besturingssysteem.
Versleutelde communicatie wordt standaard gescand. Als u de instellingen van de scanner wilt bekijken, navigeert
u naar SSL/TLS in het gedeelte Geavanceerde instellingen, klikt u op Web en e-mail > SSL/TLS en schakelt u de optie
SSL/TLS-protocolfiltering inschakelen in.
4.2.1.3 URL-adresbeheer
In de sectie voor URL-adresbeheer kunt u HTTP-adressen opgeven die u wilt blokkeren, toestaan of uitsluiten van
controle.
Websites in Lijst met geblokkeerde adressen staan zijn niet toegankelijk, tenzij ze ook staan in Lijst met toegestane
adressen. Websites die staan in Lijst met adressen die zijn uitgesloten van controle worden niet gescand op
schadelijke code wanneer ze worden bezocht.
SSL/TLS-protocolfiltering inschakelen moet worden geselecteerd als u naast HTTP-webpagina's ook HTTPS-adressen
wilt filteren. Anders worden alleen de domeinen toegevoegd van HTTPS-sites die u hebt bezocht, niet de volledige
URL.
Als u een URL-adres toevoegt aan de Lijst met adressen uitgesloten van filteren, wordt het adres uitgesloten van
scannen. U kunt ook bepaalde adressen toestaan of blokkeren door deze toe te voegen aan de Lijst met toegestane
adressen of de Lijst met geblokkeerde adressen.
Als u alle HTTP-adressen wilt blokkeren behalve adressen die in de actieve Lijst met toegestane adressen staan,
voeg dan * toe aan de actieve Lijst met geblokkeerde adressen.
U kunt de speciale tekens * (sterretje) en ? (vraagteken) gebruiken in lijsten. Het sterretje vervangt elke
willekeurige tekenreeks, terwijl het vraagteken elk willekeurig symbool vervangt. Wees voorzichtig met het
opgeven van uitgesloten adressen. De lijst mag alleen vertrouwde en veilige adressen bevatten. Ga tevens
zorgvuldig om met de symbolen * en ? en zorg ervoor dat deze correct worden gebruikt in deze lijst. Zie HTTP-
adres/domeinmasker toevoegen voor informatie over hoe u een heel domein inclusief alle subdomeinen veilig

59
kunt laten overeenkomen. Als u een lijst wilt activeren, selecteert u Lijst actief. Als u een melding wilt krijgen
wanneer u een adres invoert van de huidige lijst, selecteert u Op de hoogte gesteld.
OPMERKING
met URL-adresbeheer kunt u ook het openen van bepaalde bestandstypen blokkeren of toestaan tijdens het
surften op internet. Als u bijvoorbeeld niet wilt dat uitvoerbare bestanden worden geopend, selecteert u in het
vervolgkeuzemenu de lijst waarin u deze bestanden wilt blokkeren en voert u het masker "**.exe" in.
Besturingselementen
Toevoegen: hiermee maakt u een nieuwe lijst naast de vooraf gedefinieerde lijsten Dit kan handig zijn als u
verschillende groepen adressen om logische redenen gescheiden wilt houden. Een voorbeeld: een lijst met
geblokkeerde adressen kan adressen bevatten van een externe openbare zwarte lijst, en een andere lijst kan
een eigen zwarte lijst zijn, waardoor het eenvoudiger is de externe lijst bij te werken en uw eigen lijst
ongewijzigd te laten.
Bewerken: hiermee past u bestaande lijsten aan. Gebruik dit om adressen om toe te voegen of te verwijderen.
Verwijderen: hiermee verwijdert u bestaande lijsten. Dit is alleen mogelijk bij lijsten die zijn gemaakt met
Toevoegen, niet bij standaardlijsten.
4.2.2 Beveiliging van e-mailclient
4.2.2.1 E-mailclients
Door integratie van ESET Smart Security Premium met uw e-mailclient neemt het niveau van actieve beveiliging
tegen schadelijke code in e-mailberichten toe. Als uw e-mailclient wordt ondersteund, kan integratie in ESET Smart
Security Premium worden ingeschakeld. Als integratie in uw e-mailclient wordt geactiveerd, wordt de ESET Smart
Security Premium-werkbalk rechtstreeks in de e-mailclient opgenomen (de werkbalk voor nieuwere versies van
Windows Live Mail wordt niet opgenomen), waardoor e-mailbeveiliging nog efficiënter is. De instellingen voor
integratie vindt u onder Geavanceerde instellingen (F5) > Web en e-mail > Beveiliging van e-mailclient > E-
mailclients.
Integratie in e-mailclient
De e-mailclients die momenteel worden ondersteund zijn onder andere Microsoft Outlook, Outlook Express,
Windows Mail en Windows Live Mail. E-mailbeveiliging werkt als een invoegtoepassing voor deze programma's.
Het belangrijkste voordeel van de invoegtoepassing is dat deze onafhankelijk is van het gebruikte protocol.
Wanneer de e-mailclient een gecodeerd bericht ontvangt, wordt dit gedecodeerd en naar de virusscanner

60
verstuurd. Raadpleeg het volgende artikel in de ESET-kennisbank voor een volledige lijst met ondersteunde e-
mailclients en de bijbehorende versies.
Zelfs als integratie niet is ingeschakeld, wordt e-mailcommunicatie beschermd door de module Beveiliging van
e-mailclient (POP3, IMAP).
Schakel Controle bij wijziging inhoud Postvak IN uitschakelen wanneer u ervaart dat het systeem traag wordt bij
het werken met MS Outlook. Dit kan voorkomen wanneer e-mail wordt opgehaald vanuit het archief van Kerio
Outlook Connector.
Te scannen e-mail
Beveiliging van e-mail door clientplug-ins inschakelen : als de beveiliging van de e-mailclient is uitgeschakeld,
is de bescherming van de e-mailclient door protocolfiltering nog steeds ingeschakeld.
Ontvangen e-mail: hiermee wordt het controleren van ontvangen berichten in- of uitgeschakeld.
Verzonden e-mail: hiermee wordt het controleren van verzonden berichten in- of uitgeschakeld.
Gelezen e-mail: hiermee wordt het controleren van gelezen berichten in- of uitgeschakeld.
Uit te voeren actie op geïnfecteerde e-mail
Geen actie: als u deze optie inschakelt, worden geïnfecteerde bijlagen gemeld, maar wordt niets gedaan met e-
mails.
E-mail verwijderen: de gebruiker wordt geattendeerd op bedreigingen en het bericht wordt verwijderd.
E-mail verplaatsen naar de map Verwijderde items: geïnfecteerde e-mails worden automatisch verplaatst naar
de map Verwijderde items.
E-mail verplaatsen naar map: geïnfecteerde e-mails worden automatisch verplaatst naar de opgegeven map.
Map: geef de aangepaste map op waar u geïnfecteerde e-mails naar toe wilt verplaatsen nadat deze zijn
gedetecteerd.
Scan herhalen na bijwerken: hiermee wordt het opnieuw scannen na het bijwerken van de detectie-engine in-
of uitgeschakeld.
Scanresultaten van andere modules accepteren: als dit is ingeschakeld, accepteert de module E-mailbeveiliging
de scanresultaten van andere beveiligingsmodules (scannen van POP3, IMAP-protocollen).
OPMERKING
We raden aan Beveiliging van e-mail door clientplug-ins inschakelen en Beveiliging van e-mail door
protocolfiltering inschakelen in te schakelen. Deze instellingen vindt u onder Geavanceerde instellingen (F5) >
Web en e-mail > Beveiliging van e-mailclient > E-mailclients).
4.2.2.2 E-mailprotocollen
IMAP en POP3 zijn de meest gangbare protocollen die worden gebruikt voor de ontvangst van e-mailcommunicatie
in e-mailclients. Het IMAP-protocol (Internet Message Access Protocol) is een ander internetprotocol voor het
ophalen van e-mail. IMAP heeft enkele voordelen ten opzichte van POP3. Er kunnen bijvoorbeeld meerdere clients
gelijktijdig verbinding maken met hetzelfde postvak, waarbij de informatie over de berichtstatus (gelezen,
beantwoord, verwijderd, enzovoort) behouden blijft. ESET Smart Security Premium biedt beveiliging voor deze
protocollen, ongeacht welke e-mailclient wordt gebruikt en zonder dat de e-mailclient opnieuw hoeft te worden
geconfigureerd.
De beveiligingsmodule die deze controle verzorgt, wordt automatisch geïnitieerd bij het opstarten van het systeem
en is vervolgens actief in het geheugen. IMAP-protocolcontrole wordt automatisch uitgevoerd zonder dat de e-
mailclient opnieuw hoeft te worden geconfigureerd. Standaard wordt alle communicatie op poort 143 gescand,
maar andere communicatiepoorten kunnen zo nodig worden toegevoegd. Poortnummers moeten van elkaar
worden gescheiden door een komma.
U kunt IMAP/IMAPS- en POP3/POP3S-protocolcontrole configureren in Geavanceerde instellingen. U krijgt toegang
tot deze instelling door Web en e-mail > Beveiliging van e-mailclient > E-mailprotocollen uit te vouwen.
E-mailbeveiliging door protocolfiltering inschakelen: activeert het controleren van e-mailprotocollen.

61
In Windows Vista en later worden IMAP- en POP3-protocollen automatisch gedetecteerd en gescand op alle
poorten. In Windows XP wordt alleen Poorten gebruikt door POP3-protocol gescand voor alle toepassingen, en alle
poorten worden gescand voor toepassingen die zijn gemarkeerd als Web- en e-mailclients.
ESET Smart Security Premium ondersteunt ook het scannen van IMAPS- en POP3S-protocollen, die gebruikmaken
van een gecodeerd kanaal om gegevens uit te wisselen tussen server en client. ESET Smart Security Premium
controleert de communicatie via SSL (Secure Socket Layer) en TLS (Transport Layer Security). Het programma scant
alleen verkeer op poorten die zijn gedefinieerd in Poorten gebruikt door POP3-protocol, ongeacht de versie van het
besturingssysteem.
Versleutelde communicatie wordt standaard gescand. Als u de instellingen van de scanner wilt bekijken, navigeert
u naar SSL/TLS in het gedeelte Geavanceerde instellingen, klikt u op Web en e-mail > SSL/TLS en schakelt u de optie
SSL/TLS-protocolfiltering inschakelen in.
4.2.2.3 Waarschuwingen en meldingen
E-mailbeveiliging biedt controle over e-mailcommunicatie die wordt ontvangen via de protocollen POP3 en IMAP.
Met behulp van de invoegtoepassing voor Microsoft Outlook en andere e-mailclients, biedt ESET Smart Security
Premium controle over alle communicatie via de e-mailclient (POP3, MAPI, IMAP, HTTP). Bij het onderzoeken van
binnenkomende berichten maakt het programma gebruik van alle geavanceerde scanmethoden van de
ThreatSense-scanengine. Dit betekent dat detectie van schadelijke programma's plaatsvindt zelfs nog voordat deze
worden vergeleken met de detectie-engine. Het scannen van communicatie via het POP3- of IMAP-protocol
gebeurt onafhankelijk van de gebruikte e-mailclient.
De opties voor deze functionaliteit zijn beschikbaar in Geavanceerde instellingen onder Web en e-mail >
Beveiliging van e-mailclient > Waarschuwingen en meldingen.
Nadat een e-mail is gecontroleerd, kan een melding met het scanresultaat aan het bericht worden toegevoegd. U
kunt ook kiezen uit Tagmeldingen toevoegen aan ontvangen en gelezen e-mail, Opmerking toevoegen aan het
onderwerp van ontvangen en gelezen geïnfecteerde e-mail of Tagmeldingen toevoegen aan verzonden e-mail. In
zeldzame gevallen kunnen tagberichten in problematische HTML-berichten worden weggelaten. Dit kan ook
gebeuren als berichten worden vervalst door bepaalde malware. De meldingen kunnen aan ontvangen/gelezen e-
mailberichten en/of verzonden e-mailberichten worden toegevoegd. De volgende opties zijn beschikbaar:

62
Nooit: er worden geen berichten toegevoegd.
Alleen naar geïnfecteerde e-mail: alleen berichten met schadelijke software worden als gecontroleerd
gemarkeerd (standaardinstelling).
Naar alle gescande e-mail: er worden meldingen toegevoegd aan alle gescande e-mail.
Opmerking toevoegen aan het onderwerp van verzonden geïnfecteerde e-mail: schakel dit uit als u niet wilt dat er
een viruswaarschuwing aan het onderwerp van geïnfecteerde e-mail wordt toegevoegd. Met deze functie kunt u
geïnfecteerde e-mail eenvoudig filteren op basis van het onderwerp (vooropgesteld dat uw e-mailprogramma
hiervoor ondersteuning biedt). De verhoogt eveneens de geloofwaardigheid voor de ontvanger. Indien een
infiltratie is gedetecteerd wordt waardevolle informatie gegeven over het bedreigingsniveau van een bepaalde e-
mail of afzender.
Sjabloon toegevoegd aan onderwerp geïnfecteerde e-mail - Bewerk deze sjabloon als u de indeling van het
onderwerpsvoorvoegsel van een geïnfecteerde e-mail wilt wijzigen. Met deze functie wordt het onderwerp van het
bericht "Hallo" vervangen door een voorvoegselwaarde "[virus]" in de volgende indeling: "[virus] Hallo". De
variabele %VIRUSNAME% staat voor de gedetecteerde bedreiging.
4.2.2.4 Integratie met e-mailclients
Door integratie van ESET Smart Security Premium met e-mailclients neemt het niveau van actieve beveiliging tegen
schadelijke code in e-mailberichten toe. Als uw e-mailclient wordt ondersteund, kan integratie in ESET Smart
Security Premium worden ingeschakeld. Als integratie is geactiveerd, wordt de ESET Smart Security Premium-
werkbalk aan de e-mailclient toegevoegd zodat e-mailbeveiliging efficiënter is. De instellingen voor integratie zijn
beschikbaar via Instellingen > Geavanceerde instellingen > Web en e-mail > Beveiliging van e-mailclient > E-
mailclients.
De e-mailclients die momenteel worden ondersteund zijn onder andere Microsoft Outlook, Outlook Express,
Windows Mail en Windows Live Mail. Raadpleeg het volgende artikel in de ESET-kennisbank voor een volledige lijst
met ondersteunde e-mailclients en de bijbehorende versies.
Schakel het selectievakje naast Controle bij wijziging inhoud Postvak IN uitschakelen in als het systeem trager
wordt als u met de e-mailclient werkt. Dit kan voorkomen wanneer e-mail wordt opgehaald vanuit het archief van
Kerio Outlook Connector.
Zelfs als integratie niet is ingeschakeld, wordt e-mailcommunicatie beschermd door de module Beveiliging van e-
mailclient (POP3, IMAP).
4.2.2.4.1 Beveiliging van e-mailclient configureren
De module Beveiliging van e-mailclient ondersteunt de volgende e-mailclients: Microsoft Outlook, Outlook
Express, Windows Mail, Windows Live Mail. E-mailbeveiliging werkt als een invoegtoepassing voor deze
programma's. Het belangrijkste voordeel van de invoegtoepassing is dat deze onafhankelijk is van het gebruikte
protocol. Wanneer de e-mailclient een gecodeerd bericht ontvangt, wordt dit gedecodeerd en naar de virusscanner
verstuurd.
4.2.2.5 POP3-, POP3S-filter
Het POP3-protocol is het meestgebruikte protocol voor het ontvangen van e-mailcommunicatie in een e-
mailprogramma. ESET Smart Security Premium biedt beveiliging voor dit protocol, ongeacht de gebruikte e-
mailclient.
De beveiligingsmodule die deze controle verzorgt, wordt automatisch geïnitieerd bij het opstarten van het systeem
en is vervolgens actief in het geheugen. De module werkt alleen goed als deze is ingeschakeld. POP3-
protocolcontrole wordt automatisch uitgevoerd zonder dat de e-mailclient opnieuw hoeft te worden
geconfigureerd. Standaard wordt alle communicatie op poort 110 gescand, maar andere communicatiepoorten
kunnen zo nodig worden toegevoegd. Poortnummers moeten van elkaar worden gescheiden door een komma.
Versleutelde communicatie wordt standaard gescand. Als u de instellingen van de scanner wilt bekijken, navigeert
u naar SSL/TLS in het gedeelte Geavanceerde instellingen, klikt u op Web en e-mail > SSL/TLS en schakelt u de optie
SSL/TLS-protocolfiltering inschakelen in.

63
In dit gedeelte kunt u POP3- en POP3S-protocolcontrole configureren.
E-mailcontrole inschakelen: als deze optie is ingeschakeld, wordt al het verkeer via POP3 gecontroleerd op
schadelijke software.
Poorten gebruikt door POP3-protocol: een lijst met de poorten die worden gebruikt door het protocol POP3
(standaardpoort 110).
ESET Smart Security Premium ondersteunt tevens POP3S-protocolcontrole. Dit type communicatie maakt gebruikt
van een gecodeerd kanaal om gegevens uit te wisselen tussen server en client. ESET Smart Security Premium
controleert de communicatie via coderingsmethoden van SSL (Secure Socket Layer) en TLS (Transport Layer
Security).
Geen POP3S-controle gebruiken: gecodeerde communicatie wordt niet gecontroleerd.
POP3S-protocolcontrole gebruiken voor geselecteerde poorten: selecteer deze optie om POP3S-controle alleen in
te schakelen voor poorten die zijn gedefinieerd bij Poorten gebruikt door POP3S-protocol.
Poorten gebruikt door POP3S-protocol: een lijst met POP3S-poorten die moeten worden gecontroleerd
(standaardpoort 995).
4.2.2.6 Antispambeveiliging
Tegenwoordig behoort ongevraagde e-mail, oftewel spam, tot de grootste problemen bij elektronische
communicatie. Spam vormt tot 80 procent van alle e-mailcommunicatie. Antispambeveiliging dient als bescherming
tegen dit probleem. Door verschillende principes voor e-mailbeveiliging te combineren biedt de antispammodule
superieure filtervoorzieningen om uw Postvak IN schoon te houden.
Eén belangrijk principe bij spamdetectie is het vermogen om ongewenste e-mail te herkennen op basis van vooraf
gedefinieerde vertrouwde adressen (witte lijst) en spamadressen (zwarte lijst). Alle adressen uit uw lijst met
contactpersonen worden automatisch toegevoegd aan de witte lijst, plus alle overige adressen die door u als veilig
zijn gemarkeerd.
De hoofdmethode die wordt gebruikt voor het detecteren van spam is het scannen van eigenschappen van e-
mailberichten. Ontvangen berichten worden gescand op elementaire antispamcriteria (berichtdefinities,

64
statistische heuristiek, herkenningsalgoritmen en andere unieke methoden) en de resulterende indexwaarde
bepaalt of een bericht spam is of niet.
Antispambeveiliging van e-mailclient automatisch starten: als u deze optie inschakelt, wordt antispambeveiliging
automatisch geactiveerd wanneer het systeem wordt opgestart.
Geavanceerde antispamscan toestaan: er worden periodiek aanvullende antispamgegevens gedownload, waarmee
de mogelijkheden voor het bestrijden van spam worden uitgebreid en er betere resultaten worden bereikt.
Met de antispambeveiliging in ESET Smart Security Premium kunt u verschillende parameters instellen om met
mailinglijsten te werken. U beschikt over de volgende opties:
Berichten verwerken
Tekst toevoegen aan e-mailonderwerp: hiermee kunt u een aangepaste tekenreeks als voorvoegsel toevoegen
aan de onderwerpregel van berichten die als spam zijn geclassificeerd. De standaardtekst is '[SPAM]'.
Berichten naar spammap verplaatsen: indien ingeschakeld worden spamberichten verplaatst naar de
standaardmap voor ongewenste e-mail en berichten die opnieuw zijn geclassificeerd als geen spam worden
verplaatst naar het Postvak IN. Als u met de rechtermuisknop op een e-mailbericht klikt en ESET Smart Security
Premium in het contextmenu selecteert, kunt u uit voor de context geschikte opties kiezen.
Gebruik de map: met deze optie zorgt u dat spamberichten naar de opgegeven map worden verplaatst.
Spamberichten markeren als gelezen: schakel dit in om spamberichten automatisch als gelezen te markeren.
Hierdoor kunt u zich beter concentreren op 'schone' berichten.
Opnieuw geclassificeerd bericht markeren als ongelezen: berichten die in eerste instantie als spam zijn
geclassificeerd maar later als 'schoon' zijn gemarkeerd, worden als ongelezen weergegeven.
Logboekregistratie van spamscore De Antispam-engine van ESET Smart Security Premium wijst een
spamscore toe aan elk gescand bericht. Het bericht wordt geregistreerd in het antispamlogboek (ESET Smart
Security Premium > Hulpmiddelen > Logbestanden > Antispambeveiliging).
Geen: de score van antispamscans wordt niet vastgelegd.
Opnieuw geclassificeerd en gemarkeerd als spam: selecteer deze optie als u een spamscore wilt vastleggen
voor berichten die zijn gemarkeerd als SPAM.
Alles: alle berichten worden met een spamscore geregistreerd in het logboek.
OPMERKING
Als u op een bericht in de map met spamberichten klikt, kunt u Geselecteerde berichten herclassificeren als
GEEN spam kiezen. Het bericht wordt dan verplaatst naar het Postvak IN. Als u in uw Postvak IN op een bericht
klikt dat u als spam herkent, kunt u Berichten herclassificeren als spam kiezen. Het bericht wordt dan verplaatst
naar de map met spamberichten. U kunt meerdere berichten selecteren en de actie op alle berichten tegelijk
uitvoeren.
OPMERKING
ESET Smart Security Premium ondersteunt Antispambeveiliging voor Microsoft Outlook, Outlook Express,
Windows Mail en Windows Live Mail.

65
4.2.3 Protocolfiltering
Antivirusbeveiliging voor toepassingsprotocollen wordt geleverd door de ThreatSense-scanengine, die naadloos
alle geavanceerde technieken integreert voor het scannen op malware. Protocolfiltering werkt automatisch,
ongeacht de gebruikte internetbrowser of e-mailclient. Als u gecodeerde (SSL/TLS-) instellingen wilt bewerken,
gaat u naar Web en e-mail > SSL/TLS.
Inhoudsfilter van toepassingsprotocol inschakelen: kan worden gebruikt om protocolfiltering uit te schakelen. Veel
onderdelen van ESET Smart Security Premium (Beveiliging van webtoegang, Beveiliging van e-mailprotocollen,
Antiphishing, Webbeheer) zijn hiervan afhankelijk en zijn zonder dit niet functioneel.
Uitgesloten toepassingen: hiermee kunt u bepaalde toepassingen uitsluiten van protocolfiltering. Dit is handig als
protocolfiltering compatibiliteitsproblemen veroorzaakt.
Uitgesloten IP-adressen: hiermee kunt u bepaalde externe adressen uitsluiten van protocolfiltering. Dit is handig
als protocolfiltering compatibiliteitsproblemen veroorzaakt.
Web- en e-mailclients: wordt alleen gebruikt in Windows XP-besturingssystemen en stelt u in staat toepassingen te
selecteren waarvoor alle verkeer met protocolfiltering wordt gefilterd, ongeacht welke poorten worden gebruikt.
4.2.3.1 Web- en e-mailclients
OPMERKING
Vanaf Windows Vista Service Pack 1 en Windows Server 2008 wordt de nieuwe architectuur WFP (Windows
Filtering Platform) gebruikt om de netwerkcommunicatie te controleren. Aangezien WFP speciale
controletechnieken gebruikt, is de sectie Web- en e-mailclients niet beschikbaar.
Met het oog op de enorme hoeveelheid schadelijke code die op internet circuleert, is veilig surfen een uiterst
belangrijk aspect van computerbeveiliging. Als gevolg van frauduleuze koppelingen en beveiligingsproblemen in
webbrowsers kan schadelijke code ongemerkt het systeem binnendringen. Daarom staat de beveiliging van
webbrowsers in ESET Smart Security Premium centraal. Elke toepassing die toegang tot het netwerk krijgt, kan als
internetbrowser worden gemarkeerd. Het selectievakje heeft twee mogelijke standen:
Uitgeschakeld: communicatie van toepassingen wordt alleen voor de opgegeven poorten gefilterd.
Ingeschakeld: communicatie wordt altijd gefilterd (zelfs als een andere poort is ingesteld).

66
4.2.3.2 Uitgesloten toepassingen
Als u de communicatie van bepaalde toepassingen met toegang tot het netwerk uit wilt sluiten van
inhoudsfiltering, selecteert u deze in de lijst. De HTTP-/POP3/-IMAP-communicatie van de geselecteerde
toepassingen wordt niet op bedreigingen gecontroleerd. Het wordt aanbevolen dat u dit alleen gebruikt voor
toepassingen die niet correct werken wanneer de communicatie ervan wordt gecontroleerd.
Toepassingen en services die worden uitgevoerd, zijn hier automatisch beschikbaar. Klik op Toevoegen om
handmatig een toepassing te selecteren die niet wordt weergegeven in de protocolfilteringlijst.

67
4.2.3.3 Uitgesloten IP-adressen
De vermeldingen in de lijst worden uitgesloten van het protocolinhoudsfilter. De HTTP-/POP3-/IMAP-communicatie
van/naar de geselecteerde adressen wordt niet op bedreigingen gecontroleerd. Wij raden aan dat u deze optie
alleen gebruikt voor adressen die bekend staan als betrouwbaar.
Klik op Toevoegen om een IP-adres/IP-adressenbereik/subnet uit te sluiten van een extern punt dat niet wordt
weergegeven in de protocolfilteringlijst.
Klik op Verwijderen om de geselecteerde vermeldingen uit de lijst te verwijderen.
4.2.3.3.1 IPv4-adres toevoegen
Met deze opties kunt u het IP-adres, IP-adressenbereik of subnet toevoegen van een extern punt waarop een regel
wordt toegepast. Internet Protocol versie 4 is de oudere versie, maar is nog steeds het meest gangbaar.
Eén adres: hiermee kunt u het IP-adres toevoegen van een afzonderlijke computer waarop de regel moet worden
toegepast (bij voorbeeld 192.168.0.10).
Adresbereik: voer het eerste en laatste IP-adres in om op te geven op welk IP-bereik (van meerdere computers) de
regel moet worden toegepast (bijvoorbeeld van 192.168.0.1 tot 192.168.0.99).
Subnet: een subnet (groep van computers) wordt gedefinieerd door een IP-adres en een masker.
255.255.255.0 is bijvoorbeeld het netwerkmasker voor het voorvoegsel 192.168.1.0/24, zodat het adresbereik van
192.168.1.1 tot 192.168.1.254 loopt.
4.2.3.3.2 IPv6-adres toevoegen
Hiermee kunt u het IPv6-adres of subnet toevoegen van een extern punt waarop de regel wordt toegepast. IPv6 is
de nieuwste versie van Internet Protocol, de opvolger van versie 4.
Eén adres: hiermee kunt u het IP-adres toevoegen van een afzonderlijke computer waarop de regel moet worden
toegepast (bij voorbeeld 2001:718:1c01:16:214:22ff:fec9:ca5).
Subnet: een subnet (groep van computers) wordt gedefinieerd door een IP-adres en een masker (bijvoorbeeld:
2002:c0a8:6301:1::1/64).

68
4.2.3.4 SSL/TLS
ESET Smart Security Premium kan bedreigingen controleren in verkeer dat gebruikmaakt van het SSL-protocol. U
kunt verscheidene scanmodi gebruiken om met SSL beveiligde communicatie te controleren met vertrouwde
certificaten, onbekende certificaten of certificaten die zijn uitgesloten van controle van met SSL beveiligde
communicatie.
SSL/TLS-protocolfiltering inschakelen: als protocolfiltering is uitgeschakeld, scant het programma geen
communicatie die via SSL plaatsvindt.
Modus voor SSL/TLS-protocolfiltering is beschikbaar met de volgende opties:
Automatische modus: met de standaardmodus scant u alleen geschikte toepassingen als webbrowsers en e-
mailclients. U kunt dit negeren door toepassingen te selecteren waarvoor de communicaties worden gescand.
Interactieve modus: als u een nieuwe door SSL beveiligde site opgeeft (met een onbekend certificaat), wordt er
een actieselectievenster weergegeven. In deze modus kunt een lijst maken met SSL-certificaten / applicaties
die worden uitgesloten van scannen.
Beleidsmodus: selecteer deze optie om alle met SSL beveiligde communicatie te scannen, behalve
communicatie die wordt beveiligd door certificaten die van scannen zijn uitgesloten. Als nieuwe communicatie
een onbekend, ondertekend certificaat gebruikt, wordt u hierover niet gewaarschuwd en wordt de
communicatie automatisch gefilterd. Als u toegang krijgt tot een server met een niet-vertrouwd certificaat dat
als vertrouwd is gemarkeerd (het staat op de lijst met vertrouwde certificaten), wordt communicatie met de
server toegestaan en de inhoud van het communicatiekanaal wordt gefilterd.
Lijst met door SSL gefilterde toepassingen: hiermee kunt u het gedrag van ESET Smart Security Premium voor
bepaalde toepassingen aanpassen.
Lijst met bekende certificaten: hiermee kunt u het gedrag van ESET Smart Security Premium voor specifieke SSL-
certificaten aanpassen.
Communicatie met vertrouwde domeinen uitsluiten: indien ingeschakeld wordt communicatie met vertrouwde
domeinen uitgesloten van controle. De betrouwbaarheid van domeinen wordt bepaald aan de hand van de
ingebouwde witte lijst.
Gecodeerde communicatie met het verouderde protocol SSL v2 blokkeren: communicatie met de oude versie van
het SSL-protocol wordt automatisch geblokkeerd.
Basiscertificaat
Het basiscertificaat toevoegen aan bekende browsers: om er zeker van te zijn dat SSL-communicatie goed werkt
in uw browsers/e-mailclients, is het noodzakelijk dat u het basiscertificaat voor ESET toevoegt aan de lijst met
bekende basiscertificaten (uitgevers). Indien ingeschakeld, zal ESET Smart Security Premium het basiscertificaat
van ESET automatisch toevoegen aan bekende browsers (bijvoorbeeld Opera en Firefox). Het certificaat wordt
automatisch toegevoegd aan browsers die gebruikmaken van het archief met systeemcertificaten (bijvoorbeeld
in Internet Explorer).
Als u het certificaat wilt toepassen op niet-ondersteunde browsers, klikt u op Certificaat weergeven > Details >
Kopiëren naar bestand... en importeert u het certificaat handmatig in de browser.
Certificaatgeldigheid
Als het certificaat niet kan worden gecontroleerd met het TRCA-certificaatarchief: in sommige gevallen kan het
certificaat niet worden gecontroleerd bij het TRCA-certificaatarchief (Trusted Root Certification Authorities). Dit
betekent dat het certificaat door iemand is ondertekend (bijvoorbeeld de beheerder van een webserver of een
klein bedrijf). Een dergelijk certificaat als vertrouwd beschouwen is niet altijd een risico. De meeste grote
bedrijven (zoals banken) gebruiken een door de TRCA ondertekend certificaat. Als Vragen stellen over
geldigheid certificaat (standaardinstelling) is ingeschakeld, wordt de gebruiker gevraagd een actie te selecteren
wanneer gecodeerde communicatie tot stand wordt gebracht. U kunt Communicatie die gebruikmaakt van het
certificaat blokkeren selecteren om gecodeerde verbindingen naar sites met niet-geverifieerde certificaten
altijd te verbreken.

69
Als het certificaat ongeldig of beschadigd is: dit betekent dat het certificaat is verlopen of op een onjuiste
manier is ondertekend. In dat geval raden we aan dat u Communicatie die gebruikmaakt van het certificaat
blokkeren ingeschakeld laat.
4.2.3.4.1 Certificaten
Om er zeker van te zijn dat SSL-communicatie goed werkt in uw browsers/e-mailclients, is het noodzakelijk dat u
het basiscertificaat voor ESET toevoegt aan de lijst met bekende basiscertificaten (uitgevers). Het basiscertificaat
toevoegen aan bekende browsers moet zijn ingeschakeld. Selecteer deze optie om het basiscertificaat van ESET
automatisch toe te voegen aan de bekende browsers (bijvoorbeeld Opera en Firefox). Het certificaat wordt
automatisch toegevoegd aan browsers die gebruikmaken van het archief met systeemcertificaten (zoals Internet
Explorer). Als u het certificaat wilt toepassen op niet-ondersteunde browsers, klikt u op Certificaat weergeven >
Details > Kopiëren naar bestand... en importeert u het certificaat handmatig in de browser.
In sommige gevallen kan het certificaat niet worden gecontroleerd met het TRCA-certificaatarchief (Trusted Root
Certification Authorities) (zoals VeriSign). Dit betekent dat het certificaat door iemand zelf is ondertekend
(bijvoorbeeld een beheerder van een webserver of een klein bedrijf). Een dergelijk certificaat als vertrouwd
beschouwen is niet altijd een risico. De meeste grote bedrijven (zoals banken) gebruiken een door TRCA
ondertekend certificaat. Als Vragen stellen over geldigheid certificaat (standaardinstelling) is ingeschakeld, wordt
de gebruiker gevraagd een actie te selecteren wanneer gecodeerde communicatie tot stand wordt gebracht. Er
wordt een dialoogvenster voor het selecteren van een actie weergegeven, waarin u het certificaat kunt markeren
als vertrouwd of uitgesloten. Als het certificaat niet in de TRCA-lijst is opgenomen, is het venster rood. Als het
certificaat wel in de TRCA-lijst is opgenomen, is het venster groen.
U kunt Communicatie die gebruikmaakt van het certificaat blokkeren instellen om een gecodeerde verbinding met
de site die het niet-geverifieerde certificaat gebruikt altijd te beëindigen.
Als het certificaat ongeldig of beschadigd is, betekent dit dat het certificaat is verlopen of op een onjuiste manier
zelf is ondertekend. In dat geval reden we aan de communicatie die gebruikmaakt van het certificaat te blokkeren.
4.2.3.4.1.1 Versleuteld netwerkverkeer
Als de computer is geconfigureerd voor het scannen van het SSL-protocol, kan er een dialoogvenster worden
geopend waarin u wordt gevraagd een actie te kiezen wanneer er wordt geprobeerd gecodeerde communicatie
(met een onbekend certificaat) tot stand te brengen.
Het dialoogvenster bevat de volgende gegevens:
naam van de applicatie die de communicatie heeft gestart
naam van het gebruikte certificaat
uit te voeren actie - scannen van de gecodeerde communicatie en bijhouden van de actie voor de applicatie /
het certificaat
Als het certificaat geen deel uitmaakt van het archief Trusted Root Certification Authorities (TRCA), wordt het
certificaat niet vertrouwd.
4.2.3.4.2 Lijst met bekende certificaten
Lijst met bekende certificaten kan worden gebruikt om het gedrag van ESET Smart Security Premium aan te passen
voor specifieke SSL-certificaten, en om gekozen acties te onthouden als Interactieve modus is geselecteerd in
Modus voor SSL/TLS-protocolfiltering. De lijst kan worden bekeken en bewerkt in Geavanceerde instellingen (F5) >
Web en e-mail > SSL/TLS > Lijst met bekende certificaten.
Het venster Lijst met bekende certificaten bestaat uit:
Kolommen
Naam: de naam van het certificaat.
Uitgever van certificaat: de naam van de maker van het certificaat.

70
Certificaatonderwerp: in het onderwerpveld kunt u de entiteit zien die is gekoppeld aan de openbare code die
is opgeslagen in het veld voor het onderwerp van de openbare code.
Toegang: selecteer Toestaan of Blokkeren bij Toegangsactie om communicatie toe te staan/te blokkeren die
door dit certificaat wordt beveiligd, ongeacht de betrouwbaarheid ervan. Selecteer Automatisch om
vertrouwde certificaten toe te staan en te vragen bij niet-vertrouwde certificaten. Selecteer Vragen om de
gebruiker altijd te vragen wat er moet gebeuren.
Scannen: selecteer Scannen of Negeren bij Scanactie om communicatie te scannen of negeren die door dit
certificaat wordt beveiligd. Selecteer Automatisch om te scannen bij automatische modus en te vragen bij
interactieve modus. Selecteer Vragen om de gebruiker altijd te vragen wat er moet gebeuren.
Besturingselementen
Toevoegen: voeg een nieuw certificaat toe en wijzig de instellingen ervan voor toegang en scanopties.
Bewerken: selecteer het certificaat dat u wilt configureren en klik op Bewerken.
Verwijderen selecteer het certificaat dat u wilt verwijderen en klik op Verwijderen.
OK/Annuleren: klik op OK als u wijzigingen wilt opslaan of klik op Annuleren als wilt afsluiten zonder iets op te
slaan.
4.2.3.4.3 Lijst met door SSL/TLS gefilterde toepassingen
Lijst met door SSL/TLS gefilterde toepassingen kan worden gebruikt om het gedrag van ESET Smart Security Premium
aan te passen voor specifieke toepassingen, en om gekozen acties te onthouden als Interactieve modus is
geselecteerd in Modus voor SSL/TLS-protocolfiltering. De lijst kan worden bekeken en bewerkt in Geavanceerde
instellingen (F5) > Web en e-mail > SSL/TLS > Lijst met door SSL/TLS gefilterde toepassingen.
Het venster Lijst met door SSL/TLS gefilterde toepassingen bestaat uit:
Kolommen
Toepassing: de naam van de toepassing.
Scanactie : selecteer Scannen of Negeren om communicatie te scannen of te negeren. Selecteer Automatisch
om te scannen bij automatische modus en te vragen bij interactieve modus. Selecteer Vragen om de gebruiker
altijd te vragen wat er moet gebeuren.
Besturingselementen
Toevoegen: voeg de gefilterde toepassing toe.
Bewerken: selecteer het certificaat dat u wilt configureren en klik op Bewerken.
Verwijderen selecteer het certificaat dat u wilt verwijderen en klik op Verwijderen.
OK/Annuleren: klik op OK als u wijzigingen wilt opslaan of klik op Annuleren als wilt afsluiten zonder iets op te
slaan.
4.2.4 Antiphishing-beveiliging
De term 'phishing' verwijst naar een criminele activiteit die gebruikmaakt van 'social engineering'. Hierbij worden
gebruikers gemanipuleerd met als doel het verkrijgen van vertrouwelijke informatie. Met phishing wordt vaak
geprobeerd toegang te krijgen tot gevoelige gegevens zoals bankrekeningnummers, pincodes, enzovoort. Zie de
woordenlijst voor meer informatie over deze activiteit. ESET Smart Security Premium biedt antiphishing-
beveiliging, die webpagina's blokkeert waarvan bekend is dat deze dergelijke inhoud distribueren.
U wordt aangeraden om antiphishing in te schakelen in ESET Smart Security Premium. Ga naar Geavanceerde
instellingen (F5) en navigeer naar Web en e-mail > Antiphishing-beveiliging.
Ga naar ons artikel in de kennisbank voor meer informatie over Antiphishing-beveiliging in ESET Smart Security
Premium.

71
Een phishing-website openen
Wanneer u een bekende phishingwebsite opent, wordt het volgende dialoogvenster weergegeven in uw
webbrowser. Als u de website desondanks wilt bezoeken, klikt u op Bedreiging negeren (niet aanbevolen).
OPMERKING
Potentiële phishing-websites die op de witte lijst zijn geplaatst, verlopen standaard na enkele uren. Als u een
website permanent wilt toestaan, gebruik dan het hulpprogramma URL-adresbeheer. Vouw in Geavanceerde
instellingen (F5) de opties Web en e-mail > Beveiliging van webtoegang > URL-adresbeheer > Adreslijst uit, klik
op Bewerken en voeg de website die u wilt bewerken aan de lijst toe.
Een phishing-site rapporteren
Met de koppeling Rapporteren kunt u een phishingwebsite/schadelijke website aan ESET rapporteren voor analyse.
OPMERKING
wanneer u een website naar ESET verstuurt, moet deze aan de volgende criteria voldoen:
de website wordt helemaal niet gedetecteerd;
de website is onterecht aangemerkt als bedreiging. In dit geval kunt u Een onjuist geblokkeerde pagina
rapporteren.
U kunt de website ook per e-mail versturen. Stuur uw e-mail naar samples@eset.com. Zorg ervoor dat u een
duidelijk onderwerp gebruikt en dat u zoveel mogelijk informatie over de website opgeeft (bijvoorbeeld via welke
website u naar deze site bent doorverwezen, hoe u van het bestaan van deze website weet, enz.).

72
4.3 Netwerkbeveiliging
De Firewall bestuurt alle netwerkverkeer naar en van het systeem. Dit wordt bereikt door individuele
netwerkverbindingen toe te staan of te weigeren op basis van filterregels. Een persoonlijke firewall biedt
beveiliging tegen aanvallen vanaf externe computers en maakt het blokkeren van bepaalde services mogelijk. Het
biedt tevens antivirusbeveiliging voor HTTP-, POP3- en IMAP-protocollen. Deze functionaliteit vormt een zeer
belangrijk element bij de beveiliging van een computer. ESET Smart Security Premium brengt u op de hoogte
wanneer u verbinding maakt met een onbeveiligd draadloos netwerk of een netwerk met een zwakke beveiliging.
Firewall kan worden geconfigureerd in het deelvenster Instellingen onder Netwerkbeveiliging. Hier kunt u de
filtermodus, regels en gedetailleerde instellingen wijzigen. Uitvoerige instellingen vindt u door te klikken op het
tandrad > Configureren... naast Firewall, of door te drukken op F5 om toegang te krijgen tot Geavanceerde
instellingen.
Klik op het tandrad naast Firewall om toegang te krijgen tot de volgende instellingen:
Configureren...: hiermee opent u het venster Firewall in Geavanceerde instellingen, waar u kunt opgeven hoe
de firewall netwerkcommunicatie afhandelt.
Firewall tijdelijk uitschakelen (alle verkeer toestaan): het tegengestelde van alle netwerkverkeer blokkeren.
Indien deze optie is ingeschakeld, worden allen filteropties van Firewall uitgeschakeld en zijn alle inkomende
en uitgaande verbindingen toegestaan. Klik terwijl Netwerkverkeer filteren zich in deze modus bevindt op
Firewall inschakelen om de firewall opnieuw in te schakelen.
Alle verkeer blokkeren: alle inkomende en uitgaande communicatie wordt door Firewall geblokkeerd. Gebruik
deze optie alleen als u denkt dat er kritieke beveiligingsrisico's zijn waarvoor de verbinding van het systeem
met het netwerk moet worden verbroken. Terwijl het filteren van het netwerkverkeer plaatsvindt in de modus
Alle verkeer blokkeren, klikt u op Blokkeren van alle verkeer stoppen om de normale werking van de firewall te
herstellen.
Automatische modus (als er een andere filtermodus is ingeschakeld): klik om de filtermodus op Automatisch in
te stellen (met door de gebruiker gedefinieerde regels).

73
Interactieve modus (als er een andere filtermodus is ingeschakeld): klik om de filtermodus op Interactief in te
stellen.
Netwerkaanvalbeveiliging (IDS) : analyseert de inhoud van netwerkverkeer en beveiligt en beschermt tegen
netwerkaanvallen. Al het verkeer dat als schadelijk wordt beoordeeld, wordt geblokkeerd.
Botnet-beveiliging: detecteert malware op het systeem snel en nauwkeurig.
Verbonden netwerken: geeft de netwerken weer waarmee netwerkadapters zijn verbonden. Nadat u op de
koppeling onder de netwerknaam hebt geklikt, wordt u gevraagd een beveiligingstype (strict of toegestaan) te
selecteren voor het netwerk waarmee u via uw netwerkadapter bent verbonden. Deze instelling bepaalt hoe
makkelijke andere computers in het netwerk toegang tot uw computer kunnen krijgen.
Zwarte lijst met tijdelijk geblokkeerde IP-adressen: hier kunt u een lijst met IP-adressen weergeven die zijn
gedetecteerd als aanvalsbronnen, die aan de zwarte lijst zijn toegevoegd en waarmee gedurende een bepaalde tijd
geen verbindingen kunnen worden gemaakt. Klik op deze optie en daarna op F1 voor meer informatie.
Wizard Probleemoplossing: hiermee kunt u verbindingsproblemen oplossen die worden veroorzaakt door ESET
Firewall. Zie Wizard Probleemoplossing voor meer informatie.
4.3.1 Firewall
De Firewall bestuurt alle netwerkverkeer naar en van het systeem. Dit wordt bereikt door individuele
netwerkverbindingen toe te staan of te weigeren op basis van gespecificeerde filterregels. Een persoonlijke
firewall biedt beveiliging tegen aanvallen vanaf externe computers en kan bepaalde potentieel gevaarlijke services
blokkeren. Het biedt tevens antivirusbeveiliging voor HTTP-, POP3- en IMAP-protocollen.
Basis
Firewall inschakelen: we adviseren dat u deze functie ingeschakeld laat om de beveiliging van uw systeem te
blijven waarborgen. Als de firewall is ingeschakeld wordt het netwerkverkeer in beide richtingen gescand.
Ook regels van Windows Firewall beoordelen: in automatische modus ook inkomend verkeer toestaan dat door
regels van Windows Firewall wordt toegestaan, tenzij dit verkeer expliciet door ESET-regels wordt geblokkeerd.
Filtermodus: het gedrag van de firewall is afhankelijk van de filtermodus. Filtermodi zijn tevens van invloed op het
niveau van gebruikersinteractie dat is vereist. Er zijn drie filtermodi beschikbaar voor de Firewall van ESET Smart
Security Premium:
Automatische modus: de standaardmodus. Deze modus is geschikt voor gebruikers die de voorkeur geven aan
een eenvoudig en gemakkelijk gebruik van de firewall, zonder de noodzaak om regels te definiëren.
Aangepaste, door de gebruiker gedefinieerde regels, kunnen worden gemaakt maar zijn niet vereist in de
Automatische modus. De Automatische modus staat alle uitgaande verkeer voor het gegeven systeem toe en
blokkeert het meeste inkomende verkeer (met uitzondering van bepaald verkeer van de Vertrouwde zone,
zoals gespecificeerd in IDS en geavanceerde optie/Toegestane services en reageert of recente uitgaande
communicatie).
Interactieve modus: hiermee kunt u een aangepaste configuratie instellen voor uw Firewall. Als communicatie
wordt gedetecteerd waarvoor geen regels zijn gedefinieerd, wordt er een dialoogvenster weergegeven waarin
melding wordt gemaakt van een onbekende verbinding. Het dialoogvenster biedt de gebruiker de mogelijkheid
de communicatie toe te staan of te weigeren, en de hierbij genomen beslissing kan als nieuwe regel voor de
Firewall worden opgeslagen. Als u ervoor kiest een nieuwe regel te maken, worden alle toekomstige
verbindingen van dit type toegestaan of geblokkeerd op basis van deze regel.
Op beleid gebaseerde modus: bij de op beleid gebaseerde modus worden alle verbindingen geblokkeerd die
niet door een specifieke regel zijn toegestaan. In deze modus kunnen gevorderde gebruikers regels definiëren
die alleen gewenste en veilige verbindingen toestaan. Alle andere niet opgegeven verbindingen worden door
de Firewall geblokkeerd.
Leermodus: maakt en bewaart automatisch regels. Deze modus kan het best worden gebruikt bij de eerste
configuratie van de Firewall, maar mag niet langere tijd worden gebruikt. Er is geen interactie van de gebruiker
vereist omdat ESET Smart Security Premium regels opslaat op basis van vooraf gedefinieerde parameters.

74
Gebruik de leermodus alleen tot alle regels voor vereiste communicatie zijn ingesteld om beveiligingsrisico's te
voorkomen.
Profielen kunnen worden gebruikt om het gedrag van de ESET Smart Security Premium Firewall aan te passen door
verschillende regelsets op te geven voor verschillende situaties.
Connected Home Monitor inschakelen: beschermt computers tegen inkomende netwerkbedreigingen.
Melding geven van nieuw ontdekte netwerkapparaten:geeft aan dat er een nieuw apparaat is ontdekt op uw
netwerk.
Geavanceerd
Regels: hier kunt u regels toevoegen en opgeven voor hoe de Firewall omgaat met netwerkverkeer.
Zones: hier kunt u zones maken die bestaan uit een of meer veilige IP-adressen.
OPMERKING
U kunt een IDS-uitzondering toevoegen wanneer een Botnet uw computer aanvalt. Uitzonderingen kunnen
worden aangepast in Geavanceerde instellingen (F5) > Netwerkbeveiliging > Netwerkaanvalbeveiliging > IDS-
uitzonderingen door te klikken op Bewerken.

75
4.3.1.1 Leermodusinstellingen
De leermodus maakt automatisch een regel voor elke communicatie die in het systeem tot stand is gebracht, en
slaat deze op. Er is geen interactie van de gebruiker vereist omdat ESET Smart Security Premium regels opslaat op
basis van vooraf gedefinieerde parameters.
Deze modus kan uw systeem blootstellen aan risico's en wordt alleen aanbevolen voor de initiële configuratie van
de Firewall.
Selecteer Leermodus in het vervolgkeuzemenu in Geavanceerde instellingen (F5) > Firewall > Basis > Filtermodus
om Opties voor leermodus te activeren. Deze sectie bevat de volgende items:
WAARSCHUWING
Als de leermodus actief is, past de Firewall geen filters toe op communicatie in het systeem. Alle uitgaande en
inkomende communicatie is dus toegestaan. Dit betekent dat uw computer in deze modus niet volledig wordt
beschermd door de Firewall.
Communicatietype: selecteer voor elk type communicatie specifieke parameters voor het maken van regels. Er zijn
vier typen communicatie:
Inkomend verkeer vanuit de vertrouwde zone: een voorbeeld van een inkomende verbinding vanuit de
vertrouwde zone is een externe computer in de vertrouwde zone die probeert communicatie tot stand te brengen
met een lokale toepassing die op uw computer wordt uitgevoerd.
Uitgaand verkeer naar de vertrouwde zone: een lokale toepassing die probeert een verbinding tot stand te
brengen met een andere computer in het lokale netwerk, of in een netwerk in de vertrouwde zone.
Inkomend internetverkeer: een externe computer die probeert te communiceren met een toepassing die op de
computer wordt uitgevoerd.
Uitgaand internetverkeer: een lokale toepassing die probeert een verbinding tot stand te brengen met een
andere computer.
In elke sectie kunt u parameters definiëren die u aan nieuwe regels kunt toevoegen:
Lokale poort toevoegen: hiermee kunt u het nummer van de lokale poort voor netwerkcommunicatie toevoegen. In
het geval van uitgaande communicatie worden er meestal willekeurige nummers gegenereerd. Om die reden is het
raadzaam deze optie alleen in te schakelen voor inkomende communicatie.
Toepassing toevoegen: hiermee kunt u de naam van de lokale toepassing toevoegen. Deze optie is geschikt voor
toekomstige regels op toepassingsniveau (regels die de communicatie voor een volledige toepassing bepalen). U
kunt zo bijvoorbeeld alleen communicatie voor een webbrowser of e-mailclient inschakelen.
Externe poort toevoegen: hiermee kunt u het nummer van de externe poort voor netwerkcommunicatie
toevoegen. U kunt zo een bepaalde service die is gekoppeld aan een standaardpoortnummer (HTTP - 80, POP3 - 110,
etc.) toestaan of weigeren.
Extern IP-adres/vertrouwde zone toevoegen: u kunt voor nieuwe regels een extern IP-adres of een zone gebruiken
als parameter om alle netwerkverbindingen tussen het lokale systeem en dat externe adres of die zone aan te
geven. Deze optie is geschikt als u acties wilt definiëren voor een bepaalde computer of een groep
netwerkcomputers.
Maximum aantal verschillende regels voor een toepassing: als een toepassing communiceert via verschillende
poorten, naar verschillende IP-adressen, etc., maakt de firewall in de leermodus het juiste aantal regels voor deze
toepassing. Gebruik deze optie om het aantal regels te beperken dat voor een toepassing kan worden gemaakt.

76
4.3.1.2 Netwerkaanvalbeveiliging
Netwerkaanvalbeveiliging (IDS) inschakelen : analyseert de inhoud van netwerkverkeer en beveiligt en
beschermt tegen netwerkaanvallen. Al het verkeer dat als schadelijk wordt beoordeeld, wordt geblokkeerd.
Botnet-beveiliging inschakelen: detecteert en blokkeert communicatie met schadelijke opdrachten en
controleservers door patronen te herkennen die aangeven dat een computer is geïnfecteerd en dat een bot
probeert te communiceren.
IDS-uitzonderingen: hier kunt u IDS-uitzonderingen toevoegen en reacties op schadelijke activiteiten aanpassen.
4.3.2 Firewallprofielen
Profielen kunnen worden gebruikt om het gedrag van de ESET Smart Security Premium Firewall te besturen. Bij het
maken of bewerken van een regel voor de Firewall kunt u de regel toewijzen aan een bepaald profiel of voor elk
profiel laten gelden. Wanneer een profiel actief is op een netwerkinterface, worden alleen de algemene regels
(zonder opgegeven profiel) toegepast, samen met de regels die aan dat profiel zijn toegewezen. U kunt meerdere
profielen maken met verschillende regels die aan netwerkadapters of netwerken worden toegewezen om snel het
gedrag van de Firewall te wijzigen.
Klik op Bewerken naast Lijst met profielen om het venster Firewallprofielen te openen waarin u profielen kunt
bewerken.
Een netwerkadapter kan worden ingesteld om een profiel te gebruiken dat voor een specifiek netwerk is
geconfigureerd wanneer de adapter met dat netwerk is verbonden. U kunt ook een specifiek profiel toewijzen dat
in een bepaald netwerk moet worden gebruikt. Dit kan in Geavanceerde instellingen (F5) > Netwerkbeveiliging >
Firewall > Bekende netwerken. Selecteer een netwerk in de lijst met bekende netwerken en klik op Bewerken om
een firewallprofiel toe te wijzen aan het specifieke netwerk in het vervolgkeuzemenu Firewallprofiel. Als dat
netwerk geen toegewezen profiel heeft, wordt het standaardprofiel van de adapter gebruikt. Als de adapter is
ingesteld om het netwerkprofiel niet te gebruiken, wordt het standaardprofiel ervan gebruikt, ongeacht met welk
netwerk verbinding wordt gemaakt. Als er geen profiel voor het netwerk of voor de adapterconfiguratie is, wordt
het algemene standaardprofiel gebruikt. Als u een profiel aan een netwerkadapter wilt toevoegen, selecteert u de
netwerkadapter, klikt u op Bewerken naast Profielen die zijn toegewezen aan netwerkadapters, bewerkt u de
geselecteerde netwerkadapter en selecteert u het profiel in het vervolgkeuzemenu Standaardfirewallprofiel.
Als de Firewall naar een ander profiel overschakelt, wordt er rechtsonder in het systeemvak een melding
weergegeven.
4.3.2.1 Profielen die zijn toegewezen aan netwerkadapters
Door van profiel te wisselen kunt u snel meerdere wijzigingen tegelijk in het gedrag van de firewall doorvoeren.
Aangepaste regels kunnen worden ingesteld en toegepast op bepaalde profielen. Netwerkadaptervermeldingen
voor alle adapters die aanwezig zijn op de computer worden automatisch aan de lijst met netwerkadapters
toegevoegd.
Kolommen
Naam: de naam van de netwerkadapter.
Standaardfirewallprofiel: het standaardprofiel wordt gebruikt als het netwerk waarmee u bent verbonden geen
geconfigureerd profiel heeft, of als uw netwerkadapter niet is ingesteld om een netwerkprofiel te gebruiken.
Voorkeur voor netwerkprofiel: als Voorkeur voor firewallprofiel van verbonden netwerk is ingeschakeld, gebruikt
de netwerkadapter indien mogelijk het firewallprofiel dat is toegewezen aan een verbonden netwerk.
Besturingselementen
Toevoegen: hiermee voegt u een nieuwe netwerkadapter toe.
Bewerken: hiermee kunt u een bestaande netwerkadapter bewerken.

77
Verwijderen: selecteer een netwerkadapter en klik opVerwijderen als u een netwerkadapter in de lijst wilt
verwijderen.
OK/Annuleren: klik op OK als u wijzigingen wilt opslaan of op Annuleren als u wilt afsluiten zonder iets op te
slaan.
4.3.3 Regels configureren en gebruiken
Regels vertegenwoordigen een reeks condities die worden gebruikt om op zinvolle wijze alle netwerkverbindingen
en alle acties die zijn toegewezen aan deze condities te testen. Met regels voor Firewall kunt u de actie definiëren
die moet worden genomen wanneer verschillende soorten netwerkverbindingen tot stand worden gebracht. U
krijgt toegang tot de instellingen voor het filteren met regels door te gaan naar Geavanceerde instellingen (F5) >
Firewall > Basis. Enkele van de vooraf gedefinieerde regels zijn gebonden aan de selectievakjes van toegestane
services (IDS en geavanceerde opties) en deze kunnen niet rechtstreeks worden uitgeschakeld. In plaats daarvan
kunt u hiervoor de overeenkomstige selectievakjes gebruiken.
In tegenstelling tot de vorige versie van ESET Smart Security Premium worden regels van boven naar beneden
beoordeeld. De actie van de eerste overeenkomende regel wordt gebruikt voor elke netwerkverbinding die wordt
beoordeeld. Dit is een belangrijke gedragswijziging ten opzichte van de vorige versie, waarin de prioriteit van de
regels automatisch plaatsvond en specifiekere regels een hogere prioriteit hadden dan algemenere regels.
Verbindingen kunnen worden onderverdeeld in inkomende en uitgaande verbindingen. Inkomende verbindingen
worden geïnitieerd door een externe computer die een verbinding probeert te maken met het lokale systeem.
Uitgaande verbindingen werken andersom. Het lokale systeem maakt contact met een externe computer.
Als een nieuwe, onbekende verbinding wordt gedetecteerd, moet u zorgvuldig overwegen of u deze wilt toestaan
of weigeren. Ongevraagde, onbeveiligde of onbekende verbindingen vormen een beveiligingsrisico voor het
systeem. Als een dergelijke verbinding tot stand wordt gebracht, wordt aanbevolen speciale aandacht te besteden
aan de externe computer en de toepassing die probeert verbinding te maken met uw computer. Veel infiltraties
proberen privégegevens te verzamelen en te verzenden of andere schadelijke toepassingen te downloaden naar de
hostwerkstations. De Firewall stelt u in staat dergelijke verbindingen te detecteren en te beëindigen.

78
4.3.3.1 Firewallregels
Klik op Bewerken naast Regels op het tabblad Basis om het venster Firewallregels weer te geven, waar de lijst met
alle regels wordt weergegeven. Met Toevoegen, Bewerken en Verwijderen kunt u regels toevoegen, configureren
en verwijderen. U kunt het prioriteitsniveau van een regel wijzigen door een of meer regels te selecteren en te
klikken op Boven/Omhoog/Omlaag/Beneden.
TIP: U kunt het veld Zoeken gebruiken om een of meer regels te vinden op naam, protocol of poort.
Kolommen
Naam: naam van de regel.
Ingeschakeld: geeft aan of regels zijn ingeschakeld of uitgeschakeld. Het bijbehorende selectievakje moet
worden ingeschakeld om een regel te activeren.
Protocol: het protocol waarvoor deze regel geldig is.
Profiel: geeft het firewallprofiel aan waarvoor deze regel geldig is.
Actie: geeft de communicatiestatus aan (blokkeren/toestaan/vragen).
Richting: de richting van de communicatie (inkomend/uitgaand/beide).
Lokaal: IP-adres en poort van lokale computer.
Extern: IP-adres en poort van externe computer.
Toepassingen: de toepassing waarvoor de regel geldt.
Besturingselementen
Toevoegen: hiermee kunt u een nieuwe regel maken.
Bewerken: hiermee kunt u bestaande regels bewerken.
Wissen: hiermee kunt u bestaande regels verwijderen.
Ingebouwde (vooraf gedefinieerde) regels weergeven: door ESET Smart Security Premium vooraf gedefinieerde
regels die specifieke communicatie toestaan of weigeren. U kunt deze regels uitschakelen, maar u kunt een
vooraf gedefinieerde regel niet verwijderen.

79
Boven/Omhoog/Omlaag/Beneden: hiermee kunt u het prioriteitniveau van regels aanpassen (regels worden
uitgevoerd van boven naar beneden).
4.3.3.2 Werken met regels
Wijziging is vereist telkens wanneer bewaakte parameters worden aangepast. Als er wijzigingen worden
aangebracht die tot gevolg hebben dat een regel niet meer aan de voorwaarden kan voldoen en de opgegeven actie
niet kan worden toegepast, kan de desbetreffende verbinding worden geweigerd. Dit kan tot problemen leiden
met de werking van de toepassing waarop een regel van toepassing is. Een voorbeeld is een verandering van
netwerkadres of poortnummer voor de externe zijde.
Het bovenste deel van het venster bevat drie tabbladen:
Algemeen: hier kunt u een regelnaam opgeven, de richting van de verbinding, de actie (Toestaan, Weigeren,
Vragen), het protocol en het profiel waarin de regel wordt toegepast.
Lokaal: hier wordt informatie weergegeven over de lokale zijde van de verbinding, waaronder het nummer
van de lokale poort of het poortbereik en de naam van de communicerende toepassing. Ook kunt u een vooraf
gedefinieerde of gemaakte zone toevoegen met een IP-adressenbereik door te klikken op Toevoegen.
Extern: op dit tabblad staat informatie over de externe poort (poortbereik). Daarnaast kunt u hier een lijst met
externe IP-adressen of zones definiëren voor een bepaalde regel. Ook kunt u een vooraf gedefinieerde of
gemaakte zone toevoegen met een IP-adressenbereik door te klikken op Toevoegen.
Wanneer u een nieuwe regel maakt, moet u een naam voor de regel invoeren in het veld Naam. Selecteer de
richting waarin de regel van toepassing is in het vervolgkeuzemenu Richting en de actie in het vervolgkeuzemenu
Actie die moet worden uitgevoerd wanneer een communicatie aan de regel voldoet.
Protocol: het overdrachtprotocol dat voor de regel wordt gebruikt. Selecteer welk protocol u voor een gegeven
regel wilt gebruiken in het vervolgkeuzemenu.
ICMP-type/code vertegenwoordigt een ICMP-bericht dat wordt aangeduid met een getal (bijvoorbeeld 0
vertegenwoordigt "echoreactie").
Alle regels zijn standaard ingeschakeld voor Elk profiel. U kunt ook een aangepast firewallprofiel selecteren in het
vervolgkeuzemenu Profiel.
Als u Logbestand inschakelt, wordt de activiteit van de regel vastgelegd in een logbestand. Met Gebruiker
informeren wordt een bericht weergegeven wanneer de regel wordt toegepast.
OPMERKING
Hieronder staat een voorbeeld waarin we een nieuwe regel maken die het de webbrowser toestaat toegang tot
het netwerk te krijgen. Het volgende moet zijn geconfigureerd:
Op het tabblad Algemeen kunt u uitgaande communicatie via het TCP- en UDP-protocol inschakelen.
Voeg uw browsertoepassing toe (voor Internet Explorer is dit iexplore.exe) aan het tabblad Lokaal.
Op het tabblad Extern moet u poortnummer 80 alleen inschakelen als u surfen op internet standaard wilt
toestaan.
OPMERKING
Vooraf gedefinieerde regels kunnen in beperkte mate worden aangepast.

80
4.3.4 Zones configureren
Een zone geeft een verzameling netwerkadressen aan die één logische groep IP-adressen vormt. Dit is handig
wanneer u dezelfde set adressen in meerdere regels wilt gebruiken. Aan elk adres in de desbetreffende groep
worden regels toegewezen die centraal zijn gedefinieerd voor de hele groep. Een voorbeeld van een dergelijke
groep is de Vertrouwde zone. Een vertrouwde zone vertegenwoordigt een groep netwerkadressen die niet op
enigerlei wijze worden geblokkeerd door de Firewall. Deze zones kunnen worden geconfigureerd in Geavanceerde
instellingen > Firewall > Geavanceerd, door op Bewerken te klikken naast Zones. Als u een nieuwe zone wilt
toevoegen, klikt u op Toevoegen, geeft u een Naam en een Beschrijving voor de zone op en voegt u een extern IP-
adres toe aan het veld Adres van externe computer (IPv4, IPv6, bereik, masker).
In het venster met instellingen voor Firewallzones kunt u een zonenaam, beschrijving en netwerkadreslijst
opgeven (zie ook Editor voor bekende netwerken).
4.3.5 Bekende netwerken
Als u een computer gebruikt die regelmatig verbinding maakt met openbare netwerken buiten uw reguliere thuis-
of kantoornetwerk, raden we aan dat u de netwerkgeloofwaardigheid van nieuwe netwerken controleert waarmee
u verbinding maakt. Nadat netwerken zijn gedefinieerd, kan ESET Smart Security Premium vertrouwde netwerken
(thuis of kantoor) herkennen aan de hand van diverse netwerkparameters die zijn geconfigureerd in
Netwerkidentificatie. Computers maken vaak verbinding met netwerken via IP-adressen die lijken op die van het
vertrouwde netwerk. In dergelijke gevallen kan ESET Smart Security Premium een onbekend netwerk als vertrouwd
(thuis- of kantoornetwerk) beschouwen. We raden aan dat u Netwerkverificatie gebruikt om dit soort situaties te
voorkomen.
Wanneer een netwerkadapter wordt verbonden met een netwerk of de netwerkinstellingen ervan opnieuw
worden geconfigureerd, zoekt ESET Smart Security Premium in de lijst met bekende netwerken naar een
vermelding die overeenkomst met het nieuwe netwerk. Als Netwerkidentificatie en Netwerkverificatie (optioneel)
overeenkomen, wordt het netwerk gemarkeerd als verbonden in deze interface. Als er geen bekend netwerk wordt
gevonden zal de configuratie netwerkidentificatie een nieuwe netwerkverbinding tot stand brengen om het
netwerk te identificeren telkens wanneer u er de volgende keren een verbinding mee tot stand brengt. Standaard
maakt de nieuwe netwerkverbinding gebruik van het beveiligingstype Publiek netwerk. In het dialoogvenster
Nieuwe netwerkverbinding gedetecteerd wordt u gevraagd te kiezen tussen het beveiligingstype Publiek netwerk,
Thuis- of kantoornetwerk of Gebruik de Windowsinstelling. Als een netwerkadapter wordt verbonden met een
bekend netwerk en dat netwerk is gemarkeerd als Thuis- of kantoornetwerk, zullen de lokale subnetten van de
adapter worden toegevoegd aan de Vertrouwde zone.
Beveiligingstype van nieuwe netwerken: kies een van de onderstaande opties: Gebruik Windowsinstelling, Vraag
de gebruiker of Markeer als Openbaar standaard moet worden gebruikt voor nieuwe netwerken.
Met Bekende netwerken kunt u onder andere de netwerknaam, netwerkidentificatie en het beveiligingstype
configureren. Klik op Bewerken om naar de Editor voor bekende netwerken te gaan.
OPMERKING
Wanner u kiest voor Gebruik Windowsinstelling verschijnt een dialoogvenster en wordt het netwerk waarmee u
een verbinding maakt automatisch gemarkeerd met uw Windowsinstellingen. Dit heeft voor gevolg dat
bepaalde functies (zoals bestandsdeling en extern bureaublad) toegankelijk zijn via de nieuwe netwerken.

81
4.3.5.1 Editor voor bekende netwerken
Bekende netwerken kunnen handmatig worden geconfigureerd in Geavanceerde instellingen > Netwerkbeveiliging
> Firewall > Bekende netwerken door te klikken op Bewerken.
Kolommen
Naam: naam van bekend netwerk.
Beveiligingstype: geeft aan of het netwerk is ingesteld op Thuis- of kantoornetwerk, Openbaar netwerk of de
instelling Gebruik Windows.
Firewallprofiel: selecteer een profiel in het vervolgkeuzemenu Regels weergeven die in het profiel zijn gebruikt
om het regelfilter van het profiel weer te geven.
Updateprofiel: hiermee kunt u een gemaakt updateprofiel toepassen wanneer u bent verbonden met dit
netwerk..
Besturingselementen
Toevoegen: hiermee maakt u een nieuw bekend netwerk.
Bewerken: klik hierop om een bestaand bekend netwerk te bewerken.
Verwijderen: selecteer een netwerk en klik op Verwijderen om het netwerk te verwijderen uit de lijst met
bekende netwerken.
Boven/Omhoog/Omlaag/Beneden : hiermee kunt u de prioriteit van bekende netwerken aanpassen (netwerken
worden beoordeeld van boven naar beneden).
Netwerkconfiguratie-instellingen zijn verdeeld over de volgende tabbladen:
Netwerk
Hier kunt u de Netwerknaam definiëren en het Beveiligingstype vastleggen (openbaar netwerk, thuis- of
kantoornetwerk of instelling Gebruik Windows) voor het netwerk. Gebruik het vervolgkeuzemenu Firewallprofiel
om het profiel voor dit netwerk te selecteren. Als het netwerk het beveiligingstype Thuis- of kantoonetwerk
gebruikt, worden alle rechtstreeks verbonden netwerksubnetten als vertrouwd beschouwd. Een voorbeeld: als een
netwerkadapter wordt verbonden met dit netwerk met het IP-adres 192.168.1.5 en het subnetmasker 255.255.255.0,
wordt het subnet 192.168.1.0/24 toegevoegd aan de vertrouwde zone van die adapter. Als de adapter meerdere
adressen/subnetten heeft, worden ze allemaal vertrouwd, ongeacht de configuratie van Netwerkidentificatie van
het bekende netwerk.
Verder worden adressen die worden toegevoegd onder Aanvullende vertrouwde adressen altijd toegevoegd aan
de vertrouwde zone van adapters die met dit netwerk zijn verbonden (ongeacht het beveiligingstype van het
netwerk).
Waarschuwen bij zwakke Wi-Fi-versleuteling: ESET Smart Security Premium brengt u op de hoogte wanneer u
verbinding maakt met een onbeveiligd draadloos netwerk of een netwerk met een zwakke beveiliging.
Firewallprofiel: selecteer het firewallprofiel dat wordt gebruikt wanneer met dit netwerk verbinding wordt
gemaakt.
Updateprofiel: selecteer het updateprofiel dat wordt gebruikt wanneer met dit netwerk verbinding wordt gemaakt.
Aan de volgende voorwaarden moet worden voldaan om een netwerk als verbonden te kunnen markeren in de lijst
met verbonden netwerken:
Netwerkidentificatie: alle ingevulde parameters moeten overeenkomen met actieve verbindingsparameters.
Netwerkverificatie: als de verificatieserver is geselecteerd, moet succesvolle verificatie bij de ESET-
verificatieserver plaatsvinden.

82
Netwerkbeperkingen (alleen Windows XP): aan alle geselecteerde globale beperkingen moet worden
voldaan.
Netwerkidentificatie
Netwerkidentificatie vindt plaats op basis van de parameters van de lokale netwerkadapter. Alle geselecteerde
parameters worden vergeleken met de feitelijke parameters van actieve netwerkverbindingen. IPv4- en IPv6-
adressen zijn toegestaan.
Netwerkverificatie
Netwerkverificatie zoekt naar een specifieke server in het netwerk en gebruikt asymmetrische codering (RSA) voor
verificatie van die server. De naam van het netwerk dat wordt geverifieerd, moet overeenkomen met de zonenaam
die is ingesteld in de instellingen van de verificatieserver. De naam is hoofdlettergevoelig. Geef een servernaam
op, de luisterpoort van de server en een openbare code die overeenkomt met de persoonlijke code op de server
(zie Netwerkverificatie - Serverconfiguratie). De servernaam kan worden opgegeven in de vorm van een IP-adres,
DNS- of NetBIOS-naam en kan worden gevolgd door een pad naar de locatie van de code op de server (bijvoorbeeld
servernaam_/map1/map2/verificatie). U kunt alternatieve servers opgeven door deze aan het pad toe te voegen,
gescheiden door puntkomma's.
ESET Authentication Server downloaden.
De openbare code kan worden geïmporteerd met een van de volgende bestandstypen:
PEM-gecodeerde openbare code (.pem): deze code kan worden gegenereerd met de ESET-verificatieserver
(zie Netwerkverificatie - Serverconfiguratie).
Gecodeerde openbare code
Certificaat met openbare code (.crt)

83
Klik op Testen om uw instellingen te testen. Als de verificatie is geslaagd, wordt Serververif icatie geslaagd
weergegeven. Als de verificatie niet correct is geconfigureerd, verschijnt een van de volgende foutberichten:
Serververif icatie is mislukt. Ongeldige of niet-overeenkomende handtekening.
De serverhandtekening komt niet overeen met de opgegeven openbare code.
Serververif icatie is mislukt. Netwerknaam komt niet overeen.
De naam van het geconfigureerde netwerk komt niet overeen met de zone van de verificatieserver. Controleer
beide namen en zorg dat ze hetzelfde zijn.
Serververif icatie is mislukt. Ongeldige of geen reactie van server.
Er wordt geen reactie ontvangen als de server niet actief is of ontoegankelijk is. Er kan een ongeldige reactie
worden ontvangen als een andere HTTP-server op het opgegeven adres actief is.
Ongeldige openbare sleutel opgegeven.
Controleer of het openbare-sleutelbestand dat u hebt opgegeven niet beschadigd is.
Netwerkbeperkingen (alleen voor Windows XP)
Bij moderne besturingssystemen (Windows Vista en nieuwer) heeft elke netwerkadapter zijn eigen vertrouwde
zone en actieve firewallprofiel. Helaas wordt deze benadering niet ondersteund door Windows XP. Alle
netwerkadapters delen bij deze besturingssystemen altijd dezelfde vertrouwde zone en hetzelfde actieve
firewallprofiel. Dit kan een potentieel veiligheidsrisico inhouden als de machine tegelijk met meerdere netwerken
is verbonden. In dergelijke gevallen kan verkeer van een niet-vertrouwd netwerk worden beoordeeld met behulp
van de vertrouwde zone die en het firewallprofiel dat zijn geconfigureerd voor het andere verbonden netwerk. Om
het beveiligingsrisico te verkleinen kunt u de volgende beperkingen gebruiken om te voorkomen dat er één
netwerkconfiguratie wordt toegepast terwijl er een ander (potentieel niet-vertrouwd) netwerk is verbonden.
Bij Windows XP worden instellingen van verbonden netwerken (vertrouwde zone en firewallprofiel) globaal
toegepast, tenzij tenminste een van deze beperkingen is ingeschakeld en er niet aan wordt voldaan:
a. Er is slechts één verbinding actief
b. Geen draadloze verbinding tot stand gebracht
c. Geen onbeveiligde draadloze verbinding tot stand gebracht

84
4.3.5.2 Netwerkverificatie - Serverconfiguratie
Het verificatieproces kan worden uitgevoerd door elke op het netwerk aangesloten computer/server die moet
worden geverifieerd. De toepassing ESET-verificatieserver moet worden geïnstalleerd op een computer/server die
altijd beschikbaar is voor verificatie wanneer een client probeert verbinding te maken met het netwerk. Het
installatiebestand voor de toepassing ESET Authentication Server kan worden gedownload op de website van ESET.
Nadat u de toepassing ESET Authentication Server hebt geïnstalleerd, wordt een dialoogvenster weergegeven (u
kunt de toepassing bereiken via Start > Alle programma's > ESET > ESET Authentication Server).
Om de verificatieserver te configureren, geeft u de naam op van de verificatiezone en de serverpoort voor luisteren
(standaard is dat 80), evenals de locatie waar de openbare en persoonlijke code moeten worden opgeslagen.
Genereer vervolgens de openbare en persoonlijke code die worden gebruikt bij het verificatieproces. De
persoonlijke code blijft op de server staan; de openbare code moet worden geïmporteerd aan de clientzijde in het
gedeelte Verificatie zone wanneer een zone in de firewall-instellingen wordt ingesteld.
Zie het volgende artikel in de ESET-kennisbank voor meer informatie.
4.3.6 Logboekregistratie
De ESET Smart Security Premium Firewall slaat belangrijke gebeurtenissen op in een logbestand, dat rechtstreeks
vanuit het hoofdmenu kan worden bekeken. Klik op Hulpmiddelen > Meer hulpmiddelen > Logbestanden en
selecteer vervolgens Firewall in het vervolgkeuzemenu Logbestand.
De logbestanden kunnen worden gebruikt om fouten te detecteren en indringers in uw systeem op te sporen. De
logboeken van ESET Firewall bevatten de volgende gegevens:
Datum en tijdstip van de gebeurtenis
Naam van de gebeurtenis
Bron
Doelnetwerkadres
Netwerkcommunicatieprotocol
Toegepaste regel, of naam van worm, indien geïdentificeerd
Betrokken toepassing
Gebruiker
Een grondige analyse van deze gegevens kan helpen bij het detecteren van pogingen om de systeembeveiliging in
gevaar te brengen. Vele andere factoren duiden op potentiële beveiligingsrisico's en bieden u de mogelijkheid hun
impact tot een minimum te beperken: frequente verbindingen vanaf onbekende locaties, meerdere pogingen om
verbindingen tot stand te brengen, communicatie via onbekende toepassingen of gebruik van ongebruikelijke
poortnummers.
4.3.7 Verbinding tot stand brengen - detectie
De Firewall detecteert elke nieuw tot stand gebrachte netwerkverbinding. De actieve firewallmodus bepaalt welke
acties worden uitgevoerd voor de nieuwe regel. Als Automatische modus of Op beleid gebaseerde modus is
geactiveerd, voert de Firewall vooraf gedefinieerde acties zonder gebruikersinteractie uit.
In de interactieve modus wordt er een informatievenster weergegeven waarin de detectie van een nieuwe
netwerkverbinding wordt gemeld en gedetailleerde informatie wordt verstrekt over de verbinding. U kunt ervoor
kiezen om de verbinding toe te staan of deze te weigeren (blokkeren). Als u dezelfde verbinding herhaaldelijk
toestaat in het dialoogvenster, adviseren wij een nieuwe regel te maken voor deze verbinding. Dit kunt u doen
door Regel maken en permanent onthouden te selecteren en de actie als nieuwe regel voor Firewall op te slaan. Als
de firewall dezelfde verbinding herkent in de toekomst, wordt de bestaande regel toegepast zonder dat de
gebruiker daar iets voor hoeft te doen.

85
Wees voorzichtig bij het maken van nieuwe regels en sta alleen verbindingen toe die veilig zijn. Als alle
verbindingen worden toegestaan, kan de Firewall zijn taak niet uitvoeren. Hieronder volgen de belangrijke
parameters voor verbindingen:
Externe zijde: hiermee worden alleen verbindingen met vertrouwde en bekende adressen toegestaan.
Lokale toepassing: het is niet raadzaam verbindingen toe te staan voor onbekende toepassingen en processen.
Poortnummer: communicatie op veelgebruikte poorten (bijvoorbeeld web - poortnummer 80) kan in normale
omstandigheden worden toegestaan.
Computerinfiltraties proberen zich vaak te verspreiden door gebruik te maken van internet- en verborgen
verbindingen als hulpmiddel voor het infecteren van externe systemen. Als regels op de juiste manier worden
geconfigureerd, wordt een Firewall een nuttig beveiligingsmiddel tegen diverse aanvallen via schadelijke code.
4.3.8 Problemen oplossen met ESET Persoonlijke firewall
Als u connectiviteitsproblemen hebt met ESET Smart Security Premium, zijn er verschillende manieren om na te
gaan of ESET Firewall het probleem veroorzaakt. Verder kunt u met Firewall nieuwe regels of uitzonderingen maken
om connectiviteitsproblemen op te lossen.
Zie de volgende onderwerpen om problemen met ESET Firewall op te lossen:
Wizard Probleemoplossing
Regels of uitzonderingen registreren en maken van logbestand
Uitzonderingen maken vanuit meldingen van Firewall
Geavanceerde PCAP-logboekregistratie
Problemen oplossen met protocolfiltering
4.3.8.1 Wizard Probleemoplossing
De wizard Probleemoplossing controleert alle geblokkeerde verbindingen en begeleidt u bij het
probleemoplossingsproces om problemen met de firewall en specifieke toepassingen of apparaten op te lossen.
Vervolgens stelt de wizard een nieuwe set regels voor die kunnen worden toegepast als u die goedkeurt. De wizard
Probleemoplossing vindt u in het hoofdmenu onder Instellingen > Netwerkbeveiliging.
4.3.8.2 Regels of uitzonderingen registreren en maken van logbestand
Standaard registreert ESET Firewall niet alle geblokkeerde verbindingen. Als u wilt weten wat wordt geblokkeerd
door de Firewall, schakelt u de logboekregistratie in bij Geavanceerde instellingen onder Hulpmiddelen >
Diagnostische gegevens > Geavanceerde logboekregistratie inschakelen voor Firewall. Als u iets in het logbestand
ziet waarvan u niet wilt dat Firewall dit blokkeert, kunt u er een regel of IDS-uitzondering voor maken door er met
de rechtermuisknop op te klikken en Soortgelijke gebeurtenissen in de toekomst niet meer blokkeren te
selecteren. Het logbestand met alle geblokkeerde verbindingen kan uit wel duizenden vermeldingen bestaan en
het kan lastig zijn een bepaalde verbinding in dit logbestand te vinden. U kunt logboekregistratie uitschakelen
nadat u het probleem hebt opgelost.
Zie Logbestanden voor meer informatie over logbestanden.
OPMERKING
Gebruik logboekregistratie om de volgorde te zien waarin Firewall bepaalde verbindingen blokkeert. Verder
kunt u op basis van het logbestand regels maken die precies doen wat u wilt.

86
4.3.8.2.1 Regel maken van logbestand
In de nieuwe versie van ESET Smart Security Premium kunt u een regels vanuit het logbestand maken. Klik in het
hoofdmenu op Hulpmiddelen > Meer hulpmiddelen > Logbestanden. Kies Firewall in het vervolgkeuzemenu, klik
met de rechtermuisknop op de gewenste vermelding in het logbestand en selecteer Soortgelijke gebeurtenissen in
de toekomst niet meer blokkeren in het contextmenu. Er wordt een meldingvenster met de nieuwe regel
weergegeven.
Om het maken van nieuwe regels vanuit het logbestand mogelijk te maken, moet ESET Smart Security Premium met
de volgende instellingen worden geconfigureerd:
stel het minimale detailniveau voor logboekregistratie in op Diagnostiek in Geavanceerde instellingen (F5) >
Hulpmiddelen > Logbestanden,
schakel Ook meldingen weergeven bij inkomende aanvallen tegen beveiligingslekken in in Geavanceerde
instellingen (F5) > Firewall > IDS en geavanceerde opties > Indringingsdetectie.
4.3.8.3 Uitzonderingen maken van meldingen van Persoonlijke firewall
Als ESET Firewall schadelijke netwerkactiviteit detecteert, wordt er een meldingvenster weergegeven waarin de
gebeurtenis wordt beschreven. In de melding staat een koppeling naar meer informatie over de gebeurtenis en u
kunt desgewenst een uitzondering instellen voor deze gebeurtenis.
OPMERKING
Als een netwerktoepassing of -apparaat netwerkstandaarden onjuist implementeert, kan dit er herhaaldelijk toe
leiden dat er IDS-firewallmeldingen worden geactiveerd. Dankzij de melding kunt u rechtstreeks een
uitzondering maken om te voorkomen dat ESET Firewall deze toepassing of dit apparaat detecteert.
4.3.8.4 Geavanceerde PCAP-logboekregistratie
Deze functie is bedoeld om de ESET-klantenservice te voorzien van complexere logbestanden. Gebruik deze functie
alleen als u hierom door ESET-klantenservice wordt gevraagd aangezien er anders een heel groot logbestand kan
ontstaan en uw computer kan worden vertraagd.
1. Ga naar Geavanceerde instellingen > Hulpmiddelen > Diagnostiek en schakel Geavanceerde logboekregistratie
inschakelen voor Firewall in.
2. Probeer het probleem waarmee u te maken hebt opnieuw te produceren.
3. Schakel geavanceerde PCAP-logboekregistratie uit.
4. Het PCAP-logbestand vindt u in dezelfde map als waar de diagnostische geheugendumps worden gegenereerd:
Microsoft Windows Vista of nieuwer
C:\ProgramData\ESET\ESET Smart Security Premium\Diagnostics\
Microsoft Windows XP
C:\Documents and Settings\All Users\...

87
4.3.8.5 Problemen oplossen met protocolfiltering
Als u problemen ervaart met uw browser of e-mailclient, is de eerste stap om te bepalen of protocolfiltering
hiervoor verantwoordelijk is. Probeer protocolfiltering voor de toepassing uit te schaken in Geavanceerde
instellingen (denk eraan dit weer in te schakelen als u hiermee klaar bent, anders blijven uw browser en e-
mailclient onbeschermd). Als het probleem verdwijnt nadat u deze functie hebt uitgeschakeld, kunt u aan de hand
van de volgende veelvoorkomende problemen mogelijk een oplossing toepassen:
Problemen met het bijwerken of beveiligen van communicatie
Als uw toepassing meldt dat een communicatiekanaal niet kan worden bijgewerkt of niet is beveiligd:
Als u SSL-protocolfiltering hebt ingeschakeld, probeer dit dan tijdelijk uit te schakelen. Als dat helpt, kunt u SSL-
filtering uitgeschakeld laten en de update zijn werk laten doen door de problematische communicatie uit te
sluiten:
Maak de SSL-protocolfiltermodus interactief. Voer de update opnieuw uit. Er wordt een dialoogvenster
weergegeven over gecodeerd netwerkverkeer. Zorg dat de toepassing overeenkomt met de toepassing waarvoor
u een probleem oplost en dat het certificaat van de server komt waarvan de update afkomstig is. Kies er
vervolgens voor de actie voor dit certificaat te onthouden en klik op Negeren. Als er geen relevante
dialoogvensters meer worden weergegeven, kunt u de filtermodus terugzetten op Automatisch en zou het
probleem opgelost moeten zijn.
Als de toepassing geen browser of e-mailclient is, kunt u die in zijn geheel uitsluiten van protocolfiltering (als u
dit voor uw browsers of e-mailclient doet, loopt u een verhoogd risico). Elke toepassing waarvan de
communicatie in het verleden is gefilterd, staat al in de lijst als u een uitzondering toevoegt. Het zou dus niet
nodig hoeven zijn een toepassing handmatig toe te voegen.
Problemen met toegang tot een apparaat in uw netwerk
Als u geen enkele functie van een apparaat in een netwerk kunt gebruiken (zoals het openen van een webpagina,
het gebruik van een webcam of afspelen van video op een mediaplayer), probeer dan de IPv4- en IPv6-adressen van
dat apparaat toe te voegen aan de lijst met uitgezonderde adressen.
Problemen met een bepaalde website
U kunt bepaalde websites uitzonderen van protocolfiltering met URL-adresbeheer. Een voorbeeld: als u geen
toegang kunt krijgen tot https://www.gmail.com/intl/en/mail/help/about.html, voeg dan *gmail.com* toe aan de
lijst met uitgezonderde adressen.
De fout 'Bepaalde toepassingen die het basiscertificaat kunnen importeren zijn nog actief.'
Als u SSL-protocolfiltering inschakelt, zorgt ESET Smart Security Premium ervoor dat geïnstalleerde toepassingen de
manier waarop het SSL-protocol wordt gefilterd wordt vertrouwd doordat er een certificaat voor deze toepassingen
in de certificaatopslag wordt geïmporteerd. Voor bepaalde toepassingen is dit niet mogelijk als de desbetreffende
toepassingen worden uitgevoerd. Dit geldt onder andere voor Firefox en Opera. Zorg dat deze toepassingen niet
worden uitgevoerd (de beste manier om dit te doen is om Taakbeheer te openen en ervoor te zorgen dat
firefox.exe en opera.exe niet op het tabblad Processen worden vermeld). Klik vervolgens op Opnieuw.
Fout over niet-vertrouwde uitgever of ongeldige handtekening
Dit betekent waarschijnlijk dat het importeren zoals hierboven vermeld, is mislukt. Controleer eerst of er nog een
vermelde toepassing wordt uitgevoerd. Schakel vervolgens SSL-protocolfiltering uit en schakel het weer in. Voer
het importeren vervolgens opnieuw uit.

88
4.4 Beveiligingshulpprogramma's
Als u Beveiligingshulpprogramma's instelt, kunt u de volgende modules aanpassen:
Beveiliging van bankieren en betalingen
Ouderlijk toezicht
Antidiefstal
Wachtwoordmanager
Secure Data
4.4.1 Ouderlijk toezicht
In de module Ouderlijk toezicht kunt u de instellingen voor ouderlijk toezicht configureren, waardoor ouders
geautomatiseerde hulpprogramma's kunnen gebruiken om hun kinderen te beschermen en beperkingen voor
apparaten en services in te stellen. Het doel is om te voorkomen dat kinderen en tieners pagina's openen met
ongeschikte en schadelijke inhoud.
Met Ouderlijk toezicht kunt u webpagina's blokkeren die mogelijk schadelijk materiaal bevatten. Daarnaast kunnen
ouders de toegang verbieden tot meer dan 40 vooraf gedefinieerde websitecategorieën en meer dan 140
subcategorieën.
Volg de onderstaande stappen om Ouderlijk toezicht te activeren voor een specifiek gebruikersaccount:
1. Ouderlijk toezicht is standaard uitgeschakeld in ESET Smart Security Premium. Er zijn twee methoden voor het
activeren van Ouderlijk toezicht:
o Klik op in Instellingen > Beveiligingshulpprogramma's > Ouderlijk toezicht in het
hoofdprogrammavenster en wijzig de status voor Ouderlijk toezicht in ingeschakeld.
o Druk op F5 om de boomstructuur Geavanceerde instellingen te openen, navigeer naar Web en e-mail >
Ouderlijk toezicht en schakel de schakelaar naast Integreren in systeem in.
2. Klik op Instellingen > Beveiligingshulpprogramma's > Ouderlijk toezicht in het hoofdprogrammavenster. Hoewel
Ingeschakeld wordt weergegeven naast Ouderlijk toezicht, moet u Ouderlijk toezicht configureren voor het
gewenste account door te klikken op Kindaccount beveiligen of Ouderaccount. Voer in het volgende venster de
geboortedatum in om het toegangsniveau en aanbevolen webpagina's die voor die leeftijd geschikt zijn te
bepalen. Ouderlijk toezicht wordt nu ingeschakeld voor het opgegeven gebruikersaccount. Klik op
Geblokkeerde inhoud en instellingen... onder de accountnaam om aan te geven welke categorieën u wilt
toestaan of blokkeren op het tabblad Categorieën. Klik op het tabblad Uitzonderingen om aangepaste
webpagina's toe te staan of te blokkeren die niet overeenkomen met een categorie.

89
Als u op Instellingen > Beveiligingshulpprogramma's > Ouderlijk toezicht klikt in het hoofdproductvenster van ESET
Smart Security Premium, ziet dat het hoofdvenster bestaat uit:
Windows-gebruikersaccounts
Als u een rol hebt gemaakt voor een bestaand account, wordt deze hier weergegeven. Klik op de schuifregelaar
zodat een groen vinkje wordt weergegeven naast Ouderlijk toezicht voor het account. Klik onder
het actieve account op Geblokkeerde inhoud en instellingen... om de lijst weer te geven met toegestane
categorieën van webpagina's voor dit account en geblokkeerde en toegestane webpagina's.
BELANGRIJK
als u een nieuw account wilt maken (bijvoorbeeld voor een kind), kunt u de stapsgewijze instructies volgen voor
Windows 7 of Windows Vista:
1. Open Gebruikersaccounts door achtereenvolgens op de knop Start (linksonder op uw bureaublad),
Configuratiescherm en Gebruikersaccounts te klikken.
2. Klik op Gebruikersaccount beheren. Als u wordt gevraagd om een beheerderswachtwoord of om te
bevestigen, typt u het wachtwoord of bevestigt u het bericht.
3. Klik op Een nieuw account maken.
4. Typ een naam voor het gebruikersaccount, klik op een accounttype en klik op Account maken.
5. Open het venster Ouderlijk toezicht door nogmaals in het hoofdprogrammavenster van ESET Smart Security
Premium te klikken op Instellingen > Beveiligingshulpprogramma's > Ouderlijk toezicht.
Het onderste deel van een venster bevat
Een uitzondering toevoegen voor een website... : de specifieke website kan worden toegestaan of geblokkeerd op
basis van afzonderlijke voorkeuren voor elk ouderaccount.
Logbestand weergeven: hier kunt u een gedetailleerd logboek van de activiteiten van Ouderlijk toezicht bekijken
(geblokkeerde pagina's, het account waarvoor de pagina is geblokkeerd, de categorie, enz.). U kunt dit logboek ook
filteren op basis van door u gekozen criteria door op Filteren te klikken.

90
Ouderlijk toezicht
Nadat u Ouderlijk toezicht hebt uitgeschakeld, verschijnt het venster Ouderlijk toezicht uitschakelen. Hier kunt u
het tijdsinterval instellen gedurende welke de beveiliging is uitgeschakeld. De optie verandert vervolgens in
Onderbroken of Permanent uitgeschakeld.
Het is belangrijk om de instellingen in ESET Smart Security Premium met een wachtwoord te beveiligen. Dit
wachtwoord kan worden ingesteld in het gedeelte Toegangsinstellingen. Als er geen wachtwoord is ingesteld,
verschijnt de volgende waarschuwing: Beveilig alle instellingen met een wachtwoord om ongeoorloofde
wijzigingen te voorkomen. De beperkingen die in Ouderlijk toezicht worden ingesteld, hebben alleen invloed op de
standaardgebruikersaccounts. Aangezien een beheerder elke beperking kan opheffen, hebben deze geen invloed
op beheerders.
HTTPS-communicatie (SSL) wordt standaard niet gefilterd. Daarom kunnen met Ouderlijk toezicht geen webpagina's
worden geblokkeerd die beginnen met https://. Als u deze voorziening wilt gebruiken, schakelt u de instelling
SSL/TLS-protocolfiltering inschakelen in de structuur Geavanceerde instellingen in onder Web en e-mail > SSL/TLS.
OPMERKING
Ouderlijk toezicht werkt alleen correct als inhoudsfilter toepassingsprotocol, HTTP-protocolcontrole en
Systeemintegratie zijn ingeschakeld. Al deze functies zijn standaard ingeschakeld.
4.4.1.1 Categorieën
Druk op het schakelpictogram naast de categorie om deze toe te staan. Als u de schakelaar uit laat, is deze categorie
voor de geselecteerde account niet toegelaten.
Hier volgen enkele voorbeelden van categorieën (groepen) waar gebruikers mogelijk niet bekend mee zijn:
Overige: gewoonlijk privé-IP-adressen (lokaal) zoals intranet, 127.0.0.0/8 en 192.168.0.0/16. Wanneer een
foutcode 403 of 404 wordt weergegeven, hoort de website ook in deze categorie.
Niet opgelost: deze categorie bevat webpagina's die niet zijn opgelost vanwege een fout tijdens het maken
van een verbinding met de database-engine voor Ouderlijk toezicht.
Niet gecategoriseerd: onbekende webpagina's die nog niet in de database voor Ouderlijk toezicht staan.
Dynamisch: webpagina's die doorverwijzen naar andere pagina's op andere websites.

91
4.4.1.2 Website-uitzonderingen
Om een uitzondering voor een website toe te voegen, klikt u op Installatie > Beveiligingshulpprogramma's >
Ouderlijk toezicht en klikt u vervolgens op Een uitzondering toevoegen voor een website.
Voer de url in het veld Website-url in en selecteer (toegelaten) of (geblokkeerd) voor elke specifieke
gebruikersaccount en klik vervolgens op OK om dit toe te voegen aan de lijst.

92
Als u een URL-adres uit de lijst wilt verwijderen, klikt u op Instellingen > Beveiligingshulpprogramma's > Ouderlijk
toezicht > Geblokkeerde inhoud en instellingen onder het gewenste gebruikersaccount, klikt u op het tabblad
Uitzondering, selecteert u de uitzondering en klikt u op Verwijderen.
In de URL-adreslijst kunnen de speciale symbolen * (sterretje) en ? (vraagteken) niet worden gebruikt. Adressen
met meerdere TLD's moeten bijvoorbeeld handmatig worden ingevoerd (voorbeeldpagina.com,
voorbeeldpagina.sk, enzovoort). Als u een domein toevoegt aan de lijst, wordt alle inhoud in dit domein en alle
subdomeinen (bij voorbeeld sub.voorbeeldpagina.com) geblokkeerd of toegestaan, afhankelijk van uw op URL-
gebaseerde actie.
OPMERKING
Het blokkeren of toestaan van een specifieke webpagina kan nauwkeuriger zijn dan het blokkeren of toestaan
van een categorie webpagina's. Wees voorzichtig bij het wijzigen van deze instellingen en het toevoegen van
een categorie/webpagina aan de lijst.
4.5 Het programma bijwerken
Door regelmatig updates uit te voeren voor ESET Smart Security Premium bent u verzekerd van het maximale
beveiligingsniveau van uw computer. De module Bijwerken waarborgt dat zowel de programmamodules als de
systeemonderdelen altijd up-to-date zijn.
Als u in het hoofdvenster op Bijwerken klikt, ziet u informatie over de huidige updatestatus, inclusief de datum en
tijd van de laatste succesvolle update en of er een update nodig is.
Afgezien van automatische updates kunt u op Controleren op updates klikken om het programma handmatig te
laten bijwerken. Het regelmatig bijwerken van programmamodules en -onderdelen is een belangrijk onderdeel in
het bieden van complete beveiliging tegen schadelijke code. Besteed aandacht aan de configuratie en werking van
het updateproces. U moet uw product activeren met uw Licentiecode om updates te ontvangen. Als u dat niet hebt
gedaan tijdens de installatie, kunt u uw licentiecode invoeren om uw product te activeren tijdens updates om
toegang te krijgen tot de ESET-updateservers.
OPMERKING
u ontvangt uw licentiecode van ESET na aanschaf van ESET Smart Security Premium.

93
Huidige versie: geeft het nummer weer van de huidige versie die u hebt geïnstalleerd.
Vorige geslaagde update: geeft de datum weer van de vorige geslaagde update. Als hier geen recente datum wordt
weergegeven, zijn uw modules mogelijk niet actueel.
Vorige geslaagde controle op updates: geeft de datum weer van de vorige geslaagde controle op updates.
Alle modules weergeven: geeft een lijst weer met geïnstalleerde programma-onderdelen.
Klik op Controleren op updates om naar de recentste beschikbare versie van ESET Smart Security Premium te
zoeken.
Updateproces
Nadat u op Controleren op updates hebt geklikt, wordt de download gestart. Op het scherm ziet u een
voortgangsbalk voor het downloadproces en de resterende downloadtijd. Als u de update wilt onderbreken, klikt u
op Annuleren.

94
BELANGRIJK
Onder normale omstandigheden ziet u het groene vinkje in het venster Bijwerken, dat aangeeft dat het
programma up-to-date is. Als dit niet het geval is, is het programma verouderd, waardoor het risico van infecties
groter is. Voer zo snel mogelijk updates uit voor de modules.
Als er een bericht over een niet-geslaagde update wordt weergegeven, kan dit zijn veroorzaakt door de volgende
problemen:
1. Ongeldige licentie: de licentiecode is onjuist opgegeven tijdens het opgeven van instellingen voor updates. Wij
adviseren dat u de verificatiegegevens controleert. Het venster Geavanceerde instellingen (klik op Instellingen
in het hoofdmenu en klik vervolgens op Geavanceerde instellingen of druk op F5 op het toetsenbord) bevat
extra updateopties. Klik op Help en ondersteuning > Licentie wijzigen in het hoofdmenu om een nieuwe
licentiecode op te geven.
2. Er is een fout opgetreden tijdens het downloaden van updatebestanden: deze fout wordt mogelijk veroorzaakt
door onj uiste instellingen voor de internetverbinding. Wij adviseren u de internetverbinding te controleren
(bijvoorbeeld door een willekeurige website te openen in uw webbrowser). Als de website niet wordt geopend,
is er waarschijnlijk geen internetverbinding of zijn er verbindingsproblemen met uw computer. Neem contact op
met uw internetprovider als u geen actieve internetverbinding hebt.

95
BELANGRIJK
Wij raden aan uw computer opnieuw op te starten na een geslaagde update om ervoor te zorgen dat alle
programmamodules goed zijn bijgewerkt.
OPMERKING
Ga voor meer informatie naar dit artikel in de ESET-kennisbank.
4.5.1 Update-instellingen
Update-instellingen zijn beschikbaar in de structuur voor Geavanceerde instellingen (F5) onder Bijwerken > Basis. In
dit gedeelte wordt informatie gegeven over de bron van de update, zoals de updateservers die worden gebruikt en
verificatiegegevens voor deze servers.
Basis
Het updateprofiel dat nu in gebruik is (tenzij er een specifiek updateprofiel is ingesteld in Geavanceerde
instellingen > Firewall > Bekende netwerken), wordt weergegeven in het vervolgkeuzemenu Selecteer
standaardupdateprofiel.
Automatisch schakelen van profiel: hiermee kunt u het profiel voor een bepaald netwerk wijzigen.
Als u problemen ondervindt bij het downloaden van updates voor de detectie-engine, klikt u op Wissen om
tijdelijke updatebestanden te verwijderen.
Module terugdraaien
Als u vermoedt dat een nieuwe update van de virusdatabase en/of programmamodules onstabiel of beschadigd is,
kunt u de vorige versie herstellen en alle updates voor een bepaalde periode uitschakelen. U kunt ook eerder
uitgeschakelde updates die u voor onbepaalde tijd had uitgesteld, opnieuw inschakelen.
In ESET Smart Security Premium worden momentopnames van de detectie-engine en programmamodules
vastgelegd voor gebruik met de functie terugdraaien. Als u momentopnamen van de virusdatabase wilt maken, laat

96
u de schakelaar Momentopnames van updatebestanden maken ingeschakeld. In het veld Aantal lokaal opgeslagen
momentopnames wordt het aantal eerder opgeslagen momentopnamen van de database met viruskenmerken
gedefinieerd.
Als u klikt op Terugdraaien (Geavanceerde instellingen (F5) > Bijwerken > Basis), moet u een tijdsinterval selecteren
in het vervolgkeuzemenu dat aangeeft hoe lang updates van de detectie-engine en van programmamodules
worden onderbroken.
Het is belangrijk alle updateparameters correct in te vullen, zodat updates correct worden gedownload. Als u een
firewall gebruikt, dient u te controleren of uw ESET-programma met internet mag communiceren (bijvoorbeeld
HTTP-communicatie).
Profielen
Updateprofielen kunnen worden gemaakt voor verschillende updateconfiguraties en taken. Het maken van
updateprofielen is vooral handig voor mobiele gebruikers, die een alternatief profiel nodig hebben voor
eigenschappen van internetverbindingen die regelmatig worden gewijzigd.
In de vervolgkeuzelijst Selecteer profiel om te bewerken wordt het geselecteerde profiel weergegeven en wordt
dit standaard ingesteld op Mijn profiel. U kunt een nieuw profiel maken door op Bewerken naast Lijst met profielen
te klikken, uw eigen Profielnaam op te geven en te klikken op Toevoegen.
Updates
Standaard is Updatetype ingesteld op Reguliere update om ervoor te zorgen dat updatebestanden automatisch
worden gedownload bij de ESET-server met het minste netwerkverkeer. Bèta-updates (de optie Bèta-update) zijn
updates die intern grondig zijn getest en die naar verwachting binnenkort voor iedereen beschikbaar zullen zijn. U
kunt profijt hebben van bèta-updates, omdat u dan toegang hebt tot de recentste detectiemethoden en
oplossingen. Het is echter mogelijk dat bèta-updates nog niet altijd stabiel genoeg zijn. Gebruik ze daarom NIET op
productieservers en werkstations die een maximale beschikbaarheid en stabiliteit moeten bieden.
Vragen alvorens update te downloaden: het programma geeft een melding weer waarin u kunt kiezen of u
updatebestanden wilt downloaden of weigeren.

97
Vragen of een updatebestand groter is dan (kB): het programma geeft een melding weer als de grootte van het
updatebestand groter is dan de opgegeven waarde.
Melding over succesvolle update uitschakelen: schakel deze optie in als u rechtsonder in het scherm in het
systeemvak geen meldingen weergegeven wilt hebben. Het is handig deze optie in te schakelen als u een
toepassing of spel in de modus volledig scherm uitvoert. In de Gamer-modus zijn alle meldingen uitgeschakeld.
Module-updates
Vaker updates van detectiekenmerken inschakelen: detectiekenmerken worden met een korter interval
bijgewerkt. Het uitschakelen van deze instelling kan gevolgen hebben voor het detectiepercentage.
Update van programmaonderdelen
Toepassingsupdate: er wordt een bevestigingsdialoogvenster weergegeven als opnieuw installeren nodig is.
4.5.1.1 Instellingen voor geavanceerde update
De instellingen voor een geavanceerde update bevatten opties voor de configuratie van Updatemodus, HTTP-proxy.
4.5.1.1.1 Updatemodus
Op het tabblad Updatemodus vindt u de opties voor reguliere programma-updates. Met deze instellingen kunt u
vooraf het gedrag van het programma bepalen voor wanneer er nieuwe updates beschikbaar zijn voor de detectie-
engine of programmaonderdelen.
Updates voor programmaonderdelen zijn onder andere nieuwe functies of wijzigingen in bestaande functies ten
opzichte van eerdere versies, en maken deel uit van de reguliere updates (van de detectie-engine). Nadat een
update van programmaonderdelen is geïnstalleerd, moet de computer mogelijk opnieuw worden opgestart.
De volgende instellingen zijn beschikbaar:
Toepassingsupdate: als deze optie is ingeschakeld, wordt elke upgrade voor programmaonderdelen
automatisch en stil uitgevoerd zonder volledige productupgrade.
Handmatig bijwerken van programmaonderdeel inschakelen: is standaard uitgeschakeld. Wanneer deze functie
is ingeschakeld en een nieuwere versie van ESET Smart Security Premium beschikbaar is, kunt u updates zoeken
in het tabblad Update en de nieuwere versie installeren.
Vragen alvorens update te downloaden: wanneer deze optie actief is, wordt er een melding weergegeven en
wordt u gevraagd de installatie van beschikbare updates te bevestigen voordat deze worden geïnstalleerd.
Vragen als een updatebestand groter is dan (kB): als het updatebestand groter is dan de hier opgegeven
grootte, wordt er een melding weergegeven en wordt u gevraagd om de installatie van beschikbare updates te
bevestigen voordat deze worden geïnstalleerd.
4.5.1.1.2 Verbindingsopties
U krijgt toegang tot de opties van de proxyserverinstellingen van een bepaald updateprofiel door te klikken op
Bijwerken in de structuur Geavanceerde instellingen (F5) en door vervolgens te klikken op Profielen > Updates >
Verbindingsopties. Klik op het vervolgkeuzemenu Proxymodus en selecteer een van de volgende drie opties:
Geen proxyserver gebruiken
Verbinding maken via een proxyserver
Algemene instellingen voor proxyserver gebruiken
Selecteer Algemene instellingen voor proxyserver gebruiken om de configuratieopties van de proxyserver te
gebruiken die al zijn opgegeven in de vertakking Hulpmiddelen > Proxyserver van de structuur voor geavanceerde
instellingen.
Selecteer Geen proxyserver gebruiken om op te geven dat er geen proxyserver wordt gebruikt om ESET Smart
Security Premium bij te werken.

98
De optie Verbinding maken via een proxyserver moet worden gekozen indien:
een andere proxyserver dan deze gedefinieerd in Hulpmiddelen > Proxyserver wordt gebruikt om ESET Smart
Security Premium bij te werken. In deze configuratie moet de informatie voor de nieuwe proxyserver worden
vastgelegd onder Proxyserver adres, communicatie Poort (standaard 3128), en indien nodig de
Gebruikersnaam en het Wachtwoord voor de proxyserver.
De proxyserverinstellingen zijn niet algemeen ingesteld, maar ESET Smart Security Premium maakt verbinding
met een proxyserver voor updates.
Uw computer maakt verbinding met internet via een proxyserver. De instellingen worden tijdens de
installatie van het programma overgenomen van Internet Explorer, maar als er wijzigingen optreden
(bijvoorbeeld als u van ISP wisselt), moet u nagaan of de HTTP-proxyinstellingen in dit venster correct zijn. Als
dit niet het geval is, kan het programma geen verbinding maken met de updateservers.
De standaardinstelling voor de proxyserver is Algemene instellingen voor proxyserver gebruiken.
Directe verbinding gebruiken als proxy niet beschikbaar is: de proxy wordt omzeild tijdens het bijwerken als de
proxy onbereikbaar is.
OPMERKING
De velden Gebruikersnaam en het Wachtwoord in dit gedeelte zijn specifiek voor de proxyserver. Vul deze
velden alleen in wanneer gebruikersnaam en wachtwoord vereist zijn om toegang te krijgen tot de proxyserver.
Deze velden zijn niet bestemd voor uw gebruikersnaam/wachtwoord voor ESET Smart Security Premium en
moeten alleen worden ingevuld als u weet dat u een wachtwoord nodig hebt om via een proxyserver verbinding
te maken met internet.
4.5.2 Ongedaan maken van update
Als u vermoedt dat een nieuwe update van de detectie-engine en/of programmamodules instabiel of beschadigd
is, kunt u de vorige versie herstellen en alle updates voor een bepaalde periode uitschakelen. U kunt ook eerder
uitgeschakelde updates die u voor onbepaalde tijd had uitgesteld, opnieuw inschakelen.
In ESET Smart Security Premium worden momentopnames van de detectie-engine en programmamodules
vastgelegd voor gebruik met de functie terugdraaien. Als u momentopnamen van de detectie-engine wilt maken,
laat het selectievakj e Momentopnames van updatebestanden maken dan ingeschakeld. In het veld Aantal lokaal
opgeslagen momentopnames wordt het aantal eerder opgeslagen momentopnamen van de detectie-engine
gedefinieerd.
Als u klikt op Terugdraaien (Geavanceerde instellingen (F5) > Bijwerken > Basis), moet u een tijdsinterval selecteren
in het vervolgkeuzemenu Duur dat aangeeft hoe lang updates van de detectie-engine en van programmamodules
worden onderbroken.
Selecteer Tot handmatig ingeschakeld om regelmatige updates voor onbepaalde tijd uit te stellen totdat u de
updatefunctie handmatig herstelt. Aangezien dit een potentieel beveiligingsrisico met zich meebrengt, wordt
afgeraden om deze optie te selecteren.
Als een vorige versie wordt hersteld door middel van terugdraaien, verandert de knop Terugdraaien in Updates
toestaan. Er zijn geen updates toegestaan gedurende de periode die is geselecteerd in het vervolgkeuzemenu
Updates onderbreken. De versie van de detectie-engine wordt teruggezet naar de oudste versie die beschikbaar is
en wordt in het bestandssysteem van de lokale computer bewaard als momentopname.

99
OPMERKING
Stel dat nummer 6871 de recentste versie is van de detectie-engine. 6870 en 6868 worden opgeslagen als
momentopnamen van de detectie-engine. 6869 is niet beschikbaar, bijvoorbeeld omdat de computer werd
uitgeschakeld en een meer recente update beschikbaar werd gesteld voordat 6869 werd gedownload. Als het
veld Aantal lokaal opgeslagen momentopnames is ingesteld op 2 en u op Terugdraaien klikt, wordt de detectie-
engine (inclusief programmamodules) hersteld naar versie 6868. Dit proces kan even duren. Controleer in het
hoofdprogrammavenster van ESET Smart Security Premium bij het gedeelte Bijwerken of de versie van de
detectie-engine is teruggezet.
4.5.3 Updatetaken maken
Updates kunnen handmatig worden geactiveerd door op Controleren op updates te klikken in het
informatievenster dat wordt weergegeven nadat u in het hoofdmenu op Bijwerken hebt geklikt.
Updates kunnen ook worden uitgevoerd als geplande taken. Als u een geplande taak wilt configureren, klikt u op
Hulpmiddelen > Planner. Standaard zijn in ESET Smart Security Premium de volgende taken geactiveerd:
Regelmatige automatische update
Automatisch update uitvoeren na inbelverbinding
Automatisch update uitvoeren na aanmelding gebruiker
Iedere updatetaak kan aan uw behoeften worden aangepast. Behalve de standaardupdatetaken kunt u ook nieuwe
updatetaken maken met een door de gebruiker gedefinieerde configuratie. Zie het gedeelte Planner voor meer
informatie over het maken en configureren van updatetaken.

100
4.6 Hulpmiddelen
Het menu Hulpmiddelen bevat modules die het beheer van het programma vereenvoudigt en ervaren gebruikers
extra opties biedt.
Wachtwoordmanager : uw wachtwoorden beschermen Voor meer informatie klikt u hier.
Secure Data : uw persoonlijke en vertrouwelijke bestanden beschermen. Voor meer informatie klikt u hier.
Connected Home Monitor: het risico van veiligheidsproblemen verlagen wanneer u verbonden bent met een
netwerk. Voor meer informatie klikt u hier.
Veilig internetbankieren: ESET Smart Security Premium beschermt uw creditcardnummers en andere geheime
persoonlijke gegevens terwijl u gebruikmaakt van internetbankieren of betaalwebsites. Er wordt een beveiligde
browser geopend om veilige banktransacties te verzorgen. Zie dit artikel in de ESET-kennisbank voor meer
informatie.
Antidiefstal: helpt bij het zoeken naar uw apparaat na diefstal of verlies.
Klik op Meer hulpmiddelen om andere hulpmiddelen om uw computer te beschermen weer te geven.

101
4.6.1 Password Manager
Password Manager maakt deel uit van het pakket ESET Smart Security Premium. Dit is een
wachtwoordbeheerprogramma dat uw wachtwoorden en persoonlijke gegevens beschermt en opslaat. Ook
beschikt u hiermee over een formulieraanvullingsfunctie waarmee u tijd bespaart doordat webformulieren
automatisch en nauwkeurig worden ingevuld.
Password Manager gaan gebruiken
Password Manager inschakelen
Importeer of maak uw Identiteiten en Webaccounts of App-accounts.
Leer de beschikbare hulpmiddelen kennen waarmee u uw accounts kunt beschermen.opmerking is slechts een
beknopte informatie. Hoewel u opmerkingen kunt overslaan, kunnen opmerkingen waardevolle informatie
bevatten, zoals bepaalde functies of een koppeling naar een verwant onderwerp.
Functies en voordelen
Sterke wachtwoorden
De ingebouwde wachtwoordgenerator vraagt u sterke, onvoorspelbare
wachtwoorden te maken. Uw nieuwe aanmeldingsreferenties worden
automatisch opgeslagen wanneer er nieuwe accounts worden gemaakt.
Automatisch aanmelden bij
websites en toepassingen
Password Manager integreert met talloze toepassingen
. Met één klik opent u uw favoriete
websites die met een wachtwoord zijn beveiligd en wordt u automatisch
bij deze websites aangemeld.
Meerdere platforms
Password Manager ondersteunt alle populaire platforms; Windows, Mac,
Android en iOS.
Browserintegratie en importeren
Password Manager ondersteunt alle bekende browsers, en kunt u
gemakkelijk uw referenties en identiteiten importeren vanuit populaire
browsers of andere wachtwoordbeheerprogramma's.
Dashboard met
beveiligingsinformatie
Zwakke wachtwoorden worden op één plaats weergegeven, zodat u altijd
weet welke accounts een beter wachtwoord nodig hebben om uw
beveiliging te verbeteren.
Met één klik formulieren invullen
U bespaart tijd doordat informatie automatisch wordt ingevuld in
registratieformulieren en winkelwagentjes van webwinkels. U kunt
meerdere identiteiten opslaan en gebruiken bij uiteenlopende sites en
toepassingen, bijvoorbeeld een voor persoonlijk gebruik en een voor uw
werk.
Snelstarten
Druk op CTRL+ALT+R om direct toegang tot uw webaccounts te krijgen.

102
4.6.1.1 Password Manager inschakelen
Als u Password Manager wilt inschakelen, opent u het hoofdprogrammavenster, navigeert u naar Instellingen >
Beveiligingshulpprogramma's en klikt u op de schakelaar naast Password Manager. Wacht even tot de wijziging van
kracht is geworden en klik vervolgens op Start > Nu configureren om Password Manager te starten.
Uw Password Manager-account instellen
Nadat u Password Manager hebt ingeschakeld bij de aanvullende beveiligingshulpprogramma's, wordt Password
Manager gestart. U kunt kiezen of u Bestaand wachtwoordarchief wilt gebruiken of een Nieuw wachtwoordarchief
wilt maken.
a. Bestaand wachtwoordarchief
Geef uw E-mailadres en Hoofdwachtwoord op om uw Password Manager-account opnieuw te gaan
gebruiken.
b. Nieuw wachtwoordarchief
Volg de onderstaande stappen om een nieuw wachtwoordarchief te maken:
1. Geef uw E-mailadres op als id voor uw account en maak een nieuw Hoofdwachtwoord.
2. Bevestig uw hoofdwachtwoord.
3. Selecteer de browser die u wilt integreren met Password Manager. Zie ondersteunde browsers
voor een lijst met ondersteunde browsers.
4. U wordt gevraagd of u extensies aan uw browser(s) wilt toevoegen en/of geactiveerde browser(s)
wilt sluiten.
5. Begin met het importeren of maken van accounts en identiteiten.
4.6.1.2 Password Manager ontgrendelen
OPMERKING
Controleer of Password Manager is ingeschakeld in Instellingen.
Password Manager wordt automatisch gestart wanneer uw computer wordt opgestart en wordt op de achtergrond
uitgevoerd. Om uw wachtwoorden en persoonlijke gegevens te beschermen, is er een wachtwoord nodig om
toegang te krijgen tot Password Manager.
Password Manager wordt vanzelf vergrendeld als er enige tijd geen activiteit van de gebruiker is geweest. U kunt
het tijdinterval hiervoor wijzigen onder Instellingen > Beveiliging > Automatisch vergrendelen.
Password Manager ontgrendelen:
Druk op CTRL+ALT+L om het ontgrendelingsscherm weer te geven. Als u deze combinatie nog een keer
indrukt, wordt Password Manager vergrendeld.
Klik op het Password Manager-pictogram op de werkbalk van de browser.
Password Manager openen:
Open het menu Start, druk op de Windows-toets, typ Password Manager en druk op Enter.
Als u Password Manager wilt starten vanuit ESET Smart Security Premium, opent u het
hoofdprogrammavenster en navigeert u naar Instellingen > Beveiligingshulpprogramma's > Password
Manager.

103
4.6.1.3 Password Manager uitschakelen
Als u Password Manager wilt uitschakelen, opent u het hoofdprogrammavenster en navigeert u naar Instellingen >
Beveiligingshulpprogramma's. Klik op de schakelaar naast Password Manager en laat de wijziging van kracht
worden. Wanneer de schakelaar rood wordt, is Password Manager uitgeschakeld. Uw wachtwoorden blijven op
deze computer opgeslagen en u kunt Password Manager op elk moment opnieuw inschakelen.
Als u uw wachtwoordarchief definitief van deze computer wilt verwijderen, klikt u op het pictogram met een
tandrad naast Password Manager en selecteert u Alle wachtwoorden opnieuw instellen in het vervolgkeuzemenu.
4.6.1.4 Ondersteunde browsers
Password Manager ondersteunt de volgende browsers:
Microsoft Internet Explorer
Mozilla Firefox
Google Chrome
Chromium
Opera
Seamonkey
Yandex
Comodo Dragon
Pale Moon
Password Manager ondersteunt ook talloze populaire toepassingen, zoals Skype.
4.6.2 Identiteiten
Het toevoegen van Identiteiten is handig omdat u hiermee lange webformulieren automatisch kunt laten invullen.
Wanneer u persoonlijke gegevens in een webformulier invult, wordt u door Password Manager gevraagd of u de
gegevens als een Identiteit wilt opslaan. Nadat dit is gebeurd, wordt deze informatie door Password Manager
gebruikt om webformulieren automatisch voor u in te vullen.
U kunt meerdere Identiteiten opslaan, bijvoorbeeld een met uw privéadres, een andere met uw werkgegevens,
enzovoort. Als u wilt, kunt u uw persoonlijke gegevens rechtstreeks in Password Manager invoeren. Klik hiervoor op
het tabblad Identiteiten in de hoofdgebruikersinterface en klik vervolgens op Identiteit toevoegen. Nadat uw
Identiteiten zijn geconfigureerd, hebt u de mogelijkheid de juiste informatie te selecteren voor verschillende
formulieren en toepassingen.

104
4.6.3 App-accounts
Password Manager werkt met talloze populaire toepassingen. Als u wilt dat Password Manager
toepassingsgegevens opslaat, start u de toepassing, klikt u op het Password Manager-pictogram rechtsboven in het
venster en selecteert u Account toevoegen. Voer uw aanmeldingsnaam en wachtwoord voor deze toepassing in het
dialoogvenster in. Controleer de informatie en klik op Nieuw account toevoegen. De volgende keer dat u de app
start, wordt u door Password Manager automatisch aangemeld.
Beheer uw app-accounts met de Password Manager-knop rechtsboven, naast de vensterknoppen.
4.6.4 Webaccounts
Nieuwe Webaccounts toevoegen is heel eenvoudig. Meld u aan bij de website zoals u normaal ook zou doen door
uw gebruikersnaam en wachtwoord (aanmeldingsgegevens) op te geven. U wordt door Password Manager gevraagd
of u met behulp van de wachtwoordgenerator een sterk wachtwoord wilt maken. Als de website of de specifieke
aanmeldingsgegevens nog niet in de database zijn opgeslagen, wordt u door Password Manager gevraagd of u de
aanmeldingsgegevens wilt opslaan die u zojuist hebt opgegeven.
Bij latere bezoeken aan de website, worden uw gebruikersnaam en wachtwoord door Password Manager ingevuld
en wordt u automatisch aangemeld. Als er meerdere aanmeldingsgegevens voor een website zijn opgeslagen, kunt
u er een als standaardaanmeldingsgegevens instellen of u kunt Password Manager u bij elk bezoek laten vragen
welke aanmeldingsgegevens u wilt selecteren.
Beheer uw webaccounts met de Password Manager-browserextensie die zich op de werkbalk van uw browser
bevindt.

105
4.6.5 Menu
Vanuit het toepassingsmenu hebt u toegang tot de volgende opties:
Vergrendelen: hiermee vergrendelt u het venster van Password Manager met uw hoofdwachtwoord.
Toevoegen: hier voegt u een nieuw Webaccount, App-account of een nieuwe Identiteit toe.
Hulpmiddelen: hiermee kunt u een van de ingebouwde hulpmiddelen van Password Manager gebruiken. Zie
het onderwerp Hulpmiddelen voor meer informatie over hulpmiddelen.
Importeren/Exporteren: hiermee importeert uw wachtwoorden en persoonlijke gegevens uit browsers of
andere wachtwoordbeheerprogramma's. Of exporteer uw database naar een versleuteld bestand.
Instellingen: hiermee wijzigt u de instellingen van Password Manager.
Afsluiten: hiermee sluit u Password Manager.
4.6.5.1 Instellingen
Ondersteunde browsers
Een lijst met alle browsers die worden ondersteund door Password Manager. Geïnstalleerde browsers worden
boven in de lijst weergegeven. Er wordt een Password Manager-pictogram weergegeven naast browsers die zijn
geïntegreerd. Klik op Verwijderen als u de Password Manager-extensie wilt verwijderen of op Installeren als u
Password Manager met een browser wilt integreren.
Beveiliging
Wij zig uw Hoofdwachtwoord, tijd voor Automatisch vergrendelen of Autorisatiemethode. We raden niet aan
Password Manager te gebruiken met de functie Automatisch vergrendelen uitgeschakeld.
Genegeerde websites

106
Lijsten met websites die door Password Manager worden genegeerd. Automatisch invullen werkt niet bij deze
websites.
Vertrouwde websites
Als Password Manager u waarschuwt voor phishing wanneer u een website bezoekt waarvan u weet dat die veilig is,
kunt u die website toevoegen aan deze lijst om deze waarschuwing te voorkomen. De waarschuwing wordt
weergegeven voor sites die verdacht gedrag vertonen, zoals omleiding naar andere domeinen.
Geblokkeerde apps
Selecteer toepassingen waarvoor u Password Manager niet wilt gebruiken.
Sneltoetsen
Stel sneltoetsen op het toetsenbord in voor Password Manager.
Database
Bewerk de locatie van de Password Manager-database en back-upmap.
4.6.5.2 Hulpmiddelen
Als u een van de ingebouwde hulpmiddelen in Password Manager wilt gebruiken, opent u het
hoofdprogrammavenster, navigeert u naar Menu > Hulpmiddelen en kiest u het gewenste hulpmiddel.
Herstellen
Mocht er iets verkeerd gaan of u per ongeluk belangrijke accountgegevens verwijderen, dan kunt u uw
wachtwoorddatabase herstellen. Er worden regelmatig back-upbestanden op uw computer gemaakt en u kunt
kiezen of u wilt terugkeren naar een specifieke Back-updatum/tijd of naar specifieke Wijzigingen die in de database
zijn aangebracht. U kunt de locatie van de back-upmap wijzigen in Instellingen.
Virtueel toetsenbord
Met Virtueel toetsenbord kunt u zich verdedigen tegen keyloggers. Als u het selectievakje Antispy inschakelt om
deze functie in te schakelen, kunnen uw toetsenbordaanslagen niet worden gevolgd. Wij raden het gebruik van
Virtueel toetsenbord aan op vliegvelden, in cafés en in andere openbare ruimten. De standaardsneltoets om
Virtueel toetsenbord te starten, is CTRL+ALT+K. U kunt deze sneltoets wijzigen in Instellingen.
Wachtwoordgenerator
Elke keer wanneer u een nieuw wachtwoord maakt of een bestaand wachtwoord wilt wijzigen, genereert de
wachtwoordgenerator een complex wachtwoord dat in Password Manager kan worden opgeslagen. In Aanvullende
opties kunt u de lengte van het wachtwoord wijzigen, of tekens kiezen die wel of niet moeten worden gebruikt.
Het vak Snelstarten
Gebruik het vak Snelstarten om snel toegang te krijgen tot uw webaccounts of toepassingsaccounts. Druk op
CTRL+ALT+R om het vak Snelstarten op te roepen. U kunt deze sneltoets wijzigen in Instellingen. Voer een
trefwoord in en selecteer uw account in de lijst. Als u nog een keer op de sneltoets drukt, wordt het vak Snelstarten
weer verborgen.
Importeren/exporteren
Vanuit het hoofdvenster of het toepassingsmenu krijgt u toegang tot de import/exportfunctie. Met Importeren kunt
u al uw wachtwoorden en persoonlijke gegevens verzamelen uit een back-upbestand, andere
wachtwoordbeheerprogramma's en -toepassingen, en ondersteunde browsers.

107
Met Exporteren kunt u versleutelde back-ups in .spdb-indeling maken van uw Password Manager-database. Ook
kunt u niet-versleutelde bestanden maken in de indelingen .xml, .html en .txt. Deze indelingen zijn niet
versleuteld en we raden u niet deze te gebruiken voor wachtwoorden of persoonlijke gegevens.
4.6.6 Mijn account
De eerste keer dat u Password Manager inschakelt, maakt u een Password Manager-account. Dit is uw eigen
persoonlijke beheeraccount waarmee u licenties voor Password Manager kunt beheren. In elke licentie voor ESET
Smart Security Premium zijn 5 ESET Password Manager-seats inbegrepen.
E-mail: dit is het e-mailadres dat als uw aanmeldingsnaam fungeert en uw unieke id is voor Password Manager.
Hoofdwachtwoord: dit is uw Hoofdwachtwoord, dat u maakt om toegang te krijgen tot uw Password Manager-
account en wachtwoorddatabase.
Als u zich wilt aanmelden bij uw Password Manager-account, klikt u op Mijn account in het hoofdvenster van
Password Manager.
4.6.6.1 Hoofdwachtwoord
Uw Hoofdwachtwoord is de sleutel tot uw versleutelde database. Alleen U kent uw hoofdwachtwoord. ESET slaat
dit nooit op onze servers op en verzendt dit ook niet via internet. Als u uw Hoofdwachtwoord niet meer weet of
kwijt raakt, kan dit niet opnieuw naar u worden toegezonden. Kies een sterk wachtwoord dat u kunt onthouden. In
het algemeen geldt, hoe langer uw Hoofdwachtwoord, hoe beter: wij raden aan dat u een Hoofdwachtwoord kiest
met niet minder dan 8 tekens, en dat bestaat uit een combinatie van kleine letters en hoofdletters, cijfers en
speciale tekens.
4.6.6.2 Synchronisatie
Met Password Manager kunt u uw versleutelde database synchroniseren en er een back-up van maken in een
beveiligde cloud of op uw apparaten.
De synchronisatiestatus wordt onder in het hoofdvenster weergegeven.
Gesynchroniseerd om HH:MM:SS AM/PM: een groen vinkje dat met een tijdstempel wordt weergegeven,
betekent dat uw account is gesynchroniseerd.
Synchroniseren uitgeschakeld: synchronisatie werkt niet, uw licentie is mogelijk verlopen of Password Manager
kan geen verbinding maken met internet.
4.6.7 Inleiding in Secure Data
Met Secure Data van ESET kunt u gegevens op uw computer en USB-stations versleutelen om misbruik van
privégegevens en vertrouwelijke informatie te voorkomen.
4.6.7.1 Installatie
Secure Data is onderdeel van ESET Smart Security Premium.
Na installatie en activering van ESET Smart Security Premium kunt u Secure Data samen met andere functies
inschakelen. Klik op Inschakelen naast Secure Data om Secure Data in te schakelen.
Als u het welkomstscherm afsluit zonder Secure Data in te schakelen, kunt u de versleutelingsfunctie inschakelen in
het gedeelte Instellingen > Beveiligingshulpprogramma's van ESET Smart Security Premium door te klikken op
Secure Data.

109
4.6.7.2.1 Versleuteld virtueel station
Met Secure Data kunt u versleutelde virtuele stations maken. Er is geen maximum aantal stations dat u kunt maken,
zolang er maar hardeschijfruimte voor de stations is om te gebruiken. Volg de onderstaande stappen om een
versleuteld virtueel station te maken:
1. Klik in het scherm Versleutel gegevens op deze computer of een verwisselbaar station op Virtueel station.
2. Klik op Bladeren om de locatie te selecteren waar u het virtuele station wilt opslaan.
3. Voer een naam in voor het virtuele station en klik op Opslaan.
4. Gebruik het vervolgkeuzemenu Maximumcapaciteit om de grootte van uw virtuele station in te stellen en
klik op Doorgaan.
5. Stel een wachtwoord in voor uw virtuele station. Als u niet wilt dat het virtuele station automatisch wordt
ontsleuteld wanneer u zich bij uw Windows-account aanmeldt, schakel Automatisch ontsleutelen bij dit
Windows-account dan uit. Klik op Doorgaan.

110
6. Uw versleutelde virtuele station is gemaakt en gereed voor gebruik. Het station wordt als een lokale schijf
weergegeven als u Deze computer (Computer in Windows 7 en eerder) opent.
Als u toegang tot het versleutelde station wilt nadat u de computer opnieuw hebt opgestart, gaat u naar het
versleutelde stationsbestand (bestandstype.eed ) dat u hebt gemaakt en dubbelklikt u erop. Geef wanneer
daarom wordt gevraagd het wachtwoord op dat u hebt geconfigureerd toen u het versleutelde station maakte. Het
station wordt gekoppeld en als een lokale schijf weergegeven onder Deze computer (Computer in Windows 7 en
eerder).
OPMERKING
Wanneer een versleuteld station als een lokale schijf is gekoppeld, is die lokale schijf en de versleutelde inhoud
op die schijf beschikbaar voor andere gebruikers op die Windows-computer, tenzij u zich afmeldt of de computer
opnieuw opstart.

111
4.6.7.2.2 Versleuteld verwisselbaar station
Met Secure Data kunt u versleutelde mappen op verwisselbare stations maken. Volg hiervoor de volgende stappen:
1. Sluit het verwisselbare station (USB-flashstation, USB-schijf) op de computer aan.
2. Klik op Verwisselbaar station in het scherm Versleutel gegevens op deze computer of een verwisselbaar
station.
3. Selecteer het aangesloten, verwisselbare station dat u wilt versleutelen en klik op Doorgaan.
4. Stel het gewenste wachtwoord in voor de versleutelde map op het verwisselbare station. Als u niet wilt dat
het virtuele station automatisch wordt ontsleuteld wanneer u zich bij uw Windows-account aanmeldt,
schakel Automatisch ontsleutelen bij dit Windows-account dan uit. Klik op Doorgaan.
5. Uw verwisselbare station is beveiligd en de versleutelde map op het station is klaar voor gebruik.

112
Vanaf nu is de versleutelde map niet meer zichtbaar wanneer u uw verwisselbare station aansluit op een computer
waarop Secure Data niet is geïnstalleerd. Als het verwisselbare station wordt aangesloten op een computer waarop
Secure Data wel is geïnstalleerd, wordt u gevraagd het wachtwoord op te geven om het verwisselbare station te
ontsleutelen. Als er geen wachtwoord wordt opgegeven, is de versleutelde map wel zichtbaar maar niet
toegankelijk.
4.6.8 Connected Home Monitor
Connected Home Monitor kan helpen met het identificeren van beveiligingsproblemen in uw thuisnetwerk, zoals
open poorten of een zwak routerwachtwoord. Deze functie biedt u een toegankelijke lijst met verbonden
apparaten, gesorteerd op type apparaat (bijvoorbeeld printer, router, mobiel apparaat, enz.) om u te laten zien wat
verbinding heeft met uw thuisnetwerk. De functie configureert uw router niet opnieuw voor u. U kunt zelf de
wijzigingen aanbrengen met de gespecialiseerde interface van de router. Thuisrouters kunnen erg kwetsbaar zijn
voor malware die wordt gebruikt om een DDoS-aanval te starten. Als het routerwachtwoord niet is gewijzigd door
de gebruiker en nog steeds het standaardwachtwoord is, kunnen hackers dit wachtwoord gemakkelijk raden en zich
aanmelden bij uw router en deze opnieuw configureren of uw netwerk ondermijnen.
WAARSCHUWING
We raden ten zeerste aan om een sterk wachtwoord te maken dat lang genoeg is en nummers, symbolen of
hoofdletters bevat. Als u een wachtwoord wilt maken dat moeilijker te achterhalen is, gebruikt u een
combinatie van verschillende soorten tekens.
Elk verbonden apparaat wordt weergegeven in sonar view. Ga met de cursor over een apparaatpictogram om de
basisinformatie over het apparaat weer te geven, zoals de netwerknaam en de datum waarop het apparaat voor het
laatst werd gedetecteerd. Klik op het pictogram voor gedetailleerde informatie over het apparaat.
Om de informatie van alle verbonden apparaten weer te geven in een tabeloverzicht, klikt u op . In de
lijstweergave ziet u dezelfde informatie als in de sonarweergave. U kunt de apparaten filteren op basis van de
volgende criteria. Gebruik de vervolgkeuzelijst:
alleen de apparaten die nu met het netwerk zijn verbonden
ongecategoriseerde apparaten
apparaten die zijn verbonden met alle netwerken
Er zijn twee soorten meldingen die worden weergegeven door de module Verbonden thuismonitor:
Nieuw apparaat verbonden met het netwerk: wordt weergegeven indien een voorheen niet gedecteerd
apparaat verbinding maakt met het netwerk terwijl de gebruiker zelf verbinding heeft.
Nieuwe netwerkapparaten gevonden: wordt weergegeven wanneer u opnieuw verbinding maakt met uw
thuisnetwerk en er een voorheen niet gedecteerd apparaat aanwezig is.
OPMERKING
In beide gevallen informeert de melding u dat een niet-toegelaten apparaat verbinding met uw netwerk
probeert te maken.
OPMERKING
Onlangs verbonden apparaten worden dichter bij een router weergegeven, zodat u deze gemakkelijk kunt
vinden.
Connected Home Monitor: helpt u bij de identificatie van beveiligingsproblemen van de router en verhoogt het
beveiligingsniveau bij verbinding met een vreemd netwerk.
Klik op Scan uw netwerk om handmatig een scan uit te voeren van het netwerk waarmee u op dit moment bent
verbonden.
U kunt uit de volgende opties kiezen:

113
Alles scannen
Alleen router scannen
Alleen apparaten scannen
WAARSCHUWING
Het is belangrijk om netwerkscans alleen uit te voeren op uw eigen thuisnetwerk. Als u dit doet op een netwerk
van iemand anders loopt u potentieel gevaar.
Wanneer de scan is voltooid, wordt een melding met een koppeling naar basisinformatie over het apparaat
weergegeven of kunt u in de tabel of sonarweergave dubbelklikken op het verdachte apparaat. Klik op
Probleemoplossing om de onlangs geblokkeerde communicatie te bekijken.
OPMERKING
Voor meer informatie over probleemoplossing voor Firewall klikt u hier.
4.6.8.1 Netwerkapparaat
Gedetailleerde informatie over het apparaat kunt u hier vinden, waaronder:
Apparaatnaam
Apparaattype
Laatst gedetecteerd
Netwerknaam
IP-adres
MAC-adres
Het potloodpictogram geeft aan dat u de apparaatnaam kunt aanpassen of het apparaattype kunt wijzigen.
Apparaat verwijderen: u kunt het eerder met uw netwerk verbonden apparaat verwijderen als dat apparaat niet
meer aanwezig is.
4.6.9 Webcam-beveiliging
Webcam-beveiliging laat toe om de processen en applicaties te zien die toegang hebben tot de webcamera van uw
computer. U ontvangt een bericht op uw scherm telkens wanneer een ongewenste applicatie toegang probeert te
krijgen tot uw webcam. U hebt de keuze tussen toelaten of blokkeren.

114
4.6.10 Hulpmiddelen in ESET Smart Security Premium
Het menu Meer hulpmiddelen bevat modules die het beheer van het programma vereenvoudigt en ervaren
gebruikers extra opties biedt.

115
Dit menu bevat de volgende hulpmiddelen:
Logbestanden
Beveiligingsrapport
Activiteit bekijken
Actieve processen (als ESET LiveGrid® is ingeschakeld in ESET Smart Security Premium)
Netwerkverbindingen (als Firewall is ingeschakeld in ESET Smart Security Premium)
ESET SysInspector
ESET SysRescue Live: hiermee wordt u naar de pagina voor ESET SysRescue Live omgeleid, waar u de ESET
SysRescue Live-image of Live CD/USB Creator voor Microsoft Windows kunt downloaden.
Planner
Systeemopruiming: een hulpmiddel waarmee u de computer kunt herstellen en bruikbaar kunt maken na
het wegnemen van de bedreiging.
Verzenden van voorbeeld voor analyse: hiermee kunt u een verdacht bestand naar het
onderzoekslaboratorium van ESET verzenden om het te laten analyseren. Het dialoogvenster wordt
weergegeven nadat u op de opties hebt geklikt die in dit gedeelte wordt beschreven.
Quarantaine
OPMERKING
ESET SysRescue is mogelijk niet beschikbaar voor Windows 8 in oudere versies van ESET-beveiligingsproducten.
In dat geval raden wij aan dat u een upgrade van uw product uitvoert of een ESET SysRescue-schijf maakt op een
andere versie van Microsoft Windows.
4.6.10.1 Logbestanden
Logbestanden bevatten informatie over belangrijke programmagebeurtenissen die zich hebben voorgedaan en
bieden een overzicht van gedetecteerde bedreigingen. Logboekregistratie is een essentieel onderdeel van
systeemanalyse, bedreigingsdetectie en probleemoplossing. Logboekregistratie wordt zonder gebruikersinteractie
op de achtergrond uitgevoerd. Informatie wordt vastgelegd op basis van de huidige detailinstellingen voor
logboekregistratie. U kunt tekstberichten en logbestanden rechtstreeks vanuit de ESET Smart Security Premium-
omgeving weergeven. U kunt de logbestanden ook archiveren.
Logbestanden zijn toegankelijk vanuit het hoofdprogrammavenster door te klikken op Hulpmiddelen > Meer
hulpmiddelen > Logbestanden. Selecteer het gewenste type logbestand in het vervolgkeuzemenu Logbestand. De
volgende logboeken zijn beschikbaar:
Gedetecteerde bedreigingen: logbestanden voor bedreigingen bevatten uitgebreide informatie over
infiltraties die door ESET Smart Security Premium zijn gedetecteerd. Hierbij gaat het om informatie zoals het
tijdstip van detectie, de naam van de infiltratie, de locatie, de actie die is uitgevoerd en de naam van de
gebruiker die ten tijde van detectie was aangemeld. Dubbelklik om de details van een logboekvermelding in
een apart venster weer te geven.
Gebeurtenissen: alle belangrijke acties die door ESET Smart Security Premium worden uitgevoerd, worden
opgenomen in de gebeurtenislogboeken. Het gebeurtenislogboek bevat informatie over gebeurtenissen en
fouten die in het programma zijn opgetreden. Met deze optie kunnen systeembeheerders en gebruikers
problemen oplossen. Vaak kunt u met de hier verschafte informatie problemen in het programma oplossen.
Computerscan: in dit venster worden de resultaten van alle voltooide handmatige of geplande scans
weergegeven. Elke regel correspondeert met één computercontrole. Dubbelklik op een vermelding om de
details van de desbetreffende scan weer te geven.

116
HIPS: bevat records van specifieke HIPS-regels die zijn gemarkeerd voor registratie. Het protocol geeft de
toepassing die de bewerking heeft geactiveerd, het resultaat (of de regel is toegestaan of verboden) en de
regelnaam weer.
Netwerkbeveiliging: in het netwerkbeveiligingslogboek staan alle aanvallen van buitenaf die door de firewall
zijn gedetecteerd. Hier vindt u informatie over elke aanval op uw computer. In de kolom Gebeurtenis worden
de gedetecteerde aanvallen weergegeven. In de kolom Bron vindt u meer informatie over de aanvaller. De
kolom Protocol bevat het communicatieprotocol dat voor de aanval is gebruikt. Door het firewalllogboek te
analyseren kunt u beter op tijd pogingen tot systeeminfiltratie detecteren om ongeoorloofde toegang tot het
systeem te voorkomen.
Gefilterde websites: Deze lijst is handig als u een lijst met websites wilt bekijken die zijn geblokkeerd door
Beveiliging van webtoegang of Ouderlijk toezicht. Elk logboek bevat de tijd, het URL-adres, de gebruiker en
de toepassing die een verbinding met een website heeft gemaakt.
Antispambeveiliging: hierin staan records die betrekking hebben op e-mailberichten die als spam zijn
gemarkeerd.
Ouderlijk toezicht: hiermee wordt weergegeven welke webpagina's worden geblokkeerd of toegestaan door
Ouderlijk toezicht. In de kolommen Type overeenkomst en Waarden overeenkomst ziet u hoe de filterregels
zijn toegepast.
Apparaatbeheer: hierin staan records van verwijderbare media of apparaten die op de computer zijn
aangesloten. Alleen apparaten met een apparaatbeheerregel worden opgenomen in het logbestand. Als de
regel niet overeenkomst met een aangesloten apparaat, wordt er geen logvermelding voor dat aangesloten
apparaat gemaakt. Hier kunt u ook details bekijken als het apparaattype, het serienummer, de leverancier en
de mediagrootte (indien beschikbaar).
Webcambeveiliging: bevat de gegevens betreffende toepassingen die zijn geblokkeerd door de
Webcambeveiliging.
Selecteer de inhouden van om het even welk logboek en druk op Ctrl + C om deze inhoud te kopiëren naar het
Klembord. Houd de Ctrl- en Shift-toets ingedrukt om meerdere records te selecteren.
Klik op Filteren om het venster Logbestanden filteren te openen, waarin u de filtercriteria kunt opgeven.
Klik met de rechtermuisknop op een record om het contextmenu te openen. De volgende opties zijn beschikbaar in
het contextmenu:
Weergeven: geeft uitvoerige informatie weer over het geselecteerde logbestand in een nieuw venster.
Filteren op dezelfde records: als u dit filter activeert, worden alleen records van hetzelfde type (diagnostiek,
waarschuwingen, ...) weergegeven.
Filter/Zoeken: nadat u op deze optie hebt geklikt, kunt u in het venster Zoeken in logboek filtercriteria voor
specifieke logboekvermeldingen opgeven.
Filter inschakelen: hiermee worden filterinstellingen geactiveerd.
Filter uitschakelen: hiermee heft u alle filterinstellingen op (zoals hierboven beschreven).
Kopiëren/Alles kopiëren: hiermee kopieert u informatie over alle vermeldingen in het venster.
Verwijderen/Alles verwijderen: hiermee verwijdert u de geselecteerde record(s) of alle records die worden
weergegeven. Voor deze actie zijn beheerdersrechten vereist.
Exporteren...: hiermee wordt informatie over de record(s) in XML-indeling geëxporteerd.
Alles exporteren...: hiermee wordt informatie over de record(s) in XML-indeling geëxporteerd.
Logboek doorbladeren: laat deze optie ingeschakeld om automatisch door oude logboeken te bladeren en
actieve logboeken te bekijken in het venster Logbestanden.

117
4.6.10.1.1 Logbestanden
De configuratie van logbestanden voor ESET Smart Security Premium is toegankelijk vanuit het
hoofdprogrammavenster. Klik op Instellingen > Volledige structuur voor geavanceerde instellingen... >
Hulpmiddelen > Logbestanden. In het gedeelte Logbestanden wordt gedefinieerd hoe de logbestanden worden
beheerd. Oudere logbestanden worden automatisch verwijderd om ruimte op de vaste schijf te besparen. U kunt
de volgende opties opgeven voor logbestanden:
Minimaal detailniveau voor logboekregistratie: het minimale detailniveau waarmee gebeurtenissen worden
geregistreerd.
Diagnostisch: hiermee wordt informatie geregistreerd die nodig is om het programma en alle bovenstaande
archieven af te stemmen.
Informatief: registreert informatieve berichten, waaronder berichten over geslaagde updates, plus alle
bovenstaande archieven.
Waarschuwingen: hiermee worden kritieke fouten en waarschuwingsberichten geregistreerd.
Fouten: fouten als 'Fout bij downloaden van bestand' en kritieke fouten worden geregistreerd.
Kritiek: hiermee worden alleen kritieke fouten geregistreerd (zoals fouten bij het starten van
antivirusbeveiliging, Firewall, enzovoort).
Vermeldingen in logbestanden die ouder zijn dan het aantal dagen dat is opgegeven bij Records automatisch
verwijderen na (dagen) worden automatisch verwijderd.
Logbestanden automatisch optimaliseren: als deze optie is ingeschakeld, worden logbestanden automatisch
gedefragmenteerd als het percentage hoger is dan is opgegeven voor de waarde Overschrijdingspercentage aantal
ongebruikte records (%).
Klik op Optimaliseren om de defragmentatie van de logbestanden te starten. Alle lege logboekvermeldingen
worden hierbij verwijderd, zodat de prestaties verbeteren en de verwerking van logbestanden wordt verbeterd.
Deze verbetering wordt vooral waargenomen als de logbestanden een groot aantal vermeldingen bevatten.
Tekstprotocol inschakelen schakelt de opslag van logboeken in een andere bestandsindeling in dan voor
Logbestanden gebeurt:
Doelmap: de map waarin logbestanden worden opgeslagen (alleen van toepassing op Tekst/CSV). Elke
logboeksectie heeft een eigen bestand met een vooraf gedefinieerde bestandsnaam (bijvoorbeeld virlog.txt voor
het gedeelte Gedetecteerde bedreigingen, als u platte tekst gebruikt om logboeken op te slaan).
Type: als u de bestandsindeling Tekst selecteert, worden logboeken opgeslagen in een tekstbestand en gegevens
worden door tabs gescheiden. Hetzelfde geldt voor de door komma's gescheiden CSV-bestandsindeling. Als u
Gebeurtenis kiest, worden logboeken opgeslagen in het Windows-gebeurtenislogboek (kan worden bekeken via
Logboeken in het Configuratiescherm) in plaats van in het bestand.
Alle logbestanden verwijderen: hiermee worden alle opgeslagen logboeken gewist die zijn geselecteerd in het
vervolgkeuzemenu Type. Een melding over het succesvol verwijderen van de logbestanden wordt weergegeven.
OPMERKING
Om problemen sneller te kunnen oplossen kan het zijn dat u door ESET wordt gevraagd logboeken van uw
computer te verzenden. ESET Log Collector maakt het verzamelen van de benodigde informatie gemakkelijker.
Ga naar het artikel in onze ESET-kennisbank voor meer informatie over ESET Log Collector.

118
4.6.10.2 Actieve processen
Met Actieve processen worden de programma's en processen weergegeven die worden uitgevoerd op uw computer
en wordt ESET direct en continu op de hoogte gehouden van nieuwe infiltraties. ESET Smart Security Premium biedt
gedetailleerde informatie over actieve processen om gebruikers te beschermen met ThreatSense-technologie.
Proces: imagenaam van het programma of proces dat momenteel op de computer wordt uitgevoerd. U kunt ook het
Windows Taakbeheer gebruiken als u alle actieve processen op uw computer wilt zien. U opent de Task Manager
door met de rechtermuisknop te klikken op een leeg gebied op de taakbalk en vervolgens te klikken op Task
Manager, of u kunt op Ctrl+Shift+Esc drukken op uw toetsenbord.
Risiconiveau: in de meeste gevallen worden in ESET Smart Security Premium met behulp van de ThreatSense-
technologie risiconiveaus toegewezen aan objecten (bestanden, processen, registersleutels, enzovoort) op basis
van een reeks heuristische regels die de kenmerken van elk object onderzoeken en vervolgens een wegingsfactor
voor schadelijke activiteiten toekennen. Op basis van deze heuristiek krijgen objecten een risiconiveau
toegewezen in het bereik 1 - Goed (groen) tot 9 - Riskant (rood).
OPMERKING
Bekende toepassingen die Goed (groen) zijn gemarkeerd zijn zeker schoon (staan op de witte lijst) en worden
uitgesloten van scannen.
PID : het procesidentificatienummer kan in verschillende aangeroepen functies worden gebruikt als parameter,
bijvoorbeeld om de prioriteit van het proces te bepalen.
Aantal gebruikers: het aantal gebruikers dat een bepaalde toepassing gebruikt. Deze informatie wordt verzameld
door de ThreatSense-technologie.
Tijdstip van detectie: de periode sinds de toepassing is ontdekt door de ThreatSense-technologie.
OPMERKING
Aan applicatie die gemarkeerd is als Onbekend (orange) is niet noodzakelijk kwaadwillende software.
Gewoonlijk is het een nieuwere toepassing. Als u niet zeker weet of het bestand veilig is, kunt u het bestand

119
verzenden voor analyse aan het onderzoekslab van ESET. Als het bestand een schadelijke toepassing blijkt te
zijn, wordt de detectie ervan in een van de volgende updates opgenomen.
Naam van toepassing: de naam van een programma of proces.
Openen in een nieuw venster: de informatie van Actieve processen wordt in een nieuw venster weergegeven.
Klik op een applicatie of de volgende gegevens van die applicatie op het scherm weer te geven:
Pad: de locatie van een toepassing op de computer.
Grootte: bestandsgrootte in B (bytes).
Beschrijving: bestandskenmerken op basis van de beschrijving van het besturingssysteem.
Bedrijf: de naam van de leverancier of het toepassingsproces.
Versie: informatie van de uitgever van de toepassing.
Product: de toepassingsnaam en/of bedrijfsnaam.
Gemaakt/gewijzigd op: datum en tijd van aanmaak of wijziging.
OPMERKING
U kunt de reputatie van een bestand dat niet optreedt voor de uitvoering van programma's en processen ook
controleren. Hiervoor klikt u met de rechtermuisknop op het bestand en selecteert u Geavanceerde opties >
Bestandsreputatie controleren.
4.6.10.3 Beveiligingsrapport
Deze functie geeft een overzicht van de statistieken voor de volgende categorieën:
Webpagina's geblokkeerd: geeft het aantal geblokkeerde webpagina's weer (potentieel ongewenste
toepassingen die als URL op de zwarte lijst zijn geplaatst, phishing, gehackte router, IP-adres of certificaat).
Geïnfecteerde e-mailobjecten gedetecteerd: geeft het aantal geïnfecteerde e-mailobjecten weer dat is
gedetecteerd.
Webpagina's in Ouderlijk toezicht geblokkeerd: geeft het aantal in Ouderlijk toezicht geblokkeerde webpagina's
weer.
Potentieel ongewenste toepassing gedetecteerd: geeft het aantal gedetecteerde, potentieel ongewenste
toepassingen weer.
Spamberichten gedetecteerd: geeft het aantal gedetecteerde spamberichten weer.
Toegang tot webcamera geblokkeerd: geeft het aantal geblokkeerde webcamtoegangen weer.
Toegang tot internetbankieren beveiligd: geeft het aantal beveiligde toegangen tot internetbankieren weer.
Documenten gecontroleerd: geeft het aantal gescande documentobjecten weer.
Apps gecontroleerd: geeft het aantal gescande uitvoerbare objecten weer.
Overige objecten gecontroleerd: geeft het aantal overige gescande objecten weer.
Webpagina-objecten gecontroleerd: geeft het aantal gescande webpagina-objecten weer.
E-mailobjecten gecontroleerd: geeft het aantal gescande e-mailobjecten weer.
De volgorde van deze categorieën wordt gebaseerd op de numerieke waarde, van het hoogste tot het laagste
aantal. Categorieën met waarde nul worden niet weergegeven. Klik op Meer weergeven om verborgen categorieën
uit te vouwen.
Onder de categorieën ziet u de feitelijke virussituatie met een wereldkaart. De aanwezigheid van een virus in elk
land wordt aangegeven met een kleur (hoe donker de kleur, hoe hoger het aantal). Landen zonder gegevens zijn
grijs. Laat de muisaanwijzer rusten op een land om gegevens voor het geselecteerde land weer te geven. Als u een
bepaald werelddeel selecteert, wordt er automatisch op ingezoomd.
In het laatste gedeelte van het beveiligingsrapport kunt u de volgende functies activeren:

120
Wachtwoordmanager
Secure Data
Ouderlijk toezicht
Antidiefstal
Nadat een functie is ingeschakeld, wordt deze niet meer als niet-functioneel weergegeven in het
beveiligingsrapport.
Klik op het tandrad rechtsboven om Beveiligingsrapportmelden in/uitschakelen te selecteren of selecteer of de
gegevens van de afgelopen 30 dagen of sinds het product is geactiveerd, moeten worden weergegeven. Als ESET
Smart Security Premium minder dan 30 dagen is geïnstalleerd, kan alleen het aantal dagen vanaf de installatie
worden geselecteerd. Standaard is een periode van 30 dagen ingesteld.
Met Gegevens opnieuw instellen worden alle statistieken gewist en worden de bestaande gegevens voor het
beveiligingsrapport verwijderd. Deze actie moet worden bevestigd, behalve als u de optie Vragen alvorens
statistieken opnieuw in te stellen hebt gedeselecteerd in Geavanceerde instellingen > Gebruikersinterface >
Waarschuwingen en meldingen > Bevestigingsberichten.
4.6.10.4 Activiteit bekijken
Als u de huidige activiteiten in het bestandssysteem in een grafiek wilt weergeven, klikt u op Hulpmiddelen > Meer
hulpmiddelen > Activiteit bekijken. Onder aan de grafiek staat een tijdlijn waarop in real-time de activiteiten in het
bestandssysteem voor de geselecteerde periode worden weergegeven. U wijzigt de tijdperiode door een selectie
te maken in het vervolgkeuzemenu Vernieuwingssnelheid.

121
De volgende opties zijn beschikbaar:
Verhogen met: 1 seconde: de grafiek wordt elke seconde vernieuwd en de periode bestaat uit de laatste 10
minuten.
Verhogen met: 1 minuut (afgelopen 24 uur): de grafiek wordt elke minuut vernieuwd en de periode bestaat uit
de afgelopen 24 uur.
Verhogen met: 1 uur (afgelopen maand): de grafiek wordt elk uur vernieuwd en de periode bestaat uit de
afgelopen maand.
Verhogen met: 1 uur (geselecteerde maand): de grafiek wordt elk uur vernieuwd en de periode bestaat uit de
afgelopen X geselecteerde maanden.
De verticale as van de grafiek met activiteit bestandssysteem vertegenwoordigt gelezen gegevens (blauw) en
geschreven gegevens (rood). Beide waarden worden weergegeven in kB (kilobytes)/MB/GB. Als u de muisaanwijzer
over de hoeveelheid gelezen of weggeschreven gegevens beweegt in de legenda onder de grafiek, bevat de grafiek
alleen gegevens voor dat type activiteit.
U kunt ook Netwerkactiviteit selecteren in het vervolgkeuzemenu. De activiteiten van het bestandssysteem en de
activiteiten van het netwerk worden op dezelfde manier weergegeven in de grafiek, met als enige verschil dat voor
de netwerkactiviteiten de hoeveelheid ontvangen gegevens (rood) en verzonden gegevens (blauw) wordt
weergegeven.
4.6.10.5 Netwerkverbindingen
De sectie Netwerkverbindingen bevat een lijst met actieve verbindingen en verbindingen die in behandeling zijn.
Dit overzicht dient als hulpmiddel bij het beheren van alle toepassingen die uitgaande verbindingen tot stand
brengen.
Op de eerste regel worden de naam van de toepassing en de gegevensoverdrachtsnelheid weergegeven. Als u wilt
zien welke verbindingen door de toepassing zijn gemaakt (samen met meer gedetailleerde informatie), klikt u op +.
Kolommen
Toepassing/Lokaal IP-adres: naam van toepassing, lokale IP-adressen en communicatiepoorten.

122
Extern IP-adres: het IP-adres en poortnummer van de specifieke externe computer.
Protocol: het gebruikte overdrachtprotocol.
Snelheid in/Snelheid uit: de huidige snelheid van uitgaande en inkomende gegevens.
Verzonden/Ontvangen: de hoeveelheid gegevens die via de verbinding is uitgewisseld.
Details weergeven: kies deze optie om gedetailleerde informatie over de geselecteerde verbinding weer te
geven.
Klik met de rechtermuisknop op een verbinding om aanvullende opties weer te geven, zoals:
Hostnamen omzetten: alle netwerkadressen worden zo mogelijk in DNS-indeling weergegeven, niet in de
numerieke IP-adresindeling.
Alleen TCP-verbindingen weergeven: de lijst bevat alleen verbindingen die tot het TCP-protocolpakket behoren.
Luisterende verbindingen weergeven: selecteer deze optie om alleen verbindingen weer te geven waarvoor wel
een poort is geopend en op verbinding wordt gewacht, maar waar nog geen sprake is van communicatie.
Verbindingen in de computer weergeven: als u deze optie selecteert, worden alleen verbindingen met de lokale
host weergegeven, d.w.z. verbindingen waar de externe zijde een lokaal systeem is.
Vernieuwingssnelheid: kies de frequentie waarmee de actieve verbindingen moeten worden vernieuwd.
Nu vernieuwen: hiermee wordt het venster Netwerkverbindingen opnieuw geladen.
De volgende opties zijn alleen beschikbaar nadat er is geklikt op een toepassing of proces, niet een actieve
verbinding:
Tijdelijk communicatie voor proces weigeren: hiermee worden actieve verbindingen voor de opgegeven
toepassing geweigerd. Als er een nieuwe verbinding tot stand wordt gebracht, gebruikt de firewall een vooraf
gedefinieerde regel. Zie het gedeelte Regels configureren en gebruiken voor een beschrijving van de
instellingen.
Tijdelijk communicatie voor proces toestaan: hiermee worden actieve verbindingen voor de opgegeven
toepassing toegestaan. Als er een nieuwe verbinding tot stand wordt gebracht, gebruikt de firewall een vooraf
gedefinieerde regel. Zie het gedeelte Regels configureren en gebruiken voor een beschrijving van de
instellingen.
4.6.10.6 ESET SysInspector
ESET SysInspector is een toepassing die uw computer grondig inspecteert, gedetailleerde informatie verzamelt over
systeemonderdelen zoals stuurprogramma's en toepassingen, netwerkverbindingen of belangrijke
registervermeldingen, en die het risico van elk onderdeel beoordeelt. Deze gegevens kunnen u helpen de oorzaak
van afwijkend systeemgedrag vast te stellen. Problemen kunnen worden veroorzaakt door een malware-infectie,
maar ook door incompatibele software of hardware.
Het venster SysInspector bevat de volgende informatie over gemaakte logbestanden:
Tijd: het tijdstip waarop het logbestand is gemaakt.
Opmerking: een korte opmerking.
Gebruiker: de naam van de gebruiker die het logbestand heeft gemaakt.
Status: de status van het gemaakte logbestand.

123
De volgende acties zijn beschikbaar:
Weergeven: hiermee wordt een gemaakt logbestand geopend. U kunt ook met de rechtermuisknop op een
bepaald logbestand klikken en Weergeven in het contextmenu selecteren.
Vergelijken: hiermee worden twee bestaande logbestanden vergeleken.
Maken...: hiermee wordt een nieuw logbestand gemaakt. Wacht tot ESET SysInspector is voltooid (logstatus
wordt weergegeven als Gemaakt) alvorens te proberen het logbestand te openen.
Verwijderen: hiermee wordt het geselecteerde logbestand/de geselecteerde logbestanden uit de lijst
verwijderd.
De volgende items zijn beschikbaar in het contextmenu als een of meer logbestanden zijn geselecteerd:
Weergeven: hiermee wordt het geselecteerde logbestand geopend in ESET SysInspector (net zoals wanneer u
dubbelklikt op een logbestand).
Vergelijken: hiermee worden twee bestaande logbestanden vergeleken.
Maken...: hiermee wordt een nieuw logbestand gemaakt. Wacht tot ESET SysInspector is voltooid (logstatus
wordt weergegeven als Gemaakt) alvorens te proberen het logbestand te openen.
Verwijderen: hiermee wordt het geselecteerde logbestand/de geselecteerde logbestanden uit de lijst
verwijderd.
Alles verwijderen: hiermee kunt u alle logbestanden verwijderen.
Exporteren...: hiermee wordt het logbestand geëxporteerd als een .xml-bestand of als ingepakt .xml-bestand.
4.6.10.7 Planner
Planner beheert en start geplande taken met vooraf gedefinieerde configuratie en eigenschappen.
De Planner kan worden geopend in het hoofdprogrammavenster van ESET Smart Security Premium door te klikken
op Hulpmiddelen > Meer hulpmiddelen > Planner. De Planner bevat een lijst met alle geplande taken en hun
configuratie-eigenschappen, zoals de vooraf gedefinieerde datum en tijd en het gebruikte scanprofiel.
Met de planner kunt u de volgende taken plannen: update van de modules, scantaak, controle van de
opstartbestanden van het systeem en onderhoud van logbestanden. U kunt taken rechtstreeks in het
hoofdprogrammavenster van Planner toevoegen of verwijderen (door onderaan op de knop Taak toevoegen of
Verwijderen te klikken). U kunt de lijst met geplande taken ongedaan maken, de standaardinstellingen herstellen
en alle wijzigingen ongedaan maken door te klikken op Standaard. Klik met de rechtermuisknop op een
willekeurige plaats in het venster Planner om de volgende bewerkingen uit te voeren: gedetailleerde informatie
weergeven, de taak direct uitvoeren, een nieuwe taak toevoegen of een bestaande taak verwijderen. Gebruik de
selectievakjes naast elke vermelding om de taken te activeren of deactiveren.
Standaard worden de volgende geplande taken in de Planner weergegeven:
Logbestanden onderhouden
Regelmatige automatische update
Automatisch update uitvoeren na inbelverbinding
Automatisch update uitvoeren na aanmelding gebruiker
Regelmatig controleren op recentste productversie (zie Updatemodus)
Automatische bestandscontrole bij opstarten (na aanmelding van de gebruiker)
Automatische bestandscontrole bij opstarten (na succesvolle update van de detectie-engine)
U kunt de configuratie van een bestaande geplande taak (zowel standaard als door de gebruiker gedefinieerd)
bewerken door met de rechtermuisknop op de taak te klikken en op Bewerken... te klikken of door de taak die u
wilt wijzigen te selecteren en op Bewerken te klikken.
Een nieuwe taak toevoegen
1. Klik onder in het venster op Taak toevoegen.
2. Geef de taak een naam.

124
3. Selecteer de gewenste taak in het vervolgkeuzemenu:
Externe toepassing uitvoeren: hiermee kunt u de uitvoering van een externe toepassing plannen.
Logbestanden onderhouden: logbestanden bevatten tevens restanten van verwijderde records. Met deze taak
optimaliseert u regelmatig records in logbestanden om effectief te werken.
Opstartbestanden van systeem controleren: hiermee worden bestanden gecontroleerd die tijdens het opstarten
of aanmelden mogen worden uitgevoerd.
Momentopname van computerstatus maken: hiermee maakt u met ESET SysInspector een momentopname van
de computer, waarbij gedetailleerde informatie over systeemonderdelen (zoals stuurprogramma's en
toepassingen) wordt verzameld en het risiconiveau van elk onderdeel wordt beoordeeld.
Computerscan op aanvraag: hiermee wordt een scan uitgevoerd op bestanden en mappen op uw computer.
Bijwerken: hiermee wordt een updatetaak gepland door de modules bij te werken.
4. Zet de schakelaar Ingeschakeld aan als u de taak wilt activeren (u kunt dit later doen door het selectievakje in/uit
te schakelen in de lijst met geplande taken), klik op Volgende en selecteer een van de tijdopties:
Eenmaal: de taak wordt op de vooraf ingestelde datum en tijd uitgevoerd.
Herhaaldelijk: de taak wordt met het opgegeven tijdsinterval uitgevoerd.
Dagelijks: de taak wordt elke dag op het opgegeven tijdstip uitgevoerd.
Wekelijks: de taak wordt op de geselecteerde dag en tijd uitgevoerd.
Bij gebeurtenis: de taak wordt uitgevoerd wanneer een opgegeven gebeurtenis plaatsvindt.
5. Selecteer Taak overslaan indien op batterijvoeding om het gebruik van systeembronnen te minimaliseren als
een laptop op batterijvoeding werkt. De taak wordt uitgevoerd op de datum en tijd die is opgegeven in de
velden van Taakuitvoering. Als de taak niet op het vooraf ingestelde tijdstip kon worden verricht, kunt u
opgeven wanneer de taak opnieuw moet worden uitgevoerd:
Op het volgende geplande tijdstip
Zo spoedig mogelijk
Meteen, als tijd sinds vorige keer uitvoeren groter is dan een opgegeven waarde (het interval kan worden
opgegeven bij het vak Tijd sinds vorige keer uitvoeren)
U kunt een geplande taak bekijken door er met de rechtermuisknop op te klikken en op Taakdetails weergeven te
klikken.

125
4.6.10.8 Systeemopruiming
Systeemopruiming is een hulpmiddel waarmee u de computer kunt herstellen en bruikbaar kunt maken na het
wegnemen van de bedreiging. Malware kan systeemfuncties uitschakelen zoals Register-editor, Taakbeheer of
Windows Updates. Met Systeemopruiming worden de standaardinstellingen voor een bepaald systeem met één
klik hersteld.
Systeemopruiming meldt problemen uit vijf instellingencategorieën:
Beveiligingsinstellingen: wijzigingen in instellingen die een verhoogd beveiligingsrisico kunnen betekenen van
uw computer, zoals Windows Update
Systeeminstellingen: wijzigingen in systeeminstellingen die het gedrag van uw computer kunnen veranderen,
zoals bestandskoppelingen
Vormgeving van uw systeem: instellingen die gevolgen hebben voor hoe uw systeem eruit ziet, zoals uw
bureaubladachtergrond
Uitgeschakelde functies: belangrijke functies en toepassingen die mogelijk uitgeschakeld zijn
Windows Systeemherstel: instellingen voor de functie Windows Systeemherstel, waarmee u uw systeem kunt
terugzetten naar een eerdere status
Systeemopruiming kan worden verzocht:
wanneer een bedreiging is gevonden
wanneer een gebruiker klikt op Opnieuw instellen
U kunt de wijzigingen bekijken en de instellingen terugzetten (indien van toepassing).
OPMERKING
Alleen een gebruiker met beheerdersrechten kan handelingen uitvoeren in Systeemopruiming.
4.6.10.9 ESET SysRescue
ESET SysRescue is een hulpprogramma waarmee u een opstartbare schijf kunt maken met daarop een van de ESET
Security-oplossingen. Dit kan ESET NOD32 Antivirus, ESET Internet Security, ESET Smart Security, ESET Smart Security
Premium zijn, of bepaalde servergerichte producten. Het belangrijkste voordeel van ESET SysRescue is dat de ESET
Security-oplossing onafhankelijk van het besturingssysteem kan worden uitgevoerd, maar het programma heeft
toch rechtstreeks toegang heeft tot de schijf en het bestandssysteem. Hierdoor is het mogelijk infiltraties te
verwijderen die anders niet kunnen worden verwijderd, bijvoorbeeld omdat het besturingssysteem actief is.
4.6.10.10 Op de cloud gebaseerde beveiliging
ESET LiveGrid® (gebouwd op het geavanceerde ThreatSense.Net -systeem voor vroegtijdige waarschuwing van
ESET) maakt gebruik van gegevens die ESET-gebruikers over de hele wereld hebben ingediend, en verzendt dit naar
het onderzoekslaboratorium van ESET. Door het aanleveren van verdachte voorbeelden en metadata, geeft ESET
LiveGrid® ons de mogelijkheid direct te voldoen aan de behoeften van onze klanten en ESET alert te houden op de
nieuwste bedreigingen. Lees meer over ESET LiveGrid® in de woordenlijst.
Een gebruiker kan de reputatie van actieve processen en bestanden rechtstreeks in de programma-interface of het
contextmenu bekijken met extra informatie van ESET LiveGrid®. Er zijn twee opties:
1. U kunt ervoor kiezen om ESET LiveGrid® niet in te schakelen. De software blijft op dezelfde wijze
functioneren, maar in bepaalde gevallen reageert ESET Smart Security Premium mogelijk sneller op nieuwe
bedreigingen dan een update van de detectie-engine wanneer ESET Live Grid is ingeschakeld.
2. U kunt ESET LiveGrid® zodanig configureren dat er anonieme informatie over nieuwe bedreigingen en de
locatie waar de nieuwe bedreigingscode voorkomt worden verzonden. Dit bestand kan voor gedetailleerde
analyse naar ESET worden verzonden. Na bestudering van deze bedreigingen kan ESET haar voorzieningen
voor bedreigingsdetectie vervolgens bijwerken.

126
ESET LiveGrid® verzamelt informatie over uw computer met betrekking tot nieuw gedetecteerde bedreigingen.
Deze informatie kan een voorbeeld of kopie bevatten van het bestand waarin de bedreiging voorkwam, het pad
naar dat bestand, de bestandsnaam, de datum en tijd, het proces waarbij de bedreiging plaatsvond op uw computer
en informatie over het besturingssysteem van uw computer.
Standaard wordt ESET Smart Security Premium zodanig geconfigureerd dat verdachte bestanden voor
gedetailleerde analyse naar het viruslaboratorium van ESET worden verzonden. Bestanden met bepaalde extensies,
zoals .doc of .xls, worden altijd uitgesloten. U kunt ook andere extensies toevoegen als er bepaalde bestanden zijn
die u of uw organisatie niet wil verzenden.
Het ESET LiveGrid®-reputatiesysteem stelt witte en zwarte lijsten in de cloud op. U krijgt toegang tot de instellingen
van ESET LiveGrid® door op F5 te drukken om naar Geavanceerde instellingen te gaan en vervolgens Hulpmiddelen >
ESET LiveGrid® uit te vouwen.
ESET LiveGrid®-reputatiesysteem inschakelen (aanbevolen): het ESET LiveGrid®-reputatiesysteem verbetert de
efficiëntie van de antimalwareoplossingen van ESET door gescande bestanden te vergelijken met een database in
de cloud met items die op een witte of zwarte lijst zijn geplaatst.
ESET LiveGrid®-feedbacksysteem inschakelen: hiermee worden gegevens voor verdere analyse naar het ESET-
onderzoekslab verzonden.
Crashrapporten en diagnostische gegevens verzenden: hiermee worden gegevens verzonden zoals crashrapporten
en geheugendumps van modules.
Anonieme statistieken verzenden: hiermee kunt u toestaan dat ESET informatie verzamelt over nieuw ontdekte
bedreigingen, zoals de naam van de bedreiging, datum en tijd van detectie, detectiemethode en bijbehorende
metagegevens, productversie en configuratie, met inbegrip van informatie over uw systeem.
E-mailadres van contactpersoon (optioneel): u kunt uw e-mailadres meesturen met verdachte bestanden. Dit kan
dan worden gebruikt om contact met u op te nemen als meer informatie nodig is voor de analyse. U zult geen
antwoord van ESET ontvangen, tenzij nadere informatie nodig is voor de analyse.
Verzenden van voorbeelden
Geïnfecteerde voorbeelden verzenden: hiermee verzendt u alle geïnfecteerde voorbeelden voor analyse naar ESET
om detectie in de toekomst te verbeteren. De volgende opties zijn beschikbaar:
Alle geïnfecteerde voorbeelden
Alle voorbeelden behalve documenten
Niet indienen
Verdachte voorbeelden verzenden
Uitvoerbare bestanden: waaronder bestanden zoals .exe, .dll, .sys.
Archieven: waaronder bestandstypen zoals .zip, .rar, .7z, .arch, .arj, .bzip, .gzip, .ace, .arc, .cab.
Scripts: waaronder bestandstypen zoals .bat, .cmd, .hta, .js, .vbs, .ps1.
Overige: waaronder bestandstypen zoals .jar, .reg, .msi, .sfw, .lnk.
Mogelijk ongewenste e-mails: hiermee kunnen mogelijke spamonderdelen of ongewenste e-mails in hun
geheel met bijlage en al voor analyse worden verzonden naar ESET. Als u deze optie inschakelt, wordt de
algehele detectie van ongewenste e-mail verbeterd, waaronder de detectie voor toekomstige ongewenste e-
mails voor u.
Documenten: waaronder Microsoft Office-documenten en PDF's met actieve inhoud.
Uitsluitingen: met het uitsluitingsfilter kunt u bepaalde bestanden/mappen uitsluiten van verzending (het kan
bijvoorbeeld nuttig zijn om bestanden uit te sluiten die vertrouwelijke informatie bevatten, zoals documenten en
spreadsheets). De weergegeven bestanden worden nooit voor analyse naar het lab van ESET verzonden, zelfs niet
als de bestanden een verdachte code bevatten. Veelgebruikte bestandstypen (.doc, enz.) worden standaard
uitgesloten. U kunt als u dat wilt opties toevoegen aan de lijst met uitgesloten bestanden.
Als u ESET LiveGrid® eerder hebt gebruikt en hebt uitgeschakeld, kunnen er nog gegevenspakketten zijn die moeten
worden verzonden. Zelfs na deactivering worden dergelijke pakketten naar ESET verzonden. Nadat alle huidige
informatie is verzonden, worden er geen nieuwe pakketten meer gemaakt.

127
4.6.10.10.1 Verdachte bestanden
Als u een verdacht bestand aantreft, kunt u dit naar het onderzoekslaboratorium van ESET versturen voor analyse.
Als het bestand een schadelijke toepassing is, wordt de detectie ervan toegevoegd aan de volgende update van de
viruskenmerken.
Uitsluitingsfilter: met het uitsluitingsfilter kunt u bepaalde bestanden of mappen uitsluiten van verzending. De
weergegeven bestanden worden nooit voor analyse naar het onderzoekslaboratorium van ESET verstuurd, zelfs niet
als de bestanden een verdachte code bevatten. Het kan bijvoorbeeld handig zijn bestanden uit te sluiten die
mogelijk vertrouwelijke informatie bevatten, zoals documenten of spreadsheets. Veelgebruikte bestandstypen
(DOC enz.) worden standaard uitgesloten. U kunt als u dat wilt opties toevoegen aan de lijst met uitgesloten
bestanden.
E-mailadres van contactpersoon (optioneel): u kunt uw e-mailadres meesturen met verdachte bestanden. Dit kan
dan worden gebruikt om contact met u op te nemen als meer informatie nodig is voor de analyse. U zult geen
antwoord van ESET ontvangen, tenzij nadere informatie nodig is voor de analyse.
Selecteer Logboekregistratie inschakelen om een gebeurtenislogboek bij te houden van de verzending van
bestanden en statistische gegevens. Hierdoor worden gebeurtenissen in het gebeurtenislogboek weggeschreven
als er bestanden of statistische gegevens worden verzonden.
4.6.10.11 Quarantaine
De hoofdfunctie van de quarantaine is het veilig opslaan van geïnfecteerde bestanden. Bestanden moeten in
quarantaine worden geplaatst als ze niet kunnen worden opgeschoond, als het niet veilig of raadzaam is om ze te
verwijderen of als ze onterecht door ESET Smart Security Premium zijn gedetecteerd.
U kunt elk bestand in quarantaine plaatsen. Dit is raadzaam als een bestand zich verdacht gedraagt maar niet wordt
gedetecteerd door de antivirusscanner. In quarantaine geplaatste bestanden kunnen voor analyse naar het
onderzoekslaboratorium van ESET worden verzonden.

128
Bestanden die zijn opgeslagen in de quarantainemap, kunnen worden bekeken in een tabel waarin de datum en het
tijdstip van de quarantaine, het pad naar de oorspronkelijke locatie van het geïnfecteerde bestand, de grootte van
het bestand in bytes, de reden (bijvoorbeeld object toegevoegd door gebruiker) en het aantal bedreigingen
(bijvoorbeeld of het een archief is dat meerdere infiltraties bevat) worden weergegeven.
Bestanden in quarantaine plaatsen
ESET Smart Security Premium plaatst verwijderde bestanden automatisch in quarantaine (als u deze optie niet hebt
geannuleerd in het waarschuwingsvenster). Desgewenst kunt u elk willekeurig verdacht bestand handmatig in
quarantaine plaatsen door op de knop Quarantaine... te klikken. In dat geval wordt het oorspronkelijke bestand niet
verwijderd van de oorspronkelijke locatie. Het contextmenu kan ook hiervoor worden gebruikt. Klik met de
rechtermuisknop in het venster Quarantaine en selecteer Quarantaine....
Herstellen vanuit quarantaine
Bestanden die in quarantaine zijn geplaatst, kunnen ook worden teruggezet op de oorspronkelijke locatie. Gebruik
hiervoor de functie Herstellen. Deze functie is beschikbaar in het contextmenu, dat u weergeeft door in het venster
Quarantaine met de rechtermuisknop op een bepaald bestand te klikken. Als een bestand is gemarkeerd als een
toepassing die potentieel ongewenst is, is de optie Herstellen en uitsluiten van scannen beschikbaar. Zie de
woordenlijst voor meer informatie over dit type toepassing. Het contextmenu biedt tevens de optie Herstellen
naar..., waarmee u bestanden kunt terugzetten naar een andere locatie dan waarvan deze zijn verwijderd.
Verwijderen uit quarantaine: klik met de rechtermuisknop op een item en selecteer Verwijderen uit quarantaine of
selecteer het item dat u wilt verwijderen en druk op de toets Del op uw toetsenbord. Ook kunt u meerdere items
selecteren en deze tegelijk verwijderen.
OPMERKING
als het programma per ongeluk een onschadelijk bestand in quarantaine heeft geplaatst, sluit u het bestand uit
van scannen nadat u het hebt teruggezet en stuurt u het naar de klantenservice van ESET.
Een bestand verzenden vanuit quarantaine
Als u een verdacht bestand in quarantaine hebt geplaatst dat niet is gedetecteerd door het programma, of als een
bestand ten onrechte als geïnfecteerd is beoordeeld (bijvoorbeeld door heuristische analyse van de code) en
vervolgens in quarantaine is geplaatst, stuur het bestand dan naar het viruslaboratorium van ESET. U kunt een
bestand verzenden vanuit quarantaine door met de rechtermuisknop erop te klikken en Opsturen voor analyse te
selecteren in het contextmenu.
4.6.10.12 Proxyserver
In grote LAN-netwerken kan de communicatie tussen uw computer en internet door een proxyserver tot stand
worden gebracht. Bij een dergelijke configuratie moeten de volgende instellingen worden opgegeven. Als u dit niet
doet, kunnen geen automatische updates voor het programma worden uitgevoerd. In ESET Smart Security Premium
zijn de instellingen van de proxyserver beschikbaar in twee verschillende delen in de structuur van Geavanceerde
instellingen.
Ten eerste kunt u de instellingen van de proxyserver configureren in Geavanceerde instellingen onder
Hulpmiddelen > Proxyserver. Als u de proxyserver op dit niveau opgeeft, worden algemene instellingen voor de
proxyserver gedefinieerd voor heel ESET Smart Security Premium. Parameters hier worden gebruikt door alle
modules die verbinding met internet vereisen.
U kunt instellingen voor de proxyserver op dit niveau opgeven door Proxyserver gebruiken te selecteren en
vervolgens het adres van de proxyserver in te voeren in het veld Proxyserver, samen met het poortnummer van de
proxyserver.
Als voor communicatie met de proxyserver verificatie is vereist, selecteert u Proxyserver vereist verificatie en geeft
u een geldige gebruikersnaam en een geldig wachtwoord op in de desbetreffende velden. Klik op Detecteren om
proxyserverinstellingen automatisch te detecteren en in te vullen. De in Internet Explorer opgegeven parameters
worden gekopieerd.

129
OPMERKING
U moet uw gebruikersnaam en wachtwoord handmatig opgeven bij de instellingen voor Proxyserver.
Gebruik een directe verbinding wanneer de proxyserver niet beschikbaar is: als een product is geconfigureerd om
HTTP-proxy te gebruiken en de proxy is onbereikbaar, omzeilt het product de proxy en communiceert het direct
met ESET-servers.
Proxyserverinstellingen kunnen ook worden opgegeven bij Geavanceerde instellingen (Geavanceerde instellingen
> Bijwerken > Profielen > Updates > Verbindingsopties door Verbinding maken via een proxyserver te selecteren in
het vervolgkeuzemenu Proxymodus). Deze instellingen zijn van toepassing op het gegeven updateprofiel en
worden aanbevolen voor laptops die vaak updates van viruskenmerken ontvangen van externe locaties. Zie
Instellingen voor geavanceerde update voor meer informatie over deze instellingen.
4.6.10.13 E-mailmeldingen
ESET Smart Security Premium kan automatisch meldingen per e-mail verzenden zodra een gebeurtenis met het
geselecteerde detailniveau plaatsvindt. Schakel Gebeurtenismeldingen per e-mail verzenden in om meldingen per
e-mail te activeren.
SMTP-server
SMTP-server: de vooraf gedefinieerde poort van de SMTP-server die wordt gebruikt voor het sturen van
meldingen (bij voorbeeld smtp.provider.com:587 is 25).
OPMERKING
SMTP-servers met TLS-codering worden ondersteund door ESET Smart Security Premium.
Gebruikersnaam en Wachtwoord: als de SMTP-server verificatie vereist, moet u een geldige gebruikersnaam en
een geldig wachtwoord in deze velden invullen, zodat toegang tot de SMTP-server kan worden verkregen.
Adres van afzender: geef het adres van de afzender op, dat wordt weergegeven in de kop van e-mailmeldingen.
Ontvangstadressen: geef de adressen van de ontvangers op, die worden weergegeven in de kop van e-
mailmeldingen. Er worden meerdere waarden ondersteund. Gebruik een puntkomma als scheidingsteken.

130
In het vervolgkeuzemenu Minimaal detailniveau voor meldingen kunt u het startniveau selecteren voor de ernst
van de meldingen die worden verzonden.
Diagnostisch: hiermee wordt informatie geregistreerd die nodig is om het programma en alle bovenstaande
archieven af te stemmen.
Informatief: hiermee worden informatieve berichten geregistreerd, zoals berichten over
netwerkgebeurtenissen die niet standaard zijn, waaronder berichten over geslaagde updates, plus alle
bovenstaande records.
Waarschuwingen: hiermee worden kritieke fout- en waarschuwingsberichten vastgelegd ('Antistealth werkt
niet goed' of 'Update mislukt').
Fouten: hiermee worden fouten en kritieke fouten geregistreerd ('Documentbescherming niet gestart').
Kritiek: hiermee worden alleen kritieke fouten geregistreerd, zoals fouten bij het starten van
antivirusbeveiliging of een geïnfecteerd systeem.
TLS inschakelen: hiermee kunt u het verzenden van waarschuwingen en meldingen inschakelen die door TLS-
codering worden ondersteund.
Interval waarna nieuwe meldingen per e-mail worden verzonden (min): interval in minuten waarna nieuwe
meldingen per e-mail worden verzonden. Als u deze waarde instelt op 0, worden de meldingen meteen
verzonden.
Elke melding in een afzonderlijke e-mail verzenden: indien ingeschakeld, ontvangt de ontvanger een nieuw e-
mailbericht voor elke afzonderlijke melding. Dit kan resulteren in veel e-mailberichten die in korte tijd worden
ontvangen.
Berichtindeling
Indeling van gebeurtenisberichten: de indeling van gebeurtenisberichten die op externe computers worden
weergegeven.
Indeling van waarschuwingsberichten bij bedreigingen: waarschuwingen en meldingen over bedreigingen
hebben een vooraf gedefinieerde standaardindeling. U kunt deze indeling beter niet veranderen. In bepaalde
omstandigheden (als u bijvoorbeeld over een geautomatiseerd e-mailverwerkingssysteem beschikt) wilt u de
indeling van dergelijke berichten mogelijk wijzigen.
Tekenset: converteert een e-mailbericht naar ANSI-tekencodering op basis van de landinstellingen van Windows
(bijv. windows-1250), Unicode (UTF-8), ACSII 7-bits (bijv. "á" wordt vervangen door "a" en een onbekend symbool
door "?") of Japans (ISO-2022-JP).
Geciteerd-afdrukbare codering gebruiken: de bron van het e-mailbericht wordt gecodeerd in QP-indeling
(Quoted-printable), een indeling die ASCII-tekens gebruikt en speciale taalgebonden tekens correct per e-mail
kan verzenden in 8-bit-indeling (áéíóú).

131
4.6.10.13.1 Berichtindeling
Hier kunt u de indeling opgeven voor gebeurtenisberichten die op externe computers worden weergegeven.
Bedreigingswaarschuwingen en meldingen hebben een vooraf gedefinieerde standaardindeling. U kunt deze
indeling beter niet veranderen. In bepaalde omstandigheden (als u bijvoorbeeld over een geautomatiseerd e-
mailverwerkingssysteem beschikt) wilt u de indeling van dergelijke berichten mogelijk wijzigen.
Sleutelwoorden (tekenreeksen tussen procenttekens (%)) worden in het bericht vervangen door de feitelijke
informatie voor de betreffende waarschuwing. De volgende sleutelwoorden zijn beschikbaar:
%TimeStamp%: de datum en tijd van de gebeurtenis
%Scanner%: de desbetreffende module
%ComputerName%: de naam van de computer waarop de waarschuwing is gegenereerd
%ProgramName%: het programma dat de waarschuwing heeft gegenereerd
%InfectedObject%: de naam van het geïnfecteerde bestand, bericht, enzovoort
%VirusName%: de identificatie van de infectie
%Action%: ondernomen actie tegen infiltratie
%ErrorDescription%: beschrijving van een niet-virusgebeurtenis
De sleutelwoorden %InfectedObject% en %VirusName% worden alleen gebruikt in bedreigingswaarschuwingen, en
%ErrorDescription% wordt alleen gebruikt in gebeurtenisberichten.
Lokale alfabetische tekens gebruiken: hiermee wordt een e-mailbericht omgezet met ANSI-tekencodering op basis
van de landinstellingen van Windows (bijv. windows-1250). Als u deze optie niet inschakelt, wordt een bericht
omgezet en gecodeerd in ACSII 7-bit-indeling (een 'á' wordt bijvoorbeeld gewijzigd in een 'a' en een onbekend
symbool in '?').
Lokale tekencodering gebruiken: de bron van het e-mailbericht wordt gecodeerd in QP-indeling (Quoted-
printable), een indeling die ASCII-tekens gebruikt en speciale taalgebonden tekens correct per e-mail kan
verzenden in 8-bit-indeling (áéíóú).
4.6.10.14 Voorbeeld voor analyse selecteren
In het dialoogvenster voor verzending van bestanden kunt u een bestand of site naar ESET verzenden voor analyse.
Dit dialoogvenster opent u via Hulpmiddelen > Bestand verzenden voor analyse. Als u een bestand op uw computer
of een site op internet ontdekt die verdacht gedrag vertoont, kunt u dit aan het onderzoekslaboratorium van ESET
sturen om te laten analyseren. Als het bestand een schadelijke toepassing of website blijkt te zijn, wordt de
detectie ervan in een van de volgende updates opgenomen.
U kunt het bestand ook per e-mail versturen. Als u deze optie verkiest, pakt u de bestanden in met WinRAR/ZIP,
beveiligt u het archief met het wachtwoord "infected" en stuurt u het naar samples@eset.com. Zorg dat u een
duidelijk onderwerp gebruikt en zo veel mogelijk informatie over het bestand opgeeft als mogelijk (bijv. de
website waar u het hebt gedownload).
OPMERKING
Voordat u een bestand naar ESET verstuurt, moet u zorgen dat het bestand aan een van de volgende criteria
voldoet:
het bestand wordt helemaal niet gedetecteerd
het bestand is onterecht aangemerkt als bedreiging
U zult geen antwoord ontvangen, tenzij meer informatie nodig is voor de analyse.
Selecteer in het vervolgkeuzemenu Reden voor verzending van bestand de omschrijving die het best bij uw
melding past:
Verdacht bestand
Verdachte site (een website die is geïnfecteerd met malware),
Fout-positieve bestand (een bestand dat wordt gedetecteerd als infectie, maar niet geïnfecteerd is)
Fout-positief site
Anders

132
Bestand/site: het pad naar het bestand dat of de website die u wilt verzenden.
E-mailadres van contactpersoon: het e-mailadres van de contactpersoon wordt samen met de verdachte bestanden
naar ESET verzonden en kan worden gebruikt om contact met u op te nemen als meer informatie nodig is voor de
analyse. Het invoeren van een e-mailadres voor de contactpersoon is optioneel. Het bestand kan anoniem worden
ingediend. Omdat de servers van ESET dagelijks tienduizenden bestanden ontvangen, is het onmogelijk om
iedereen te beantwoorden. U zult dan ook geen antwoord van ESET ontvangen tenzij meer informatie nodig is.
4.6.10.15 Microsoft Windows®-update
De updatefunctie van Windows is een belangrijk onderdeel bij het beschermen van gebruikers tegen schadelijke
software. Het is dan ook zeer belangrijk dat updates van Microsoft Windows zo snel mogelijk worden geïnstalleerd.
Afhankelijk van het waarschuwingsniveau dat u instelt, verstuurt ESET Smart Security Premium meldingen over
ontbrekende updates. De volgende niveaus zijn beschikbaar:
Geen updates: er worden geen systeemupdates aangeboden als download.
Optionele updates: updates gemarkeerd als lage prioriteit en hoger worden aangeboden als download.
Aanbevolen updates: updates gemarkeerd als normale prioriteit en hoger worden aangeboden als download.
Belangrijke updates: updates gemarkeerd als belangrijke prioriteit en hoger worden aangeboden als
download.
Essentiële updates: alleen essentiële updates worden aangeboden als download.
Klik op OK om de wijzigingen op te slaan. Het venster Systeemupdates wordt weergegeven nadat de status is
gecontroleerd op de updateserver. Het is dan ook mogelijk dat de gegevens van de systeemupdate niet direct
beschikbaar zijn na het opslaan van de wijzigingen.
4.6.10.16 ESET CMD
Dit is een functie die geavanceerde ecmd-opdrachten mogelijk maakt. Hiermee kunt u instellingen met behulp van
de opdrachtregel (ecmd.exe) exporteren en importeren. Tot nu toe was het alleen mogelijk om instellingen te
exporteren met de grafische gebruikersinterface. De ESET Smart Security Premium-configuratie kan worden
geëxporteerd naar een .xml-bestand.
Wanneer u ESET CMD hebt ingeschakeld, zijn er twee autorisatiemethodes beschikbaar:
Geen: geen autorisatie. Wij raden deze methode niet aan, omdat dit het importeren van niet-ondertekende
configuraties toestaat, wat een potentieel gevaar vormt.
Wachtwoord voor geavanceerde instellingen: er is een wachtwoord vereist om een configuratie te importeren uit
een .xml-bestand. Dit bestand moet zijn ondertekend (zie 'Een .xml-configuratiebestand ondertekenen'
hieronder). Het wachtwoord dat is ingesteld in Toegangsinstellingen, moet worden opgegeven voordat er een
nieuwe configuratie kan worden geïmporteerd. Als u toegangsinstellingen niet hebt ingeschakeld, komt uw
wachtwoord niet overeen of is het .xml-configuratiebestand niet ondertekend en wordt de configuratie niet
geïmporteerd.
Nadat ESET CMD is ingeschakeld, kunt u de opdrachtregel gebruiken om ESET Smart Security Premium-configuraties
te importeren of exporteren. U kunt dit handmatig doen of een script maken om dit te automatiseren.
BELANGRIJK
Als u geavanceerde ecmd-opdrachten wilt gebruiken, moet u deze uitvoeren met beheerdersrechten of een
Windows-opdrachtprompt (cmd) openen met behulp van Als Administrator uitvoeren. Als u dat niet doet, ziet u
het bericht Error executing command.. Ook wanneer u een configuratie exporteert, moet de doelmap bestaan.
De exportopdracht werkt ook als de ESET CMD-instelling is uitgeschakeld.
VOORBEELD
Opdracht instellingen exporteren:
ecmd /getcfg c:\config\settings.xml

133
Opdracht instellingen importeren:
ecmd /setcfg c:\config\settings.xml
OPMERKING
Geavanceerde ecmd-opdrachten kunnen alleen lokaal worden uitgevoerd.
Een .xml-configuratiebestand ondertekenen:
1. Download het uitvoerbare XmlSignTool-bestand.
2. Open een Windows-opdrachtprompt (cmd) met behulp van Als Administrator uitvoeren.
3. Navigeer naar de opslaglocatie van xmlsigntool.exe
4. Voer een opdracht uit om het .xml-configuratiebestand te ondertekenen. Gebruik:
xmlsigntool /version 1|2 <xml_file_path>
BELANGRIJK
De waarde van de parameter /version hangt af van uw versie van ESET Smart Security Premium.
Gebruik /version 1 voor eerdere versies van ESET Smart Security Premium dan 11.1. Gebruik /version 2
voor de huidige versie van ESET Smart Security Premium.
5. Voer het wachtwoord voor Geavanceerde instellingen in en daarna nog een keer, wanneer hier door
XmlSignTool naar wordt gevraagd. Uw .xml-configuratiebestand is nu ondertekend en kan worden gebruikt om
een ander exemplaar van ESET Smart Security Premium te importeren met ESET CMD en de
wachtwoordautorisatiemethode.
VOORBEELD
De geëxporteerde configuratiebestandopdracht ondertekenen:
xmlsigntool /version 1 c:\config\settings.xml
OPMERKING
Als uw wachtwoord voor Toegangsinstellingen wordt gewijzigd en u een configuratie wilt importeren die eerder
met een oud wachtwoord is ondertekend, moet u het .xml-configuratiebestand opnieuw ondertekenen met uw
huidige wachtwoord. Hierdoor kunt u een ouder configuratiebestand gebruiken zonder dat u dit voorafgaand aan

134
het importeren hoeft te exporteren naar een andere computer waarop ESET Smart Security Premium wordt
uitgevoerd.
4.7 Gebruikersinterface
In het gedeelte Gebruikersinterface kunt u het gedrag van de GUI (Graphical User Interface, grafische
gebruikersinterface) van het programma configureren.
Met het hulpmiddel Grafische instellingen kunt u het uiterlijk en de gebruikte effecten van het programma
aanpassen.
Door Waarschuwingen en meldingen te configureren, kunt u het gedrag van waarschuwingen bij gedetecteerde
bedreigingen en systeemmeldingen wijzigen. U kunt deze aan uw behoeften aanpassen.
Als u maximaal wilt worden beveiligd door uw beveiligingssoftware, kunt u ongeautoriseerde wijzigingen
voorkomen door de instellingen te beveiligen met een wachtwoord via het hulpmiddel Toegangsinstellingen.
4.7.1 Elementen van gebruikersinterface
Via de configuratie-opties voor de gebruikersinterface van ESET Smart Security Premium kunt u de werkomgeving
aan uw eigen behoeften aanpassen. Deze configuratieopties zijn toegankelijk via Geavanceerde instellingen >
Gebruikersinterface > Elementen van gebruikersinterface.
Als u het welkomstscherm van ESET Smart Security Premium wilt uitschakelen, schakelt u Welkomstscherm
weergeven bij opstarten uit.
Als u wilt dat ESET Smart Security Premium een geluid afspeelt als er zich een belangrijke gebeurtenis voordoet
tijdens een scan, bijvoorbeeld als er een bedreiging wordt ontdekt of als het scannen is voltooid, schakel dan
Geluidssignaal gebruiken in.
Integreren in het contextmenu: hiermee kunt u de besturingselementen van ESET Smart Security Premium
integreren in het contextmenu.
Statussen
Toepassingsstatussen: klik op de knop Bewerken om statussen te beheren (uitschakelen) die worden
weergegeven in het eerste deelvenster van het hoofdvenster.

135

136
4.7.2 Waarschuwingen en meldingen
In het gedeelte Waarschuwingen en meldingen onder Gebruikersinterface kunt u configureren hoe
waarschuwingsberichten en systeemmeldingen (bijvoorbeeld berichten over geslaagde updates) worden
afgehandeld door ESET Smart Security Premium. Daarnaast kunt u de weergavetijd en de transparantie van
meldingen in het systeemvak instellen (alleen van toepassing op systemen die ondersteuning bieden voor
meldingen in het systeemvak).
Waarschuwingsvensters
Als u Waarschuwingen weergeven uitschakelt, worden alle waarschuwingsvensters geannuleerd. Deze optie is
alleen geschikt in een beperkt aantal specifieke situaties. Voor de meeste gebruikers adviseren wij de
standaardoptie (ingeschakeld) te gebruiken.
In-product messaging
Marketingberichten weergeven: de berichten in het product zijn bedoeld om gebruikers op de hoogte te
brengen van ESET-nieuws en andere communicatie. Voor verzending van marketingberichten is de instemming
van een gebruiker vereist. Marketingberichten worden daarom niet standaard naar een gebruiker verzonden
(weergegeven als een vraagteken). Door deze optie in te schakelen, gaat u akkoord met de ontvangst van ESET-
marketingberichten. Als u niet bent geïnteresseerd in de ontvangst van ESET-marketingmateriaal, schakel de
optie dan uit.
Bureaubladmeldingen
Meldingen op het bureaublad en ballontips zijn informatiemiddelen waarbij geen gebruikersinteractie nodig is.
Ze worden weergegeven in het systeemvak in de rechterbenedenhoek van het scherm. Als u de
bureaubladmeldingen wilt activeren, selecteert u Meldingen weergeven op bureaublad.
Zet de schakelaar Geen meldingen weergeven wanneer toepassingen in de modus Volledig scherm worden
uitgevoerd aan om alle niet-interactieve meldingen te onderdrukken. Meer gedetailleerde opties, zoals
weergavetijd van meldingen en transparantie van het venster, kunnen hieronder worden aangepast.

137
Meldingen over beveiligingsrapporten uitschakelen: u kunt meldingen over beveiligingsrapporten in- of
uitschakelen.
In het vervolgkeuzemenu Minimaal detailniveau voor weergegeven gebeurtenissen kunt u de ernst selecteren
voor de weergave van waarschuwingen en meldingen. De volgende opties zijn beschikbaar:
Diagnostisch: hiermee wordt informatie geregistreerd die nodig is om het programma en alle bovenstaande
archieven af te stemmen.
Informatief: hiermee registreert u informatieve berichten, waaronder berichten over geslaagde updates, plus
alle bovenstaande records.
Waarschuwingen: hiermee worden kritieke fouten en waarschuwingsberichten geregistreerd.
Fouten: hiermee worden fouten als 'Fout bij downloaden van bestand' en kritieke fouten geregistreerd.
Kritiek: hiermee worden alleen kritieke fouten geregistreerd (zoals fouten bij het starten van
antivirusbeveiliging, ingebouwde firewall, enzovoort).
Met de laatste functie in dit gedeelte kunt u het doel van de meldingen specificeren in een omgeving met
meerdere gebruikers. In het veld In systemen met meerdere gebruikers meldingen weergeven op het scherm
van deze gebruiker kunt u opgeven welke gebruiker in systemen met meerdere gebruikers meldingen van het
systeem en andere meldingen moet ontvangen. Gewoonlijk is dit een systeem- of netwerkbeheerder. Deze
optie is met name handig voor terminalservers, op voorwaarde dat alle systeemmeldingen naar de beheerder
worden verzonden.
Berichtvensters
U kunt pop-upvensters automatisch na een bepaalde tijd laten sluiten door Berichtvensters automatisch sluiten
te selecteren. Als de waarschuwingsvensters niet handmatig worden gesloten, gebeurt dit automatisch nadat
de opgegeven tijdsperiode is verstreken.
Bevestigingsberichten: hiermee wordt een lijst met bevestigingsberichten getoond en u kunt selecteren of u
deze wilt weergeven of niet.
4.7.2.1 Geavanceerde instellingen
In de vervolgkeuzelijst Minimaal detailniveau voor weergegeven gebeurtenissen kunt u het startniveau selecteren
voor de weergave van waarschuwingen en meldingen.
Diagnostisch: hiermee wordt informatie geregistreerd die nodig is om het programma en alle bovenstaande
archieven af te stemmen.
Informatief: registreert informatieve berichten, waaronder berichten over geslaagde updates, plus alle
bovenstaande archieven.
Waarschuwingen: hiermee worden kritieke fouten en waarschuwingsberichten geregistreerd.
Fouten: fouten als 'Fout bij downloaden van bestand' en kritieke fouten worden geregistreerd.
Kritiek: hiermee worden alleen kritieke fouten geregistreerd (zoals fouten bij het starten van
antivirusbeveiliging, Firewall, enzovoort).
Met de laatste functie in dit gedeelte kunt u het doel van de meldingen specificeren in een omgeving met
meerdere gebruikers. In het veld In systemen met meerdere gebruikers meldingen weergeven op het scherm van
deze gebruiker kunt u de gebruiker opgeven die in systemen met meerdere gebruikers meldingen van het systeem
en andere meldingen moet ontvangen. Gewoonlijk is dit een systeem- of netwerkbeheerder. Deze optie is met
name handig voor terminalservers, op voorwaarde dat alle systeemmeldingen naar de beheerder worden
verzonden.

138
4.7.3 Toegangsinstellingen
Instellingen van ESET Smart Security Premium vormen een cruciaal onderdeel van uw beveiligingsbeleid.
Onbevoegde wijzigingen kunnen de stabiliteit en beveiliging van uw systeem in gevaar brengen. Onbevoegde
wijzigingen kunnen worden verhinderd door de instellingsparameters van ESET Smart Security Premium te
beveiligen met een wachtwoord.
Instellingen met wachtwoord beveiligen: geven wachtwoordinstellingen aan. Klik om het venster Wachtwoord
instellen te openen.
Klik op Instellen om een wachtwoord ter beveiliging van de ingestelde parameters in te stellen of te wijzigen.
OPMERKING
Wanneer u de beveiligde functie Geavanceerde instellingen wilt openen, wordt het venster voor het invoeren
van het wachtwoord weergegeven. Als u uw wachtwoord bent vergeten of kwijt bent, klikt u hieronder op de
optie Wachtwoord herstellen en voert u het e-mailadres in dat u hebt gebruikt om uw licentie te registreren.
ESET stuurt u dan een e-mail met de verificatiecode en instructies voor het opnieuw instellen van uw
wachtwoord. Klik hier voor meer informatie.
Volledige beheerdersrechten vereist voor beperkte beheerdersaccounts: selecteer dit om de huidige gebruiker (als
hij of zij niet over beheerdersrechten beschikt) te vragen om de gebruikersnaam en het wachtwoord van een
beheerder om bepaalde systeemparameters te kunnen aanpassen (vergelijkbaar met Gebruikersaccountbeheer
(UAC) in Windows Vista en Windows 7). Het betreft hier aanpassingen zoals het uitschakelen van
beveiligingsmodules of de firewall. In Windows XP-systemen waarin UAC niet wordt uitgevoerd, is de optie
Beheerdersrechten vereist (systeem zonder UAC-ondersteuning) beschikbaar voor gebruikers.
Alleen voor Windows XP:
Beheerdersrechten vereist (systeem zonder UAC-ondersteuning): schakel deze optie in als u wilt dat ESET Smart
Security Premium naar aanmeldingsgegevens van een beheerder vraagt.

139
4.7.4 Programmamenu
Enkele van de belangrijkste instellingen en functies zijn toegankelijk door met de rechtermuisknop te klikken op
het systeemvakpictogram .
Snelle koppelingen: geeft de meestgebruikte onderdelen van ESET Smart Security Premium weer. U hebt hiertoe
snel toegang vanuit het programmamenu.
Beveiliging tijdelijk uitschakelen: geeft het bevestigingsvenster weer dat Antivirus- en antispywarebeveiliging
uitschakelt, waarmee bescherming wordt geboden tegen schadelijke aanvallen op het systeem, door middel van
controle over bestanden, e-mail en internetcommunicatie.
De vervolgkeuzelij st Tijdsinterval vertegenwoordigt de periode waarin alle antivirus- en antispywarebeveiliging is
uitgeschakeld.
Firewall tijdelijk uitschakelen (alle verkeer toestaan): plaatst de firewall in inactieve toestand. Zie Netwerk voor
meer informatie.
Alle netwerkverkeer blokkeren: blokkeert alle netwerkverkeer. U kunt dit opnieuw inschakelen door te klikken op
Blokkeren van alle netwerkverkeer stoppen.
Geavanceerde instellingen: selecteer deze optie om de structuur Geavanceerde instellingen te openen. U kunt
Geavanceerde instellingen ook op andere manieren weergeven, bijvoorbeeld door op F5 te drukken of door naar
Instellingen > Geavanceerde instellingen te gaan.
Logbestanden: de logbestanden bevatten informatie over belangrijke programmagebeurtenissen die zich hebben
voorgedaan en bieden een overzicht van gedetecteerde bedreigingen.
ESET Smart Security Premium verbergen: hiermee verbergt u het ESET Smart Security Premium-venster.

140
Vensterindeling opnieuw instellen: stelt het venster van ESET Smart Security Premium opnieuw in op de
standaardgrootte en het venster wordt hiermee opnieuw op de standaardpositie van het scherm geplaatst.
Controleren op updates: hiermee wordt de detectie-engine (voorheen 'database met viruskenmerken' genoemd)
bijgewerkt om uw bescherming tegen schadelijke code te garanderen.
Info over: biedt systeeminformatie, details over de geïnstalleerde versie van ESET Smart Security Premium en de
geïnstalleerde programmamodules. Hier vindt u tevens de vervaldatum van uw licentie en informatie over het
besturingssysteem en systeembronnen.

141
5. Geavanceerde gebruiker
5.1 Profielen
Profielbeheer wordt op twee plaatsen in ESET Smart Security Premium gebruikt: in het gedeelte Computerscan op
aanvraag en in het gedeelte Bijwerken.
Computerscan
U kunt uw voorkeursparameters voor scannen opslaan voor toekomstige scans. Wij adviseren u voor elke regelmatig
gebruikte scan een ander profiel te maken (met verschillende scandoelen, scanmethoden en andere parameters).
Als u een nieuw profiel wilt maken, opent u het venster Geavanceerde instellingen (F5) en klikt u op Detectie-
engine > Malwarescans > Op aanvraag scannen > Lijst met profielen. Het venster Profielbeheer bevat de
vervolgkeuzelijst Geselecteerd profiel met bestaande scanprofielen en de optie om een nieuw profiel te maken.
Raadpleeg het gedeelte Parameters voor ThreatSense-engine instellen voor een beschrijving van elke parameter
van de scaninstellingen, zodat u een scanprofiel kunt maken dat aan uw behoeften voldoet.
OPMERKING
Stel: u wilt een eigen scanprofiel maken en de configuratie voor Uw computer scannen is deels geschikt, maar u
wilt geen scanprogramma's voor runtime-compressie of potentieel onveilige toepassingen scannen en u wilt ook
Volledig opschonen toepassen. Geef de naam van uw nieuwe profiel op in het venster Profielbeheer en klik op
Toevoegen. Selecteer uw nieuwe profiel in het vervolgkeuzemenu Geselecteerd profiel en pas de resterende
parameters aan om aan uw vereisten te voldoen, en klik op OK om uw nieuwe profiel op te slaan.
Bijwerken
Met de profieleditor in het gedeelte Instellingen voor update kunnen gebruikers nieuwe updateprofielen maken.
Maak en gebruik uw eigen aangepaste profielen (alle andere profielen dan het standaardprofiel Mijn profiel) alleen
als de computer op verschillende manieren verbinding met updateservers maakt.
Een laptop die normaliter verbinding maakt met een lokale server (mirror) in het lokale netwerk, maar updates
rechtstreeks van de updateservers van ESET downloadt als de laptop niet met het lokale netwerk is verbonden
(bijvoorbeeld tijdens een zakenreis), kan twee profielen gebruiken: een om verbinding met de lokale server te
maken en een om verbinding met de servers van ESET te maken. Ga nadat deze profielen zijn geconfigureerd naar
Hulpmiddelen > Planner en bewerk de taakparameters voor updates. Definieer het ene profiel als het primaire
profiel en het andere als het secundaire profiel.
Updateprofiel: het updateprofiel dat momenteel wordt gebruikt. Als u dit profiel wilt wijzigen, kiest u een profiel
in de vervolgkeuzelijst.
Lijst met profielen: nieuwe updateprofielen maken of bestaande updateprofielen verwijderen.
5.2 Sneltoetsen
Voor betere navigatie in uw ESET-product kunnen de volgende sneltoetsen worden gebruikt:
F1
Help-pagina's weergeven
F5
Geavanceerde instellingen openen
Omhoog/
Omlaag
Navigatie in product via items
-
Het knooppunt Geavanceerde instellingen samenvouwen
TAB
De cursor in een venster verplaatsen
Esc
Het actieve dialoogvenster sluiten
Ctrl+U
geeft licentie-informatie weer (details voor de klantenservice)
Ctrl+R
herstelt de standaardgrootte en -positie op het scherm van het
productvenster

142
5.3 Diagnostiek
Diagnostiek biedt dumpbestanden bij het vastlopen van toepassingen van processen van ESET (bijvoorbeeld ekrn).
Als een toepassing vastloopt, wordt een dumpbestand gegenereerd. Dit kan ontwikkelaars helpen bij het opsporen
van fouten en het oplossen van verschillende problemen met ESET Smart Security Premium. Klik op het
vervolgkeuzemeu naast Dumptype en selecteer een van de drie beschikbare opties:
Selecteer Uitschakelen (standaard) om deze functie uit te schakelen.
Mini: hiermee wordt de kleinst mogelijke hoeveelheid nuttige informatie vastgelegd waarmee kan worden
geïdentificeerd waarom de toepassing onverwacht is vastgelopen. Dit type dumpbestand kan handig zijn
wanneer er beperkte ruimte beschikbaar is. Omdat er echter maar weinig informatie in is opgenomen, worden
fouten die niet rechtstreeks werden veroorzaakt door de thread die werd uitgevoerd op het moment van het
probleem mogelijk niet ontdekt door een analyse van dit bestand.
Volledig: Hiermee wordt de volledige inhoud van het systeemgeheugen vastgelegd wanneer een toepassing
onverwacht stopt. Een volledige geheugendump kan gegevens bevatten van processen die werden uitgevoerd
op het moment dat de geheugendump werd gemaakt.
Geavanceerde logboekregistratie inschakelen voor netwerkbeveiliging: alle netwerkgegevens registreren die in
PCAP-indeling door de firewall worden verwerkt, om de ontwikkelaars te helpen problemen met de firewall te
diagnosticeren en op te lossen.
Geavanceerde logboekregistratie inschakelen voor Protocolfiltering: alle netwerkgegevens registreren die in PCAP-
indeling door de engine van Protocolfiltering worden verwerkt, om de ontwikkelaars te helpen problemen met
Protocolfiltering te diagnosticeren en op te lossen.
Geavanceerde logbestanden voor update-engine inschakelen: alle gebeurtenissen registreren die tijdens het
updateproces plaatsvinden. Hiermee kunnen ontwikkelaars problemen diagnosticeren en oplossen die betrekking
hebben op de update-engine.
Geavanceerd logbestand voor Ouderlijk toezicht inschakelen: alle gebeurtenissen registreren die plaatsvinden in
Ouderlijk toezicht. Hiermee kunnen ontwikkelaars problemen diagnostiseren en oplossen die betrekking hebben
op Ouderlijk toezicht.
Geavanceerde logbestanden voor licentiëring inschakelen: alle productcommunicatie met de licentieserver
registreren.
Geavanceerde logboekregistratie voor Antidienstal-engine inschakelen: alle gebeurtenissen registreren die
plaatsvinden in Antidiefstal, om te helpen bij het diagnosticeren en oplossen van problemen.
Geavanceerde logbestanden voor Antispam-engine inschakelen: alle gebeurtenissen registreren die tijdens het
scannen op antispam plaatsvinden. Hiermee kunnen ontwikkelaars problemen diagnosticeren en oplossen die
betrekking hebben op de ESET Antispam-engine.
Geavanceerd logbestand voor besturingssysteem inschakelen: er wordt aanvullende informatie verzameld over het
besturingssysteem, zoals over actieve processen, CPU-activiteit en schijfbewerkingen. Ontwikkelaars kunnen met
deze informatie problemen diagnosticeren en oplossen met betrekking tot ESET-producten die op uw
besturingssysteem worden uitgevoerd (beschikbaar voor Windows 10).
Logbestanden vindt u hier:
C:\ProgramData\ESET\ESET ESET Smart Security Premium \Diagnostics\ bij Windows Vista en later of C:\Documents
and Settings\All Users\... bij eerdere versies van Windows.
Doelmap: de map waarin het dumpbestand bij het vastlopen wordt gegenereerd.
Diagnostiekmap openen: klik op Openen om deze map te openen in een nieuw venster van Windows Verkenner.
Diagnostische dump maken: klik op Maken om diagnostische dumpbestanden te maken in de Doelmap.

143
5.4 Instellingen importeren en exporteren
U kunt uw aangepaste XML-configuratiebestand van ESET Smart Security Premium importeren of exporteren via het
menu Instellingen.
Importeren en exporteren van configuratiebestanden is handig als u een back-up wilt maken van uw huidige
configuratie van ESET Smart Security Premium voor later gebruik. De optie voor het exporteren van instellingen is
ook handig voor gebruikers die hun voorkeursconfiguratie willen gebruiken op meerdere systemen. Ze kunnen
eenvoudig een .xml-bestand importeren om deze instellingen over te brengen.
Het importeren van een configuratie is heel gemakkelijk. Klik in het hoofdprogrammavenster op Instellingen >
Instellingen importeren en exporteren en selecteer de optie Instellingen importeren. Voer de bestandsnaam van
het configuratiebestand in of klik op de knop ... om naar het configuratiebestand te bladeren dat u wilt importeren.
De stappen voor het exporteren van een configuratie zijn vergelijkbaar. Klik in het hoofdprogrammavenster op
Instellingen > Instellingen importeren en exporteren. Selecteer Instellingen exporteren en voer de bestandsnaam
van het configuratiebestand in (bijvoorbeeld export.xml). Gebruik de browser om een locatie te selecteren op uw
computer waar u het configuratiebestand wilt opslaan.
OPMERKING
er kan een fout optreden bij het exporteren van instellingen als u onvoldoende rechten hebt om het
geëxporteerde bestand naar de opgegeven map te schrijven.
5.5 ESET SysInspector
5.5.1 ESET SysInspector
ESET SysInspector is een toepassing waarmee u een uitgebreide inspectie van uw computer kunt uitvoeren om
allerlei nuttige gegevens te verzamelen. Informatie zoals geïnstalleerde stuurprogramma's en toepassingen,
netwerkverbindingen of belangrijke registervermeldingen, kunnen u helpen mogelijke oorzaken van afwijkend
systeemgedrag te elimineren. Het hoeft namelijk niet altijd zo te zijn dat een malware-infectie problemen
veroorzaakt. Het is ook mogelijk dat incompatibele software of hardware de oorzaak is.
U kunt ESET SysInspector op twee manieren openen: vanuit de geïntegreerde versie in ESET Security-producten of
door de op zichzelf staande versie (SysInspector.exe) gratis te downloaden vanaf de ESET-website. Beide versies
werken precies hetzelfde en hebben dezelfde besturingselementen. Het enige verschil is het beheer van de
uitvoer. U kunt zowel in de gedownloade als de geïntegreerde versie momentopnamen van uw systeem exporteren
als een .xml-bestand en deze op schijf opslaan. Met de geïntegreerde versie kunt u echter ook momentopnamen
van uw systeem rechtstreeks opslaan in Hulpmiddelen > ESET SysInspector behalve ESET Remote Administrator).

144
Het kost ESET SysInspector enige tijd om uw computer te scannen. Het kan variëren van 10 seconden tot enkele
minuten, afhankelijk van uw hardwareconfiguratie, besturingssysteem en het aantal op uw computer
geïnstalleerde toepassingen.
5.5.1.1 ESET SysInspector starten
Als u ESET SysInspector wilt starten, voert u het uitvoerbare bestand SysInspector.exe uit dat u hebt gedownload van
de ESET-website.
Wacht totdat de toepassing klaar is met het inspecteren van uw systeem. Dit kan enkele minuten duren.
5.5.2 Gebruikersinterface en gebruik van de toepassing
Het hoofdprogrammavenster is verdeeld in vier gedeelten: de besturingselementen boven aan het
hoofdprogrammavenster, het navigatievenster aan de linkerkant, het venster Omschrijving aan de rechterkant en
het venster Details onder aan het hoofdprogrammavenster. In het gedeelte Status logbestand staan de
basisparameters van een logbestand (het gebruikte filter, het filtertype, of het logbestand het resultaat van een
vergelijking is, enz.).
5.5.2.1 Besturingselementen in programma
Dit gedeelte bevat een omschrijving van alle besturingselementen die beschikbaar zijn in ESET SysInspector.
Bestand
Klik op Bestand om een rapport op te slaan voor latere analyse of om een eerder opgeslagen rapport te openen.
Voor publicatiedoeleinden wordt u aanbevolen een logboek te genereren als Geschikt voor verzenden. In deze
vorm worden gevoelige gegevens niet in het logboek opgenomen (huidige gebruikersnaam, computernaam,
domeinnaam, huidige gebruikersrechten, omgevingsvariabelen, enz.).
OPMERKING: U kunt eerder opgeslagen rapporten van ESET SysInspector openen door ze naar het
hoofdprogrammavenster te slepen.

145
Structuur
Hiermee kunt u alle knooppunten uit- of samenvouwen en geselecteerde delen exporteren naar een servicescript.
Lijst
Dit menu bevat functies voor een eenvoudige navigatie binnen het programma, evenals verschillende andere
functies, zoals voor het zoeken van online-informatie.
Help
Dit menu bevat informatie over de toepassing en de verschillende mogelijkheden.
Details
Deze instelling heeft invloed op de informatie die wordt weergegeven in het hoofdprogrammavenster zodat u
gemakkelijker met de informatie kunt werken. In de modus Standaard hebt u toegang tot gegevens die nodig zijn
voor het vinden van oplossingen voor veelvoorkomende problemen met het systeem. In de modus Gemiddeld
worden mindergebruikte details weergegeven. In de modus Volledig van ESET SysInspector wordt alle informatie
weergegeven die nodig is om zeer specifieke problemen op te lossen.
Filteren
Deze optie is het meest geschikt voor het zoeken van verdachte bestanden of registervermeldingen in het systeem.
Beweeg de schuifregelaar om items te filteren op risiconiveau. Als u de schuifregelaar helemaal links zet
(Risiconiveau 1), worden alle items weergegeven. Door de schuifregelaar naar rechts te bewegen worden alle items
eruit gefilterd die minder riskant zijn dan het huidige risiconiveau. Alleen items die verdachter zijn dan het gekozen
niveau worden dan weergegeven. Als u de schuifregelaar helemaal rechts zet, worden alleen items weergegeven
waarvan bekend is dat ze schadelijk zijn.
Alle items met de aanduiding risico 6 tot 9 kunnen een beveiligingsrisico vormen. Als u geen van de
beveiligingsoplossingen van ESET gebruikt, is het raadzaam uw systeem te controleren met ESET Online Scanner als
ESET SysInspector een dergelijk item heeft gevonden. ESET Online Scanner is gratis.
OPMERKING: het risiconiveau van een item kan eenvoudig worden bepaald door de kleur van het item te
vergelijken met de kleuren op de schuifregelaar Risiconiveau.
Vergelijken
Als u twee logbestanden vergelijkt, kunt u kiezen of u alle items wilt weergeven, alleen toegevoegde items, alleen
verwijderde items of alleen vervangen items.
Opsporen
Gebruik deze optie om snel een item te vinden door de naam van het item of een deel van de naam in te voeren.
De resultaten van de zoekopdracht worden weergegeven in het beschrijvingsvenster.
Bevestigen
Klik op de pijl Vorige of de pijl Volgende om terug te keren naar eerder weergegeven informatie in het
beschrijvingsvenster. U kunt de toets Backspace en de spatiebalk gebruiken in plaats van op Vorige en Volgende te
klikken.
Sectie Status
Hier wordt het huidige knooppunt in het navigatievenster weergegeven.
Belangrijk: Rood gemarkeerde items zijn onbekend. Om die reden zijn ze door het programma gemarkeerd als
potentieel gevaarlijk. Als een item rood wordt weergegeven, betekent dit niet automatisch dat u het bestand kunt
verwijderen. Controleer eerst altijd of het bestand daadwerkelijk gevaarlijk of overbodig is.

146
5.5.2.2 Navigeren in ESET SysInspector
In ESET SysInspector worden verschillende soorten informatie opgedeeld in een aantal basisdelen (knooppunten).
Als er aanvullende gegevens beschikbaar zijn, kunt u deze weergeven door een knooppunt uit te vouwen. U kunt
een knooppunt uit- of samenvouwen door op de naam van het knooppunt te dubbelklikken. U kunt ook klikken op
of naast de naam van het knooppunt. Terwijl u in het navigatievenster door de boomstructuur met knooppunten
en subknooppunten bladert, kunnen er in het beschrijvingsvenster verschillende gegevens voor een knooppunt
verschijnen. Als u bladert door items in het beschrijvingsvenster, kunnen er aanvullende gegevens van het item
worden weergegeven in het detailvenster.
Hieronder volgt een omschrijving van de belangrijkste knooppunten in het navigatievenster. Daarnaast wordt er
voor die knooppunten aangegeven welke informatie er kan worden weergegeven in het beschrijvingsvenster en
het detailvenster.
Actieve processen
Dit knooppunt bevat informatie over toepassingen en processen die actief zijn op het moment dat het logbestand
wordt gegenereerd. In het beschrijvingsvenster kunnen voor elk proces aanvullende details worden weergegeven,
zoals de DLL's (Dynamic Link Libraries) die worden gebruikt door het proces en hun locatie in het systeem, de naam
van de leverancier van de toepassing, het risiconiveau van het bestand, enz.
Het detailvenster bevat aanvullende informatie over items die zijn geselecteerd in het beschrijvingsvenster, zoals
de bestandsgrootte of de hash-waarde.
OPMERKING: Een besturingssysteem bestaat uit een aantal belangrijke kernel-onderdelen die continu actief zijn en
die eenvoudige maar ook essentiële functies verzorgen voor andere gebruikerstoepassingen. In bepaalde gevallen
worden deze processen in ESET SysInspector weergegeven met een bestandspad dat begint met \??\. Deze
symbolen maken het mogelijk dat die processen vóór uitvoering kunnen worden geoptimaliseerd. Het zijn veilige
processen voor het systeem.
Netwerkverbindingen
Het beschrijvingsvenster bevat een lijst met processen en toepassingen die communiceren over het netwerk met
het protocol dat is geselecteerd in het the navigatievenster (TCP of UDP), evenals het externe adres waarmee de
toepassing verbinding heeft. U kunt tevens de IP-adressen van DNS-servers controleren.
Het detailvenster bevat aanvullende informatie over items die zijn geselecteerd in het beschrijvingsvenster, zoals
de bestandsgrootte of de hash-waarde.
Belangrijke registervermeldingen
Dit gedeelte bevat een lijst met specifieke registervermeldingen, die vaak te maken hebben met verschillende
problemen die in het systeem kunnen optreden. Denk hierbij aan problemen met programma's die automatisch
moeten worden gestart of BHO's (Browser Helper Objects).
In het beschrijvingsvenster kunnen bestanden worden weergegeven die zijn gekoppeld aan bepaalde
registervermeldingen. Het detailvenster kan aanvullende gegevens over de vermeldingen bevatten.
Services
Het beschrijvingsvenster bevat een lijst met bestanden die zijn geregistreerd als Windows-services. U kunt hier
bijvoorbeeld zien op welke manier een service wordt gestart. Het detailvenster kan specifieke gegevens van het
bestand bevatten.
Stuurprogramma's
Een lijst met de stuurprogramma's die in het systeem zijn geïnstalleerd.
Belangrijke bestanden
Het beschrijvingsvenster bevat de inhoud van belangrijke bestanden die essentieel zijn voor het besturingssysteem
Microsoft Windows.

147
Taken van systeemplanner
Bevat een lijst met taken die op een opgegeven tijd/interval zijn gegenereerd door de Windows-taakplanner.
Systeeminformatie
Bevat gedetailleerde informatie over hardware en software, en informatie over ingestelde omgevingsvariabelen,
gebruikersrechten en logboeken over systeemgebeurtenissen.
Bestandsgegevens
Een lijst met belangrijke systeembestanden en bestanden in de map Program Files. Het beschrijvingsvenster en
detailvenster bevatten aanvullende informatie over de bestanden.
Info over
Informatie over de versie van ESET SysInspector en de lijst met programmamodules.

148
5.5.2.2.1 Sneltoetsen
U kunt de volgende sneltoetsen gebruiken tijdens het werken met ESET SysInspector:
Bestand
Ctrl+O
Een bestaand logbestand openen.
Ctrl+S
Logbestanden opslaan.
Genereren
Ctrl+G
hiermee wordt een standaardmomentopname van de computerstatus gemaakt
Ctrl+H
een momentopname van de computerstatus maken die ook vertrouwelijke gegevens mag
bevatten
Items filteren
1, O
Goed, items met het risiconiveau 1-9 worden weergegeven.
2
Goed, items met het risiconiveau 2-9 worden weergegeven.
3
Goed, items met het risiconiveau 3-9 worden weergegeven.
4, U
Onbekend, items met het risiconiveau 4-9 worden weergegeven.
5
Onbekend, items met het risiconiveau 5-9 worden weergegeven.
6
Onbekend, items met het risiconiveau 6-9 worden weergegeven.
7, B
Riskant, items met het risiconiveau 7-9 worden weergegeven.
8
Riskant, items met het risiconiveau 8-9 worden weergegeven.
9
Riskant, items met het risiconiveau 9 worden weergegeven.
-
Het risiconiveau verlagen.
+
Het risiconiveau verhogen.
Ctrl+9
Filtermodus, gelijk niveau of hoger.
Ctrl+0
Filtermodus, alleen gelijk niveau.
Beeld
Ctrl+5
Weergeven op leverancier, alle leveranciers.
Ctrl+6
Weergeven op leverancier, alleen Microsoft.
Ctrl+7
Weergeven op leverancier, alle overige leveranciers.
Ctrl+3
Volledige details weergeven.
Ctrl+2
Gemiddelde hoeveelheid details weergeven.
Ctrl+1
Alleen essentiële details weergeven.
Backspace
Eén stap terug gaan.
Spatiebalk
Eén stap vooruit gaan.
Ctrl+W
Structuur uitvouwen.
Ctrl+Q
Structuur samenvouwen.
Overige besturingselementen
Ctrl+T
Terug naar de oorspronkelijke locatie van item na selectie in zoekresultaten.
Ctrl+P
Basisinformatie over een item weergeven.
Ctrl+A
Volledige informatie over een item weergeven.
Ctrl+C
De structuur van het huidige item kopiëren.
Ctrl+X
Items kopiëren.
Ctrl+B
Informatie over geselecteerde bestanden zoeken op internet.
Ctrl+L
De map van het geselecteerde bestand openen.
Ctrl+R
De bijbehorende vermelding openen in de Register-editor.
Ctrl+Z
Het pad naar een bestand kopiëren (als het item is gekoppeld aan een bestand).
Ctrl+F
De focus verplaatsen naar het zoekveld.
Ctrl+D
De zoekresultaten sluiten.
Ctrl+E
Servicescript uitvoeren.

149
Vergelijken
Ctrl+Alt+O
Het oorspronkelijke/vergelijkende logbestand openen.
Ctrl+Alt+R
De vergelijking annuleren.
Ctrl+Alt+1
Alle items weergeven.
Ctrl+Alt+2
Alleen toegevoegde items weergeven; het logbestand bevat de items die aanwezig zijn in het
huidige logbestand.
Ctrl+Alt+3
Alleen verwijderde items weergeven; het logbestand bevat de items die aanwezig zijn in het
vorige logbestand.
Ctrl+Alt+4
Alleen vervangen items weergeven (inclusief bestanden).
Ctrl+Alt+5
Alleen verschillen tussen logbestanden weergeven.
Ctrl+Alt+C
Vergelijking weergeven.
Ctrl+Alt+N
Het huidige logbestand weergeven.
Ctrl+Alt+P
Het vorige logbestand openen.
Overige
F1
De Help weergeven.
Alt+F4
Het programma afsluiten.
Alt+Shift+F4
Het programma zonder bevestiging afsluiten.
Ctrl+I
Logboekstatistieken.
5.5.2.3 Vergelijken
Met de functie Vergelijken kan de gebruiker twee bestaande logbestanden vergelijken. Het resultaat is een set
items die niet in beide logbestanden voorkomen (d.w.z. die slechts in een van beide bestanden voorkomen). Deze
functie is handig wanneer u wijzigingen in het systeem wilt bijhouden, bijvoorbeeld om schadelijke code op te
sporen.
Als u de functie uitvoert, wordt een nieuw logbestand gemaakt. Dit bestand wordt weergegeven in een nieuw
venster. Klik op Bestand > Logbestand opslaan om een logbestand op te slaan. U kunt logbestanden later openen en
weergeven. Als u een bestaand logbestand wilt openen, klikt u op Bestand > Logbestand openen. In het
hoofdvenster van ESET SysInspector kan altijd maar één logbestand worden weergegeven.
Het voordeel van het vergelijken van twee logboeken is dat u een actief logboek samen met een opgeslagen
logbestand kunt bekijken. Als u logbestanden wilt vergelijken, klikt u op Bestand > Logbestanden vergelijken en
kiest u Bestand selecteren. Het geselecteerde logbestand wordt dan vergeleken met het actieve logbestand in het
hoofdvenster van het programma. In het vergelijkende logboek worden alleen de verschillen tussen die twee
logboeken weergegeven.
OPMERKING: Als u twee logbestanden wilt vergelijken, klikt u op Bestand > Logbestand opslaan om het bestand op
te slaan als een ZIP-bestand. Beide bestanden worden opgeslagen. Als u dit bestand later opent, worden de
logbestanden automatisch vergeleken.
Naast de weergegeven items geeft ESET SysInspector symbolen weer die de verschillen tussen de vergeleken
logbestanden aangeven.
Hier volgt een omschrijving van alle symbolen die kunnen worden weergegeven bij een item:
nieuwe waarde, niet aanwezig in het vorige logbestand
sectie van boomstructuur bevat nieuwe waarden
verwijderde waarde, alleen aanwezig in het vorige logbestand
sectie van boomstructuur bevat verwijderde waarden
waarde/bestand is gewijzigd
sectie van boomstructuur bevat gewijzigde waarden/bestanden
het risiconiveau is afgenomen/was hoger in het vorige logbestand
het risiconiveau is toegenomen/was lager in het vorige logbestand
In de linkerbenedenhoek worden alle symbolen beschreven en ziet u ook de namen van de logbestanden die
worden vergeleken.

150
Een vergelijkend logbestand kunt u opslaan en later opnieuw openen.
Voorbeeld
Genereer een logbestand met systeeminformatie en sla het bestand op met de naam vorigbestand.xml. Nadat er
wijzigingen zijn aangebracht in het systeem, opent u ESET SysInspector en genereert u een nieuw logbestand. Sla
dit logbestand op met de naam huidigbestand.xml.
Als u de verschillen tussen deze twee logbestanden wilt bekijken, klikt u op Bestand > Logbestanden vergelijken. Er
wordt een vergelijkend logbestand gemaakt met de verschillen tussen de twee logbestanden.
U kunt dit ook doen door de volgende parameters te gebruiken op de opdrachtregel:
SysIsnpector.exe huidigbestand.xml vorigbestand.xml
5.5.3 Opdrachtregelparameters
U kunt ESET SysInspector gebruiken om rapporten te genereren vanaf de opdrachtregel. Hierbij kunt u de volgende
parameters gebruiken:
/gen
logbestand rechtstreeks genereren vanuit opdrachtregel zonder GUI uit te voeren
/privacy
logbestand genereren zonder vertrouwelijke gegevens
/zip
logbestand opslaan in gecomprimeerd zip-archief
/silent
voortgangsvenster niet weergeven bij genereren van logbestand vanuit opdrachtregel
/blank
SysInspector starten zonder logbestand te genereren/laden
Voorbeelden
Syntaxis:
Sysinspector.exe [load.xml] [/gen=save.xml] [/privacy] [/zip] [compareto.xml]
Als u een bepaald logbestand direct in de browser wilt weergeven, gebruik dan: SysInspector.exe .\clientlog.xml
Als u een logbestand wilt genereren vanaf de opdrachtregel, gebruik dan: SysInspector.exe /gen=.
\mynewlog.xml
Als u een logbestand rechtstreeks in een gecomprimeerd bestand wilt genereren zonder vertrouwelijke
gegevens, gebruik dan: SysInspector.exe /gen=.\mynewlog.zip /privacy /zip
Als u twee logbestanden wilt vergelijken en verschillen wilt bekijken, gebruik dan: SysInspector.exe new.xml
old.xml
OPMERKING: als de naam van het bestand of de map een spatie bevat, moet u de naam tussen enkele
aanhalingstekens plaatsen.

151
5.5.4 Servicescript
Servicescript is een hulpmiddel waarmee gebruikers van ESET SysInspector eenvoudig ongewenste objecten van
het systeem kunnen verwijderen.
Met Servicescript kan de gebruiker het logbestand van ESET SysInspector in zijn geheel of gedeeltelijk exporteren.
Na het exporteren, kunt u ongewenste objecten markeren om te verwijderen. Vervolgens kunt u het gewijzigde
logbestand uitvoeren om de gemarkeerde objecten te verwijderen.
Servicescript is geschikt voor ervaren gebruikers die eerder een diagnose hebben gesteld van systeemproblemen.
Onjuiste aanpassingen kunnen het besturingssysteem beschadigen.
Voorbeeld
Als u vermoedt dat uw computer is geïnfecteerd met een virus, maar dit virus niet door uw antivirusprogramma
wordt gedetecteerd, volgt u de stapsgewijze instructies hieronder:
1. Voer ESET SysInspector uit om een nieuwe momentopname van het systeem te maken.
2. Selecteer het eerste item in het gedeelte aan de linkerkant (in de bestandsstructuur), druk op Shift en
selecteer het laatste item om alle items te markeren.
3. Klik met de rechtermuisknop op de geselecteerde objecten en selecteer de optie Geselecteerde secties naar
servicescript exporteren.
4. De geselecteerde objecten worden geëxporteerd naar een nieuw logbestand.
5. Nu volgt de belangrijkste stap van deze procedure: open het nieuwe logbestand en wijzig het kenmerk - in +
voor alle objecten die u wilt verwijderen. Zorg dat u geen belangrijke bestanden/objecten van het
besturingssysteem markeert.
6. Open ESET SysInspector, klik op Bestand > Servicescript uitvoeren en voer het pad naar uw script in.
7. Klik op OK om het script uit te voeren.
5.5.4.1 Servicescript genereren
Om een script te genereren, klikt u met de rechtermuisknop op een item in de menustructuur (in het
linkerdeelvenster) in het hoofdvenster van ESET SysInspector. In het contextmenu selecteert u Alle secties naar
servicescript exporteren of Geselecteerde secties naar servicescript exporteren.
OPMERKING: het is niet mogelijk het servicescript te exporteren wanneer twee logbestanden vergeleken worden.
5.5.4.2 Structuur van het servicescript
In de eerste regel van de kop van het script kunt u informatie vinden over de engine-versie (ev), GUI-versie (gv) en
de logbestandsversie (lv). U kunt deze gegevens gebruiken om eventuele wijzigingen op te sporen in het XML-
bestand waarmee het script wordt gegenereerd om eventuele inconsistenties tijdens de uitvoering te voorkomen.
Dit deel van het script moet niet worden gewijzigd.
De rest van het bestand is onderverdeeld in secties waarin items kunnen worden bewerkt (geef de items aan die
door het script moeten worden verwerkt). U markeert items voor verwerking door het minteken ("-") voor een item
te vervangen door een plusteken ("+"). Secties in het script worden van elkaar gescheiden door een witregel.
Iedere sectie heeft een nummer en titel.
01) Uitgevoerde processen
Deze sectie bevat een lijst met alle processen die in het systeem worden uitgevoerd. Ieder proces wordt aangeduid
met het UNC-pad en vervolgens de CRC16-hash-code in sterretjes (*).

152
Voorbeeld:
01) Running processes:
- \SystemRoot\System32\smss.exe *4725*
- C:\Windows\system32\svchost.exe *FD08*
+ C:\Windows\system32\module32.exe *CF8A*
[...]
In dit voorbeeld is een proces, module32.exe, geselecteerd (gemarkeerd met een plusteken, "+"). Het proces wordt
beëindigd bij uitvoering van het script.
02) Geladen modules
In deze sectie staan alle momenteel gebruikte systeemmodules.
Voorbeeld:
02) Loaded modules:
- c:\windows\system32\svchost.exe
- c:\windows\system32\kernel32.dll
+ c:\windows\system32\khbekhb.dll
- c:\windows\system32\advapi32.dll
[...]
In dit voorbeeld is de module khbekhb.dll gemarkeerd met een "+". Wanneer het script wordt uitgevoerd, worden
de processen herkend die die specifieke module gebruiken en deze worden beëindigd.
03) TCP-verbindingen
Deze sectie bevat informatie over bestaande TCP-verbindingen.
Voorbeeld:
03) TCP connections:
- Active connection: 127.0.0.1:30606 -> 127.0.0.1:55320, owner: ekrn.exe
- Active connection: 127.0.0.1:50007 -> 127.0.0.1:50006,
- Active connection: 127.0.0.1:55320 -> 127.0.0.1:30606, owner: OUTLOOK.EXE
- Listening on *, port 135 (epmap), owner: svchost.exe
+ Listening on *, port 2401, owner: fservice.exe Listening on *, port 445
(microsoft-ds), owner: System
[...]
Wanneer het script wordt uitgevoerd, wordt de eigenaar van de socket in de gemarkeerde TCP-verbindingen
gelokaliseerd en wordt de socket gestopt waardoor systeembronnen worden vrijgemaakt.
04) UDP-eindpunten
Deze sectie bevat informatie over bestaande UDP-eindpunten.
Voorbeeld:
04) UDP endpoints:
- 0.0.0.0, port 123 (ntp)
+ 0.0.0.0, port 3702
- 0.0.0.0, port 4500 (ipsec-msft)
- 0.0.0.0, port 500 (isakmp)
[...]
Wanneer het script wordt uitgevoerd, wordt de eigenaar van de socket op de gemarkeerde UDP-eindpunten
geïsoleerd en wordt de socket gestopt.
05) DNS-serververmeldingen
Deze sectie bevat informatie over de huidige DNS-serverconfiguratie.

153
Voorbeeld:
05) DNS server entries:
+ 204.74.105.85
- 172.16.152.2
[...]
Gemarkeerde DNS-serververmeldingen worden verwijderd wanneer u het script uitvoert.
06) Belangrijke registervermeldingen
Deze sectie bevat informatie over belangrijke registervermeldingen.
Voorbeeld:
06) Important registry entries:
* Category: Standard Autostart (3 items)
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HotKeysCmds = C:\Windows\system32\hkcmd.exe
- IgfxTray = C:\Windows\system32\igfxtray.exe
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Google Update = "C:
\Users\antoniak\AppData\Local\Google\Update\GoogleUpdate.exe" /c
* Category: Internet Explorer (7 items)
HKLM\Software\Microsoft\Internet Explorer\Main
+ Default_Page_URL = http://thatcrack.com/
[...]
De gemarkeerde vermeldingen worden bij uitvoering van het script verwijderd, teruggebracht tot waarden van 0
byte of teruggezet op de standaardwaarden. De actie die wordt uitgevoerd op een bepaalde vermelding is
afhankelijk van de categorie van de vermelding en de sleutelwaarde in het specifieke register.
07) Services
Deze sectie bevat de services die binnen het systeem geregistreerd zijn.
Voorbeeld:
07) Services:
- Name: Andrea ADI Filters Service, exe path: c:\windows\system32\aeadisrv.exe,
state: Running, startup: Automatic
- Name: Application Experience Service, exe path: c:
\windows\system32\aelupsvc.dll, state: Running, startup: Automatic
- Name: Application Layer Gateway Service, exe path: c:
\windows\system32\alg.exe, state: Stopped, startup: Manual
[...]
De gemarkeerde services en de bijbehorende onderliggende services worden gestopt en verwijderd wanneer het
script wordt uitgevoerd.
08) Stuurprogramma's
Deze sectie bevat de geïnstalleerde stuurprogramma's.
Voorbeeld:
08) Drivers:
- Name: Microsoft ACPI Driver, exe path: c:\windows\system32\drivers\acpi.sys,
state: Running, startup: Boot
- Name: ADI UAA Function Driver for High Definition Audio Service, exe path: c:
\windows\system32\drivers\adihdaud.sys, state: Running, startup: Manual
[...]
Wanneer u het script uitvoert, worden de geselecteerde stuurprogramma's stopgezet. Houd er rekening mee dat
bepaalde stuurprogramma's zich niet laten stopzetten.

154
09) Belangrijke bestanden
Deze sectie bevat informatie over bestanden die essentieel zijn voor een goede werking van het
besturingssysteem.
Voorbeeld:
09) Critical files:
* File: win.ini
- [fonts]
- [extensions]
- [files]
- MAPI=1
[...]
* File: system.ini
- [386Enh]
- woafont=dosapp.fon
- EGA80WOA.FON=EGA80WOA.FON
[...]
* File: hosts
- 127.0.0.1 localhost
- ::1 localhost
[...]
De geselecteerde items worden verwijderd of teruggezet naar de oorspronkelijke waarden.
10) Geplande taken
Deze sectie bevat informatie over geplande taken.
Voorbeeld:
10) Scheduled tasks
- c:\windows\syswow64\macromed\flash\flashplayerupdateservice.exe
- c:\users\admin\appdata\local\google\update\googleupdate.exe
- c:\users\admin\appdata\local\google\update\googleupdate.exe
- c:\windows\syswow64\macromed\flash\flashplayerupdateservice.exe
- c:\users\admin\appdata\local\google\update\googleupdate.exe /c
- c:
\users\admin\appdata\local\google\update\googleupdate.exe /ua /installsource
- %windir%\system32\appidpolicyconverter.exe
- %windir%\system32\appidcertstorecheck.exe
- aitagent
[...]
5.5.4.3 Servicescripts uitvoeren
Markeer alle gewenste items, sla het script op en sluit het. Voer het bewerkte script uit, direct vanuit het
hoofdvenster van ESET SysInspector, door de optie Servicescript uitvoeren te selecteren in het menu Bestand.
Wanneer u een script opent, wordt het volgende bericht weergegeven: Weet u zeker dat het servicescript %
Scriptname% wilt uitvoeren? Nadat u uw selectie hebt bevestigd, wordt mogelijk nog een bericht weergegeven om
u te waarschuwen dat het servicescript dat u wilt uitvoeren niet ondertekend is. Klik op Uitvoeren om het script te
starten.
In een dialoogvenster wordt de geslaagde uitvoering van het script bevestigd.
Als het script slechts gedeeltelijk kan worden uitgevoerd, wordt een venster weergegeven met het volgende
bericht: Het servicescript is gedeeltelijk uitgevoerd. Wilt u het foutrapport weergeven? Selecteer Ja om een
uitgebreid foutrapport weer te geven met alle bewerkingen die niet zijn uitgevoerd.
Als het script niet wordt herkend, wordt een dialoogvenster met het volgende bericht weergegeven: Het
geselecteerde servicescript is niet ondertekend. Wanneer u niet-ondertekende en onbekende scripts uitvoert,

155
kunnen de computergegevens beschadigd raken. Weet u zeker dat u het script en de acties wilt uitvoeren? Dit kan
worden veroorzaakt door inconsistenties in het script (beschadigde kop, beschadigde sectietitel, ontbrekende
witregel tussen secties, enz.). U kunt het scriptbestand opnieuw openen en de fouten in het script corrigeren of een
nieuw servicescript maken.
5.5.5 Veelgestelde vragen
Zijn er beheerdersrechten nodig om ESET SysInspector uit te voeren?
Hoewel er geen beheerdersrechten nodig zijn om ESET SysInspector uit te voeren, zijn bepaalde gegevens die het
programma verzamelt alleen toegankelijk met een beheerdersaccount. Als u het programma uitvoert met een
gewoon account of een account met beperkte rechten, worden er minder gegevens verzameld over de
besturingsomgeving.
Wordt er een logbestand bijgehouden door ESET SysInspector?
ESET SysInspector kan een logbestand maken van de configuratie van uw computer. Als u een logbestand wilt
opslaan, kiest u Bestand > Logbestand opslaan in het hoofdprogrammavenster. Logbestanden worden standaard
opgeslagen met de indeling XML. Standaard worden bestanden opgeslagen in de map %GEBRUIKERSPROFIEL%\Mijn
documenten\. De bestanden krijgen een naam in de volgende notatie: "SysInpsector-%COMPUTERNAAM%-
JJMMDD-UUMM.XML". U kunt de locatie en naam van het logbestand desgewenst wijzigen voordat u het opslaat.
Hoe kan ik het logbestand van ESET SysInspector weergeven?
Als u een logbestand wilt bekijken dat door ESET SysInspector is gemaakt, start u het programma en kiest u Bestand
> Logbestand openen in het hoofdprogrammavenster. U kunt logbestanden ook naar ESET SysInspector slepen. Als u
regelmatig logbestanden van ESET SysInspector moet bekijken, is het verstandig op het bureaublad een
snelkoppeling te maken naar het bestand SYSINSPECTOR.EXE. U kunt logbestanden dan snel weergeven door deze
naar de snelkoppeling op het bureaublad te slepen. Uit beveiligingsoverwegingen is het slepen van bestanden
tussen vensters met verschillende beveiligingsrechten in Windows Vista/7 mogelijk niet toegestaan.
Is er een specificatie beschikbaar voor de indeling van de logbestanden? Of misschien een SDK?
Op dit moment is er geen specificatie beschikbaar en evenmin een SDK. De reden hiervoor is dat het programma
nog steeds in ontwikkeling is. Als het programma is vrijgegeven, zullen deze voorzieningen mogelijk worden
toegevoegd. Dit is echter afhankelijk van de feedback en wensen van klanten.
Hoe evalueert ESET SysInspector het risico dat een bepaald object vormt?
In de meeste gevallen worden in ESET SysInspector risiconiveaus toegewezen aan objecten (bestanden, processen,
registersleutels, enz.) op basis van een reeks heuristische regels die de kenmerken van elk object onderzoeken en
vervolgens een wegingsfactor voor schadelijke activiteiten toekennen. Op basis van deze heuristiek krijgen
objecten een risiconiveau toegewezen in het bereik 1 - Goed (groen) tot 9 - Riskant (rood). In het navigatievenster
aan de linkerkant hebben secties een bepaalde kleur, die is gebaseerd op het object met het hoogste risiconiveau
in de sectie.
Betekent het risiconiveau "6 - Onbekend (rood)" dat een object gevaarlijk is?
Het is niet mogelijk om uitsluitend op basis van de beoordelingen van ESET SysInspector vast te stellen of een
object schadelijk is. Hiervoor moet de hulp worden ingeroepen van een expert. Het doel van ESET SysInspector is
om een systeem snel te kunnen controleren op afwijkingen, zodat een expert vervolgens gericht nader onderzoek
kan uitvoeren als er dubieuze objecten zijn aangetroffen.
Waarom maakt ESET SysInspector verbinding met internet?
Net als veel andere toepassingen is ESET SysInspector voorzien van een "certificaat" met een digitale handtekening
dat aantoont dat de software daadwerkelijk afkomstig is van ESET en niet is aangepast. Om het certificaat te
controleren, maakt het besturingssysteem verbinding met een certificeringsinstantie die de identiteit van de
softwarefabrikant controleert. Dit is gebruikelijk voor alle digitaal ondertekende programma's die werken met
Microsoft Windows.

156
Wat is Anti-Stealth-technologie?
De Anti-Stealth-technologie detecteert op effectieve wijze rootkits.
Als het systeem wordt aangevallen door schadelijke code die zich gedraagt als een rootkit, kunnen de gegevens van
de gebruiker verloren raken of gestolen worden. Zonder een hulpmiddel dat speciaal is bedoeld voor het
detecteren van rootkits, is het vrijwel onmogelijk dit type bedreiging te bestrijden.
Waarom zijn er soms bestanden gemarkeerd met "Ondertekend door Microsoft", maar hebben deze
wel een andere bedrijfsnaam?
Bij de identificatie van de digitale handtekening van een uitvoerbaar bestand controleert ESET SysInspector eerst of
er een digitale handtekening in het bestand is ingesloten. Als er een digitale handtekening is gevonden, wordt het
bestand gevalideerd met die informatie. Als er geen digitale handtekening is gevonden, wordt er gezocht naar het
overeenkomstige CAT-bestand (Beveiligingscatalogus: %systemroot%\system32\catroot) dat informatie bevat over
het uitvoerbare bestand dat wordt verwerkt. Als het relevante CAT-bestand wordt gevonden, wordt de digitale
handtekening van dat CAT-bestand toegepast bij de validatie van het uitvoerbare bestand.
Daarom zijn er soms bestanden "Ondertekend door Microsoft", maar hebben deze een andere bedrijfsnaam.
Voorbeeld:
Windows 2000 bevat de toepassing HyperTerminal op de locatie C:\Program Files\Windows NT. Het uitvoerbare
bestand van de hoofdtoepassing is niet digitaal ondertekend, maar wordt door ESET SysInspector gemarkeerd als
een bestand dat is ondertekend door Microsoft. De reden hiervoor is dat er in C:
\WINNT\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\sp4.cat wordt verwezen naar C:\Program
Files\Windows NT\hypertrm.exe (het uitvoerbare bestand van de toepassing HyperTerminal), en sp4.cat is digitaal
ondertekend door Microsoft.

157
5.6 Opdrachtregel
De antivirusmodule van ESET Smart Security Premium kan worden gestart via de opdrachtregel, handmatig (met de
opdracht 'ecls') of via een batchbestand ('bat'). Verbruik van ESET-opdrachtregelscanner:
ecls [OPTIES..] BESTANDEN..
De volgende parameters en schakelaars kunnen worden gebruikt tijdens het uitvoeren van de scanner op aanvraag
vanaf de opdrachtregel:
Opties
/base-dir=MAP
modules laden vanuit MAP
/quar-dir=MAP
MAP in quarantaine plaatsen
/exclude=MASKER
bestanden die overeenkomen met MASKER uitsluiten van scannen
/subdir
submappen scannen (standaard)
/no-subdir
submappen niet scannen
/max-subdir-level=NIVEAU
maximaal subniveau voor mappen binnen mappen voor scannen
/symlink
symbolische koppelingen volgen (standaard)
/no-symlink
symbolische koppelingen overslaan
/ads
ADS scannen (standaard)
/no-ads
ADS niet scannen
/log-file=BESTAND
logboekuitvoer vastleggen in BESTAND
/log-rewrite
uitvoerbestand overschrijven (standaard - toevoegen)
/log-console
uitvoer registreren in console (standaard)
/no-log-console
uitvoer niet registreren in console
/log-all
ook schone bestanden opnemen in logbestand
/no-log-all
schone bestanden niet opnemen in logbestand (standaard)
/aind
activiteitenindicator weergeven
/auto
lokale schijven scannen en automatisch opschonen
Scanneropties
/files
bestanden scannen (standaard)
/no-files
bestanden niet scannen
/memory
geheugen scannen
/boots
opstartsectoren scannen
/no-boots
opstartsectoren niet scannen (standaard)
/arch
archieven scannen (standaard)
/no-arch
archieven niet scannen
/max-obj-size=GROOTTE
alleen bestanden scannen die kleiner zijn dan GROOTTE megabytes (standaard 0 =
onbeperkt)
/max-arch-level=NIVEAU
maximaal subniveau voor archieven binnen archieven (geneste archieven) voor
scannen
/scan-timeout=LIMIET
archieven scannen gedurende maximaal LIMIET seconden
/max-arch-size=GROOTTE
bestanden in een archief alleen scannen als deze kleiner zijn dan GROOTTE
(standaard 0 = onbeperkt)
/max-sfx-size=GROOTTE
bestanden in zelfuitpakkende archieven alleen scannen als deze kleiner zijn dan
GROOTTE megabytes (standaard 0 = onbeperkt)
/mail
e-mailbestanden scannen (standaard)
/no-mail
e-mailbestanden niet scannen
/mailbox
postvakken scannen (standaard)
/no-mailbox
postvakken niet scannen
/sfx
zelfuitpakkende archieven scannen (standaard)
/no-sfx
zelfuitpakkende archieven niet scannen
/rtp
software voor runtime-compressie scannen (standaard)
/no-rtp
software voor runtime-compressie niet scannen
/unsafe
scannen op mogelijk onveilige toepassingen

158
/no-unsafe
niet scannen op potentieel onveilige toepassingen (standaard)
/unwanted
scannen op mogelijk ongewenste toepassingen
/no-unwanted
niet scannen op potentieel ongewenste toepassingen (standaard)
/suspicious
scannen op verdachte toepassingen (standaard)
/no-suspicious
niet scannen op verdachte toepassingen
/pattern
kenmerken gebruiken (standaard)
/no-pattern
geen kenmerken gebruiken
/heur
heuristiek inschakelen (standaard)
/no-heur
heuristiek uitschakelen
/adv-heur
geavanceerde heuristiek inschakelen (standaard)
/no-adv-heur
geavanceerde heuristiek uitschakelen
/ext=EXTENSIES
alleen EXTENSIES scannen die van elkaar worden gescheiden door dubbele punt
/ext-exclude=EXTENSIES
EXTENSIES, door dubbele punt gescheiden, uitsluiten van scannen
/clean-mode=MODUS
MODUS voor opschonen gebruiken voor geïnfecteerde objecten
De volgende opties zijn beschikbaar:
none - er vindt geen automatische opschoning plaats.
standard (standaard) - ecls.exe zal automatisch proberen geïnfecteerde bestanden op te
schonen of te verwijderen.
strict - ecls.exe zal automatisch proberen alle geïnfecteerde bestanden op te schonen of
te verwijderen zonder tussenkomst van de gebruiker (u wordt niet gevraagd voordat
bestanden worden verwijderd).
rigorous - ecls.exe verwijdert bestanden zonder ze proberen op te schonen ongeacht om
welk bestand het gaat.
delete - ecls.exe verwijdert bestanden zonder ze te proberen op te schonen, maar zal
geen gevoelige bestanden verwijderen zoals Windows-systeembestanden.
/quarantine
geïnfecteerde bestanden (indien opgeschoond) naar quarantaine kopiëren
(aanvulling op de actie die wordt uitgevoerd bij het opschonen)
/no-quarantine
geïnfecteerde bestanden niet naar quarantaine kopiëren
Algemene opties
/help
help weergeven en afsluiten
/version
versiegegevens weergeven en afsluiten
/preserve-time
tijdstempel laatste toegang bewaren
Afsluitcodes
0
geen bedreiging gevonden
1
bedreiging gevonden en opgeschoond
10
sommige bestanden konden niet worden gescand (zijn mogelijk bedreigingen)
50
bedreiging gevonden
100
fout
OPMERKING
Afsluitcodes groter dan 100 betekenen dat het bestand niet is gescand en dus geïnfecteerd kan zijn.

159
6. Woordenlijst
6.1 Typen infiltraties
Bij een infiltratie probeert schadelijke software de computer van een gebruiker binnen te dringen en/of te
beschadigen.
6.1.1 Virussen
Een computervirus is een schadelijke code die wordt toegevoegd aan bestaande bestanden op uw computer. De
naam 'virussen' verwijst naar biologische virussen, omdat deze vergelijkbare methoden gebruiken om zich van
computer tot computer te verspreiden. De term 'virus' wordt vaak onterecht gebruikt voor elk type bedreiging. Hier
komt echter langzaam verandering in doordat de nieuwe term 'malware' (malicious software = schadelijke
software), die de lading beter dekt, in zwang is gekomen.
Computervirussen hebben het voornamelijk voorzien op uitvoerbare bestanden en documenten. Een
computervirus werkt als volgt: Wanneer een geïnfecteerd bestand wordt uitgevoerd, wordt eerst de schadelijke
code aangeroepen en uitgevoerd voordat de oorspronkelijke toepassing wordt uitgevoerd. Een virus kan in principe
alle bestanden infecteren waarvoor de huidige gebruiker schrijfrechten heeft.
Het doel en het gevaar van computervirussen kan variëren. Sommige virussen zijn uiterst gevaarlijk omdat ze
worden gebruikt om opzettelijk bestanden van een vaste schijf te verwijderen. Andere virussen veroorzaken geen
schade, maar zijn alleen ontwikkeld om de gebruiker te irriteren en de technische vaardigheden van de
ontwikkelaars tentoon te spreiden.
Als uw computer is geïnfecteerd met een virus en opschonen niet mogelijk is, verzendt u het naar het
onderzoekslaboratorium van ESET voor analyse. In bepaalde gevallen worden geïnfecteerde bestanden zodanig
gewijzigd dat opschonen niet meer mogelijk is en dat de bestanden moeten worden vervangen door schone
exemplaren.
6.1.2 Wormen
Een computerworm is een programma met schadelijke code dat hostcomputers aanvalt en zich verspreidt via een
netwerk. Het belangrijkste verschil tussen een virus en een worm is dat een worm in staat is zichzelf te verspreiden.
Wormen zijn niet afhankelijk van hostbestanden (of opstartsectoren). Wormen verspreiden zich via e-mailadressen
in uw lijst met contactpersonen of maken gebruik van beveiligingsproblemen in netwerktoepassingen.
Wormen zijn daarom veel hardnekkiger dan computervirussen. Door het massale internetgebruik kunnen wormen
zich binnen enkele uren of zelfs minuten nadat ze in omloop zijn gebracht, over de hele wereld verspreiden.
Doordat wormen zich zelfstandig met grote snelheid kunnen verspreiden, zijn ze gevaarlijker dan andere typen
malware.
Als een worm in een systeem wordt geactiveerd, kan dat leiden tot verschillende problemen: de worm kan
bestanden verwijderen, de prestaties van het systeem verminderen of zelfs programma's deactiveren. Door zijn
eigenschappen is de worm geschikt als 'transportmiddel' voor andere typen infiltraties.
Als uw computer is geïnfecteerd met een worm, adviseren wij u de geïnfecteerde bestanden te verwijderen omdat
ze waarschijnlijk schadelijke code bevatten.

160
6.1.3 Trojaanse paarden
Volgens de traditionele definitie zijn Trojaanse paarden bedreigingen die zichzelf proberen voor te doen als nuttige
programma's en die vervolgens door nietsvermoedende gebruikers worden uitgevoerd.
Omdat deze categorie erg breed is, worden Trojaanse paarden vaak verdeeld in een aantal subcategorieën:
Downloader – Schadelijke programma's waarmee andere bedreigingen van het internet kunnen worden
gedownload.
Dropper – Schadelij ke programma's waarmee andere typen malware kunnen worden geïnstalleerd op
geïnfecteerde computers.
Backdoor – Schadelij ke programma's die communiceren met externe aanvallers, waardoor zij toegang tot de
computer kunnen krijgen en deze kunnen overnemen.
Keylogger – (keystroke logger): een programma waarmee elke toetsaanslag van een gebruiker wordt
geregistreerd, waarna de gegevens naar externe aanvallers worden verzonden.
Dialer – Een schadelijk programma waarmee automatisch verbinding wordt gemaakt met nummers met hoge
tarieven in plaats van de internetprovider van de gebruiker. Het is vrijwel onmogelijk te merken dat er een
nieuwe verbinding tot stand is gebracht. Dialers kunnen alleen schade veroorzaken voor gebruikers met
inbelmodems, die niet vaak meer worden gebruikt.
Als er een Trojaans paard op uw computer wordt gedetecteerd, adviseren wij u het bestand te verwijderen, omdat
het waarschijnlijk alleen maar schadelijke code bevat.
6.1.4 Rootkits
Rootkits zijn schadelijke programma's waarmee internetaanvallers onbeperkte toegang tot een systeem kunnen
krijgen, terwijl hun aanwezigheid verborgen blijft. Nadat rootkits zich toegang tot een systeem hebben verschaft
(meestal door gebruik te maken van een systeembeveiligingsprobleem), gebruiken ze functies in het
besturingssysteem om te voorkomen dat ze worden gedetecteerd met de antivirussoftware: ze verbergen
processen, bestanden en Windows-registergegevens. Hierdoor is het vrijwel onmogelijk rootkits te detecteren met
de gebruikelijke testmethoden.
Er zijn twee detectieniveaus om rootkits te voorkomen:
1. Detectie wanneer ze toegang tot het systeem proberen te krijgen: Op dat moment zijn ze nog niet aanwezig
en dus inactief. Met de meeste antivirussystemen kunnen rootkits op dit niveau worden geëlimineerd
(aangenomen dat dergelijke bestanden als geïnfecteerde bestanden worden herkend door het
antivirussysteem).
2. Detectie wanneer ze zijn verborgen voor de gebruikelijke testmethoden: Gebruikers van ESET Smart Security
Premium kunnen gebruikmaken van de Anti-Stealth-technologie, waarmee actieve rootkits kunnen worden
gedetecteerd en verwijderd.
6.1.5 Adware
Adware is een afkorting voor door advertenties ondersteunde software. Programma's waarin reclamemateriaal
wordt weergegeven vallen onder deze categorie. Adwareprogramma's openen vaak automatisch een nieuw pop-
upvenster met reclame in een internetbrowser of wijzigen de startpagina van de browser. Adware is vaak
opgenomen in freewareprogramma's, waardoor de makers ervan de ontwikkelkosten van hun (gewoonlijk nuttige)
toepassingen kunnen terugverdienen.
Adware zelf is niet gevaarlijk. Gebruikers worden alleen lastiggevallen met advertenties. Het gevaar schuilt in het
feit dat adware ook traceringsfuncties kan uitvoeren (net als spyware).
Als u besluit een freewareproduct te gebruiken, let dan speciaal op het installatieprogramma. Het
installatieprogramma waarschuwt u gewoonlijk bij de installatie van een extra adwareprogramma. Vaak kunt u deze
annuleren en het programma installeren zonder adware.
In sommige gevallen kunnen programma's niet worden geïnstalleerd zonder adware of wordt hun functionaliteit
beperkt. Dit betekent dat adware vaak op 'legale' wijze toegang heeft tot het systeem, omdat gebruikers hiermee
akkoord zijn gegaan. In dat geval is het beter het zekere voor het onzekere te nemen. Als er op uw computer een

161
bestand als adware wordt geïdentificeerd, is het raadzaam dit te verwijderen, aangezien de kans groot is dat dit
schadelijke code bevat.
6.1.6 Spyware
Deze categorie omvat alle toepassingen waarmee persoonlijke gegevens worden verzonden zonder dat de
gebruiker daar toestemming voor heeft gegeven of zonder dat de gebruiker zich ervan bewust is. Spyware maakt
gebruik van traceerfuncties om verschillende statistische gegevens te verzenden, zoals websites die de gebruiker
heeft bezocht, e-mailadressen van de contactpersonen van de gebruiker of toetsaanslagen van de gebruiker.
De makers van spyware stellen dat deze toepassingen zijn bedoeld om de wensen en interesses van de gebruiker te
inventariseren, zodat ze hun reclameboodschappen beter op de gebruiker kunnen afstemmen. Het probleem is
echter dat er geen duidelijk onderscheid tussen nuttige en schadelijke toepassingen kan worden gemaakt.
Bovendien kan niemand garanderen dat er geen misbruik van de gegevens wordt gemaakt. Voorbeelden van
gegevens die kunnen worden verzameld met spywaretoepassingen zijn beveiligingscodes, pincodes,
bankrekeningnummers, enzovoort. Spyware wordt vaak bij gratis versies van een programma gevoegd door de
maker van het programma om inkomsten te genereren of om de gebruiker ertoe te bewegen de software aan te
schaffen. Vaak worden gebruikers tijdens de installatie van een programma geïnformeerd over de aanwezigheid
van spyware om ze ertoe te bewegen een betaalde versie zonder spyware aan te schaffen.
Voorbeelden van bekende freewareproducten waarbij spyware wordt meegeleverd, zijn clienttoepassingen van
P2P-netwerken (peer-to-peer). Spyfalcon of Spy Sheriff (en vele andere programma's) behoren tot een speciale
subcategorie spywareprogramma's. Deze programma's doen zich voor als antispywareprogramma's, maar zijn in
feite zelf spywareprogramma's.
Als er op uw computer een bestand als spyware wordt geïdentificeerd, is het raadzaam dit te verwijderen,
aangezien de kans groot is dat het schadelijke code bevat.
6.1.7 Compressiesoftware
Compressiesoftware is een zelfuitpakkend uitvoerbaar bestand voor runtime waarin verschillende soorten malware
in één pakket zijn samengevoegd.
Enkele veelgebruikte compressieprogramma's zijn UPX, PE_Compact, PKLite en ASPack. Bepaalde malware kan
anders worden gedetecteerd wanneer deze is gecomprimeerd met andere compressiesoftware. De 'kenmerken'
van compressiesoftware kunnen na verloop van tijd veranderen, zodat het moeilijker is om de malware te
detecteren en verwijderen.
6.1.8 Potentieel onveilige toepassingen
Er zijn veel legitieme programma's die zijn bedoeld om het beheer van computers in een netwerk te
vereenvoudigen. In de verkeerde handen kunnen deze programma's echter worden gebruikt om schadelijke
praktijken uit te oefenen. ESET Smart Security Premium biedt de optie dergelijke bedreigingen te detecteren.
Potentieel onveilige toepassingen is de classificatie voor commerciële, legitieme software. Deze categorie omvat
hulpprogramma's voor externe toegang, toepassingen voor het kraken van wachtwoorden, keyloggers
(programma's die elke toetsaanslag van een gebruiker registreren), enzovoort.
Als u merkt dat er een potentieel onveilige toepassing (die u niet zelf hebt geïnstalleerd) op uw computer actief is,
neemt u contact op met de netwerkbeheerder of verwijdert u de toepassing.

162
6.1.9 Potentieel ongewenste toepassingen
Grayware (of potentieel ongewenste toepassingen) is een brede categorie software die niet ondubbelzinnig
schadelijk is als andere typen malware, zoals virussen en Trojaanse paarden. Grayware kan echter aanvullende
ongewenste software installeren, het gedrag van het digitale apparaat wijzigen, of activiteiten uitvoeren die de
gebruiker niet heeft goedgekeurd of had verwacht.
Categorieën die tot grayware worden gerekend, zijn onder andere: software die advertenties weergeeft,
downloadpakketten, diverse taakbalken voor browsers, software met misleidend gedrag, bundleware, trackware of
andere twijfelachtige software, of software die gebruikmaakt van illegale of op zijn minst onethische zakelijke
praktijken (ondanks dat de software er legitiem uitziet) en door een eindgebruiker mogelijk als ongewenst wordt
beschouwd wanneer die weet wat de software kan doen als die zou worden geïnstalleerd.
Een potentieel onveilige toepassing is er een die op zich legitieme software is (mogelijk in de handel verkrijgbaar),
maar die door een aanvaller kan worden misbruikt. Detectie van deze typen applicaties kan worden ingeschakeld of
uitgeschakeld door gebruikers van ESET-software.
Er kunnen zich situaties voordoen waarin een gebruiker van mening is dat de voordelen van een potentieel
ongwenste toepassingen opwegen tegen de risico's ervan. ESET geeft om deze reden dergelijke toepassingen een
lagere risicocategorie in vergelijking tot andere typen schadelijke software, zoals Trojaanse paarden of wormen.
Waarschuwing - Potentiële bedreiging gevonden
Als er een potentieel ongewenste toepassing wordt gedetecteerd, kunt u beslissen welke actie moet worden
ondernomen:
1. Opschonen/Verbinding verbreken: met deze optie wordt de actie beëindigd en wordt voorkomen dat de
bedreiging uw systeem binnenkomt.
2. Negeren: Met deze optie kan een potentiële dreiging uw systeem binnendringen.
3. Als u wilt toestaan dat de toepassing in de toekomst zonder onderbreking op uw computer wordt uitgevoerd,
klikt u op Geavanceerde opties en schakelt u het selectievakje in naast Uitsluiten van detectie.
Wanneer een potentieel ongewenste applicatie wordt gedetecteerd die niet kan worden opgeschoond, verschijnt
het bericht Adres werd geblokkeerd. Voor meer informatie over deze gebeurtenis navigeert u naar Hulpmiddelen >
Logbestanden > Gefilterde websites in het hoofdmenu.

163
Potentieel ongewenste toepassingen - Instellingen
Tijdens de installatie van uw ESET-product kunt u kiezen of u detectie van potentieel ongewenste toepassingen wilt
inschakelen, zoals hieronder aangegeven:
WAARSCHUWING
Potentieel ongewenste toepassingen kunnen adware of werkbalken installeren, of andere ongewenste en
onveilige programmafuncties bevatten.
Deze instellingen kunnen op elk moment worden aangepast in uw programma-instellingen. Volg deze instructies
als u de detectie van potentieel ongewenste, onveilige of verdachte toepassingen wilt uitschakelen:
1. Open uw ESET-product. Mijn ESET-product openen
2. Druk op de toets F5 om Geavanceerde instellingen te openen.
3. Klik op Antivirus en schakel Detectie van potentieel ongewenste toepassingen inschakelen, Detectie van
potentieel onveilige toepassingen inschakelen en Detectie van verdachte toepassingen inschakelen in of uit
op basis van uw voorkeuren. Bevestig uw keuze door op OK te klikken.

164
Potentieel ongewenste toepassingen - Softwarewrappers
Een softwarewrapper is een speciaal soort aanpassing van een toepassing die door bepaalde websites wordt
gebruikt waarop bestanden als downloads worden aangeboden. Een hulpprogramma van derden installeert het
programma dat u wilt downloaden maar voegt er extra software aan toe, zoals werkbalken of adware. De extra
software kan ook de startpagina van uw webbrowser en zoekinstellingen wijzigen. Websites waarop dergelijke
bestanden worden gehost melden deze wijzigingen vaak niet aan de leverancier van de software en degenen die
de bestanden downloaden. Vaak wordt de optie om uit te schrijven ook verborgen. Om deze redenen classificeert
ESET softwarewrappers als een type potentieel ongewenste toepassing, zodat gebruikers kunnen kiezen of ze de
download accepteren of niet.
Raadpleeg dit artikel in de ESET-kennisbank voor een bijgewerkte versie van deze Help-pagina.
6.1.10 Botnet
Een bot, of een webrobot, is een geautomatiseerd malwareprogramma dat netwerkadresblokken scant en
kwetsbare computers infecteert. Hierdoor kunnen hackers de controle over een groot aantal computers tegelijk
overnemen en ze als bots (ook bekend als zombies) inzetten. Hackers gebruiken bots doorgaans om grote aantallen
computers te infecteren, zodat er een netwerk met bots, ook wel bekend als een botnet, ontstaat. Wanneer uw
computer eenmaal deel uitmaakt van een botnet kan deze worden ingezet voor DDoS-aanvallen (Distributed Denial
of Service) of als proxy, en kan uw computer ook worden gebruikt om geautomatiseerde taken via internet uit te
voeren, zonder dat u dat weet (bijvoorbeeld voor het verzenden van spam, virussen of om persoonlijke en privé-
informatie te stelen, zoals bankgegevens of creditcardnummers).

165
6.2 Typen externe aanvallen
Aanvallers beschikken over een groot aantal speciale methoden om de veiligheid van externe systemen in gevaar
te brengen. Deze methoden kunnen in verschillende categorieën worden onderverdeeld.
6.2.1 DoS-aanvallen
DoS, of Denial of Service, is een poging een computer of netwerk niet langer beschikbaar te maken voor de beoogde
gebruikers. De communicatie tussen getroffen gebruikers is geblokkeerd en kan niet langer worden voortgezet op
een functionele wijze. Computers die worden blootgesteld aan DoS-aanvallen moeten gewoonlijk opnieuw worden
opgestart om weer correct te kunnen werken.
In de meeste gevallen zijn webservers het doelwit en is het de bedoeling dat zij gedurende een bepaalde periode
niet langer beschikbaar zijn voor gebruikers.
6.2.2 DNS Poisoning
Via DNS Poisoning (DNS staat voor Domain Name Server) kunnen hackers valse gegevens aanbieden aan de DNS-
server van een computer en ervoor zorgen dat deze gegevens als legitiem en authentiek worden geaccepteerd. De
valse informatie wordt gedurende enige tijd in de cache opgeslagen, zodat hackers DNS-reacties voor IP-adressen
kunnen herschrijven. Het resultaat is dat gebruikers die proberen toegang te krijgen tot websites op het internet
computervirussen en wormen downloaden in plaats van de oorspronkelijke inhoud van de site.
6.2.3 Wormaanvallen
Een computerworm is een programma met schadelijke code dat hostcomputers aanvalt en zich verspreidt via een
netwerk. Netwerkwormen maken gebruik van beveiligingsproblemen in verschillende toepassingen. Door het
massale gebruik van het internet kunnen wormen zich enkele uren nadat ze in omloop zijn gebracht, over de hele
wereld verspreiden.
De meeste wormaanvallen (Sasser, SqlSlammer) kunnen worden voorkomen door de
standaardbeveiligingsinstellingen in de firewall te gebruiken, of door onbeveiligde en ongebruikte poorten te
blokkeren. Het is ook van essentieel belang dat u de recentste beveiligingspatches op uw systeem installeert.
6.2.4 Port Scanning
Port Scanning wordt gebruikt om te bepalen welke computerpoorten open zijn op een netwerkhost. Een
poortscanner is software waarmee dergelijke poorten kunnen worden gedetecteerd.
Een computerpoort is een virtueel punt voor de verwerking van inkomende en uitgaande gegevens.
Computerpoorten zijn van cruciaal belang vanuit beveiligingsoogpunt. In een groot netwerk kunnen potentiële
beveiligingsproblemen worden gedetecteerd op basis van de gegevens die met poortscanners worden verzameld.
In dergelijke gevallen worden poortscanners voor legitieme doeleinden gebruikt.
Port Scanning wordt echter ook vaak gebruikt door hackers die de beveiliging in gevaar willen brengen. Eerst
verzenden ze pakketten naar elke poort. Afhankelijk van de reactie is het mogelijk te bepalen welke poorten in
gebruik zijn. Het scannen zelf veroorzaakt geen schade, maar houd er rekening mee dat deze activiteit potentiële
beveiligingsproblemen kan blootleggen en aanvallers in staat kan stellen externe computers over te nemen.
Netwerkbeheerders wordt geadviseerd alle ongebruikte poorten te blokkeren en alle gebruikte poorten te
beveiligen tegen onbevoegde toegang.

166
6.2.5 TCP-desynchronisatie
TCP-desynchronisatie is een aanvalsmethode die wordt gebruikt om TCP-kapingen uit te voeren. TCP-
desynchronisatie wordt geactiveerd door een proces waarbij het volgnummer in inkomende pakketten afwijkt van
het verwachte volgnummer. Pakketten met een onverwacht volgnummer worden verwijderd (of opgeslagen in de
bufferopslag als ze aanwezig zijn in het huidige communicatievenster).
Bij desynchronisatie worden ontvangen pakketten door beide communicatie-eindpunten verwijderd. Op dit punt
kunnen externe aanvallers infiltreren door pakketten met correcte volgnummers te verzenden. De aanvallers zijn
zelfs in staat de communicatie te manipuleren of te wijzigen.
TCP-kapingen zijn erop gericht de communicatie tussen servers en clients, of peer-to-peer-communicatie te
verstoren. Veel aanvallen kunnen worden voorkomen door verificatie voor elk TCP-segment te gebruiken. U wordt
ook geadviseerd de aanbevolen configuraties voor uw netwerkapparaten te gebruiken.
6.2.6 SMB Relay
SMB Relay en SMB Relay 2 zijn speciale programma's waarmee externe computers kunnen worden aangevallen.
Deze programma's maken gebruik van het SMB-protocol (Server Message Block) voor bestandsdeling, dat is gelaagd
op het NetBIOS. Een gebruiker die een map of directory binnen het LAN deelt, gebruikt meestal dit protocol voor
bestandsdeling.
Binnen lokale netwerkcommunicatie worden wachtwoordhashes uitgewisseld.
SMB Relay ontvangt een verbinding op UDP-poort 139 en 445, relayeert de pakketten die door de client en de server
zijn uitgewisseld en wijzigt de pakketten. Nadat de verbinding tot stand is gebracht en de verificatie is uitgevoerd,
wordt de verbinding met de client verbroken. SMB Relay maakt een nieuw virtueel IP-adres. Het nieuwe adres is
toegankelijk met behulp van de opdracht 'net use \\192.168.1.1'. Vervolgens kan het adres door alle Windows-
netwerkfuncties worden gebruikt. SMB Relay relayeert communicatie via het SMB-protocol, met uitzondering van
onderhandelingen en verificatie. Externe aanvallers kunnen het IP-adres gebruiken zolang de clientcomputer is
verbonden.
SMB Relay 2 werkt volgens hetzelfde principe als SMBRelay, alleen gebruikt SMB Relay 2 NetBIOS-namen in plaats
van IP-adressen. Beide kunnen 'man-in-het-midden'-aanvallen uitvoeren. Hierbij kunnen externe aanvallers
ongemerkt berichten die tussen twee communicatie-eindpunten worden uitgewisseld, lezen, invoegen en
wijzigen. Computers die aan dergelijke aanvallen worden blootgesteld, reageren vaak niet meer of worden
onverwacht opnieuw opgestart.
Wij adviseren u verificatiewachtwoorden of -sleutels te gebruiken om deze aanvallen te voorkomen.
6.2.7 ICMP-aanvallen
ICMP (Internet Control Message Protocol) is een populair en veelgebruikt internetprotocol. Het wordt hoofdzakelijk
gebruikt door netwerkcomputers om allerlei foutberichten te verzenden.
Externe aanvallers proberen misbruik te maken van de zwakke punten van het ICMP-protocol. Het ICMP-protocol is
ontworpen voor communicatie in één richting, zonder dat verificatie is vereist. Hierdoor kunnen externe aanvallers
zogenaamde DoS-aanvallen (Denial of Service) activeren, of aanvallen die onbevoegden toegang geven tot
inkomende en uitgaande pakketten.
Typische voorbeelden van een ICMP-aanval zijn ping flood, ICMP_ECHO flood en smurf attack. Computers die
worden blootgesteld aan een ICMP-aanval zijn aanzienlijk trager (dit geldt voor alle toepassingen waarbij gebruik
wordt gemaakt van het internet) en hebben problemen met het maken van verbinding met het internet.

167
6.3 ESET Technology
6.3.1 Exploit Blocker
Exploit blocker is ontworpen om de beveiliging te verstevigen van veelbedreigde toepassingen zoals webbrowsers,
PDF-readers, e-mailclients en MS Office-onderdelen. Het werkt door het gedrag van processen te gecontroleren op
verdachte activiteiten die kunnen wijzen op misbruik.
Wanneer Exploit Blocker een verdacht proces identificeert, kan Exploit Blocker dit proces onmiddellijk stopzetten
en gegevens over de bedreiging vastleggen. Deze gegevens worden vervolgens verzonden naar het ThreatSense-
cloudsysteem. De gegevens worden verwerkt door het onderzoekslaboratorium van ESET en gebruikt om alle
gebruikers beter te kunnen beschermen tegen onbekende bedreigingen en zero-day-aanvallen (nieuw
uitgebrachte malware waarvoor nog geen voorgeconfigureerde oplossing beschikbaar is).
6.3.2 Geavanceerde geheugenscanner
Geavanceerde geheugenscanner werkt in combinatie met Exploit Blocker voor een betere bescherming tegen
malware die is ontworpen om detectie te omzeilen door middel van verhulling en/of codering. In het geval dat
gewone emulatie of heuristiek een bedreiging niet waarnemen, kan de Geavanceerde geheugenscanner verdacht
gedrag identificeren en bedreigingen scannen wanneer ze zichtbaar worden in het systeemgeheugen. Deze
oplossing is zelfs effectief tegen zwaar verhulde malware.
Anders dan Exploit Blocker is Geavanceerde geheugenscanner een post-execution-methode, wat wil zeggen dat het
risico bestaat dat schadelijke activiteiten hebben plaatsgevonden voordat de bedreiging werd waargenomen.
Echter, indien andere detectietechnieken een bedreiging niet hebben waargenomen, biedt Geavanceerde
geheigenscanner een extra beveiligingslaag.
6.3.3 Netwerkaanvalbeveiliging
Netwerkaanvalbeveiliging is een uitbreiding van de Firewall waarmee de detectie van bekende exploits op
netwerkniveau wordt verbeterd. Door detectie van veelvoorkomende exploits te implementeren in veelgebruikte
protocollen zoals SMB, RPC en RDP, vormt dit een belangrijke extra beschermlaag tegen de verspreiding van
malware, aanvallen via het netwerk en misbruik van kwetsbaarheiden waar nog geen patch voor is uitgegeven of
toegepast.
6.3.4 ESET LiveGrid®
ESET LiveGrid® is gebouwd op het ThreatSense.Net®-systeem voor vroegtijdige waarschuwing en maakt gebruik van
gegevens die ESET-gebruikers over de hele wereld hebben ingediend, en verzendt dit naar het
onderzoekslaboratorium van ESET. Door het aanleveren van verdachte voorbeelden en metadata, geeft ESET
LiveGrid® ons de mogelijkheid direct te voldoen aan de behoeften van onze klanten en ESET alert te houden op de
nieuwste bedreigingen. Malware-onderzoekers van ESET gebruiken de informatie om een nauwkeurige
momentopname te maken van de aard en omvang van wereldwijde bedreigingen, zodat wij ons op de juiste doelen
kunnen richten. ESET LiveGrid®-gegevens spelen een belangrijke rol bij het stellen van prioriteiten in onze
geautomatiseerde verwerking.
Daarnaast stelt het een reputatiesysteem in werking waarmee we de algehele efficiëntie van onze antimalware-
oplossingen kunnen verbeteren. Wanneer een uitvoerbaar bestand of archief wordt onderzocht op het systeem van
een gebruiker, wordt de hash-code eerst vergeleken met een database met items die zijn opgenomen in de witte
en zwarte lijsten. Als de hash-code op de witte lijst wordt gevonden, wordt het onderzochte bestand als schoon
beschouwd en gemarkeerd om te worden overgeslagen tijdens toekomstige scans. Als de hash-code wordt
gevonden op de zwarte lijst, wordt er actie ondernomen die passend is voor de aard van de bedreiging. Als er geen
overeenkomstige hash-code wordt gevonden, wordt het bestand grondig gescand. Afhankelijk van de uitkomst van
deze scan, worden bestanden gecategoriseerd als bedreiging of geen bedreiging. Deze benadering heeft een
duidelijk positief effect op scanprestaties.

168
Met dit reputatiesysteem kunnen malwarevoorbeelden effectief worden gedetecteerd, nog voor de
handtekeningen daarvan via een bijgewerkte virusdatabase worden geïnstalleerd op de computer van de gebruiker
(wat meerdere keren per dag gebeurt).
6.3.5 Botnet-beveiliging
Botnet-beveiliging ontdekt malware door netwerkcommunicatieprotocollen te analyseren. In tegenstelling tot
netwerkprotocollen die de afgelopen jaren niet zijn veranderd, verandert Botnet-malware voortdurend. Dankzij
deze nieuwe technologie kan ESET malware verslaan die detectie probeert te omzeilen en die uw computer met
een botnet-netwerk probeert te verbinden.
6.3.6 Java Exploit Blocker
Java Exploit Blocker is een extensie voor bestaande Exploit Blocker-beveiliging. Deze extensie bewaakt Java en
zoekt naar exploit-achtig gedrag. Geblokkeerde voorbeelden kunnen worden gemeld aan malware-analisten, zodat
zij definities kunnen maken waarmee ze op meerdere niveaus kunnen worden geblokkeerd (URL blokkeren,
bestand downloaden blokkeren, enz.).
6.3.7 Beveiliging van bankieren en betalingen
Beveiliging van bankieren en betalingen is een extra beveiligingslaag bedoeld om uw financiële gegevens te
beschermen tijdens online transacties.
ESET Smart Security Premium bevat een ingebouwde lijst met vooraf gedefinieerde websites die zorgen dat een
beveiligde browser wordt geopend. U kunt een website toevoegen of de lijst met websites in de
productconfiguratie bewerken.
Meer informatie over deze voorziening vindt u in het volgende artikel in de ESET-kennisbank:
Hoe gebruik ik ESET Beveiliging van bankieren en betalingen?
In de meeste gevallen wordt Beveiliging van bankieren en betalingen in uw standaardbrowser gestart wanneer u
een bekende website van een bank bezoekt.

169
We adviseren dat u op Beveiligde browser openen klikt wanneer u dit wordt gevraagd bij gebruik van de Beveiliging
van bankieren en betalingen.
Als u zou beslissen om niet langer gebruik te maken van de beveiligde browser voor een website die u al hebt
opgeslagen, open dan Instellingen > Beveiligingshulpmiddelen > Beveiliging van bankieren en betalingen wanneer
u de website kunt verwijderen van de lijst met URL's waarmee een beveiligde browser wordt gestart.
Voor beveiligd surfen is het gebruik nodig van gecodeerde HTTPS-communicatie. Voor veilig surfen moet uw
internetbrowser voldoen aan de hieronder vermelde minimumvereisten:
Mozilla Firefox 24
Internet Explorer 8
Google Chrome 30
We raden aan dat u de beveiligde browser sluit na het afronden van online transacties of betalingen.
6.3.8 Beveiliging tegen aanvallen met scripts
Beveiliging tegen aanvallen met scripts is een beveiliging tegen javascript in webbrowsers en AMSI-bescherming
(Antimalware Scan Interface) tegen scripts in de Powershell.
WAARSCHUWING
HIPS moet zijn ingeschakeld om deze functie te doen werken.
Beveiliging tegen aanvallen met scripts ondersteunt de volgende webbrowsers:
Mozilla Firefox
Google Chrome
Internet Explorer
Microsoft Edge

170
OPMERKING
De minimaal ondersteunde versies van de webbrowsers kunnen verschillen omdat de signatuur van browsers
vaak verandert. De laatste versie van de webbrowser wordt altijd ondersteund.
6.3.9 Ransomwareschild
Ransomware is een type malware waarbij gebruikers de toegang tot hun systeem wordt ontzegd door het scherm te
vergrendelen of bestanden te coderen. Ransomwareschild bewaakt het gedrag van toepassingen en processen die
uw persoonlijke gegevens proberen te wijzigen. Indien het gedrag van een toepassing wordt beschouwd als
schadelijk of uit scans op basis van reputatie blijkt dat dit gedrag verdacht is, wordt de toepassing geblokkeerd en
wordt aan de gebruiker gevraagd de toepassing te blokkeren of toe te laten.
BELANGRIJK
ESET LiveGrid® moet zijn ingeschakeld om Ransomwareschild correct te laten werken.
6.3.10 UEFI-scanner
UEFI-scanner (Unified Extensible Firmware Interface) maakt deel uit van het Host-based Intrusion Prevention
System (HIPS) dat UEFI op uw computer beveiligt. UEFI is firmware die aan het begin van het opstartproces in het
geheugen wordt geladen. De code bevindt zich op een flashgeheugen-chip die op de systeemkaart is gesoldeerd.
Door deze te infecteren, kunnen aanvallers malware implementeren die overleeft wanneer het systeem opnieuw
wordt opgestart en wanneer het systeem volledig opnieuw wordt geïnstalleerd. De malware kan gemakkelijk
onopgemerkt blijven door antimalwareoplossingen, omdat de meeste van deze oplossingen deze laag niet
scannen.
UEFI-scanner wordt automatisch ingeschakeld. U kunt ook handmatig een computerscan starten in het
hoofdprogrammavenster door te klikken op Computerscan > Geavanceerde scans > Aangepaste scan en
Opstartsectoren/UEFI als doel te selecteren. Zie de sectie Computerscan voor meer informatie over computerscans.
Als uw computer al is geïnfecteerd met UEFI-malware, lees dan het volgende artikel in de ESET-kennisbank:
Mijn computer is geïnfecteerd met UEFI-malware. Wat moet ik doen?
6.4 E-mail
E-mail, of elektronische post, is een moderne communicatievorm met vele voordelen. E-mail is flexibel, snel en
direct, en heeft een cruciale rol gespeeld tijdens de opkomst van internet aan het begin van de jaren negentig.
Jammer genoeg bieden e-mail en internet, met hun hoge mate van anonimiteit, veel ruimte voor illegale
activiteiten zoals spam. Spam kan worden onderverdeeld in ongevraagde advertenties, nepmeldingen en
verspreiding van schadelijke software (malware). Het ongemak en gevaar voor u wordt vergroot door het feit dat de
kosten van het verzenden van spam minimaal zijn en auteurs van spam over veel hulpmiddelen beschikken om
nieuwe e-mailadressen te verwerven. Daarnaast maken het volume en de variatie aan spam het heel moeilijk
hiervoor regels op te leggen. Hoe langer u uw e-mailadres gebruikt, hoe groter de kans dat het in de database van
een spamengine terechtkomt. Enkele tips ter voorkoming hiervan:
Voorkom, indien mogelijk, publicatie van uw e-mailadres op internet.
Verstrek uw e-mailadres alleen aan vertrouwde personen.
Maak, indien mogelijk, geen gebruik van veelvoorkomende aliassen. Hoe ingewikkelder de alias, des te
geringer de kans op spam.
Beantwoord geen spam die reeds in uw Postvak IN is binnengekomen.
Wees voorzichtig met het invullen van internetformulieren. Let met name op selectievakjes als 'Ja, ik wil
informatie ontvangen'.
Gebruik 'gespecialiseerde' e-mailadressen, dus één voor uw werk, één voor communicatie met vrienden, enz.
Verander af en toe van e-mailadres.
Gebruik een antispamoplossing.

171
6.4.1 Advertenties
Adverteren via internet is een van de snelst groeiende vormen van reclame. De belangrijkste marketingvoordelen
zijn de minimale kosten en hoge mate van directheid. Bovendien worden berichten vrijwel onmiddellijk
afgeleverd. Veel bedrijven gebruiken marketinghulpmiddelen via e-mail om op effectieve wijze te communiceren
met huidige en mogelijke klanten.
Deze vorm van adverteren is legitiem, aangezien u mogelijk geïnteresseerd bent in het ontvangen van commerciële
informatie over sommige producten. Maar veel bedrijven verzenden ongevraagd grote hoeveelheden commerciële
berichten. In dergelijke gevallen overschrijdt adverteren per e-mail een grens en wordt het spam.
De hoeveelheid ongevraagde e-mailberichten is een probleem geworden en het lijkt nog niet minder te worden.
Auteurs van ongevraagde e-mailberichten proberen vaak hun spam te laten doorgaan voor legitieme berichten.
6.4.2 Nepmeldingen
Een nepmelding (hoax) is onjuiste informatie die wordt verspreid via internet. Gewoonlijk wordt de nepmelding
verspreid via e-mail en via communicatiemiddelen zoals ICQ en Skype. Het bericht zelf is vaak een grap of een
"broodje aap".
Nepmeldingen over computervirussen zijn bedoeld om angst, onzekerheid en twijfel te zaaien onder de
geadresseerden, zodat zij gaan geloven dat er een 'ondetecteerbaar virus' is dat bestanden verwijdert en
wachtwoorden steelt of andere schadelijke activiteiten uitvoert op hun systeem.
Sommige nepmeldingen werken doordat ontvangers worden gevraagd de berichten door te sturen naar hun
contactpersonen, waardoor deze blijven voortbestaan. Er zijn nepmeldingen over mobiele telefoons, verzoeken om
hulp, mensen die aanbieden u geld toe te sturen vanuit het buitenland, enz. In de meeste gevallen is het
onmogelijk achter de ware bedoelingen van de schepper van de melding te komen.
Als u een bericht ziet waarin u wordt gevraagd dit door te sturen naar iedereen die u kent, kan het heel goed een
nepmelding kan zijn. Er zijn vele websites op internet waar kan worden geverifieerd of een e-mailbericht legitiem
is of niet. Voer, alvorens een bericht door te sturen, eerst een zoekactie op het internet uit voor elk bericht waarvan
u vermoedt dat het een nepmelding is.
6.4.3 Phishing
De term 'phishing' verwijst naar een criminele activiteit die is gebaseerd op 'social engineering'. Hierbij worden
gebruikers gemanipuleerd met als doel vertrouwelijke gegevens te verkrijgen. Met phishing wordt geprobeerd
toegang te krijgen tot vertrouwelijke gegevens zoals bankrekeningnummers, pincodes, enzovoort.
De meestgebruikte methode is het verzenden van een e-mailbericht waarin iemand zich voordoet als een
betrouwbare persoon of onderneming (bijvoorbeeld een financiële instelling of verzekeringsmaatschappij). Dit e-
mailbericht kan er zeer authentiek uitzien en bevat mogelijk afbeeldingen en tekst die afkomstig zijn van de bron
die wordt geïmiteerd. Onder valse voorwendselen (gegevensverificatie, financiële transacties) wordt u gevraagd
persoonlijke gegevens (bankrekeningnummers, gebruikersnamen of wachtwoorden) in te voeren. Als u dergelijke
gegevens verstrekt, is het risico van diefstal en misbruik groot.
Banken, verzekeringsmaatschappijen en andere legitieme bedrijven zullen nooit ongevraagd e-mailberichten
sturen om gebruikersnamen en wachtwoorden op te vragen.

172
6.4.4 Spam herkennen
In het algemeen zijn er enkele aanwijzingen te noemen die u kunnen helpen spam (ongevraagde e-mailberichten)
in uw postvak te herkennen. Als een bericht aan ten minste enkele van de volgende criteria voldoet, is het
waarschijnlijk een spambericht.
Het adres van de afzender behoort niet toe aan iemand op uw lijst met contactpersonen.
U wordt een groot geldbedrag aangeboden, maar u moet eerst zelf een gering bedrag op tafel leggen.
Onder valse voorwendselen (verificatie van gegevens, financiële activiteiten) wordt u gevraagd een aantal van
uw persoonlijke gegevens, zoals bankrekeningnummers, gebruikersnamen en wachtwoorden in te voeren.
Het is geschreven in een vreemde taal.
U wordt gevraagd een product te kopen waarin u niet bent geïnteresseerd. Als u besluit toch tot aanschaf over
te gaan, controleert u of de afzender van het bericht een betrouwbare leverancier is (raadpleeg de
oorspronkelijke productfabrikant).
Sommige van de woorden zijn onjuist gespeld in een poging om uw spamfilter te omzeilen. Bijvoorbeeld
'vaigra' in plaats van 'viagra', enzovoort.
6.4.4.1 Regels
Regels in antispamoplossingen en e-mailclients zijn hulpmiddelen voor het aanpassen van e-mailfuncties. Regels
bestaan uit twee logische elementen:
1. Voorwaarde (bijvoorbeeld een inkomend bericht dat van een bepaald adres afkomstig is)
2. Actie (bijvoorbeeld het bericht verwijderen of het bericht naar een opgegeven map verplaatsen)
Het aantal regels en de combinatie van regels verschillen per antispamoplossing. Deze regels worden gebruikt als
maatregelen tegen spam (ongevraagde e-mail). Enkele voorbeelden:
1. Voorwaarde: een inkomend e-mailbericht bevat bepaalde woorden die vaak in spamberichten voorkomen.
2. Actie: het bericht wordt verwijderd.
1. Voorwaarde: een inkomend e-mailbericht bevat een bijlage met de extensie .exe.
2. Actie: de bijlage wordt verwijderd en het bericht wordt in het postvak bezorgd.
1. Voorwaarde: er komt een bericht binnen dat van uw werkgever afkomstig is.
2. Actie: het bericht wordt naar de map 'Werk' verplaatst.
Wij adviseren u een combinatie van regels in antispamprogramma's te gebruiken om het beheer te vereenvoudigen
en spam effectiever te filteren.
6.4.4.2 Witte lijst
In het algemeen is een witte lijst een lijst met items of personen die zijn geaccepteerd of waaraan rechten zijn
toegekend. De term 'witte e-maillijst' verwijst naar een lijst met contactpersonen waarvan de gebruiker berichten
wil ontvangen. Dergelijke witte lijsten zijn gebaseerd op sleutelwoorden waarnaar wordt gezocht in e-
mailadressen, domeinnamen of IP-adressen.
Als de 'exclusiviteitsmodus' actief is voor de witte lijst, worden berichten van andere adressen, domeinen of IP-
adressen niet ontvangen. Als een witte lijst niet exclusief is, worden dergelijke berichten niet verwijderd, maar op
een andere manier gefilterd.
Een witte lijst is het tegenovergestelde van een zwarte lijst. Anders dan zwarte lijsten zijn witte lijsten betrekkelijk
eenvoudig te beheren. Wij adviseren u zowel de witte lijst als de zwarte lijst te gebruiken om spam effectiever te
filteren.

173
6.4.4.3 Zwarte lijst
In het algemeen is een zwarte lijst een lijst met niet-geaccepteerde of verboden items of personen. In de virtuele
wereld is het een techniek die het mogelijk maakt berichten te accepteren van alle gebruikers die niet op een
dergelijke lijst staan.
Er zijn twee typen zwarte lijst: die door gebruikers zijn gemaakt binnen hun antispamtoepassing, en professionele,
regelmatig bijgewerkte zwarte lijsten die worden gemaakt door gespecialiseerde instellingen die te vinden zijn op
het internet.
Het gebruik van zwarte lijsten is essentieel voor het blokkeren van spam, maar ze zijn zeer moeilijk bij te houden
aangezien er elke dag nieuwe items verschijnen die moeten worden geblokkeerd. We raden aan zowel een witte
lijst als een zwarte lijst te gebruiken om spam zo effectief mogelijk te filteren.
6.4.4.4 Uitzonderingenlijst
Op de uitzonderingenlijst staan e-mailadressen die mogelijk vervalst zijn en voor het verzenden van spam worden
gebruikt. E-mailberichten afkomstig van adressen die in de uitzonderingenlijst staan, worden altijd gescand op
spam. Standaard bevat de uitzonderingenlijst alle e-mailadressen van bestaande e-mailclientaccounts.
6.4.4.5 Controle vanaf de server
Controle vanaf de server is een techniek voor het identificeren van massaal verzonden spamberichten op basis van
het aantal ontvangen berichten en de reacties van gebruikers. Elk bericht laat een unieke digitale 'voetafdruk'
achter op basis van de inhoud van het bericht. Het unieke identificatienummer zegt niets over de inhoud van de e-
mail. Twee identieke berichten hebben een identieke voetafdruk, terwijl verschillende berichten verschillende
voetafdrukken hebben.
Als een bericht is gemarkeerd als spam, wordt de voetafdruk naar de server verzonden. Als de server meerdere
identieke voetafdrukken (overeenkomstig met een bepaald spambericht) ontvangt, wordt de voetafdruk
opgeslagen in de database met spamvoetafdrukken. Tijdens het scannen van binnenkomende berichten verzendt
het programma de voetafdrukken van de berichten naar de server. De server retourneert informatie over welke
voetafdrukken overeenkomen met berichten die reeds door gebruikers zijn gemarkeerd als spam.

174
7. Veelgestelde vragen
In dit hoofdstuk worden enkele veelgestelde vragen en regelmatig voorkomende problemen beschreven. Klik op
de titel van het onderwerp om erachter te komen hoe u uw probleem kunt oplossen:
ESET Smart Security Premium bijwerken
Een virus van de pc verwijderen
Communicatie toestaan voor een bepaalde toepassing
Ouderlijk toezicht inschakelen voor een account
Een nieuwe taak maken in Planner
Een scantaak plannen (elke 24 uur)
Als uw probleem niet op de bovenstaande Help-pagina's staat vermeld, zoek dan op de Help-pagina's van ESET
Smart Security Premium.
Als u de oplossing voor uw probleem of het antwoord op uw vraag niet kunt vinden op de Help-pagina's, ga dan naar
onze regelmatig bijgewerkte online ESET-kennisbank. Hieronder staan koppelingen naar de populairste artikelen in
de kennisbank zodat u veelvoorkomende problemen kunt oplossen:
Ik krijg een activeringsfout bij het installeren van mijn ESET-product. Wat betekent dat?
Mijn ESET-thuisproduct voor Windows activeren met behulp van mijn gebruikersnaam, wachtwoord of
licentiecode
Mijn ESET-thuisproduct verwijderen of opnieuw installeren
Ik krijg een bericht dat mijn ESET-installatie voortijdig is beëindigd
Wat moet ik doen na het vernieuwen van mijn licentie? (thuisgebruikers)
Wat als ik mijn e-mailadres wijzig?
Hoe start ik Windows in Veilige modus of Veilige modus met netwerkmogelijkheden
Neem indien nodig contact op met onze Klantenservice met uw vragen of vragen. Het contactformulier vindt u op
het tabblad Help en ondersteuning van ESET Smart Security Premium.
7.1 ESET Smart Security Premium bijwerken
U kunt ESET Smart Security Premium handmatig of automatisch bijwerken. U kunt de update activeren door op Nu
bijwerken te klikken in het gedeelte Bijwerken.
Bij de standaardinstallatie wordt een automatische updatetaak gemaakt die elk uur wordt uitgevoerd. Als u het
interval wilt wijzigen, navigeert u naar Hulpmiddelen > Planner (klik hier voor meer informatie over Planner).
7.2 Een virus van de pc verwijderen
Als de computer tekenen van infectie door malware vertoont, bijvoorbeeld trager is, vaak vastloopt, enz., adviseren
wij u het volgende te doen:
1. Klik in het hoofdprogrammavenster op Computerscan.
2. Klik op Scan op computer uitvoeren om te beginnen met het scannen van uw systeem.
3. Controleer, nadat de scan is voltooid, het logbestand met het aantal gescande, geïnfecteerde en opgeschoonde
bestanden.
4. Als u alleen een bepaald gedeelte van de schijf wilt scannen, klikt u op Aangepaste scan en selecteert u de
doelen die u wilt scannen op virussen.
Voor aanvullende informatie verwijzen wij u naar ons artikel in de ESET-kennisbank die regelmatig wordt
bijgewerkt.

175
7.3 Communicatie toestaan voor een bepaalde toepassing
Als een nieuwe verbinding wordt gedetecteerd in de interactieve modus waarvoor geen regel beschikbaar is, wordt
u gevraagd de verbinding toe te staan of te weigeren. Als u wilt dat ESET Smart Security Premium steeds dezelfde
actie uitvoert wanneer de toepassing verbinding probeert te maken, schakelt u het selectievakje Actie onthouden
(regel maken) in.
U kunt nieuwe Firewall-regels voor toepassingen maken voordat deze door ESET Smart Security Premium worden
gedetecteerd in het instellingenvenster voor Firewall, onder Netwerk > Firewall > Regels en zones > Instellingen.
De filtermodus van Firewall moet worden ingesteld op Interactieve modus om het tabblad Regels beschikbaar te
maken in Instellingen voor zones en regels.
Voer op het tabblad Algemeen de naam, de richting en het communicatieprotocol voor de regel in. In dit venster
kunt u de actie definiëren die moet worden uitgevoerd als de regel wordt toegepast.
Voer het pad naar het uitvoerbare bestand van de toepassing en de lokale communicatiepoort in op het tabblad
Lokaal. Klik op het tabblad Extern om het externe adres en de externe poort (indien van toepassing) in te voeren.
De nieuw gemaakte regel wordt toegepast zodra de toepassing opnieuw probeert te communiceren.
7.4 Ouderlijk toezicht inschakelen voor een account
Volg de onderstaande stappen om Ouderlijk toezicht te activeren voor een specifiek gebruikersaccount:
1. Ouderlijk toezicht is standaard uitgeschakeld in ESET Smart Security Premium. Er zijn twee methoden voor het
activeren van Ouderlijk toezicht:
o Klik op in Instellingen > Beveiligingshulpprogramma's > Ouderlijk toezicht in het
hoofdprogrammavenster en wijzig de status voor Ouderlijk toezicht in ingeschakeld.
o Druk op F5 om de boomstructuur Geavanceerde instellingen te openen, navigeer naar Web en e-mail >
Ouderlijk toezicht en schakel de schakelaar naast Integreren in systeem in.
2. Klik op Instellingen > Beveiligingshulpprogramma's > Ouderlijk toezicht in het hoofdprogrammavenster. Hoewel
Ingeschakeld wordt weergegeven naast Ouderlijk toezicht, moet u Ouderlijk toezicht configureren voor het
gewenste account door te klikken op Kindaccount beveiligen of Ouderaccount. Voer in het volgende venster de
geboortedatum in om het toegangsniveau en aanbevolen webpagina's die voor die leeftijd geschikt zijn te
bepalen. Ouderlijk toezicht wordt nu ingeschakeld voor het opgegeven gebruikersaccount. Klik op
Geblokkeerde inhoud en instellingen... onder de accountnaam om aan te geven welke categorieën u wilt
toestaan of blokkeren op het tabblad Categorieën. Klik op het tabblad Uitzonderingen om aangepaste
webpagina's toe te staan of te blokkeren die niet overeenkomen met een categorie.

176
7.5 Een nieuwe taak maken in Planner
U kunt een nieuwe taak maken in Hulpmiddelen > Meer hulpmiddelen > Planner, klik op Toevoegen of klik met de
rechtermuisknop en selecteer Toevoegen... in het contextmenu. Er zijn vijf typen geplande taken beschikbaar:
Externe toepassing uitvoeren: hiermee kunt u de uitvoering van een externe toepassing plannen.
Logbestanden onderhouden: logbestanden bevatten tevens restanten van verwijderde records. Met deze taak
optimaliseert u regelmatig records in logbestanden om effectief te werken.
Controle van systeemopstartbestanden: hiermee worden bestanden gecontroleerd die tijdens het opstarten
of aanmelden mogen worden uitgevoerd.
Momentopname van computerstatus maken: hiermee maakt u een ESET SysInspector-momentopname van de
computer, waarbij gedetailleerde informatie over systeemonderdelen (zoals stuurprogramma's en
toepassingen) wordt verzameld en het risiconiveau van elk onderdeel wordt beoordeeld.
Computerscan op aanvraag: hiermee wordt een scan uitgevoerd op bestanden en mappen op uw computer.
Bijwerken: hiermee wordt een updatetaak gepland door de modules bij te werken.
Aangezien Bijwerken een van de meest geplande taken is, wordt hieronder uitgelegd hoe u een nieuwe updatetaak
kunt toevoegen:

177
Selecteer Bijwerken in het vervolgkeuzemenu Geplande taak. Voer de naam van de taak in het veld Taaknaam in en
klik op Volgende. Selecteer de frequentie van de taak. De volgende opties zijn beschikbaar: Eenmaal, Herhaaldelijk,
Dagelijks, Wekelijks en Bij gebeurtenis. Selecteer Taak overslaan indien op batterijvoeding om het gebruik van
systeembronnen te minimaliseren als een laptop op batterijvoeding werkt. De taak wordt uitgevoerd op de datum
en tijd die is opgegeven in de velden van Taakuitvoering. Vervolgens definieert u de actie die moet worden
ondernomen als de taak niet kan worden uitgevoerd of voltooid op het geplande tijdstip. De volgende opties zijn
beschikbaar:
Op het volgende geplande tijdstip
Zo spoedig mogelijk
Meteen, als tijd sinds vorige keer uitvoeren groter is dan een opgegeven waarde (het interval kan worden
opgegeven bij het schuifvak Tijd sinds vorige keer uitvoeren (uren))
In de volgende stap wordt een venster weergegeven met een samenvatting van de huidige geplande taak. Klik op
Voltooien als u klaar bent met het aanbrengen van wijzigingen.
Er wordt een dialoogvenster weergegeven waarin u de profielen kunt kiezen voor gebruik bij de geplande taak. Hier
kunt u het primaire en alternatieve profiel instellen. Het alternatieve profiel wordt gebruikt als de taak niet kan
worden voltooid met het primaire profiel. Bevestig uw keuze door op Voltooien te klikken. De nieuwe geplande
taak wordt toegevoegd aan de lijst met huidige geplande taken.
7.6 Een wekelijkse computerscantaak plannen
Als u een regelmatig terugkerende taak wilt plannen, opent u het hoofdprogrammavenster en klikt u op
Hulpmiddelen > Meer hulpmiddelen > Planner. Hieronder ziet u een korte handleiding over het plannen van een
taak die elke 24 uur een scan van de lokale schijven uitvoert. Zie ons Knowledgebase-artikel voor meer
gedetailleerde instructies.
Een scantaak plannen:
1. Klik op Toevoegen in het hoofdprogrammavenster van Planner.
2. Selecteer Computerscan op aanvraag in het vervolgkeuzemenu.
3. Geef een naam op voor de taak en selecteer Wekelijks als taakfrequetie.
4. Stel de dag en de tijd in waarop de taak moet worden uitgevoerd.
5. Selecteer Taak zo spoedig mogelijk uitvoeren om de taak later uit te voeren wanneer de geplande taak om
welke reden dan ook niet wordt gestart (bijvoorbeeld omdat de computer was uitgeschakeld).
6. Bekijk de samenvatting van de geplande taak en klik op Voltooien.
7. Selecteer Lokale schijven in het vervolgkeuzemenu Lokale schijven.
8. Klik op Voltooien om de taak toe te passen.
7.7 Geavanceerde instellingen ontgrendelen
Wanneer u de beveiligde functie Geavanceerde instellingen wilt openen, wordt het venster voor het invoeren van
het wachtwoord weergegeven. Als u uw wachtwoord bent vergeten of kwijt bent, klikt u hieronder op de optie
Wachtwoord herstellen en voert u het e-mailadres in dat u hebt gebruikt om uw licentie te registreren. ESET stuurt
u dan een e-mail met de verificatiecode. Voer de verificatiecode in, typ een nieuw wachtwoord en bevestig het
nieuwe wachtwoord. De verificatiecode is 7 dagen geldig.
Ook kunt u uw wachtwoord herstellen via uw my.eset.com-account. Gebruik deze optie als de licentie is gekoppeld
aan uw ESET Licentiebeheer.
Als u zich uw e-mailadres niet kunt herinneren, klikt u op Ik weet mijn e-mailadres niet. U wordt dan doorgestuurd
naar de ESET-website om snel contact op te nemen met onze afdeling Klantenservice.

178
Geneer code voor klantenservice: met deze optie genereert u de code die u aan de klantenservice geeft. Kopieer
de code en klik op Ik heb een verificatiecode. Voer de verificatiecode in, typ een nieuw wachtwoord en bevestig uw
nieuwe wachtwoord. De verificatiecode is 7 dagen geldig.
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
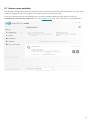 17
17
-
 18
18
-
 19
19
-
 20
20
-
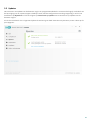 21
21
-
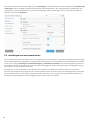 22
22
-
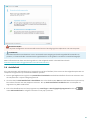 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
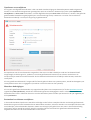 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
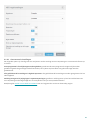 53
53
-
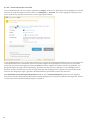 54
54
-
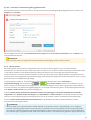 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
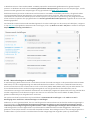 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
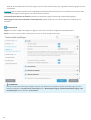 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
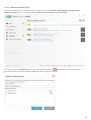 91
91
-
 92
92
-
 93
93
-
 94
94
-
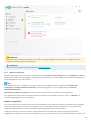 95
95
-
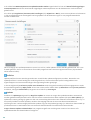 96
96
-
 97
97
-
 98
98
-
 99
99
-
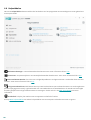 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
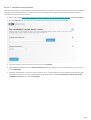 109
109
-
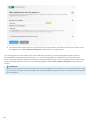 110
110
-
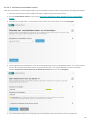 111
111
-
 112
112
-
 113
113
-
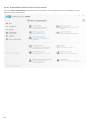 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
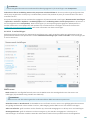 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
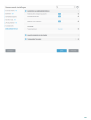 135
135
-
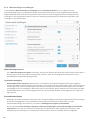 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
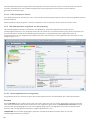 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
-
 151
151
-
 152
152
-
 153
153
-
 154
154
-
 155
155
-
 156
156
-
 157
157
-
 158
158
-
 159
159
-
 160
160
-
 161
161
-
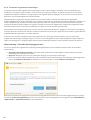 162
162
-
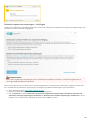 163
163
-
 164
164
-
 165
165
-
 166
166
-
 167
167
-
 168
168
-
 169
169
-
 170
170
-
 171
171
-
 172
172
-
 173
173
-
 174
174
-
 175
175
-
 176
176
-
 177
177
-
 178
178
ESET Smart Security Premium Gebruikershandleiding
- Type
- Gebruikershandleiding
Gerelateerde papieren
-
ESET SMART SECURITY Gebruikershandleiding
-
ESET Internet Security Gebruikershandleiding
-
ESET SMART SECURITY Gebruikershandleiding
-
ESET Smart Security Premium 12 de handleiding
-
ESET Internet Security 12 de handleiding
-
ESET Internet Security 14 de handleiding
-
ESET Smart Security Premium 14 de handleiding
-
ESET Smart Security Premium 13 de handleiding
-
ESET NOD32 Antivirus Gebruikershandleiding
-
ESET NOD32 Antivirus Gebruikershandleiding



















































































































































































